An internet ________ is a collection of utility programs designed to maintain your security and privacy while you are on the web.
Answers
An internet security suites is a collection of utility programs designed to maintain your security and privacy while you are on the web.
What is Internet Security Suite?As the name is called, an Internet Security Suite is known to be a kind of a protection services where all your security requirement are known to be in one package.
Note that they are called an all in one computer security packages that a person can have and it come with an anti-virus scanner, as well as an anti-spyware scanner, email protection, and others.
Therefore, An internet security suites is a collection of utility programs designed to maintain your security and privacy while you are on the web.
Learn more about internet security suites from
https://brainly.com/question/16341928
#SPJ1
Related Questions
Create an object called game in the game.js file.
Add 2 properties: lives - initially 3, and coins - initially 0.
Add a getter called points that returns coins * 10.
Add a playerDies() method that subtracts 1 from lives if lives is greater than 0.
Add a newGame() method that sets lives to 3 and coins to 0.
The script.js file includes several console.log() statements, which should match the output below if the game object works correctly.
Answers
The instructions involve creating an object called "game" with properties "lives" and "coins," a getter "points," and methods "playerDies()" and "newGame()."
What are the instructions for creating the "game" object and its properties, getters?The given instructions involve creating an object called "game" in the game.js file and adding properties, getters, and methods to it. The properties "lives" and "coins" are initialized with their respective initial values.
The getter "points" calculates the points by multiplying coins by 10. The method "playerDies()" subtracts 1 from lives if lives is greater than 0. The method "newGame()" resets lives to 3 and coins to 0.
The script.js file contains console.log() statements that should produce the expected output if the game object is implemented correctly.
Learn more about object
brainly.com/question/14964361
#SPJ11
What is the function of this logical comparator! =?
Answers
Answer:
See explanation
Explanation:
!= means not equal
The given operator is not a logical operator but rather a comparison operator.
It compares two expressions, values or variables and returns true if the items being compared are not equal.
Complete the code to check the length of a password.
When done, valid should be True if the password is between eight and 20 characters long.
Valid will be False if it is not.
valid = true
password = input("Password? ")
lengthPassword = _____
(password)
if lengthPassword _____
20:
valid = False
elif lengthPassword _____
8:
valid = False
1. len, size, length
2. >, <
3. >,
Answers
Answer:Here's the completed code to check the length of a password:
valid = True
password = input("Password? ")
lengthPassword = len(password)
if lengthPassword > 20:
valid = False
elif lengthPassword < 8:
valid = False
Explanation:
The len function is used to get the length of the password. If the length is greater than 20 or less than 8, valid is set to False. Otherwise, valid remains True.
Note that the if statement uses the comparison operators > and < to check if the length of the password is greater than 20 or less than 8, respectively.
Why do politically-powerful groups get bigger positive impacts of externalities?
- 1. GOVERNMENT CORRECTION FAVORS THEM
- 2. MORE POWERFUL GROUPS BECAME POWERFUL BECAUSE OF THESE EXTERNALITIES
- 3. BECAUSE OF CORRUPTION AND BRIBERY
- 4. BECAUSE THE POSITIVE IMPACTS ALWAYS OUTWEIGH THE NEGATIVE TO EVERYONE ELSE
Answers
There are a few reasons why politically-powerful groups get bigger positive impacts of externalities. One reason is that government correction favors them. Another reason is that more powerful groups became powerful because of these externalities.
What is government?
An organised community is governed by a system or group of people, typically a state. Government typically consists of the legislative, executive, and judicial branches in the case of its broad associative definition. Government is a mechanism for making policy decisions as well as a way to enforce organisational policies. A declaration of the government's guiding principles and philosophy is the equivalent of a kind of constitution in many nations. The term "government" is frequently used more specifically to refer to the roughly 200 independent national governments as well as subsidiary organisations, even though all organisations have governance. Modern democracies, monarchies, as well as authoritarian as well as totalitarian regimes are the main varieties of political systems.
Yet another reason is because of corruption and bribery. Finally, because the positive impacts always outweigh the negative to everyone else.
To learn more about government
https://brainly.com/question/1078669
#SPJ1
What is the final value for X ?
x= 1
x=13
x= x+3
x=0
Answers
Answer:
60
Explanation:
A company has a network printer that is utilzed by several departments. Although the printer shows online and other departments can access the printer, the accounting group is unable to print to this network printer. Which of the following would the technician use to resolve the problem?
a. The printer needs a maintenance kit repalced.
b. The TCP/IP print spooler service need to be restarted.
c. The security settings for the print spooler need to be modified to include the department.
d. Replace the network cable on the printer
Answers
Answer: c. The security settings for the print spooler need to be modified to include the department.
Explanation:
The print spooler makes Windows computer enable to interact with the printer, and to commands the printer for print jobs .
If all the other departments can access the printer, but not the accounting group, then the technician should check the security settings for the print spooler and modify it accordingly to include the accounting group .
Hence, the correct answer is c. The security settings for the print spooler need to be modified to include the department.
Which range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE?
A. 10.120.160.0 to 10.120.168.0
B. 10.120.160.0 to 10.127.255.255
C. 10.120.160.0 to 10.120.191.255
D. 10.120.160.0 to 10.120.167.255
Answers
10.120.160.0 to 10.120.167.255 is the range represents all the IP addresses that are affected when network 10.120.160.0 with a wildcard mask of 0.0.7.255 is used in an ACE.
Thus option D is correct.
What is IP addresses?An Internet Protocol address (IP address) is a numerical label such as 192.0.2.1 that is connected to a computer network that uses the Internet Protocol for communication. An IP address serves two main functions: network interface identification and location addressing.
Internet Protocol version 4 (IPv4) defines an IP address as a 32-bit number. However, because of the growth of the Internet and the depletion of available IPv4 addresses, a new version of IP (IPv6), using 128 bits for the IP address, was standardized in 1998. IPv6 deployment has been ongoing since the mid-2000s.
IP addresses are written and displayed in human-readable notations, such as 192.0.2.1 in IPv4, and 2001:db8:0:1234:0:567:8:1 in IPv6. The size of the routing prefix of the address is designated in CIDR notation by suffixing the address with the number of significant bits, e.g., 192.0.2.1/24, which is equivalent to the historically used subnet mask 255.255.255.0.
Learn more about IP addresses
https://brainly.com/question/16011753
#SPJ4
Which function is used to add a range of cells?
A) =SUM
B) =AVERAGE
C) =MAX
D) =ADD
Answers
Answer:
Sum
Sum a range of cells -- SUM Function
The quickest way to sum a range of cells is to use the AutoSum button. It automatically enters a SUM function in the selected cell. The SUM function totals one or more numbers in a range of cells.
Explanation:
The answer is "Option A" because it is used for adding the range of the cell, and the further explanation can be defined as follows:
The AutoSum button was its fastest way to add up a range of cells in Excel. It automatically inserts a SUM function into the specified cell. The SUM function sums up one or more numbers inside a range of cells. SUM function combines numbers together. Numbers can be added individually, as well as numerical values and ranges.The wrong solution can be defined as follows:
In option B, it is used to calculate the average of the value.In option C, it is used to calculate the maximum number in the among values.In option D, it is used to calculate the Autosum.Therefore "Option A" is the correct choice.
Learn more:
Excel function: brainly.com/question/10307135

What icon indicated video mode?
Av
Tv
The video camera icon
Answers
The video camera icon indicated video mode.
The video camera icon is a universally recognized symbol that indicates video mode on electronic devices such as cameras, smartphones, and video recorders. This icon usually appears on the interface of the device, usually on the screen or as a button that you can press, when you are in video mode, and it allows you to record videos.
AV and TV icons are related to audio-video and television, but they are not used specifically to indicate video mode. AV icon can be used for different purposes such as indicating the audio-video input/output of a device or indicating an audio-video format. The TV icon is used to indicate the television mode, which typically refers to the display mode of a device.
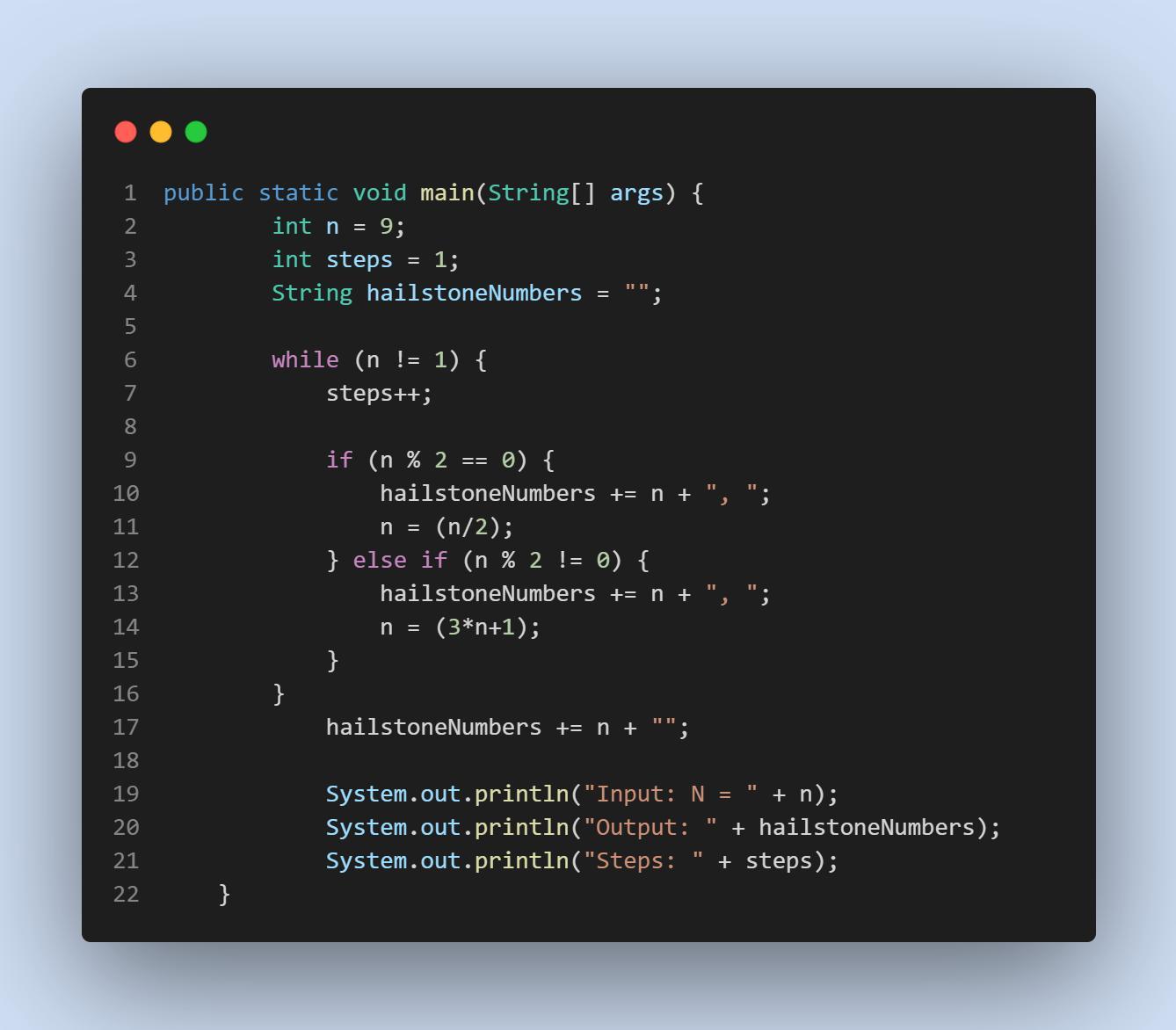
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
How does VPN software ensure that people accessing a network are authorized to do so?Multiple ChoiceOVPN software establishes secure connections.VPN software uses encryption to protect the users' credentials.VPN software authenticates users.VPN software links blocks of transactions connected to theuser.
Answers
How does VPN software ensure that people accessing a network are authorized to do so: C. VPN software authenticates users.
What is a VPN?In Computer technology, a VPN is an abbreviation for Virtual Private Network and it can be defined as a secured, encrypted and private web-based service that is typically used for accessing region-restricted and censored internet content from remote locations.
Generally speaking, a Virtual Private Network (VPN) simply refers to a computer software that enable internet users to remotely create a secured connection (sends and receives data) over public or shared networks, as if they are directly connected to the private network.
In conclusion, Virtual Private Network (VPN) software is designed and developed to authenticates end users in order to ensure that people accessing a network are authorized.
Read more on VPN here: brainly.com/question/28945467
#SPJ1
Did anyone else remember that Unus Annus is gone? I started crying when I remembered.... Momento Mori my friends.... Momento Mori...
Answers
Answer:
???
Explanation:
Did I miss something?
Answer:
Yes I remember its gone.
Explanation: I was there when the final seconds struck zero. The screen went black, and the people screaming for their final goodbyes seemed to look like acceptance at first. I will never forget them, and hopefully they will remember about the time capsule. Momento Mori, Unus Annus.
Qualífiers and absolutes shoud be taken as a warning when answering which type of question?
O short answer
O matching
O true/false
O essay
Answers
Answer:
C-true or false
Explanation:
just did it on edg 2020 and got 100%
big data is measured in
Answers
Answer:
Big data is enormous. While traditional data is measured in familiar sizes like megabytes, gigabytes and terabytes, big data is stored in petabytes and zettabytes.
Explanation:
Which of the below would provide information using data-collection technology?
Buying a new shirt on an e-commerce site
Visiting a local art museum
Attending your friend's baseball game
Taking photos for the school's yearbook
Answers
The following statement would provide the information by utilising data-collection technology: Buying a new shirt on an e-commerce site.
What is data collection?
The process of obtaining and analysing data on certain variables in an established system is known as data collection or data gathering. This procedure allows one to analyse outcomes and provide answers to pertinent queries. In all academic disciplines, including the physical and social sciences, the humanities, and business, data collecting is a necessary component of research. Although techniques differ depending on the profession, the importance of ensuring accurate and truthful collection does not change. All data gathering efforts should aim to gather high-caliber information that will enable analysis to result in the creation of arguments that are believable and convincing in response to the issues that have been addressed. When conducting a census, data collection and validation takes four processes, while sampling requires seven steps.
To learn more about data collection
https://brainly.com/question/25836560
#SPJ13
high-pitched sounds with short wavelengths displace the basilar membrane far from the oval window. true or false
Answers
The statement "High-pitched sounds with short wavelengths displace the basilar membrane far from the oval window" is true.
The basilar membrane is a thin, delicate membrane that stretches along the length of the cochlea's spiral form. It is located between the scala media and the scala tympani of the cochlea. The organ of Corti, which senses sound waves and is responsible for transmitting them to the brain via the auditory nerve, is located on top of this membrane.The basilar membrane's fundamental role is to vibrate in response to sound waves and, in the process, to activate the hair cells that line the organ of Corti, which send signals to the brain via the auditory nerve. These hair cells are tuned to respond to particular frequencies, which means they can detect and convey different pitches to the brain.Short wavelengths and high-pitched sounds will have a greater impact on the basilar membrane. When exposed to high-frequency sounds, the basilar membrane vibrates near its base and is displaced from the oval window, allowing hair cells at that location to sense the sound. This movement's size varies depending on the frequency of the sound.
Know more about basilar membrane here:
https://brainly.com/question/31047000
#SPJ11
A radio and communications security repairer is responsible for both radio and satellite communication systems.
True
False
Answers
Answer:
The answer is true
Explanation:
I got it correct on the quiz
from the current view (layout view), move the premium column to place it between the dob and providername columns in this report.
Answers
The ay to go about the work from the current view (layout view), move the premium column to place it between the dob and providername columns in this report is that:
Simply select the Premium label option. Click the bound control displaying the premium value while holding down Ctrl. To relocate both controls to the empty layout space to the right of the providername columns, click and drag them down.What is the view about?An Access app's web datasheet view shows online data organized in rows and columns via a web browser.
While viewing data in a form or report, you can make numerous typical design adjustments using the Layout view. Each control on the form displays actual data in Layout view, making it a highly helpful view for changing the size of controls or other tasks that have an impact on the form's aesthetics and usefulness.
Therefore, Design view is more abstract in nature than Layout view. Each control in the Layout view of a form shows actual data. This makes it a very helpful view for changing the size of controls and other things that have a visual impact.
Learn more about layout view from
https://brainly.com/question/27648067
#SPJ1
Whenever ___________ information is available, it should be used instead of accounting data.
Answers
Whenever Market information is available, it should be used instead of accounting data.
What is meant by market information?Marketing Information is known to be a term that connote all the information that are said to be associated to the marketing of any form of products or services.
They are made up of customer names, lists, sales targets, sales statistics, and others. The types of marketing information used by marketers are internal data, competitive intelligence, as well as marketing research.
Therefore, Whenever Market information is available, it should be used instead of accounting data
Learn more about Market from
https://brainly.com/question/24906199
#SPJ1
You have two Windows Server 2016 computers with the Hyper-V role installed. Both computers have two hard drives, one for the system volume and the other for data. One server, HyperVTest, is going to be used mainly for testing and what-if scenarios, and its data drive is 250 GB. You estimate that you might have 8 or 10 VMs configured on HyperVTest with two or three running at the same time. Each test VM has disk requirements ranging from about 30 GB to 50 GB. The other server, HyperVApp, runs in the data center with production VMs installed. Its data drive is 500 GB. You expect two VMs to run on HyperVApp, each needing about 150 GB to 200 GB of disk space. Both are expected to run fairly disk-intensive applications. Given this environment, describe how you would configure the virtual disks for the VMs on both servers.
Answers
The virtual disk configuration for the VMs on both servers in this environment is shown below.
In the Hyper V Test,
Since there will be two or three virtual machines running at once, each of which needs between 30 and 50 GB of the total 250 GB of disk space available,
What is virtual disks?Setting up 5 virtual disks, each 50 GB in size.
2 VMs each have a 50 GB virtual drive assigned to them.
The above setup was chosen because running three VMs with various virtual disks assigned to them will not pose an issue when two or three VMs are running concurrently and sharing the same virtual disk. This is because the applications are disk-intensive.
To learn more about virtual disks refer to:
https://brainly.com/question/28851994
#SPJ1
Given this environment, the virtual disk configuration for the VMs on both servers is shown below. Because two or three VMs will be running at the same time, and each VM has disk requirements ranging from 30 to 50 GB of total disk space of 250 GB.
What is Hyper V Test?While there are several methods for testing new virtual machine updates, Hyper-V allows desktop administrators to add multiple virtual machines to a single desktop and run tests. The Hyper-V virtualization technology is included in many versions of Windows 10. Hyper-V allows virtualized computer systems to run on top of a physical host. These virtualized systems can be used and managed in the same way that physical computer systems can, despite the fact that they exist in a virtualized and isolated environment. To monitor the utilization of a processor, memory, interface, physical disk, and other hardware, use Performance Monitor (perfmon) on a Hyper-V host and the appropriate counters. On Windows systems, the perfmon utility is widely used for performance troubleshooting.Therefore,
Configuration:
Creating 5 Virtual disks of 50 GB each.
1 virtual disk of 50 GB is assigned to 2 VM.
The above configuration is because since two or three VM will be running at the same time and using the same virtual disk will cause a problem since the applications are disk intensive, running three VMs with different virtual disks assigned to them, will not cause a problem.
For Hyper V App,
Two VM will run at the same time, and the disk requirement is 150 - 200 GB of 500 GB total disk space.
Configuration:
Creating 2 virtual disks of 200 GB each with dynamic Extension and assigning each one to a single VM will do the trick.
Since only two VMs are run here, the disk space can be separated.
To learn more about Hyper V Test, refer to:
https://brainly.com/question/14005847
#SPJ1
could someone please list the psychological impacts of Video games that differ the mind of teenagers. If you’ve previously completed a essay or report on this, please show me as an example. Thank you!
Answers
Answer:
Previous studies show that violent video games increase adolescent aggressiveness, but new Dartmouth research finds for the first time that teenagers who play mature-rated, risk-glorifying video games are more likely subsequently to engage in a wide range of behaviors beyond aggression, including alcohol use, smoking.
Explanation:
it has effected me by the way but im fine now it was for a short amount of time
as an amazon solution architect, you currently support a 100gb amazon aurora database running within the amazon ec2 environment. the application workload in this database is primarily used in the morning and sporadically upticks in the evenings, depending on the day. which storage option is the least expensive based on business requirements?
Answers
Answer:
Based on the provided business requirements, the least expensive storage option for the 100GB Amazon Aurora database within the Amazon EC2 environment would be Amazon Aurora Provisioned Storage.
Explanation:
Amazon Aurora Provisioned Storage is a cost-effective option for databases with predictable and consistent workloads. It offers lower costs compared to Amazon Aurora Serverless and Amazon Aurora Multi-Master, which are designed for different workload patterns.
In this case, since the application workload is primarily used in the morning and sporadically upticks in the evenings, it suggests a predictable workload pattern. Amazon Aurora Provisioned Storage allows you to provision and pay for the storage capacity you need, making it suitable for this scenario.
By selecting Amazon Aurora Provisioned Storage, you can optimize costs while meeting the business requirements of the application workload.
the workload for the Amazon Aurora database primarily occurs in the morning and sporadically upticks in the evenings.
Based on these business requirements, the least expensive storage option would be Amazon Aurora Serverless.
Amazon Aurora Serverless is a cost-effective option for intermittent or unpredictable workloads. It automatically scales the database capacity based on the workload demand, allowing you to pay only for the resources you consume during peak usage periods.
With Aurora Serverless, you don't have to provision or pay for a fixed database instance size. Instead, you are billed based on the capacity units (Aurora Capacity Units or ACUs) and the amount of data stored in the database. During periods of low activity, the database can automatically pause, reducing costs.
Compared to traditional provisioned instances, where you pay for a fixed capacity regardless of usage, Aurora Serverless provides cost savings by optimizing resource allocation based on workload demand. This makes it a cost-effective option for intermittent workloads, such as the morning and sporadic evening upticks described in your scenario.
To know more about Amazon related question visit:
https://brainly.com/question/31467640
#SPJ11
Java Programming : 1. Develop this JavaFX application. 1. Create a JavaFX application that draws a pattern of evenly spaced circles. 2. Use four constants to control the pattern: the number of circles to draw, 3. the radius of the first circle, 4. the change in the radius of each subsequent circle, and 5. the change in the x-coordinate of the circle. 6. Cycle the colors of the circles through red, green, and blue. II. Repeat the previous project, but position the centers of the circles on a spiral. The center of each circle will depend on both an angle and a distance from the origin. A constant change in both the angle and the distance will result in a spiral pattern.
Answers
Java Programming: Develop a JavaFX application that draws a pattern of evenly spaced circles. Use four constants to control the pattern: the number of circles to draw, the radius of the first circle, the change in the radius of each subsequent circle, and the change in the x-coordinate of the circle.
Cycle the colors of the circles through red, green, and blue. Also, position the centers of the circles on a spiral. The center of each circle will depend on both an angle and a distance from the origin. A constant change in both the angle and the distance will result in a spiral pattern. The development of this JavaFX application requires a user interface for outputting the graphic and inputs for the constants.
Therefore, you need to define a class to hold the values of the four constants and write a class that implements Event Handler, which receives input from the user interface. Use the Graphics Context object to draw the circles and their colors. For instance, you can draw a circle by calling the fill Oval method, which takes four arguments: the x and y-coordinates of the upper left corner of the oval, and the width and height of the oval.
A spiral pattern of circles requires knowledge of the position of each circle, given a constant change in angle and distance. The color cycle can be implemented by defining an array of three colors and cycling through it for each circle drawn.
To know more about Java Programming visit:-
https://brainly.com/question/2266606
#SPJ11
When an entrepreneur has three employees at a busy and growing software company, what is the primary responsibility of the employees?
create the product that customers want
explain business decisions to stakeholders
identify and contact financial investors
select new types of software to sell
Answers
Answer:
A: Create the product that customers
Explanation:
I did it on edgy
Answer:
(A). Create the product that customers want
Explanation:
I got it right on edge2020.
Your client would like to measure how many new users are seeing their campaign. They'd like to view this on a spreadsheet emailed daily. Which Campaign Manager 360 measurement feature should you use to meet their request?
Answers
To meet your client's request of measuring how many new users are seeing their campaign and viewing the data on a spreadsheet emailed daily, you can utilize the "Scheduled Reports" feature in Campaign Manager 360.
Scheduled Reports allow you to generate automated reports based on specified criteria and have them emailed to designated recipients at regular intervals. This feature provides the flexibility to customize the report to include specific metrics and dimensions, such as new user counts, campaign performance, and other relevant data.
By configuring a scheduled report with the desired metrics and dimensions related to new user counts, you can set it to generate the report daily and have it sent as an email attachment in a spreadsheet format (e.g., CSV, XLSX). This will enable your client to receive regular updates on the number of new users exposed to their campaign.
Additionally, Campaign Manager 360 offers various customization options, allowing you to tailor the report's layout, filters, date ranges, and other parameters to suit your client's specific requirements.
Learn more about spreadsheet here
https://brainly.com/question/11452070
#SPJ11
a small organization operates several virtual servers in a single host environment. the physical network utilizes a physical firewall with nids for security. what would be the benefits of installing a host intrusion prevention system (hips) at the end points?
Answers
The thing that would be the benefits of installing a host intrusion prevention system (hips) at the end points is Prevent Malicious Traffic between VMs and Protection from zero day attacks.
Can you fend off zero-day assaults?A security measure called zero-day protection is made to guard against zero-day attacks. This can involve doing things like utilizing security software, updating your software, and steering clear of clickbait and phishing scams. Malware that exploits a zero-day vulnerability is known as a zero-day virus.
Therefore, the security strategy known as a host intrusion prevention system (HIPS) uses external software tools to detect and stop hostile activity. Endpoint device protection is frequently provided by host-based intrusion prevention systems.
Learn more about host intrusion prevention system from
https://brainly.com/question/28095974
#SPJ1
how does the timestamp method of concurrency control prevent conflicts?
Answers
Concurrency control is an important aspect of database management systems to ensure that multiple users can access and modify data simultaneously without conflicts.
The timestamp method assigns a unique timestamp to each transaction when it starts. The timestamp represents the time when the transaction begins and is used to determine the order of execution for concurrent transactions. The transactions are executed in increasing order of the timestamp.
To prevent conflicts, the timestamp method uses two rules:
1. The Read Rule: A transaction with a higher timestamp can only read data that has been modified by transactions with lower timestamps. This ensures that a transaction reads the most recent version of the data.
2. The Write Rule: A transaction with a higher timestamp can only modify data that has not been modified by transactions with lower timestamps. This ensures that a transaction does not overwrite changes made by other transactions.
By enforcing these rules, the timestamp method ensures that transactions execute in a serializable order, which means that the final result of the transactions is equivalent to the result if they had executed serially, one after the other.
In summary, the timestamp method of concurrency control prevents conflicts by assigning a unique timestamp to each transaction and enforcing the read and write rules to ensure that transactions access and modify data in a consistent order.
Know more about the Concurrency control
https://brainly.com/question/30539854
#SPJ11
Carol is working on her family farms to produce better variety of crops which have higher yields which process should carol use to create a better variety of crops?
Answers
Answer:
Genetic engineering
Explanation:
Answer:
B - Crop Rotation
Explanation:
Sniffer turns the NIC of a system to the promiscuous mode so that it listens to all the data transmitted on its segment. It can constantly read all information entering the computer through the NIC by decoding the information encapsulated in the data packet. Passive sniffing is one of the types of sniffing. Passive sniffing refers to:
Answers
Answer:
The right answer will be "Sniffing through a hub".
Explanation:
Packet sniffer seems to be a device that listens for transmitted data on what seems like a channel. Sniffing enables the detection of data by individual people as it has been transferred throughout a cable. Appropriate nodes are using this methodology to make a diagnosis of connection issues, or even just harmful programs to obtain confidential information, like authentication and encryption.You can only use center left turn lanes to ____. pass other drivers stop make a left turn get out of the way submit answer
Answers
Answer:
Turn left, don't pass other drivers, stop, make a left turn, then get out of the way.
Explanation: