can inverted page tables be implemented on a generic x86 or risc-v machine, whose hardware implement a non-inverted, hierarchical page table?
Answers
With the help of Multilevel Paging, inverted page tables can be implemented on a generic x86 or risc-v machine, whose hardware implement a non-inverted, hierarchical page table.
What is page tables?A virtual memory system in a computer operating system uses a page table as its primary data structure to store the mapping between virtual addresses and physical addresses. Physical addresses are utilised by the hardware, more specifically the random-access memory (RAM) subsystem, whereas virtual addresses are utilised by the programme that is run by the accessing process.
Virtual address translation, which is required to access data in memory, heavily relies on the page table. Every process in operating systems that employ virtual memory is given the impression that it is working with sizable, continuous blocks of memory. Physically speaking, the memory associated with each process may be spread out over various regions of physical memory or it may have been transferred (paged out) to secondary storage.
Learn more about page table
https://brainly.com/question/29776022
#SPJ4
Related Questions
Fill in the blank with the correct response.
People in STEM careers are considered
thinkers who reach conclusions through sound judgment and reasoning
Save and Exit
Next
What goes in the blank between considered and thinkers
Answers
Answer:
logical
Explanation:
Answer:
logical thinkers
Explanation:
they are logical thinkers because they know whats going on
Question 2 (1 point)
Anastigmatic lenses were made possible by the development of
optical glass.
a
b
Joliet
Jena
Jeddah
Jordan
C
8
d
Answers
Answer:
The correct option is;
Jena
Explanation:
The first anastigmatic lenses were calculated in 1886 in Jena by the mathematician Paul Rudolph, who was employed by Carl Zeiss, from the characteristics of the new Jena glasses (Jenaer Glas in German) which is a quality heat and shock resistant glass first invented and produced by Otto Schott
In 1889, the Zeiss Anastigmat, which was the first anastigmatic lens was launched and it in 1890it was renamed and sold as Protar.
Consider two perfect complements, a keyboard and a computer. If the price of the keyboard only is increased, then the substitution effect of the price change will
Answers
If the price of the keyboard, which is a perfect complement to the computer, is increased, the substitution effect of the price change will be minimal or nonexistent.
In the case of perfect complements, such as a keyboard and a computer, the goods are consumed together in fixed proportions. They are highly complementary, meaning that one is practically useless without the other. As a result, if the price of the keyboard increases, consumers will not substitute it with another product because it is necessary to use it in conjunction with the computer. The substitution effect refers to the consumer's tendency to switch to a substitute product when the price of one good changes. However, in the case of perfect complements, there are no close substitutes available, so the substitution effect is limited. Consumers will continue to purchase the keyboard, despite its increased price, to maintain its complementary functionality with the computer.
Learn more about perfect complements here:
https://brainly.com/question/32634352
#SPJ11
Kate saves her work on a secondary storage device that is fairly new, and uses flash technology instead of disks.
Kate is using a(n) __________ drive.
CD/DVD-ROM
SSD
hard disk
optical disk
Answers
Kate saves her work on a secondary storage device that is fairly new and uses flash technology instead of disks. Kate is using an SSD drive. Thus the correct answer is B.
What is a secondary storage device?The devices that store the information of the user in a protected way outside of the computer with the help of external devices are called secondary storage devices. This includes Hard disk, optical disk, CD disk, and so on.
SSD is an acronym for Solid State Storage Devices. They are silicon-based devices that use non-moving flash memory to store information digitally. These include USB flash drives, SIM cards, SD cards, and pen drives.
SSD will be used to enhance the performance of the computer as they help to provide quick access to information as compared to regular hard drives used due to the latest technology.
Therefore, option B SSD is appropriate.
Learn more about secondary storage devices, here:
https://brainly.com/question/11599772
#SPJ5
Create three procedures that will convert a value given to Fahrenheit to the following temperatures:
Celsius
Kelvin
Newton
The procedures should be named
C2F
K2F
N2F
The following equations can be used to convert different temperature types to Fahrenheit :
Kelvin - F = (K - 273.15) * 1.8000 + 32
Celsius - F = C * 9/5 + 32
Newton - F = N * 60 / 11 + 32
You should pass the all values to the procedures using the floating point stack. You should return the converted temperature back using the floating point stack. In other words, the converted temperature should be at ST(0)
Once you have the procedures written test them in main by getting a value in Fahrenheit from the keyboard. You might want to store it in a real variable. Convert the value to the three different temperatures and output them.
Your output should look like the following
Enter a value in C
38.1
In Fahrenheit that value is 100.58
Enter a value in K
45.95
In Fahrenheit that value is -376.96
Enter a value in N
23.98
In Fahrenheit that value is 162.8
Press any key to close this window . . .
Do NOT use any global variables. If need be create local variables.
Required:
The temperature conversion procedures must be in a separate asm file called conversion.asm. This means you should have main.asm and conversion.asm. You can use constant values in the data segment of conversion.asm but you MUST pass the temperature to be converted to the procedure through the floating point stack and return the converted value back to main on the floating points stack.
Make sure to do it in assembly language with irvine library and not c++
Answers
Here's an implementation of the three conversion procedures in assembly language using Irvine library:
conversion.asm:
INCLUDE Irvine32.inc
.DATA
FAHRENHEIT REAL ?
CELSIUS REAL 9.0, 5.0, 32.0
KELVIN REAL 273.15, 1.8000, 32.0
NEWTON REAL 60.0, 11.0, 32.0
.CODE
C2F PROC
fld qword ptr [esp+4] ; load Celsius value from stack
fmul celsius ; multiply by 9/5
fadd kELVIN+8 ; add 32
fstp qword ptr [esp+4] ; store result back on stack
ret
C2F ENDP
K2F PROC
fld qword ptr [esp+4] ; load Kelvin value from stack
fsub kELVIN ; subtract 273.15
fmul kELVIN+4 ; multiply by 1.8000
fadd kELVIN+8 ; add 32
fstp qword ptr [esp+4] ; store result back on stack
ret
K2F ENDP
N2F PROC
fld qword ptr [esp+4] ; load Newton value from stack
fmul newton ; multiply by 60/11
fadd newton+8 ; add 32
fstp qword ptr [esp+4] ; store result back on stack
ret
N2F ENDP
main.asm:
INCLUDE Irvine32.inc
.CODE
main PROC
call Clrscr
; get Fahrenheit value from user
mov edx, OFFSET promptF
call WriteString
call ReadFloat
; convert to Celsius
sub esp, 8
fstp qword ptr [esp]
call C2F
fstp qword ptr [esp]
mov edx, OFFSET resultC
call WriteString
call WriteFloat
; convert to Kelvin
sub esp, 8
fstp qword ptr [esp]
call K2F
fstp qword ptr [esp]
mov edx, OFFSET resultK
call WriteString
call WriteFloat
; convert to Newton
sub esp, 8
fstp qword ptr [esp]
call N2F
fstp qword ptr [esp]
mov edx, OFFSET resultN
call WriteString
call WriteFloat
exit
main ENDP
.DATA
promptF BYTE "Enter a value in Fahrenheit: ",0
resultC BYTE "In Celsius that value is ",0
resultK BYTE "In Kelvin that value is ",0
resultN BYTE "In Newton that value is ",0
.CODE
END main
To test the program, assemble and link both files and run the resulting executable. The program will prompt the user for a Fahrenheit temperature, convert it to Celsius, Kelvin, and Newton using the three procedures, and output the results as shown in the example output provided in the question.
Learn more about assembly language here:
https://brainly.com/question/31227537
#SPJ11
is monitor is a television
Answers
Answer:
No, a monitor only shows what a different device tells them too however, a tv can be connected to nothing and show tv shows
Reggie is writing a paper on his school laptop for history class. What does Reggie need to create in order to save the document and work on it later?
A. a file
B. a spreadsheet
C. an app
D. systems software
Answers
Answer:
file
Explanation:
got it right on edge 2021
Q3. The 1st day of 2022 was Saturday, write a program to input any day number within the month of January and print which day was it. Also check whether the day number entered is a valid date or not.
For example, Input:
Enter day number: 20 Output: Thursday
Input:
Enter day number: 30
Output: Sunday Input:
Enter day number: 34 Output: Invalid day number
Answers
Answer: Here's the code if you solve it using python
Explanation:
day="Saturday"
date=int(input("Enter the day number: "))
if (date<=0) or (date>31):
print("Invalid day number")
else:
if date%7==1:
day="Saturday"
elif date%7==2:
day="Sunday"
elif date%7==3:
day="Monday"
elif date%7==4:
day="Tuesday"
elif date%7==5:
day="Wednesday"
elif date%7==6:
day="Thursday"
elif date%7==0:
day="Friday"
print(day)
Let's see
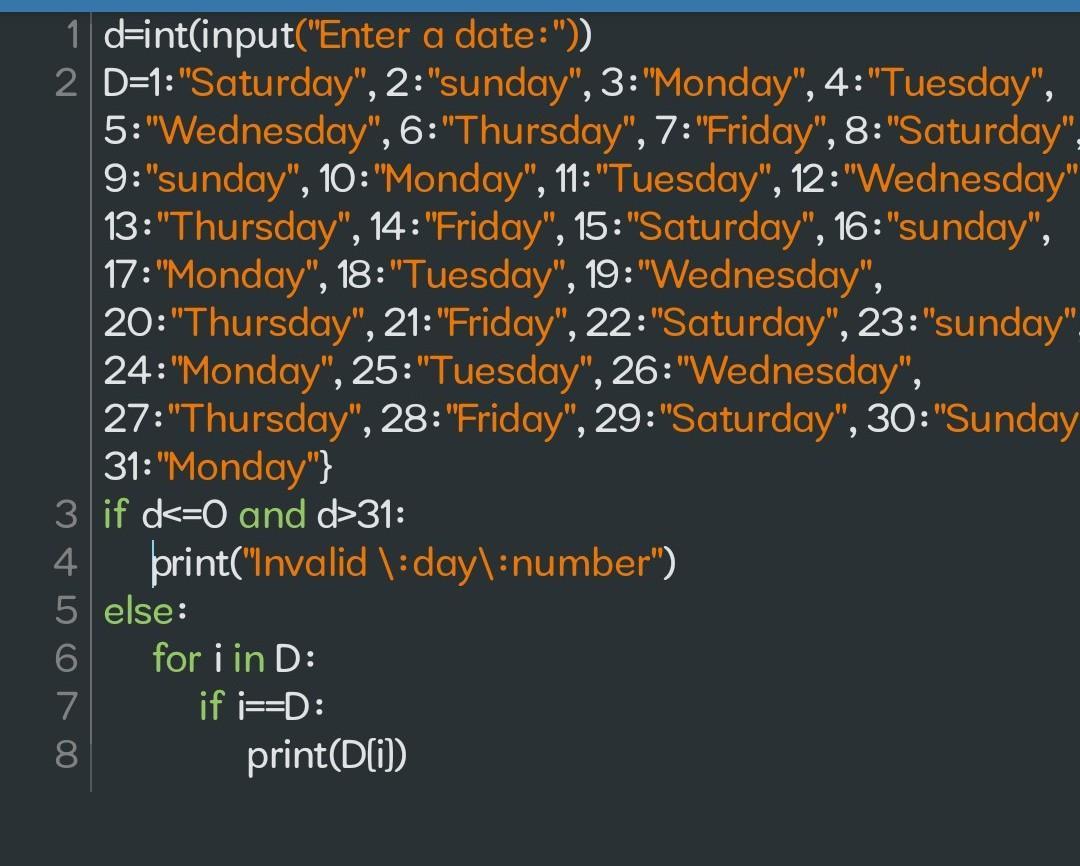
\(\tt d=int(input("Enter \:a \:date:"))\)
\(\tt D=\left\{1:"Saturday",2:"sunday",3:"Monday",4:"Tuesday",5:"Wednesday",6:"Thursday",7:"Friday",8:"Saturday",9:"sunday",10:"Monday",11:"Tuesday",12:"Wednesday",13:"Thursday",14:"Friday",15:"Saturday",16:"sunday",17:"Monday",18:"Tuesday",19:"Wednesday",20:"Thursday",21:"Friday",22:"Saturday",23:"sunday",24:"Monday",25:"Tuesday",26:"Wednesday",27:"Thursday",28:"Friday",29:"Saturday",30:"Sunday",31:"Monday"\right\}\)
\(\tt if\:d<=0\:and\:d>31:\)
\(\quad\tt print("Invalid \:day\:number")\)
\(\tt else:\)
\(\quad\tt for\:i\:in\:D:\)
\(\quad\quad\tt if\:i==d:\)
\(\quad\quad\quad\tt print(D\left[i\right])\)
Guys can anyone tell me answer from this photo Get Branilliest

Answers
Answer:
1. A computer itself
2.I don't no
(9 pts) what are the cidr addresses for a network if all its addresses start with 145.98? and if this network has exactly two subnets, what are the cidr addresses for each of its subnets?
Answers
The cidr addresses for each of its subnets are 145.98.0.1 to 145.98.127.255 and 145.98.128.1 to 145.98.255.255.
What is a network?A network is a collection of two or more computers or other electronic devices that are linked together to exchange data and share resources.
It should be noted that 145.98 = 10010001.01100010
Then there are 2^(32-16) = 2^16 addresses possible. The range of addresses is from 145.98.0.1 to 145.98.255.255
If there are 2 subnets, 1 bit will be used for the subnet. So each subnet will have 2^32-17 = 2^15 addresses.
For subnet 1 range of IP shall be 145.98.0.1 to 145.98.127.255
For subnet 2, the range of IP shall be 145.98.128.1 to 145.98.255.255
Learn more about network on:
https://brainly.com/question/1326000
#SPJ1
needham company has prepared a classified balance sheet for fiscal year 10. multiple classification and reporting errors exist in the balance sheet.
Answers
Needham Company's classified financial sheet for fiscal year 10 contains numerous classification and reporting mistakes.
These mistakes may involve misclassifying objects as assets, liabilities, or equity, calculating totals or subtotals incorrectly, or presenting financial data in an inappropriate way. Common mistakes include misclassifying current liabilities as long-term liabilities, long-term assets in current assets, or omitting key elements entirely. These mistakes may mislead stakeholders and affect the company's financial picture. Needham Company should carefully evaluate and correct the inaccuracies, making the required adjustments, and abiding by the proper accounting standards and procedures in order to ensure accurate financial reporting.
learn more about classification here :
https://brainly.com/question/606324
#SPJ11
migrating a traditional database design to the web can require design modification, additional software, and some added expense. t or f
Answers
A standard database architecture may need to be modified for the web, which might include purchasing new software and costing more money.
What purposes serve databases?database, often termed online version, any collection pf data, or content, that is particularly arranged for quick searches and retrievals by a robot. To make it simple to save, retrieve, update, and delete the file while performing various data-processing functions, databases are built.
What is a database, exactly?In computing, a database is an organized set of data that is accessible and stored electronically. Large databases are housed on data centers or cloud storage, whilst small data can be kept on a file system. .
To know more about Database visit :
https://brainly.com/question/13275751
#SPJ1
what is the maximum effective range of a typical passive rfid tag?
Answers
The maximum effective range of a typical passive RFID tag varies depending on the frequency it operates and the tag's design, operating frequency, environmental conditions, and the reader's power output. However, the range for passive RFID tags is generally relatively short compared to active RFID tags.
Generally, the effective range of a passive RFID (Radio Frequency Identification) tag is between a few centimeters to a few meters. However, in some cases, it can be extended up to 10 meters or more using specialized equipment. It is important to note that the effective range of a passive RFID tag can be affected by factors such as the presence of metal, liquids, and other materials that can interfere with the signal.
Learn more about RFID tags here: https://brainly.com/question/32414075.
#SPJ11
Need Some Photography help

Answers
cellular networks use digital signals and can transmit voice and data at different speeds based on how fast the user is moving; it supports video, web browsing, and instant messaging
Answers
What behavior do elements in a stack follow?
Answers
Answer:
last in, first out, or LIFO behavior
Explanation:
B
What finger should be on the T key?
1. Right Index finger
2. Right Middle finger
3. Left Index finger
4. Left Middle finger
Answers
Answer:
3 left index pointer
Explanation:
How is a digital representation of analog data a form of abstraction? Why is the quality of the photo, music, etc better when more samples are taken? Music is an example of analog data. What other examples of analog data can you think of?
Answers
Answer:
1. This is because non-essential parts of the analog data is cut of so as to represent the analog data digitally.
2. This is because it mirrors closely to the original analog material.
3. i. Temperature ii. Speed ii. Distance iv. Electric current
Explanation:
1. How is a digital representation of analog data a form of abstraction?
Digital representation of analog data is a form of abstraction because, since abstraction, which is the removal of non-essential parts of a material so as to reduce complexity, also non-essential parts of the analog data is cut of so as to represent the analog data digitally.
2.Why is the quality of the photo, music, etc better when more samples are taken?
The quality of these items is better because, as more samples are taken, it reduces the error in the sampling and the item(photo, music etc) mirrors closely to the original analog material.
3. What other examples of analog data can you think of?
i. Temperature ii. Speed ii. Distance iv. Electric current
did your batting improve? what techniques did you try to improve your number of hits?
Answers
Yes, my batting has improved significantly. I have implemented various techniques to enhance my number of hits.
To improve my batting, I focused on technique and practice. Firstly, I worked on my stance, grip, and footwork to ensure a solid foundation. I studied the bowlers' techniques and analyzed their strengths and weaknesses. This allowed me to anticipate their deliveries and make better shot selections. I also practiced extensively in the nets, facing different types of deliveries and honing my timing and shot execution. Additionally, I worked on my physical fitness, which helped me generate more power and maintain concentration throughout the innings. By combining these strategies, I was able to improve my overall batting performance and achieve more consistent and impactful hits.
Learn more about physical fitness here
brainly.com/question/14338730
#SPJ11
Kris is the project manager for a large software company. Which part of project management describes the overall project in detail? Analysis report Resources document Scope Scope creep
Answers
Answer:
The given option "Resource document" is the correct answer.
Explanation:
Whenever it applies to chronology as either the documentation a resource records collection of specific documents should indeed be regarded as a component of this kind of record. The resource component encompasses a series of proclamations provided by the researcher including its memorandum, and therefore is willing to take responsibility for each other by the very same body is nonetheless accountable again for the file.The remaining three options do not apply to something like the specified scenario. And the latter is the correct one.
Answer:
Resource document
Explanation:
Plzzzz help me
Part B
Often, computer professionals suffer from an RSI disease known as carpal tunnel syndrome (CTS). Research online and write about its causes and
symptoms.
Answers
Answer:
Answered below
Explanation:
Carpal tunnel syndrome is a disease which occur as a result of pressure on the median nerve supplying the hand. The median nerve passes under the carpal tunnel, which is a band of tendons at the wrist, and gets compressed.
Causes include;
Excessive, prolonged, repetitive typing, diabetes, obesity, arthritis.
Symptoms include;
Numbness of the hand, weakness of the hand, inability to grasp, tingling sensations on the parts of the hand affected.
Write a programme in python to read a line and print the number of uppercase,lowercase,alphabet and digit in it
Answers
The code in phyton that can reads a line of text from the user and prints the number of uppercase letters, lowercase letters, alphabetic characters, and digits in it is given as follows
def count_characters(line):
uppercase_count = 0
lowercase_count = 0
alphabet_count = 0
digit_count = 0
for char in line:
if char.isupper():
uppercase_count += 1
alphabet_count += 1
elif char.islower():
lowercase_count += 1
alphabet_count += 1
elif char.isdigit():
digit_count += 1
print("Uppercase letters:", uppercase_count)
print("Lowercase letters:", lowercase_count)
print("Alphabetic characters:", alphabet_count)
print("Digits:", digit_count)
# Read a line of text from the user
line = input("Enter a line of text : " )
# Call the function to count the characters
count_characters(line)
How does this work ?
We define the count_characters function in this program, which accepts a line of text as input.
Uppe rcase letters, lowercase letters, alphabetic characters, and numerals have their counts set to zero.
Then we go over the line, incrementing the counters based on the character type ( isupper( ), islower(), isdigit()). Finally, we publish the category counts.
Learn more about Python:
https://brainly.com/question/26497128
#SPJ1
4. Write technical term for the following statements
A) The computers designed to handle specific single tasks.
B) The networked computers dedicated to the users for professional wrok.
C) The computers that uses microprocessor as their CPU.
D) A computer that users analog and digital device.
E) The computer that processes discontinuous data.
F) The portable computer which can be used keeping in laps.
G) The general purpose computers used keeping on desk.
Answers
Answer:
a) Special-purpose computer
b)
c)microcomputers
d) hybrid computer
e) digital computer
f) laptop computers
g) desktop computers.
Please mark me as brainlist :)T/F. a comment in excel can capture an ongoing text conversation.
Answers
It is accurate to say that an excel comment can record a text dialogue in progress.
Can Excel threaded chats incorporate comments?The way comments function has changed in Excel for Microsoft 365. Now that comments are threaded, you can discuss the data with other readers. Notes function similarly to comments did in older iterations of Excel and are used for creating notes or remarks regarding the data.
What is a comment and how is it used?Comments are text notes that are included into programs to provide explanations of the source code. In a programming language, they are used to describe the program, remind programmers of the tough things they recently accomplished with the code, and assist the following generation.
To know more about comments visit:-
https://brainly.com/question/30318947
#SPJ1
b.) A programmer can precede an expression with
to temporarily
convert an expression's value to the indicated data type, such as changing an int to a double.
Answers
Answer:
a type cast
Explanation:
A type cast converts a value to another type.
Pls match the following extra points for brainly answer

Answers
Please check the image for the answer.
✍️ By Benjemin ☺️

Plaintext is the input to a ________, with ciphertext being the output. In cryptography, algorithms transform plaintext into ciphertext, and ciphertext into plaintext. These respective processes are called encryption and decryption.
Answers
Plaintext is the input to a cryptographic algorithm, with ciphertext being the output. In cryptography, algorithms transform plaintext into ciphertext, and ciphertext into plaintext. These respective processes are called encryption and decryption.
What is Plaintext?Plaintext is the original, readable message or data that is input to a cryptographic algorithm.
The algorithm processes the plaintext using various mathematical operations to produce an unreadable ciphertext.
Encryption is the process of converting plaintext into ciphertext, while decryption is the process of converting ciphertext back to plaintext using a secret key or algorithm.
Cryptography ensures secure communication by making it difficult for unauthorized parties to read the ciphertext without the key.
Read more about plaintext here:
https://brainly.com/question/25658352
#SPJ1
What type of software problem is it when a particular program on the pc works for a short time but then suddenly terminates and its not hardware related
Answers
When a particular program on a PC works for a short time but then suddenly terminates, it is likely a software problem related to the program itself or the operating system. There could be several reasons for this issue, including:
Software bugs: The program may have a coding error that causes it to crash after running for a short time. This could be due to a memory leak, infinite loop, or other programming errors.Compatibility issues: The program may not be compatible with the operating system or other software on the PC, causing it to crash.Corrupted files: The program files may have become corrupted, which can cause the program to crash.Insufficient resources: The program may require more system resources than are available, causing it to crash.To resolve this issue, users can try several solutions, such as updating the program, reinstalling it, running a virus scan to ensure that the PC is not infected with malware, and checking for any conflicts with other software or hardware. If the issue persists, users may need to seek help from the software developer or a technical support professional.
To learn more about operating system click the link below:
brainly.com/question/6689423
#SPJ4
stem will help you learn to use ____skills to solve everyday life problems.
Answers
Answer:
science, technology, engineering,and math
Answer:
Science, Technology, Engineering, and Math
Jeremy has been asked by his manager to begin drafting a report on last year sales figures when he’s midway through the report a co-worker stops by and asks if Jeremy will help him with a problem she has on her project Jeremy also needs to respond to number of emails before the end of the day he is able to accomplish all these tasks which positive workplace behavior has he demonstrated
Answers
Answer:
Time management.
Explanation:
Answer:
Adaptability.
Explanation:
because he was being ASKED to do it if he wasn't asked and did it, it's initiative.