A and b verify that they possess a common key k, using a public one-wayfunction h, as follows:1. a sends h(h(k)) to b2. b verifies that the received value is correct3. b sends h(k) to a4. a verifies that the received value is correct
Answers
In this scenario, A and B are using a public one-way function (h) to verify that they possess a common key (k). The process starts with A sending h(h(k)) to B, which B verifies is correct. B then sends h(k) to A, which A verifies is correct.
To clarify, A and B verify that they possess a common key (k) using a public one-way function (h) through the following steps:
1. A sends h(h(k)) to B: A applies the one-way function h twice on the common key k and sends the result to B.
2. B verifies that the received value is correct: B also applies the one-way function h twice on their key k and checks if the result matches the value received from A.
3. B sends h(k) to A: After verification, B applies the one-way function h once on the common key k and sends the result to A.
4. A verifies that the received value is correct: A applies the one-way function h once on their key k and checks if the result matches the value received from B.
This process helps A and B confirm that they both have the same common key k while using the public one-way function h to ensure the security of their communication.
To know more about public key visit:
https://brainly.com/question/29999097
#SPJ11
Related Questions
From The Top Of Page Gallery, Insert An Accent Bar 1 Page Number. Close Header And Footer.
Answers
The way to go about the function from From The Top Of Page Gallery are:
On the Insert tab, click.Click the Page Number button in the Header & Footer category.Opens the Page Number menu.Point to Top of Page under Page Number in the menu.The page number formats gallery appears.Select Accent Bar 2 from the gallery.The header includes the pre-formatted word "Page" and the page number.Select the Close Header and Footer button within the Close group.What exactly do MS Word's header and footer do?In regards to the difference to a footer, which is text that is positioned at the bottom of a page, a header is text that is positioned at the top of a page. In most cases, this space is used to add document details like the title, chapter heading, page numbers, and creation date.
Therefore, to place a header or a footer in your MS word, Select Page Layout from the View drop-down menu on the Layout tab. The Header & Footer button is located under Page Setup on the Layout tab. By selecting the desired header or footer from the Header or Footer pop-up menu, you can choose from a variety of standard headers or footers.
Learn more about Page Gallery from
https://brainly.com/question/15489395
#SPJ1
Millions of americans have visited a newly launched government website over the past week to apply for what?.
Answers
Millions of Americans have visited a newly launched government website over the past week to apply for Student Debt Relief.
Are the student loans automatically forgiven?After you have repaid your Direct Loans in full for 120 eligible months while employed full-time by a qualifying company, PSLF will forgive the remaining balance on your loans.
According to higher education expert Mark Kantrowitz, if you recertified your wages on an income-driven repayment plan in 2021 or 2022, you may be eligible for the automatic cancellation. You must, however, have submitted the FAFSA for the academic year 2022–2023, he added.
Learn more about student Debt Relief from
https://brainly.com/question/28146556
#SPJ1
The data you enter into a statistical software program to perform analyses on constitutes values of the ______________.
a. dependent variable
b. independent variable
c. extraneous variable
d. confound
Answers
The data is entered into a statistical software program to perform analyses on constitutes values of the dependent variable. The dependent variable is the outcome variable that is measured or observed during an experiment. So, the correct option is A.
It is the variable that is affected by the independent variable, which is the variable being manipulated or changed by the researcher. The independent variable is used to see how it affects the dependent variable. For example, if a researcher wanted to study the effects of caffeine on cognitive performance, they would manipulate the independent variable (caffeine consumption) and measure the dependent variable (cognitive performance).
Extraneous variables are variables that can potentially affect the outcome of an experiment but are not intentionally manipulated by the researcher. These variables are often controlled for in the study design or through statistical methods to ensure they do not confound the results.
Confounding variables are variables that have an impact on the dependent variable that cannot be distinguished from the effects of the independent variable. Confounding variables can lead to inaccurate or misleading results, so it is important for researchers to identify and control for them during the study design and analysis process.
Overall, understanding the role of dependent and independent variables is essential for conducting effective and accurate statistical analyses.
You can learn more about statistical software programs at: brainly.com/question/17017761
#SPJ11
you are not sure if a certain word has an"e"at the end
Answers
do you think fintechs, in general, will make trading markets more or less volatile? be specific and provide solid defense in your post for the position you take
Answers
I believe that overall FinTechs will reduce the volatility of trading markets in the future.
What does reduce volatility means?
Volatility is frequently used to describe the degree of risk or uncertainty associated with the magnitude of variations in a security's value. A security's value may potentially range over a wider range of values if its volatility is higher. This implies that the security's price can fluctuate sharply in either direction over a brief period of time. A security's value will not change significantly and will be more stable if its volatility is lower.
FinTechs employ technology to improve the function of finance and boost the effectiveness of operations in the financial and investing industries. Technology may be employed in financial trading, and it has a lot of benefits and conveniences to offer.
There are benefits in terms of efficiency, accessibility, cost effectiveness, and speed for different trading market participants. The settings and circumstances for market volatility are greatly diminished and diluted by the integration and convergence of all these components.
Additionally, a lot of FinTechs are using blockchain technology, which makes up for the shortcomings of the centralized system it replaces. It should be noted that one of the main causes of market volatility is the use of a centralized system. Blockchain is based on a decentralized system, which significantly reduces market volatility.
Additionally, FinTechs eliminate unnecessary legal and financial red tape, which enables the hosting of real-time secondary markets. FinTechs implement a safe and unquestionable infrastructure based on mathematical principles, which reduces the level of volatility in the trading markets.
Learn more about Volatility click here:
https://brainly.com/question/29394588
#SPJ4
Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time. True or False
Answers
Answer:
true
Explanation:
The statement "Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time" is true.
What is a PowerPoint presentation?G slides can be used to create a PowerPoint presentation. By clicking the large sign at the top left of your screen, you can log in and create a presentation if you have an account. I use slides to create my presentations because it is so simple to use.
You ought to investigate it for yourself. Since it is entertaining, students should enjoy both watching and participating in such presentations. With the right approach, it can assist schools in meeting the needs of all students.
When using PowerPoint, you can project color, images, and video for the visual mode to present information in a variety of ways (a multimodal approach).
Therefore, the statement is true.
To learn more about PowerPoint presentations, refer to the below link:
https://brainly.com/question/16779032
#SPJ2
q9. big o notations and runtime of algorithms: suppose you have the option of running three algorithms, alg1, alg2, alg3, with running times o(1000n ln n), o(n3), 300n2, respectively. which algorithm would you select (i.e., which one is the fastest according to big-oh analysis) to run on input instances with arbitrarily large sizes n?
Answers
Big O predicts how an algorithm's performance will change as the input size increases and uses this information to define the runtime necessary to carry out an algorithm. The runtime of your algorithm is not, however, indicated. Using time and space complexity, Big O notation evaluates your algorithm's effectiveness and performance.
What is Big O?A representation of an algorithm's worst-case complexity is Big O, commonly referred to as Big O notation. The complexity of an algorithm is described using algebraic language.Big O predicts how an algorithm's performance will change as the input size increases and uses this information to define the runtime necessary to carry out an algorithm. The runtime of your algorithm is not, however, indicated.Using time and space complexity, Big O notation evaluates your algorithm's effectiveness and performance.The hardware, OS, and CPU you utilise are a significant underlying component determining the effectiveness and performance of your software.When examining an algorithm's performance, however, you don't take this into account. What matters is the time and space complexity as a function of the amount of the input, not the other way around.To Learn more About Big O Refer To:
https://brainly.com/question/29647434
#SPJ4
Big O uses this information to define the runtime required to execute an algorithm and predicts how an algorithm's performance will change as the input size grows.
However, your algorithm's runtime is not shown. Big O notation evaluates the efficiency and performance of your algorithm using time and space complexity.
Big O: What is it?Big O, or Big O notation, is a representation of an algorithm's worst-case complexity. An algebraic language is used to describe an algorithm's complexity. Big O uses this information to define the runtime required to execute an algorithm and predicts how an algorithm's performance will change as the input size grows. However, your algorithm's runtime is not shown.
Big O notation evaluates the efficiency and performance of your algorithm using time and space complexity. The effectiveness and performance of your software are heavily influenced by the hardware, operating system, and CPU you use.
However, this is not taken into account when evaluating an algorithm's performance. The time and space complexity as a function of the quantity of input is what matters, not the other way around.
Learn more about Big O :
brainly.com/question/15691129
#SPJ4
James wants to buy a pair of pants for $60.
When he went to the store he found that the
price was marked down by 20%. How much do
they cost now?
Answers
Suppose you have two different methods to accelerate a program. They have the same cost but cannot be used at the same time. Method 1 can accelerate 20% of the program 100 times. Method 2 can accelerate 20% of the program 10 times and 15% of the program 6 times. Calculate the speedup of each method on the entire application.
Answers
Method 1 Speedup = 1.25; Method 2 Speedup = 1.225.
To calculate the speedup of each method, we use the formula: Speedup = 1 / (1 - A + A/S), where A is the percentage of the program accelerated and S is the acceleration factor.
For Method 1, A = 20% = 0.2 and S = 100.
For Method 2, we have two portions to consider.
For the first portion, A1 = 20% = 0.2 and S1 = 10. For the second portion, A2 = 15% = 0.15 and S2 = 6.
To find the total speedup of Method 2, we'll first calculate the speedup for each portion and then combine them.
With these values, we find that Method 1 Speedup = 1 / (1 - 0.2 + 0.2/100) = 1.25, and Method 2 Speedup = (1 / (1 - 0.2 + 0.2/10)) * (1 / (1 - 0.15 + 0.15/6)) = 1.225.
Therefore, Method 1 offers a slightly higher speedup for the entire application.
To know more about program visit:
brainly.com/question/14368396
#SPJ11
You are designing software for elderly people. Which two features can you
add to your program to improve accessibility?
O A. Give instructions in both text and audio formats
B. Increase the font size of the text
C. Avoid using colors in the design
D. Allow birthdates in the 1800s to be entered
Answers
give instructions in both text and audio formats
Safety Rules Criss-Cross Puzzle
15
Across
2. Report all equipment
that is out of
to the
1. Observe all safety
3. Never use equipment without
6. Make sure to save and close all your
application.
7. Sit in the chair in an
9. Playing or running around the room is not
10. Never insert a
computer.
13. Cutting blades should be directed
teacher.
4. When using the
keep your
fingers away from the
area where the staples
come out.
5. No student will be
allowed to
a
machine until he has
been instructed in its
proper use.
8. Never eat or drink in
the
11. Never throw, toss or
pitch
to
another person.
12. When cut or injured
report to the
at once.
14. Avoid
backwards in chairs.
15. Keep your
Down
listed on the equipment.
off
other people and don't
talk to them while they
are operating a machine.
with the individual
position.
object in the outlets at the back of the
from the body.
Answers
After Mila plugged her phone into the battery pack the amount of energy in the battery pack pack increase ,decrease or stay the same explain why
Answers
Answer: The amount of energy in the battery pack is reduced as the phone receives energy stored from the battery pack. This will cause the phone to charge and the battery pack to lose power.
Explanation:
[Edhesive] 4. 2 Code Practice: Question 1
Write a program that inputs numbers and keeps a running sum. When the sum is greater than 100, output the sum as well as the count of how many numbers were entered.
Sample Run:
Enter a number: 1
Enter a number: 41
Enter a number: 36
Enter a number: 25
Sum: 103
Numbers Entered: 4
Hint: If you get an EOF error while running the code you've written, this error likely means you're asking for too many inputs from the user
Answers
#Sum and count variable.
sum, count = 0, 0
#While loop
while(sum<100):
sum += int(input("Enter a number: "))
count += 1
#Print stats.
print(f"Sum: {sum}\nNumbers Entered: {count}")
C++:#include <iostream>
int main(int argc, char* argv[]) {
// Sum and count variable.
int sum, count, temp;
// While loop
while (sum < 100) {
std::cout << "Enter a number: ";
std::cin >> temp;
sum += temp;
count++;
}
// Print stats.
std::cout << "Sum: " << sum
<< "\nNumbers Entered: " << count
<< std::endl;
return 0;
}
The Monte Carlo method uses ___________ for computer simulations
Answers
The Monte Carlo method uses repeated random sampling for computer simulations.
What do you mean by Monte Carlo method?The Monte Carlo Method, sometimes referred to as the Monte Carlo Simulation or a multiple probability simulation, is a statistical method for predicting the outcomes of an uncertain event.
It is possible to think of Monte Carlo methods as a group of computer approaches that rely heavily on random sampling in order to solve mathematical issues in a (often approximate) manner. Within this paradigm, integration and optimization are the two categories of statistical issues that are most frequently addressed.
Since their inception, Monte Carlo Simulations have evaluated how risk affects a variety of real-world situations, including artificial intelligence, stock markets, sales forecasting, project management, and pricing.
To learn more about statistical methods refer to:
https://brainly.com/question/14441578
#SPJ1
Helpppp
You can see the output if your html result using any web browser ?
True or False
Answers
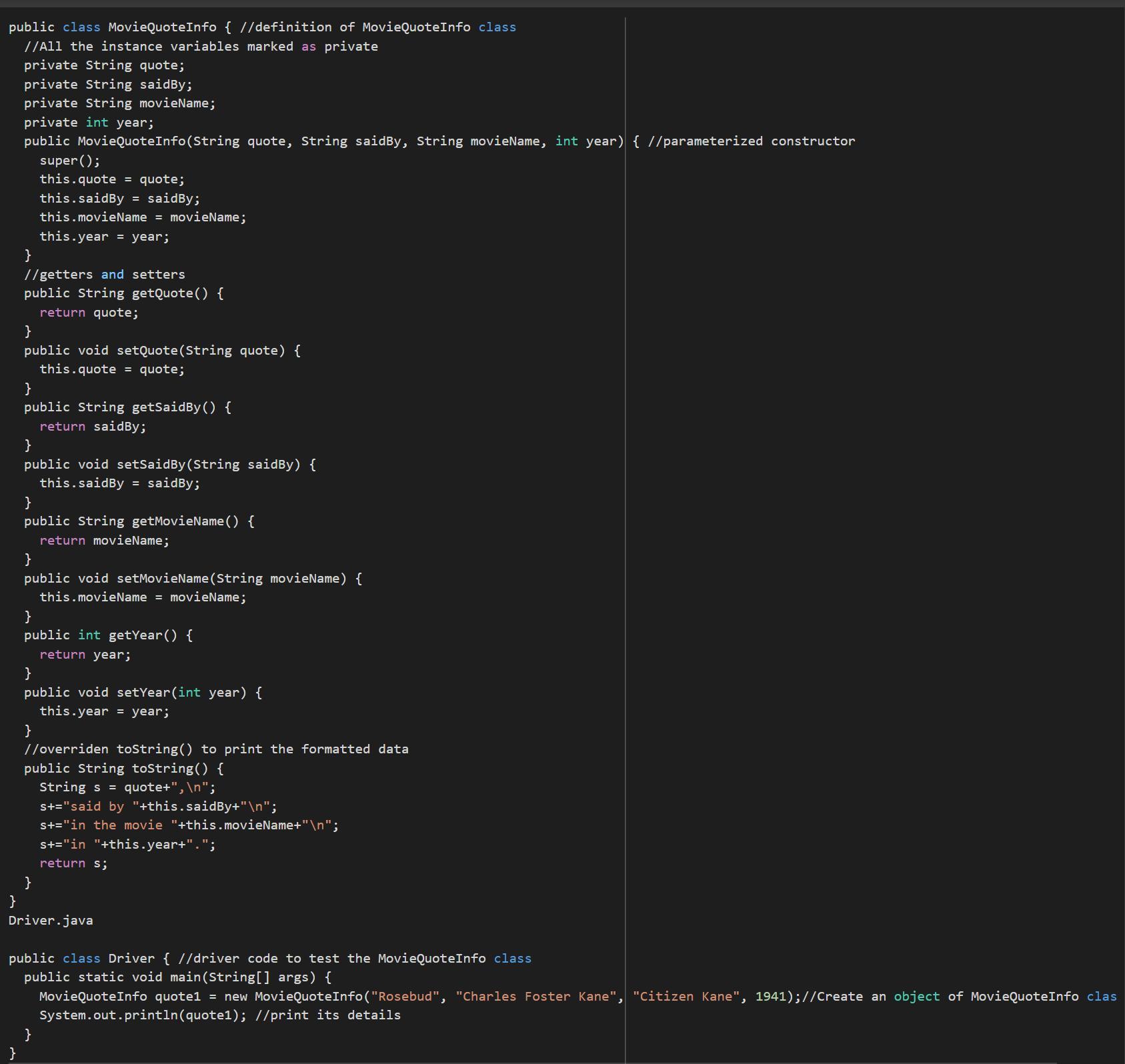
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
Suppose you are writing an anonymous JavaScript function that will run when your web page loads, and you want to include a statement that will cause a selection list in a web form to become active and ready for data entry. Which method should you apply in this statement?
a. element.focus()
b. element.blur()
c. element.select()
d. element.selectedIndex()
Answers
Answer:
The correct answer is a. element.focus().
Explanation:
the focus() method sets cognizance on the specified element if it can be focused. The focused detail is the element on the way to receive the keyboard and similar occasions by default. So, in case you need to make a ramification listing in a web form active and geared up for information access, you should use the focus() technique.
Here is an example of how to use the focus() method in an anonymous JavaScript function:
function() {
var selectionList = document.getElementById("mySelectionList");
selectionList.focus();
}
This function will set focus on the selection list with the id mySelectionList when the web page loads.
To learn more about JavaScript function,
https://brainly.com/question/30331545
Answer:
Explanation:
The correct method to use in the statement to cause a selection list in a web form to become active and ready for data entry is:
element.focus()
The focus() method is used to give focus to an element on a web page, such as an input field or a selection list. When an element receives focus, it becomes the active element, and the user can interact with it or enter data.
In this case, to make a selection list active and ready for data entry when the web page loads, you can use the focus() method on the corresponding <select> element.
For example, if your selection list has an element ID of mySelect, you can include the following statement in your anonymous JavaScript function:
javascript
Copy code
document.getElementById('mySelect').focus();
This will programmatically give focus to the selection list with the ID mySelect, making it active and ready for data entry when the web page loads.
Therefore, the method to apply in the statement is element.focus()'.
T/F: A computer server experiences large fluctuations in the amount of data requests it receives throughout the day. Because of this variation, Little's Law does not apply.
Answers
False. Little's Law applies to any stable system, regardless of the variation in the arrival rate or service time.
What Little's Law states?
Little's Law states that the average number of items in a stable system is equal to the product of the average arrival rate and the average time that an item spends in the system.
Therefore, as long as the server is stable (i.e., the number of incoming requests is roughly equal to the number of outgoing requests), Little's Law can be used to analyze its performance. However, it is important to note that the fluctuations in the arrival rate or service time can affect the accuracy of the performance analysis.
To learn more about performance, visit: https://brainly.com/question/24610643
#SPJ4
For the network shown below, use two-pass method to determine the critical path, the project duration and each activity's slack time. (All durations shown are in weeks). (1 point)
Answers
The critical path for the network is A-C-E-G-I-K, with a project duration of 18 weeks. The slack time for each activity is as follows: Activity B has a slack time of 0 weeks, Activity D has a slack time of 1 week, Activity F has a slack time of 2 weeks, Activity H has a slack time of 0 weeks, and Activity J has a slack time of 3 weeks.
To determine the critical path, project duration, and slack time for each activity, we use the two-pass method.
First, we calculate the earliest start (ES) and earliest finish (EF) times for each activity. The ES for the first activity is 0, and the EF is the duration of that activity. For subsequent activities, the ES is the maximum EF of all preceding activities, and the EF is ES + duration.
Using this method, we find the following values:
Activity A: ES = 0, EF = 4
Activity B: ES = 4, EF = 4
Activity C: ES = 4, EF = 9
Activity D: ES = 9, EF = 10
Activity E: ES = 10, EF = 15
Activity F: ES = 15, EF = 17
Activity G: ES = 17, EF = 21
Activity H: ES = 4, EF = 4
Activity I: ES = 21, EF = 23
Activity J: ES = 23, EF = 26
Activity K: ES = 26, EF = 30
Next, we calculate the latest start (LS) and latest finish (LF) times for each activity. The LF for the last activity is the project duration, and the LS is LF - duration. For preceding activities, the LF is the minimum LS of all succeeding activities, and the LS is LF - duration.
Using this method, we find the following values:
Activity K: LS = 30, LF = 30
Activity J: LS = 26, LF = 30
Activity I: LS = 21, LF = 26
Activity H: LS = 4, LF = 4
Activity G: LS = 17, LF = 21
Activity F: LS = 15, LF = 17
Activity E: LS = 10, LF = 15
Activity D: LS = 9, LF = 10
Activity C: LS = 4, LF = 9
Activity B: LS = 4, LF = 4
Activity A: LS = 0, LF = 4
Finally, we calculate the slack time (ST) for each activity by subtracting EF from LS. The critical path consists of activities with zero slack time.
Using this calculation, we find the following slack times:
Activity A: ST = 0
Activity B: ST = 0
Activity C: ST = 0
Activity D: ST = 1
Activity E: ST = 0
Activity F: ST = 2
Activity G: ST = 0
Activity H: ST = 0
Activity I: ST = 0
Activity J: ST = 3
Activity K: ST = 0
The critical path for the network is A-C-E-G-I-K, with a project duration of 18 weeks. Activities B, H, and K have zero slack time, meaning any delay in these activities will cause a delay in the overall project. Activities D, F, and J have some slack time available, indicating that they can be delayed without impacting the project's duration.
To know more about network follow the link:
https://brainly.com/question/1326000
#SPJ11
Eleanor's company is providing her with training in the social and business practices of the country of Morocco. She will be working there for the next two years and it is important for her to understand these practices. This demonstrates expatriate Blank______ training.
Answers
Eleanor's company is providing her with expatriate cultural training. This type of training is essential for employees who are sent to work in a foreign country for an extended period.
It helps them to understand the cultural norms, business practices, and social etiquette of the host country. By providing Eleanor with this training, the company is ensuring that she will be able to integrate into the Moroccan culture and work effectively with her colleagues and clients. Expatriate cultural training can help to reduce culture shock, improve communication, and increase productivity. Overall, it is a crucial aspect of international business operations.
learn more about expatriate cultural training.here:
https://brainly.com/question/30005286
#SPJ11
a static class method can be accessed without referring to any objects of the class. group of answer choices false true
Answers
A static method cannot be invoked by an object of a class.
What is the difference between class methods and static methods?
A class method does not require a class instance. You can't access the instance ( self ), but you can access the class itself via cls . Static methods cannot access cls or self. They work like normal functions, but belong to the namespace of the class.
How can I find the static methods of a class?
A static method can be called directly from a class without creating an instance of the class. Static methods can only access static variables. Cannot access instance variables. A static method is associated with a class, so the syntax for calling or referencing a static method is:
name of the class. Method name.
How can I access static classes in Java?
A static class is a class created within a class, known in Java as a static nested class. Non-static data members and methods cannot be accessed. You can access it via the external class name. You can access static data members of external classes, including private ones.
To know more about static method visit;
https://brainly.com/question/13098297
#SPJ4
Critically define and discuss IPv4 addressing and differentiate between static and dynamic IP configuration
Answers
IPv4 addressing is a system used to identify and locate devices on a network using the Internet Protocol version 4 (IPv4) protocol. It employs a 32-bit address space, allowing for a total of approximately 4.3 billion unique addresses.
Static IP addressing refers to a configuration where a device on a network is assigned a fixed IPv4 address that does not change over time. The assignment of a static IP address is usually done manually by a network administrator or by configuring the device's network settings. Static IP addresses are typically used for devices that require a consistent and reliable address, such as servers, routers, or printers. Dynamic IP addressing, on the other hand, involves the automatic assignment of IP addresses to devices on a network. This is typically accomplished using a service called Dynamic Host Configuration Protocol (DHCP). With dynamic addressing, devices on the network are assigned IP addresses from a pool of available addresses maintained by a DHCP server. When a device connects to the network, it requests an IP address, and the DHCP server assigns it an available address for temporary use. The address lease can have a predefined time limit, after which the device may request a renewal or be assigned a different IP address.
Learn more about IP configuration here : brainly.com/question/32133615
#SPJ11
PYTHON --- Toll roads have different fees based on the time of day and on weekends. Write a function calc_toll() that has three parameters: the current hour of time (int), whether the time is morning (boolean), and whether the day is a weekend (boolean). The function returns the correct toll fee (float), based on the chart below.Weekday TollsBefore 7:00 am ($1.15)7:00 am to 9:59 am ($2.95)10:00 am to 2:59 pm ($1.90)3:00 pm to 7:59 pm ($3.95)Starting 8:00 pm ($1.40)Weekend TollsBefore 7:00 am ($1.05)7:00 am to 7:59 pm ($2.15)Starting 8:00 pm ($1.10)Ex: The function calls below, with the given arguments, will return the following toll fees:calc_toll(8, True, False) returns 2.95calc_toll(1, False, False) returns 1.90calc_toll(3, False, True) returns 2.15calc_toll(5, True, True) returns 1.05
Answers
The toll program illustrates the use of conditional statements;
As a general rule, conditional statements are used to make decisions
The toll programThe toll program written in Python where conditional statements are used to make several decisions is as follows:
def calc_toll(hour, morning, weekend):
toll_fee = 0
if weekend == False:
if morning == True:
if hour < 7:
toll_fee+=1.15
elif hour < 10:
toll_fee+=2.95
elif hour <= 12:
toll_fee+=1.90
else:
if hour < 3:
toll_fee+=1.90
elif hour < 8:
toll_fee+=3.95
elif hour >= 8:
toll_fee+=1.40
else:
if morning == True:
if hour < 7:
toll_fee+=1.05
elif hour <= 12:
toll_fee+=2.15
else:
if hour < 8:
toll_fee+=2.15
elif hour >= 8:
toll_fee+=1.10
return toll_fee
Read more about conditional statements at:
https://brainly.com/question/24833629
#SPJ1
Jack knows how to use word processors, spreadsheets, and presentation software. He also has a basic knowledge of hardware, software, and the Internet. Given this information, it can be concluded that Jack has _____ literacy.
Answers
Answer: computer literacy
Given the above information, it can be concluded that Jack has computer literacy.
What is Computer literacy?This is known to be defined as given knowledge and ability that a person has in the area of the use of computers and its related technology in an efficient manner.
Note that Given the above information, it can be concluded that Jack has computer literacy.
Learn more about computer literacy from
https://brainly.com/question/20892559
#SPJ6
Web are websites that allow people to congregate online and exchange views on topics of common interest.
a. True
b. False
Answers
Answer:
B
Explanation:
B. False a web is not a Website
How do I indent the 1. bullet so it is not lined up with the regular bullet above it?

Answers
Answer:
Change bullet indents
Select the bullets in the list by clicking a bullet. ...
Right-click, and then click Adjust List Indents.
Change the distance of the bullet indent from the margin by clicking the arrows in the Bullet position box, or change the distance between the bullet and the text by clicking the arrows in the Text indent box.
Explanation:
mark me braineliest
500 Points
Multiple Choice Questions (MCQs).
1.Which one of the following options in the Start menu will you click to access any
program installed on your computer controls?
a.Shut down
b. Documents
Control Panel
d All Programs
2.When you right click on the desktop area what do you get?
a.Acontext menu
b. A short icon
c. Documents Folder
d Network Places Folder
3.Which shortcut key should be pressed to switch between open program windows?
a. Alt + Tab
b. Ctrl + Tab
C. Shift + Tab
d Shift + Alt
4.Windows distinguishes between the different drives by means of a naming convention. Each
drive is designated by a letter followed by:
a. A colon(:) sign
b. Anasterisk (*) sign
c. An exclamation point (!) sign
d. A semicolon (;) sign
5. Which of the following will you use to display the contents of a drive?
a Shift + click
b. Right click
c. Double click
d Ctrl + click
6. You can display a shortcut menu for most objects in Windows by
them
a. Right clicking
b. Shift + clicking
c. Double clicking
d. Ctrl + clicking
7. Which of the following characters is allowed in a Windows file name or folder?
a. :
b. ?
c. >
d. None of these
8. You can copy and paste files from one folder to another using the Copy and Paste commands in _____the menu.
a File
b. View
c. Special
d. Edit
9. Which of the following is not a method of deleting files and folders?
a. Select and press Delete key
b. Right click and select Delete option.
c. Use the shortcut menu.
d. Hold down Shift key, select and Delete.
10. In Windows Explorer, the currently selected folder in the navigation pane is:
a bold faced
b. shaded
c.italicized
d highlighted
Bhai please solve those people solve it marked as branlist
Answers
Answer:
1. d
2. b
3. c
4. d
5. a
6. a
7. d
8. c
9.a
10.b
Explanation:
2-a
3-b
4-a
5-a
6-a
7-d
8-a
9-c
10-d
Thank you!
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
a picture password is made up of what components? (choose all that apply.) a. Picture b. Letters c. Symbols d. Numbers
Answers
A picture password is made up of the following components: a. Picture, c. Symbols. A picture password is a security feature in Windows operating system that allows users to sign in using a combination of gestures or patterns drawn on an image instead of a traditional password.
The user chooses an image and then creates a set of gestures or patterns, such as circles, lines, or taps, on specific parts of the image. When the user logs in, they simply redraw the same gestures or patterns on the image to authenticate themselves. Picture password is designed to be an easier and more intuitive way of logging into a device, especially on touch-enabled devices such as tablets and smartphones. However, it may not be as secure as traditional passwords as the gestures or patterns may be easily guessed or observed.
To learn more about Password Here:
https://brainly.com/question/30482767
#SPJ11
I don't have anything but thank for the help
Answers
Answer:
lol bro ur welcomeee.ee.e.e.e.e.