12. Describe the operation of a ripple-carry adder. Why are ripple-carry adders not used in most computers today?
Answers
A ripple-carry adder is a digital circuit that performs the addition of two binary numbers. It is called a ripple-carry adder because each bit in the result "ripples" into the next bit, using a carry bit that is passed from one stage to the next.
The two binary numbers to be added are presented as input to the adder.The least significant bits of the two numbers are added together, along with any carry-in bit from the previous stage. The sum and carry-out bits are generated as outputThe process is repeated for each bit position, with the carry-out from the previous stage being used as the carry-in for the current stageThe final result is the sum of the two input numbers, with any carry-out from the most significant bit being discardedWhile the ripple-carry adder is a simple and straightforward method for adding two binary numbers, it has a few drawbacks that limit its usefulness in modern computers. One of the primary issues is its relatively slow operation, as each stage in the adder must wait for the previous stage to complete before it can begin its own calculation. This leads to a longer overall calculation time, which is unacceptable for many high-speed computing applications.Additionally, the ripple-carry adder requires a large number of full addercircuits to be implemented, which can take up a significant amount of space on a computer chip. This is not a major issue for smaller adders, but as the number of bits being added increases, the amount of space required can become prohibitive.As a result of these limitations, ripple-carry adders are typically not used in most modern computers. Instead, faster and more efficient adders, such as carry-lookahead adders or carry-select adders, are used to perform binary addition in a more optimized and streamlined manner.
To learn more about binary numbers. click on the link below:
brainly.com/question/31596830
#SPJ11
Related Questions
Question 15(Multiple Choice Worth 6 points)
(03.02 MC)
Which of the actions below becomes part of your digital identity?
O Meeting a friend at a juice shop
Attending your school's prom
Borrowing a neighbor's blender
Responding to an email
Answers
Answer:
Responding to an email
Explanation:
I did the assignment. The other ones you do not use any technology, while you do when responding to an email.
The one that is becoming a part of digital identity is responding to a mail. The correct option is D.
What is digital identity?A digital identity is the body of information that exists online about an individual, organization, or electronic device. Individuals or their devices can be identified using unique identifiers and usage patterns.
Your Digital Identity allows you to prove who you are online for work, education, and personal purposes, and you can use it again and again.
Before any of your details are shared with the service you want to access, you will be asked to give consent each time you use your Digital Identity.
Thus, the correct option is D.
For more details regarding digital identity, visit:
https://brainly.com/question/26077914
#SPJ1
Which do you think is the most important C of credit?
Answers
Answer:
If you have borrowed money, you have most likely heard your lender discuss the Five C's of Credit. Recently, many lenders have indicated that character of the borrower is the most important of the Five C's, particularly in tough economic times.
Hope this helps!
Don't forget to mark me as Brainliest.
A summer camp offers a morning session and an afternoon session. The list morningList contains the names of all children attending the morning session, and the list afternoonList contains the names of all children attending the afternoon session.
Only children who attend both sessions eat lunch at the camp. The camp director wants to create lunchList, which will contain the names of children attending both sessions.
The following code segment is intended to create lunchList, which is initially empty.
It uses the procedure IsFound (list, name), which returns true if name is found in list and returns false otherwise.
FOR EACH child IN morningList
{
}
Which of the following could replace so that the code segment works as intended?
(A)
IF (IsFound (afternoonList, child))
{
APPEND (lunchList, child)
}
(B)
IF (IsFound (lunchList, child))
{
APPEND (afternoonList, child)
}
(C)
IF (IsFound (morningList, child))
{
APPEND (lunchList, child)
}
(D)
IF ((IsFound (morningList, child)) OR
(IsFound (afternoonList, child)))
{
APPEND (lunchList, child)
}
Answers
Answer:
The answer is "Option A".
Explanation:
In this question, the choice "A" is correct because in this a conditional if block statement is used that that use "IsFound" method that takes two parameters "afternoonList and Child" in its parameter and use the append method that takes "lunchList and child" in parameter and add values, that's why other choices are wrong.
Deb needs to add borders on the cells and around the table she has inserted into her Word document.
Where should she go to achieve this?
Insert tab, Tables group
Table Tools Design contextual tab
Home tab, Page Layout
Home tab, Format group
Answers
Answer:
Answer: B) Table Tools Design , contextual tab
Explanation:
Answer:
B
Explanation:
EDGE 2021
what is the best definition of inflation?
Answers
Inflation is a situation of rising prices in the economy. A more exact definition of inflation is a sustained increase in the general price level in an economy. Inflation means an increase in the cost of living as the price of goods and services rise.
Or inflation can be growing the size (blowing up a balloon)
what is the most popular monitor
Answers
Which organization has published more than 300 Web standards, and encourages manufacturers to follow these standards, many of which define levels of conformance? This task contains the radio buttons and checkboxes for options. The shortcut keys to perform this task are A to H and alt+1 to alt+9.
A) World Wide Web Consortium (W3C)
B) Institute of Electrical and Electronics Engineers (IEEE)
C) Internet Engineering Task Force (IETF)
D) International Organization for Standardization (ISO)
Answers
Answer:
c
Explanation:
what is the output
a = 10
b = 23
print (a+b * a)
Answers
Answer:
240 is the output.
hope it will help you.
when information collected for one purpose is put to another purpose, that is called a group of answer choices backdoor exploit cookie secondary use of the data collaborative filter data leveraging opportunity
Answers
It is referred to as a when information is used for another purpose. data's secondary use. There is a policy that states that any information sharing between organizations must have the explicit consent of the consumer. opt-in.
Data mining, also known as knowledge discovery in databases, is a process used in computer science to identify intriguing and practical patterns and relationships in massive data sets. When you visit a website, a little text file called a cookie is downloaded and saved to your computer's hard disk. When you return to the same website later, the web server will be able to read the information in this text file. There are many uses for cookies. Queries. In a database, queries can carry out a wide range of tasks.
Learn more about information here-
https://brainly.com/question/27798920
#SPJ4
What command can be used to troubleshoot routing by displaying all routers between the current computer and a remote computer
Answers
The "traceroute" command can be used to troubleshoot routing by displaying all routers between the current computer and a remote computer.
The "traceroute" command is a network diagnostic tool used to track the route that an IP packet takes from the source computer to a destination computer. It provides information about each hop along the path, including the IP addresses and round-trip times.
By sending packets with increasing Time-to-Live (TTL) values, traceroute identifies the intermediate routers between the source and destination.
This command helps in troubleshooting network connectivity issues, identifying network latency or packet loss, and understanding the network topology. It is available on various operating systems and is a valuable tool for network administrators and engineers.
Learn more about traceroute command here:
https://brainly.com/question/13014215
#SPJ4
Set of programs that coordinates all the activities among computer hardware devices.
Answers
Set of programs that coordinates all the activities among computer hardware devices is Operating system (OS).
An operating system (OS) is a type of system software that controls how computer hardware and software resources are used and offers basic services to other software applications.
Operating systems that use time-sharing plan activities to make the most of the system's resources. They may also contain accounting software to allocate costs for processing time, mass storage, printing, and other resources.
Although application code is typically run directly by the hardware and frequently makes system calls to an OS function or is interrupted by it, the operating system serves as a bridge between programs and computer hardware for hardware functions like input and output and memory allocation. From mobile phones and video game consoles to web servers and supercomputers, many devices that house a computer have operating systems.
To know more about operating system (OS), visit;
brainly.com/question/25143116
#SPJ4
Give 3 ways in which the middle adulthood experience is different than it was a generation ago
Answers
The middle adulthood experience has significantly changed compared to a generation ago, primarily due to1) advancements in technology, 2)evolving social norms, and 3)changes in work dynamics.
Technological Advancements: One significant difference in the middle adulthood experience compared to a generation ago is the rapid advancement of technology. Today, individuals in middle adulthood have access to a wide range of digital tools and platforms that have transformed various aspects of their lives. Communication has become instantaneous and more accessible, with the widespread use of smartphones and social media. Additionally, technology has reshaped industries and the nature of work, creating new job opportunities and altering traditional career paths. This shift has brought both benefits and challenges, requiring middle-aged individuals to adapt to new technologies and skills to remain competitive in the job market.
Evolving Social Norms: Middle adulthood today is influenced by evolving social norms and cultural shifts. Compared to a generation ago, there is a greater emphasis on individualism and personal fulfillment. Middle-aged individuals now have more freedom to explore their personal interests, pursue hobbies, and engage in self-care. There is also an increased acceptance and recognition of diverse lifestyles and relationships, including same-sex partnerships, blended families, and unconventional career choices. These changing social norms have created a more inclusive and diverse environment for middle-aged individuals to navigate their personal and professional lives.
Changes in Work Dynamics: The nature of work has transformed significantly over the past generation, impacting the middle adulthood experience. Traditional career paths and long-term job security have become less common, with more individuals engaging in freelance work, gig economy jobs, or pursuing entrepreneurial ventures. This shift has brought greater flexibility but also increased uncertainty and financial instability. Additionally, the rapid pace of technological advancement has led to automation and job displacement in certain industries, requiring middle-aged individuals to upskill and adapt to new roles. Work-life balance and the integration of work and personal life have also become important considerations, with a growing emphasis on flexible work arrangements and remote work options.
In summary, middle adulthood today differs from a generation ago due to technological advancements, evolving social norms, and changes in work dynamics. These factors have reshaped communication, individual autonomy, career paths, and work-life balance, presenting both new opportunities and challenges for individuals in this life stage.
learn more about middle adulthood experience here:
https://brainly.com/question/32106528
#SPJ11
For a computer to be able to process data it needs to be converted to binary data.True or False
Answers
Answer:
I'm pretty sure that it's true.
The statement "For a computer to be able to process data, it needs to be converted to binary data" is true.
What is binary data?Binary data or binary codes are the codes that are a language used by a computer to read the data. The computer reads the data only in binary codes. They use “On” (1) and “Off” (0) to convey everything from webpages to Video games. This basically allows for computers to communicate in a simpler way by just using On/Off or 1's and 0's.
After the conversion of Analog to Digital Converter (ADC), the data is stored in a series of numbers encoded in binary mode (combinations of Zeros and Ones).
The on and off are electrical signals, which are on and off, to see everything in binary numbers.
Therefore, the statement is true.
To learn more about binary data, refer to the link:
https://brainly.com/question/27752107
#SPJ2
explain the difference between paste and paste special
Answers
Answer:
Explanation:
Ñ fas sentido so colocou o especial
when an individual element of an array is passed to a method . question 9 options: a) a reference to the array is passed b) it is passed like any other variable c) the method does not have access to the original array d) all of these are true.
Answers
The correct option is D i.e all of these are true. An array is often supplied to a function or method as a reference parameter when it is passed as a parameter. In reality, the address of its first element is passed.
Due to the fact that arrays are frequently supplied by reference, if the function modifies the value of an element in an array, the corresponding actual array will also modify that element. One must provide the parameters before declaring an array of real numbers as a parameter.
Therefore, no new array is made. The same array is referenced by both the argument and parameter.
Array items and their subscripts must be provided in the function call if specific elements are to be sent as arguments. Simple variables are used in function definition to receive the elements. Additionally, when a single element from an array is provided to a method, that method does have direct access to the process's original array.
Use the array's indexed name as an argument in the method call to pass a specific array element to it. The ref keyword must be used if you want to transmit a value-type array element.
To learn more about methods click here:
brainly.com/question/28256755
#SPJ4
Unscramble the words
A: ESUOM RETUPOC
B: KSID EVIRD
Answers
B. Disk drive
B) Disk Drive
hope this helps x
Python String Functions: Create a new Python Program called StringPractice. Prompt the user to input their name, then complete the following:
Length
• Print: “The length of your name is: [insert length here]”
Equals
• Test to see if the user typed in your name. If so, print an appropriate message
Really appreciate the help.
Answers
#Swap this value by your name. Mine is Hamza :)
my_name = "Hamza"
#Get input from user.
inp = input("What's your name?: ")
#Print the length of his/her name.
print("The length of your name is",len(inp),"characters.")
#Check if the input matches with my name?
#Using lower() method due to the case insensitive. Much important!!
if(inp.lower()==my_name.lower()):
print("My name is",my_name,"too! Nice to meet you then.")
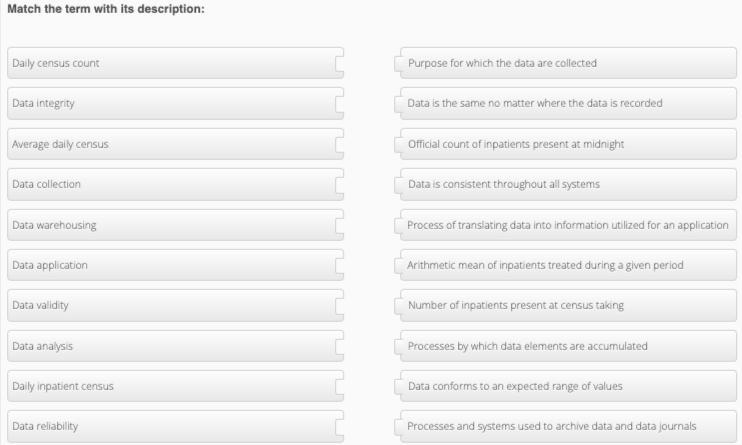
Please! I need help matching this.
Answers
We can see here that matching the term with its description, we have:
Daily census count: Official count of inpatients present at midnightData integrity: Data conforms to an expected range of valuesAverage daily census: Arithmetic mean of inpatients treated during a given periodData collection: Processes by which data elements are accumulatedData warehousing: Processes and systems used to archive data and data journals.What is data?Data refers to a collection of facts, figures, statistics, measurements, or any other information that can be analyzed or used to gain insights and knowledge about a particular subject or topic. In today's digital age, data can exist in various forms such as text, numbers, images, audio, and video.
Continuation of the matching:
Data application: Process of translating data into information utilized for an applicationData validity: Purpose for which the data are collectedData analysis: Processes by which data elements are accumulatedDaily inpatient census: Number of inpatients present at census takingData reliability: Data is consistent throughout all systems.Learn more about data on https://brainly.com/question/28132995
#SPJ1
screenshot of sql queryselect * from employee where jobcode = 'fte' and lastname = 'james' what does the asterisk (*) after select tell the database to do in this query?
Answers
The asterisk (*) after the "SELECT" keyword in the given SQL query instructs the database to retrieve all columns from the "employee" table that match the specified conditions.
In SQL, the asterisk (*) is a shorthand notation used in the "SELECT" statement to represent all columns in a table. By including the asterisk after "SELECT" in the query
"SELECT * FROM employee",
the database understands that it should retrieve all columns from the "employee" table. This means that the query will return all the data (all columns) for the rows that satisfy the conditions specified in the "WHERE" clause, which in this case are
"jobcode = 'fte'" and "lastname = 'james'".
To know more about SQL queries click here: brainly.com/question/30755095
#SPJ11
Explain media streaming and buffering process (Include the buffering diagram)
Answers
ANYONE AHHH HELP ME 50 Points





Answers
Answer:
1, tilt 2, zoom
Explanation:
I'm not sure I have a camera but I don't take pictures like prof
Write an application that allows a user to input the height and width of a rectangle. It should output the area and perimeter of the rectangle. Use methods for entering the values, performing the computations, and displaying the results. Results should be formatted with one position to the right of the decimal and printed number aligned in a tabular display.
Answers
Answer:
Explanation:
This code is written in Java. It creates a Rectangle class that contains variables for the height and width. It also contains constructor, methods for calculating perimeter and area, and a printInfo method to print out all the results. A test case has been created in the main method which creates a Rectangle object and prints out the printInfo which calls the area and perimeter methods as well. The output can be seen in the attached image below. Due to technical difficulties I have added the code as a txt file below.

1. List five types of information data brokers are collecting about
you.
2. What is Disconnect?
Answers
Data brokers collect a wide variety of information, such as personal, demographic, and behavioral data. Disconnect is a software application designed to help protect users' online privacy and security.
Data brokers might collect the following types of information: (1) Personal details like name, age, gender, and contact information, (2) Online activities, including browsing history and social media behavior, (3) Financial information, such as credit scores, income, and purchasing habits, (4) Demographic details, including education level, marital status, and family size, (5) Health-related data, including medical conditions and insurance information. Meanwhile, Disconnect is an app that blocks trackers to improve browser speed and performance while ensuring your online privacy. It protects against unwanted tracking and encrypts your internet connection, enhancing your overall online experience and ensuring your data isn't harvested without your consent.
Learn more about data brokers here:
https://brainly.com/question/12448881.
#SPJ11
he concept that internet service providers (isps) permit data to be transmitted and accessed without regard to the data’s content or amount of bandwidth required to transmit the data is known as net
Answers
The concept that internet service providers (isps) permit data to be transmitted and accessed without regard to the data’s content or amount of bandwidth required to transmit the data is known as net neutrality.
Does net neutrality exist in the US?While many states have passed their own versions of net neutrality legislation, most of these have largely complied with the FCC's established guidelines. States do not have the power to override the FCC decision, according to language in the FCC's repeal.
According to the concept of "net neutrality," all websites, applications, and material must be accessible at the same speed and on the same terms, without any content being blocked or given priority by an internet service provider (ISP).
Therefore, Internet service providers (ISPs) should treat all internet traffic equally, according to this idea. To maintain an open and unrestricted internet, the FCC votes in support of strict net neutrality regulations.
Learn more about net neutrality from
https://brainly.com/question/13165766
#SPJ1
Which of the following is not one of the three defining characteristics of a portal? A) commerce B) content C) auctions D) navigation of the Web
Answers
The three fundamental features of a portal do not include auctions. The three defining virtues of portals are personalisation, consistency, and integration.
What is the portal's architecture?Architecture is the art and technique of designing and building, as opposed to the skills associated to construction. Drawing, imagining, planning, designing, and building are all procedures that go into the creation of buildings and other structures.
What role does the portal play?Clients can easily access pertinent information via portals, including FAQs, troubleshooting advice, company and product data, and much more. This data is accurate and current thanks to well-managed portals. Major general portals include AOL.com by America Online, Yahoo, Excite, Netscape, Lycos, CNET, and Microsoft Network.
To know more about portal visit:-
https://brainly.com/question/29315516
#SPJ4
If you want to open the Navigation pane to do a Find, what should you first click on the Home tab? Paragraph, Editing, Styles, or View
Answers
Answer:
You would first click view.
Explanation:
hope this helps
Answer:
editing (b)
Explanation:
Which view would you need to use to make changes to the design theme for the entire presentation?
Answers
Open your presentation.
On the Design tab, you'll find design themes in the Themes group.
To preview how the current slide would look with a particular theme applied, rest your pointer over the thumbnail image of that theme.
To view more themes, on the Design tab, in the Themes group, click More More button at the right end of the gallery.
To select and apply a theme, click the thumbnail image of that theme.
Unless you specify otherwise, PowerPoint applies the theme you select to the entire presentation.
To apply a theme to only one or a few slides, select the slide or slides, right-click the theme you want, and select Apply to Selected Slides.
Answer:
slide master
Explanation:
the answer on edge2020
Write a program to declare an integer array of size 10 and fill it with random numbers using the random number generator in the range 1 to 5. The program should then perform the following: . Print the values stored in the array Change each value in the array such that it equals to the value multiplied by its index. Print the modified array. You may use only pointerioffset notation when solving the programt Example run: The sales red the fa (& 7 4- 8 A hp 144 ( 9 Add text 1 Draw P
Answers
We declare an integer array 'arr' of size 10. We then use the 'srand' function to seed the random number generator with the current time to ensure different random numbers on each program run.
Here's a program in C that fulfills the requirements you mentioned:
#include <stdio.h>
#include <stdlib.h>
#include <time.h>
int main() {
int arr[10];
srand(time(NULL)); // Seed the random number generator
// Fill the array with random numbers between 1 and 5
for (int i = 0; i < 10; i++) {
arr[i] = rand() % 5 + 1;
}
// Print the original array
printf("Original Array: ");
for (int i = 0; i < 10; i++) {
printf("%d ", arr[i]);
}
printf("\n");
// Modify each value in the array by multiplying it with its index
for (int i = 0; i < 10; i++) {
arr[i] = arr[i] * i;
}
// Print the modified array
printf("Modified Array: ");
for (int i = 0; i < 10; i++) {
printf("%d ", arr[i]);
}
printf("\n");
return 0;
}
We fill the array with random numbers between 1 and 5 using the rand function. To limit the range, we use the modulo operator (%) to get the remainder when divided by 5 and add 1 to shift the range from 0-4 to 1-5.
We then print the original array using a for loop. After that, we modify each value in the array by multiplying it with its index. Finally, we print the modified array.
Each array element is accessed using pointer arithmetic notation, 'arr[i]', where 'i' represents the index of the element.
Upon running the program, you should see the original array printed first, followed by the modified array.
To know more about integer array
brainly.com/question/32893574
#SPJ11
we want you to write a function, organizeitems, that organizes items by category. the argument to the function is an array of item objects. each item object has 3 properties, category (string), itemname (string), and onsale (boolean). here's an example:
Answers
A function, organize items, that organizes items by category.
The Functionconst itemData =
[ { category: 'fruit', itemName: 'apple', onSale: false }
, { category: 'canned', itemName: 'beans', onSale: false }
, { category: 'canned', itemName: 'corn', onSale: true }
, { category: 'frozen', itemName: 'pizza', onSale: false }
, { category: 'fruit', itemName: 'melon', onSale: true }
, { category: 'canned', itemName: 'soup', onSale: false }
]
const result = itemData.reduce((r,{category,itemName,onSale})=>
{
r[category] = r[category] || []
r[category].push( itemName + (onSale?'($)':''))
return r
},{})
// show result
console.log( JSON.stringify(result)
.replace(`{"`,`\nresult =\n { `)
.replace(/"],"/g,`' ]\n , `)
.replace(`"]}`,`' ]\n }`)
.replace(/":\["/g,`: [ '`)
.replace(/","/g,`', '`))
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Hello guys where's bios chip in this motherboard help me

Answers
Answer:
Explanation:
Hey there!
Do you see the lower corner?
on the right beside the anti surge thingy
its rectangular, its also black from the center its here