a is a block of code containing standard sql statements and procedural extensions that is stored and executed at the dbms server. question 45 options: a) cursor-style process b) base table c) statement-level trigger d) persistent storage module (psm)
Answers
PSMs provide a robust and flexible way to implement complex database operations. They can perform multiple SQL statements and can also use procedural logic to perform conditional operations, error handling, and other tasks.
PSMs are a block of code that contains both standard SQL statements and procedural extensions, such as conditionals, loops, and variables. They are stored and executed on the database management system (DBMS) server, providing a way to execute complex database operations that cannot be performed using standard SQL alone.PSMs are used to implement complex business rules, data validations, and data manipulation tasks within a database application. They are stored in the database, making them persistent across sessions and transactions, and can be called by other parts of the application or by other PSMs.For such more question on database
https://brainly.com/question/518894
#SPJ11
Related Questions
Search and read all phenomenon listed below and identify the ICT platform they used.
PHENOMENON
1. EDSA and Cardinal Sin
2. EDSA dos
3. Million people march against Pork Barrel
4. Disaster relief operations and mobilization
Answers
Answer:
1. Radio broadcast
2. Text brigades
3. Social media and change website
4. Internet and text brigades
Explanation:
I'm having issues posting my answer. Please go through the attachment.
Answer:
1. Radio broadcast
2. Text brigade
3. Social media and change website
4. Internet and text brigades
Explanation:
ICT can serve as a medium through which change can be effected in a society.
1 EDSA and cardinal
The ICT used here was the radio.
2. EDSA dos
The ICT that was used her was the text brigades.
3. Million people march
The ICT used here was social media and the change website.
4. ICT used here is internet and text messaging.
Please I have provided background information to what caused these events. I typed my answers but the editor did not allow me post it.
Thank you.

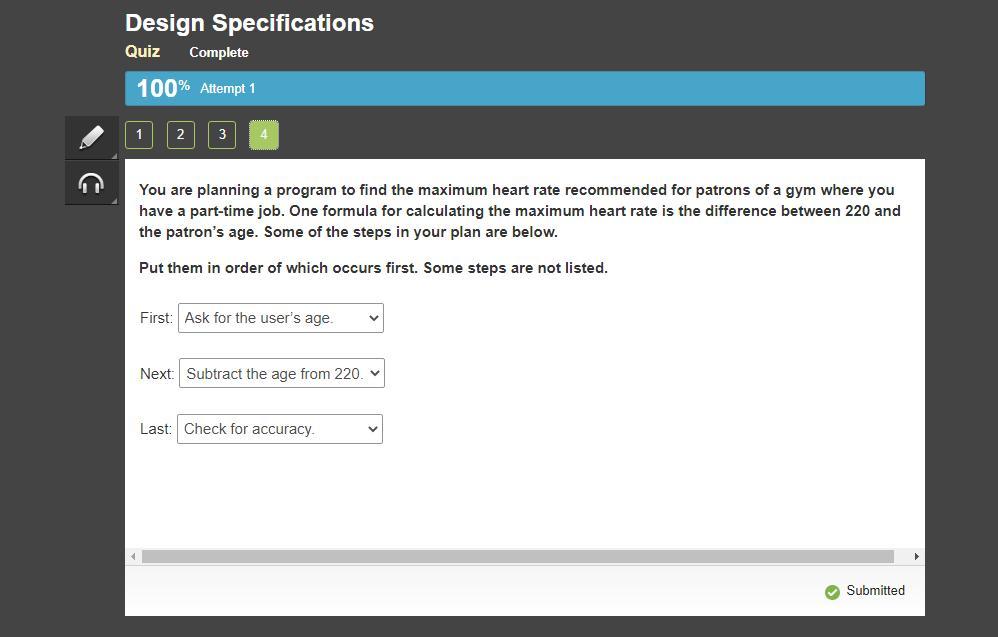
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
2 The software needed to send an email is:
+
A presentation software
B web authoring software
C communication software
D graphics software
Answers
Answer:
C communication software
Explanation:
C communication software IS THE ANSWER
Machines used in manufacturing, computers, printers, vehicles, furniture and fixtures generally are classified as
Answers
Machines used in manufacturing, such as computers, printers, vehicles, furniture and fixtures generally are classified as capital assets.
Explanation:
What are capital assets?
Capital assets are long-term assets used in business operations and can be classified as tangible or intangible assets. Computers, printers, vehicles, furniture, fixtures, and machines used in manufacturing are all examples of capital assets. Tangible assets are assets that can be touched, such as machines, vehicles, furniture, and fixtures. Tangible assets can be seen, touched, and felt. Intangible assets, on the other hand, cannot be touched. Copyrights, patents, and trademarks are examples of intangible assets. Most businesses classify their assets as either fixed or current, but the Financial Accounting Standards Board (FASB) does not require companies to do so.
Capital assets are long-term assets used in business operations and can be classified as tangible or intangible assets. Computers, printers, vehicles, furniture, fixtures, and machines used in manufacturing are all examples of capital assets.
Learn more about intangible assets here:
https://brainly.com/question/13541651
#SPJ11
Which of the following provides research abilities in Excel 2019?
O Thesaurus
O Smart Lookup
O Dictionary
O Spell check
Answers
The option that provides research abilities in Excel 2019 is option B: Smart Lookup.
What does Excel's clever lookup function do?Smart Lookup is a function that has the potential to be quite helpful. Simply right click on the cell in question and choose Smart Lookup to do a search. After that, Excel will start a Bing-powered search engine within the software, enabling you to look up what's in the cell online.
Note that You can easily access the features or actions you want to utilize by using the text field "Tell me" to input the words and phrases that describe what you want to do next.
Learn more about Thesaurus from
https://brainly.com/question/722610
#SPJ1
i need help, thank you

Answers
Answer:
uhh yes?
Explanation:
i think people can go on weeks without food, so a set of trays wit food should last them a day
plssss helppp meee with itt

Answers
..................................d
Further explains information found in a chapter
Answers
Answer:
The answer is E: Appendix
Explanation:
When examining the User accounts did any have unusual assignments
Answers
Unable to respond because the context or specific system for looking at user accounts is not mentioned.
I need additional details regarding the platform or system that is being used to look at user accounts in order to respond to this topic. I'm unable to give a precise response without this information. strange assignments in user accounts may, however, generally involve things like increased privileges, access to confidential data or systems, or strange login patterns. It's crucial to routinely examine user accounts in order to see any potential security issues and take the necessary precautions to reduce them. Sensitive information can be protected and security breaches can be avoided with regular user account monitoring and inspection.
learn more about user accounts here:
https://brainly.com/question/31375562
#SPJ11
what is an information technology?
Answers
Answer:
PLEASE BRAINLIEST
Explanation:
Information Technology means the use of hardware, software, services, and supporting infrastructure to manage and deliver information using voice, data, and video.
Answer:
Information technology is a subject that is the use of computers to store, retrieve, transmit and manipulate data or information, often in the context of business or other enterpise.
In order to make a character jump in Scratch, it is necessary to change what movement value?
Group of answer choices
x-value and z-value
z-value
y-value
x-value
Answers
Answer:
y value
Explanation:
Answer:
Y Values
Explanation:
Did on Edge
with a satellite phone system, you can call anywhere in the
Answers
With a satellite phone system, you can call anywhere in the world as long as you have a clear line of sight to a satellite.
Satellite phones operate on a different frequency than traditional cellular phones, which allow for communication over large distances. One type of mobile phone that is not commonly used is the satellite phone. It's a wireless phone, but it doesn't use cell towers like a typical cell phone. Instead, it communicates directly with satellites orbiting the planet.To make a call, the user must dial the phone number of the person they want to call and then press the call button. The signal is then sent to a satellite in orbit, which then routes the call to its destination.
More Questions on Satellites: https://brainly.com/question/18496962
#SPJ11
1. It defines the amount of white space that appears at the top, bottom, left, and right edge of
our document.
d clipboard.
Answers
Answer:
Margin is the correct answer to the given question .
Explanation:
The main objective of the margin is to setting the white space that are showing up at the top , bottom, left and the right corners of the file or the document .
Following are steps to setting the white space that are showing up at the top , bottom, left and the right corners of the file or the document
Firstly click on the page layout options .After that click on the margin tab .In this tab you will given the the top, bottom, left, and right margin according to your need Finally click on ok to finish them .Provide one example of how information technology has created an ethical dilemma that would not have existed before the advent of I.T
Answers
Answer:
grip
Explanation:
aaaaaaaaaaaaaaaaaaa
An enum switch case label must be the unqualified name of an enumeration constant.
a. True
b. False
Answers
According to the question of enumeration constant, the answer of the question is true.
What is enumeration constant?Enumeration constant is a named constant whose value is represented by a fixed number or a string. It is used in programming languages to represent a set of values. An enumeration constant can be used to represent a set of values such as days of the week, months of the year, or a set of states like open, closed, pending, etc. Enumeration constant makes code more readable and provides a way to assign a name to a set of values. It also eliminates the need to remember actual values. For example, if a program has to process values based on the days of the week, it can assign a number to each day, and then use the enumeration constant to refer to them instead of the actual values. Enumeration constants are also used in switch statements to identify cases that are part of a set of related values.
To learn more about enumeration constant
https://brainly.com/question/13264699
#SPJ1
host address: 00001010.00001010.00001100.11010000 subnet mask: 11111111.11111111.11110000.00000000 write the host address in decimal cidr notation.
Answers
The host address in decimal CIDR notation is 10.10.12.208/24.
The given host address is 00001010.00001010.00001100.11010000 and the subnet mask is 11111111.11111111.11110000.00000000.
The decimal CIDR notation is calculated as follows:
Divide the IP address into 4 octets: 00001010.00001010.00001100.11010000
Find the subnet mask in binary notation: 11111111.11111111.11110000.00000000
Count the number of ones in the subnet mask: 24 (there are 24 ones in the mask) The decimal CIDR notation is /24. Therefore, the host address in decimal CIDR notation is 10.10.12.208/24.
What is CIDR notation?
CIDR notation, short for Classless Inter-Domain Routing notation, is a way of representing IP addresses with their associated network masks. CIDR notation is an alternative way to represent subnet masks and is considered a more modern way to represent IP addresses, as opposed to the traditional subnetting system that uses the decimal system.
Learn more about CIDR at: https://brainly.com/question/31773091
#SPJ11
2. what are the advantages of breaking up a single logical message into a number of fixed-sized packets and then sending each one of those packets independently through the network?
Answers
The advantages of breaking up a single logical message into a number of fixed-sized packets is that it makes it more flexible and also it increases the performance and also the reliability of the internet.
There is an Easy lost data recovery Internet as it is an heterogeneous network.
Are packets made of fixed size?Packets are known to come in different sizes. They can also be made of a fixed size.
The examples are 1,000 or 1,500 bytes, or other kinds of variable sizes, based on the system. Its advantages is one where errors can be corrected easily and data recovery is fast.
Learn more about fixed-sized packets from
https://brainly.com/question/3991989
Identify the clusters in the figure below using the center-, contiguity-, and density-based definitions, for each of the figures. Also indicate the number of clusters for each case, and give a brief indication of your reasoning. Note that darkness or the number of dots indicates density. If it helps, assume center-based means K-means, contiguity-based means single link hierarchical, and density-based means DBSCAN.
Answers
I apologize, but as a text-to see obasedr analyze figures or images. Therefore, I cannot provide a specific analysis of clusters in a figure. However, I can provide a general explanation of the concepts you mentioned.
Center-based clustering, such as to identify clusters based on the centroid or center points of the data. It partitions the data into a predefined number of clusters by minimizing the sum of squared distances between data points and their assigned centroids.Contiguity-based clustering, like hierarchical clustering, focuses on identifying clusters based on the proximity or similarity between data points. It builds a hierarchy of clusters by iteratively merging the two closest points or clusters until a stopping criterion is met., such as identifies clusters based on the density of data points in the feature space. It groups together data points that are densely connected while considering regions of lower density as noise or outliers.
To learn more about mentioned click on the link below:
brainly.com/question/15105550
#SPJ11
What makes e-mail different from other forms of business communication?
I unable to send messages after hours
m unable to hear tone of voice
in unable to save messages
I unable to get communication cues from body language
Answers
Email offers convenience and flexibility but lacks the immediacy, personal connection, and non-verbal cues found in other forms of business communication.
You are unable to send messages after hours: With email, you have the flexibility to send and receive messages at any time, even outside regular business hours, unlike phone calls or in-person meetings that are subject to timing constraints. You are unable to hear the tone of voice: Unlike phone calls or face-to-face conversations where you can hear someone's tone of voice, email communication relies solely on written words, making it more challenging to interpret the tone and intent behind the message. You are unable to get communication cues from body language: Body language plays a crucial role in face-to-face interactions, conveying additional meaning and context. In email, this non-verbal communication element is absent, making it important to rely solely on the written words.
Learn more about email here:
https://brainly.com/question/30262540
#SPJ11
What is typeface
A. A family of fonts in a certain style
B. The spacing between individual letters
C. The tapered feature at the end of strokes
D. The logo and tagline that represent a company
E. The spacing between lines in a paragraph
Answers
Answer:
the answer is A - family of fonts.
Explanation:
plato/edmentum users! i got it correct on the test.
If a program needs to respond to what the user inputs by printing one of three different statements, what will the program require? Group of answer choices database random number generator decision generator conditional statement
Answers
Answer:
B
Explanation:
Answer:
Answer B: random number generator
Explanation:
Computer programming is the process that professionals use to write code that instructs how a computer, application or software program performs. At its most basic, computer programming is a set of instructions to facilitate specific actions. If you're wondering what a computer programmer is, it's a professional that creates instructions for a computer to execute by writing and testing code that enables applications and software programs to operate successfully.
Assuming a 300 km layer height, if the slant TEC is measured at 80 TECu for a 30∘ elevation, what is the vertical TEC? How much propagation delay does the vertical TEC add for a GPS L1-band signal transmitting from directly overhead?
I got 36.303 TECu for the VTEC, but I don't know how to find the propagation delay
Answers
The vertical TEC is 92.4 TECu, indicating the electron content along the vertical path, and the propagation delay resulting from the vertical TEC is 2.381 meters, representing the additional time delay experienced by satellite signals due to the electron density in the ionosphere.
Vertical TEC = Slant TEC / cos(elevation angle) is used. Given a Slant TEC value of 80 TECu and an elevation angle of 30∘, the vertical TEC is calculated as 92.4 TECu. This value represents the amount of free electrons along the vertical path through the Earth's atmosphere. Propagation delay (in meters) = (40.3 / L1 frequency) x VTEC is employed. With an L1 frequency of 1575.42 MHz and a VTEC of 92.4 TECu, the propagation delay amounts to 2.381 meters. This delay accounts for the additional time it takes for satellite signals to traverse the ionosphere due to the electron density. SO, the vertical TEC is 92.4 TECu, indicating the electron content along the vertical path. Therefore, the propagation delay resulting from the vertical TEC is 2.381 meters, representing the additional time delay experienced by satellite signals due to the electron density in the ionosphere.
Read more about Propagation delay. https://brainly.com/question/14868254 #SPJ11
For the same situation, which of the following statements is true about the charge on the capacitor plates?(1) Stored energy and voltage of a capacitor with a given charge are proportional to each other.(2) The capacitance of a plate capacitor is proportional to the dielectric constant.(3) Polarization amplifies the electric field in a material.(4) An electric field can induce dipoles in a material.
Answers
For the same situation, the statement that is true about the charge on the capacitor plates is that the stored energy and voltage of a capacitor with a given charge are proportional to each other.
What is a capacitor?
A capacitor is an electronic component that stores electrical energy in an electric field. A capacitor is made up of two conductive plates with an insulating layer separating them, known as a dielectric. Capacitance is a property of a capacitor that indicates how much charge can be stored on its plates for a given voltage difference between the plates. The stored energy and voltage of a capacitor with a given charge are proportional to each other. This is the correct statement about the charge on the capacitor plates.
The other statements mentioned in the question are not true about the charge on the capacitor plates.
Learn more about capacitors here:
https://brainly.com/question/29301875
#SPJ11
this text command defines how text will appear
Answers
In programming, the text command is not a specific command, but rather a term used to refer to a wide range of commands and functions that manipulate or display text.
What is a text command?Text commands may include functions for formatting, searching, replacing, and displaying text within a program or on a screen. These commands may be used in a variety of programming languages, including C, as you mentioned.
In C, for example, there are many standard library functions that can be used to work with text. Some of the most commonly used functions for working with text in C include:
printf(): used to display formatted text on the screen or in a file
scanf(): used to read formatted text from the keyboard or a file
strcpy(): used to copy one string of text to another
strcmp(): used to compare two strings of text to determine if they are equal
strlen(): used to determine the length of a string of text
Overall, text commands are a crucial part of programming and are used extensively in applications that involve working with text data.
Learn more about text on:
https://brainly.com/question/20169296
#SPJ1
So we see all the good aspects of Asymmetric Encryption. What are the downsides......
Answers
Asymmetric encryption does have some downsides despite its many advantages. One of the main drawbacks of asymmetric encryption is that it can be slower and more resource-intensive than symmetric encryption, which uses a single key for both encryption and decryption. This is because asymmetric encryption involves complex mathematical calculations to generate and manage the public and private keys.
Another potential downside is the risk of key compromise. Since the private key is so critical to the security of the system, if it falls into the wrong hands, it can be used to decrypt all of the encrypted messages sent using the corresponding public key. Furthermore, asymmetric encryption may not be suitable for all applications.
For instance, it may not be practical for encrypting large amounts of data, as the overhead of generating and managing keys for each transmission could become burdensome. asymmetric encryption relies heavily on the trustworthiness of the certificate authorities that issue and manage public keys. If these authorities are compromised or otherwise unreliable, the security of the entire system can be compromised as well.
To know more Asymmetric encryption visit:-
https://brainly.com/question/15187715
#SPJ11
Why do cooler substances have a tendency to sink?
Answers
Answer:
Explanation:
the molecules to slow down and they get closer to together.
:)
Convection happens in fluids (liquids & gases). The heat energy moves through the material as the particles in the material move through the material.
Hot liquids and gases rise because when they are heated they expand and become less dense. The less dense warm liquid or gas then floats up through the more dense cold liquids and gases.
Cold liquids and gases sink because when cooled they contract and become more dense. The more dense cold liquids and gases sink down through the less dense warm liquids and gases.
These changes in density cause the convection currents in the liquid or gas.

The question is attached. Please help! I'm about to fail this class for non-completion!
Use the getDay() method to extract the day of the week from the thisDay variable, storing the value in the wDay variable

Answers
Here is the code for the switch/case statement you described:
The ProgramThis code sets the wDay variable to an example value of 3. The switch/case statement checks the value of wDay and sets the imgSrc variable to the corresponding image filename.
The htmlCode variable is then set to an HTML string with an image tag that uses the value of imgSrc as the src attribute. Finally, the imgSrc value is stored in the inner HTML of the element with the ID banner.
The code is in the txt document.
Read more about switch statement here:
https://brainly.com/question/20228453
#SPJ1
T/F. MULTISET is similar to the table datatype.
Answers
The statement" a MULTISET is similar to the table datatype" is True because Both MULTISET and table datatype are used to store and manipulate collections of data.
A MULTISET is a type of collection that allows multiple instances of the same element to be stored, while the table datatype represents a collection of rows with a specific structure. They are used in database management systems to organize and store data in a structured manner.
However, there are some differences between them, such as the way they handle duplicate values and the operations that can be performed on them. Nonetheless, the similarities between a MULTISET and the table datatype make them comparable and useful for handling various data storage and manipulation tasks.
Learn more about database management systems : https://brainly.com/question/24027204
#SPJ11
What kind of technology is helping people who don't have access to the internet get it? A) Airplanes B) Balloons C) Routers D) Ships
Answers
Answer: c router
Explanation:
I took a test with the same question
If the value is set to equals to current entry then
a) the argument remains unchanged
b) the argument always changed
c) the argument will be deleted
d) the argument can be ignored
I will definitely mark you Brainliest for answering the correct answer!
Answers
Answer:
this is a fallacy
a is the answer