(a) List transport layer services. [3] (b) Write down the role of IP addresses and port numbers in selecting the final destination of data.
Answers
(a) Transport layer services are services provided by the Transport Layer of the OSI Model to ensure reliable data communication between applications running on networked hosts.
The three most common Transport layer services are given below:
Reliable data transfer: Data that is sent from one device to another is subject to loss, duplication, and corruption. To ensure that the data arrives at its intended destination, the Transport layer ensures reliable data transfer.
Service Access Points: The Transport layer provides a service access point to enable applications to interact with the Transport layer, which in turn interacts with the network layer.
Connection-oriented services: The Transport layer establishes a connection between two devices before data is transferred. This connection ensures that data is delivered without errors, duplication, or loss.
(b) An IP address is a unique numerical identifier assigned to a network device, whereas a port number is a unique numerical identifier assigned to a process running on a network device.
The role of IP addresses and port numbers in selecting the final destination of data is as follows:
An IP address determines the destination network and device to which the data is to be sent. The network address part of an IP address identifies the destination network, whereas the host address part identifies the specific device. This helps the network layer to forward the data to the correct network and device.
A port number determines the specific process or service running on the destination device that is responsible for handling the incoming data. Port numbers range from 0 to 65,535, with certain numbers reserved for specific applications. By identifying the specific process or service on the destination device, the port number enables the Transport layer to deliver the incoming data to the correct process or service.
Learn more about Transport layer services here:
https://brainly.com/question/31744066
#SPJ11
Related Questions
CAN SOMEONE HELP PLEASE GIVING OUT BRAINLIEST
Answers
you change the color, highlight, font, and size for a portion of text, and you later want to apply that same style to another section of the text. What is the easiest way to do that ?
a . alter permissions
b . format painter
c . design modification
d . picture tools
Answers
Answer:
Changing text color:
1. Click on the textbox to open the Text panel.
2. Click Edit Text.
Explanation:
Are there any incremented values from one loop to the next?
What variables may be used to track each loop in the program?
Answers
Answer:
You can place any expression you'd like in the final expression of the for loop, but it is typically used to update the counter variable.
counter variable is used throughout those parts. That variable keeps track of the current repetition, and is typically named i . The initialization part initializes the counter variable to a starting value.
Explanation:
While in the Current View command group for notes, which view options do you have available? Check all that apply.
Answers
Answer: A, B, C (is this for a Microsoft class?)
Explanation: Edge
Answer:
Icon
Note list
Last 7 days
Explanation:
Asia is selling bracelets to raise money for the school's band trip. She needs to determine how much she has already raised and how many more bracelets she must sell. Which response best explains why a computer would perform this task better than a human?
Computers can perform calculations at unbelievable speeds.
Computers can think creatively.
Computers can replicate human tasks.
Computers don't require sleep.
Answers
Note that where Asia is selling bracelets to raise money for the school's band trip and she needs to determine how much she has already raised and how many more bracelets she must sell, the response that best explains why a computer would perform this task better than a human is: "Computers can perform calculations at unbelievable speeds." (Option A)
What is the speed of the fastest computer?Frontier, the fastest supercomputer on the TOP500 supercomputer list as of May 2022, with a LINPACK benchmark score of 1.102 ExaFlop/s, followed by Fugaku. The United States has five of the top ten, China has two, and Japan, Finland, and France each have one.
As of June 2022, China had 173 of the world's 500 most advanced and powerful, one-third more than its next competitor, the United States, which had an additional 128 supercomputers.
Learn more about computing speed:
https://brainly.com/question/2072717
#SPJ1
I will give brainliest help!
Architectural blueprints are protected under copyright but the actual buildings are not.
A.
True
B.
False
Answers
(I’m 100% sure, I searched it up)
Please mark as brainiest
What is 01101010 in Denary?
PLEASE ANSWER I WILL GIVE U BRAINILEST !!!
Answers
Answer:
Binary 01101010 = 106
Explanation:
Answer:139
Explanation:
brain
Tech A says that most lug nuts and studs are right-hand threaded, which means they tighten when turned clockwise. Tech B says that some lug nuts and studs are left-handed, which means they tighten when turned counterclockwise.
Answers
This question is incomplete.
Complete Question
Tech A says that most lug nuts and studs are right-hand threaded, which means they tighten when turned clockwise. Tech B says that some lug nuts and studs are left-handed, which means they tighten when turned counterclockwise. Who is correct?
a) Tech A
b) Tech B
c) Both Tech A and B
d) Neither Tech A not B
Answer:
c) Both Tech A and B
Explanation:
The Wheels of cars or vehicles are attached or fastened to the car rims using what we call lug nuts and wheel studs. The lug nuts attached or torqued properly on the wheel studs in order to ensure that the wheels of the car are well secured , attached and firm.
We have different types of lug nuts and wheel studs. The differences is based on the threading that it found on both the lug nut and wheel studs.
We have:
a) The right handed threaded lug nuts and studs(wheel studs)
b) The left handed threaded lug nuts and studs(wheel studs).
The right handed threaded lug nuts and studs are tightened when they are turned in the clockwise direction while left handed threaded lug nuts and studs are tightened in the anticlockwise or counterclockwise direction.
It is important to note that no matter the kind of lug nuts and studs(whether right handed threaded or left handed threaded) used to fastened wheels to car rims, it is essential that they are well fastened and torqued to car to prevent them from loosening up.
For the question above, both Tech A and Tech B are correct. Therefore , Option C is the correct option.
Describing Label Printing Options
What are some options when printing labels? Check all that apply.
random addresses
single label
handwritten label
full page of same label
Answers
Custom labels are printed using a variety of techniques in the label printing process. Some options when printing labels are Single label and Full page of same label.
What Is Label Printing?
Label printing is the process of creating personalized labels using different techniques. These techniques include wide-format printing, flexographic printing, and digital printing, all of which have an impact on how the label looks, feels, and serves its purpose.
Label Printing Today:
Flexographic printing has continued to advance and prosper up until the 1990s, when digital printing emerged as a brand-new method for producing labels. With the addition of inkjet technology, this process has advanced today, producing premium, full-color labels with a less time-consuming procedure and less waste.
To know more about Label Printing, visit: https://brainly.com/question/4676056
#SPJ9
Which of the following is a good way to find a research topic
A. Personal Experience
B. Getting an idea from an advisor
C. Looking for the next step in the research process
D. All of the above
I need the answer quickly giving brainliest to the first person who answers
Answers
Answer:
Im bored wanna talk?
Explanation:
A man is a network that is frequently used as links between office buildings that are located throughout a city.a. trueb. false
Answers
The statement "A MAN is a network that is frequently used as links between office buildings that are located throughout a city" is true (a).
The term "MAN" refers to a Metropolitan Area Network, which is a type of network designed to connect various office buildings, institutions, or facilities within a city or metropolitan area. This type of network allows for efficient communication and data sharing among the connected locations.
MANs enable efficient communication and data sharing among the connected locations, facilitating seamless connectivity and information exchange within a specific geographical area. As technology continues to advance, MANs play a crucial role in supporting communication and data transfer needs for businesses, organizations, and institutions operating within a metropolitan area. By providing connectivity between different locations, MANs contribute to the efficient functioning of urban areas and support the growth of businesses and institutions in the modern digital age.
Learn more about network: https://brainly.com/question/8118353
#SPJ11
consider the task of developing a reliable protocol. if we assume the crc code used is capable of detecting any errors (in our lifetime), we can implement reliability by tagging data packets and acknowledgments with sequence numbers. what is the minimum set of sequence numbers needed to implement reliability? explain briefly.
Answers
The minimum set of sequence numbers needed to implement reliability would be two - one for the data packets and one for the acknowledgments.
By tagging each data packet with a unique sequence number, we can ensure that the recipient can identify and keep track of the order in which the packets were sent. Similarly, by tagging each acknowledgment with a sequence number, the sender can confirm which packets were received successfully and which need to be resent. This tagging system helps to maintain the reliability of the protocol, even in the presence of errors that may be missed by the CRC code. With this approach, we can ensure that our protocol is able to handle any errors that may arise and deliver data packets accurately and efficiently.
learn more about data packets here:
https://brainly.com/question/14403686
#SPJ11
The sun has been up for several hours, and it has been shining on these trees.
What can the trees do because they are in sunlight? What does this mean for the number of energy storage molecules in the trees?
The trees can . . .
A. give off carbon to the air. Giving off carbon allows them to make energy storage molecules.
B. give off carbon to the air. Giving off carbon uses up energy storage molecules.
C. take in carbon from the air. The carbon is used to make energy storage molecules.
D. take in carbon from the air. The carbon is used to break down energy storage molecules.
Answers
For some hours now, the light has been beaming on these trees. Because they are in sunlight, The trees can "take in carbon from the air. The carbon is used to make energy storage molecules." (Option C).
What is the above process called?The above process is called Photosynthesis. Photosynthesis is the process through which plants convert sunlight, water, and carbon dioxide into oxygen and sugar energy.
Photosynthesis is the process through which plants and other organisms convert light energy into chemical energy, which is subsequently released to fuel the organism's activities through cellular respiration.
Photosynthesis has the following characteristics: It is a process that happens only in plants that have the green pigment chlorophyll, which is utilized to manufacture food. Sunlight, water, and oxygen are required, and two processes occur, one light-dependent and one light-independent.
Learn more about trees:
https://brainly.com/question/11076581
#SPJ1
assume a program takes 320 seconds to run using 1 thread. assuming perfect threading, how long would the program take to run using 8 cores?
Answers
Assuming perfect threading, the program should ideally take 1/8th of the time to run using 8 cores. This is because threading allows the program to be divided into smaller tasks that can be executed simultaneously by multiple cores.
So, each core can execute a separate task and complete it faster than a single core executing all the tasks sequentially. Therefore, the time taken by the program to run using 8 cores can be calculated by dividing the original time taken by the number of cores used. In this case, the program should take approximately 40 seconds to run using 8 cores, as 320 seconds divided by 8 cores is equal to 40 seconds.
However, it is important to note that perfect threading is not always possible, and there may be limitations to how much the program can be divided into smaller tasks. Additionally, other factors such as the memory bandwidth and cache size of the system can also impact the performance of the program.
Learn more about program here :-
https://brainly.com/question/30613605
#SPJ11
What humidity level should be maintained for computing equipment? a. 50 percent b. 40 percent c. 60 percent d. 30 percent
Answers
Answer:
A. 50 percent
Explanation:
The correct option is - A. 50 percent
Another preventive measure you can take is to maintain the relative humidity at around 50 percent. Be careful not to increase the humidity too far—to the point where moisture starts to condense on the equipment.
Imagine a piece of graph paper situated behind an image and think about how all the
tiny squares sit in proximity to one another. Next, imagine an invisible force behind
the grid pushing and pulling the little squares so they appear blown up or minimized
--what concept does this represent?
A. Manipulation
B. Watermarking
C. Image cropping
D. Imagine distortion
Answers
The scenario where qn invisible force behind the grid pushes the little squares so they appear blown up or minimized is known as C. Image cropping.
What is image cropping?It should be noted that image cropping simply means improving the framing and composition of an image.
It's the scenario where an invisible force behind the grid pushes the little squares so they appear blown up or minimize.
Learn more about image on:
https://brainly.com/question/26307469
What is output by the following code? Select all that apply.
c = 0
while (c < 11):
c = c + 6
print (c)
Group of answer choices
0
2
4
8
10
6
14
16
1
3
12
Answers
Answer:
6
12
Explanation:
c starts with value zero. When the while loop starts 6 is added to the value, so 0 + 6 = 6. then the value is printed on the screen. The while checks if 6 is less than 11, since it's true then the the loop executes again and more 6 is added to the previous value, so now the value is 12. The value is again printed. Then the while checks again if 12 is less than 11, since it's not, then the loop breaks there, and nothing more is printed. So if there is no line break, the printing should look like:
612
if there is a line break, then its:
6
12
You have a version control system installed. Several developers work with this system. A new developer wants to work on the code. What is the first task that the developer must perform
Answers
The first task that the developer must perform is to check out the existing code. A code developer can develop software and applications.
What is a code developer?A code developer, also known as a computer programmer or software developer, is a person that works by developing new software and applications.
Code developers write and also test computer codes in order to determine if they function in a proper manner.
Code developers play a fundamental role in the industry by developing instructions that computers can easily follow.
Learn more about software development here:
https://brainly.com/question/26135704
write java code that uses a for loop to print each element of an array named data that contains five primitive integers. for example, if your array contains the elements {14, 5, 27, -3, 2598}, then your code should produce output similar to this:
Answers
Explanation:
Here's an example Java code that uses a for loop to print each element of an array named `data` that contains five primitive integers:
```java
int[] data = {14, 5, 27, -3, 2598};
for (int i = 0; i < data.length; i++) {
System.out.println(data[i]);
}
```
The code initializes an array of integer values named `data` and then uses a for loop to iterate through each element of the array. The loop starts at index 0 and continues until it reaches the end of the array, which is represented by the `length` property of the array.
For each iteration of the loop, the code uses the index variable `i` to access the element at that index in the array (using the square bracket notation `data[i]`) and prints its value to the console using the `System.out.println()` method. This process repeats until all elements in the array have been printed.
what is a malicious program that can replicate and spread from computer to computer?
Answers
Answer:
A computer virus
Explanation:
Self-explanatory
What does it mean when the lottery machine says function suppressed after scanning a ticket
Answers
When a machine says function suppressed after scanning a ticket, it implies that you have won some certain amount.
What is lottery wins?This term connote that a person has a winning ticket in a lottery that is often owned by a government.
Note that if a winning ticket is scanned, the terminal often shows a message just for you and that suppress function implies that your the ticket has won something.
Learn more about lottery from
https://brainly.com/question/9216200
the basics of color theory assume what central tenets
Answers
Computers that are close to one another are connected to form a LAN
Answers
Explanation:
different computer are connected to a LAN by a cable and an interface card
Answer:
network is a group of computers (or a group of smaller networks) that are connected to each other by various means, so that they may communicate with each other. The internet is the largest network in the world.
what does the sap menu button do?
Answers
Note that the SAP menu button Shows all the transactions within SAP whether your have access or not.
What is the rationale for the above response?The SAP menu button, also known as the SAP Easy Access Menu, is a graphical user interface (GUI) tool that provides easy navigation to various SAP transactions and functions. When clicked, the SAP menu button opens a drop-down menu that displays a hierarchical list of SAP modules and sub-modules, including frequently used transactions and reports.
Users can navigate the SAP menu by clicking on the relevant modules and sub-modules, which then displays further options and transaction codes. This menu is customizable and can be tailored to suit specific user requirements.
In addition to the SAP menu button, users can also use the transaction code field to access specific SAP transactions directly. However, the SAP menu button is a useful tool for users who are not familiar with the transaction codes or who prefer a visual, hierarchical view of the SAP system.
Learn more about SAP at:
https://brainly.com/question/30457107
#SPJ1
Describe the Existing Control Design for this following Control Area: User Access Provisioning [e.g. For a new employee]
Answers
The existing control design for user access provisioning in the context of adding a new employee to the system includes several steps to ensure proper access is granted.
The process begins with HR notifying the IT department of a new employee's start date, role, and access requirements. IT then reviews the access needed and assigns appropriate permissions based on their job duties.
Next, IT sends an access request to the manager or supervisor for approval. Once approved, the access request is sent to the security team for final approval and implementation.
A log is maintained to track all access requests and approvals for auditing purposes.
This process helps to ensure that new employees have the appropriate access needed for their job duties while minimizing the risk of unauthorized access. It is important to regularly review and update access permissions to ensure ongoing compliance and security.
For more questions on control design
https://brainly.com/question/14581318
#SPJ11
the sysdate keyword cannot be included in the insert command, only the update command.T/F
Answers
Answer: False
Explanation:
The SYSDATE keyword can be used in both the INSERT and UPDATE commands in certain database systems, such as Oracle.
In an INSERT statement, the SYSDATE keyword can be used to insert the current date and time into a date column. For example:
INSERT INTO my_table (date_column) VALUES (SYSDATE);
In an UPDATE statement, the SYSDATE keyword can be used to update a date column with the current date and time. For example:
UPDATE my_table SET date_column = SYSDATE WHERE id = 1;
However, it's important to note that the availability of the SYSDATE keyword and its usage may vary depending on the specific database system being used.
Learn more about SYSDATE and UPDATE here:
https://brainly.com/question/2985058
#SPJ11
A solid weighs 20gf in air and 18gf in water .find the specific gravity of the solid
Answers
10
Explanation:Specific gravity (also called relative density) is the ratio of the density of an object (or substance) to the density of a reference substance (mostly water). It has no unit and is given by the following;
Specific gravity = \(\frac{density-of-object}{density-of-water}\)
Specific gravity is also given by the ratio of the weight of the object in air to the loss of weight of the object in water. i.e
Specific gravity = \(\frac{weight-of-object-in-air}{loss-of-weight-in-water}\) --------------(* * *)
In this case;
i. The object is the solid which has a weight of 20gf in air.
ii. The loss of weight of the solid in water is the difference between the weight in air (20gf) and the weight in water (18gf).
Therefore the loss of weight is
20gf - 18gf = 2gf
Now substitute these values from (i) and (ii) into equation (* * *) as follows;
Specific gravity = \(\frac{20gf}{2gf}\)
Specific gravity = 10
Therefore the specific gravity of the solid is 10
Carafano vs. MetroSplash (1-2 pages double spaced please)
Read the Carafano case and answer the following questions:
Question: What role did Matchmaker play in developing the content that was posted as a profile of Carafano?
Question: Was Matchmaker a content provider?
Question: Is Matchmaker liable?
Question: Why did Congress make ISPs immune from liability for material posted online by others under the Communications Decency Act?
Question: Can Carafano recover damages from anyone?
Question: A great deal of harm can be done very quickly on the Internet. Did Congress make the right policy decision when it passed the CDA?
Answers
In the Carafano vs. MetroSplash case, Matchmaker played a role in developing the content that was posted as a profile of Carafano. Matchmaker can be considered a content provider, and therefore, may be held liable. Congress made ISPs immune from liability for material posted online by others under the Communications Decency Act (CDA) to encourage free speech and innovation on the internet.
Carafano may be able to recover damages from Matchmaker if they can establish certain legal elements. While the internet can facilitate quick harm, the question of whether Congress made the right policy decision in passing the CDA is subjective and open to debate.
In the Carafano vs. MetroSplash case, Matchmaker played a role in developing the content that was posted as a profile of Carafano. Matchmaker provided the template for the profile, which was filled with information and images by its subscribers. This involvement suggests that Matchmaker acted as a content provider, contributing to the creation and dissemination of the content.
Considering Matchmaker's role as a content provider, the question of liability arises. Matchmaker may be held liable if it can be proven that the company knowingly or materially contributed to the unlawful or defamatory content. Liability would depend on the specific circumstances and evidence presented during the case.
Congress enacted the Communications Decency Act (CDA) to promote the growth of the internet and encourage free expression. One aspect of the CDA is Section 230, which grants immunity to internet service providers (ISPs) for content posted by others. The goal was to shield ISPs from liability and avoid potential chilling effects on internet speech and innovation. However, the CDA does not provide immunity for ISPs who actively participate in the development or creation of the content, potentially leaving room for liability.
Carafano may be able to recover damages from Matchmaker if they can establish certain legal elements, such as defamation, invasion of privacy, or intentional infliction of emotional distress. The outcome would depend on the specific facts of the case, the jurisdiction, and the application of relevant laws.
The question of whether Congress made the right policy decision in passing the CDA, considering the potential harm that can be done quickly on the internet, is subjective and open to debate. The CDA's immunity provisions have been criticized for potentially shielding platforms from responsibility for harmful or illegal content. On the other hand, the CDA's intent was to foster innovation and free speech online, providing a legal framework that balances the rights of internet users and service providers. The ongoing debate centers around finding the right balance between protecting individuals from harm and preserving the open nature of the internet.
Learn more about internet here: https://brainly.com/question/28347559
#SPJ11
hi good morning
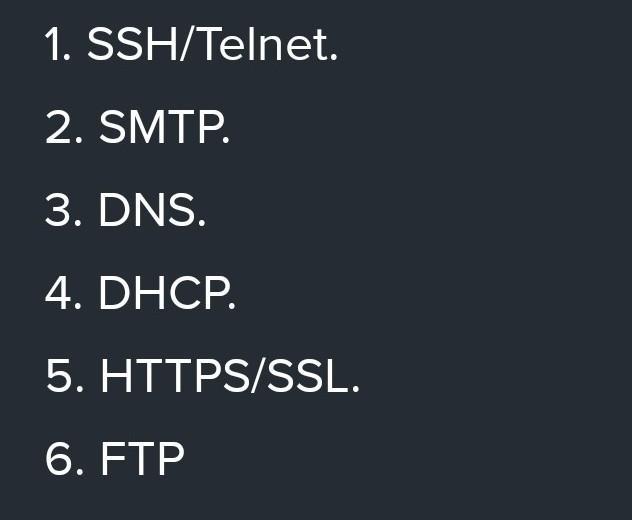
Type the name of the protocol for each protocol define on the table below
nonsense answers well be reported

Answers
Answer:
1. SSH/Telnet.
2. SMTP.
3. DNS.
4. DHCP.
5. HTTPS/SSL.
6. FTP
Explanation:
1. Provides connections to computers over a TCP/IP network: the standard protocol used for this is SSH/Telnet, through port number 22 and 23 respectively.
SSH is acronym for secure shell.
2. Sends e-mail over a TCP/IP network: SMTP using port number 25.
SMTP is an acronym for Simple Mail Transfer Protocol and it uses the standard port number of 25 to provide clients with requested services.
3. Translates URLs to IP address: DNS using port number 53.
A Domain Name System (DNS) can be defined as a naming database in which internet domain names (website URLs) are stored and translated into their respective internet protocol (IP) address. This simply means that, DNS is used to connect uniform resource locator (URL) or web address with their internet protocol (IP) address.
4. Automates assignment of IP address on a network: DHCP using port number 67.
Dynamic Host Configuration Protocol (DHCP) is a standard protocol that assigns IP address to users automatically from the DHCP server.
5. Securely transports web pages over a TCP/IP network: HTTPS/SSL using port number 443.
HTTPS is acronym for Hypertext Transfer Protocol Secure while SSL is acronym for Secure Sockets Layer (SSL).
6. Transports files over a TCP/IP network: FTP using port number 20 or 21.
FTP is an acronym for file transfer protocol.
Explanation:
I guess there is no need of mine for giving ans now
as the above guy has explained everything
Recursive functions are ________ iterative algorithms. as efficient as less efficient than more efficient than impossible to compare to
Answers
Based on computer programming, Recursive functions are less efficient than iterative algorithms.
Recursive Function vs. Iterative AlgorithmDuring implementation, the Recursive functions require the module to call itself multiple times till the base condition is satisfied, thereby making the line of codes longer and slower to execute.
In contrast, the Iterative algorithm utilizes looping statements such as for LOOP, WHILE LOOP, or DO-WHILE LOOP to repeat the same steps, thereby making the line of codes shorter and faster to execute.
Hence, in this case, it is concluded that the correct answer is "less efficient than."
Learn more about Recursive Functions here: https://brainly.com/question/25647517