A network engineer may?
Answers
Answer:
Network engineers design and implement network configurations, troubleshoot performance issues, carry out network monitoring and configure security systems such as firewalls.
Explanation:
Related Questions
+20 POINTS!!!~~~~~When adding delegates to his mailbox, which role should Joel use if he would like the user to be able to read and create items in a particular folder?
Editor
Publishing Editor
Author
Manager
Answers
Answer:
B) Publishing Editor
Explanation:
Joel should use the publishing editor tool. The correct option is B.
What is a mailbox?A mailbox is where electronic mail messages found on a remote server or downloaded to the user's hard drive are stored.
In this scenario, the role he should assign to the delegates is the publishing editor. This role grants them the ability to create, read, modify, and delete all items within a given folder, as well as create subfolders.
The other options listed either do not grant access to create/modify existing files or simply grant all of these rights to files created by the user but not to files already present in the folder. As a result, this would be the most appropriate role for Joel's goals.
To know more about mailbox follow
https://brainly.com/question/13276817
#SPJ6
Round spongy pads that act as shock absorbers in the spine are known as
intervertebral disks.
ballistic
tight hip flexor muscles
Answers
Intervertebral disks are round, spongy pads located between the vertebrae in the spine.
So, the correct answer is A.
They serve as shock absorbers, cushioning the impact of everyday movements such as walking, jumping, and bending.
These disks are made up of two parts: a tough outer layer and a soft, jelly-like center.
However, the disks can become damaged or degenerate over time, causing pain and discomfort.
One way to prevent this is by maintaining strong core muscles and good posture.
Tight hip flexor muscles can also contribute to lower back pain and can be improved through stretching and strengthening exercises.
Ballistic movements, or rapid, explosive movements, should be avoided as they can put excessive stress on the
Hence the answer of the question is A.
Learn more about intervertebral disks at
https://brainly.com/question/10232446
#SPJ11
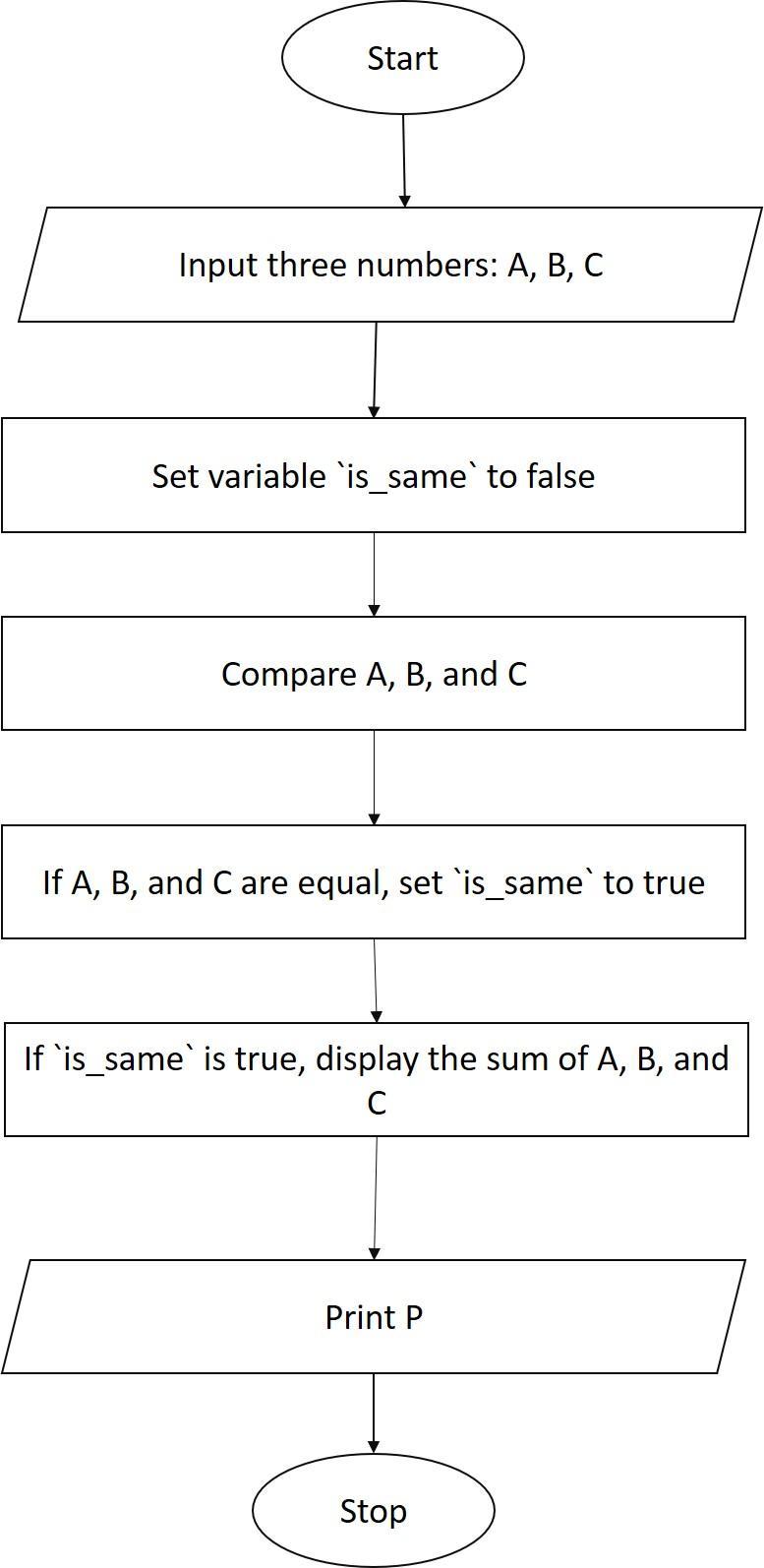
Draw the flowchart to accept three numbers check if they are same then display sum otherwise display product
Answers
The required flow chart is depcied as follows
Start
Input three numbers, A,B, and C
Compare A, B, and C
If A, B, and C are the same, then
Display the sum of A, B, and C
Else
Display the product of A, B, and C
End
What is the explanation for the above?The program starts by inputting three numbers, A, B, and C.
The program then compares A, B, and C.
If A, B, and C are the same, then the program displays the sum of A, B, and C.
Otherwise, the program displays the product of A, B, and C.
The program ends.
Learn more about Flow Chart at:
https://brainly.com/question/6532130
#SPJ1
Troy, an aspiring screenwriter, aspires to work with a famous director known for his philanthropic work. Troy gets an appointment with the director to present his idea for a video project. The director asks Troy to send him a synopsis of the video project. What should Troy include in the synopsis?
Answers
Troy should include a short overview of the story that his video will tell and why he wants to tell it (or what the video will be about and why). It should also include the target audience, and where the video will be published.
Answer: a brief description of the story
i hope i was able to answer your question
Explanation: passed the test with this answer
#PlatoUser
#PlatoStudentAnswers
Which of the following describes organizations that
self-regulate via feedback loops?
Group of answer choices
Cybernetics
Chaos Theory
Scientific Management
Classical Organization Theory
Answers
Organizations that self-regulate via feedback loops can be described as applying principles of cybernetics.
Cybernetics is a field that deals with systems and control processes, specifically focusing on the study of feedback loops and self-regulation. Organizations that employ self-regulation through feedback loops can be seen as applying cybernetic principles to their operations. In this context, feedback loops refer to the process of gathering information about a system's performance, comparing it to desired outcomes, and making necessary adjustments to achieve those outcomes.
By using feedback loops, organizations can monitor their activities, evaluate their performance, and make continuous improvements. Feedback loops involve collecting data, analyzing it, and using the insights gained to adjust behaviors, processes, or strategies. This iterative process enables organizations to adapt to changes, optimize their performance, and achieve desired outcomes.
In summary, organizations that self-regulate via feedback loops can be understood as implementing principles from cybernetics. They utilize feedback mechanisms to monitor and adjust their operations, aiming to improve performance and achieve their goals.
Learn more about Cybernetics here:
https://brainly.com/question/32095235
#SPJ11
Engineers at Edison Laboratories developed a _____ strip that allowed them to capture sequences of images on film.
kinetoscope
selenium
cotton
celluloid
Answers
Answer:
Celluloid
Explanation:
It is Sis
Complete the sentence.
A
is a device that connects one network with another
Answers
encapsulation allows you to control access to group of answer choices the data members of an object the member functions of an object the helper functions of an object the private members of an object
Answers
Encapsulation allows you to control access to the data members of an object.
What is encapsulation?
Encapsulation is the bundling of data only with methods that operate on that data, or the restriction of direct access to some of an object's components. Encapsulation is used to hide the values and state of a structured data object within a class, limiting direct access to them to clients in a way that could expose secret implementation details or violate state invariance provided by the methods.
Encapsulation is a technique for restricting direct access to some components of an object, so that users cannot get state values for all variables of a specific object. Encapsulation can be used to conceal either data members or data functions and methods associated with a class or object that has been instantiated.
So, A is the right answer.
To learn more about encapsulation
https://brainly.com/question/28482558
#SPJ4
Functions in Excel are grouped for easy reference. Locate the Insert Function button (Fx button) to bring up the Insert Function dialog box. How many different ways exist to look for a function
Answers
Following are the different ways that exist to look for a function,
Option 1: Insert function button (Fx button) on the Formulas ribbon.
Option 2 : More Functions from arrow near Auto sum icon on Home ribbon.
Option 3: Function Library on the Formulas ribbon.
Option 4: Shift + F3
Option 5: Enter = followed by first letter of the function.
What it does -
This function returns the number of whole working days between two dates with custom weekend parameters.
What it needs -
1. Start date, End date, Weekend (Optional), Holidays (Optional)
2. If start date later than end date, then value will be negative.
3. Enter date in specified format.
What is Excel?Excel uses a large collection of cells formatted to organize and manipulate data and solve mathematical functions.
Learn more about excel here,
https://brainly.com/question/21382498
#SPJ1
At the command prompt, type ls /etc/rc.d/init.d and press Enter. Which. UNIX SysV daemons are available on Fedora 28?
Answers
To find the available UNIX SysV daemons on Fedora 28, type ls /etc/rc.d/init.d and press Enter. It will show all the available daemons in the init.d directory.
In computing, a daemon is a background process that runs without an interactive user interface. It waits for a specific event or condition to occur and then responds appropriately. Daemons are frequently used to provide network services, such as web servers or file-sharing systems, as well as to manage system resources, such as printers or storage devices. Daemons are typically started at system boot time and run continuously until the system is shut down. UNIX SysV daemons are services or processes that are controlled by the UNIX System V init process, which is a common system initialization and management utility for UNIX-based operating systems such as Fedora 28. The init process starts and stops daemons based on a specified run level. Fedora 28 is a Linux-based operating system that uses Systemd as its system initialization and management utility. The /etc/rc.d/init.d directory contains scripts for System V init-compatible daemons, which are used to start and stop background services on the system. By typing ls /etc/rc.d/init.d at the command prompt and pressing Enter, you can see a list of available daemons on the system.Learn more about network services: https://brainly.com/question/901213
#SPJ11
Where would you find the Create Table Dialog box ?
Answers
Hope it’s right
Best luck with your studying
Answer:
From the Insert command tab, in the Tables group, click Table. NOTES: The Create Table dialog box appears, displaying the selected cell range.
Explanation:
Elige una metodología presentada en la lectura para aplicar la prospectiva (Método Delphi o Construcción de escenarios) y de manera gráfica represente cada metodología y sus fases.
Answers
Answer:
Método Delphi
Explanation:
El método Delphi es un método experto que se ha utilizado ampliamente en la investigación de futuros. En la actualidad, el método Delphi involucra típicamente de 15 a 40 expertos en dos o tres rondas.
La selección de un panel de expertos que represente de manera integral a las partes interesadas relevantes es un paso crucial en el estudio. La primera ronda, a menudo realizada a través de entrevistas, busca preguntas relevantes y motiva al panel a seguir trabajando. En la siguiente ronda, los panelistas evalúan las declaraciones prospectivas y justifican sus respuestas con diferentes perspectivas. Una característica clave del método es dar respuestas sin nombre, es decir, de forma anónima.
El método Delphi es especialmente adecuado para tratar un tema complejo o que cambia rápidamente, para el cual se pueden identificar expertos o partes interesadas (como ciertos grupos de población) u organizaciones (desarrollo tecnológico, problema social) que estén particularmente familiarizados con él.
El proceso Delphi produce una variedad de perspectivas, hipótesis y argumentos que se someten a pruebas y argumentaciones de expertos abiertos. El proceso busca filtrar las opiniones en opiniones de la comunidad compartidas o disidentes. Ambos resultados son valiosos. Puede haber desacuerdo no solo sobre los argumentos sino también sobre los objetivos, la probabilidad y la conveniencia de las alternativas.
Sans serif typeface is a good choice for
a. printed documents
b.document headings
c. document text
d. document content
Answers
Answer: A Sans-serif font is a good choice for headings and small text where clarity and readability are paramount. A Serif font is good to use on larger blocks of printed text like on a flyer.
Explanation:
4.7 Code Practice: Question 1

Answers
for x in range(20, 31):
print(x, end=" ")
I hope this helps!
The program prints all the integers from 20 up to and including 30 on the same line. The program written in python 3 goes thus :
for num in range(20,31):
#use a for statement to loop through all the integers between 20 and 30(inclusive)
print(num, end =' ')
#print each iterated value, followed by a space with the cursor remaining on the same line.
A sample run of the program is attached.
Learn more :https://brainly.com/question/18855444

who is known as the first computer programmer
Answers
Answer:
Ada Lovelace
Explanation:
English mathematician Ada Lovelace, the daughter of poet Lord Byron, has been called "the first computer programmer" for writing an algorithm for a computing machine in the mid-1800s.
Answer:
i think its ada lovelalce
Using more than one array to store related data is called _____________ arrays.
Answers
Answer:
Using more than one array to store related data is called parallel arrays.
Explanation:
I just did it and got 100% on the quiz
Using more than one array to store related data is called parallel arrays.
What is array?An array is a type of data structure used in computer science that holds a set of elements that are all uniquely recognised by at least one array index or key.
An array is stored in a way that allows a mathematical formula to determine each element's position given its index tuple.
In parallel arrays, a collection of data is represented by two or more arrays, where each corresponding array index represents a field that matches a particular record.
For instance, the array items at names and ages would explain the name and age of the third person if there were two arrays, one for names and one for ages.
Thus, the answer is parallel array.
For more details regarding parallel array, visit:
https://brainly.com/question/27041014
#SPJ6
3.19 lab: convert from seconds people find it easier to read time in hours, minutes, and seconds rather than just seconds. write a program that reads in seconds as input, and outputs the time in hours, minutes, and seconds. ex: if the input is: 4000 the output is: hours: 1 minutes: 6 seconds: 40
Answers
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
seconds = int(input("Enter time in seconds: "))
hours = int(seconds / 3600)
minutes = int((seconds - (hours * 3600)) / 60)
seconds = seconds - ((hours * 3600) + (minutes * 60))
print("{} hour(s) {} minute(s) {} second(s)".format(hours, minutes, seconds))
*The code is in Python.
Ask the user to enter the time in seconds
Calculate the hours, divide the seconds by 3600 and cast it to the integer
Calculate the minutes, subtract the corresponding seconds in hours you previously found, divide it by 60 and cast the result to the integer
Calculate the seconds, subtract the corresponding seconds in hours and minutes you previously found, the remaining is the seconds you have
Print the hours, minutes, and seconds
Learn more about print here-
https://brainly.com/question/14668983
#SPJ4
is cheque money? give reason
Answers
Answer:
Cheque is not money. cheque is a paper instructing the bank to pay a specific amount from the person's account to the person in whose name the cheque has been drawn. The facility of cheque against demand deposits makes it possible to directly settle the payments without the use of withdrawal.
Explanation:
True/False: Python does not allow the input of multiple values with a single statement.
Answers
The statement "Python does not allow the input of multiple values with a single statement." is False.
Python allows the input of multiple values with a single statement using various techniques. One common method is to use the `input()` function along with the `split()` method to separate the values based on a delimiter (such as space or comma).
Here's an example:
# Inputting multiple values separated by space
values = input("Enter multiple values: ").split()
# Inputting multiple values separated by comma
values = input("Enter multiple values: ").split(',')
# Inputting multiple integer values separated by space
values = list(map(int, input("Enter multiple values: ").split()))
Learn more about Python function here:
https://brainly.com/question/30629544
#SPJ4
Worldwide, the device that most people use to connect to the internet is the ___.
Answers
Worldwide, the device that most people use to connect to the internet is the Modem
What is a modem used for?
The sole ambition of the modem is to provide you with internet access. If you were to only have one internet-connected machine with an Ethernet port (such as a desktop computer), you could attach the modem directly to your computer with no need for a router.
What's the difference between a modem and a router?Your modem is a box that attaches your home network to the wider Internet. A router is a box that lets all of your wired and wireless machines use that Internet connection at once and also allows them to talk to one another without including to do so over the Internet.
To learn more about Modem, refer
https://brainly.com/question/23625215
#SPJ4
which of the software engineering characteristics do you most identify with? why do you connect most with those characteristics?
Answers
I most identify with the characteristic of creativity.
What is software engineering?
Software engineering is the application of engineering principles and techniques to the design, development, and maintenance of software systems. It is the process of creating and maintaining large, complex, and high-quality software systems. It involves planning, designing, coding, testing, and verifying software to ensure that it meets the user requirements and is reliable, secure, and efficient. Software engineering also involves managing the entire software development process, from requirements gathering to product design and implementation.
Characteristics of software engineering:
Creativity: Creative thinking is a key component of software engineering. It is essential for coming up with unique and powerful solutions to complex software problems.
Problem-solving: Software engineers must be able to identify problems and develop solutions to them. They must be able to assess the complexity of a problem and develop an efficient and effective solution.
Collaboration: Software engineering often involves working with other engineers, designers, and stakeholders to develop software. Collaboration is a key component of software engineering as it allows multiple minds to work together to come up with the best solution to a problem.
Communication: Effective communication is essential for software engineering. Software engineers must be able to explain their ideas and collaborate with other engineers and stakeholders to ensure that everyone is on the same page.
Attention to detail: Software engineers must pay attention to the smallest details of their software. They must be able to identify potential issues and find ways to fix them.
Time management: Software engineering often requires software engineers to manage their time effectively in order to ensure that projects are completed on time.
Software engineering is a complex field that requires a variety of skills. .As an engineer, I believe that creativity is essential in finding innovative solutions to complex problems. I also appreciate the importance of taking a creative approach when designing new products or services that meet the needs of users. I believe that creative thinking is a key component of software engineering and is essential for coming up with unique and powerful solutions.
Learn more about Software engineering from the given link:
https://brainly.com/question/7145033
#SPJ4
What are the five generations of computers?
Answers
Answer:
First Generation, Second Generation, Third Generation, Fourth Generation, Fifth Generation
Explanation:
First Generation- Vacuum Tubes
Second Generation- Transistors
Third Generation- Integrated Circuits
Fourth Generation- Microprocessors
Fifth Generation- Artificial Intelligence
evaluate the extent to which technology transformed the us economy in the period from 1865 to 1898 dbq
Answers
Between 1865 and 1898, the US underwent a fast shift fueled by technology.
the creation of electricitybuilding of railroadsthe typewriter and many pieces of equipment.What is American technology?The American people have become more dependent on technology as a result of these advancements.This was because certain machinery was quicker and more productive than people.Due to the usage of technology, more Americans migrated into the manufacturing industry as well.American Technology is any proprietary commercial and technical information about American's operations and company, including but not limited to American's A/C, and any of its derivatives. It is sometimes said that technology is the changing and manipulating of the human environment. Technology is the application of scientific knowledge to the practical goals of human life.To learn more about american technology, refer to:
https://brainly.com/question/12947584
Please help!
I own a SanDisk flash drive, and I want to download pictures on it so I can plug into my tv and use them for art references, but when I put the flash drive into my tv, and when I clicked on an image, it say that, "the files are unsupported."
Any idea what that means, and how I can fix it?
Thanks!
Answers
If the SanDisk flash drive does not support your file images, the TV would not support the images of the file. Use another device to open images.
What is a flash drive?A USB flash drive can be used to launch an operating system from a bootable USB, store crucial files and data backups, transport preferred settings or programs, perform diagnostics to diagnose computer issues, and more.
The drives are compatible with a wide range of BIOS boot ROMs, Linux, MacOS, and Microsoft Windows.
Therefore, your file's photos would not be supported on the TV if the SanDisk flash drive could not read them. To view photos, switch to another device.
To learn more about flash drive, refer to the link:
https://brainly.com/question/30032318
#SPJ1
This is an example of what type of formula? =average(d1:d17) question 1 options: addition subtraction range average
Answers
Answer:
d average
Explanation:
The average is the ratio of the sum of the observation to the total number of observations. Then the correct option is D.
What is average?Average is simply defined as the mean of the given set of numbers. The mean is considered as one of the measures of central tendencies in statistics. The average is said to be an arithmetic mean.
The average is given as
\(\rm Average = \dfrac{Sum\ of\ the\ observation}{Total\ number\ of \ observations}\)
This is an example of the average formula.
More about the average link is given below.
https://brainly.com/question/521501
ASAP
There are two competing scientific theories that try to explain the illusion of animation. Which of these answers is NOT one of the competing theories?
Persistence of Vision
Image-permanence
Phi Phenomenon
The first who answers correct will get brainlest and those that are incorrected will be marked with a red flag.
Answers
Write a program that hardcodes a proposed password and checks that it is an acceptable password.
If the proposed password is acceptable password, the program writes a message "Password zzzzzzzzz is acceptable" and ends.
If it is not acceptable, it writes a message "Password is acceptable because it "
Where
is the password which was checked.
is one of:
"is not at least 7 characters long."
"does not contain both upper and lower case alphabetic characters."
"does not contain at least 1 digit."
is used if the PW is not acceptable, else the word not isn't printed.
"is an acceptable password."
Acceptable passwords:
are at least 7 characters long.
contain both upper and lower case alphabetic characters.
contain at least 1 digit.
The logic of this program can be quite tricky. Hint: use toUpperCase(), toLowerCase, and equals(). You will also need nested ifs.
Here some sample runs of the program; your output should look substantially the same:
C:\>java PasswordChecker
Enter your password:
snowflake
Password snowflake is not acceptable because it does not contain both upper and lower case alphabetic characters."
Enter your password:
SnowFlake
Answers
Using the knowledge in computational language in JAVA it is possible to write the code that write a program that hardcodes a proposed password and checks that it is an acceptable password.
Writting the code:
class InvalidPasswordException extends Exception {
int passwordConditionViolated = 0;
public InvalidPasswordException(int conditionViolated)
{
super("Invalid Password: ");
passwordConditionViolated = conditionViolated;
}
public String printMessage()
{
switch (passwordConditionViolated) {
case 1:
return ("Password length should be"
+ " between 8 to 15 characters");
case 2:
return ("Password should not"
+ " contain any space");
case 3:
return ("Password should contain"
+ " at least one digit(0-9)");
case 4:
return ("Password should contain at "
+ "least one special character");
case 5:
return ("Password should contain at"
+ " least one uppercase letter(A-Z)");
case 6:
return ("Password should contain at"
+ " least one lowercase letter(a-z)");
}
return ("");
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Which of the following IP addresses ranges is reserved for Automatic Private IP Addressing?
a)169.254.0.1 - 169.254.255.254
b)255.255.0.0 169.254.0.0
c)121265594/525
d)None of these
Answers
The IP addresses ranges is reserved for Automatic Private IP AddressingThe correct answer is (a) 169.254.0.1 - 169.254.255.254.
The Automatic Private IP Addressing (APIPA) is a method that enables computers to self-assign IP addresses without the use of a DHCP server. When a computer is not able to obtain an IP address from a DHCP server, APIPA assigns an IP address that is within a reserved range of IP addresses.APIPA automatically assigns the following range of IP addresses:169.254.0.1 – 169.254.255.254.
IP addresses that fall outside the range of APIPA are considered to be valid, global IP addresses, so none of the other options are reserved for Automatic Private IP Addressing.255.255.0.0 169.254.0.0 is an invalid address as it contains a subnet mask and a default gateway.121265594/525 is not a valid IP address as it is not within any of the three classes of IP addresses.Hence, option (a) 169.254.0.1 - 169.254.255.254 is the only range of IP addresses reserved for Automatic Private IP Addressing.
Learn more about IP addresses: https://brainly.com/question/14219853
#SPJ11
Which term refers to an HPE B-Series routing configuration, similar to a fibre channel zone, where shared devices in different fabrics are identified and replicated so that they can communicate across this distinct fabrics?IFRVSANFSPFLSAN39.Which optional, licensed HPE C-Series SAN switch feature enables you to configure devices in one VSAN to access devices in another VSAN?IFRFSPFIRFIVR
Answers
IFR and IVR technology refer to an HPE B-Series routing configuration that resembles a fibre channel zone and allows for the identification and replication of shared devices across several fabrics.
IVR, or interactive voice response, is a type of automated phone system that allows callers to interact with pre-recorded messages or text-to-speech technology through a dual-tone multi-frequency (DTMF) interface and offer and access information without the need for a human agent.
Because the pilot only utilises the navigational instruments in the cockpit, instrument flying gets its name. It takes an instrument rating and an IFR flight plan to fly in IMC (flying in the clouds).
Without external references, flying by instruments looks dangerous, but with the correct training, it's really quite safe.
Frequently used in contact centres, interactive voice response (IVR) is a type of telecommunication software. Through a sequence of automated menus known as IVR, businesses may communicate with customers and frequently provide them the option to self-serve for quicker response.
Learn more about Technology here:
https://brainly.com/question/15059972
#SPJ4
Please help!!!! 100 points!!

Answers
Answer:
I DONT GET IT
Explanation:
I was also looking for an answer for the same question lo