ARPAnet was an early Internet system developed by the Department of Defense as a communication network that would be distributed and thus impervious to nuclear attacks. T/F
Answers
The statement is true. ARPAnet was indeed an early Internet system developed by the Department of Defense with the objective of creating a distributed communication network that would be resistant to nuclear attacks.
ARPAnet, which stands for Advanced Research Projects Agency Network, was a pioneering computer network developed in the late 1960s by the Department of Defense's Advanced Research Projects Agency (ARPA), now known as DARPA. The primary motivation behind ARPAnet's development was to create a robust and resilient communication system that could withstand disruptions, including nuclear attacks.
To achieve this goal, ARPAnet employed a decentralized and distributed network architecture. Instead of relying on a centralized hub, the network consisted of multiple interconnected nodes or computers. Each node acted as a point of communication, and data could be routed through alternative paths in case of damage or failures.
The distributed nature of ARPAnet made it more resistant to single points of failure, as information could be rerouted through available paths even if certain nodes or links were compromised. This design feature contributed to ARPAnet's resilience in the face of potential disruptions, including those caused by nuclear attacks.
Learn more about ARPAnet here:
https://brainly.com/question/28577400
#SPJ11
Related Questions
Participants in a study are asked to press the left button if they see an unpleasant word or a photo of a White person, and to press the right button if they see a pleasant word or a photo of a Black person. The probable purpose of this procedure is to measure
subtle prejudices that people do not admit to themselves
Answers
The probable purpose of this procedure is to measure subtle prejudices that people do not admit to themselves.
What is Participant observation?Several academic fields, including anthropology, sociology, communication studies, and even market research, have made extensive use of participant observation.In this post, we've assembled the methodology's most crucial features, its significance, and a few different types of participant observation that you might use in your next study to provide you a general understanding of it.In the qualitative research method known as participant observation, the researcher investigates a group by both observing it and taking part in its activities.The researcher immerses himself in the participants' daily routines using this qualitative observation methodology in order to record the behaviour in as many different contexts as feasible.To learn more about Participant observation refer to:
https://brainly.com/question/14619255
#SPJ4
the primary agency of the united states government responsible for biomedical and health-related research is the ____.
Answers
The primary agency of the United States government responsible for biomedical and health-related research is the National Institutes of Health (NIH).
The primary agency of the United States government responsible for biomedical and health-related research. The agency has various institutes and centers, each with its research agenda that focuses on a specific health issue.The National Institutes of Health (NIH) is a part of the United States Department of Health and Human Services. It is the biggest biomedical research agency in the world and the only one funded entirely by the federal government.
The National Institutes of Health (NIH) is responsible for biomedical and health-related research, and it is the primary agency of the United States government for the same.
Learn more about biomedical visit:
https://brainly.com/question/31233975
#SPJ11
systems known as ___ are able to continue their operation even when problems are present.
Answers
Systems known as fault-tolerant are able to continue their operation even when problems are present.
Fault-tolerant systems are designed to continue operating properly in the event of hardware or software failures. This is an important feature for systems that are critical to the operation of a business or organization, as it helps to ensure that there is minimal downtime and that the system can continue to function even in the face of problems. Fault-tolerant systems typically include redundant components, such as multiple processors, storage devices, or network connections, which can take over in the event of a failure. They may also use advanced error detection and correction techniques to identify and fix problems before they cause a system outage.
Fault-tolerant systems are designed to be able to withstand and adapt to disruptions or failures, and to recover quickly and continue functioning with minimal or no impact on their overall performance. Fault-tolerant systems are important in many areas, including engineering, computer science, ecology, and social systems.
Learn more about a fault system here https://brainly.com/question/9349830
#SPJ11
please help me i will award brainliest
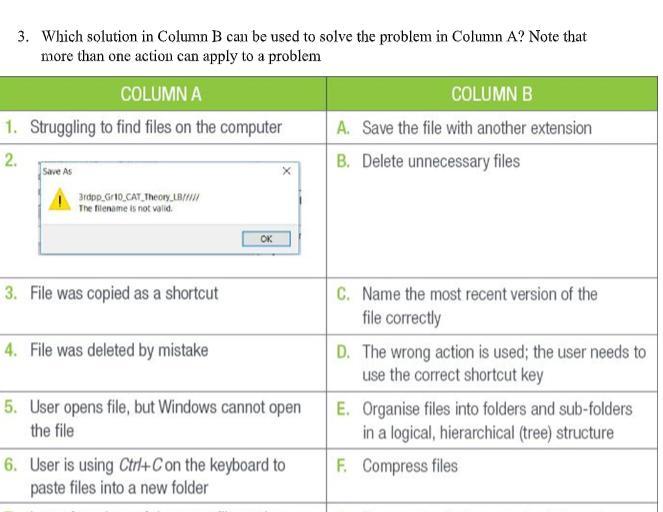

Answers
Answer: It would be option C.
Explanation: The file name is invalid, so therefore it would make sense to rename the most recent version correctly.
difference between data bus and address bus and control bus
Answers
Answer: The address bus carries the information about the device with which the CPU is communicating and the data bus carries the actual data being processed, the control bus carries commands from the CPU and returns status signals from the devices.
During which phase of the sdlc is software tested to make sure each function works as intended?.
Answers
Coding is completed in the implementation phase, and the software created serves as the input for the testing step that follows.
The developed code is rigorously tested throughout the testing process to find any software flaws. The requirement analysis stage of the SDLC is the first. All of the customer's data is collected in the first stage. The client's expectations are included in this. Understanding the nature of the product, the target market, and the motivations behind its creation are all taken into account User Acceptance The last phase of any software development or change request lifecycle before going live is testing, or application testing. Verifying sure the software performs as intended in actual circumstances is the last step in any development process.
Learn more about software here-
https://brainly.com/question/985406
#SPJ4
What is malicious code and its types?
Answers
Unwanted files or programmes that can harm a computer or compromise data saved on a computer are known as malicious code. Malicious code can be divided into a number of categories, including viruses, worms, and Trojan horses.
A specific kind of destructive computer code or web script intended to introduce system weaknesses that could lead to back doors, security failures, information and data theft, and other potential harm to files and computing systems is referred to as "malicious code" in this context. Antivirus software might not be able to stop the risk on its own. Computer viruses, worms, Trojan horses, logic bombs, spyware, adware, and backdoor programmes are a few examples of malicious programming that prey on common system weaknesses. By accessing infected websites or clicking on a suspicious email link or file, malicious software might infiltrate a machine.
Learn more about malicious from
brainly.com/question/29549959
#SPJ4
A pointing device that has a laser guide on its underside and two or more buttons for clicking commands; you control the movement of the pointer by moving the entire thing around on your desk.
Answers
In the lesson, you learned about the various uses of computers in manufacturing, from design to the control of manufacturing processes. Write a short report about the advantages and main features of CAD. Discuss the main applications of CAM as well.
Answers
Some of the main features of Computer Aided Design:
(CAD) are:
Glassworking, woodturning, metallurgy and spinning, and graphical refinement of the entire production technique are some of the key uses of the Computer Aided Manufacturing (CAM) system. CAM systems are used to create solids of rotation, flat surfaces, and screw threads.
What is CAD?The use of computers to help in the development, alteration, analysis, or optimization of a design is known as computer-aided design.
This program is used to boost the designer's efficiency, improve design quality, improve communication through documentation, and develop a database for production.
Learn more about Computer Aided Manufacturing:
https://brainly.com/question/14039774
#SPJ1
Which computer is the fastest to process complex data?
Answers
Answer:
Supercomputers for sure.
For this recitabian project, white a peogranithat wil diiphy in menu and perfoem e fiferent arithmetic operation based on the ifiection that i made from the menu. This wilchentine until the duit option is ielected from the menu. The menur that is diplayed: a) add two numbern 6) Tquare a numbo. d) divide tuo numbero. d) गuith What is yout chotce? The cholce that is entered ha sinde fetter string value. A cPp file (mesu.कp) has been provided. It contalin the doclaraton for a string varable (mens choicel, and code that will display the mena to the user and get a strine value. Add code that will process the menu choite that was made by getting the required vilue(s) from the user; perfermine the selected arithmetic operation, and daplaves the result of the operation. This should entainse : fer as lang as the vet does not want to quit. Make sure that the mens of options is diplayed to the user atter the retults of each operation fis been displayed. If the addition operation f
∗
a
∗
or " A ") is selected, the user should be prompted for two integer values that should: be added and thy gewleing sum should be displyyed. Make sure the promphs to the user and the daplay of the results macch whll is shown in the output section. If the square operation f
"s"
" of "S") is selected, the user should be prorthted far a sincle intecer value that should be squared and the resulaing product should be derglayed, Make uare the peompt to the uner and the Cisplay of the results match what is shown in the cutput section. If If the division operation F"d
∗
or "DTlis selected, the saer shiould be prompted for two inteser values fa dividend and divisor) that should be dilded and the resulting quotient AkD remainder should be cipliyed. Make sure the prompls to the user and the digily of the result match what is shown in the output section. If the mena selection is invalid, dispizy "invald selection". Frint a newaine at the end of the prceram. File You Must Submit Pace the con pleted promam code in a tource fle named menu.cPp. Output The output enat is preduced by the program will vary based en the values that ace enternd when the progam in enecuted. The ocfput that is shown below is what the program wis peoduce when it a run in an enwirentrent fuch as Dev Cer oc XCode. When it is ran theocsh the Auto Grader, the portions that ask for values Will Not: shuw the valuef that are entered. A single run of the program follow? a) adid two nimbert: a) squari a turiber d) divide taro: nu=bera
Answers
In this project, a C++ program that will display a menu and perform a different arithmetic operation based on the user's choice that was made from the menu is to be written.
This will continue until the quit option is selected from the menu. If the choice is invalid, the program should display "invalid selection". The menu that is displayed is given below:a) add two numbers b) subtract two numbersc) multiply two numbersd) divide two numberse) modulof) square a numberg) quitWhat is your choice?The choice that is entered has a single-letter string value.
A C++ file (menu.cpp) has been provided. It contains the declaration for a string variable (menuChoice), and code that will display the menu to the user and get a string value. Add code that will process the menu choice that was made by getting the required value(s) from the user; performing the selected arithmetic operation, and displaying the result of the operation.
This should contain a loop that will continue for as long as the user does not want to quit. Make sure that the menu of options is displayed to the user after the results of each operation have been displayed. If the addition operation (or "A") is selected, the user should be prompted for two integer values that should be added and their resulting sum should be displayed. If the subtraction operation (or "B") is selected, the user should be prompted for two integer values that should be subtracted and their resulting difference should be displayed. If the multiplication operation (or "C") is selected, the user should be prompted for two integer values that should be multiplied and their resulting product should be displayed. If the division operation (or "D") is selected, the user should be prompted for two integer values (a dividend and divisor) that should be divided and the resulting quotient and remainder should be displayed.
If the modulo operation (or "E") is selected, the user should be prompted for two integer values that should be divided and their resulting modulo should be displayed. If the square operation (or "F" or "S") is selected, the user should be prompted for a single integer value that should be squared and the resulting product should be displayed. If the menu selection is invalid, display "invalid selection". Print a newline at the end of the program.
To learn more about arithmetic operations:
https://brainly.com/question/30553381
#SPJ11
Women in Mathematics: This woman, who was born in London in 1815, was one of the first people to realize that computing machines (such as the never-completed Analytical Engine) could perform more general actions than just arithmetic. Her namesakes include a programming language and two computing awards?
Answers
Augusta Ada King, Countess of Lovelace, an English mathematician and author who lived from 10 December 1815 to 27 November 1852, is most remembered for her contributions to Charles Babbage's Analytical Engine, a mechanical general-purpose computer.
What is programming language?For programmers (developers) to interact with computers, they need to use a programming language. In order to generate machine code or, in the case of visual programming languages, graphical elements, programming languages must follow a set of rules that allow string values to be transformed into different types of code. A programming language is a notational scheme used to create computer programmes. While they occasionally include graphics, formal programming languages tend to be text-based. They are an instance of a computer language. The fact that it took at least two years to complete developing the first Malbolge code demonstrates how difficult Malbolge is to learn.To learn more about programming language, refer to:
https://brainly.com/question/16936315
conceited or self confident? why?
Answers
Answer:
self confident
Explanation:
self confident mean that u don't lose your hope and you can focus on your aim then u cann be success in any field
Answer: self confident because you should always love yourself and not need other people option or attention to motivate yourself
Explanation:
Is there any router that you can just buy that provides a internet service and don't have to pay for monthly subscriptions?
Answers
There is no router that provides a internet service to end users without them having to pay for monthly or yearly subscriptions.
What is a router?A router can be defined as a network device (node) that is designed and developed to connect two (2) different computer networks together, in order to allow them communicate by forwarding and receiving packets.
What is wi-fi?Wi-Fi can be defined as a wireless network technology that is designed and developed to avail end users and network devices such as computer systems, mobile devices, router and switches, to communicate with one another over the Internet or through an active network connection.
In conclusion, there is no router that provides a internet service to end users without them having to pay for monthly or yearly subscriptions because this is the fee charged by an internet service provider (ISP) for data plans.
Read more on router here: brainly.com/question/24812743
#SPJ1
This workout demonstrates the operation of a botnet. You willfully executed the botnet client script, what are two ways an adversary could execute the script on a target victim's computer? Question 3 If the adversary's motive included financial theft, how might they use this botnet to accomplish their objective? Question 4 −110 How could an adversary obtain remote screen access to the computer using this botnet script? Question 5 How might a defender identify the presence of this botnet thmonoh network traffic? Then how could the adversarv victim's computer? Question 3 If the adversary's motive included financial theft, how might they use this botnet to accomplish their objective? Question 4 How could an adversary obtain remote screen access to the computer using this botnet script? Question 5 −110 How might a defender identify the presence of this botnet through network traffic? Then, how could the adversary modify its tactics to evade the defender's detection?
Answers
An adversary may execute a botnet client script on a target's computer through methods like phishing emails or drive-by downloads. The botnet could then be used to conduct various financially motivated attacks, such as crypto-mining or stealing banking information.
An adversary could employ tactics such as sending phishing emails containing malicious links or attachments or exploiting browser vulnerabilities to initiate drive-by downloads. Once the botnet client script is installed, it can transform the victim's computer into a 'bot' that follows the commands of the botnet 'master'. This network can then be used for several purposes, such as mining cryptocurrency, launching Distributed Denial of Service (DDoS) attacks, or even stealing banking or credit card details for financial theft. To gain remote screen access, adversaries may use a variety of spyware or other Remote Access Trojans (RATs).
Learn more about botnet here:
https://brainly.com/question/29606977
#SPJ11
Which of the following functions is performed by both TCP and UDP? a. Windowing b. Error recovery c. Multiplexing using port numbers d. Routing
Answers
Both TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) use port numbers to identify the applications that are sending or receiving data. This is known as multiplexing, which means that multiple applications can use the network simultaneously without interfering with each other.
However, TCP and UDP differ in their approach to error recovery and windowing. TCP is a connection-oriented protocol that provides reliable data transfer and error recovery mechanisms, including windowing and retransmission of lost packets. On the other hand, UDP is a connectionless protocol that does not provide any error recovery mechanisms and does not use windowing.
Routing is a function that is performed by network layer protocols such as IP (Internet Protocol), which are responsible for forwarding packets from one network to another. TCP and UDP operate at the transport layer, which is one layer above the network layer, and are not involved in routing. In conclusion, the function that is performed by both TCP and UDP is multiplexing using port numbers.
To know more about User Datagram Protocol visit :
https://brainly.com/question/31113976
#SPJ11
the dbms accomplishes by reading the log for the problem transactions and applying before images to under thier updates
Answers
The DBMS accomplishes backward recovery by reading the log for the problem transactions and applying before images to their updates.
What is DBMS?
Software programs called database management systems (DBMS) are used to store, retrieve, and query data. A DBMS acts as an interface between an end-user and a database, enabling users to create, read, update, and remove data in the database.
DBMSs control the data, the database engine, and the database structure, enabling users and other applications to extract or modify the data. It also contributes to concurrency, uniform data management practices, and data security.
The normalization technique, used in database schema design, allows DBMS to optimize the arrangement of data by dividing large tables into smaller ones when any of their properties have redundant values. DBMS provides a number of advantages over conventional file systems, such as flexibility and a more intricate backup system.
To learn more about DBMS, use the link given
https://brainly.com/question/19089364
#SPJ4
true/false. in a two-dimensional array, the elements are arranged in a table form.
Answers
In a two-dimensional array, the elements are arranged in a table form where each element is identified by a pair of indices representing its row and column position. So, the given statement is true.
Explanation:
In a two-dimensional array, the elements are arranged in a table form where each element is identified by its row and column index. A two-dimensional array can be thought of as a collection of rows and columns, where each row is itself an array of elements and all rows have the same number of elements. The elements in the array can be accessed using their corresponding row and column indices.
For example, consider a 2D array of integers called "arr" with 3 rows and 4 columns:
arr = [[1, 2, 3, 4],
[5, 6, 7, 8],
[9, 10, 11, 12]]
This array can be visualized as a table with 3 rows and 4 columns:
To know more about two-dimensional array click here:
https://brainly.com/question/30463245
#SPJ11
…..is the smallest size in audio files
Answers
Answer:
Wav files can be 16 bit,8 kHz (i.e 128 k bits per second) while mp3 could be compressed to 16 kbits per second. Typically wav is x10 larger than mpg. This is ratio is highly content specific. Wav is a raw format, while mp3 is a compressed format for audio.
Explanation:
Answer:
Wav files can be 16 bit,8 kHz (i.e 128 k bits per second) while mp3 could be compressed to 16 kbits per second. Typically wav is x10 larger than mpg. This is ratio is highly content specific. Wav is a raw format, while mp3 is a compressed format for audio.
The reply url specified in the request does not match the reply urls configured for the application.
Answers
The error message “The reply URL specified in the request does not match the reply URLs configured for the application” indicates that there is a mismatch between the reply URL that was specified in the authentication request and the reply URL that was configured for the application.
In order to resolve this error, you need to make sure that the reply URL specified in the authentication request exactly matches the reply URL that was configured for the application. This can be done by verifying the reply URL configuration in the Azure portal. You can do this by following the steps below:1. Sign in to the Azure portal.2. Select the Azure Active Directory blade.3. Navigate to the App Registrations tab.
4. Locate the application that is generating the error.5. Click on the application to view the application properties.6. Navigate to the Authentication tab.7. Verify that the reply URLs listed in the configuration exactly match the reply URL specified in the authentication request.8. Update the reply URL configuration if necessary.9. Save the changes.10. Try the authentication request again.
To know more about application visit:
https://brainly.com/question/31164894
#SPJ11
Another term for the plot structure of the hero journey
Answers
when prominences erupt into space releasing gas and energy we call this
Answers
A solar flare is a sudden brightening of the Sun's atmosphere that occurs when stored energy is suddenly released. This energy is stored in twisted magnetic fields that exist throughout the Sun's atmosphere, called the corona. The energy released during a solar flare heats the corona and produces bursts of radiation, including X-rays and ultraviolet light.
These bursts can cause problems for communication systems on Earth, as well as for satellites and other space-based technologies. Solar flares are often accompanied by coronal mass ejections (CMEs), which are huge clouds of charged particles that are also released into space.
CMEs can cause geomagnetic storms when they interact with Earth's magnetic field, producing phenomena such as the aurora borealis (northern lights). Solar flares are classified according to their X-ray brightness, with the most powerful flares classified as X-class flares. The energy released during an X-class flare can be equivalent to billions of hydrogen bombs.
To know more about solar visit:
https://brainly.com/question/28510762
#SPJ11
Show the shortest form of these IPv6 addresses by removing leading zeros and using ::
a) 000C:1234:0000:0000:0001:0000:0000:C201
b) 0000:1A27:2337:0000:0000:A231:090A:0000
c) 8000:0008:4000: 0004:2000:0002: 1000:0001
d) 0001:0000:0000:0000:0000:0000:0000:0000
Answers
a) Shortest form: C:1234::1:0:0:C201, b) Shortest form: 0:1A27:2337::A231:90A:0, c) Shortest form: 8000:8:4000:4:2000:2:1000:1, d) Shortest form: 1::.
What is the shortest form of these IPv6 addresses by removing leading zeros and using "::"?Certainly! Here are the valid answers for each IPv6 address, along with their explanations:
000C:1234:0000:0000:0001:0000:0000:C201Shortest form: C:1234::1:0:0:C201
In IPv6, leading zeros within each 16-bit block can be omitted. The "::" notation can be used to replace consecutive blocks of zeros. In this case,
we can shorten "0000:0000" to "::" and remove the leading zeros from the other blocks, resulting in the shortest form.
0000:1A27:2337:0000:0000:A231:090A:0000Shortest form: 0:1A27:2337::A231:90A:0
Similar to the previous case, we can remove leading zeros within each block and use the "::" notation to represent consecutive blocks of zeros.
After applying these rules, we obtain the shortest form.
8000:0008:4000:0004:2000:0002:1000:0001Shortest form: 8000:8:4000:4:2000:2:1000:1
The leading zeros within each block can be omitted, resulting in the shortest form of the given IPv6 address.
0001:0000:0000:0000:0000:0000:0000:0000Shortest form: 1::
In this case, all blocks except the first one contain only zeros. According to the IPv6 rules, we can represent consecutive blocks of zeros with a double colon "::".
Therefore, we can replace all the zero blocks with "::", resulting in the shortest form.
These answers follow the standard conventions of IPv6 address representation by removing leading zeros and utilizing the "::" notation when applicable.
Learn more about Shortest form
brainly.com/question/2774548
#SPJ11
tle electrical instulation maintance
1.what is inventory 2. what is job order 3. what is barrow form 4. what is purchase request
Answers
Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. A job order is a document that contains all the information necessary to complete a specific maintenance task.
Definition of the aforementioned questions1) Inventory refers to the process of keeping track of all materials and equipment used in electrical insulation maintenance. This includes maintaining a list of all the items in stock, monitoring their usage, and ensuring that there are enough supplies to meet the demands of the job.
2) A job order is a document that contains all the information necessary to complete a specific maintenance task. This includes details about the task, such as the materials and tools required, the location of the work, and any safety considerations.
3) A barrow form is a document used to request materials or equipment from the inventory. It contains details about the requested item, including the quantity, the purpose of the request, and the name of the person or team making the request. The form is usually signed by an authorized person and submitted to the inventory manager or other appropriate personnel.
4) A purchase request is a document used to initiate the process of purchasing new materials or equipment for the electrical insulation maintenance program. It contains details about the item to be purchased, including the quantity, the cost, and the vendor or supplier. The purchase request is typically reviewed and approved by a supervisor or manager before the purchase is made.
learn more about electrical insulation maintenance at https://brainly.com/question/28631676
#SPJ1
question 4 a data analyst uses the aes() function to define the connection between their data and the plots in their visualization. what argument is used to refer to matching up a specific variable in your data set with a specific aesthetic?
Answers
A certain parameter in your data collection and a particular aesthetic are matched through a process known as mapping.
Do data analysts need a bunch of math skills?The success of data analysts depends on a solid foundation in mathematics, much like any other scientific profession. Before studying how to work as a data analyst, it could be crucial to review or, if required, develop your mathematical abilities.
Do data analysts perform their jobs well?Skilled data analysts are some of the most searched specialists globally. Data analysts command high wages and benefits even when they are entry-level due to the high demand for their expertise and the scarcity of qualified people.
To know more about data analyst visit:
https://brainly.com/question/29824383
#SPJ4
Utility Maximization Summary
Write a minimum of 150 words summarizing the material of this
module.
Answers
The to the question is that utility maximization refers to the concept of individuals or households making choices to maximize their overall satisfaction or well-being from consuming goods and services. In other words, it is the process of deciding how to allocate limited resources to obtain the most satisfaction or utility.
To explain this concept step-by-step, let's start with the assumption that individuals have preferences and can rank different combinations of goods and services in terms of their desirability or utility. The goal is to find the combination that maximizes overall utility.To achieve utility maximization, individuals must consider their budget constraint, which represents the limit on the amount of goods and services they can consume given their income and the prices of the goods. They need to find the combination of goods that provides the highest level of utility within their budget constraint.
One approach to utility maximization is the concept of marginal utility, which measures the additional satisfaction gained from consuming one more unit of a good. Individuals should allocate their budget in a way that the marginal utility per dollar spent is equal across different goods.In summary, utility maximization involves individuals making choices to allocate limited resources in a way that maximizes their overall satisfaction or utility. This is achieved by considering preferences, budget constraints, and the concept of marginal utility.
To know more about services visit:
https://brainly.com/question/33643094
#SPJ11
A user is redesigning a network for a small company and wants to ensure security at a reasonable price. The user deploys a new application-aware firewall with intrusion detection capabilities on the ISP connection. The user installs a second firewall to separate the company network from the public network. Additionally, the user installs an IPS on the internal network of the company. What approach is the user implementing
Answers
"Layered approach" will be the appropriate response.
The method that divides the OS into multiple layers, is a layered approach. The latter empowers application developers to modify their internal functions as well as enhances adaptability.The network idea throughout this method is generally separated into multiple levels and a certain responsibility or activity is delegated to every other layer.
Thus the above is the right answer.
Learn more layered approaches here:
https://brainly.com/question/10105615
2. What is the use of the percent sign (6) and underscore in the LIKE clause? How do they differ in
operation and production of a report?
Answers
Answer:
The percent sign % (or per cent sign in British English) is the symbol used to indicate a percentage, a number or ratio as a fraction of 100.
See also: U+2030 ‰ PER MILLE SIGN; U+2031 ...
Answer:
There are two wildcards used in conjunction with the LIKE operator. The percent sign represents zero, one or multiple characters. The underscore represents a single number or character.
Explanation:
There are two wildcards used in conjunction with the LIKE operator. The percent sign represents zero, one or multiple characters. The underscore represents a single number or character.
What were the important developments that occurred in photography that facilitated the creation of motion pictures? Two critical developments in photography that enabled the development of motion pictures were___and___
Answers
Answer:
"A moving picture is an illusion that makes a still photo seem to move. The basic principal behind motion pictures is the fast transition between one picture to the next, almost creating a seamless transition. A flip-book is a good example of this. Another example would be film used for old movies. The film contains negatives of an image which when light is shined through creates a "shadow" of the image. If you quickly transition the film from one image to the next you end up a motion picture."
Explanation:
brands can be positioned on multiple brand features-attributes-benefits (fab). which answer (see below) does not feature a product-, promotional, and/or pricing-difference on which firms would differentiate or position their brand? -Technologically superior
-Affordable
-Truly "cool" - in the most appealing sense of the word cool
-Cost Effectiveness
-Important
Answers
The answer that does not feature a product-, promotional, and/or pricing-difference on which firms would differentiate or position their brand is "Important."
Branding is a process of creating and maintaining a name, term, design, symbol, or other feature that distinguishes one company's products from those of others. The brand might be a combination of qualities, including physical features, color, price, and customer service, that establishes the brand in the minds of customers.Positioning is the method of creating a brand image in the mind of a consumer. Marketers accomplish this by emphasizing the product's distinctive attributes, benefits, or character. The main goal of positioning is to set a product apart from its competitors.
In marketing, a differentiation strategy is used to distinguish a company's product or service from those of its competitors. This might be achieved through product, promotion, and pricing differentiation.
Learn more about Marketers: https://brainly.com/question/25754149
#SPJ11