a python int can represent indefinitely large numbers. group of answer choices true false
Answers
The statement "a python int can represent indefinitely large numbers" is not true is because in Python, like any other programming language, there is a limit to the maximum value an int can represent, and it depends on the amount of memory available on the system
.Here's an example:```pythonx = 10**1000print(x)```
The output of the above code is a SyntaxError: "integer literal too large to be represented in a 'int'."
In Python, the maximum value that an int can represent is determined by the maximum size of an integer, which varies from system to system. On most systems, the maximum size of an integer is 2^31-1 or 2^63-1, depending on whether the system is 32-bit or 64-bit.The
Learn more about Python at:
https://brainly.com/question/31055701
#SPJ11
Related Questions
Select the correct answer.
What helps the project team to identify the latest software build?
A.
defect
B.
version number
C.
test plan
D.
test environment
E.
hardware
Answers
Answer:
B version number
Explanation:
Leroy wants to keep the bride and groom in a picture, but remove the rest of the family. Which photo-editing tool should Leroy use?
Answers
Answer:
He can use Ms paint, Adobe photoshop, Picasa etc.
The photo-editing tool should Leroy use are Ms paint, Adobe photoshop, or Picasa.
What is photo editing tool?
The tool used for editing pictures clicked by the phone or shooting cameras.
Leroy wants to keep the bride and groom in a picture, but remove the rest of the family.
Leroy should use the photo editing tool for the same. The tools popularly used for the purpose are Ms paint, Adobe photoshop, or Picasa.
Thus, the photo-editing tool should Leroy use are Ms paint, Adobe photoshop, or Picasa.
Learn more about photo editing tool.
https://brainly.com/question/14800338
#SPJ2
Ask the user to enter a name. If there is an ‘a’ in the name, print the message saying ‘The name contains at least one ‘a.’ If there is no ‘a’ then print “The name does not contain the letter a.”
Answers
name = input("Enter your name: ")
if "a" in name:
print("There's at least one 'a'")
else:
print("The name does not contain the letter a.")
I wrote my code in python 3.8. I hope this helps!
How do milestones help a project manager ensure that a project goes smoothly
Answers
Answer: I think milestones, or goals, help everyone not to get overwhelmed by the projects end. Milestones help everyone focus on little goals they can reach, so you slowly but surely make it to the end of your project. Hope this helps! Please let me know if I'm wrong.
The milestones help a project manager ensure that a project goes smoothly by showing whether the project is progressing as planned. Thus, option A is correct.
What is the main role of project manager?The main role of the project manager is that it basically assisting the project managers by coordinating, as well as analyzing and the planning the specific project.
The main responsibility of the assistant project managers has to supporting the given function of the project and to execute the given project.
According to the given question, a typical project office is basically responsible for managing the large projects which include both the project manager and the assistant project managers.
Therefore, the duty of project manager is to ensure that a project goes smoothly by showing whether the project is progressing as planned. Thus, option C is correct.
Learn more about project manager on:
https://brainly.com/question/15404120
#SPJ7
The question seems to be incomplete, the complete part may be:
How do milestones help a project manager ensure that a project goes smoothly?
A. By showing whether the project is progressing as planned
B. By showing whether the project is being monitored appropriately
C. By indicating whether the right team members have been given the right tasks
D. By indicating whether the project plan needs to be changed
Sophia wants to purchase and use a mat board that will be the safest option for long-term use. What would likely be the BEST option for her?
A. Installation board
B. velveteen mat board
OC. acid-soaked board
OD. archival rag board
Answers
The most likely best option for Sophia is installation board is Installation board.
What can I use in place of a mat board?An alternative forms of matboard is Scrapbooking papers as it is made up of a wide range of options that one can be able to see at any craft store.
Therefore, the most likely best option for Sophia is installation board is Installation board. as it is the best option.
Learn more about board from
https://brainly.com/question/5016185
#SPJ1
Answer:
archival rag board
Explanation:
I just took it and this is the correct answer
PLEASE HELP 15 POINTS Emma plans on building a dog house using an algorithm. What will be the final step of the process? a) creating a blueprint b) building the roof c) thinking about what went wrong d) applying her algorithm to build a deck
Answers
Answer:
Most likely C
Explanation:
Blueprint is the plan so she makes it 1st.
Building the roof is after the deck.
The deck is after the blueprint.
After it's all done she looks at it and thinks about what went wrong at then end.
If there are no mistakes it's B.
Hope this answers your question :).
What are the uses of DVD Ram
Answers
Answer:
Like ordinary random access memory (RAM), it can be repeatedly read, written to, and erased. Intended mostly for removable computer storage, DVD-RAM provides the capabilities of Rewriteable CD (CD-RW) - users can run programs from the discs, copy files to them and rewrite or delete them.
What was the name of the first computer, developed by charles babbage?.
Answers
Answer: Analytical Engine
Explanation:
Answer:
analytical engine - 1837
Which of the following keys are typically escrowed?
A) Digital signature/non-repudiation
B) Authentication
C) Encipherment
Answers
The digital signature/non-repudiation key and the encipherment key are the ones that are escrowed.
Escrowed keys are keys that are kept by a trusted third party, such as a government agency or a specialized service provider. These keys are typically used for purposes such as law enforcement investigations or to recover encrypted data in case of a disaster or a lost key.
The digital signature/non-repudiation key is often escrowed because it is crucial for verifying the authenticity and integrity of digital documents or transactions, and for preventing disputes over their validity. In case of a dispute or a legal challenge, the escrowed key can be used to provide proof of the document's origin and contents.
The encipherment key, on the other hand, is typically escrowed because it is used to encrypt sensitive data, such as financial transactions, health records, or government secrets. If the key is lost or stolen, the data may become inaccessible or compromised. Escrowing the key allows for a backup copy to be stored securely, and for authorized parties to access the data when needed.
The authentication key, which is used for verifying the identity of users or systems, is less commonly escrowed, as it is usually tied to specific hardware or software configurations that cannot be easily replicated or shared. However, in some cases, such as high-security environments or critical infrastructure, authentication keys may also be escrowed as a precautionary measure.
Learn more about digital signature: https://brainly.com/question/20463764
#SPJ11
Which concept allows the computer to repeat a group of steps in an
algorithm?
OA. Iteration
OB. Storage
OC. Sequencing
OD. Selection
Answers
OD. Selection concept allows the computer to repeat a group of steps in an algorithm .
What is algorithm
An algorithm is a set of instructions that can be used to solve a problem or accomplish a task. It is a step-by-step process that takes an input and produces an output. Algorithms are used in many areas including mathematics, computer science, and data science. To be effective, an algorithm must be well-defined and complete, meaning that all instructions must be clearly stated and complete. It should be efficient, meaning that it uses the minimum amount of resources and time to accomplish a task; and it should be accurate, meaning that it produces the correct result. Algorithms are also often tested for their correctness and performance.
To know more about algorithm
https://brainly.com/question/22984934
#SPJ4
Answer: A. Iteration
Explanation:

The biggest impact of computers and computing is ?
1.) in the past
2.)in the future
3.)right now
Answers
The biggest impact of computers and computing is in the future. Thus, the correct option is 2.
What is the effect of computing?Computers have supplied the infinite resources for learning and made education more flexible with time and easy to access to people all over the world. Through computing, students can now gain knowledge and information not only from their classroom assignments and libraries but also from the available online resources as this contains knowledge about everything.
Computing has made things easier for people such as research work, education, artificial intelligence, machine learning, etc. One of the biggest impact of computers and computing is in the future times.
Therefore, the correct option is 2.
Learn more about Computing here:
https://brainly.com/question/21080395
#SPJ2
what is concurrency control and why does a dbms need a concurrency control facility?
Answers
Concurrency control controls concurrent access to a database in a database management system (DBMS). Additionally, it serializes transactions for backup and recovery and stops two users from modifying the same record at the same time.
What is Concurrency control?Concurrency control in information technology and computer science ensures that accurate results for concurrent processes are obtained while acquiring those results as soon as feasible, particularly in the domains of computer programming, operating systems, multiprocessors, and databases. Computer systems are made up of modules, or components, both in the hardware and software. Each part is intended to function properly, that is, to adhere to or satisfy a set of consistency rules. A given component's consistency may be broken by another component when concurrently running components communicate via messaging or share accessed data (in memory or storage). Concurrency control as a whole offers guidelines, techniques, design approaches, and theories to preserve the consistency of parts that operate concurrently and interact, and thereby the consistency and accuracy of the entire system.
To know more about Concurrency control visit:
https://brainly.com/question/14209825
#SPJ1
Decimal To Binary Conversion
128 64 32 16 8 4 2 1 = 255
_1____1____1____0___1__ 1__1___0_________ 238
_0____0____1____0___0___0__1___0_________ 34
1._________________________________________ 96
2._________________________________________ 63
3._________________________________________ 210
4._________________________________________ 193
5._________________________________________ 207
Binary To Decimal Conversion
128 64 32 16 8 4 2 1 = 255
1 0 0 1 0 0 1 0 = 146
0 1 1 1 0 1 1 1 = 119
1 1 1 1 1 1 1 1 = 6. _______
1 1 0 0 0 1 0 1 = 7. _______
1 1 0 1 0 1 1 0 = 8. _______
0 0 0 1 0 0 1 1 = 9. _______
1 0 0 0 1 0 0 1 = 10._______
Address Class Identification
Address Class
10.250.1.1 ___A__
150.10.15.0 ___B__
11. 172.14.2.0 _____
12. 198.17.9.1 _____
13. 123.42.1.1 _____
14. 127.8.156.0 _____
15. 191.200.23.1 _____
Network Addresses
Using the IP address and subnet mask shown write out the network address:
188.10.18.2 ______188.10.0.0_____________________
255.255.0.0
10.10.48.80 ______10.10.48.0_____________________
255.255.255.0
16. 192.149.24.191 _____________________________
255.255.255.0
17. 150.203.23.19 _____________________________
255.255.0.0
18. 10.10.10.10 _____________________________
255.0.0.0
19. 199.13.23.110 _____________________________
255.255.255.0
20. 203.69.230.250 _____________________________
255.255.0.0
Answers
Divide a decimal number by 10. Subtract 2 from this number (2 is base of binary so divisor here). Keep the rest in an array (it will be either 0 or 1 because of divisor 2). TillIf the sum is more than zero, repeat the first two steps.
How are 0.75 converted to binary?Similar to this, when writing a number between 0 and 1 in binary, powers of 12 are used rather than powers of 2. As an illustration, 0.75=12+14=1121+1122 The binary equivalent of the decimal value 0.75 is 0.11 (binary).
How is 1 represented in binary?Binary 1 is 1. In a binary number system, we only need the digits 2 to express a number, in contrast to the decimal number system where we utilise the digits 0 to 9.
To know more about binary visit:-
https://brainly.com/question/19802955
#SPJ4
What happens when you change just ONE character in your input string?
Answers
which digits are used in digital computer?
Answers
Answer:
binary digits i.e. 0s and 1s
what are the answers for theses question?




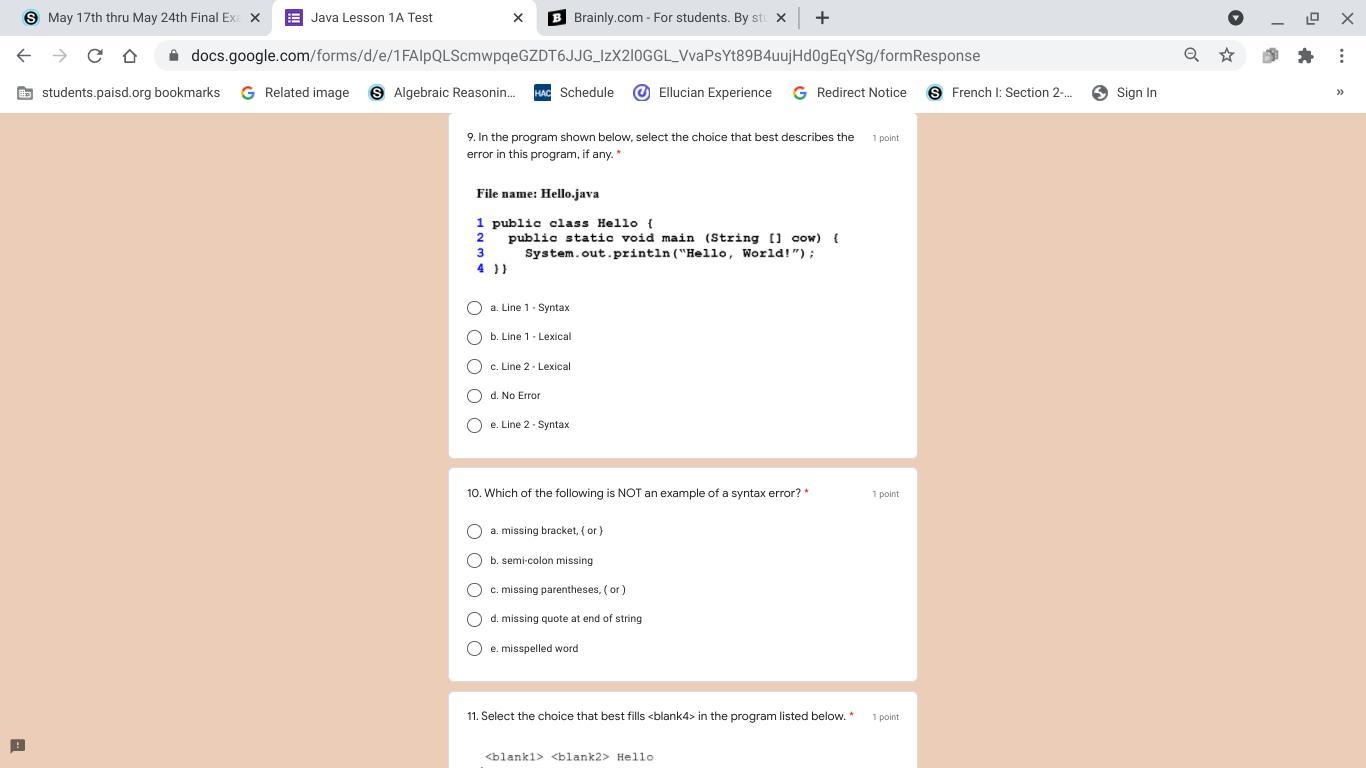
Answers
Answer: me no comprende coding
Explanation:
sorry
(50 points) The discipline of computer science focuses on software programming. It includes learning how to develop application software, expert systems, artificial intelligence (AI), websites, embedded coding, and robotics.
A. True
B. False
Answers
in a basic program with 3 IF statements, there will always be _________ END IIF's.
a)2
b)3
c)4
Answers
Answer:
c)4
Explanation:
Hope it could helps you
You are the IT Administrator for the CorpNet.local domain. You are in the process of implementing a group strategy for your network. You have decided to create global groups as shadow groups for specific departments in your organization. Each global group will contain all users in the corresponding department. In this lab, your task is to: Create the following global security groups on the CorpDC server in their corresponding OUs: OU Creation Location New Group Name Accounting Accounting Research-Dev Research-Dev Sales Sales
Answers
Answer:
1. Select Tools then Active Directory Users from the Server Manager
2. Navigate to the relevant Organizational Unit, OU, in the Active Directory
3. Select New then Group in the OU in which a global securities group is to be created
4. The group name (Accounting, Research-Dev, or Sales) is entered into the Group name field
5. Select the scope of the group
6. The group type is then selected (Domain Local, Global, or Universal)
7. The user accounts are then added to the group as follows;
i) Selecting the Add to a group option after right clicking a user account
ii) Enter the name of the appropriate group in the field to Enter the object names to select
iii) A group scope and group type is then selected
iv) Click on Check names
v) Other users can be added to the group by repeating steps i), ii), iii), and iv)
8) To add additional users to the group, the step 6, 7, and 8 is to be repeated
Explanation:
Why is it important to back up files?
Question 4 options:
It prevents phishing.
It prevents identity theft.
It will help restore files in case of online shaming.
It will help restore files in case of a computer virus.
Answers
Answer:
it will help restore files in the event of a computer virus <3
Explanation:
restoring damaged files is what backups are for. although the original files are lost, you can restore them and the problem is fixed.
ph*shing {have to censor} is mainly through manipulation, and having a duplicate file containing your P.I. will not reverse the fact that it is out to the public.
identity theft won't be PREVENTED. nuff said
A shorthand method consists of a symbol of the element surrounded by dots?.
Answers
Answer:
Since it is falling freely, the only force on it is its weight, w. w = m ⋅ g = 1000kg ⋅ 9.8m s2 = 9800N To draw a Free Body Diagram, draw an elevator cage (I am sure you would get lots of points for drawing it with intricate detail) with a downward force of 9800 N. I hope this helps,
Explanation:
A website design can be rated as acceptable if it enables the site to fulfill its purpose and also
does not contain any broken, mislabeled, or misdirected hyperlinks.
contains a link to the site map on the main navigation menu.
meets audience expectations for navigation, layout, and readability.
implements a site search feature in addition to a main navigation menu.
Answers
Answer:
does not contain any broken, mislabeled, or misdirected hyperlinks.
Explanation:
All the other answers don't make sense, you are not looking to meet the audiences needs, you want to make sure the website is good enough to be considered acceptable, I only see this answer as possible.
Answer:
(A) does not contain any broken, mislabeled, or misdirected hyperlinks.
after developing your website, tweaking it so it looks exactly the way you want, and testing it to ensure everything works as expected, how can you make it available for other people to access it?
Answers
To make your website available for others to access, you need to host it on a web server. Purchase a domain name, choose a web hosting service, upload your website files to the server, and configure the domain to point to the server's IP address.
1. Purchase a domain name: Choose and register a unique domain name for your website.
2. Choose a web hosting service: Select a hosting provider that suits your needs and purchase a hosting plan.
3. Upload website files: Use FTP or a hosting provider's control panel to upload your website files to the server.
4. Configure domain: Set up the domain to point to the server's IP address through the domain registrar's control panel.
5. DNS propagation: Wait for DNS propagation to complete, which can take up to 48 hours, before the website becomes accessible globally.
Learn more about IP address here:
https://brainly.com/question/31171474
#SPJ11
the default case must be specified in a switch statement. T/F?
Answers
In a switch statement, is it necessary to specify the default case. Yes, it is.
The switch statement is a type of conditional statement that allows the code to choose between many alternatives, and it is used when we have several options to choose from. If none of the other options is a match, we use the default case.The syntax for the switch statement is as follows:
```switch(expression)
{case constant-expression : statements; break;
case constant-expression : statements; break;
default : statements;}```
The switch statement works by comparing the expression provided in parentheses to each of the values stated in the case statements. The code in the appropriate case is executed if a match is discovered. If there is no match, the default case code is executed.
We should have a default case in our switch statements because it will execute when none of the other cases match. It's because the switch statement needs to cover all possibilities. Therefore, in switch statements, it is necessary to specify a default case. TRUE
Know more about the switch statement
https://brainly.com/question/33324074
#SPJ11
If button1 is a JButton object, which of the following statements will make its background blue? a. button1.setBackground(Color.blue); b. button1.setBackground(Color.BLUE); c. button1.setBackground(Color.BLUE); d. button1.setBackground(blue);
Answers
The correct statement to make the background of button1 blue is: a. button1.setBackground(Color.blue);
In Java, colors are represented as objects of the Color class, and the setBackground() method of the JButton class is used to set the background color of a button.
The color blue is one of the predefined colors in the Color class, and it is represented by the constant Color.blue. The correct way to set the background color of button1 to blue is to call the setBackground() method and pass in Color.blue as the argument, as shown in option a.
Option b is also correct since Color.BLUE is another constant in the Color class that represents the color blue, but with uppercase letters. Option c is incorrect because it uses the constant Color.BLUE with lowercase letters, which is not a valid syntax in Java. Option d is incorrect because blue is not a valid color in Java, and it would result in a compilation error.
Learn more about background here:
https://brainly.com/question/30114468
#SPJ11
which protocol is by far the most common type of session on a typical tcp/ip network?
Answers
The most common protocol for session on a typical TCP/IP network is the Transmission Control Protocol (TCP).
TCP is a connection-oriented protocol that ensures reliable transmission of data between devices on the network. It is used for many applications, including web browsing, email, file transfers, and more. TCP breaks data into packets and reassembles them at the receiving end, ensuring that all packets are received and in the correct order. Overall, TCP is essential for maintaining a stable and efficient network communication.
Learn more about TCP/IP network:
brainly.com/question/30831123
#SPJ11
you are given two sequences a and b of n numbers each, possibly containing duplicates. describe an efficient algorithm for determining if a and b contain the same set of numbers, possibly in different orders. what is the running time of this algorithm?
Answers
Given are two sequences, S1 and S2, both with n items and possibly including duplicates. Efficient algorithm would be extremely wasteful to compare two sets of sequences if they were in some random order.
"A collection of finite rules or instructions to be followed in calculations or other problem-solving procedures" is what the word algorithm signifies. Or, "A finite-step process for solving a mathematical problem that frequently uses recursive operations."
As a result, an algorithm is a set of limited procedures used to solve a certain problem. Depending on what you want to do, algorithms might range from simple to sophisticated.
By using the process of making a novel recipe as an example, it can be understood. When following a new recipe, one must read the directions and carry out each step in the correct order. The new meal is cooked to perfection as a result of this procedures.
You employ algorithms every time you use a phone, computer, laptop, or calculator. Similar to this, algorithms assist programmers in carrying out tasks to produce desired results. The developed algorithm is language-independent, meaning that it consists only of simple instructions that can be used to build it in any language and still produce the desired results.
To know more about algorithm click on the link:
https://brainly.com/question/22984934
#SPJ4
Which online note-taking device allows students to clip a page from a website and reuse it later?
web clipping tools
electronic sticky notes
offline data storage sites
online data storage sites
Answers
Answer:
The answer is A.) web clipping tools.
Explanation:
Cuz like yeah
Answer: WEB CLIPPING TOOLS
Explanation:
there are no loops in the agile life cycle. that would defeat the purpose of agile - to get quickly from start to finish. group of answer choices true
Answers
The given statement of agile life cycle is false.
What is agile life cycle?
The Agile life cycle will differ differently based on the project management technique that a team chooses. Scrum teams, for example, work in short time periods known as sprints, which are analogous to iterations. They also have distinct duties, such as Scrum master. Kanban teams, on the other hand, have a more continuous flow with no needed roles. Another example is Extreme Programming, in which teams work in shorter iterations and place a special emphasis on engineering principles. However, the goal of all software development teams is the same: to provide users with functional product on schedule.
To learn more about agile life cycle
https://brainly.com/question/13668097
#SPJ4
how does robotic process automation (rpa) differ from intelligent automation (ia)? rpa is more expensive to implement than ia. rpa is more complex to design and implement than ia. rpa is not compatible with existing applications, unlike ia. rpa can be implemented more quickly than ia.
Answers
Robotic Process Automation (RPA) and Intelligent Automation (IA) are both automation technologies, but they differ in their capabilities.
What is RPA?Both robotic process automation (RPA) and intelligent automation (IA) are automation technologies, but their capabilities differ.
The cost of implementing RPA or IA is determined by several factors, including the scope of the automation project, the complexity of the processes to be automated, the technology stack used, and the resources needed.
While both RPA and IA necessitate design and implementation efforts, the complexity of the two technologies varies depending on the processes to be automated.
Both RPA and IA can integrate with existing applications, but the degree of integration varies depending on the technology stack and architecture used.
The timeline for RPA and IA implementation is determined by several factors, including the complexity of the processes being automated, the technology stack used, and the resources required.
Thus, this way robotic process automation (RPA) differ from intelligent automation.
For more details regarding RPA, visit:
https://brainly.com/question/30000191
#SPJ1