A symmetric multi-processor system with uniform memory access
(SMP UMA) contains 50 processors and is to compute a running sum by
adding all of the elements in a one million-element vector. Each
proce
Answers
A symmetric multi-processor system with uniform memory access (SMP UMA) can compute the running sum of a one million-element vector efficiently by dividing the workload among its 50 processors.
In a symmetric multi-processor system with uniform memory access (SMP UMA), each processor has equal access to the system's memory. This characteristic enables efficient parallel processing, making it suitable for tasks like computing the running sum of a large vector.
To compute the running sum of a one million-element vector, the system can divide the workload among its 50 processors. Each processor can be assigned a portion of the vector, and they can concurrently process their assigned segments. By dividing the task into smaller sub-tasks and executing them simultaneously, the overall computation time can be significantly reduced.
The processors can perform addition operations on their respective segments independently, without requiring extensive communication or coordination between them. As a result, the system can achieve high throughput and efficient resource utilization. This parallel approach leverages the computational power of multiple processors to expedite the computation of the running sum.
Learn more about symmetric multi-processor systems
brainly.com/question/13161610
#SPJ11
Related Questions
provide(s) many scalability benefits by offering additional network and storage resources on demand and services like autoscaling and load balancing.
Answers
Answer:
The answer is cloud services.
Explanation:
The other answer choices just don't make sense. Python is a coding language and has nothing to do with scalability. Benchmarking has to do with finding out how powerful your system is. Denial of Service is when a website doesn't allow you to access it due to their servers being down.
the metric unit used for length
Answers
Answer:
kilometer
Centimeter
Meter
Milimeter
Hope it helps
Please mark me as the brainliest
Thank you
what is the first rule of digital forensics and subsequent analysis of evidence? it doesn't matter what copy you use as long as there is a duplicate copy preserve the original evidence, and analyse a copy only store and analyse original evidence only make a copy of the evidence, but analyse the original only
Answers
The first rule of digital forensics and subsequent analysis of evidence is:
Preserve the original evidence, and analyze a copy only.
In digital forensics, the first rule is to preserve the original evidence and analyze a copy only.
This is done to ensure the integrity and authenticity of the evidence and avoid any accidental or intentional modification or destruction of the original data.
By making a copy of the original evidence, investigators can perform various analyses and tests without altering the original data, and have a reference for comparison.
This also allows for multiple people to analyze the same data, as well as have backup in case the original data is lost or damaged.
Preserving the original evidence and analyzing a copy only is a critical step in maintaining the integrity of the evidence and ensuring accurate results in digital forensics investigations.
To know more about digital forensics, click on the link below:
brainly.com/question/3501191
#SPJ4
The first rule of digital forensics and subsequent analysis of evidence is to make a copy of the evidence, but analyse the original only.
It is important to always make a copy of the evidence that is being analyzed, as this will help to preserve the original evidence while still allowing for an accurate analysis to take place. This will help to ensure that the evidence is not accidentally corrupted or changed during the analysis process, allowing for an accurate and unbiased assessment of the evidence.
When making a copy of the evidence, it is important to ensure that the copy is exact and complete. This means that the copy should have the same file structure and contents as the original, and should not be modified in any way. It is also important to note that any analysis should be conducted on the original evidence, and not the copy. This is because any modifications made to the copy may not accurately reflect what actually happened on the original evidence.
When conducting a digital forensics investigation, it is important to ensure that all evidence is handled with care and that all necessary steps are taken in order to ensure that the evidence is not corrupted or changed in any way. This includes making a copy of the evidence, properly preserving the original evidence, and only analyzing a copy of the evidence. These steps will help to ensure that the evidence is handled properly and that all analysis is conducted accurately and without bias, allowing for an accurate assessment of the evidence.
Learn more about digital forensic: https://brainly.com/question/26694391
#SPJ4
ning and e-Publishing: Mastery Test
1
Select the correct answer.
Which statement best describes desktop publishing?
O A.
a process to publish drawings and photographs on different media with a laser printer
B.
a process to design and produce publications, with text and images, on computers
OC.
a process to design logos and drawings with a graphics program
OD
a process to publish and distribute text and graphics digitally over various networks
Reset
Next
Answers
Answer:
B
Explanation:
I dont no if it is right but B has the things you would use for desktop publishing
Answer:
the answer is B.
a process to design and produce publications, with text and images, on computers
Explanation:
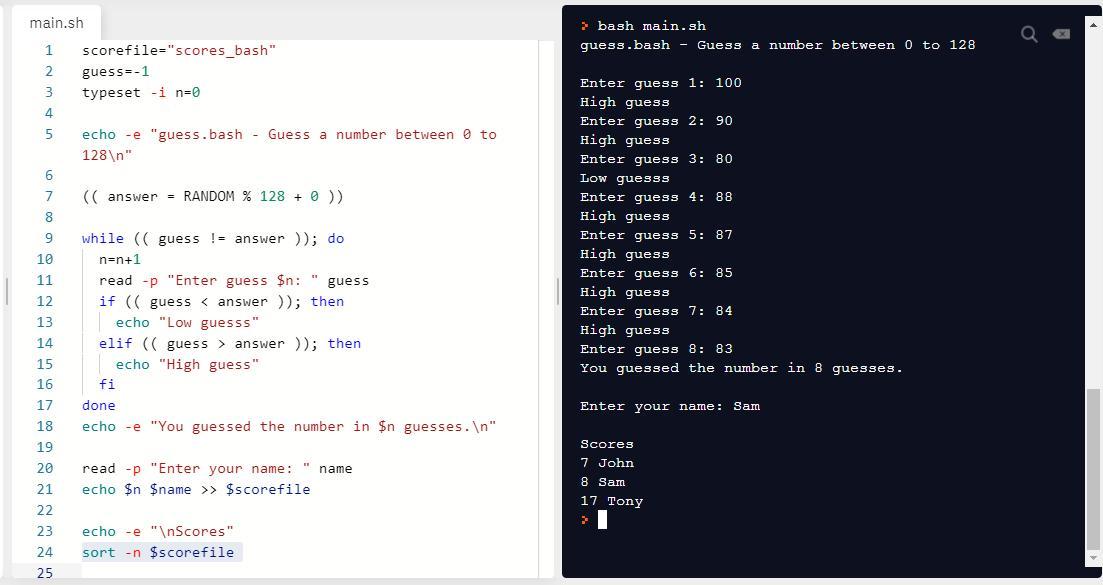
Create a bash shell script for a number guessing game. Here are the requirements: a. Your program generates a random number between 0 and 128 and keeps asking the user to guess the number until the user guesses it correctly. b. If the user guesses a number that is lower or higher than the number to be guessed then indicate that information to the user as a ‘low guess’ or a ‘high guess’ so that the user can get to the correct guess quicker. c. The program keeps track on number of guesses taken by the user to get to the correct guess. This is user’s score. d. Your program asks user for the name and adds user’s name and the score in a file that keeps track of the scores by various users. e. At the end of the game, the program displays the top 3 scores (lowest 3 scores) along with the name of the users to conclude the game. John 4 Sam 7 Tony 10
Answers
Answer:
Here is the bash shell script:
scorefile="scores_bash"
guess=-1
typeset -i n=0
echo -e "guess.bash - Guess a number between 0 to 128\n"
(( answer = RANDOM % 128 + 0 ))
while (( guess != answer )); do
n=n+1
read -p "Enter guess $n: " guess
if (( guess < answer )); then
echo "Low guesss"
elif (( guess > answer )); then
echo "High guess"
fi
done
echo -e "You guessed the number in $n guesses.\n"
read -p "Enter your name: " name
echo $n $name >> $scorefile
echo -e "\nScores"
sort -n $scorefile
Explanation:
The program creates a scorefile as scores_bash to store the names and scores. Next the program initializes the guess with -1. guess is used to store the guess made by user and n is used to store the number of trials user took to guess the correct number. Next the program prompts the user to: Guess a number between 0 to 128 and generates random numbers from 0 to 128 and store it into answer. Next the while loop keeps repeating until the user guesses the correct number. If the user guess is less than the correct answer then the program displays the message Low guess otherwise displays High guess. When the user guesses the correct number, the loop breaks and the message You guessed the number in $n guesses. is displayed where in place of $n the number of trials user take to guess the number is displayed. Next the user is asked to enter his name.
echo $n $name >> $scorefile statement adds the n which is the user score and name which is the names of user to the score file. sort -n $scorefile sorts the file in ascending order to display the lowest scores. The screenshot of program with its output is attached.
which of the following is a type of memory fault? group of answer choices a) address decode fault b) stuck-at fault c) bit isolation fault d) coupling fault e) a, b, and d f) a and d g) b, c, and d
Answers
The following is a type of memory fault address decode fault, stuck-at fault.
What exactly is memory?Memory is the ability to take in input from the environment, analyze it, store it, and then recall it at a later time—often years later. A disk storage system or file cabinet are frequently used as analogies for human memory.
Why is memory so crucial?Memory is most commonly used to describe the ongoing process of knowledge retention across time. It is a crucial element of human cognition because it enables people to recall and make use of previous experiences to frame their perception of and action in the present.
To know more about Memory visit :
https://brainly.com/question/29775537
#SPJ4
which option is the correct format of placing html tags while coding in html
A.
B.
C.
D.
Answers
Answer:
what are the answers?
it just says A, B. C. or D.
Explanation:
the increasing integration of the United States into the twenty-first-century world economy. ideological clashes over the power of the presidency and the federal government. demographic shifts in the U.S. population since 1980. liberals' inability to transform the political status quo.
Answers
Answer:
Explanation:
1
Which of the following is a mathematical representation of a real-world system, behavior, or
event? (1 point)
O function
O equation
O model
O algorithm
Answers
The option that is a mathematical representation of a real-world system, behavior, or event is option C: model.
What is the model of a real-world system?A model is an abstract representation of a system or process. It can be used to understand and predict the behavior of the system or process, or to test different scenarios and their outcomes.
Note that Models can be seen as a mathematical, computational, or graphical in nature, and they can be used in a variety of fields, including physics, biology, economics, and computer science.
Therefore, based on the context of the above, one can say that the option selected is the best as it best tells what the system of a real world scenario is.
Learn more about real-world system from
https://brainly.com/question/12302914
#SPJ1
inserting merge fields in the letter
steps required
plz
Answers
Answer:
Click or tap where you want the merge field.
Choose the down-arrow under Insert Merge Field, and select a field.
Insert Merge Field menu of available fields
If you don’t see your field name in the list, choose Insert Merge Field.
Choose Database Fields to see the list of fields that are in your data source.
Choose Insert.
Answer:
Once you have a data source connected to your document, adding merge fields is a way to personalize a document with information from the data source. The merge fields come from the column headings in the data source.
WindowsmacOS
Here’s an example of how the Address Block and Greeting Line collections of merge fields might pull data from an Excel spreadsheet into a form letter.
Data pulled into mail merge fields
The Address Block and Greeting Line fields are collections of merge fields.
Note: If the merge field commands appears dimmed, click Select Recipients and choose the kind of mailing list you’re using. If you don’t have a mailing list yet, click Type New List to create your list in Word.
Explanation:
Hope it's answer you plz mark as Brainlist
pls help
Question 2 (1 point)
True or false: when you use someone's copyrighted work in something you are
selling, you only have to cite them.
Answers
The given statement of copyrighted work is false.
What do you mean by copyright?
A copyright is a type of intellectual property that grants the owner the exclusive right to copy, distribute, adapt, display, and perform a creative work for a specific period of time. The creative work could be literary, artistic, educational, or musical in nature. The purpose of copyright is to protect the original expression of an idea in the form of a creative work, not the idea itself. A copyright is subject to public interest limitations, such as the fair use doctrine in the United States.
When you use someone's copyrighted work in something you are selling, you must get their permission first.
To learn more about copyright
https://brainly.com/question/357686
#SPJ13
Which of the following expressions will evaluate to true? (3 points)
7 == 7.0
7 != 7.0
7 < 7.0
Question 1 options:
1)
I only
2)
II only
3)
III only
4)
I and III only
5)
II and III only
Question 2 (3 points)
Saved
Which of the following expressions will evaluate to true? (3 points)
12 / 5 != 2.0
12 / 5.0 == 2.0
(int)(12.0 / 5.0) == 2.0
Question 2 options:
1)
I only
2)
II only
3)
III only
4)
I and II only
5)
I and III only
Question 3 (3 points)
Assume an integer variable named num is assigned a value of 20. What is the value of num - 7 < 15? (3 points)
Question 3 options:
1)
True
2)
False
3)
0
4)
1
5)
An error occurs
Question 4 (3 points)
What is the result of the following code segment? (3 points)
int x = 10;
if(x + 1 < 20)
x += 5;
System.out.println(x);
Question 4 options:
1)
10
2)
11
3)
15
4)
16
5)
20
Question 5 (3 points)
Assume the integer variable num has been assigned a valid value. What is the purpose of the following code segment? (3 points)
if(num % 10 != 0)
System.out.print(num);
Question 5 options:
1)
It prints num if its value is a multiple of 10.
2)
It prints num if its value is not a multiple of 10.
3)
It always prints the value of num.
4)
It never prints the value of num.
5)
An error occurs at compile time.
Answers
Answer:
A and B
Explanation:
What is an operating system? What are the different types of security threats it faces? Describe the steps you take to secure an operating system. Explain the steps you take to secure the operating system you use. How would you verify that your operating system is secure?
Answers
Answer:
An operating system is an interface built toward a consumer made of code. The security threats it faces are worms, viruses, and bugs (digital) On my operating system, macOS X, I added the Avast Secure Antivirus, and added a program called lockdown initiator to it (works with windows). To verify, see if your antivirus captures any viruses, or have a pro add a virus to your computer and test if it gets in or not(the same way a doctor gives you vaccines).
What are the benefits of transferable skills check all the boxes that apply
Answers
Answer:
They allow easy cross-company transfers.
They help a person develop self-esteem.
They open up a variety of employment options.
Explanation:
Answer:
Las habilidades duras son cuantificables y, en ocasiones, exclusivas de una profesión (como la capacidad de un idioma
Explanation:
which of the following is the best example of inappropriate content for a slide presentation
Answers
Answer:
an image that has no relevance to the presentation topic
An image that has no relevance to the text on the slide of the following week is the best example of inappropriate content for a slide presentation. The correct option is B.
What is a good slide presentation?Try to avoid using paragraphs, or the quotations, and even the full sentences. Limit your slides to five lines of the text and try to make your points with the words as well as the phrases. Key points will be easier to digest and retain for the audience. Use your slides for more than just speaker notes or to project an outline of your presentation.
Disadvantage of a good slide presentation is that or it is because PowerPoint slides are the linear, the presenter has been forced to reduce the complex subjects to the set of the bullet items that are insufficient in order to support the decision-making or the demonstrate the complexity of an issue. Disadvantage are the basic presentation equipment which are required.
Thus, the ideal selection is option B.
Learn more about slide presentation here:
https://brainly.com/question/938745
#SPJ7
Which equipment needs special shields to protect against dust and wind?
O A. editing equipment
OB. tripods
OC lights
D. microphones
Answers
D. microphones
editing equipment, tripods and lights do not need protection against dust and wind. Microphones do though, because of how sensitive they are towards dust and wind.
Answer:D
Explanation:
Which is an example of a crime that might occur in an e-commerce transaction?
A customer’s new purchase is stolen after delivery.
A customer’s credit card information is stolen and used by someone else.
A customer can easily take merchandise without having to pay for it.
A customer pays an unfair price for the merchandise she bought.
Answers
Answer:
A costumers credit card information is stolen and used by someone else.
Answer:
A customer's credit card information is stolen and used by someone else.
Explanation:
Since e-commerce is online sales, the customer can not take merchandise without having to pay for it.
Also the customer can search for the best price.
What is nail punch in your own words?
Answers
Answer:
in my own words
nail punch
a punch for driving the head of a nail below or flush with the surrounding surface
Explanation:
Sana po naka tolung
correct me if im wrong thanj you
#Brainly
How do I calculate this square footage?

Answers
Answer:
To calculate it, you have to break it apart. Sorry for the bad writing but after you break it apart, you multiply the smaller squares. Then with all of the smaller areas, add them together for the final answer which in this case is 456.

Which of the following code provides instructions to the hardware? Service Pack Operating System Application Firmware Submit iii 5 of 7 6 Question For which of the following Windows versions, Microsoft has stopped providing support services? [Choose all that apply.] Windows 8.1 Windows 8 Windows XP Windows 7 Submit iii 6 of 7
Answers
Firmware is code that provides instructions to hardware. Firmware is stored in read-only memory (ROM) and is typically used to boot the device and run its basic functions.
Updating Firmware: The Pros and ConsFirmware can be updated to fix bugs or add new features, but this requires specialised knowledge and tools.
Firmware is a type of software that is stored on a hardware device, such as a computer’s BIOS chip. Firmware is used to perform low-level tasks and is usually not updated or replaced by users. However, in some cases, users may need to update their firmware in order to fix bugs or add new features.
Why Microsoft Stopped Supporting Windows 8.1, 8, and XPAs of January 2020, Microsoft no longer provides support services for:
Windows 8.1.Windows 8.Windows XP.This means that users of these operating systems will no longer receive security updates or other patches from Microsoft. While users are still able to use these operating systems, it is generally recommended that they upgrade to a newer version of Windows in order to stay secure.
Learn more about Windows at: https://brainly.com/question/14531631
#SPJ4
Open the PT Activity. Perform the tasks in the activity instructions and then answer the question. Fill in the blank. Do not use abbreviations. What is the missing command on router R2 to establish an adjacency between routers R1 and R3? [blank_start]network 172.16.10.0 0.0.0.255 area 0[blank_end]
Answers
The missing command on router R2 to establish an adjacency between routers R1 and R3 is network 172.16.10.0 0.0.0.255 area 0.
This command is used to advertise the network 172.16.10.0/24 in OSPF area 0, which allows R2 to establish an adjacency with both R1 and R3. The network command is used to specify the networks that should be advertised by OSPF, and the area parameter specifies the OSPF area to which the network belongs.
By advertising the same network in the same area on both R1 and R3, R2 can act as a transit router between them and allow them to communicate with each other.
Learn more about command here:
https://brainly.com/question/14548568
#SPJ11
Ryan is the operations manager for a national financial company. His company is in the process of creating a customer handbook. Employees all over the country will collaborate on the different documents that will be included in the handbook and frequent additions and revisions will be made. He is looking for a telecommunications technology that can help him efficiently manage this task.
In 2-5 paragraphs, describe the points that Ryan needs to consider when choosing a telecommunications technology to meet his needs.
Answers
Answer:
Ryan first needs to determine his goals, in his case he is looking for a telecommunications technology that will often need to be updated and revised by others. Once he determines what he is looking for he can start gathering data, and once he's done that he can analyze his choices from the data he's gathered, in his case I would assume he'd be looking at either a wiki or a blog. Now it's time for Ryan to make his decision, I would go with a wiki since a wiki can be updated by many people in diverse locations. He said so himself that employees all over the country would be contributing to it so that is why I think a wiki would best suit him. Now that he's made his decision and can take a step back and evaluate what he has done and make sure he made the right choice.
Explanation:
:)
What feature allows you to access previous copies of a document on OneDrive?
Answers
Answer:
go to downloads and find drives
Explanation:
A(n) _____ describes your core values and highest career goals. A. résumé B. objective statement C. qualifications profile D. personal mission statement
Answers
Answer: D.) Personal Mission Statement
Explanation: The personal mission statement refers to a write up which is usually written by an individual and it's tailored to embody one's complete definition in terms of core values, skills, attributes and most importantly present and future desires, goals and objectives. The statement of purpose is usually detailed and will showcase where an individual is currently placed while also showcasing how he or she intends to achieve future aspiration.
Answer:
The answer would be D.) Personal Mission Statement (APEX)
Draw a flowchart to find greater number among three number
Answers
Answer:
See attachment for flowchart
Explanation:
First, we get input for the three numbers
The flowchart then checks if the first number is greater than the other two
If yes, the first is assigned the largest
If otherwise, the second number is tested
If it is greater than the other two, then the second is assigned the largest
If otherwise, the third is assigned the largest
Lastly, the largest is printed before the flowchart ends

which of the following statements is true? the value of a global named constant cannot be changed during program execution. unlike using global variables, using global named constants can introduce detrimental side effects to your program. a global named constant must be defined in the main function. the value of a global named constant cannot be accessed from anywhere in the program.
Answers
The statement "The value of a global named constant cannot be changed during program execution" is true. Global named constants are variables whose values are fixed and cannot be modified once they are defined. They provide a way to store values that should remain constant throughout the program.
The other statements are false. Using global named constants does not introduce detrimental side effects to a program; in fact, it is considered good practice to use constants to improve code readability and maintainability. Global named constants can be defined outside of the main function, typically at the top of the program or in a separate header file. Lastly, global named constants can be accessed from anywhere in the program where their scope is visible.
learn more about "global":- https://brainly.com/question/1133228
#SPJ11
Which of the following is NOT a characteristic of Advanced Persistent Threat (APT)?
a. can span several years
b. targets sensitive proprietary information
c. uses advanced tools and techniques
d. is only used by hactivists against foreign enemies
Answers
One of the following is NOT a trait of Advanced Persistent Threat (APT), which is only applied by activists against adversaries abroad.
Which of the following traits best describes an apt attack?APT assaults differ from conventional cyber-attacks in four ways [9], which are listed below. Advanced or Complex, Persistent, Targeted, and Evasive (APTs) (see Figure 3). APT assaults are meticulously and methodically prepared, spanning several steps.
What traits define an advanced persistent threat that gives it that moniker?An advanced persistent threat (APT) is one that uses persistent, covert, and sophisticated hacking methods to enter a system and stay there for an extended length of time, perhaps with harmful effects.
To know more about Advanced Persistent Threat visit :-
https://brainly.com/question/28902554
#SPJ4
Short Python Code for 20 pts.
Get a positive integer from the user, and check to see if that number is or is not divisible by 5 random integers (from 1 - 10). If the user typed in a negative number - do nothing, however if they did type a positive number, report back to the user if their number is divisible by the 5 random numbers generated.
**HINT: You need to use modulus (%) for the project**
Example output of program:
10 is divisible by 2
10 is not divisible by 6
10 is not divisible by 4
10 is divisible by 2
10 is divisible by 1
Answers
import random
# get user input
num = int(input("Enter a positive integer: "))
# check if user input is positive
if num > 0:
# generate 5 random numbers between 1 and 10
rand_nums = random.sample(range(1, 11), 5)
# check if num is divisible by each of the random numbers
for i in rand_nums:
if num % i == 0:
print(f"{num} is divisible by {i}")
else:
print(f"{num} is not divisible by {i}")
This code prompts the user to enter a positive integer, and then checks if the input is greater than 0. If it is, it generates 5 random numbers between 1 and 10 using the 'random.sample()' function. It then uses a for loop to iterate through the list of random numbers, and for each number, it checks if the user's input is divisible by the current number by using the modulus operator ('%'). If the input is divisible by the current number, it prints a message saying so, otherwise, it prints a message saying the input is not divisible by the current number.
Which of these cannot be used to open a zip file?
O WinZip
O WordPad
File Viewer Plus
O Apple Archive Utility
Answers
Answer:
c
Explanation:
bc
write a 128 x 9 ( 128 entries, 9-bit wide) ram model in verilog , with ports addr, data in, data out, rd, wr. indicate how many address and data bits you would need.
Answers
In this model, the `addr` port requires 7 bits because it needs to address 128 entries (\(2^7\) = 128). The `data_in` and `data_out` ports are 9 bits wide to accommodate the 9-bit data.
Please note that in the provided code, it assumes the presence of a clock signal for the synchronous behavior of the RAM module. Additionally, you may need to include appropriate testbenches and other components as per your design requirements.
Learn more about RAM https://brainly.com/question/31089400
#SPJ11