Design a circuit that has two inputs, clk and X, and produces one output O. X may change every clock cycle, and the change happens at the falling edge. The circuit samples the input at every rising edge of the clock. If the input is 1, consider as read a 1, else read a 0. O is 1 (for one clock cycle, from positive edge to positive edge) if the last three bits read are 001, with 1 as the most recent bit
Answers
To design a circuit that satisfies the given specifications, we can use a shift register and a combinational logic circuit. The shift register will store the last three bits read, and the combinational logic circuit will check if the bits match the pattern 001.
The circuit will have two inputs: clk and X. The clk input is a clock signal that triggers the circuit to sample the X input at every rising edge. The X input is the binary input that may change every clock cycle, and the change happens at the falling edge. To detect the falling edge of the clock signal, we can use a flip-flop.
At every rising edge of the clock, the circuit will sample the X input and store the bit in a shift register. The shift register will have three stages, and it will shift the bits to the right at every clock cycle. The most recent bit will be stored in the first stage, and the oldest bit will be stored in the third stage.
The combinational logic circuit will check if the three bits stored in the shift register match the pattern 001. If the bits match the pattern, the output O will be set to 1 for one clock cycle, from positive edge to positive edge. Otherwise, the output will be set to 0.
To implement the combinational logic circuit, we can use a series of AND gates and inverters. We can connect the output of the shift register to the inputs of the AND gates, and use the outputs of the gates to check if the bits match the pattern. If the three bits match the pattern, the output of the last AND gate will be 1, and we can use an inverter to generate the output O.
To learn more about Circuit designing, visit:
https://brainly.com/question/2969220
#SPJ11
Related Questions
how do you loop a makebeat in earsketch
Answers
Answer:
i dont know if this help but To do this, we will use a 'for loop'. The “for loop” allows the programmer to call a section of code repeatedly within a range of values. The range() function will return integer values depending on the arguments.
Explanation:
All of the salespeople in hyperactive media sales use laptops, so that they can take their applications and data on the road to client sites. one of the salespeople, bob, has a docking station so that his laptop easily connects to a printer and external monitor when he is in the office. what should you do to ensure that windows 10 uses the proper device drivers when bob is in and out of the office?
Answers
The thing that a person should do to ensure that windows 10 uses the proper device drivers when bob is in and out of the office is to make use of the Microsoft stores to check for the right driver or go online to search for it and then download as well as install it.
How do I manage my drivers in Windows 10?In Windows 10, the Device Manager is known to be a kind of widget that can be found in the Control Panel and it is known to be one that tends to provides information in regards as well as the control over the device drivers.
For a person to launch Device Manager, type in the word "Windowskey-X" and then click on Device Manager from the displayed menu.
Note that the drivers needed for Windows 10 are:
Chipset Video Audio and Network (Ethernet/Wireless), etc.For laptops one can get them if they download the latest Touch Pad drivers.
Therefore, The thing that a person should do to ensure that windows 10 uses the proper device drivers when bob is in and out of the office is to make use of the Microsoft stores to check for the right driver or go online to search for it and then download as well as install it.
Learn more about windows 10 from
https://brainly.com/question/27960518
#SPJ1
Which type of software can be used without paying a license fee and can be modified to add capabilities not realized by its originators?.
Answers
A type of software which can be used without paying a license fee and modified to add capabilities not realized by its originators is referred to as an: C. Open-source software.
What is a software license?A software license can be defined as a formal agreement between an end user (customer) and the owner of a software program or software developer, that allows him or her to perform certain tasks with the software application (program), usually after paying a license fee.
The types of software license.In Computer technology, there are three (3) main types of software programs based on usage rights and these include the following:
Shareware softwareFreeware softwareOpen source softwarePurchased licenseIn Computer science, an open source can be defined as a terminology for software that all end users can use or modify for free without paying any license fee (money).
Read more on software here: brainly.com/question/25703767
#SPJ1
Complete Question:
Which type of software can be used without paying a license fee and can be modified to add capabilities not realized by its originators? *
10 points
Application software
System software
Open-source software
Proprietary software
What is the confirmation or validation of an event or object?a.Fact.b.Data.c.Information technology.d.All of the above.
Answers
Fact is the Confirmation or validation refers to the process of verifying that an event or object is true or accurate.
Fact is a statement or piece of information that can be verified and is considered to be true. It is a confirmed or validated event or object. Facts can be supported by evidence and documentation, and they are an important part of understanding and explaining the world around us. They are different from opinions or beliefs, which are subjective and may not be supported by evidence. In scientific research, facts are the foundation of theories and hypotheses, and are subject to testing and verification to establish their validity.
Confirmation or validation refers to the process of verifying that an event or object is true or accurate. This is often done through the use of evidence or other forms of documentation. In this context, a "fact" would be the confirmation or validation of an event or object, as it is a piece of information that can be verified and is considered to be true. While data and information technology may be used to confirm or validate facts, they do not represent the confirmation or validation itself.
Learn more about Validation here:
https://brainly.com/question/14356883.
#SPJ4
Write a program in the if statement that sets the variable hours to 10 when the flag variable minimum is set.
Answers
Answer:
I am using normally using conditions it will suit for all programming language
Explanation:
if(minimum){
hours=10
}
Write a Python program to get the top three item prices in a shop. (15 points) Sample data: {'Apple': 0. 50, 'Banana': 0. 20, 'Mango': 0. 99, 'Coconut': 2. 99, 'Pineapple': 3. 99} Expected Output: Pineapple 3. 99 Coconut 2. 99 Mango 0. 99
Answers
To write a Python program to get the top three item prices in a shop. Here the code that represent the situation given:
def get_top_three_prices(items):
sorted_items = sorted(items.items(), key=lambda x: x[1], reverse=True)
top_three_items = sorted_items[:3]
for item, price in top_three_items:
print(item, price)
data = {'Apple': 0.50, 'Banana': 0.20, 'Mango': 0.99, 'Coconut': 2.99, 'Pineapple': 3.99}
get_top_three_prices(data)
How this codes work?In order to determine the top three of the price. The program need to do the following step :
Create a dictionary containing the item names and pricesStep Use the `sorted()` function with the `reverse` parameter set to `True` to sort the dictionary by price in descending orderStep Loop through the sorted dictionary and print the top three items and their prices. Here's the Python code to get the top three item prices in a shopAs per data given, by following this steps, the top three items and their prices in the given shop are Pineapple for 3.99, Coconut for 2.99, and Mango for 0.99.
Learn more about looping
https://brainly.com/question/31033657
#SPJ11
A web developer overhears an executive’s username and password, and then uses it to download the company’s secret chocolate-chip cookie recipe. He makes the cookies at home and posts the recipe on his blog.
identity theft
corporate espionage
software piracy
sale of trade secrets
Answers
Answer:Sale of trade secrets
Explanation:
Just took it
Answer:
sale of trade secrets
Explanation:
Just took it edgen 2020 is correct
A web developer overhears an executive’s username and password, and then uses it to download the company’s secret chocolate-chip cookie recipe. He makes the cookies at home and posts the recipe on his blog.
trade
/trād/
the action of buying and selling goods and services.

how to enter privileged exec mode on a cisco packet tracer
Answers
To enter privileged exec mode on a cisco packet tracer, enter the command enable to enter Privileged EXEC mode.
What is exec mode?The default setting for the device is user EXEC mode, which supports the most basic level of user permissions.
A Cisco router begins in User EXEC mode when you turn it on or log in. This model is extremely constrained and does not permit configuration modifications. Enter the command configure terminal to enter Global Configuration mode while in Privileged EXEC mode (router#).
Therefore, use the command enable to enter Privileged EXEC mode on a Cisco packet tracer to access this mode.
To learn more about exec mode, refer to the link:
https://brainly.com/question/5213706
#SPJ1
TRUE OR FALSE: It is possible to style elements uniquely no matter what class they belong to
Answers
I believe it is true.
What is that tool that makes liquid metal? Ik I might sound dumb but I'm rlly curious
(the thing on the right)

Answers
Answer:
it’s called a solder. It’s used to permanently fuse two metals together. And they’re used in many different areas like construction, technology, etc.
That pic that you have i think is a computer chip or something similar.
So a solder is the tool that is used to make metal into liquid.
hope this helps and pls mark me brainliest :)
How do we “read” and “write” in MAR and MDR memory unit, please help I am very confused :)
Answers
Answer:
No entiendo
Por favor traduce al español
Read the mini case study below. It documents a project’s (in some cases catastrophic) failure. In light of this module’s topics, discuss two contributing factors to the failure of this project.
Organization: Dyson Ltd – UK
Project type: Development of an electric car
Project name: The Dyson
Date: Oct 2019
Cost: £500M
Synopsis:
The future of transportation is here to see and it is of course electric! As a result, the development of electric cars has been a growth area for the past ten years and the pace of change continues to grow.
That growth and the potential to revolutionize the car market has interested both newcomers and the incumbents alike. Of the newcomers Tesla has of course made the cut and has proven they have the stamina to stay in the game. Other start-ups and have come, gone, been resurrected and gone again. At the time of writing Rivian, Fisker and other start-ups are still in the game, but they face the monumental challenge of taking on the likes of Volkswagen, Nissan, GM and other organizations that already have the infrastructure to design, build, sell and support vehicles on a worldwide basis.
One of the recent challengers to throw in the towel is Dyson Ltd. James Dyson is one of the UK richest men. An engineer, a techie and an entrepreneur, Dyson made his fortune developing high-end home appliances (most notably vacuum cleaners). Always looking for fields in need of his engineering prowess, Dyson started down the difficult road of developing a from-scratch electric car. The jump from vacuum cleaners to cars is of course massive and the decision to invest in the project was a quantum leap of faith.
Normally such a move would require careful due diligence and active management of the downside risks. It appears, however, that as a privately owned business, Dyson took a different path. In a Mar 2020 interview with business magazine "Fast Company" Dyson was asked about the role up front market analysis plays in developing Dyson products. Dyson replied…
"We never think of the market for the product. It’s not something that guides us. We look for a problem in the product, and then we go to solve the problem. Hand dryers aren’t a particularly big market compared to hair dryers or vacuum cleaners, but that didn’t stop us from wanting to make a hand dryer. Having an interesting technology for products decides what we do, whether the market is small or big."
To be fair, Dyson’s leap of faith did make a lot of progress and reports indicate that his nascent project got as a far as a fully functional vehicle that was near ready for production. However, as costs mounted past the £500M mark, the monumental costs of product launch came into view. Recognizing that to cover the investment and production costs the finished product was likely to have a price higher than the market would bare, the project has been canned.
Note: Dyson is a privately owned company and the cost of the project was apparently born by Mr. Dyson himself. Although Mr. Dyson can certainly afford to absorb the £500M cost, I think we should also remember the time, talent, sweat and tears of the team who work on the project. To see all of that effort wasted is a heart break in its own right. Hopefully some of the technology will still find a way forward and some of that effort will be rewarded, but as it stands, the project may not be catastrophic for Dyson, but it is likely a massive disappointment for those who vested themselves in the project’s success.
Answers
The failure of the Dyson electric car project can be attributed to a combination of factors. The lack of thorough market analysis and consideration of the competitive landscape prevented Dyson from adequately positioning their product in the automotive market.
Two contributing factors to the failure of the Dyson electric car project are:
Lack of market analysis and consideration of competitive landscape:
Dyson's approach of focusing primarily on solving a problem rather than considering the market demand and competition played a significant role in the project's failure. The decision to develop an electric car without thoroughly analyzing the market and understanding the challenges posed by established automotive manufacturers with global infrastructure put Dyson at a disadvantage. While Dyson had a track record of innovation and success in the home appliances industry, the automotive sector is highly complex and competitive. Not adequately assessing the market dynamics and competition hindered their ability to develop a competitive product and establish a viable market position.
Mounting costs and pricing challenges:
Although the project made substantial progress and reached the stage of a fully functional vehicle near production readiness, the costs associated with launching the product became a significant concern. As the costs exceeded £500 million, the realization that the final product would likely have a price higher than what the market would bear posed a major obstacle. Dyson's decision to halt the project can be attributed to the realization that the financial viability of the electric car was questionable due to the high production costs and anticipated pricing challenges. Failing to align the project's costs with market expectations and feasible pricing strategies contributed to its ultimate discontinuation.
The failure of the Dyson electric car project can be attributed to a combination of factors. The lack of thorough market analysis and consideration of the competitive landscape prevented Dyson from adequately positioning their product in the automotive market. Additionally, the mounting costs and pricing challenges posed significant financial risks and made the project economically unviable. While the project may not have had catastrophic consequences for Dyson as a company, it was undoubtedly a disappointment for the team involved and a missed opportunity to leverage their technological advancements in the automotive industry.
To know more about electric car visit
https://brainly.com/question/30016414
#SPJ11
a company has point-of-sale devices across thousands of retail shops that synchronize sales transactions with a centralized system. the system includes an amazon api gateway api that exposes an aws lambda function. the lambda function processes the transactions and stores the transactions in amazon rds for mysql. the number of transactions increases rapidly during the day and is near zero at night. how can a developer increase the elasticity of the system most cost-effectively?
Answers
The developer can set up an Amazon EC2 Auto Scaling group, which will automatically scale the system up and down depending on the number of transactions.
What is SQL and MYSQL
SQL (Structured Query Language) is a programming language used for managing data stored in relational databases. It is used for performing various operations such as creating databases, inserting data into the database, updating data, retrieving data, and deleting data from the database. SQL can be used to query data from a single table or multiple tables. MySQL is an open source relational database management system (RDBMS) based on Structured Query Language (SQL). MySQL is a popular choice of database for use in web applications, and is a central component of the widely used LAMP web application software stack (and other “AMP” stacks).
To know more about SQL and MYSQL
https://brainly.com/question/28484922
#SPJ4
write a single C program that will:
1. Have a major processing loop that will ask the user if they
want to go again and stay in the loop until they ask to quit.
2. Will ask the user if they want to create a file (your choice as to
the filename) and if so,
create a file with 100 random numbers (from 1 - 100) in it. The file create operation must then close the file.
3. Will ask the user if they want to process the file and if so,
the program will open the file,
read the numbers from the file and find the average of the numbers, the biggest and the smallest numbers,
close the file and then report the average and the biggest and smallest numbers.
4. Programming note: the program must have error checking to ensure
that the file was successfully opened before writing to or reading from it.
If you use functions for the create File and process File operations, you
may use Global variables.
Answers
The below given is the code in C which will have a major processing loop that will ask the user if they want to go again and stay in the loop until they ask to quit:
```#include #include #include #define FILE_NAME "random_number_file.txt"FILE* fp;int createFile();int processFile();int main() { int opt = 1; while (opt) { printf("\nPlease choose the following options:\n0: Quit\n1: Create File\n2: Process File\n"); scanf("%d", &opt); switch (opt) { case 0: printf("Exiting the program..."); break;
case 1: createFile(); break;
case 2: processFile(); break; default: printf("Invalid option. Try again.\n"); } } return 0;} ```
The above code will ask the user if they want to create a file (your choice as to the filename) and if so, create a file with 100 random numbers (from 1 - 100) in it. The file create operation must then close the file.```int
create File() { int count = 0, number = 0; fp = fopen (FILE_NAME, "w"); if (fp == NULL) { printf("Unable to create file.\n"); return 0; } srand((unsigned int) time(NULL)); for (count = 0; count < 100; count++) { number = rand() % 100 + 1; fprintf(fp, "%d\n", number); } fclose(fp); printf("File created successfully!\n"); return 1;}```
The above code will ask the user if they want to process the file and if so, the program will open the file, read the numbers from the file and find the average of the numbers, the biggest and the smallest numbers, close the file and then report the average and the biggest and smallest numbers.
```int processFile() { int count = 0, number = 0, total = 0, max = 0, min = 101; float avg = 0; fp = fopen(FILE_NAME, "r"); if (fp == NULL) { printf("Unable to read file.\n"); return 0; } while (fscanf(fp, "%d", &number) != EOF) { count++; total += number; if (number > max) max = number; if (number < min) min = number; } if (count == 0) { printf("File is empty.\n"); fclose(fp); return 0; } avg = (float) total / count; fclose(fp); printf("Average: %.2f\n", avg); printf("Maximum number: %d\n", max); printf("Minimum number: %d\n", min); return 1;}```
The above code will have error checking to ensure that the file was successfully opened before writing to or reading from it. It is also using Global variables for create File and process File operations. Hence the required code is given.
To know more about average refer to:
https://brainly.com/question/130657
#SPJ11
Select the correct answer. In which item is energy stored in the form of gravitational potential energy? A. a slice of bread B. a compressed spring C. an apple on a tree D. a stretched bow string
Answers
Answer:
C. an apple on a tree
Explanation:
Energy can be defined as the ability (capacity) to do work. The two (2) main types of energy are;
a. Kinetic energy (KE): it is an energy possessed by an object or body due to its motion.
b. Gravitational potential energy (GPE): it is an energy possessed by an object or body due to its position above the earth.
Mathematically, gravitational potential energy is given by the formula;
\( G.P.E = mgh\)
Where;
G.P.E represents gravitational potential energy measured in Joules.
m represents the mass of an object.
g represents acceleration due to gravity measured in meters per seconds square.
h represents the height measured in meters.
In an apple on a tree, energy is stored in the form of gravitational potential energy.
The following code will not compile. Which of the options below would allow the code to
compile and run as intended?
if (x >= -10 and < 10):
print("In range")
Answers
Answer:
if (x >= -10 and x < 10):
print("In range")
Explanation:
you're missing an x in the if statement. program is getting confused when you run because it doesnt know what to compare after the and if you add x it'll know what to compare.
all this is saying is that if x is greater than or equal to -10 and x is less than 10 its in range!
if (x >= -10 and x< 10):
print("In range")
Write a program that continually reads user input (numbers)
until a multiple of 7 is provided. This functionality must be
written in a separate function, not in main().
Answers
Here is a Python program that continually reads user input (numbers) until a multiple of 7 is provided. This functionality is written in a separate function, not in main(). The program uses a while loop to keep reading input until the user enters a multiple of 7:```def read_until_multiple_of_7():
x = int(input("Enter a number: "))
while x % 7 != 0:
x = int(input("Enter another number: ")) print("Multiple of 7 detected: ", x)```Here's how the code works:1. The function `read_until_multiple_of_7()` is defined.2. The variable `x` is initialized to the integer value entered by the user.3. A while loop is used to keep reading input until the user enters a multiple of 7.
The loop condition is `x % 7 != 0`, which means "while x is not a multiple of 7".4. Inside the loop, the user is prompted to enter another number. The input is read as an integer and stored in the variable `x`.5. When the user finally enters a multiple of 7, the loop exits and the function prints a message indicating that a multiple of 7 was detected, along with the value of `x`.Note: Make sure to call the `read_until_multiple_of_7()` function from your `main()` function or from the interactive interpreter to test it out.
To know more about Python visit:
https://brainly.com/question/30391554
#SPJ11
Edhesive 2.2 code practice
questions 1 and 2
Python
Answers
Answer:
1)
a = float(input("Enter an integer: "))
print(a + 1)
print (a + 2)
print (a + 3)
2)
a = float(input("Enter a decimal: "))
b = float(input("Enter another decimal: "))
c = float(input("Enter a third decimal: "))
print("sum: " + str(a + b + c))
Answer:
2.2 question 1
x = int(input("Enter an integer: "))
print(x + 1)
print(x + 2)
print(x + 3)
2.2 question 2
a = float(input("Enter number here: "))
b = float(input("Enter number here: "))
c = float(input("Enter number here: "))
print(a + b + c)
Explanation:
There you go let me know if it didnt work
what is full form off computer
Answers
Answer:
Explanation:
Computer is not an acronym, it is a word derived from a word "compute" which means to calculate. ... Some people say that COMPUTER stands for Common Operating Machine Purposely Used for Technological and Educational Research.
in a physical star topology, what happens when a workstation loses its physical connection to another device
Answers
In a physical star topology, if a workstation loses its physical connection to another device, the device is disconnected from the network.
A physical star topology is a type of network topology in which devices are connected to a central hub or switch. Each device has its own separate cable that connects it to the hub or switch.The hub or switch serves as the central connection point for all devices on the network. This topology is widely used in local area networks (LANs) because it is simple to implement and maintain.If a workstation loses its physical connection to another device, it cannot communicate with other devices on the network.
The device will be isolated and cannot send or receive data from other devices. As a result, the network's performance may be negatively impacted. The network will continue to function, but the device will no longer be able to participate in the network. In summary, if a workstation loses its physical connection to another device in a physical star topology, the device is disconnected from the network, and it will no longer be able to communicate with other devices on the network.
Learn more about physical star topology: https://brainly.com/question/28901549
#SPJ11
A document intended for World Wide Web distribution is commonly referred to as
A. optical
B. magnetic
C. volume
D. pages
Answers
correct option is D. Web page. A document or resource on a Web site, transported over the Internet, created using the established standards, and made viewable to a user through a program called a browser.
A document intended for World Wide Web distribution is commonly referred to as a page. Thus, the correct option for this question is D.
What is a document on a world wide web called?A web page (also written as a webpage) is a document that is suitable for the World Wide Web and web browsers. It is a type of document which can be displayed in a web browser such as Firefox, Chrome, Opera, Microsoft Internet Explorer or Edge, or Apple's Safari.
According to the context of this question, a web browser takes you anywhere on the internet. It significantly retrieves information from other parts of the web and displays it on your desktop or mobile device. The information is transferred using the Hypertext Transfer Protocol, which defines how text, images, and video are transmitted on the web.
Therefore, a document intended for World Wide Web distribution is commonly referred to as a page. Thus, the correct option for this question is D.
To learn more about Web pages, refer to the link;
https://brainly.com/question/28431103
#SPJ2
Is the GPU shortage over? What do you think this means for other
chip-using industries? Why else do you think the prices are falling
on chip based products?
Respond to the question in full sentences.
Answers
The GPU shortage is not entirely over, but there have been some improvements in recent months. The GPU shortage has primarily been driven by a combination of factors, including the global semiconductor supply chain constraints, increased demand due to the growth of gaming and remote work, and the high demand for GPUs in cryptocurrency mining.
As for the impact on other chip-based products, the semiconductor shortage has affected various industries such as automotive, consumer electronics, and telecommunications. Manufacturers of these products have faced challenges in meeting the high demand, leading to delays and increased costs. However, as production capacity for semiconductors gradually ramps up and various governments invest in domestic chip production, the situation may improve in the coming months.
In summary, the GPU shortage is still ongoing but showing signs of improvement. The consequences of this shortage extend to other chip-based products, leading to production delays and increased costs across different industries. As semiconductor production increases and global efforts to resolve the issue continue, we can hope to see more stable supply chains and reduced shortages in the near future.
Learn more about GPU here:
https://brainly.com/question/27139687
#SPJ11
Question : What can protect a computer from a transient voltage that's too high but not too low?
Reasoning : An uninterruptible power supply (UPS) takes the functionality of a surge suppressor and combines that with a battery backup. So now, our computer is protected not only from surges and spikes, but also from sags, brownouts, and blackouts. Use a UPS to protect your computer from power outages!
Answers
A UPS (Uninterruptible Power Supply) can protect a computer from both high and low transient voltages by combining surge suppression with battery backup.
A UPS is designed to provide reliable power protection to electronic devices, including computers, by offering two primary functions: surge suppression and battery backup. Surge suppression is responsible for safeguarding against high transient voltages or power surges that can damage sensitive components within a computer. It actively monitors the incoming power supply and suppresses any voltage spikes or surges to a safe level, preventing them from reaching and harming the connected devices.
In addition to surge suppression, a UPS also incorporates battery backup capabilities. This means that during a power outage, the UPS will seamlessly switch from the main power source to its internal battery, ensuring a continuous and uninterrupted power supply to the computer. This protection extends beyond high transient voltages and also safeguards against low voltages, such as sags, brownouts, and even complete blackouts. By providing a stable power source, the UPS prevents the computer from experiencing sudden shutdowns or potential damage due to inconsistent power levels.
In conclusion, by combining surge suppression with battery backup, a UPS offers comprehensive protection for a computer against both high and low transient voltages. It safeguards the system from power surges and spikes while also providing a reliable power source during outages, ensuring the computer remains operational and protected from potential electrical hazards.
Learn more about Uninterruptible Power Supply here :
https://brainly.com/question/31536929
#SPJ11
Multiple TCP streams can distinguished on a given machine using.
Select one:
a. network interface cards
b. All of the mentioned ,t. c. Ports
0 d. DNS addresses
Answers
The correct answer is option c. Ports.
Multiple TCP streams can be distinguished on a given machine using ports. In TCP/IP networking, ports are used to identify specific applications or services running on a device. Each TCP stream is associated with a unique combination of source and destination ports, allowing the system to differentiate between multiple concurrent connections.By using different port numbers for each TCP stream, the operating system can correctly route incoming packets to the corresponding application or service, ensuring that the data is delivered to the correct destination.
Learn more about TCP here:
https://brainly.com/question/27975075
#SPJ11
Which type of document would most likely find the disaster recovery plan for a corporation?
Answers
The type of document that would most likely contain the disaster recovery plan for a corporation is called a Business Continuity Plan (BCP).
The BCP is a comprehensive document that outlines the procedures and protocols to be followed in the event of a disaster or disruption to normal business operations. It includes a detailed plan for recovering and restoring critical systems, processes, and infrastructure.
The BCP typically covers various scenarios such as natural disasters, cyberattacks, power outages, and other emergencies. It includes information about the roles and responsibilities of key personnel, communication protocols, backup and recovery strategies, and the steps to be taken to ensure the resumption of business operations as quickly and smoothly as possible.
The BCP is an essential document for ensuring business resilience and minimizing the impact of disasters on the corporation.
To know more about Business visit:-
https://brainly.com/question/29896340
#SPJ11
What combination will always produce both real and virtual images? real objects with diverging lenses virtual objects with converging lenses erect objects with diverging lenses real objects with converging lenses
Answers
Real objects with converging lenses will always produce both real and virtual images.
What are lenses?A lens is an object that has been created to manipulate light rays, which are created by an object, and then transfer the image of the object onto a surface so that it can be seen.
The lens will produce an image that is magnified or reduced in size. The optical properties of the lenses can either converge or diverge light rays passing through them. The image produced by the lenses is either real or virtual.
The image can either be real or virtual. Real images can be projected onto a screen, while virtual images cannot be projected onto a screen. The distance between the lens and the image is what determines the size of the image. The distance between the lens and the object also affects the size of the image
Learn more about lenses at
https://brainly.com/question/11134508
#SPJ11
which of the following answers refer to the characteristic features of the - ( ) ipv4 address space? (select 2 answers)
a. ::1 b. FE80::/10 c. 0:0:0:0:0:0:0:1 d. 169.254/16 e. 127.0.0.1
Answers
The characteristic features of the IPv4 address space can be found in options (d) 169.254/16 and (e) 127.0.0.1. The given options represent different IP addresses and address ranges.
Let's examine each option to identify the characteristic features of the IPv4 address space. Option (d) 169.254/16 corresponds to an address range within the IPv4 link-local address space. This range is reserved for automatic private IP addressing when a device cannot obtain an IP address from a DHCP server. Option (e) 127.0.0.1 represents the loopback address in the IPv4 address space. This address is reserved for the loopback interface, which allows a device to send network traffic to itself. It is commonly used for testing and diagnostic purposes. Options (a) ::1 and (c) 0:0:0:0:0:0:0:1 are IPv6 addresses. Option (b) FE80::/10 represents an IPv6 link-local address range. Therefore, the characteristic features of the IPv4 address space can be identified in options (d) 169.254/16 and (e) 127.0.0.1.
Learn more about DHCP server here:
https://brainly.com/question/30490668
#SPJ11
anyone can help me answer this puzzle i really need it right now. thanks!
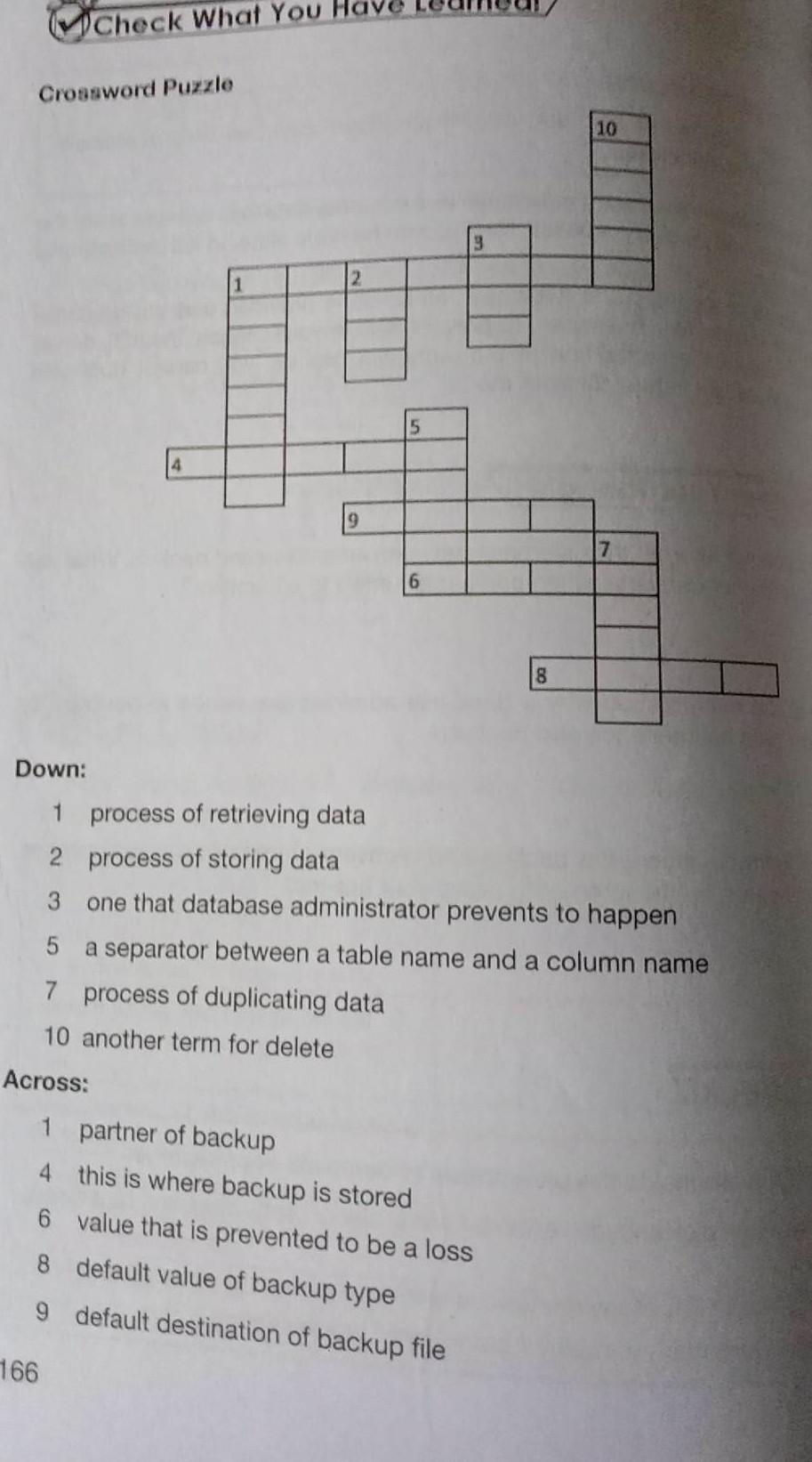
Answers
The right words that can be used to fill up the blank spaces in the puzzle are as follows:
data is fetching. data storagebreachperiodredundancydelete is remove or dropHow to fill up the blanksTo insert the correct words in the puzzles, we need to understand certain terms that are used in computer science.
For example, a data breach occurs when there is a compromise in the systems and it is the duty of the database administrator to avoid any such breaches. Also, data fetching is another jargon that means retrieving data.
Learn more about data fetching here:
https://brainly.com/question/14939418
#SPJ1
The principle of symmetrical balance applies only to multiplayer games, not to single-player experiences. (1 point)
True
False
Answers
Answer:
True
Explanation:
I had this on a quiz before and i passed with a 100
Answer:
True was wrong for me so i say false....
Explanation:
alice is a network engineer who has been tasked with researching a virtual private network (vpn) tunneling protocol to be used by her company. it must be able to pass traffic through a network address translation (nat) server and be compatible with a number of well-known proprietary and open source platforms. what solution does she select?
Answers
Anyone might access the home network by using the default username and password, which are presumably publicly available on the Internet.
What is virtual private network ?
An encrypted connection between a device and a network via the Internet is known as a virtual private network, or VPN. Secure transmission of sensitive data is aided by the encrypted connection. It makes it impossible for unauthorized parties to eavesdrop on the traffic and enables remote work for the user. The use of VPN technology is common in business settings. By creating secure connections over the Internet, a VPN expands a company network. Traffic stays private while traveling because it is encrypted between the device and the network. While working away from the office, an employee can safely connect to the company network. A VPN connection is possible even on cellphones and tablets.
To know more about virtual private network , visit
https://brainly.com/question/14122821
#SPJ4