access controls consist of , which confirms user identity, and , which determines user access levels.group of answer choicesaccess; privilegespasswords; privilegesauthentication; authorizationauthorization; privileges
Answers
Authentication is the process of confirming a user's identity, while authorization is the process of determining a user's access levels.
Authentication is the process of confirming a user's identity to ensure that they are who they say they are. It usually involves providing a username and password, or some other kind of proof of identity, such as a fingerprint or facial recognition. This process is important for protecting sensitive information and ensuring that only authorized users have access. Authorization is the process of determining a user's access levels. This typically involves assigning levels of privilege, such as read-only access or full administrative access, to different users. This helps to ensure that users with higher levels of privilege can't access information or perform tasks that are beyond their authority. By using both authentication and authorization, organizations can effectively protect their data and ensure that only authorized users are able to access sensitive information.
Learn more about Authentication here:
brainly.com/question/17217803
#SPJ4
Related Questions
Q3: How were basic sounds used to create tension in the early generations of
gaming?
Answers
Adjusted for inflation, the many versions of the game are estimated to have grossed over $13 billion in total revenue as of 2016,[5] making it the highest-grossing video game of all time.
How were basic sounds used to create tension in the game?Space Invaders is considered one of the most influential video games of all time. It helped expand the video game industry from a novelty to a global industry, and ushered in the golden age of arcade video games. It was the inspiration for numerous video games and game designers across different genres, and has been ported and re-released in various forms. The 1980 Atari VCS version quadrupled sales of the VCS, thereby becoming the first killer app for video game consoles. More broadly, the pixelated enemy alien has become a pop culture icon, often representing video games as a whole.Designer Nishikado drew inspiration from games like 1976's ball-bouncing game Breakout and the 1975 shooter game Gun Fight, as well as science fiction narratives such as The War of the Worlds, Space Battleship Yamato, and Star Wars. To complete development of the game, he had to design custom hardware and development tools.To learn more about gaming refer to;
https://brainly.com/question/14226703
#SPJ1
describe one advantage of using QR codes rather than traditional barcodes. Explain how barcodes bring the advantage you have describes
Answers
The advantage of using QR codes rather than traditional barcodes is that QR codes are known to be quiet smaller.
Bar coding offers a lot of advantages such as the Reduction in errors.
Why are QR codes smaller?QR codes are known to be quiet smaller when compared to traditional barcodes.
Note that the QR code can be about 10 times smaller when compared to a bar code and are known to be still readable.
Therefore, based on the above, one can say that the The advantage of using QR codes rather than traditional barcodes is that QR codes are known to be quiet smaller. Bar coding offers a lot of advantages such as the Reduction in errors.
Learn more about barcodes from
https://brainly.com/question/13117502
#SPJ1
What is the rarest gun on surviv io
Answers
Answer: It's the M249
Explanation: I wanna get brainliest XD
Answer: Bippity Boopity the answer is yesity
Explanation: No
ANSWER:POST-TEST
direction encircle the letter of the correct answer..
1 .the written description accompanying the working drawing
2. a board made of plaster with covering of paper
3.a fire protection device that discharge water when the effect of a fire have been detected, such as when a predetermined temperature has been reached.
4.structural members in building construction that holds the ceiling board
5.the position or placement of lightning fixtures of the house.
with answer na din.
1.C
2.D
3.B
4.A
5.D
SANA MAKATULONG★☆☆
TLE
Answers
Answer:
1. Specifications.
2. Gypsum board.
3. Sprinkler systems.
4. Ceiling joist.
5. Lighting fixtures.
Explanation:
In Engineering, it is a standard and common practice to use drawings and models in the design and development of buildings, tools or systems that are being used for proffering solutions to specific problems in different fields such as banks, medicine, telecommunications and industries.
Hence, an architect or design engineer make use of drawings such as pictorial drawings, sketches, or architectural (technical) drawing to communicate ideas about a plan (design) to others, record and retain informations (ideas) so that they're not forgotten and analyze how different components of a plan (design) work together.
Architectural drawing is mainly implemented with computer-aided design (CAD) software and it's typically used in plans and blueprints that illustrates how to construct a building or an object.
1. Specifications: it's a well-written description that accompanies a working drawing used for designs and constructions.
2. Gypsum board: also referred to as drywall due to its inherent ability to resist fire. It's a type of board that's typically made of plaster with some covering of paper and it's used for ceilings, walls, etc.
3. Sprinkler systems: it's an automatic fire protection device that is typically designed to discharge a volume of water as soon as the effect of a fire is detected. For instance, when a predetermined or set temperature has been reached such as 69°C
4. Ceiling joist: structural members that are aligned or arranged horizontally in building construction in order to hold the ceiling board together.
5. Lighting fixtures: it's typically the position or placement of lightning fixtures of the house.
which of the following are the five modes available for users to set up in specter? question 22 options: open, secure, insecure, failing, aggressive secure, insecure, failing, aggressive, progressive open, secure, insecure, half secure, aggressive open, secure, failing, strange, aggressive
Answers
The five modes available for users to set up in Specter are **open, secure, insecure, failing,** and **aggressive**.
In the **open** mode, Specter will connect to any Wi-Fi network it encounters without user confirmation.
In the **secure** mode, Specter will only connect to known Wi-Fi networks and will require user confirmation for any new network.
In the **insecure** mode, Specter will connect to any Wi-Fi network it encounters without any encryption.
In the **failing** mode, Specter will only connect to a known Wi-Fi network if it meets certain criteria and will fail to connect to networks that don't meet those criteria.
In the **aggressive** mode, Specter will attempt to connect to any Wi-Fi network it encounters and will use brute-force methods to gain access.
To learn more about aggressive
https://brainly.com/question/30867018
#SPJ11
How are desktop and mobile operating systems similar?
Answers
Answer:
An operating system is a program that manages the complete operation of your computer or mobile device and lets you interact with it. False. Caps Lock is a toggle key. your welcome
Which filter enhances the color contrast around the edges of an image?
Answers
To increase the appeal of an image or video, edge enhancement is a type of image processing filter that increases the border contrast (apparent sharpness).
What is edge enhancement?Border Enhancement: This function tries to give the picture a little more sharpness. That is true, but excessive sharpening can also result in artefacts, such as a "halo effect" around the margins. Most of the time, this should be omitted. The human eye can distinguish shapes and outlines in low light, but it cannot distinguish finer details because it cannot see edges of objects in higher contrast (edge enhancement).At first look, this might appear to have more detail, but in reality it hides fine detail, and excessive sharpening can give objects a halo. Therefore, turn it way down or off entirely.To learn more about edge enhancement, refer to:
https://brainly.com/question/29451683
how to create an e mail account
Answers
Answer:
Go into setting; go to accounts; look for create account or add account; it will then come up with a tab asking what you want to create the for ( choose Email) it will ask who you want to create it for (yourself or Bussiness), you choose whichever you want and then fill in your information.
Hope this helps....
Explanation:
Image a response where a Web browser returns an outdated cached page instead of a more recent one that had been updated at the server. Do you consider this as a failure, and if so, what kind of failure?
Answers
Returning an outdated cached page instead of a recent one can be considered a failure in delivering up-to-date content to users, specifically a cache coherence failure.
When a web browser returns an outdated cached page instead of a more recent one updated at the server, it can be considered a failure in terms of delivering the most up-to-date content to the user. This type of failure is commonly known as a "cache coherence failure" or "cache inconsistency."
Caching is a technique used by web browsers to store copies of web pages locally on the user's device.
This helps improve performance by reducing the need to fetch content from the server every time a user requests a page. However, caching can lead to issues when the cached version of a page becomes outdated.
In the scenario described, the web browser fails to update its cached copy of the page, resulting in the user seeing an older version instead of the latest content. This can be problematic, especially for dynamic websites where the content frequently changes.
From a user perspective, encountering an outdated cached page can be frustrating as it undermines their expectation of receiving the most recent information. It can lead to confusion, inaccuracies, and potentially impact user experience and decision-making.
To address this failure, web developers and administrators employ various techniques. These include setting appropriate caching headers and expiration times on web pages, implementing cache validation mechanisms like ETags or Last-Modified headers, or utilizing cache-busting techniques such as appending version numbers to resource URLs.
In conclusion, the situation where a web browser returns an outdated cached page instead of a more recent one can be considered a failure in delivering up-to-date content to the user.
It falls under the category of cache coherence failure or cache inconsistency, highlighting the need for effective caching strategies and cache management techniques to ensure a seamless browsing experience.
Learn more about cached page:
https://brainly.com/question/30706463
#SPJ11
How do computers hold integers greater than 255?
Answers
Answer:
It depends on the number of bits you use. In your example, you've used an 8 bit (one byte) number, which does max out at 255. Ever since forever, computers have used numbers that are larger than one byte. For when that isn't enough, Fortran includes the 'double precision' numbers which use 8 bytes.
Explanation:
While making a digital portfolio, Sarah wants to add names and contact information of people she knows professionally. What should she
Include regarding these people?
Sarah should include
letters regarding names and contact information of people she knows professionally.
Reset
Next
Answers
In adding names and contact in a digital portfolio, Sarah should include the full name, street address, city, state, and zip code, and contact information.
What is a digital portfolio?A digital portfolio is an electronic portfolio where a person includes it blog, names, pictures, texts, etc.
Thus, In adding names and contact in a digital portfolio, Sarah should include the full name, street address, city, state, and zip code, and contact information.
Learn more about digital portfolio
https://brainly.com/question/23758218
#SPJ1
Which of the following describes why graphical interfaces quickly became popular after their introduction to the mass market?
A.superior usability
B.form over function
C.strong ISO standards
D.contextual design analysis of a market demographic
Answers
A.superior usability
you are working on a project to build an encrypted messaging platform. the platform has undergone several iterations and recently your organization has expanded. as part of this expansion you will be taking on two junior developers. you have been asked to bring them up to speed on the project quickly and ensure that they get all the support required for them to move into senior developer positions in due time. you want to make sure that their needs are met. what should you do?
Answers
To bring the junior developers up to speed quickly and ensure they have the support they need to move into senior developer positions.
The recommended procedure is as follow:
Provide thorough onboarding and training: Make sure the new developers have a clear understanding of the project's goals, architecture, and codebase. Provide them with any relevant documentation and resources to help them get up to speed quickly.Assign a mentor: Pair each junior developer with a senior developer who can serve as a mentor and guide them through the project. This will give the junior developers a point of contact for any questions or concerns they may have.Set clear expectations: Clearly communicate the expectations for the junior developers' role and performance. This will help them understand what is expected of them and how they can succeed in their new position.Provide regular feedback: Provide the junior developers with regular feedback on their performance and progress. This will help them understand what they are doing well and where they need to improve.Encourage collaboration: Encourage the junior developers to work with their peers and senior developers. This will help them learn new skills and best practices, and will also foster a sense of teamwork and camaraderie within the organization.Offer opportunities for growth: Provide the junior developers with opportunities to take on more responsibility and learn new skills. This will help them grow as developers and prepare them for senior developer positions in the future.To learn more about junior developers, visit: https://brainly.com/question/29989649
#SPJ4
You cannot remember the address of Kayah’s website. What type of tool will help you
locate/find it by typing in keywords to look for it?
Answers
Answer:
A search engine
Explanation:
View the pdf
give a summary of html forms
Answers
HTML forms are used to collect data from users. Users essentially enter data into forms by filling in text fields, selecting toggles and making choices from selection objects. When the user has filled in the data it is transmitted to the server for processing. HTML forms are specified using the <form> element.
Hope this helps you!
which approach to data analytics attempts to characterize the typical behavior of an individual, group or population by generating summary statistics about the data?
Answers
The approach to data analytics that attempts to characterize the typical behavior of an individual, group, or population by generating summary statistics about the data is called descriptive analytics.
Descriptive analytics focuses on understanding and summarizing data to gain insights into patterns, trends, and central tendencies. It involves the use of statistical techniques to calculate measures such as mean, median, mode, standard deviation, and percentiles. These summary statistics provide a high-level overview of the data and help in describing the characteristics and behavior of the individuals, groups, or populations under study.
By analyzing and interpreting these summary statistics, analysts can identify key features of the data, detect outliers, and make informed decisions based on the observed patterns and trends. Descriptive analytics serves as a fundamental step in data analysis, providing a foundation for further exploration and inference.
Learn more about data analytics here:
https://brainly.com/question/23860654
#SPJ11
What are characteristics of the Advanced Calendar options in Outlook? Check all that apply.
Meeting responses can be tracked.
Free/busy settings can be enabled.
Multiple calendars can be managed.
One extra time zone can be created.
Display and theme settings can be changed.
Options are accessed through the Backstage view.
Answers
Answer:
b,d,e,f
Explanation:
The characteristics of the Advanced Calendar options in Microsoft Outlook are:
B. Free/busy settings can be enabled.
D. One extra time zone can be created.
E. Display and theme settings can be changed.
F. Options are accessed through the Backstage view.
What is Microsoft Outlook?Microsoft Outlook can be defined as a personal information (e-mail) manager and task management software application that is designed and developed by Microsoft Inc.
Functions of Microsoft OutlookSome of the functions of Microsoft Outlook include the following:
e-mail clientTask managementContact management Taking of notes Journal loggingWeb browsingCalendaringThe calendar is a scheduling and time management component of Microsoft Outlook which is fully integrated and can be synchronized with contacts, e-mail, and other Outlook features.
Read more on Microsoft Outlook here: https://brainly.com/question/24266817
What does the statement mean “To take a photograph is to participate in another’s person’s mortality, vulnerability, and mutability?
Answers
Answer:
probuly to take a photograph of ur childhood
Explanation:
idk
Answer:
To take photograph is to participate in another’s person’s mortality, vulnerability, and mutability. That means when you take a picture of someone you are participating in their lives, it may be just a small fragment of that life, but it still is a life.
Explanation:
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
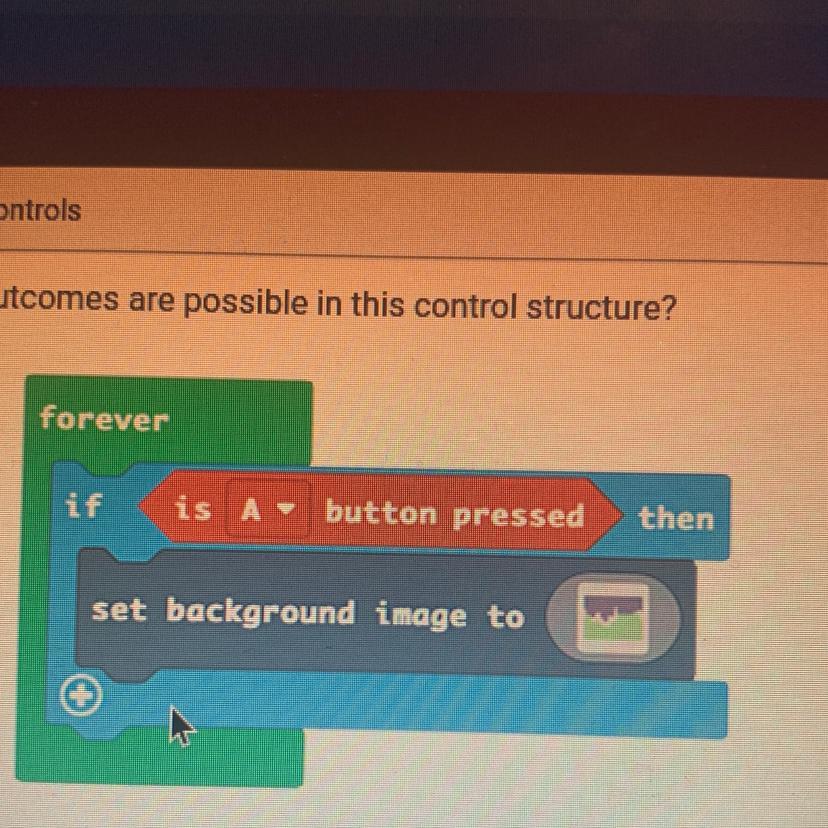
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
a force from water that brings water to your house
Answers
Answer:
hydroenergy hope that will help you in the future
Assume the following rule is the only one that styles the body element:_______.
body{
font-family: Cursive, Helvetica, Verdana;
}
What happens if the browser doesn't support any of these font families?
A. The text will be displayed in the default browser font-family
B. The text will not be displayed
C. The text will be displayed in Cursive
Answers
Answer:
The answer is A, it will substitute those font families for the default font family.
what does the binary odometer show about representing large numbers
Answers
Answer and Explanation:
The binary odometer represents the large number to judge that what happened when there is a large number that gets too large
Here we visit the level 2 of the binary odometer widget in the chapter of Code studio
This represents a widget that reproduced an odometer of a car in which the tracking of a device could be known that how much far the car is driven with respect to the miles or kilometers
An odometer, also known as an odograph measures the distance that a vehicle (including bicycles, and cars) has travelled
What the binary odometer shows about representing large numbers is that more a number larger than the number displayable will cause it to roll-over overflow error and therefore, a new system will be required
A binary odometer is an odometer based on the binary number system of 1s and 0s
When the values represented by the binary odometer is very large such that the value exceeds the largest number it can display, such as having all 1s, the odometer rolls-over, and restarts with a 1 at the right while the rest digits are 0s, that is the odometer rolls over
Therefore, representing large numbers requires more resources such as new odometer that can show large numbers
Learn more about binary odometer here:
https://brainly.com/question/4922102
on windows 10, using storage spaces eliminates the need for which of the following tasks? (select two).
Answers
On Windows 10, using Storage Spaces eliminates the need for manual disk management and third-party RAID implementations.
What tasks does using Storage Spaces on Windows 10 eliminate?
Using Storage Spaces on Windows 10 eliminates the need for manual disk management by providing a unified interface to manage multiple drives as a single logical volume.
It also eliminates the need for implementing third-party RAID solutions, as Storage Spaces offers built-in data redundancy and fault tolerance features.
With Storage Spaces, users can easily create storage pools, combine drives of different sizes, and configure data protection options without relying on separate disk management tools.
This simplifies the process of organizing and managing storage, improving efficiency and reducing complexity for users.
Storage Spaces provides the flexibility to expand storage capacity by adding more drives to the pool without disrupting data accessibility.
Learn more about manual disk
brainly.com/question/32110688
#SPJ11
The location of a specific input or output field device is identified by the processor by means of its _____.
Answers
The location of a specific input or output field device is identified by the processor by means of Address
When it comes to input and output devices, the processor needs to know the address of each device in order to communicate with it. The address is like a unique identifier for each device, and it tells the processor where to find the device in memory.
There are two main ways that processor addresses can be assigned to devices. The first is called static addressing, and the second is called dynamic addressing.
With static addressing, the address of a device is fixed and does not change. This means that the processor always knows where to find the device, and there is no need for the address to be stored in memory.
Dynamic addressing is a bit more complex. The address of a device can change depending on the current conditions, and so the processor needs to store the address in memory. This means that the processor has to search for the device every time it wants to communicate with it, which can take up more time and resources.
Learn more about addressing here:
https://brainly.com/question/17191250
#SPJ4
A business analyst compares 2017 daily sales to 2018 daily sales using descriptive statistics for each. In 2017, the standard deviation of daily sales was 73.87, while in 2018 the standard deviation of daily sales was 136.32. The analyst could conclude that ____________.
Answers
Answer:
The analyst could conclude that there was more variation in sales in 2018.
Explanation:
Given
\(SD_{2017} = 73.87\)
\(SD_{2018} = 136.32\)
Required
Conclusion about the standard deviations
In statistics, standard deviation gives the average variation in the data being measured.
The standard deviation of 2018 is more than that of 2017. This implies that, in 2018, there is more variation in daily sales compared to 2017
So, the analyst could conclude that there was more variation in sales in 2018.
Why did we decide to send a message as a sequence of two options rather than modifying our devices to represent more options?
Answers
Answer:
Following are the solution to this question:
Explanation:
Please find the complete question in the attachment file.
The binary message is also an XML text SMS, which is used to represent in binary character. It may also flag the binary text as binary, and it can attach the UDH as just the start of its message. In this question, we assume that you can include A and B because there could be no more than 2 choices in such a binary message.

We decided to send a message as a sequence of two states (A and B) rather than modifying our devices to represent more states (State C, State D, State E, etc.) primarily for simplicity and efficiency.
Using a binary communication system with just two states is straightforward and easier to implement than introducing more complex modifications for additional states.
Binary communication allows for clear and unambiguous encoding and decoding, making it more reliable and less prone to errors.
While using more states could potentially convey more information, it would also require more complex hardware and software, increasing the risk of communication errors and complicating the overall system design and operation.
Know more about binary communication:
https://brainly.com/question/32447290
#SPJ3
Your question is incomplete, but most probably your full question was.
Why did we decide to send a message as a sequence of state (A and B) rather than modifying our devices to represent more State (State C, State D, State E,....)?
Describe the contents of a basic program outline.
Answers
Answer:
Oneday
Explanation:
ONEDAY WE WILL BE ABLE TO DO IT!
what is the fullform of COMPUTER?
Answers
Answer:
COMPUTER stands for Common Operating Machine Purposely Used for Technological and Educational Research
Explanation:
Task 4
Write Fe is the statement is about the file explorer, and MC if it is for my computer
1. it allows user to access the local drivers
2.you can put your favorite application in this management
3.it prodives the GUI for accessing file system
4.the storage of the computer can be seen here
5.you can see the storage condition of any connected drive here
6.there is a default folders and file here instantly
7.you can view different folders and file here instantly
8. if you insert a flash drive on your computer you can check the storage in this area
9.the desktop documents downloads music pictures videos are the default folders here
10.it previous mane in windows explorer
Answers
Statement about file explorer and my computer are given below.
1)Fe - it allows the user to access the local drives. The file explorer provides a graphical interface for users to navigate and access the files and folders on their local drives.
2)MC - you can put your favorite application in this management.
This statement is related to the computer's desktop or start menu, where users can organize shortcuts to their favorite applications or programs.
3)Fe - it provides the GUI for accessing the file system. The file explorer provides a graphical user interface (GUI) that allows users to interact with the file system.
4)MC - the storage of the computer can be seen here. This statement refers to the computer's storage capacity, including the primary hard drive and any additional drives.
5)Fe - you can see the storage condition of any connected drive here.
6)Fe - there are default folders and files here instantly. When opening the file explorer, there are usually default folders and files displayed instantly.
7)Fe - you can view different folders and files here instantly. The file explorer allows users to view and navigate through different folders and files instantly.
8)MC - if you insert a flash drive on your computer, you can check the storage in this area.
9)MC - the desktop, documents, downloads, music, pictures, and videos are the default folders here.
10)Fe - it was previously named Windows Explorer.
For more questions on file explorer
https://brainly.com/question/30320716
#SPJ8
define a touch-sensitive pad and state one use
Answers
Answer:
A touch pad is a device for pointing (controlling input positioning) on a computer display screen. It is an alternative to the mouse. Originally incorporated in laptop computers, touch pads are also being made for use with desktop computers. A touch pad works by sensing the user's finger movement and downward pressure.
Explanation: