a technician is troubleshooting a computer and wants to eliminate any factors that could cause the problem to reoccur. what can the technician use to mitigate reoccurrence?
Answers
To mitigate the reoccurrence of a problem when troubleshooting a computer, a technician can employ several strategies and tools: Software Updates: Ensure that the computer's operating system, drivers, and software applications are up to date with the latest patches and updates. This helps address known bugs and vulnerabilities.
Antivirus and Security Software: Install and regularly update antivirus and security software to detect and prevent malware or other security threats that could lead to recurring issues. Diagnostic Tools: Utilize diagnostic software or built-in diagnostic tools to identify hardware or software issues accurately. Running diagnostic tests can help pinpoint the root cause and take appropriate actions to prevent future occurrences. Hardware Checks: Thoroughly inspect hardware components for any signs of damage or malfunction. Replace faulty hardware, such as RAM, hard drives, or power supplies, to prevent recurring issues caused by faulty components. Review Configuration and Settings: Verify and optimize system configurations, settings, and preferences to ensure they are aligned with best practices and appropriate for the computer's intended use. User Education and Best Practices: Provide users with guidance on safe computing practices, such as avoiding suspicious websites, not clicking on unknown links or attachments, and regular data backups.
Learn more about troubleshooting here
https://brainly.com/question/28508198
#SPJ11
Related Questions
the best answer it requests services, data and other resources available on the server
Answers
Answer:
Explanation:
?
Which programming paradigm focuses on abstraction to the level of math and the elimination of side-effects and state based programming
Answers
Answer:
The functional programming paradigms has its roots in mathematics and it is language independent.
Explanation:
The key principle of this paradigms is the execution of series of mathematical functions. The central model for the abstraction is the function which are meant for some specific computation and not the data structure.
what is different types of secondary memory of computer system?
Answers
Secondary memory refers to the non-volatile memory devices in a computer system that are used for long-term storage of data and programs. Here are some of the different types of secondary memory:
Hard disk drives (HDD): These are mechanical devices that store data on spinning disks using magnetic fields. They are commonly used in desktop and laptop computers as the primary storage device.
Solid-state drives (SSD): These are non-mechanical devices that use flash memory to store data. They are faster and more reliable than HDDs and are commonly used as the primary storage device in laptops, tablets, and smartphones.
Optical storage devices: These include CD, DVD, and Blu-ray discs, which are used to store data and programs. They are read by lasers and can be used for backup and archival purposes.
USB flash drives: These are small portable storage devices that use flash memory to store data. They are commonly used to transfer files between computers and as a backup storage device.
Memory cards: These are small storage devices commonly used in cameras, smartphones, and other portable devices to store data and media files.
Magnetic tape: This is a sequential access storage medium commonly used for backup and archival purposes.
Each of these secondary memory types has its own advantages and disadvantages, and is used in different ways depending on the specific needs of the user or organization.
Secondary memory refers to the non-volatile memory devices in a computer system that are used for long-term storage of data and programs. Here are some of the different types of secondary memory:
Hard disk drives (HDD): These are mechanical devices that store data on spinning disks using magnetic fields. They are commonly used in desktop and laptop computers as the primary storage device.
Solid-state drives (SSD): These are non-mechanical devices that use flash memory to store data. They are faster and more reliable than HDDs and are commonly used as the primary storage device in laptops, tablets, and smartphones.
Optical storage devices: These include CD, DVD, and Blu-ray discs, which are used to store data and programs. They are read by lasers and can be used for backup and archival purposes.
USB flash drives: These are small portable storage devices that use flash memory to store data. They are commonly used to transfer files between computers and as a backup storage device.
Memory cards: These are small storage devices commonly used in cameras, smartphones, and other portable devices to store data and media files.
Magnetic tape: This is a sequential access storage medium commonly used for backup and archival purposes.
Each of these secondary memory types has its own advantages and disadvantages, and is used in different ways depending on the specific needs of the user or organization.
You want the output to be left justified in a field that is nine characters wide. What format string do you need?
print('{: __ __ }' .format(23)
Answers
Answer:
> and 8
Explanation:
> and 8 format string one will need in this particular input of the java string.
What is a format string?The Format String is the contention of the Format Function and is an ASCII Z string that contains text and configuration boundaries, as printf. The parameter as %x %s characterizes the sort of transformation of the format function.
Python String design() is a capability used to supplant, substitute, or convert the string with placeholders with legitimate qualities in the last string. It is an inherent capability of the Python string class, which returns the designed string as a result.
The '8' specifies the field width of the input The Format String is the contention of the Configuration Capability and is an ASCII Z string that contains the text.
Learn more about format string, here:
https://brainly.com/question/28989849
#SPJ3
why is it important for a network architect to work in the office
Answers
The different between a compiler and a translaror
Answers
Answer:
Compiler converts the program from one computer language to another computer language that is translating from a higher level language to a lower level language. A translator usually has a fixed body of code that is required to translate the program.
Answer:
Answer: Compiler converts the program from one computer language to another computer language that is translating from a higher level language to a lower level language. ... A translator usually has a fixed body of code that is required to translate the program.
Explanation:
How would you monitor the performance of others that you have to lead
Answers
Answer:
Check over their progress daily.
Explanation:
Add my ps4 account FG_Colut_ ωωω
Answers
jfkdhsjfka
Answer:
i will
Explanation: for points on here bro
What shape will this code make?
import turtle
Mark = turtle.Turtle()
Mark.back(80)
Mark.left(90)
Mark.forward(50)
Mark.right(90)
Mark.forward(80)
Mark.back(80)
Mark.left(90)
Mark.foward(50)
Mark.right(90)
Mark.forward(80)
Answers
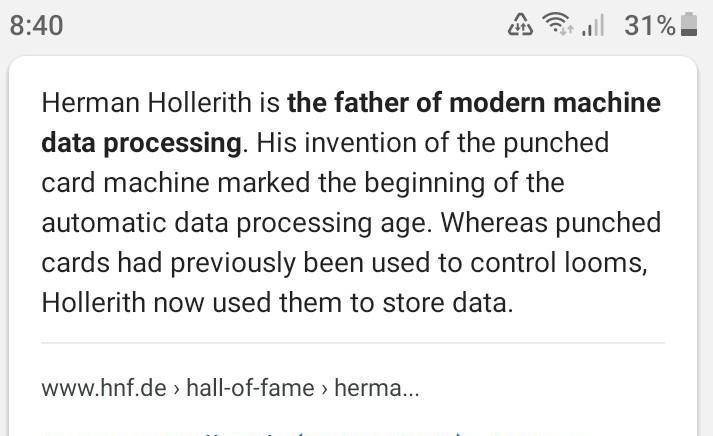
who was Dr. Hean Hollerith
Answers
Answer: Herman Hollerith, (born February 29, 1860, Buffalo, New York, U.S.—died November 17, 1929, Washington, D.C.), American inventor of a tabulating machine that was an important precursor of the electronic computer.
Explanation:
Answer:
☝️here is a answer ......
If a fingerprint or retina scan is required to open a secured door, which kind of physical security has been implemented
Answers
Answer:
Biometrics
Explanation:
Use of unique features as a measure of security such as fingerprints
Rafael needs to add a title row to a table that he has inserted in Word. What should he do? Use the alignment options. Use the Merge and Center option for all the cells in the top row. Use the Merge and Center option on the first two cells in the top row. none of the above
I'll mark brainliest
Answers
Answer:
Use the Merge and Center option for all the cells in the top row.
Explanation:
took the test!
Rafael needs to add a title row to a table that he has inserted in a Word document. He should require to use the Merge and Center options for all the cells in the top row. Thus, the correct option for this question is B.
What are the characteristics of Word documents?The characteristics of a word document are as follows:
It has a large diversity of styles that saves your time.It assembles your document in a systematic order which enhances its attractiveness. It includes font name, color, size, paragraph alignment, borders, spacing, etc.According to the context of this question, the title which is inserted must be at the top and center of the table. In order to avail of this, one must use the merge and center option for all the cells in the top row.
Therefore, the correct option for this question is B.
To learn more about Word documents, refer to the link:
https://brainly.com/question/1504260
#SPJ5
2. dreamhouse realty wants to offer a form on its experience cloud site where inspectors will submit findings from a property inspection. which feature should an administrator place on the page to fulfill this requirement?
Answers
A web form feature should be placed on the page of Dreamhouse Realty's Experience Cloud Site where inspectors will submit findings from a property inspection to fulfill this requirement.
A web form is a common way for a user to interact with a website. It is a container that collects data from users and sends it to the site's server. Web forms can have various types of inputs, such as text fields, radio buttons, checkboxes, and dropdown menus. They can also have complex elements like file uploads, captcha tests, and rich text editors. Web forms are widely used on e-commerce sites, contact forms, and job application forms.
You can learn more about web form at: brainly.com/question/28315791
#SPJ11
What two names are given to UDP blocks of communication?
Answers
The two names given to UDP blocks of communication are datagrams and packets.
Datagram refers to a self-contained unit of data that is transmitted over a network and contains all the necessary information for its delivery, including source and destination addresses. It is a fundamental component of the User Datagram Protocol (UDP) that provides an unreliable, connectionless service for transmitting datagrams between network hosts.
A packet, on the other hand, is a similar unit of data that is used in various network protocols, including UDP and TCP (Transmission Control Protocol). A packet contains not only the data to be transmitted but also additional information such as header information, error detection codes, and other control information necessary for its successful transmission and reception. Unlike datagrams, packets can be guaranteed to arrive at their destination, as they are transmitted using connection-oriented protocols like TCP that ensure their reliable delivery.
In summary, datagrams and packets are both essential units of data used in network communication, with datagrams being used in connectionless, unreliable protocols like UDP, and packets being used in connection-oriented protocols like TCP. Understanding the differences between these terms is crucial for network engineers and administrators to effectively manage and troubleshoot network issues.
know more about User Datagram Protocol here:
https://brainly.com/question/20038618
#SPJ11
For each of the four ANSI levels of query isolation, discuss the impact on recovery. What prop erties must a transaction schedule have to ensure recovery works correctly
Answers
ANSI defines four levels of query isolation, each with its own properties that affect the impact on recovery: Read Uncommitted, Read Committed, Repeatable Read.
Serializable: This level ensures that concurrent transactions behave as if they were executed serially, preventing any interleaving of transactions. In the event of a failure, the recovery process must ensure that all transactions are committed or rolled back properly, to prevent inconsistent data from being read. To ensure recovery works correctly, a transaction schedule must have the following properties: Atomicity: Each transaction should be treated as a single unit of work, meaning that either all of its operations are executed, or none of them are. This ensures that transactions can be rolled back if necessary, without leaving the database in an inconsistent state. Consistency: Each transaction should maintain the consistency of the database, meaning that it should start and end in a consistent state. This ensures that all transactions can be committed, without leaving the database in an inconsistent state. Isolation: Each transaction should execute independently of other transactions, meaning that they should not interfere with each other. This ensures that each transaction can be rolled back or committed independently, without affecting the consistency of the database. Durability: Each committed transaction should persist, even in the event of a failure, to ensure that the database can be restored to a consistent state. This means that the recovery process must ensure that all committed transactions are stored safely, and can be recovered in case of failure.
Learn more about recovery here:
https://brainly.com/question/29925389
#SPJ11
Please Help, Thank you!
-State whether- True or False :
a) Bluetooth uses Radio waves...
b) White hackers steal confidential information...
c) Hub transfers send the incoming data to the desired
destination only...
d) Infra-red signals are suitable for long distance data
communication...
e) HTTP is used in between a web server and a web browser...
f) LAN (Local Area Network) is the network exists around a person...
g) Coaxial cable consists of a copper conductor (wire)...
h) Microwave antennas are located at a substantial height above
the ground level...
i) Firewall can be implemented as a software, hardware or a
combination of both...
Please, please help me!♡´・ᴗ・`♡
j) Star topology is complicated to set up...
Answers
Answer: Devices connected in a Bluetooth network communicate with each other using ultra-high frequency (UHF) radio waves. These are electromagnetic waves with frequencies around 2.4 gigahertz (2.4 billion waves per second). UHF waves of different frequencies are used in microwave ovens, GPS systems and many other devices, White hat hackers employ the same methods of hacking as black hats, with one exception- they do it with permission from the owner of the system first, which makes the process completely legal. ... There are even courses, training, conferences and certifications for ethical hacking. A hub connects multiple computers together in a Local Area Network (LAN). All information sent to the hub is then sent through each port to every device in the network.
Hubs are unable to tell one computer from another, so they receive information on one port and then blindly forward it to all other ports — whether it was intended for those computers or not.
So even though you may only want to send information to one other computer, if you have five total computers on your network, then there will be four other computers receiving data that wasn’t intended for them. Showing results for are Infrared signals are suitable for long distance data communication..
Search instead for are Infra-red signals are suitable for long distance data communication..
Infrared laser systems can also be used for long-range communication (up to about 2.4 kilometres), with a maximum projected data rate of 16 Mbps. ... An infrared transmitting device, either a light-emitting diode (LED) or a laser diode, converts an electrical signal to an optical signal.
Web Browser is a software which is used to browse and display pages available over internet whereas web server is a software which provides these documents when requested by web browsers. ... Web browser sends an HTTP Request and gets a HTTP Response. Web server receives HTTP Request and sends a HTTP Response.
Simple LANs generally consist of cabling and one or more switches. A switch can be connected to a router, cable modem, or ADSL modem for Internet access. A LAN can include a wide variety of other network devices such as firewalls, load balancers, and network intrusion detection.
Coaxial cable, or coax (pronounced /ˈkoʊ. æks/) is a type of electrical cable consisting of an inner conductor surrounded by a concentric conducting shield, with the two separated by a dielectric (insulating material); many coaxial cables also have a protective outer sheath or jacket.
Terrestrial microwave- The most common type of microwave antenna is the parabolic “dish.”A typical size is about 3 m in diameter. The antenna is fixed rigidly and focuses a narrowbeam to achieve line-of-sight transmission to the receiving antenna. Microwave antennasare usually located at substantial heights above ground level to extend the range betweenantennas and to be able to transmit over intervening obstacles. To achieve long-distancetransmission, a series of microwave relay towers is used, and point-to-point microwave linksare strung together over the desired distance. Used in long haul telecommunicationsservice, as an alternative to coaxial cable or optical fiber.
You can implement a firewall in either hardware or software form, or a combination of both. Firewalls prevent unauthorized internet users from accessing private networks connected to the internet, especially intranets
Which generation experienced a generation gap?
A.
the boom generation
B.
the silent generation
O C.
Generation X
D.
the millennial generation
Answers
Answer:
B. Baby boomers (the boom generation)
Explanation:
They went against everything their parents said. Also I took a test on it and got it right.
A new class of objects can be created conveniently by ________; the new class (called the ________) starts with the characteristics of an existing class (called the ________), possibly customizing them and adding unique characteristicsof its own.
Answers
Answer:
A new class of objects can be created conveniently by inheritance; the new class (called the superclass) starts with the characteristics of an existing class (called the subclass), possibly customizing them and adding unique characteristicsof its own.
hlp plz...........,....

Answers
Letters are sent out automatically when books are late.
And:
It is easier to see if books are available.
Plz let me know if I’m wrong and I’m sorry if I am :)
Brainliest would be nice
Thank you
The strncat() function is tricky to use correctly.
You can compare two C-strings, s1 and s2, by using the strcmp() function.
C-strings are character arrays that rely on a special embedded sentinel value, the character with the ASCII code 0.
The allocated size for the C-string char s1[] = "hello"; is 6 characters, while the effective size is 5 characters.
The sizeof operator returns the allocated size of a C-string allocated as an array.
The effective size of the C-string char * s1 = "hello"; is 5 characters, but 6 characters are used for storage.
strcmp(s1, s2) returns a positive number if s1 is lexicographically "greater than" s2.
C-strings use the strcat() function for concatenation.
The strlen() function returns the effective size of a C-string.
C-strings are often needed to interoperate with legacy C libraries.
When writing programs that interact with your operating system facilities, either Windows, Mac OSX or Linux, you will normally use C-strings instead of the C++ library string type.
The characters for the C-string char s1[] = "hello"; are stored in user memory and may be modified.
C-strings are char pointers to the first character in a sequence of characters, terminated with a '\0' character.
C-string functions may be more efficient than C++ string member functions.
strcmp(s1, s2) returns a negative number if s1 is lexicographically "less than" s2.
Given the C-string char * s3 = "hello"; strlen(s3) returns 5.
C-string assignment uses the strcpy() function.
strcmp(s1, s2) returns 0 if s1 and s2 contain the same characters.
The C-string type is built into the C++ language, not defined in the standard library.
The strcpy() function always appends a trailing NUL when the copy is finished.
The strncpy() function can be used to make sure that you don't copy more characters than necessary.
Programs written for embedded devices often use C-strings rather than the C++ library string type.
The length of a C-string is never stored explicitly
The C-string literal "cat" contains 4 characters.
The strncat() function allows you to limit the maximum number of characters that are concatenated.
The character with the ASCII code 0 is called the NUL character. True or False
Answers
The statement "The character with the ASCII code 0 is called the NUL character" is true. In C and C++, the NUL character, represented by '\0', is used as a sentinel value to indicate the end of a C-string. It is used to mark the termination of character sequences and is not considered a printable character.
- C-strings are character arrays that rely on the NUL character ('\0') to determine the end of the string.
- The NUL character has an ASCII code of 0, and its presence at the end of a C-string allows various string functions to identify the end of the string.
- By convention, C-strings are terminated with the NUL character to ensure proper string handling and prevent reading beyond the intended string length.
- The NUL character is not considered part of the visible characters in the string but rather serves as a termination marker.
- Understanding the NUL character and its role in C-strings is crucial for correctly working with C-string functions and ensuring proper string manipulation and termination.
Learn more about ASCII code:
https://brainly.com/question/30530273
#SPJ11
Calculate the sum of 24 in binary using the 2's complement of 18.
Answers
Answer:
the answer is 0101110
A technician has been dispatched to a customer site to diagnose an issue where the computer turns off intermittently. Upon arriving at the site, the technician detects a smoke smell coming from the computer. Which of the following is the BEST solution?
A. Power down the system and replace the CPU.
B. Power down the system and replace the power supply.
C. Install an additional case fan for proper ventilation.
D. Remove the side panel for proper ventilation.
Answers
Answer:
The answer is "Option B".
Explanation:
When the technician detects a smoke smell, which is coming from the computer system it means it will sort to solve this problem the technician will shut the system down and substitute electricity, at this, it overcomes the problem, and wrong choices can be defined as follows:
In choice A, It is wrong because in this system component may be destroyed.In choice C and D both are wrong because it is not a software and side panel problem.-Steve wants to publish a portfolio online. He use Mozilla Firebug. What will it help him do?

Answers
Mozilla Firebug is a web development tool used to inspect, edit, and debug HTML, CSS, and JavaScript in real-time. It is an extension of the Mozilla Firefox web browser and allows users to analyze and modify web page content on the fly.
For Steve, Firebug can be an extremely useful tool in creating and publishing his portfolio online. By using Firebug, he can inspect the HTML and CSS of his portfolio website to identify any errors, bugs, or issues that may be affecting its functionality or appearance. Additionally, he can edit the code directly within Firebug to test out new changes and see how they affect the website in real-time.
Overall, Firebug is a powerful tool for web developers like Steve who want to ensure that their website is functioning optimally and delivering the best possible user experience.
For more questions on HTML:
https://brainly.com/question/4056554
#SPJ11
fitb in the context of cloud computing, infrastructure as a service (iaas) is also known as _____as a service.
Answers
A fitb in the context of cloud computing, infrastructure as a service (iaas) is also known as hardware as a service.
Is hardware a service business?The term is seen as a licensing or leasing business model is also the same as a hardware as a service (HaaS) concept. Instead of buying the hardware in this case, the consumer pays for the services it provides. In essence, the consumer does not actually own the underlying gear; rather, they pay for the value that the service offers.
Note that Infrastructure for cloud computing is the group of hardware and software components required to make cloud computing possible. In addition to an interface that allows users to access their virtualized resources, it also comprises processing power, networking, and storage.
Therefore, based on the above context, one can say that a managed service provider (MSP) installs hardware at a customer's location under the terms of a service level agreement (SLA), which spells out each party's obligations. This procurement model is known as hardware-as-a-service (HaaS), and it is seen as comparable to leasing or licensing.
Learn more about cloud computing from
https://brainly.com/question/19057393
#SPJ1
With the launch of Windows 10, Microsoft announced that it would publish ongoing, incremental upgrades instead of releasing new versions of the software every few years. However, some IS professionals have opted out of frequent updates because they believe making minimal changes will ensure reliable operations. T/F
Answers
Answer:
Explanation:
False.
Some IS professionals may choose to opt out of frequent updates due to concerns about potential disruptions to their systems and operations. However, the statement that making minimal changes will ensure reliable operations is not entirely accurate. While minimizing changes can reduce the risk of introducing new issues or compatibility problems, it can also result in missing out on important security patches, bug fixes, and new features that are included in the updates.
Regular updates are crucial for maintaining the security, stability, and performance of software systems. They often address vulnerabilities, improve compatibility with other software and hardware, and introduce enhancements and optimizations. Therefore, keeping software up to date with the latest updates is generally recommended to ensure reliable and secure operations.
Learn more about launch of windows 10 here:
https://brainly.com/question/31735777
#SPJ11
PLEASE HELP!!!
The unit talks about various astronomical tools, but satellites don’t make the list—why? Explain how satellites help us learn more about the Earth from space and analyze whether they can also help us learn more about space.
Answers
Answer:
The bird's-eye view that satellites have allows them to see large areas of Earth at one time. This ability means satellites can collect more data, more quickly, than instruments on the ground.
Explanation:
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
why are nutrients needed for living things?describe the diffrence betwwen living and nonliving things.
Answers
Nutrients are essential to keep living organisms alive. Living organisms need specific conditions and environment to be able to stay alive, while non-living organisms are the abiotic factors in an ecosystem and don't need oxygen, or the previously stated things living things need.
When numbers are formatted in percent format, they are multiplied by _______ for display purposes.
1000
100
10
20
Answers
Which of the following is not the characteristics of On-line Analytical Processing (OLAP)?
A. Provide decision support tool through analytical investigation of complex data association
B. Provide management real-time information
C. Provide mission-critical tasks through simple queries of operational database
D. Provide modeling, information retrieval, and ad-hoc analysis
Answers
The characteristic of Online Analytical Processing (OLAP) that is not listed among the options is providing mission-critical tasks through simple queries of operational databases (option c).
On-line Analytical Processing (OLAP) is a technology used for analyzing and querying multidimensional data from various perspectives. It is designed to provide decision support and enable analytical investigations of complex data associations.
OLAP systems allow users to perform modeling, information retrieval, and ad-hoc analysis to gain insights and make informed decisions based on the data. They are specifically designed to handle complex analytical tasks and provide real-time information to management.
However, OLAP is not typically used for executing mission-critical tasks through simple queries of operational databases. Operational databases are primarily used for day-to-day transactional operations and may have different structures and purposes compared to OLAP databases.
While OLAP can support decision-making processes and provide valuable insights, it is not designed for direct operational tasks or simple queries of operational databases. OLAP systems are focused on providing powerful analytical capabilities, multidimensional data modeling, and advanced querying functionality to support complex data analysis and reporting requirements.
Learn more about operational databases here:
https://brainly.com/question/32396682
#SPJ11