A _________ , also known as a trapdoor, is a secret entry point into a program that allows someone who is aware of the door to gain access without going through the usual security access procedures.
Answers
The trapdoor is a method that breaches the security of the system and bypasses the authentication. The trapdoor is also called the backdoor.
What is a backdoor?A backdoor or the trapdoor is the method of a security breach that bypasses the authentication check of the system to access the cryptographic systems through unauthorized means.
It is a secret entry point known by someone to gain entry by bypassing the security check for harming the system and is also used to test and debug programs.
Therefore, the correct blank is the backdoor.
Learn more about backdoor here:
https://brainly.com/question/14315309
#SPJ1
Related Questions
when enabling dynamic memory for virtual machines, what does the memory weight setting specify?
Answers
The memory weight setting, when enabling dynamic memory for virtual machines, specifies the priority or preference given to a virtual machine when allocating memory resources.
When dynamic memory is enabled for virtual machines, the memory weight setting determines the relative priority of a virtual machine when allocating available memory resources. Each virtual machine is assigned a memory weight value, and the higher the weight, the more likely the virtual machine will receive additional memory when resources are constrained.
The memory weight is used by the hypervisor to prioritize memory allocation among virtual machines based on their assigned weights. This allows for efficient memory management and ensures that virtual machines with higher memory weight settings receive a larger share of available memory when needed.
Learn more about memory here:
https://brainly.com/question/30273393
#SPJ11
There is a new product launched and its customer ratings are being recorded in an array. the ratings are being monitored and analyzed if there is any decrease in the ratings. find the number of periods in which the rating is consecutively decreasing.
example - ratings = [4,3,5,4,3]
periods (in other words sub arrays in which ratings are decreasing):
one day periods = [4],[3],[5],[4],[3] (count of subarrays is 5)
two day periods = [4,3],[5,4],[4,3] (count of subarrays is 3)
3 day periods = [5,4,3] (count of subarrays is 1)
so, the output for this example will be 9 (5 + 3 + 1)
Answers
The program to find the number of periods in which the rating is consecutively decreasing is; As written in the attached file
What is the program array?What we are required to do to find the number of elements in decreasing part. For example;
4,3 means One decreasing part and has 2 elements
5, 4, 3 means second decresing part and has 3 element.
Thereafter, we just add n*(n + 1)/2 to result.
where;
n = number of elements in any part
n*(n + 1) /2 is number of decreasing subarray that can be made
For the second decreasing part which is [5, 4, 3];
number of sub arrays you can make = 3 * 4/2 = 6
Thus, we have;
[5], [4,], [3], [5,4],[4,3],[5,4,3]
The program to find the number of periods in which the rating is consecutively decreasing is as follows in the attached file;
Read more about program array at; https://brainly.com/question/16266708

answer john recently upgraded from windows 8.1 to windows 10, after the upgrade is complete, on the right-hand side of his desktop there is a new area that contains a way to toggle several windows features on and off, access the settings app, and view notifications. what is this area called in windows 10?
Answers
Answer:
nswer john recently upgraded from windows 8.1 to windows 10, after the upgrade is complete, on the right-hand side of his desktop there is a new area that contains a way to toggle several windows features on and off, access the settings app, and view notifications. what is this area called in windows 10?
The area in windows 10 is called the Action center
new action center which is in windows 10 you'll find app notifications and quick actions. Program alerts as well as quick actions can be contained within Window 10's new action center. Browse for the action center icon just on the taskbar.
The original action center has already been rebranded Security and Maintenance, however, it is still intact. Users still visit the site to modify their security settings. It is also s a central place wherein users can access alerts and perform actions that can ensure Windows works efficiently. This is when critical safety, as well as servicing notifications, will appear if Windows uncovers certain software or equipment problems that require user response.
learn more about Action center here: https://brainly.com/question/17827631
#SPJ4
From Edmentum/Plato
You may be familiar with rubrics used for grading at your school. Take the idea of a rubric and create your own grading or evaluation form based on what you think is important for employers to evaluate about their employees. You may use online resources to gain a better understanding of work-based evaluation forms and rubrics to support your answer
Answers
Answer:
Given below is an example of an evaluation form for a workplace. It consists of various parameters that an employer would ideally consider when evaluating an employee’s work performance during a specific period, such as six months or a year. While evaluating an employee, an employer could circle or make a check mark on the following scales:
5 (excellent)
4 (good)
3 (average)
2 (below average)
1 (poor)
Parameters Excellent Good Average Below Average Poor
Appearance/Grooming 5 4 3 2 1
Attendance 5 4 3 2 1
Communication Skills 5 4 3 2 1
Coordination 5 4 3 2 1
Initiative 5 4 3 2 1
Working in a group 5 4 3 2 1
Creativity 5 4 3 2 1
Problem-solving Ability 5 4 3 2 1
Punctuality 5 4 3 2 1
Overall Work Attitude 5 4 3 2 1
Explanation: edmentum answer
You are designing a simple calculator program for young children to use. Right now, if they do something that the program didn’t expect, a message appears that reads, “User input deemed invalid.” What changes could you make so that the message would be more suitable for this audience?
Answers
The change you could make to make the message more suitable for this audience would be to identify a suitable message so that the children understand that they made a mistake using the program. For example: You made a mistake, try again.
What is a user input?A user input is a term that refers to the action performed by a user of a digital system or a specific program. This message has been standardized to indicate to the user that he has made a mistake in pressing buttons or in handling a program.
How to modify the message?To modify the message we must edit the base font of the program so that the message that we want to appear on the screen is different. On the other hand, we must identify a message that is simple and direct so that the children understand that they made a mistake when using the program.
What message can we put for the children?The right message for children should clearly communicate to them what has happened without discouraging them. So a suitable example of a message would be:
You've made a mistake, try again.Learn more about user input in: https://brainly.com/question/8789964
#SPJ1
What is wrong with the following code? correct the bugs to produce the following expected output: first = [3, 7] second = [3, 7] they contain the same elements.
Answers
public class ArrayError {
public static void main(String[] args) {
int[] first = new int[2];
first[0] = 3;
first[1] = 7;
int[] second = new int[2];
What is the bug in computer?
In computer technology, a bug is a coding error in a computer program. We consider a program to also include the microcode that is manufactured into a microprocessor.) The process of finding bugs -- before users do -- is called debugging.first = [ 3,7 ]
second = [ 3 , 7]
They contains the same elements.
Process finished with exit code 0.
Learn more about bug
brainly.com/question/24124347
#SPJ4
The complete question is -
What is wrong with the following code? Correct the bugs to produce the following expected output: first = [3, 7] second = [3, 7] They contain the same elements. lype your solution here: 1 int[] first new int [2]; 2 first [0] 3; 3 first [1] 7; 4 int [ ] second = new int [2]; 5 second [0] = 3; 6 second [1] = 7; 8// print the array elements 9 System.out.println("first" first); 10 System.out.println("second"second); 12 // see if the elements are the same 13 if (first - second) I 14 System.out.println("They contain the same elements."); 15 else 16 System.out.println("The elements are different."); 17 h
Which MLA web source citations are formatted correctly? Check all that apply.
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.
Herman, Barbara. “Where’s the Fire?” Newsweek. Newsweek, 24 Oct. 2013. Web. 25 Feb. 2014.
Niesen, Joan. “Learning to Cope: Disabled Vet Hunt Finds Freedom as Paralympic Skier.” Sports Illustrated. Web. 27 Feb. 2014.
A Mighty Girl. N.p., n.d. Web. 26 Feb. 2014.
Kloc, Joe. “Kepler Mission Finds Hundreds More Planets.” 2 Feb. 2014. Web. 25 Feb. 2014.
Answers
Answer:
Explanation:
A,B on exp.

The correct MLA web source citations are:
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.Others are:
Herman, Barbara. “Where’s the Fire?” Newsweek. Newsweek, 24 Oct. 2013. Web. 25 Feb. 2014. What is MLA citation?MLA in-text citation style is known to be a citation method that is often used in citing authors. Her one often uses the author's last name and the page number from where the work is taken from.
A good example of this MLA web source citations is:
Wolfson, Elijah. “Newsweek Names a Mars Crater.” Newsweek. Newsweek, 28 Feb. 2014. Web. 1 Mar. 2014.Learn more about MLA web source from
https://brainly.com/question/26110488
#SPJ2
Which securities protects networks from intruders? *
Application security
Network security
Information security
Operational security
Answers
Answer:
I think it is network security
Explanation:
Heard in an ad before :T
Answer:
Use Kika Clipboard to make paste easypneumonoultramicroscopicsilicovolcanoconiosis
Create a C++ program using arithmetic operators to compute the AVERAGE of THREE (3) QUIZZES and display the score and average on different lines.
The output should be similar to this:

Answers
using the knowledge in computational language in python it is possible to write a code that using arithmetic operators to compute the average of three quizzes and display the score and average on different lines.
Writting the code:#include <iostream>
using namespace std;
int main()
{
float n1,n2,n3,n4,tot,avrg;
cout << "\n\n Compute the total and average of four numbers :\n";
cout << "----------------------------------------------------\n";
cout<<" Input 1st two numbers (separated by space) : ";
cin>> n1 >> n2;
cout<<" Input last two numbers (separated by space) : ";
cin>> n3 >> n4;
tot=n1+n2+n3+n4;
avrg=tot/4;
cout<<" The total of four numbers is : "<< tot << endl;
cout<<" The average of four numbers is : "<< avrg << endl;
cout << endl;
return 0;
}
See more about C++ at brainly.com/question/19705654
#SPJ1

How does segmenting your network increase network security?
Answers
Answer:
By segmenting networks, it becomes easier to protect the most sensitive data that you have on your internally-facing network assets. The creation of a layer of separation between servers containing sensitive data and everything outside of your network can do wonders to reduce your risk of data loss or theft.
Explanation:
PLEASE MARK ME AS BRAINLIEST
Why do companies collect information about consumers? A. Because they want to meet new friends on social networks B. Because they take consumers' best interests to heart C. Because they want to effectively advertise to consumers D. Because they are looking for good employees to hire
Answers
Answer:
C. Because they want to effectively advertise to consumers.
Explanation:
Companies collect info for more accurate advertisements, which are designed to make people interact with them more commonly.
A computer game allows a player to repeat a level until they run out of lives. Which two of the following loops would work correctly?

Answers
Answer:
c.
Explanation:
because this is the right syntax for the following loops
use huffman coding to encode these symbols with given frequencies: a: 0.10, b: 0.25, c: 0.05, d: 0.15, e: 0.30, f: 0.07, g: 0.08. what is the average number of bits required to encode a symbol?
Answers
The average number of bits required to encode a symbol using Huffman coding is 2.32 bits.
How to determine the average number of bits required to encode a symbol using Huffman coding?To determine the average number of bits required to encode a symbol using Huffman coding, follow these steps:
1. Arrange the symbols in ascending order based on their frequencies:
c: 0.05, f: 0.07, g: 0.08, a: 0.10, d: 0.15, b: 0.25, e: 0.30.
2. Create a binary tree by repeatedly combining the two symbols with the lowest frequencies until all symbols are merged into a single tree.
0.60
/ \
0.25 0.35
/ \ / \
b:0.25 a:0.10 d:0.15, e:0.30
\
c:0.05,f:0.07,g:0.08
3. Assign a "0" to the left branch and a "1" to the right branch for each split.
4. Encode each symbol by traversing the tree from the root to the symbol, recording the corresponding path of 0s and 1s.
a: 01
b: 00
c: 100
d: 110
e: 111
f: 1010
g: 1011
5. Calculate the average number of bits required:
(0.10 * 2) + (0.25 * 2) + (0.05 * 3) + (0.15 * 3) + (0.30 * 3) + (0.07 * 4) + (0.08 * 4) = 2.32 bits
Therefore, the average number of bits required to encode a symbol using Huffman coding is 2.32 bits.
Learn more about Huffman coding
brainly.com/question/31323524
#SPJ11
what the effect rendered more hooks than during the previous render.
Answers
If the effect rendered more hooks than during the previous render, it means that the content loaded in the current render cycle has triggered the creation of more hooks than in the previous render cycle.
When the effect "rendered more hooks than during the previous render," it means that the current rendering of the component includes more hook functions than in the previous render. This could potentially lead to inconsistencies in the component's state and behavior, as the order and number of hooks must remain constant between renders to ensure proper functionality.
This could be due to changes in the data or props passed to the component, or changes in the component's state. It could also be due to updates in the component's lifecycle methods or changes in the logic of the component. Ultimately, the increase in the number of hooks could have various effects on the component's behavior and performance, depending on the specific use case.
learn more about hooks here:
https://brainly.com/question/30660854
#SPJ11
Two devices used by the supermarket point-of-sale (POS) terminal are a bar code reader and a keyboard. Name two other input/output devices used at the POS and give a use for each device.
Answers
Answer:
1. Receipt printer
Use of receipt printer:
i. They are used to print customer transaction receipts for proof.
2. Touch screen monitor
Use of touch screen monitor:
i. Allow record of when, where, price, and other important information about the sale conducted.
Explanation:
A Point of sale (POS) terminal takes record of transactions at the point where a product is purchased or a service is rendered. A barcode reader is a price scanner that is an input device used in a point-of-sale (POS) terminal. The keyboard is also an input device. The receipt printer is an output device since it converts information into a readable format. While only a touch screen monitor among the other devices mentioned above is an input and output device, because of its touch panel and its ability to display information.
In a file called bank.py, implement a program that prompts the user for a greeting. If the
greeting starts with “hello”, output $0. If the greeting starts with an “h” (but not “hello”),
output $20. Otherwise, output $100. Ignore any leading whitespace in the user’s greeting,
and treat the user’s greeting case-insensitively.
I am using the Python 3 programming language.
Answers
Using the knowledge in computational language in python it is possible to write a code that greeting starts with “hello”, output $0 If the greeting starts with an “h" output $20.
Writting the code:from bank import value
def main():
test_noh()
test_h()
test_hello()
def test_noh():
assert value("Cat") == "$100"
assert value("meoW") == "$100"
assert value(" meow ") == "$100"
def test_h():
assert value("Hey") == "$20"
assert value("hi") == "$20"
assert value("How are you?") == "$20"
assert value(" How's it going") == "$20"
def test_hello():
assert value("Hello There") == "$0"
assert value("hello") == "$0"
assert value("HELLO") == "$0"
if __name__ == "__main__":
main()
See more about python at brainly.com/question/12975450
#SPJ1

You can't export data from Access to Word. True False
Answers
False. Exporting data from Access to Word is a relatively simple process that can be done in just a few steps. By doing so, you can create documents, reports, and other written materials that include data from your database.
You can export data from Access to Word.Access and Word are part of the Microsoft Office suite of productivity applications. Although they are separate applications, they can be used together to perform a variety of tasks. Access is a database management application that can be used to create, store, and manage data, while Word is a word processing application that can be used to create documents, reports, and other written materials.
While it is true that Access and Word are different applications, they can be used together to perform a variety of tasks. For example, you can export data from Access to Word to create a report or other document that includes information from your database. This process is known as a mail merge.In order to export data from Access to Word, you will need to follow these steps:Open the database that contains the data you want to export.Select the table or query that contains the data you want to export.
Click on the "External Data" tab in the ribbon.Select the "Word" option from the "Export" group.In the "Export - Word Document" dialog box, select the options you want for your export, such as the file name, file format, and data to include.Click "OK" to export the data from Access to Word.
To know more about export data visit :
https://brainly.com/question/14337731
#SPJ11
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
When performing an offline join, which is the first system on which the djoin.exe needs to be run?
Answers
When performing an offline join, which exists the first system on which the djoin.exe needs to be run exists offline domain join.
What is meant by offline domain join?With the help of the brand-new offline domain join capability in Windows 7 and Windows Server 2008 R2, you may add a machine to a domain without directly contacting a domain controller. When network connectivity is not widespread, this capability can add computers to a domain.
Trust links between the computer and the Active Directory domain are altered when a computer joins a domain. There was no software available to update these relationship settings on a computer prior to Windows 7 and Windows Server 2008 R2, unless it was d When the computer reboots, it will be joined to the domain after running the text file on it with djoin.exe.
When performing an offline join, which exists the first system on which the djoin.exe needs to be run exists offline domain join.
To learn more offline domain join, refer to:
https://brainly.com/question/21258550
#SPJ4
4. name at least 4 different common output devices
Answers
These are the four most typical output devices that can be utilized to create and display output data.
Output devices are those that allow the user to receive output data that was entered in a computer. These are crucial devices that can be used to produce output in various formats, and they may be used to complete a task. There are a variety of output devices available on the market, and each has its own set of characteristics. Let's take a look at some of the most prevalent output devices in the following paragraphs.
1. Monitor: A monitor is one of the most frequently used output devices, and it is utilized to see the output of a computer. It displays pictures and videos in high definition and features various screen sizes.
2. Printer: Printers are devices that print output data on paper or other materials, and there are several sorts of printers. Inkjet, laser, and dot-matrix printers are the most common types.
3. Speaker: Speakers are devices that allow us to hear output data in the form of sound. They come in a range of sizes and shapes, with some being quite large, while others are small enough to be used with laptops.
4. Projector: Projectors are output devices that are used to project images or videos on a screen. They are primarily utilized in presentations, classrooms, and movie theaters, among other places.
In conclusion, these are the four most typical output devices that can be utilized to create and display output data.
Learn more about Output here,https://brainly.com/question/27646651
#SPJ11
Four different common output devices are monitors, printers, speakers, and headphones.
Output devices are peripheral devices that display or present data from a computer. They allow users to receive information or output from the computer system. Here are four different common output devices:
monitors: Monitors are visual output devices that display text, images, and videos. They come in various sizes and resolutions, and allow users to interact with the computer system visually.printers: Printers produce hard copies of digital documents. They can print text, images, and graphics on paper or other media. There are different types of printers, such as inkjet printers and laser printers.speakers: Speakers are audio output devices that produce sound. They allow users to listen to audio from the computer system, such as music, videos, or voice recordings.headphones: Headphones are also audio output devices that allow users to listen to sound from the computer system. They are worn over the ears and provide a more private listening experience.Learn more:About common output devices here:
https://brainly.com/question/30901728
#SPJ11
How would Patrick save his formatted message in Outlook?
O The Draft Folder saves a real-time version automatically.
O Click Save As Draft and it is placed in the Saved Folder.
O Click Save and it remains in the Draft folder for later edits.
O Click Archive and it will save the message in your Documents folder.
Answers
Answer:
O Click Save and it remains in the Draft folder for later edits.
Explanation:
I hope it's help
Answer:
The Answer is C!
Hope it helps
Explanation:
Write a code in python that guesses a hardcoded answer and keeps on asking the user until the user gets the answer correct. The cmputer should be telling the user if the number they are guessing is too low or too high.
Answers
import random
#You can change the range.
answer = random.randint(1,1000)
counter = 0
while(True):
guess = int(input("Make a guess: "))
message = "Too high!" if guess>answer else "Too low!" if guess<answer else "You won!"
print(message)
if(message=="You won!"):
print("It took",counter,"times.")
break
else:
counter+=1

Look at the examples of type on a background.
Which example best shows the use of contrast to help the reader distinguish the type on the background?
Answers
An example of using contrast to help the reader distinguish the type on the background would be using a light colored font (such as white or pale yellow) on a dark background (such as black or dark blue). This creates a high contrast between the font and the background, making it easy for the reader to read the text.
What is background?In order to convey meaning and amplify the qualities of a piece of art, contrast in art refers to the technique of placing dissimilar visual elements next to one another.
Artists use a variety of tools at their disposal, such as shadows, light, color, size, and composition, to create contrast. A background is a part of your artwork that is typically situated behind or around the subject.
Learn more about background on:
https://brainly.com/question/23198052
#SPJ1
coment on this if your user starts with dida
Answers
Answer:
oh sorry i needed points but i have a friend whos user starts with dida
Explanation:
THIS QUESTION IS ABOUT NETWORK ACCESS LAYER! WILL GIVE 30 POINTS PLEASE ANSWER ASAP
Diagram: Include a diagram (using squares, circles, arrows, etc.) showing the data unit and what its headers and footers do.
Answers
Answer:
it's 15 points
Explanation:
send a photo...can't understand like this
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
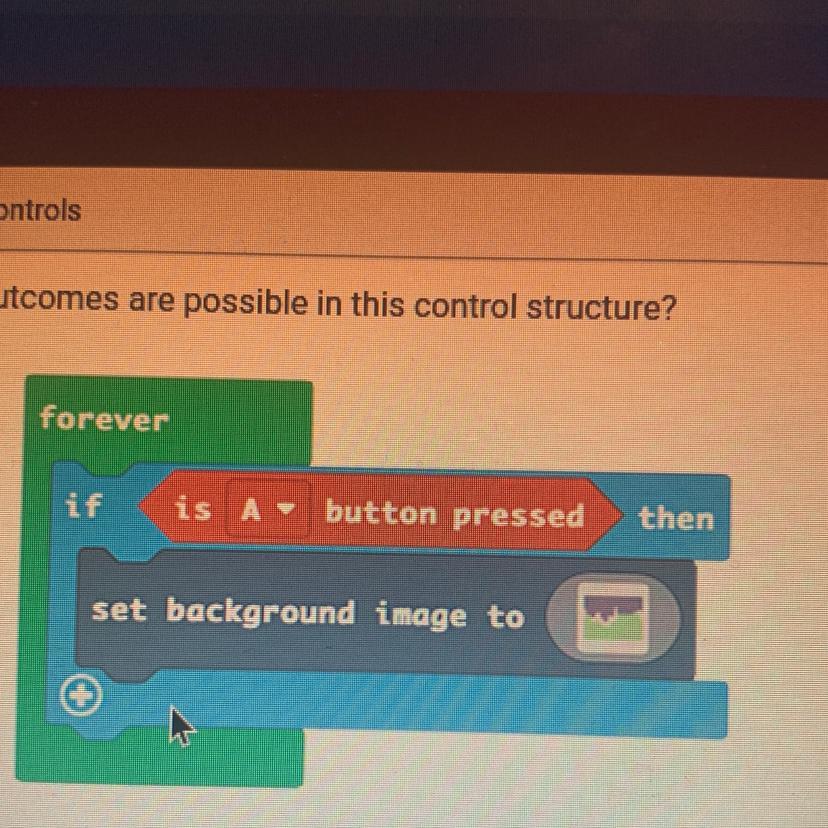
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
you are tasked with improving the performance of a functional unit. the computation for the functional unit has 4 steps (a-d), and each step is indivisible. assume there is no dependency between successive computations. (5pts) what is the greatest possible clock rate speedup possible with pipelining? you do not need to worry about the register timing constraints (e.g., delay, setup, hold). explain your reasoning. (5pts) for maximizing the clock rate, what is the minimum number of pipeline registers you would use? where would you insert the registers (draw or describe) into the datapath provided for this functional unit? why not use fewer or more pipeline stages?
Answers
What is pipeline?
A pipeline, also known as a data pipeline, is a succession of data processing devices connected in computing, where the output of one is the input of the next. Pipeline elements are frequently processed in parallel or in a time-sliced fashion. Between elements, some buffer storage is frequently inserted.
Execution time for 1 instruction in Non-pipeline
=(5+8+4+3)
=20ns
Execution time for I instruction in pipeline.
= Max (5,8,4,3)
= 8 ns
Speedup= 20/8
=2.5
Minimum number of pipeline registers= 3
Each register stores intermediate result of 2 steps in pipeline. Hence, only 3 registers is needed.
To learn more about pipeline
https://brainly.com/question/10854404
#SPJ4
Cryptocurrency is a form of payment that:
• A. can be used for digital or face-to-face transactions.
•
B. can only be exchanged for specific things.
®
C. exists online and in local banks.
•
D. can be exchanged online for goods and services.
Answers
Cryptocurrency is a form of payment that can be used for digital or face-to-face transactions. Option A is the correct answer.
Cryptocurrencies is a decentralized digital currency that is secured through cryptography, and it exists solely online. Cryptocurrencies are not backed by any government or financial institution and can be used to purchase goods and services, as well as exchanged for other currencies. Transactions made using cryptocurrency are recorded in a decentralized public ledger called a blockchain.
Cryptocurrency can be stored in digital wallets and can be bought and sold on various online exchanges. As it is not bound by traditional banking regulations, cryptocurrency has the potential to offer a more secure and efficient way to make payments.
Option A is the correct answer.
You can learn more about Cryptocurrency at
https://brainly.com/question/26103103
#SPJ11
which keyboard shortcut would you press to copy cells that are selected in a spreadsheet?
Answers
Answer:
ctrl c
Explanation:
why does hashing prevent hackers from stealing the contents of a password file?
Answers
Answer:
Hashing prevents passwords from being exposed or stolen by threat actors, since they are not stored as plaintext. For example, when users create an account with a username and password on a website, their password is hashed and stored in an internal file system in an encrypted form.
Explanation:
pls mark brainliest