aw computing would like to improve its case lightning record page by including: *a filtered component to display a message in bold font when a case is saved as a critical record type. *a quick way to update the account status from the case layout. which two components should an administrator use to satisfy these requests?
Answers
As per the given statement, the two components that an administrator should use to satisfy these requests are as follows: Filtered component and Quick Action
The Filtered Component can be used to display a message in bold font when a case is saved as a critical record type. A Quick Action can be used to provide a quick way to update the account status from the case layout.
The Filtered component allows displaying the critical record type in bold font when the case is saved. The Quick Action is used to update the account status from the case layout. It enables the user to access a specific task directly without navigating to other pages and saves time.
Therefore, using these two components will improve the Case Lightning Record page by displaying the required information and providing quick access to update the
Learn more about Quick action at:
https://brainly.com/question/31447762
#SPJ11
Related Questions
Write a program that accepts a number as input, and prints just the decimal portion. Your program should also work if a negative number is inputted by the user. Lastly, write a print statement that states “The final outcome is: ”, followed by the decimal portion, and remember to change the final outcome to a string.
Sample Run
Enter a number: 15.789
Sample Output
The final outcome is: 0.789
Answers
A program that accepts a number as input, and prints just the decimal portion is given below:
The Programnum = float ( input ( " Insert the number : " ) )
res = str ( num )
print ( " Fractional portion : " , res [ res . find ( ' . ' ) + 1 : ] )
except:
print ( " ERROR ! This is not a number ! " )
ExplanationThe given program makes use of the float to indicate that a fractional number or decimal would be used and this is better than declaring with int.
Also, a print statement is used to show the decimal portion, and changes the final outcome to a string.
Also, the code can be written in the way below:
x = float ( input ( " Enter a number : " ) )
sub = ( x - int ( x ) )
print ( sub )
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
how to use software for simulation experiments and probability calculations, and how to interpret the results and observe patterns in the data.
Answers
using simulation and probability software can help to streamline the process of running experiments and calculations, and can make it easier to interpret the results. By following these tips, you can ensure that you are getting the most out of your software and making informed decisions based on the data.
Simulations and probability calculations can be performed using software that is designed for this purpose. The following are some tips on how to use such software and interpret the results:
1. Content loading: To use simulation and probability software, you will need to load the appropriate content into the program. This content may include data on variables, constraints, and other factors that will be used in the simulation or calculation. The content can be loaded into the software either manually or automatically.
2. Software usage: Once the content is loaded, the software can be used to perform the simulation or probability calculation. This may involve setting certain parameters, defining variables, and specifying other details of the experiment or calculation.
3. Interpretation of results: Once the simulation or calculation is complete, the results must be interpreted in order to make sense of the data. This may involve analyzing the data to identify patterns, trends, or other relevant factors. The results can then be used to draw conclusions about the experiment or calculation, and to inform future decision-making.
4. Observing patterns in data: Patterns in the data can be observed by looking at the graphs, charts, and other visualizations that are generated by the software. These visualizations can help to highlight trends, correlations, and other important factors that may not be immediately apparent from the raw data.
To know more about software Visit:
https://brainly.com/question/32393976
#SPJ11
when both a base class and a derived class have constructors, the base class’s constructor is called
Answers
When both a base class and a derived class have constructors, the derived class's constructor is called:
In object-oriented programming, when a class is derived from another class (base class), the derived class inherits the members and behaviors of the base class.
This includes constructors. When an object of the derived class is created, the derived class's constructor is responsible for initializing its own data members as well as invoking the base class's constructor to initialize the inherited members.
The derived class's constructor can explicitly specify which base class constructor to call using the super keyword (in languages like Java) or by providing arguments to match the base class constructor's parameters.
By calling the base class's constructor, the derived class ensures that the initialization of the inherited members from the base class is performed before executing its own constructor code. This allows for proper initialization and establishes the inheritance hierarchy in the object creation process.
Learn more about OOP here:
https://brainly.com/question/31741790
#SPJ11
describe the advantage of using a mini computer over a micro computer
Answers
Answer:
A mini-PC can have all the power of a standard desktop PC and you can easily change components like the RAM and hard drive. Hook it up to your screen of choice, whether that is a regular monitor, open frame display, or a TV screen. Cost. Mini-PCs are more affordable and very cost effective to operate.
Explanation:
https://brainly.in/question/42519168?tbs_match=1
Discuss the Autonomous Robots and Additive Manufacturing contribution to Smart Systems. Why are these two technologies are important for the Smart Systems? Explain the technologies with an example.
Answers
Additive manufacturing, also known as 3D printing, revolutionizes traditional manufacturing methods by constructing objects layer by layer. It enables rapid prototyping, customization, and on-demand production. For instance, in a smart healthcare system, additive manufacturing can be employed to produce personalized medical implants, such as customized prosthetics or dental implants, based on patient-specific requirements, resulting in improved patient outcomes and reduced lead times. Both technologies contribute to the advancement of Smart Systems by optimizing processes, enhancing productivity, and enabling customization in various industries.
refer to the exhibit. router r1 is configured with static nat. addressing on the router and the web server are correctly configured, but there is no connectivity between the web server and users on the internet. what is a possible reason for this lack of connectivity?
Answers
One possible reason for the lack of connectivity between the web server and users on the internet despite static NAT configuration on router R1 could be the absence of a corresponding access list that permits traffic to pass through.
It is important to note that static NAT is only responsible for the translation of the IP address of the web server to a public address that can be accessed from the internet. However, an access list is needed to permit traffic from the internet to access the web server. In this case, it is possible that the access list is not configured properly or is not present at all, thereby preventing internet traffic from accessing the web server despite the successful NAT translation. To address this issue, the access list should be properly configured to allow traffic from the internet to access the web server.
To learn more about NAT configuration
https://brainly.com/question/30583473
#SPJ11
Which of the following represent features of free software licensing? Check all of the boxes that apply.
is concerned with defending users' freedom of use
is always free of cost
makes source code available for editing
allows users to redistribute modified software as proprietary
is an idea that was developed by the Open Source Initiative (OSI)
Answers
Answer: A :is concerned with defending users’ freedom of use
C:makes source code available for editing
Explanation:
Answer:
a and c
Explanation:
proofreading is a. unnecessary for digital communication. b. a casual scan up and down the page or screen. c. more difficult on mobile devices. d. the quality inspection stage for a document. e. something you do immediately after finishing a document.
Answers
Proofreading is the quality inspection stage for a document. So, the correct option is D.
It is necessary for all forms of communication, whether digital or print. Proofreading helps to eliminate errors that may affect the reader's comprehension of the content being communicated. Proofreading is the process of checking a document for errors in spelling, grammar, and punctuation. It is the final stage of the writing process and is necessary to ensure that the final product is of high quality. Proofreading can be done on any type of document, whether it is digital or print. It is important to proofread all documents to avoid errors that may be embarrassing or costly.
Casual scan up and down the page or screenCasual scanning is not the same as proofreading. It involves quickly going through a document to get a general idea of its contents. It is not an effective way of catching errors that may be present in the document. Casual scanning is used when you are looking for specific information in a document, not when you are trying to ensure its accuracy
Proofreading is not more difficult on mobile devices than it is on a computer. However, it may be harder to spot errors on smaller screens, making it more important to pay attention to detail when proofreading on a mobile device.
Proofreading is not something you do immediately after finishing a document. It is the final stage of the writing process and should be done after the document has been edited and revised. Editing and revising involves checking the structure and flow of the document, as well as the overall content. Proofreading is done after these stages to check for errors that may have been missed.
You can learn more about Proofreading at: brainly.com/question/11845575
#SPJ11
The Sundae Shoppe has 3 types of ice cream (chocolate, vanilla, and strawberry) and 4 types of toppings (fudge, caramel, marshmallow, and whipped cream). Model all possibilities for a single dip, single topping sundae using either a tree diagram or a rectangular array.
Answers
A rectangular array can be used to model all possibilities for a single dip, single topping sundae at the Sundae Shoppe.
The rows of the array represent the ice cream flavors (chocolate, vanilla, strawberry) and the columns represent the toppings (fudge, caramel, marshmallow, whipped cream). Each cell in the array represents a unique combination of ice cream flavor and topping, resulting in a total of 12 possibilities.
learn more about:- rectangular array here
https://brainly.com/question/29199707
#SPJ11
what is the term for sending emails that imitate legitimate companies?
Answers
Answer:
phishing,,,, it imitates the company email so that when you get on the mail it can collect all your data and then can begin to hack using your information such as password
Phishing refers to the malicious attack method by attackers who imitate legitimate companies in sending emails in order to entice people to share their passwords, credit card or other sensitive personal information. ... If you do surrender such information, the attacker will immediately capture your personal information.
Generalized goals are more likely to be achieved than specific goals. True or False
Answers
They are likely to be achieved because they are well defined, clear, and unambiguous.
What are three formatting tools that are available in the shape styles group 
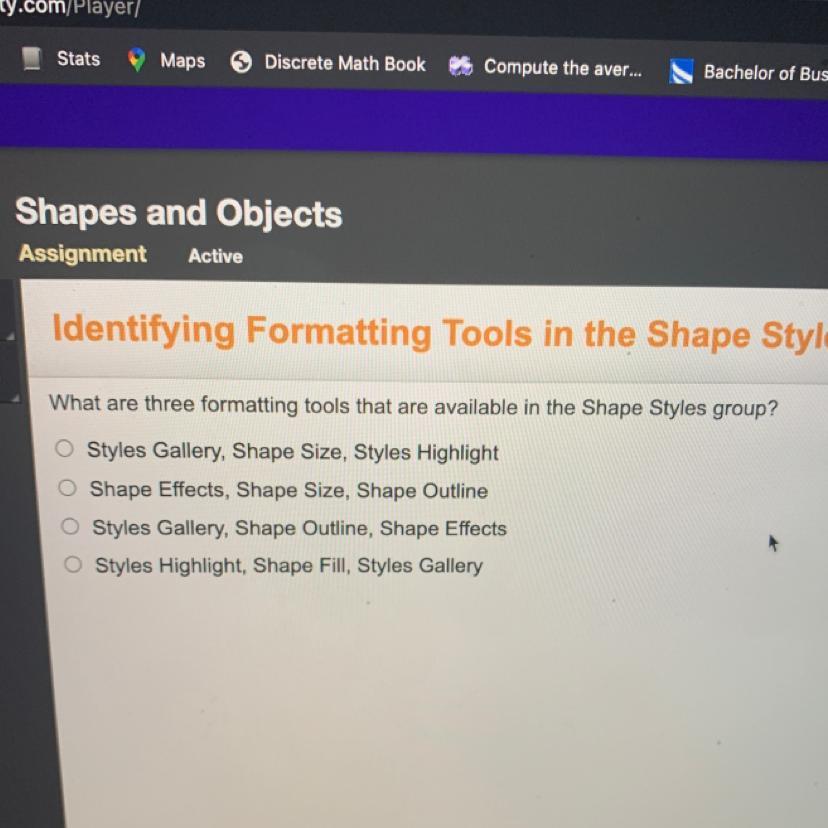
Answers
Answer: C. Shape Gallery, Shape Outline, Shape effects
Explanation:
When formatting on Microsoft, the Shape Styles group allows for one to adjust the shape fill by providing a styles gallery where a style can be chosen from for the fill.
It also has a shape outline feature to edit the outline of the shape to make it stand out more. There are also shape effects to enable the author to apply visual effects such as reflections and glows.
describe the possible problems resulting from the limitations in the resources in a computer system.
Answers
Performance degradation,Data loss,Security issues.
Describe the possible problems resulting from the limitations?
A computer system's limitations in resources can cause a variety of problems. The following are some of the potential problems that may arise:
Performance degradation:
When a system is low on resources, it may begin to slow down or become unresponsive. Programs may take longer to load, and simple tasks may take longer to complete.
Program crashes: Programs may become unstable and crash more frequently if there are insufficient system resources. This may cause data loss, and the program may be unable to recover from the crash.
Data loss:
If a program crashes, any data that was not saved may be lost. If the system runs out of memory or storage, data may be lost. This may result in critical files becoming inaccessible.
System errors: When a system lacks resources, it may generate error messages. These messages can be vague and difficult to interpret, making troubleshooting more difficult. Some errors may cause the system to stop working entirely.
Security issues:
When a system lacks resources, it may become more vulnerable to security threats. For example, an attacker could exploit a vulnerability in a program that has crashed and is not functioning correctly. Alternatively, the system may not have the resources to run security software, leaving it unprotected.
Learn more about troubleshooting.
brainly.com/question/30048504
#SPJ11
Suppose the free-space list is implemented as a bit vector. What is the size of the bit vector of a 1TB disk with 512-byte blocks? a) 2MB. b) 2 to the power of 8 MB. c) 28MB. d) 8MB.
Answers
The correct answer is c) 28MB. The size of the bit vector for a 1TB disk with 512-byte blocks is: a) 2MB.
To calculate the size of the bit vector, we need to know the total number of blocks in a 1TB disk with 512-byte blocks.
1TB = 1024GB ,1GB = 1024MB ,1MB = 1024KB ,1KB = 1024 bytes
1TB = 1024 x 1024 x 1024 x 1024 bytes
1TB / 512 bytes per block = 2 x 10^12 / 512 = 3.90625 x 10^9 blocks
The available options, which might be due to rounding or using different values for conversions (i.e., using 1024 instead of 1000). Please double-check the values and assumptions provided in the question, and let me know if I can help with any further clarifications.
To know more about Bit Vector visit:-
https://brainly.com/question/29854433
#SPJ11
Mobile device apps that enable users to pay for things or check-in to hotels or venues use _________ technology. Select one: a. GPS b. GIS c. TCP/IP d. NFC
Answers
Answer:
ip
vgfjffffffffvfdxx
Explanation:
fsxqwvetsgsrwfuxhsrwctsdqccdhvxrsbx7shgxfrxvshxrc
một số được gọi là thác đổ nếu phần tử biểu diễn thập phân của nó nhiều hơn một chữ số đồng thời theo chiều từ trái qua phải chữ số đứng trước lớn hơn chữ số đứng sau
dữ liệu vào tệp THACDO.INP gồm nhiều dòng,mỗi dòng chứa số nguyên N
kết quả ra tệp THACDO.OUT gồm nhiều dòng thông báo,mỗi dòng ghi "CO" nếu N là thác đổ và ngược lại thông báo "KHONG" nếu N không phải
Answers
Which action requires an organization to carry out a Privacy Impact Assessment?
A. Storing paper-based records
B. Collecting PII to store in a new information system
C. Collecting any CUI. including but not limited to PII
D. Collecting PII to store in a National Security System
Answers
Collecting PII to store in a new information system requires an organization to carry out a Privacy Impact Assessment.
What is Privacy Impact Assessment?
Privacy Impact Assessment (PIA) is a process of examining how personal data is collected, used, stored, and shared by an organization. A PIA helps to identify and mitigate potential privacy risks to individuals and their personal information. It is an important tool for organizations to ensure that their data collection practices are compliant with applicable privacy laws and regulations. The PIA process includes analyzing the data flow from collection to storage, understanding the purpose of the data collection, and determining the privacy risks associated with the data. By conducting a PIA, organizations can identify and address potential privacy concerns, ensure that appropriate security measures are taken to protect personal data, and improve overall data management practices.
To learn more about Privacy Impact Assessment
https://brainly.com/question/14297557
#SPJ1
Objectives • Research best practices for dashboard presentation • Create a dashboard to monitor key performance indicators
• Prepare a memo explaining the dashboard and implementation plan for the dashboard to present to the chief clinical officer Instructions Read the scenario that follows, perform research as indicated and create a dashboard and memo to present to the chief clinical officer. Scenario Karen White, RHIA, was recently hired as the new HIM director at a 450-bed suburban teaching hospital. Karen has been in the HIM field for approximately three years. Her past experience includes being a data quality specialist for the registration department of a large teaching facility. She is familiar with the functions of data reporting, but not as familiar with the other functions within the HIM department. Her boss, the chief clinical officer, wants her to create a department dashboard for monitoring key performance indicators within the department. He would like the dashboard sent to him on the first day of each month. The HIM department is comprised of the following functions and staff to support the functions: • Coding: Inpatient, outpatient, emergency department, and physician hospital-based coding Staff: 1 coding manager, 1 data quality coder, 15 remote-based coders • Electronic Record Management (ERM): Document imaging and file retrieval Staff: 1 ERM lead, 2 document imaging technicians, 3 file retrieval clerks • Record Processing (RP): ROI, electronic chart completion, and transcription (all outsourced) Staff: 1 RP lead, 2 ROI coordinators, 1 chart analyst, 1 transcription coordinator • Administrative Support: Phone support for ROI and file retrieval, administrative support for director Staff: 1 lead support specialist (director support position), 2 support specialists • Technical Support: Maintain hardware and software, computer upgrades, interface issues, workflow errors, perform duplicate master patient index clean up and health record merges Staff: 1 application specialist, 2 application analysts Assumptions • Each functional area within the HIM department maintains productivity and quality performance data for the activities performed but none of the data is aggregated or shared on a regular basis, and there are no benchmarks in place for the activities. • The dashboard will be basic: two indicators from each of the five functional areas (coding, ERM, RP, administrative support, technical support), and two indicators for the overall HIM department. • The hospital does not offer a specific dashboard product. • Additional research is needed in order to create a dashboard. • The chief clinical officer requested a draft and implementation plan for the dashboard. • Actual numbers for each key performance indicator should not be included on the dashboard; it should be a representation of what the dashboard will look like. Students will identify the metric/indicator - but do not have to provide actual figures. Deliverables Create a user-friendly dashboard including key performance indicators from each functional area and the HIM department. Make sure a benchmark is included for each key performance indicator. Create a memo to the chief clinical officer to accompany the dashboard using these parameters: 1. There is no template provided. Part of the assignment requires the student to perform research on effective dashboards and create their own dashboard. 2. The dashboard should be created in Excel. 3. The memo to the chief clinical officer should include at least the following regarding implementation: data collection method, communication plan for the managers and leads, and the HIM department timeline. 4. An APA-formatted reference must be provided to support the dashboard research. This should not be part of the memo, but be provided following the memo.
Answers
The objective is to create a department dashboard to monitor key performance indicators (KPIs) within the HIM department and prepare a memo with an implementation plan to present to the chief clinical officer.
What is th objective of the scenario described?In this scenario, Karen White, the new HIM director at a teaching hospital, is tasked with creating a department dashboard to monitor key performance indicators (KPIs) within the HIM department.
The department consists of coding, electronic record management, record processing, administrative support, and technical support functions. The assumption is that each functional area has its own productivity and quality data, but it is not aggregated or shared regularly.
The dashboard is expected to include two indicators from each functional area and two indicators for the overall HIM department, with benchmarks for each indicator. The hospital does not have a specific dashboard product, so additional research is needed to create the dashboard. The chief clinical officer requested a draft and implementation plan for the dashboard.
The deliverables for this project include a user-friendly dashboard created in Excel, along with a memo to the chief clinical officer explaining the implementation plan, including data collection methods, communication plan, and the HIM department timeline. An APA-formatted reference should be provided to support the dashboard research.
Learn more about objective
brainly.com/question/31018199
#SPJ11
What is the MINIMUM number of paths that would need to be broken to prevent Computing Device A from connecting with Computing Device E? a) 1 b) 2 c) 3 d) 4
Answers
Answer:
The answer is "Option c".
Explanation:
In the given question the device A is connected by 3 wires, contributing all of them, which also includes several connector paths. When all the wires of A are broken down, and if all of this leaves no routes that can be used. Even so, if it is done to E, it's also linked to four different routes. Its solution would've been C because its value will be the MINIMUM.
Answer:
c
Explanation:
How many keys are required in asymmetric encryption?
Answers
Two keys are used in asymmetric cryptography; if you encrypt with one key, you can decrypt with the other. An algorithmic one-way cryptographic transformation is called hashing.
In symmetric encryption, how many keys are there?only one key Symmetric cryptography encrypts and decrypts data using the same key. Two keys are used in asymmetric cryptography, one for encryption and the other for decryption.
What two kinds of keys are employed in asymmetric encryption?A key pair is used in asymmetric encryption; a distinct key is used for encryption and decryption. Typically, one of the keys is referred to as the private key, and the other as the public key.
To know more about encryption visit:-
https://brainly.com/question/9404669
#SPJ4
what is workplace procedure?
Answers
Answer:
MY ANSWER
Explanation:
Workplace procedures explain specific action plans for employees when carrying out a policy. Workplace procedures are important because they tell your employees how to deal with a situation and when.14 Mar 2021
Answer:
ksksozozozosmsmsmssoqoqaokanzxbbxjdjsoaoalassbsbsjjajajakakakakanananannan
PC Shopping Network may upgrade its modem pool. It last upgraded 2 years ago, when it spent $115 million on equipment with an assumed life of 5 years and an assumed salvage value of $15 million for tax purposes. The firm uses straight-line depreciation. The old equipment can be sold today for $80 million. A new modem pool can be installed today for $150 million. This will have a 3 -year life, and will be depreciated to zero using straight-line depreciation. The new equipment will enable the firm to increase sales by $25 million per year and decrease operating costs by $10 million per year. At the end of 3 years, the new equipment will be worthless. Assume the firm's tax rate is 35 percent and the discount rate for projects of this sort is 12 percent. What are the Free Cash Flows, the NPV and IRR of the replacement project? Note: There is double jeopardy on this problem. If you miss a free cash flow, you will miss the NPV and the IRR. (6 points) FCF 0
= FCF 1
= FCF 2
= FCF 3
= NPV= IRR=
Answers
The replacement project involves upgrading the modem pool of PC Shopping Network. The old equipment was purchased 2 years ago for $115 million, has a 5-year assumed life, and a salvage value of $15 million.
The old equipment can be sold today for $80 million. The new equipment can be installed for $150 million and has a 3-year life. The new equipment is expected to increase sales by $25 million per year and decrease operating costs by $10 million per year. The tax rate is 35% and the discount rate is 12%. We need to calculate the Free Cash Flows (FCFs), the Net Present Value (NPV), and the Internal Rate of Return (IRR) of the replacement project.
To calculate the FCFs, we need to determine the cash inflows and outflows associated with the project. In this case, the cash inflows are the increase in sales ($25 million) and the decrease in operating costs ($10 million) each year. The cash outflows include the initial investment in the new equipment ($150 million) and the tax savings resulting from depreciation expense. By subtracting the cash outflows from the cash inflows for each year, we can calculate the FCFs.
The NPV of the project is the present value of the FCFs, discounted at the given rate of 12%. By summing up the present values of the FCFs, we can calculate the NPV. If the NPV is positive, the project is considered financially viable.
The IRR is the discount rate at which the NPV of the project becomes zero. It represents the project's internal rate of return or the rate of return that the project is expected to generate. The IRR is calculated iteratively until the NPV reaches zero.
To obtain the specific values of FCF0, FCF1, FCF2, FCF3, NPV, and IRR, the calculations need to be performed based on the given information and formulas for each year.
learn more about salvage value here
https://brainly.com/question/28387066
#SPJ11
define ; proprietary software.
Answers
how would running your server in a chroot jail limit the impact of command execution vulnerabilities?
Answers
chroot jail is a security feature that help to contain and limit the potential damage caused by command execution vulnerabilities by isolating the server and limiting the attacker's access to the file system.
Running a server in a chroot jail limits the impact of command execution vulnerabilities by isolating the server from the rest of the system. A chroot jail is a mechanism that allows a process to run with a limited view of the file system, such that the process can only see files within the jail.
When a command execution vulnerability is exploited, an attacker can execute arbitrary commands on the server. However, if the server is running in a chroot jail, the attacker's commands will be limited to the files and directories within the jail. This means that the attacker will not have access to sensitive files or system-level utilities outside of the jail.
Additionally, chroot jail can limit the access to the system resources, and in case of a compromise, the attacker will not have access to system files, libraries, and other resources, which makes it more difficult to perform further malicious activities.
Learn more about vulnerabilities here:
https://brainly.com/question/30296040
#SPJ4
how lhospital rule calculator with steps
Answers
By differentiating the functions, L'hopital's Rule Calculator determines the limits of undefinable functions. The outcome and steps are provided by this hospital calculator.
What does the L Hospital rule's full name mean?"lopital" is how to pronounce L'Hôpital. He was a 16th-century French mathematician. It claims that after taking the derivative of each function, the limit when dividing one function by another is the same (with some special conditions shown later).
Who made the rule at the hospital public?Although John (Johann) Bernoulli of Switzerland developed L'Hospital's Rule in 1694, it wasn't until the Marquis de l'Hospital's calculus textbook Analyse des Infiniment Petits that it was first made public.
To know more about lhospital rule visit:-
https://brainly.com/question/14105620
#SPJ4
consider a source and destination host. before packets leave the source host, the host needs to define the path over which the packets will travel to reach the destination host. false
Answers
Before packets leave the source host, the source host does not define the path over which the packets will be traveling to reach the destination host. Thus the given statement is false.
When packets are transmitted over the network from a source host to a destination host, the source host does not determine the path through which packets will travel toward the destination host from the source host. Instead, it is the router that defines the best path and directs the packets from the source host to the destination host.
What is a router?
A router is a network layer device that determines the optimal path along which packets are forwarded over the network. Based on network layer information, routers forward packets from one network to the other network.
You can learn more about routers at
https://brainly.com/question/28180161
#SPJ4
When someone refers to "space" on a computer or device, they are usually referring to _____, which allows the user to save a file for future use, even after the computer has been turned off.
Answers
Answer:
Memory.
Explanation:
When someone refers to "space" on a computer or device, they are usually referring to memory, which allows the user to save a file for future use, even after the computer has been turned off.
In Computer science, a memory is a term used to describe the available space or an electronic device that is typically used for the storage of data or any computer related information such as images, videos, texts, music, codes and folders. There are basically two (2) main types of memory;
1. Read only memory (ROM).
2. Random access memory (RAM).
Answer: Secondary Storage
Explanation: Source: trust me bro
plz answer this question
the three (3) classification of computers.
Answers
Explanation:
micro computers
mini computers
super computers
adds and removes printers or fax machines using add printer wizard
Answers
Answer:
1.Adds and removes printers or fax machines using add printer wizard.
2.Customized elements for pointing device.
3.change or customized how folders behave in windows.
4.creative things for managing power options on your computer.
5.configure our customized options for dialing with connected phone or modem device.
6.make windows more accessible for people with physical challenges or disabilities.
7.change screen appearance.
8.setup how taskbar or start menu appears or behaves.
9.provide system information and advanced settings.
10.configure network adapter cards, services and protocols or join workgroup/domain.
Explanation:
Describe how you use the ruler icon to indent text in two different ways.
Answers
Drag the arrow at the top of the ruler to add or change the first line indent. Only the first line of the paragraph where cursor is located will be indented as a result. Choose the triangle and move it to create a hanging indent.
How do you make a ruler indent?Choose the text in which to insert a first line indent. On the ruler, drag the triangular marker on the top left of the ruler to the place you want the indentation to start, for example to the 1" mark.
How many types of indent are there on ruler?Ruler format the left, right, top and bottom margins of page. Paragraph indentation: Indentation describes the starting point of a paragraph. Ruler format the First line indentation.
To know more about cursor visit:-
https://brainly.com/question/30355731
#SPJ1