alice sends a message to bob that is intercepted by trudy. which scenario describes an availability violation?
Answers
An availability violation scenario in the given context would be if Trudy intercepts Alice's message and prevents Bob from receiving it, causing a disruption in the communication between Alice and Bob.
Availability is one of the fundamental principles of information security that ensures timely and uninterrupted access to data and resources by authorized users. In the given scenario, if Trudy intercepts the message sent by Alice to Bob, it results in an availability violation because Bob is unable to receive and access the message as intended.
Availability violations can occur through various means, such as network disruptions, denial-of-service attacks, unauthorized access, or interception by malicious actors. In this case, Trudy's interception disrupts the availability of the communication channel between Alice and Bob. The message intended for Bob is no longer accessible, leading to a violation of the availability principle. To maintain availability, it is essential to protect the communication channels, ensure secure transmission, and implement measures to prevent unauthorized interception and disruptions.
Learn more about communication channels here:
https://brainly.com/question/25630633
#SPJ11
Related Questions
What is the HTML code symbol to the !nstagram Facts Part 2?
FIRST ONE GETS BRAINEST!!

Answers
¶^↑↓→← html code symbol
which of the following statements is false? a. the first generation of computer languages is machine language. b. the second generation of computer languages is assembly language. c. the third generation of computer languages is high-level language. d. the fourth generation of computer languages is natural language processing.
Answers
The statement that is false is, D. The fourth generation of computer languages is not natural language processing.
Natural language processing is a type of artificial intelligence that allows computers to understand and process human language.
Natural language processing (NLP) is a branch of artificial intelligence that enables computers to understand, interpret and manipulate human language. NLP is used to analyze written and spoken language and extract actionable insights from it. It is used in a variety of applications, such as machine translation, information retrieval, automated customer service, text summarization, sentiment analysis, question answering, and more.
NLP algorithms use natural language processing techniques such as text analysis, natural language understanding, and natural language generation to process and understand human language. NLP algorithms can take various forms, such as rule-based systems, statistical models, and machine learning models.
Learn more about Natural language processing (NLP):
https://brainly.com/question/28039408
#SPJ4
data link layer protocol defined by ieee specification 802.1dT/F
Answers
The statement, data link layer protocol defined by IEEE specification is false.
The IEEE specification 802.1d does not define a data link layer protocol.
The data link layer protocol defined by IEEE specification 802.1d is called Spanning Tree Protocol (STP). It is used to prevent loops in a network by disabling redundant links. The 802.1t amendment introduced Rapid Spanning Tree Protocol (RSTP), which improves the convergence time of STP. The 802.1s amendment introduced Multiple Spanning Tree Protocol (MSTP), which allows for multiple instances of STP to be run on a single switch.
The IEEE 802.1d standard, also known as the Spanning Tree Protocol (STP), is a network protocol that operates at the data link layer (Layer 2) of the OSI model. It provides a mechanism for preventing loops in Ethernet networks by creating a loop-free logical topology. The STP algorithm determines the best path to reach each network segment and blocks redundant paths to prevent loops.
However, it is important to note that the IEEE 802.1d standard does not define a specific data link layer protocol. Instead, it specifies the operation of the Spanning Tree Protocol and its implementation details. The actual data link layer protocol used in Ethernet networks is defined by the IEEE 802.3 standard, which includes various Ethernet protocols such as Ethernet II, Fast Ethernet, and Gigabit Ethernet.
For more questions on data link layer protocol: https://brainly.com/question/29760365
#SPJ11
LightZone Inc., a manufacturer of LED lamps, uses a software to create programmed instructions for its automated equipment to ensure that its products are made as efficiently as possible. In this scenario, LightZone most likely uses _____ to program the automated equipment.
Answers
Computer aided manufacturing (CAM) is commonly known as a software tool/program. In the scenario stated, LightZone most likely uses computer-aided manufacturing software to program the automated equipment.
Computer aided manufacturing (CAM) software is simply known a s a computer program that makes use of numerical control (NC) so as to make a well thorough instructions which are called the G-code.This codes are known to drive CNC machines. CAM software often narrow the machining process and automates actions such as drilling and cutting. It therefore create high-quality manufacturing.
Learn more from
https://brainly.com/question/13918120
In Excel, which direction does a Row go and does it use letters or numbers to track the cells? A. Vertical and Letters B. Vertical in numbers C. Horizontal and numbers D. Horizontal and Letters
Answers
Answer:
In Excel, a Row goes horizontally and uses numbers to track the cells. (Option D. Horizontal and Numbers)
What is remote viewing CCTV?
Answers
The full form of CCTV is generally known as closed circuit television.
What is CCTV?CCTV is an abbreviation for closed circuit television and it can be defined as a television system that makes use of video cameras to privately transmit digital signals to a specific location (place), especially for the purpose of security surveillance and monitoring of an environment.
The importance of CCTV is that it ultimately implies that, a closed circuit television (CCTV) is primarily used for enhancing the security of a location wherein it is installed.
Therefore, The full form of CCTV is generally known as closed circuit television.
Learn more about CCTV on:
brainly.com/question/23348225
#SPJ1
Sports photography is not included in news coverage.
True
False
Answers
Answer:
False yes it is
Explanation:
Is it necessary to follow a writing process when preparing a short message? a long message? why or why not?
Answers
For short messages, it helps ensure clarity, conciseness, and effective communication.
For long messages, it aids in organization, engagement, completeness, and revisions to maintain coherence and achieve communication goals.
Short Message:
1. Clarity and Conciseness: It allows you to focus on the main point and convey it effectively within a limited space.
2. Tone and Impact: Going through a writing process can help you choose the appropriate language, structure, and format to convey your message in a way that resonates with the recipient.
3. Proofreading and Editing: Regardless of the message length, proofreading and editing are crucial to avoid errors and improve the overall quality of the message. Following a writing process allows you to review and refine your short message, ensuring it is error-free and well-presented.
Long Message:
1. Organization and Structure: Planning and outlining your thoughts through a writing process can help you structure your ideas, include relevant details, and maintain a logical progression.
2. Audience Engagement: A writing process allows you to consider the needs and expectations of your audience, choose an appropriate writing style, and incorporate strategies to keep readers engaged.
3. Consistency and Completeness: Long messages may contain multiple sections or complex information.
Learn more about Message Writing here:
https://brainly.com/question/11290887
#SPJ4
You are working as a project manager. One of the web developers regularly creates dynamic pages with a half dozen parameters. Another developer regularly complains that this will harm the project’s search rankings. How would you handle this dispute?
Answers
From the planning stage up to the deployment of such initiatives live online, web project managers oversee their creation.They oversee teams that build websites, work with stakeholders to determine the scope of web-based projects, and produce project status report.
What techniques are used to raise search rankings?
If you follow these suggestions, your website will become more search engine optimized and will rank better in search engine results (SEO).Publish Knowledgeable, Useful Content.Update Your Content Frequently.facts about facts.possess a link-worthy website.Use alt tags.Workplace Conflict Resolution Techniques.Talk about it with the other person.Pay more attention to events and behavior than to individuals.Take note of everything.Determine the points of agreement and disagreement.Prioritize the problem areas first.Make a plan to resolve each issue.Put your plan into action and profit from your victory.Project managers are in charge of overseeing the planning, execution, monitoring, control, and closure of projects.They are accountable for the project's overall scope, team and resources, budget, and success or failure at the end of the process.Due to the agility of the Agile methodology, projects are broken into cycles or sprints.This enables development leads to design challenging launches by dividing various project life cycle stages while taking on a significant quantity of additional labor.We can use CSS to change the page's background color each time a user clicks a button.Using JavaScript, we can ask the user for their name, and the website will then dynamically display it.A dynamic list page: This page functions as a menu from which users can access the product pages and presents a list of all your products.It appears as "Collection Name" in your website's Pages section.To learn more about search rankings. refer
https://brainly.com/question/14024902
#SPJ1
Explain any TWO (2) data information that shall be covered under "Safety Data Sheet" and elaborate why do you think the information is needed
Answers
Safety data sheets include details about chemical items that assist users in evaluating the risks. They outline the risks the chemical poses and include details on handling, storage, and emergency procedures in the event of an accident.
The properties of each chemical, its physical, health and environmental properties, protective measures, and precautions for handling, storage and transportation of the chemical are contained in a safety data sheet (formerly called safety data sheet).
Provides recommendations for each individual chemical on topics such as:
PPE, or personal protective equipmentfirst aid techniquescleanup procedures for spillsTo learn more on Safety Data Sheets, here:
https://brainly.com/question/28244620
#SPJ4
____, as a technique, is quite similar to e-mail bombing. However, it is accomplished differently and involves enrolling potentially hundreds of target users through e-mail lists and distributed e-mail message systems
Answers
The technique that is quite similar to e-mail bombing, but accomplished differently by enrolling potentially hundreds of target users through e-mail lists and distributed e-mail message systems, is known as list bombing or subscription bombing.
List bombing, also known as subscription bombing, is a technique that shares similarities with e-mail bombing. However, it differs in the approach used to overwhelm the target. Instead of flooding the target's inbox with a large number of individual emails, list bombing involves enrolling numerous target users into subscription lists or mailing lists without their consent. This can be achieved by exploiting vulnerabilities in the subscription process or by utilizing automated tools to submit subscription requests. The intention is to inundate the target with a high volume of unwanted emails, potentially causing disruption or overwhelming their resources.
Learn more about e-mail here:
https://brainly.com/question/29532673
#SPJ11
What is the result when you run the following line of code after a prompt??
>>>print(3 + 11)
Answers
Answer:
The following output is 14
Explanation:
When you print something, python interprets it and spits it out to the console. In this case, python is just interpreting 3 + 11, which equals 14. Thus, making the answer 14.
hope i helped :D
Answer:
14
Explanation:
Extensive research undertaken by the respected game analytics company, Quantic Foundry, categorises players using twelve different motivations:
• Destruction. "Guns. Explosives. Chaos. Mayhem." • Excitement. "Fast-Paced. Action. Surprises. Thrills." • Competition. "Duels. Matches. High on Ranking." • Community. "Being on Team. Chatting. Interacting." • Challenge. "Practice. High Difficulty. Challenges." • Strategy. "Thinking Ahead. Making Decisions." • Completion. "Get All Collectibles. Complete All Missions." • Power. "Powerful Character. Powerful Equipment." • Fantasy. "Being someone else, somewhere else." • Story. "Elaborate plots. Interesting characters." • Design. "Expression. Customization." • Discovery. "Explore. Tinker. Experiment."
Where possible, map the twelve Quantic Foundry motivations onto the eight Player Types (Griefers, Politicians, Opportunists, Planners, Scientists, Gurus, Networkers, Politicians). Where not possible, outline why it isn’t possible.
Answers
Quantic Foundry is a well-known game analytics company that has conducted extensive research and classified players into twelve different categories based on their motivations.
The twelve motivations are Destruction, Excitement, Competition, Community, Challenge, Strategy, Completion, Power, Fantasy, Story, Design, and Discovery.
Below is the mapping of these motivations onto the eight Player Types:Griefers:
The motivation of Destruction maps well with Griefers since they are players who take pleasure in destroying the gaming experience of other players. Destruction is their ultimate motivation.
Politicians: The motivation of Community maps well with Politicians since they are players who enjoy being on teams, communicating, and interacting with other players.
Opportunists: The motivation of Completion maps well with Opportunists since they are players who enjoy collecting items, completing missions, and achieving goals.
Planners: The motivation of Challenge maps well with Planners since they enjoy practicing, facing difficult challenges, and overcoming obstacles.
Scientists: The motivation for Discovery maps well with Scientists since they enjoy exploring, experimenting, and discovering new things.
Gurus: The motivation of Fantasy maps well with Gurus since they enjoy being someone else and somewhere else in the game.
Networkers: None of the Quantic Foundry motivations maps well with Networkers since they are players who enjoy building relationships with other players, which is not covered in the twelve motivations. Therefore, it is not possible to map any of the twelve motivations onto Networkers.
Politicians: The motivation of Design maps well with Politicians since they enjoy expressing themselves and customizing their gaming experience.
Learn more about analytics
https://brainly.com/question/30101345
#SPJ11
You want to use a computer to make a painting of your backyard to go along with a story you wrote. Which software would be appropriate? Choose all that apply.
Adobe Photoshop
LibreOffice Calc
LibreOffice Draw
Internet Explorer
GIMP
the answer is A, C, E
Answers
Answer:
A, C, and E
Explanation:
I did the math
What does else do in an if/else statment?
O Gives the if statement a command to run if the condition is false
O Runs a command regardless of whether the condition is tru or false
O Determines whether the condition is true or false
O Tells the condition which code to run
Answers
Answer:
Gives the if statement a command to run if the condition is false
with a satellite phone system, you can call anywhere in the
Answers
With a satellite phone system, you can call anywhere in the world as long as you have a clear line of sight to a satellite.
Satellite phones operate on a different frequency than traditional cellular phones, which allow for communication over large distances. One type of mobile phone that is not commonly used is the satellite phone. It's a wireless phone, but it doesn't use cell towers like a typical cell phone. Instead, it communicates directly with satellites orbiting the planet.To make a call, the user must dial the phone number of the person they want to call and then press the call button. The signal is then sent to a satellite in orbit, which then routes the call to its destination.
More Questions on Satellites: https://brainly.com/question/18496962
#SPJ11
What are the effects of air pollution on human life.
Answers
Answer:
Heart disease
Lung cancer
Respiratory infection
Explanation:
Air pollution is very dangerous to human health or contains lots of dust particles and air particulate. When these air pollutants get into the body through different external openings it can be very detrimental to the human body.
Write a MATLAB code segment that assumes two variables are set:
PT - 1x2 matrix representing an X,Y coordinate
D - single real number
The code segment should set the variable R to the word 'HIT', 'CLOSE' or 'MISS' depending on the distance from PT to the origin. Set to HIT if the distance is less than or equal to D, CLOSE if the distance is between D and 2*D, or MISS if the distance is greater than or equal to 2*D.
Answers
The MATLAB code segment provided below sets the variable R to 'HIT', 'CLOSE', or 'MISS' based on the distance between a given coordinate PT and the origin, relative to a provided value D.
The code segment calculates the distance between the coordinate PT and the origin using the Euclidean distance formula. It then compares this distance with the value D and assigns the appropriate label to the variable R. If the distance is less than or equal to D, R is set to 'HIT'. If the distance is between D and 2D, R is set to 'CLOSE'. Otherwise, if the distance is greater than or equal to 2D, R is set to 'MISS'.
PT = [x, y]; % Set the coordinates of PT as a 1x2 matrix [x, y]
D = 5; % Set the value of D
% Calculate the distance between PT and the origin
distance = norm(PT);
% Check the distance and assign the appropriate label to R
if distance <= D
R = 'HIT';
elseif distance > D && distance <= 2*D
R = 'CLOSE';
else
R = 'MISS';
end
In the code segment, you need to replace [x, y] with the actual values of the X and Y coordinates for PT. The norm() function calculates the Euclidean distance, which is the square root of the sum of squares of the coordinates. The code then checks the distance against the provided criteria and assigns the corresponding label to the variable R.
Learn more about code here: https://brainly.com/question/30029994
#SPJ11
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
plllsssssss i have a test rn for computer science in code hs 3.2.1: Fetch
pllss i need the answer asap tyy
Answers
Using the knowledge in computational language in python it is possible to write a code that made the functions and Fetch.
Writting the code:def getInfo(sc: SparkContext, startDate:String, cachingValue: Int, sparkLoggerParams: SparkLoggerParams, zkIP: String, zkPort: String): RDD[(String)] = {{
val scan = new Scan
scan.addFamily("family")
scan.addColumn("family","time")
val rdd = getHbaseConfiguredRDDFromScan(sc, zkIP, zkPort, "myTable", scan, cachingValue, sparkLoggerParams)
val output: RDD[(String)] = rdd.map { row =>
(Bytes.toString(row._2.getRow))
}
output
}
def getHbaseConfiguredRDDFromScan(sc: SparkContext, zkIP: String, zkPort: String, tableName: String,
scan: Scan, cachingValue: Int, sparkLoggerParams: SparkLoggerParams): NewHadoopRDD[ImmutableBytesWritable, Result] = {
scan.setCaching(cachingValue)
val scanString = Base64.getEncoder.encodeToString(org.apache.hadoop.hbase.protobuf.ProtobufUtil.toScan(scan).toByteArray)
val hbaseContext = new SparkHBaseContext(zkIP, zkPort)
val hbaseConfig = hbaseContext.getConfiguration()
hbaseConfig.set(TableInputFormat.INPUT_TABLE, tableName)
hbaseConfig.set(TableInputFormat.SCAN, scanString)
sc.newAPIHadoopRDD(
hbaseConfig,
classOf[TableInputFormat],
classOf[ImmutableBytesWritable], classOf[Result]
).asInstanceOf[NewHadoopRDD[ImmutableBytesWritable, Result]]
}
See more about python at brainly.com/question/18502436
#SPJ1

what are the answers for theses question?




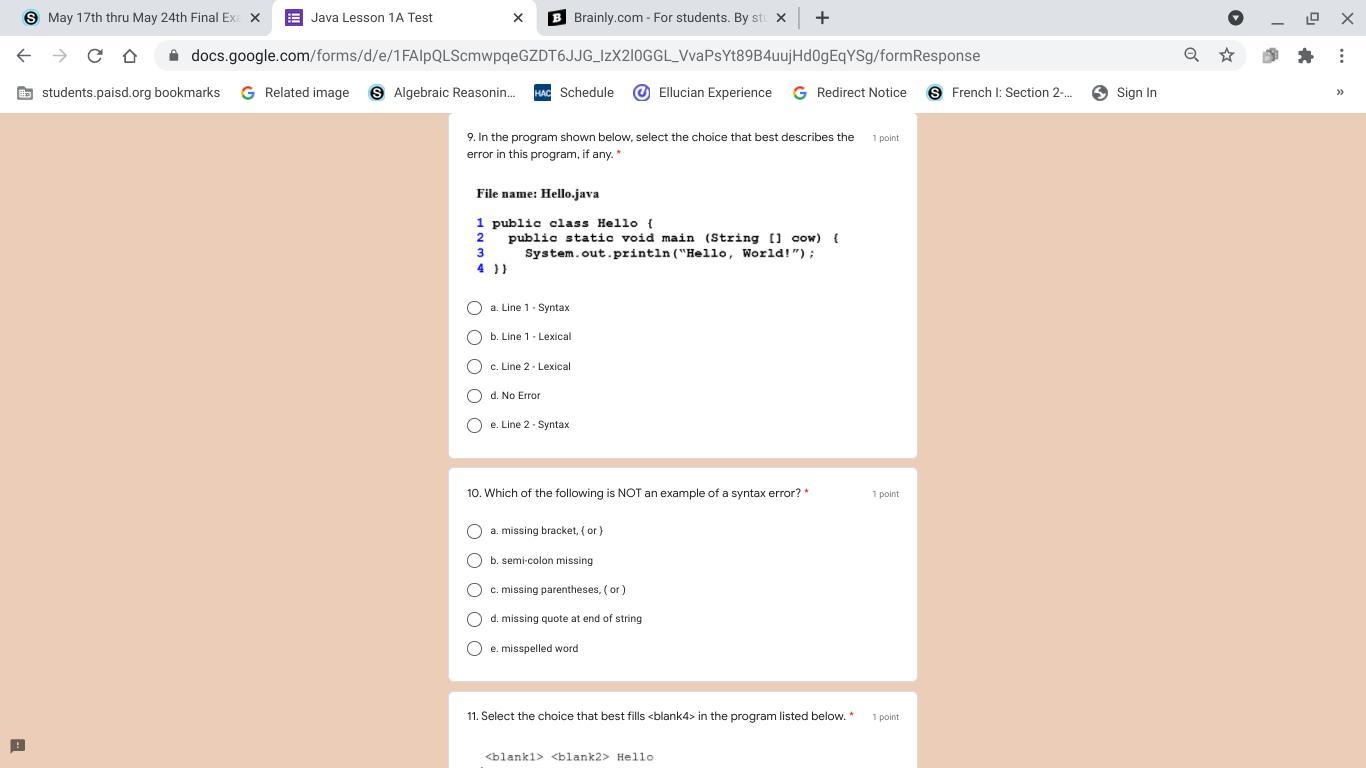
Answers
Answer: me no comprende coding
Explanation:
sorry
What is the purpose of the CC option in an email?
A.
Create a carbon copy of the message.
B.
Save the message as a template for future use.
C.
Send a copy of the message to one or more people.
D.
Forward a message to multiple recipients.
( Edmentum MSE )
Answers
Answer:
c
Explanation:
send a copy of the messege
After the following code executes what are the values in array2? (2 points):
int[] array1 (6, 3, 9, 1, 11);
int[] array2 = (0, 0, 0, 0, 0);
int a2 = 0;
for (int al = 0; al < array1.length - 1; a1++)
(
}
if (array1[al] >= 5)
(
}
array2 [a2] = array1[al];
a2++;
(A) (0, 0, 0, 0, 0);
(B) (6, 9, 0, 0, 0);
(C) (6, 0, 9, 0, 11);
(D) {6, 9, 11, 0, 0);
(E) (6, 3, 9, 1, 11); by
Answers
Answer:
After this code executes, the values in array2 would be (6, 9, 0, 0, 0) because the code loops through array1 and checks if each element is greater than or equal to 5. If it is, the element is added to array2 and a2 is incremented. In this case, array1 has two elements that are greater than or equal to 5, which are 6 and 9. So array2 will have those values in the first two elements, and the remaining elements will be 0. Therefore, the answer is (B) (6, 9, 0, 0, 0)
a support desk technician is asking a customer a series of questions about a problem connecting to the network. which step of the troubleshooting process is the technician applying?
Answers
When a support desk technician is asking a customer a series of questions about a problem connecting to the network, the step of the troubleshooting process that the technician is applying is the problem identification step.
This step is the first and most important step in the troubleshooting process. The identification step involves the following processes: Identify and isolate the problem. Identify the source of the problem. Identify the symptoms that the user is experiencing. Collect information and review data to help with problem identification.
If the problem is difficult to identify or requires additional analysis, it may require the support of higher-level technical support, such as network engineers, to determine the cause and develop a solution. Once the problem has been identified, the support technician can move on to the next step of the troubleshooting process, which is the analysis phase.
The analysis phase involves investigating the cause of the problem and developing a solution or workaround to the issue. After that, the support technician can move on to the resolution phase, which involves implementing the solution or workaround, testing the solution to ensure it is working properly, and communicating the resolution to the customer.
To know more about troubleshooting visit:
https://brainly.com/question/29022893
#SPJ11
Find solutions for your homework
Find solutions for your homework
businessaccountingaccounting questions and answersconsider the following 3-step worker-paced series of machine-related tasks. each worker is dedicated to a single step. each step employs a single worker. workers are relieved for two 15 minute breaks and a half hour lunch so that the operation runs throughout a 8 hour shift each day. set up represents time in minutes a worker spends setting up the
Question: Consider The Following 3-Step Worker-Paced Series Of Machine-Related Tasks. Each Worker Is Dedicated To A Single Step. Each Step Employs A Single Worker. Workers Are Relieved For Two 15 Minute Breaks And A Half Hour Lunch So That The Operation Runs Throughout A 8 Hour Shift Each Day. Set Up Represents Time In Minutes A Worker Spends Setting Up The
student submitted image, transcription available below
student submitted image, transcription available below
student submitted image, transcription available below
student submitted image, transcription available below
Show transcribed image text
Expert Answer
1st step
All steps
Final answer
Step 1/3
1) The time for each step = setup time + run time*...
View the full answer
answer image blur
Step 2/3
Step 3/3
Final answer
Transcribed image text:
Consider the following 3-Step worker-paced series of machine-related tasks. Each worker is dedicated to a single step. Each step employs a single worker. Workers are relieved for two 15 minute breaks and a half hour lunch so that the operation runs throughout a 8 hour shift each day. Set up represents time in minutes a worker spends setting up the workstation prior to running an ORDER. Run Time represents time in minutes required per UNIT for the Step to be completed. The company accepts only multi-Unit orders and has operations in Jacksonville, FL; Denver, CO and Nashville, TN. STEP 1 STEP 2 STEP 3 etermine which step is the Bottleneck if the plant only accepts 3 unit orders. At what specific order size (Units per Order) would the Bottleneck move to an alternative step? Since at each of the three facilities production tasks are worker-paced, were we to visit the Denver, CO plant we would MOST likely see Work-InProcess Inventory (WIP) before Step(s) ? Step 2 Step 3 Step 1 Steps 1&2 No WIP accumulates The Company is considering an adjustment to its production pacing policy to take into account the operational impact of its Bottleneck. If it decides to move to Bottleneck Pacing it should expect to reduce Work in Process (WIP) Inventory, but trade off longer Throughput Time (TPT). True False
Answers
The given question presents a 3-step worker-paced series of machine-related tasks. Each step employs a single worker, and workers have two 15-minute breaks and a half-hour lunch during an 8-hour shift.
The question involves determining the bottleneck step, identifying the order size at which the bottleneck would shift to an alternative step, predicting the presence of work-in-process (WIP) inventory at a specific step in a particular facility, and considering the impact of bottleneck pacing on work-in-process inventory and throughput time.
To determine the bottleneck step, we need information about the setup time and run time for each step. Unfortunately, the transcription of the question and the accompanying images are not available, making it impossible to provide a specific answer. Similarly, without the details regarding order size and the setup and run times for each step, it is not feasible to identify the order size at which the bottleneck would shift to an alternative step. The presence of work-in-process inventory before a specific step in a particular facility also cannot be determined without the necessary information. Lastly, the impact of bottleneck pacing on work-in-process inventory and throughput time cannot be evaluated without the relevant data. Therefore, a comprehensive answer to the question cannot be provided based on the available information. It is recommended to refer to the provided textbook or additional resources to obtain the necessary data for solving the problem.
learn more about bottleneck here
https://brainly.com/question/32633322
#SPJ11
the niu (network interface unit) or nid (network interface device) at the isp's demarc serves what purpose?
Answers
Network interface device: The physical enclosure that links the HFC network to the nearby home wire is situated at the service endpoint.
What is network interface device ?A network interface device (NID; also known by a number of other names) is a piece of equipment used in telecommunications to mark the boundary between the carrier's local loop and the customer's premises wiring. Outdoor telephone NIDs also give the subscriber access to the station wiring and act as an easy testing location for the subscriber's internal wiring and loop integrity.
An item of telecommunications equipment called a network interface device (NID; also known by a variety of other names) is used to delineate the space between the carrier's local loop and the customer's premises cabling. In addition to providing the subscriber with access to the station wire, outdoor telephone NIDs also serve as a convenient testing ground for the subscriber's internal wiring and loop integrity.
Learn to know more about network interface device :
https://brainly.com/question/1172216
#SPJ4
Why making sustainable food choices is better for the environment and the disadvantages or negative effects when not choosing sustainable food products may have.
Answers
Answer:
Question 1:
I. It will help to reduce or eliminate wastes
II. It will help to conserve energy
III. It will help to improve the quality of life.
Question 2:
I. It will lead to environmental pollution
II. It will lead to poor quality of products
III. It will deplete the natural resources and energy.
Explanation: Sustainable food choices are the various choices and decisions we make when choosing the various processes and activities required to produce,process and consume food with the aim of ensuring that energy is conserved, pollution is reduced or eliminated, energy and the natural resources in and around the environment are effectively utilised to help improve the quality of life and environmental. There are several negative consequences of not adopting sustainable food products which includes pollution, energy depletion, poor quality of life etc.
the functional description of the transport layer in the osi model provides
Answers
por que se dice que las TIC´S son las integracion de las TI y las TC?
Answers
La respuesta correcta para esta pregunta abierta es la siguiente.
A pesar de que no se anexan opciones o incisos para responder, podemos comentar lo siguiente.
Se dice que las TIC´S son las integración de las TI y las TC porque ambas actividades se han integrado o fusionado en una solo concepto al momento de juntar las herramientas tecnológicas para almacenar, procesar y mandar información a través de los recursos tecnológicos utilizando los canales o recursos de los medios masivas de comunicación como lo son las redes satelitales o las comunicaciones vía microondas.
Al fusionarse las TI (Tecnologías de la Información) con las TC (Tecnologías de Comunicación), se maximiza la capacidad de enviar una mayor cantidad de información al momento a diferentes lugares del planeta.
write a program to ask 10 numbers and find out total even and odd numbers
Answers
A program in Python that asks the user for 10 numbers and determines the total count of even and odd numbers is given below.
Program:
even_count = 0
odd_count = 0
for i in range(10):
number = int(input("Enter number: "))
if number % 2 == 0: # Check if the number is even
even_count += 1
else:
odd_count += 1
print("Total even numbers:", even_count)
print("Total odd numbers:", odd_count)
In this program, we use a for loop to iterate 10 times, asking the user to enter a number in each iteration.
We then check whether the number is even by using the modulo operator % to check if the remainder of dividing the number by 2 is zero. If it is, we increment the even_count variable; otherwise, we increment the odd_count variable.
After the loop completes, we print the total count of even and odd numbers.
For more questions on Python
https://brainly.com/question/26497128
#SPJ8