a(n) blank support system is designed to be easy to use and allows someone to obtain essential information without extensive training.
Answers
System software refers to the operating system applications made to manage intricate operating tasks in the background. A database is used to hold two different types of data in a DSS. Decision Model: Decision Model is the analytical engine of the DSS.
What are the computer systems that enable communication and in-person meetings between persons who are spread across different geographic locations?
The two-way or multipoint reception and transmission of audio and video signals by individuals in various locations for real-time communication is known as videotelephony, also known as videoconferencing and video teleconferencing.
managers by using both internal data from MIS and TPS and external data?
Senior management uses decision support tools to make complex decisions. Both internal (such as transaction processing systems and management information systems) and external systems provide input to decision support systems.
To know more about Decision Support System visit;
https://brainly.com/question/28170825
#SPJ4
Related Questions
Discuss and elaborate the impact of technology advancement in
seaport wayfinding to community
Answers
Answer:
international technology
Technologies are becoming increasingly complicated and increasingly interconnected. Cars, airplanes, medical devices, financial transactions, and electricity systems all rely on more computer software than they ever have before, making them seem both harder to understand and, in some cases, harder to control. Government and corporate surveillance of individuals and information processing relies largely on digital technologies and artificial intelligence, and therefore involves less human-to-human contact than ever before and more opportunities for biases to be embedded and codified in our technological systems in ways we may not even be able to identify or recognize. Bioengineering advances are opening up new terrain for challenging philosophical, political, and economic questions regarding human-natural relations. Additionally, the management of these large and small devices and systems is increasingly done through the cloud, so that control over them is both very remote and removed from direct human or social control. The study of how to make technologies like artificial intelligence or the Internet of Things “explainable” has become its own area of research because it is so difficult to understand how they work or what is at fault when something goes wrong
Explanation:
Which of the following operating systems cannot be licensed for a PC? A) Mac OS X B) Winodws Vista C) Windows 7. D) Red Hat Linux E) Windows XP.
Answers
The operating system that cannot be licensed for a PC is "Mac OS X." Mac OS X is exclusively designed for Apple's hardware, such as MacBook, iMac, Mac Pro, etc. and cannot be installed on a PC without violating Apple's licensing agreements. On the other hand, Windows Vista, Windows 7, Windows XP, and Red Hat Linux can be licensed and installed on a PC, provided that the user purchases a valid license and meets the system requirements. It's important to note that while Red Hat Linux is an open-source operating system, it still requires a license for commercial use. Ultimately, the choice of operating system depends on the user's needs, preferences, and compatibility with their hardware and software requirements.
To know more about MacBook visit:
https://brainly.com/question/31567320
#SPJ11
listen to exam instructions as a linux administrator, you need to create the directory /var/oracle/database/9i. only the directory /var currently exists. the current working directory is the root of the filesystem. which of the following commands will create the directory path?
Answers
The correct command to create the directory path /var/oracle/database/9i is:
`mkdir -p /var/oracle/database/9i`
Explanation:
In Linux, the `mkdir` command is used to create new directories. The `-p` option is used to create parent directories as needed. This means that if any of the parent directories do not exist, they will be created automatically.
In this case, since only the /var directory currently exists, we need to use the `-p` option to create the /oracle, /database, and /9i directories along the way. By using the `-p` option, we can create the entire directory path with one command, instead of having to create each directory individually.
Therefore, the correct command to create the directory path /var/oracle/database/9i is `mkdir -p /var/oracle/database/9i`.
Learn more about Linux:
https://brainly.com/question/25480553
#SPJ11
What is the purpose of a network device?
To allow the computer to store information or programs.
To allow the user to give data or information to the computer.
O
To allow computers to connect and communicate with other computers.
To allow the computer to display or communicate the result of a
computation

Answers
Answer:
c
Explanation:
:)
What is the analysis stage in System development life cycle?
Answers
Answer:
Explanation:
end user business requirements are analyzed and project goals converted into the defined system functions that the organization intends to develop. The three primary activities involved in the analysis phase are as follows: Gathering business requirement. Creating process diagrams.
How to turn off 2-step verification without signing in.
Answers
Answer:
You cannot do this; you need to sign into the account to gain access to any account security settings
write the java statement to creat an object mp4 class digital
Answers
Answer:
Answer:
digital mp4 = new digital ( );
Explanation:
mark as brainliest
if it is helpful
Explanation:
Discuss briefly four types of websites and the criteria you will use to evaluate the content of a website
Answers
Answer: I would look at who made it, what date it was published, what it is about and if it says .gov, .com or etc.
Explanation:
What is the first phase in which a software program is usable enough to test?
A.
Pre-alpha release
B.
Feature complete
C.
Alpha release
D.
Beta release
Answers
Answer:
Alpha release
Explanation:
Pre-alpha refers to all activities performed during the software project before formal testing.
The alpha phase of the release life cycle is the first phase of software testing.
A feature complete version of a piece of software has all of its planned or primary features implemented but is not yet final due to bugs, performance or stability issues.
A Beta phase generally begins when the software is feature complete but likely to contain a number of known or unknown bugs.
you are presenting with two monitors. which view displays a preview of the next slide and speaker notes on the second monitor?
Answers
dion training has just installed a new web server and created an a record for diontraining. when users try entering www.diontraining, though, they get an error. you tell their network administrator that the problem is because he forgot to add the appropriate dns record to create an alias for www to the domain's root. which type of dns record should be added to fix this issue?
Answers
To resolve the issue of users receiving an error when trying to access "www.diontraining," the network administrator needs to add the appropriate DNS record to create an alias for "www" to the domain's root.
A "CNAME" (Canonical Name) record needs to be added to the DNS settings by the network administrator. An existing domain or subdomain can have an alias or alternate name by using a CNAME record. In this instance, users will be able to visit "www.diontraining" without any issues by setting up a CNAME record for "www" that points to the domain's root. In a sense, the CNAME record serves as a pointer, enabling the web server to correctly resolve the domain and steer users to the desired location.
To learn more about Dion Training file, refer:
brainly.com/question/31064582
#SPJ11
If I subscribe to 5GB monthly data on my network and I watched a video of 500MB, How much data do I have left
Answers
Answer: around 6 hours
Explanation:
How do I make the text and heading different colors?
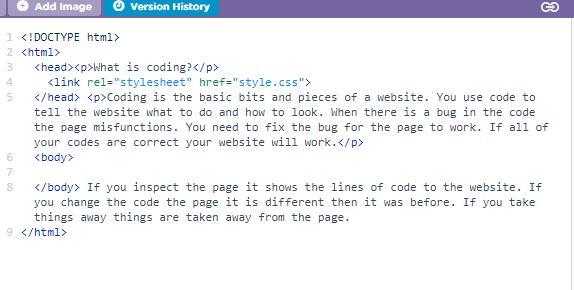
Answers
Answer: do u have word if you do go to font and u can change ur font
Explanation:
This question has two parts : 1. List two conditions required for price discrimination to take place. No need to explain, just list two conditions separtely. 2. How do income effect influence work hours when wage increases? Be specific and write your answer in one line or maximum two lines.
Answers
Keep in mind that rapid prototyping is a process that uses the original design to create a model of a part or a product. 3D printing is the common name for rapid prototyping.
Accounting's Business Entity Assumption is a business entity assumption. It is a term used to allude to proclaiming the detachment of each and every monetary record of the business from any of the monetary records of its proprietors or that of different organizations.
At the end of the day, we accept that the business has its own character which is unique in relation to that of the proprietor or different organizations.
Learn more about Accounting Principle on:
brainly.com/question/17095465
#SPJ4
Computer _ rely on up to date definitions?
A. Administrators
B. Malware Scan
C. Firmware updates
D. Storage Drivers
Answers
Answer: The correct answer is B. Malware Scan
Explanation:
The word "definition" only applies to antivirus and malware removal applications that scan for patterns using the definitions. The other choices do not use definitions. Firmware updates rely on images, storage drives use drivers and administrators are user privilege type.
Select the correct answer.
Which of these components is utilized in use case diagrams?
A.
classes
B.
components
C.
flow
D.
actors
Answers
Answer:
B.components
Explanation:
Phoebe is a Counselor who is trying to schedule a meeting with one of her patients. Which best describes an inappropriate location for a meeting with a patient? a private office a hospital cafeteria a treatment center a family consult room.
Answers
Answer: a hospital cafeteria because there is no privacy and the patient may feel uncomfortable and it can be too noisy
Explanation:
B hospital cafeteria
Explanation:
I took the test
define the computer with its workintg principple
Answers
Explanation:
Computer is an electronic device that is designed to work with information.
WORKING PRINCIPLE OF COMPUTER
a.It accepts data and instructions by way of input,
b.It stores data,
c.It can process data as required by the user,
d.It gives result in the form of output,
e.It controls all operations inside a computer.
I hope it will help you
A(n) ____ is a live internet presentation that supports interactive communications between the presenter and the audience.
a. e-conference
b. web conference
c. webcast
d. webinar
Answers
A webinar refers to a live internet presentation that supports interactive communications between the presenter and the audience.
What is a presentation?A presentation can be defined as an act that involves the process through which a presenter speaks to an audience (listeners), so as to formally share and explain an idea, piece of work, subject matter (topic), product, or project, especially for the purpose of proffering a solution to a particular problem.
What is a webinar?A webinar can be defined as a live Internet presentation that is designed and developed to support interactive communications between a presenter and his or her audience.
In this context, we can infer and logically deduce that a live Internet presentation that is designed and developed to support interactive communications between a presenter and his or her audience is generally referred to as a webinar.
Read more on presentation here: https://brainly.com/question/10545084
#SPJ4
¿ Porque la madera presenta mayor resistencia a ser cortada en sentido travesal que en sentido longitudinal
Answers
La madera es más fuerte en la dirección paralela al grano. Debido a esto, las propiedades de resistencia y rigidez de los paneles estructurales de madera son mayores en la dirección paralela al eje de resistencia que perpendicular a él
How does VPN software ensure that people accessing a network are authorized to do so?Multiple ChoiceOVPN software establishes secure connections.VPN software uses encryption to protect the users' credentials.VPN software authenticates users.VPN software links blocks of transactions connected to theuser.
Answers
How does VPN software ensure that people accessing a network are authorized to do so: C. VPN software authenticates users.
What is a VPN?In Computer technology, a VPN is an abbreviation for Virtual Private Network and it can be defined as a secured, encrypted and private web-based service that is typically used for accessing region-restricted and censored internet content from remote locations.
Generally speaking, a Virtual Private Network (VPN) simply refers to a computer software that enable internet users to remotely create a secured connection (sends and receives data) over public or shared networks, as if they are directly connected to the private network.
In conclusion, Virtual Private Network (VPN) software is designed and developed to authenticates end users in order to ensure that people accessing a network are authorized.
Read more on VPN here: brainly.com/question/28945467
#SPJ1
In C++, write (that is, declare and define) a class named personWeight that stores the data necessary to represent the weight of a person in pounds and ounces.
The personWeight class has private member variables named pounds (which can store only whole numbers, such as 5), and ounces (which can store either whole numbers such as 5 or decimal numbers such as 1.5)
The personWeight class has a public function (method) named weight_in_ounces that returns the weight of a person in ounces. The formula for computing the weight of a person in ounces is:
(16 * pounds) + ounces
NOTE: the declaration of the weight_in_ounces method should reside inside the declaration/definition of the personWeight class, and the definition of the weight_in_ounces function (method) should reside outside of the declaration/definition of the personWeight class.
NOTE: Do not write any constructors for the class here. You will do that in the next question.
Be careful of the variable types declarations you use to declare pounds and ounces (and the type of value returned by the weight_in_ounces method)
Answers
The code has been written below using the C ++ language of programming
How to write the code
// Header file (personWeight.h)
class personWeight {
private:
int pounds; // Whole number
double ounces; // Decimal number
public:
double weight_in_ounces(); // Returns weight in ounces
};
// Source file (personWeight.cpp)
#include "personWeight.h"
double personWeight::weight_in_ounces() {
return (16.0 * pounds) + ounces;
}
Read mroe on C++ here https://brainly.com/question/28959658
#SPJ4
A _________ agreement is an agreement that any information leamed while working on a project will be kept
private
Answers
Answer:
non-disclosure
Explanation:
An audience member is worried about an upcoming exam and is unlikely to remember much of what the speaker says. This is a type of...
external noise
internal noise
physical noise
educational noise
Answers
The type of situation described, where an audience member is worried about an upcoming exam and is unlikely to remember much of what the speaker says, can be categorized as internal noise.
Internal noise refers to distractions or barriers that exist within an individual's mind or thoughts, which can interfere with effective communication or information processing. In this case, the individual's worries and preoccupation with the upcoming exam create mental noise, making it difficult for them to focus on and retain the speaker's message. It is an internal factor that affects their ability to receive and process information effectively. External noise, on the other hand, refers to physical or environmental factors that disrupt communication, such as loud noises, poor acoustics, or distractions in the surroundings. Physical noise relates to actual disturbances, such as a loud sound or interference, that impede communication. Educational noise is not a commonly used term in the context of communication and is not applicable to this scenario.
Learn more about external noise here:
https://brainly.com/question/10118252
#SPJ11
1. Implement a three layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset (https://en.wikipedia.org/wiki/MNIST_database). Output the prediction accuracy. The dataset can be downloaded here: https://pypi.org/project/python-mnist/. Or you can download it from other source
upload the solution with step by step in jupyter and screenshots of output and source code.
Thank you
Answers
Implementing a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset and outputting the prediction accuracy can be achieved by using Jupyter notebook, Python, and the appropriate libraries such as TensorFlow or PyTorch.
How can you implement a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset and obtain the prediction accuracy?To implement a three-layer feedforward artificial neural network (ANN) training by Backpropagation for the MNIST dataset, follow these steps:
1. Set up the Jupyter notebook environment and import the necessary libraries such as TensorFlow or PyTorch.
2. Load the MNIST dataset using the provided link or any other reliable source.
3. Preprocess the dataset by performing tasks such as data normalization, splitting it into training and testing sets, and converting labels into one-hot encoded vectors.
4. Design the architecture of the three-layer feedforward ANN with appropriate activation functions, number of hidden units, and output layer.
5. Initialize the network parameters (weights and biases) randomly or using predefined methods.
6. Implement the forward propagation algorithm to compute the predicted outputs.
7. Implement the backpropagation algorithm to update the weights and biases based on the calculated errors.
8. Repeat steps 6 and 7 for a specified number of epochs or until convergence.
9. Evaluate the trained model on the testing set and calculate the prediction accuracy.
10. Upload the solution in Jupyter notebook along with the necessary screenshots of the output and the complete source code.
Learn more about Backpropagation
brainly.com/question/32647624
#SPJ11
Please help!!
What does a for loop look for in the sequence of
data? Check all that apply
the first variable
the second variable
the third variable
the last variable
Answers
Answer:
The first and last variable
Explanation:
Answer:
A) the first variable and D) the last variable
Explanation:
because i said so, you're welcome !
you want to provide redundancy so that a failure on a single component doesn't cause the website to become unavailable. what should you add to your configuration to accomplish this?
Answers
To provide redundancy and prevent website unavailability in the event of a single component failure, you should consider adding load balancing and failover capabilities to your configuration.
Load balancing involves distributing incoming traffic across multiple servers, ensuring that no single server is overwhelmed with too much traffic.
Failover, on the other hand, involves automatically redirecting traffic to a secondary server in the event of a primary server failure. By implementing both load balancing and failover,
you can ensure that your website stays up and running even if a component fails. Additionally, it's important to regularly monitor your system for any potential failures or issues, and have a plan in place to quickly address and resolve any issues that do arise.
To learn more about : configuration
https://brainly.com/question/14114305
#SPJ11
who developed the first personal computer called the altair
Answers
Which item represents unstructured data? A. Video training content. B. SQL tables of training instructors. C.Relational db for training tracking. D. Training db backup
Answers
The item that represents unstructured data is video training content (Option A).
Unstructured data refers to information that does not have a predefined or organized format, making it difficult to fit into traditional databases or tables. Among the given options, video training content (Option A) is the most likely to represent unstructured data. Videos typically contain a combination of visual, audio, and textual information that lacks a specific structure or predefined schema.
On the other hand, Options B and C mention SQL tables and relational databases, respectively, which suggest structured data. Finally, Option D mentions a training database backup, which may contain structured data depending on the backup format used.
To learn more about unstructured data: -brainly.com/question/32817506
#SPJ11
Which one of the following is not an importance of fungi?
Answers
The correct answer to the given question about fungi is D) Contributing to climate change by releasing greenhouse gases.
What roles do fungi play?While fungi play important roles in decomposing organic matter in the ecosystem, providing food for humans and animals, and producing antibiotics and other medicines, they do not directly contribute to climate change by releasing greenhouse gases.
In fact, some species of fungi can help mitigate climate change by sequestering carbon in the soil and as a result of this, the answer choice that is NOT an importance of fungi is option D because it does not release greenhouse gases.
Read more about fungi here:
https://brainly.com/question/10878050
#SPJ1
A) Decomposing organic matter in the ecosystem
B) Providing food for humans and animals
C) Producing antibiotics and other medicines
D) Contributing to climate change by releasing greenhouse gases