75 + what equals 180
Answers
Answer:
105
Explanation:
Let the unknown number be " x ".
75 + x = 180
Subtract 75 on both sides,
x = 180 - 75
x = 105
Related Questions
what is a file named TR/Dldr.Adload.ugkeo doing on my computer
Answers
Answer:
That's brainly's way of making sure you're not a bot
Explanation:
I don't actually know
Answer:
did you download any file from this user or this similar link look at the picture below. If you please take it to someone who know how to get rid of viruses

Which of the following would be studied using an Earth-observing satellite?
tracking changes in land used for corn production
tracking heat and energy being released by the earth
O tracking atmospheric changes resulting from volcanic eruptions
tracking cloud cover and its relationship to global warming
Help plz will give BRAINLYIST
Answers
Answer:
climate is what you expect and weather is what you get. More formally, climate is the long-term average of temperature, precipitation, and other weather variables at a given location
Explanation:
Answer:
Geography
Explanation:
__________ refers to a variety of software applications that analyze an organization's raw data and obtain useful insights from it.
Answers
Business Intelligence or data analysis refers to a variety of software applications that analyze an organization's raw data and obtain useful insights from it.
Business intelligence (BI) is a data analysis is used by organizations to analyze data and hence gain insights on overall business performance so as to help the organization make good business decisions.
It helps organizations to increase revenue and efficiency thereby being more competitive than other business organizations.
Find out more at: https://brainly.com/question/15406226
A linear representation of a hierarchical file directory is known as what?
Answers
Answer:
C.) a directory path
Explanation:
because I got it right.
NEEDS TO BE IN PYTHON:
(Column sorting)
Implement the following function to sort the columns in a two-dimensional list. A new list is returned and the original list is intact.
def sortColumns(m):
Write a test program that prompts the user to enter a 3 by 3 matrix of numbers and displays a new column-sorted matrix. Note that the matrix is entered by rows and the numbers in each row are separated by a space in one line.
Sample Run
Enter a 3-by-3 matrix row by row:
0.15 0.875 0.375
0.55 0.005 0.225
0.30 0.12 0.4
The column-sorted list is
0.15 0.005 0.225
0.3 0.12 0.375
0.55 0.875 0.4
Answers
The sample program prompts the user to enter a 3-by-3 matrix of numbers, stores it as a list of lists, calls the sort to python column sorting function obtain the sorted matrix, and prints it to the console in the requested format.
Here's a Python implementation of the requested function sort Columns and a sample program to test it:
python
Copy code
def sort Columns(m):
# transpose the matrix
transposed = [[m[j][i] for j in range(len(m))] for i in range(len(m[0]))]
# sort each column
sorted_cols = [sorted(col) for col in transposed]
# transpose back the sorted matrix
sorted_m = [[sorted_cols[j][i] for j in range(len(sorted_cols))] for i in range(len(sorted_cols[0]))]
return sorted_m
# sample program
matrix = []
print("Enter a 3-by-3 matrix row by row:")
for i in range(3):
row = [float(x) for x in input().split()]
matrix.append(row)
sorted_matrix = sortColumns(matrix)
print("The column-sorted list is")
for row in sorted_matrix:
print(" ".join(str(x) for x in row))
Explanation:
The sort Columns function takes a matrix m as input and returns a new matrix that has the columns sorted in ascending order. To achieve this, we first transpose the matrix using a nested list comprehension. Then, we sort each column using the sorted function, and finally, we transpose the sorted matrix back to the original shape using another nested list comprehension. The function does not modify the original matrix.
The sample program prompts the user to enter a 3-by-3 matrix of numbers, stores it as a list of lists, calls the sort python column sorting function to obtain the sorted matrix, and prints it to the console in the requested format.
For such more questions on python column sorting function.
https://brainly.com/question/31964486
#SPJ11
Here's the implementation of the sortColumns() function in Python:
def sortColumns(m):
sorted_cols = []
num_cols = len(m[0])
for col in range(num_cols):
sorted_cols.append([row[col] for row in m])
sorted_cols[col].sort()
return [[sorted_cols[j][i] for j in range(num_cols)] for i in range(len(m))]
And here's a sample program that uses the sortColumns() function to sort a 3x3 matrix entered by the user:
python
Copy code
# Prompt the user to enter a 3x3 matrix
print("Enter a 3-by-3 matrix row by row:")
m = [[float(num) for num in input().split()] for i in range(3)]
# Sort the columns of the matrix
sorted_m = sortColumns(m)
# Display the sorted matrix
print("The column-sorted list is")
for row in sorted_m:
print(' '.join(str(num) for num in row))
Sample Output:
Enter a 3-by-3 matrix row by row:
0.15 0.875 0.375
0.55 0.005 0.225
0.30 0.12 0.4
The column-sorted list is
0.15 0.005 0.225
0.3 0.12 0.375
0.55 0.875 0.4
Learn more about function here:
https://brainly.com/question/12431044
#SPJ11
how can robots help us with online learning? 3 reasons please thank u :)
Answers
Answer:
The use of robots increases the practicality of online education, such that the difference between in person attendance and online learning is minimized
In elementary school, robots can help deliver teaching materials in a class like setting, to students who are unable to attend classes due to their current situation
In high school, simulators can give driving (and flying) lessons to would be drivers, without the exposure of the students to risk
Robots in higher education, such as medicine, can be used to carry out operational procedures with students where, there are no subjects to perform the surgical procedure on
The use of simulators makes possible training in disaster and crisis management
Explanation:
For extra depth of perspective, you should consider using a gradient. (pg. 219)
O True
O False
Answers
Answer:
true
Explanation:
Please Help!
Assume that you have an array named items containing 100 integers, and an integer named numItems that represents the number of valid integers currently used in the array. All elements from items[numItems] to items[items.length-1] have values of 0.
The following code is designed to calculate and print the average of the valid array elements:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
statement 1
}
statement 2
Which of the following substitutions for and will cause this code to correctly print the average of the valid array elements in items?
A. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / count);
B. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / items.length);
C. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / numItems);
D. Statement 1:
sum += items[items.length-1];
Statement 2:
System.out.println(sum / 100);
E. Statement 1:
sum += items[items.length-1];
Statement 2:
System.out.println((double)sum / numItems);
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
This question is about calculating the sum and average of the elements in the given array.
The code is given below:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
statement 1
}
statement 2
Then this question is asked that which of the following substitutions for and will cause this code to correctly print the average of the valid array elements in items?
So, The correct answer is A. Because the first statement counts the sum of all the given elements in the array. And, the second statement print the average (sum/count) and store result in double.
A. Statement 1:
sum += items[count];
Statement 2:
System.out.println((double)sum / count);
So that the correct and complete program is given below:
int sum=0, count;
for (count = 0; count < items. length; count++)
{
sum += items[count];
}
System.out.println((double)sum / count);
Consider the scenario shown below, with four different servers connected to four different clients over four three-hop paths. The four pairs share a common middle hop with a transmission capacity of R = 300 Mbps. The four links from the servers to the shared link have a transmission capacity of RS = 100 Mbps. Each of the four links from the shared middle link to a client has a transmission capacity of RC = 10 Mbps.
What is the maximum achievable end-end throughput (in Mbps) for each of four client-to-server pairs, assuming that the middle link is fairly shared (divides its transmission rate equally)?
Answers
The maximum achievable end-to-end throughput for each of the four client-to-server pairs would be 75 Mbps.
How to find this?Let's assume that each of the four client-to-server pairs is sending data at the maximum rate possible. The four links from the servers to the shared middle hop would have a combined transmission rate of 4 * RS = 4 * 100 Mbps = 400 Mbps.
Since the shared middle hop has a transmission capacity of R = 300 Mbps, it can only transmit at a rate of 300 Mbps.
Since the shared middle hop is dividing its transmission rate equally among the four client-to-server pairs, each client-to-server pair would receive 300 / 4 = 75 Mbps of the transmission rate.
Finally, since each of the four links from the shared middle hop to a client has a transmission capacity of RC = 10 Mbps, each client-to-server pair would only be able to receive data at a rate of 10 Mbps, which is the bottleneck in this scenario.
Therefore, the maximum achievable end-to-end throughput for each of the four client-to-server pairs would be smaller of 75 Mbps and 10 Mbps, which is 10 Mbps.
Read more about network throughput here:
https://brainly.com/question/28426125
#SPJ1
Omar needs to build a website fast for a client. The website needs to be highly scalable as it is predicted to become quite popular. Due to time constraints, Omar can’t build all the code himself. Which of the following would be best for Omar to use?
A.
AngularJS
B.
Django
C.
SQL
D.
jQuery
Answers
B no reason why but I have done this just forgot explaining ")
Im boing exam help please In a category-based course grading system, teachers weigh a student's performance in all courses. all categories equally. some categories more heavily than others. extra credit as a bonus.
Answers
Answer:
some categories more heavily than others.
Explanation:
A category-based course grading system is a form of a grading system that involves an examiner to set up different categories of the overall assessment and at the same time placed different weight or marks over each category.
Therefore, the examiners weigh a student's performance in " some categories more heavily than others." For example, an examiner placed different weight over different categories in the overall assessment
1. Homework category: 30%
2. Classwork category: 20%
3. Quiz category: 20%
4. Final exam category: 30%
Answer:
B
Explanation:
advanced computer solutions, incorporated has two main services: (1) time on a timeshared computer system and (2) proprietary computer programs. the operation department (op) provides computer time and the programming department (p) writes programs. the percentage of each service used by each department for a typical period is: supplied user op p op --- 35% p 25% --- sold to customers 75% 65% in a typical period, the operation department (op) spends $6,400 and the programming department (p) spends $4,400. under the step method (op first), what is the cost of the computer time and the computer programs for sale? time programs a. $ 6,400 $ 4,400 b. $ 4,800 $ 6,000 c. $ 1,600 $ 9,200 d. $ 4,160 $ 6,640
Answers
Answer:
Explanation:
Using the step method, we can determine the cost of computer time and computer programs for sale as follows:
Calculate the total cost of each department's operations:
Operation department (OP): $6,400
Programming department (P): $4,400
Allocate the costs of each department's operations based on the percentage of services used:
OP supplies 35% of time and 75% of programs, so allocate 35% of OP's cost to time and 75% of OP's cost to programs:
Time: $6,400 x 35% = $2,240
Programs: $6,400 x 75% = $4,800
P supplies 25% of time and 65% of programs, so allocate 25% of P's cost to time and 65% of P's cost to programs:
Time: $4,400 x 25% = $1,100
Programs: $4,400 x 65% = $2,860
Add up the allocated costs for each service:
Time: $2,240 + $1,100 = $3,340
Programs: $4,800 + $2,860 = $7,660
Therefore, the cost of computer time and computer programs for sale is $3,340 and $7,660, respectively.
Answer: (a) $6,400 for time and $4,400 for programs are the total costs of each department's operations, not the allocated costs of each service.
what is the limitation of computer
Answers
The limitation of computer are:
No self-intelligenceNo feelingNo learning powerDependencyA professional-looking portfolio gives a clear message. What does it convey?
Ο Α. .
that you like to build up a sales pitch
OB. that you like to flaunt your work
OC. that you are serious about your work
OD.
that you put on a show for effect
Ο Ε.
that you only care about appearances
Reset
Next
Answers
Answer:a
Explanation:
A professional-looking portfolio gives a clear message that you put on a show for effect. Thus, the correct option is D). that you put on a show for effect.
What is a professional portfolio?Professional portfolio refers to the collection of work and other documents that make clear the abilities of the candidate to the potential employers. It can be created in both digital and physical format.
A portfolio is an collected album of all work samples and professional documentation that provides proof about the accomplishments, skills, potential and samples of an individual's work.
In order to give portfolio a professional look, there are several categories to be consider such as Personal Information, Values, Personal Goals and History, Accomplishments and Job History, Skills and Attributes, Education and Training as well.
Learn more about professional portfolio here:-
https://brainly.com/question/20411709
#SPJ2
One of the goals of information security entails that every action taken by a subject on any information asset (object) under any conditions (time of day, location, IP Address etc.), including the outcome(s) of those actions; must be able to be uniquely traced back to the subject (i.e. the identity) that took those actions. This goal is specifically referred to as:
Answers
The goal of information security that ensures every action taken by a subject on an information asset can be traced back to the subject's identity is known as "accountability."
Accountability is a crucial aspect of information security that focuses on establishing a clear link between the actions performed by a subject and their identity. It aims to ensure that any activity carried out on an information asset, regardless of the circumstances, can be uniquely traced back to the responsible individual or entity.
By enforcing accountability measures, organizations can monitor and track the actions of users, identifying any potential security breaches, unauthorized access, or malicious activities. This helps in investigating incidents, auditing system usage, and holding individuals accountable for their actions.
To achieve accountability, various security mechanisms are employed, such as user authentication, access controls, logging systems, and audit trails. These mechanisms enable the recording and tracking of user activities, ensuring that actions can be attributed to specific individuals or entities. Overall, accountability plays a crucial role in maintaining the integrity and security of information assets within an organization.
Learn more about information security here:
https://brainly.com/question/31561235
#SPJ11
For this assignment, you will select a digital media career that you would be interested in pursuing. You will need to do some research to identify the right career for you. Next, you will research and discover what kind of training you will need to land your dream job. Finally, you will find available jobs in your career and select a job that you would want. After doing some research and some thinking, you will:
Select a career that is right for you. Write at least 150 words describing the career and why you believe it would be a good fit for you. Keep in mind your interests and talents.
Research and learn about what training the career requires. After you research, write at least 150 words describing the training. You can include what types of course you would take. How long the training program is, and how much it might cost you.
Finally, you will find a job! Research available jobs in your career and select a job you would want. Provide a copy of the job posting. You can snapshot this, copy and paste it, or copy it word for word. Make sure you include where you found the job posted. You will include at least 75 words on why you selected this particular position. Some helpful sites for job hunting are Indeed, Dice, Career Builder, and Monster.
Answers
A digital media career involves using technology to create and distribute various forms of digital content, such as video, audio, graphics, and multimedia. This can include roles such as graphic designers, web developers, social media specialists, digital marketers, and video producers.
How long the training program is, and how much it might cost you.To land a career in digital media, you will typically need a combination of technical skills and creativity, as well as a strong understanding of digital media platforms and technologies. Depending on the specific career path you choose, you may need to have skills in areas such as graphic design, web development, video editing, or social media management.
Training for a digital media career can vary depending on the specific path you choose, but often involves completing a degree or certificate program in a related field such as digital media, graphic design, or marketing. These programs can range in length from a few months to several years, and can cost anywhere from a few thousand dollars to tens of thousands of dollars.
Job opportunities in digital media can be found on job search sites such as Indeed, Dice, Career Builder, and Monster. One example of a job posting for a digital media position is:
Position: Social Media Specialist
Company: XYZ Digital Agency
Location: New York, NY
Job Type: Full-time
Responsibilities:Develop and execute social media strategies for client accounts
Create engaging social media content, including graphics and video
Monitor social media channels for trends and insights
Analyze social media metrics and adjust strategies as needed
Why I selected this particular position:
I am interested in pursuing a career in social media management, and this position seems like a good fit for my skills and interests. I am drawn to the opportunity to create engaging content and develop strategies to help clients achieve their social media goals. Additionally, the location and job type align with my preferences.
Read more on digital media career here https://brainly.com/question/29363025
#SPJ1
ansys.core.datamodel.dataentitynotfoundexception: data entity not found: /schematic/component:results
Answers
The error message you received, "ansys.core.datamodel.dataentitynotfoundexception: data entity not found: /schematic/component:results", indicates that the ANSYS software is unable to find a specific data entity related to the schematic component results.
To resolve this issue, you can try the following steps:
1. Double-check the path and name of the data entity mentioned in the error message. Ensure that it is correctly spelled and matches the existing data entity.
2. Verify that the data entity is properly defined and accessible within the ANSYS software. If not, you may need to create or import the data entity.
3. Check if there are any missing dependencies or references that might be causing the error. Make sure all necessary files and components are present and properly linked.
4. Update the ANSYS software to the latest version, as newer versions often include bug fixes and improvements that could resolve this type of issue.
5. Consult the ANSYS documentation or contact ANSYS support for further assistance. They may be able to provide specific guidance or troubleshoot the issue with you.
To know more about ANSYS visit:
brainly.com/question/33945698
#SPJ11
Use the th element to indicate a table column or row _____.
Question options:
O data
O heading
O summary
O caption
Answers
To indicate a table column or row heading in HTML, you should use the "th" element.
Start by creating an HTML table using the "table" element.For each row of the table, use the "tr" element to create a new row.For each cell in the row, use the "td" element to create a new cell.If the cell is a heading for either a column or a row, use the "th" element instead of "td".Use the "scope" attribute to indicate whether the heading applies to a row or column. For example, "scope='row'" would indicate that the heading applies to a row, while "scope='col'" would indicate that the heading applies to a column.You can also use the "abbr" attribute to provide an abbreviation or shortened version of the heading text, which can be helpful for accessibility and screen readers.Here is an example of a simple HTML table with column and row headings://php
<table>
<tr>
<th></th>
<th scope="col">January</th>
<th scope="col">February</th>
<th scope="col">March</th>
</tr>
<tr>
<th scope="row">Sales</th>
<td>$100</td>
<td>$150</td>
<td>$200</td>
</tr>
<tr>
<th scope="row">Expenses</th>
<td>$50</td>
<td>$75</td>
<td>$100</td>
</tr>
</table>
In this example, the first row contains column headings, which are indicated using the "th" element with a "scope" of "col". The first column contains row headings, which are also indicated using the "th" element with a "scope" of "row". The remaining cells contain data for each intersection of row and column.
Learn more about the table column or row heading in HTML:
https://brainly.com/question/17516706
#SPJ11
Explain two ways by which the calendar meets or fails to meet the criteria of showing the correct data

Answers
Answer:
The two ways the calendar meets the criteria of showing the correct date are;
1) The calendar can give dates in the 12 months in a year
2) The calendar can show up to the 31 different days in a month
Explanation:
The two ways in which the calendar meets the criteria of showing the correct date are;
1) The number number of long blocks with 4 different months each = Three
Therefore, the total number of months the blocks can hold = 3 × 4 months = 12 months = The number of months in a year
2) The number of faces on each dice = 6 faces
The number of dice = 2 dice
The total number of faces = 12
The number of identical faces = 2 (11th and 22nd of the month)
The number of unique faces = 10
The number of combinations of the dices = ₁₀C₂ = 45
The number of combination of faces required to show = 1 to 31 = 31 combination
Therefore, there are adequate combinations on the dice to show all the dates of month
are special characters usually found on the keyboard?
Answers
Answer:
No
Explanation:
When typing in predefined characters, Automatic substitution feature will change the characters into a symbol or special character. No.
creating the lexical and syntax analyzer for a programming language that will be defined in this problem. this language will be able to create variables, assign them value, calculate basic mathematic operations and relational operations for integers of different types, as well as variables that can be either.
Answers
A lexical analyzer, also known as a Lexer or tokenizer, is a program or function that reads a stream of text and breaks it up into individual tokens, or basic elements, such as keywords, operators, and punctuation marks.
How to create the analyzers?To create a lexical and syntax analyzer for a programming language, you would need to first define the rules and syntax of the language, including the keywords, operators, and other elements that make up the language. This would involve deciding on the types of variables and data structures that the language would support, as well as the rules for defining and using variables and other language constructs.
Once the rules and syntax of the language have been defined, you would then need to create a lexical analyzer to identify the individual tokens, or basic elements, of the language.
This would involve writing code to scan the source code of a program written in the language and identify the keywords, operators, and other elements that make up the program.
After the lexical analyzer has identified the individual tokens of the language, you would then need to create a syntax analyzer to check the structure and syntax of the program to ensure that it is valid according to the rules of the language.
This would involve writing code to verify that the program follows the correct syntax and structure, and to identify any errors or inconsistencies in the program.
To Know More About lexical analyzer, Check Out
https://brainly.com/question/13211785
#SPJ1
Some outputs were not as expected. thomas is now going through the code carefully attempting to establish the cause of these errors and change the code to remove them. what is this procedure called?
Answers
As some of the outputs were not as expected, the procedure of Thomas going through the code carefully and attempting to establish the cause of these errors and changing the code to remove them is called debugging.
Debugging a code is the process of eliminating errors or malfunctions in a system. Find and eliminate existing and possible software code errors (also known as "bugs") that can cause unexpected behavior or crashes.
Debugging is used to find and fix errors and defects to prevent incorrect operation of a software or system. Debugging a code takes more time than actual coding.
Learn about how to find bugs to debug in a coding project:
https://brainly.com/question/15079851
#SPJ4
For which task would you most likely use word-processing software? question 5 options: formatting text with various fonts, sizes and styles placing text in rows and columns for sorting and filtering creating slides and displaying them in a continuous loop placing numeric data in rows and columns for statistical analysis.
Answers
Answer:
Option 1, Option 2, Option 4
Explanation:
Word processors like Word and Docs can be used to format text and create visually appealing works for presentation, and, while it is used for presentation, it is not used for slideshows, meaning all of the options except making slides are correct.
The tasks for which word-processing software is required are formatting text with various fonts, sizes and styles, placing text in rows and columns for sorting and filtering, and placing numeric data in rows and columns for statistical analysis. The correct options are A, B, and D.
What is word processing software?A word processor is a hardware or computer program that allows for the input, editing, formatting, and output of text, along with other functions.
The act of creating, editing, saving, and printing documents on a computer is referred to as word processing. Word processing requires the use of specialized software known as a Word Processor.
Word processing software is used to edit text documents such as resumes and reports. You basically enter text by typing, and the software provides tools for copying, deleting and various types of formatting.
Today, the word processor is one of the most frequently used software programs on a computer, with Microsoft Word being the most popular word processor.
Thus, the correct options are a, b, and d.
For more details regarding word processing software, visit:
https://brainly.com/question/20910519
#SPJ2
using digital signatures is primarily a technique to ____.
Answers
Using digital signatures is primarily a technique to ensure the integrity, authenticity, and non-repudiation of digital information.
How does this secure digital information?It enables secure and verifiable electronic transactions and communications in the digital world. Digital signatures use cryptographic algorithms to create a unique digital representation of a document or message, which can be attached or embedded within the digital file.
This signature verifies that the document has not been tampered with since the signature was applied and can be attributed to a specific signer.
By employing digital signatures, individuals and organizations can establish trust, protect against fraud, and verify the validity of digital content and transactions.
Read more about digital signatures here:
https://brainly.com/question/30616795
#SPJ4
What is meaning of geo and bio
Answers
Answer:
Geo means Earth and Bio mean life
How can Swift Acclivity
LLC conduct campaign planning for digital media with the following
characteristics of digital media?
2. Campaign insight
Answers
Data entry and formatting controls play a crucial role in minimizing the likelihood of input errors. These controls include validation checks, data formatting restrictions, input masks, default values, and data verification.
Data entry and formatting controls help minimize input errors by imposing restrictions and validations on the data being entered. Validation checks verify the data against predefined rules and criteria, ensuring that only valid and allowable data is entered. This can include checks for data type, range, length, and format. For example, a numeric field may be validated to accept only positive integers within a specific range. Data formatting controls impose specific formats on data entry, such as date formats, phone number formats, or social security number formats. Input masks guide users to enter data in the desired format, preventing inconsistencies and errors.
For instance, an input mask for a phone number field may automatically format the entered digits into a standard phone number format. Default values can be set for fields that have predictable or common values, reducing the need for manual input and minimizing the chances of errors. Data verification processes, such as double-entry verification or cross-referencing with existing data, can be implemented to ensure accuracy and completeness. By combining these controls, organizations can create a data entry environment that promotes accurate and error-free input. These controls act as safeguards against common input mistakes, enhance data quality, and contribute to the overall integrity and reliability of the data being entered.
Learn more about positive integers here:
https://brainly.com/question/18380011
#SPJ11
YOOO CAN ANYONE SOLVE THIS IN JAVA??
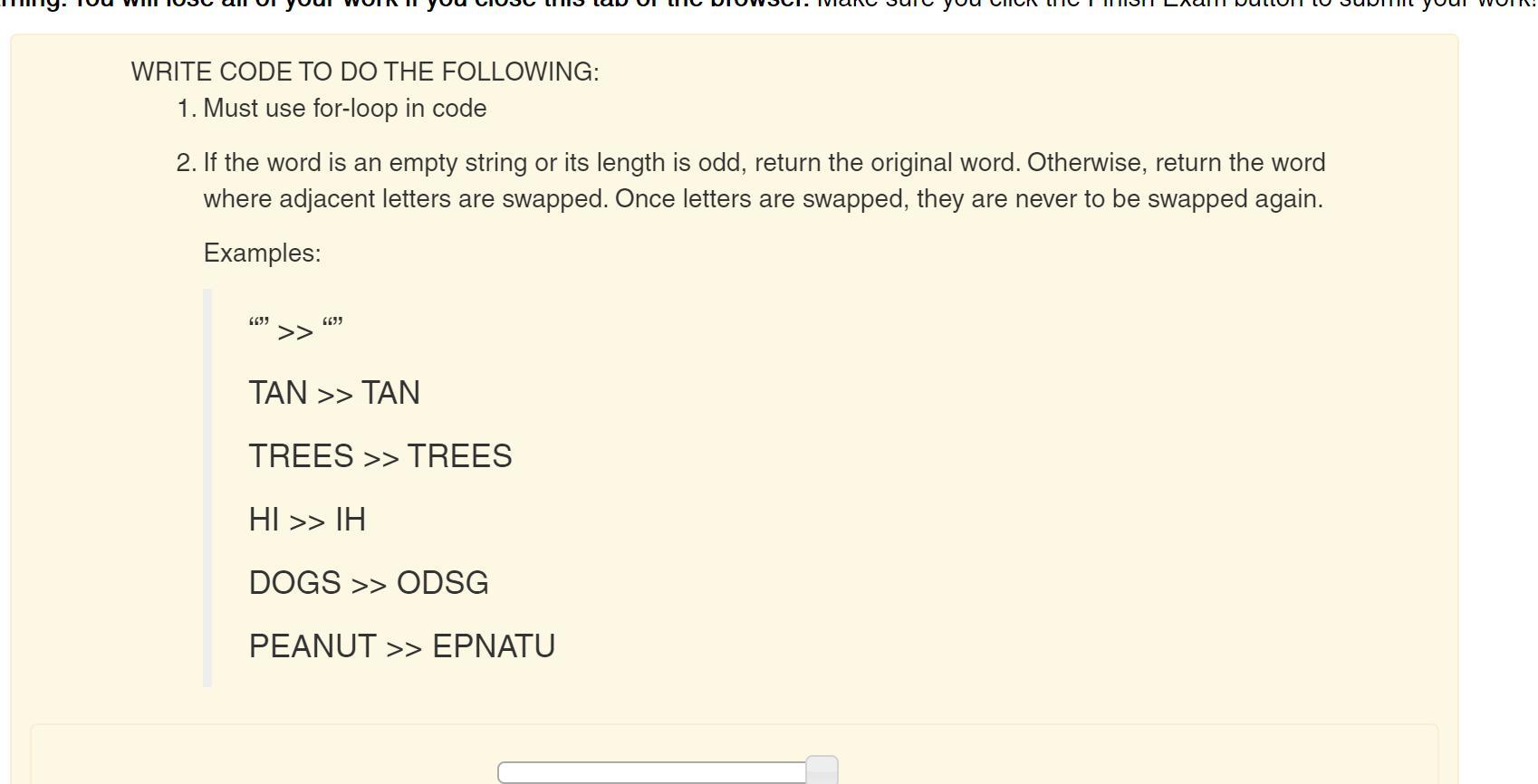
Answers
public class JavaApplication80 {
public static String swapLetters(String word){
char prevC = '_';
String newWord = "";
int count = 0;
if (word.length() % 2 == 1 || word.isBlank()){
return word;
}
else{
for (int i = 0; i<word.length(); i++){
char c = word.charAt(i);
if(count % 2 == 1){
newWord += (c +""+ prevC);
}
prevC = c;
count+=1;
}
}
return newWord;
}
public static void main(String[] args) {
System.out.println(swapLetters("peanut"));
}
}
This works for me. Best of luck.
Answer:
I do not know
Explanation:
How can i print an art triangle made up of asterisks using only one line of code. Using string concatenation (multiplication and addition and maybe parenthesis)?
Answers
#include <iostream>
int main(int argc, char* argv[]) {
//One line
std::cout << "\t\t*\t\t\n\t\t\b* *\t\t\b\n\t\t\b\b* *\t\t\b\b\n\t\t\b\b\b* *\t\t\b\b\b\n\t\t\b\b\b\b* *\t\t\b\b\b\b\n\t\t\b\b\b\b\b* * * * * *\t\t\b\b\b\b\b\n";
return 0;
}
Yes, it is possible with a single line and using escape sequences, but it is tedious and not recommended. Instead, you can use loops to write more readable and easy on the eyes code. We only used the cout method (C++). Good luck!

Chris needs to modify the default bullets that are used in a nonnumbered list in Word.
Which method should he use?
Select the arrow next to the bullet list option in the Paragraph group.
Select the arrow next to the number list option in the Paragraph group.
Use the Styles group on the Home tab.
This cannot be done.
Answers
Answer:
he should select the arrow next to the bullet list
Explanation:
Answer: Select the arrow next to the bullet list option in the paragraph group.
Explanation:
Edge 2020
____ media include television and radio
Answers
Answer:
Broadcast media include television and radio.
Explanation:
Broadcast media includes information transmitted through one of several mass communication channels, such as television and radio.