Forcing the compiler to deal with pipeline hazards can cause binary compatibility problems down the road, when new microarchitectures have different ________ lengths.
Answers
Answer:
Forcing the compiler to deal with pipeline hazards can cause binary compatibility problems down the road, when new microarchitectures have different pipeline lengths.
Explanation:
With the microarchitectures having divergent lengths of pipeline, by compiler forcing the process with pipeline hazards can result in incompatibility issues.
By consequence, the best explanation for the blank space is pipeline
Related Questions
xamine the following output:
Reply from 64.78.193.84: bytes=32 time=86ms TTL=115
Reply from 64.78.193.84: bytes=32 time=43ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=47ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=44ms TTL=115
Reply from 64.78.193.84: bytes=32 time=73ms TTL=115
Reply from 64.78.193.84: bytes=32 time=46ms TTL=115
Which of the following utilities produced this output?
Answers
The output provided appears to be from the "ping" utility.
How is this so?Ping is a network diagnostic tool used to test the connectivity between two network devices,typically using the Internet Control Message Protocol (ICMP).
In this case, the output shows the successful replies received from the IP address 64.78.193.84,along with the response time and time-to-live (TTL) value.
Ping is commonly used to troubleshoot network connectivity issues and measureround-trip times to a specific destination.
Learn more about utilities at:
https://brainly.com/question/30049978
#SPJ1
A business that helps people find jobs for a fee
Answers
career coaches is a business that help people to find job for free
Features of online advertising
Answers
Answer:
Well impacts of online advertising
Explanation:
•More people are likely to see the advertisement.
•If the quality of advertisement is good, people will trust it more.
Question 2 Multiple Choice Worth 5 points)
(04.01 LC)
Computers take in and process certain kinds of information
O at the same rate as humans can
O in the same way humans can
much faster than humans can
O much more slowly than humans can

Answers
Answer:
Answer:much faster than Humans can
Answer:
c
Explanation:
System testing – During this stage, the software design is realized as a set of programs units. Unit testing involves verifying that each unit meets its specificatio
Answers
System testing is a crucial stage where the software design is implemented as a collection of program units.
What is Unit testing?Unit testing plays a vital role during this phase as it focuses on validating each unit's compliance with its specifications. Unit testing entails testing individual units or components of the software to ensure their functionality, reliability, and correctness.
It involves executing test cases, evaluating inputs and outputs, and verifying if the units perform as expected. By conducting unit testing, developers can identify and rectify any defects or issues within individual units before integrating them into the larger system, promoting overall software quality.
Read more about System testing here:
https://brainly.com/question/29511803
#SPJ1
are most often used to create web pages and web applications
Answers
Answer: HTML CSS AND JS
Explanation: These programming languages are best well known for building webs HTML is for the skeleton basically and the CSS is for styling the JS is for cool interactions.
acronym physical education
Answers
How is workflow defined? (IMAGE ATTACHED)

Answers
The sequence of steps one follows from start to finish of a work process is how workflow is defined. (Option C)
What is the rationale for the above response?Workflow refers to the sequence of steps or tasks that are performed in order to complete a particular work process, often in a specific order or with specific dependencies between steps.
A workflow can involve the interaction between hardware, software, and humans, but it is primarily defined by the steps that must be followed to achieve a specific outcome. In this sense, a workflow can be thought of as a structured or organized way of working, designed to optimize efficiency and productivity.
Learn more about workflow:
https://brainly.com/question/14399047
#SPJ1
4. SHORT ANSWERS:
i. Suppose tree T is a min heap of height 3.
- What is the largest number of nodes that T can have? _____________________
- What is the smallest number of nodes that T can have? ____________________
ii. The worst case complexity of deleting any arbitrary node element from heap is ___________
Answers
Answer:
i. A min heap of height 3 will have a root node with two children, each of which has two children of its own, resulting in a total of 7 nodes at the bottom level. Therefore:
The largest number of nodes that T can have is 1 + 2 + 4 + 7 = 14.
The smallest number of nodes that T can have is 1 + 2 + 4 = 7.
ii. The worst case complexity of deleting any arbitrary node element from a heap is O(log n), where n is the number of nodes in the heap. This is because deleting a node from a heap requires maintaining the heap property, which involves swapping the deleted node with its child nodes in order to ensure that the heap remains complete and that the heap property is satisfied. This process requires traversing the height of the tree, which has a worst-case complexity of O(log n).
Explanation:
Which IP QoS mechanism involves prioritizing traffic? Group of answer choices IntServ RSVP COPS DiffServ None of the above
Answers
Answer:
DiffServ
Explanation:
The IP QoS which is fully known as QUALITY OF SERVICE mechanism that involves prioritizing traffic is DIFFERENTIATED SERVICES (DiffServ).
DIFFERENTIATED SERVICES help to differentiate ,arrange ,manage, control and focus on network traffic that are of great significance or important first before network that are less important or by their order of importance in order to provide quality of service and to avoid network traffic congestion which may want to reduce the quality of service when their is to much load on the network .
Write a Python Program to find Prime Factors of a Number using For Loop, and While Loop
Answers
Answer:
1. Take the value of the integer and store in a variable.
2. Using a while loop, first obtain the factors of the number.
3. Using another while loop within the previous one, compute if the factors are prime or not.
4. Exit.
hope it helps☺
Please answer the question in the picture

Answers
The IP address of host 2 on subnet 6 would be the second address in the subnet, which is: 227.12.1.41
How to get the informationIt should be noted that to discover the IP address of Host 2 on Subnet 6, first we must uncover the network address of the sixth subnet. Since the number is 6, the network address bears the designation of the sixth subnet belonging to a Class C Network 227.12.1.0.
In order to ascertain the network adress of Subnet 6, one must become familiar with the block size. By examining the subnet mask /29, it can be deduced that the block size's magnitude must be equal to 2^(32-29)= 8. Summarily, the network address of Subnet 6 would correspond as:
227.12.1.0 + (6-1) * 8 = 227.12.1.40
Learn more about subnet on
https://brainly.com/question/28256854
#SPJ1
What is a countermeasure that could be implemented against phishing attacks?
Smart cards
Biometrics
Two-factor authentication
Anti-virus programs
Answers
Two-factor authentication:- Two-factor authentication (2FA) is an additional layer of security that requires a second method of authentication in addition to a password. It is also known as multi-factor authentication (MFA).Smart cards, biometrics, and one-time passwords (OTPs) are all examples of 2FA mechanisms that are frequently used.
Antivirus programs:- Antivirus programs can assist in preventing phishing attacks by preventing malicious code from running on a user's device.
Smart cards:- A smart card is a secure device that can be used to store sensitive data, such as a user's private key or a digital certificate.
Biometrics:- Biometric authentication is a security measure that uses physical and behavioral characteristics to verify a user's identity.
Two-factor authentication:- Two-factor authentication (2FA) is an additional layer of security that requires a second method of authentication in addition to a password. It is also known as multi-factor authentication (MFA).Smart cards, biometrics, and one-time passwords (OTPs) are all examples of 2FA mechanisms that are frequently used.2FA works by asking the user to verify their identity in two different ways, such as entering their password and a one-time code generated by an app or sent to their phone. This makes it much more difficult for attackers to obtain access, even if they have obtained a user's password.
Antivirus programs:- Antivirus programs can assist in preventing phishing attacks by preventing malicious code from running on a user's device. Antivirus software can detect malware and spyware that are frequently delivered in phishing emails, and it can prevent these malicious files from being downloaded and installed on a user's device.
Smart cards:- A smart card is a secure device that can be used to store sensitive data, such as a user's private key or a digital certificate. Smart cards can be used for authentication, encryption, and digital signature functions, making them a useful tool for preventing phishing attacks.
Biometrics:- Biometric authentication is a security measure that uses physical and behavioral characteristics to verify a user's identity. Biometrics can include fingerprint scanning, facial recognition, voice recognition, and other biometric technologies. Biometric authentication can be used in conjunction with passwords or smart cards to provide an additional layer of security against phishing attacks.
For more such questions on Antivirus, click on:
https://brainly.com/question/17209742
#SPJ8
Some commands listed in a menu cannot be selected.
True or False
Answers
Answer:
Explanation:
it is true
Which of the following represents the numeric value nine as a decimal number? ( 9 01001 ΟΝ Nine
Answers
Nine is represented as the digit "9" in numerical form. "01001" and "N Nine," the other values mentioned, do not correspond to the decimal value of nine.
What is output with a 0d start?Python output denotes a decimal integer by beginning with 0d.
What are some of the benefits of procedural programming over object-oriented programming, according to 6 points?A comparatively straightforward method for programming computers is procedural programming. This is why procedural programming languages are the starting point for many developers because they offer a coding base that the developer can use as they learn other languages, like an object-oriented language.
To know more about decimal visit:
https://brainly.com/question/28033049
#SPJ9
how does the internet bring people farther apart
use a paragraph to answer the question
Answers
Answer:
First of all you may not be able to see your friend in person and it gets very sad. Sometimes you call them but they don't answer you because they don't have enough time to talk or they have something else to do. They won't always want to be on the internet you know, they want to go outside and get a life and not be like the FRE-KIN T-I-K T-O-K-E-R-S WHO ARE CHILDREN AND BEING VERY STU-PID AND ARE TOTAL IDIOTS AND SAY STUFF THAT MAKE NO SENSE AND TRY TO GET ATTENTION. OH DON'T BRING TOWARDS THE GA-CHA IT SO TRASH. I still hate gacha :) and I am happy. Another thing is what some people post, you see you meet friends in real life and sometimes you get to know them but you don't know what they might be doing on the internet and another thing is that they post stuff that makes you feel uncomfortable and disgusted.
what is a bit?
what is 6mpbs?
Answers
A bit, short for "binary digit," is the smallest unit of information used in computing and digital communications. It can represent either a 0 or a 1, and it's used to measure digital data, such as the amount of storage capacity in a computer or the speed of a network connection.
What is Mbps?Mbps stands for "megabits per second," and it's a measure of data transfer rate or internet speed. 6 Mbps means that data can be transferred at a rate of 6 million bits per second. This measurement is commonly used for internet connections, as it indicates how quickly data can be downloaded or uploaded. A higher Mbps means a faster internet speed, which can result in faster downloads, smoother video streaming, and better online gaming experiences.
When it comes to internet connections, Mbps is an important factor in determining the quality of the connection. For example, a higher Mbps is generally better for activities like streaming high-definition video or online gaming, as it means that data can be transmitted more quickly and with less lag.
However, it's important to note that Mbps is just one factor in determining internet speed and quality. Other factors like network latency, signal strength, and congestion can also affect internet performance.
To learn more about binary digit, visit:
https://brainly.com/question/28060935
#SPJ1
You just purchased a single license for the latest Microsoft Office Suite. Your friend has asked to borrow the CD, so he can install it on his computer, too.
Is it okay for him to install it?
No; acts of piracy are legal; however, I paid for it. If he wants it, he can pay for it, too.
No; this would be considered piracy, so he should buy his own license.
Yes; I purchased the single license, so I can install it on as many computers as I want.
Yes; this would only be considered piracy if my friend paid me to install it on his computer too.
Answers
Answer:
B
Explanation:
No, this would be piracy. If he would want to install it, he would have to buy it himself.
Hope this helps :D
Based on The given information, No; this would be considered piracy, so he should buy his own license. Thus the correct option is B.
What is the license?A license is referred to as access rights or permission granted to an individual to operate any activity. This license acts as an approval method. For example, the approval license for driving is a driving license that allows individuals to drive vehicles.
Piracy is the act of producing more duplicates of a piece of software than the license allows for, either for individual use or business purposes, and using those copies for illegal purposes. In the given case, it is explained that
In the given case, it is explained that you recently bought a single license for the most recent version of the Microsoft Office Suite. To install the CD on his computer as well, your friend has asked to borrow it. He ought to get his own license since doing this would be piracy.
Therefore, option B is appropriate.
Learn more about Piracy, here:
https://brainly.com/question/870393
#SPJ6
What is the default location for saving a template in Word
D Custom Templates
D Created Templates
D Created Office Templates
D Custom Office Templates
Answers
The default location for saving a template in Word is Custom Office Templates. The correct option is D.
What is a template?When used in the context of word processing software, the term template refers to a sample document that already has some details in place.
These can be done by hand or through an automated iterative process, such as with a software assistant.
Templates are pre-formatted documents that are designed to speed up the creation of common document types such as letters, fax forms, and envelopes.
The default location for new templates is a subfolder named "Custom Office Templates" in the user's documents folder.
Thus, the correct option is D.
For more details regarding template, visit:
https://brainly.com/question/13566912
#SPJ1
Answer:
the correct option is D
Explanation:
• Describe the core components and terminology of Group Policy.
Answers
The core components and terminology of the group policy are directory services and file sharing.
What is the group policy component?A GPO is a virtual object that stores policy-setting information and consists of two parts: GPO's and their attributes are saved in a directory service, such as Active Directory.
It essentially provides a centralized location for administrators to manage and configure the settings of operating systems, applications, and users.
File share: GPO's can also save policy settings to a local or remote file share, such as the Group Policy file share.
Therefore, the group policy's main components and terminology are directory services and file sharing.
To learn more about the group policy component, visit here:
https://brainly.com/question/14275197
#SPJ1
Malcolm Movers charges a base rate of $200 per move plus $150 per hour and $2 per mile. Write a program named MoveEstimator that prompts a user for and accepts estimates for the number of hours for a job and the number of miles involved in the move and displays the total moving fee. For example, if 25 hours and 55 miles are input the output would be displayed as: For a move taking 25 hours and going 55 miles the estimate is $4,060.00
Answers
Answer:
import java.util.Scanner;
public class MoveEstimator
{
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
final int BASE_RATE = 200, RATE_PER_HOUR = 150, RATE_PER_MILE = 2;
int hours, miles;
double totalFee = 0.0;
System.out.print("Enter the number of hours for a job: ");
hours = input.nextInt();
System.out.print("Enter the number of miles: ");
miles = input.nextInt();
totalFee = BASE_RATE + (hours * RATE_PER_HOUR) + (miles * RATE_PER_MILE);
System.out.printf("For a move taking %d hours and going %d miles the estimate is $%.2f", hours, miles, totalFee);
}
}
Explanation:
*The code is in Java.
Create the Scanner object to be able to get input
Initialize the constant values using final keyword, BASE_RATE, RATE_PER_HOUR, RATE_PER_MILE
Declare the variables, hours, miles, totalFee
Ask the user to enter the hours and miles
Calculate the totalFee, add BASE_RATE, multiplication of hours and RATE_PER_HOUR, multiplication of miles and RATE_PER_MILE
Print the output as in required format
The program named MoveEstimator that prompts a user for and accepts estimates for the number of hours for a job and the number of miles involved in the move and displays the total moving fee is as follows:
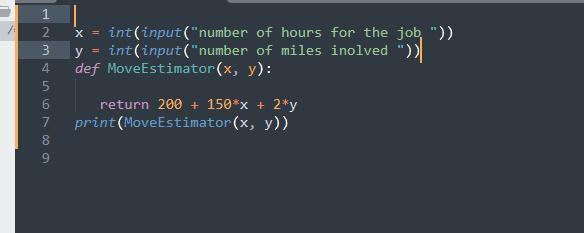
x = int(input("number of hours for the job "))
y = int(input("number of miles involved "))
def MoveEstimator(x, y):
return 200 + 150*x + 2*y
print(MoveEstimator(x, y))
Code explanation:The first line of code used the variable, x to store the input of the hours for the jobThe second line of code is used to store the input of the number of miles travelled. Then, we define a function that accept the users inputs(argument) as variable x and y. Then return the mathematical operation to find the total moving fee.Finally, we call the function with a print statement.learn more on python code here: https://brainly.com/question/22841107

The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least 65 percent transfer efficiency.
What is the transfer efficiency
EPA lacks transfer efficiency requirement for auto refinishing spray guns. The EPA regulates auto refinishing emissions and impact with rules. NESHAP regulates paint stripping and coating operations for air pollutants.
This rule limits VOCs and HAPs emissions in automotive refinishing. When it comes to reducing overspray and minimizing wasted paint or coating material, transfer efficiency is crucial. "More efficiency, less waste with higher transfer rate."
Learn more about transfer efficiency from
https://brainly.com/question/29355652
#SPJ1
What techniques overcome resistance and improve the credibility of a product? Check all that apply.
Including performance tests, polls, or awards
Listing names of satisfied users
Sending unwanted merchandise
Using a celebrity name without authorization
Answers
Answer: Including performance tests, polls, or awards.
Listing names of satisfied users
Explanation:
For every business, it is important to build ones credibility as this is vital on keeping ones customers and clients. A credible organization is trusted and respected.
The techniques that can be used to overcome resistance and improve the credibility of a product include having performance tests, polls, or awards and also listing the names of satisfied users.
Sending unwanted merchandise and also using a celebrity name without authorization is bad for one's business as it will have a negative effect on the business credibility.
The total number of AC cycles completed in one second is the current’s A.timing B.phase
C.frequency
D. Alterations
Answers
The total number of AC cycles completed in one second is referred to as the current's frequency. Therefore, the correct answer is frequency. (option c)
Define AC current: Explain that AC (alternating current) is a type of electrical current in which the direction of the electric charge periodically changes, oscillating back and forth.
Understand cycles: Describe that a cycle represents one complete oscillation of the AC waveform, starting from zero, reaching a positive peak, returning to zero, and then reaching a negative peak.
Introduce frequency: Define frequency as the measurement of how often a cycle is completed in a given time period, specifically, the number of cycles completed in one second.
Unit of measurement: Explain that the unit of measurement for frequency is hertz (Hz), named after Heinrich Hertz, a German physicist. One hertz represents one cycle per second.
Relate frequency to AC current: Clarify that the total number of AC cycles completed in one second is directly related to the frequency of the AC current.
Importance of frequency: Discuss the significance of frequency in electrical engineering and power systems. Mention that it affects the behavior of electrical devices, the design of power transmission systems, and the synchronization of different AC sources.
Frequency measurement: Explain that specialized instruments like frequency meters or digital multimeters with frequency measurement capabilities are used to accurately measure the frequency of an AC current.
Emphasize the correct answer: Reiterate that the current's frequency represents the total number of AC cycles completed in one second and is the appropriate choice from the given options.
By understanding the relationship between AC cycles and frequency, we can recognize that the total number of AC cycles completed in one second is referred to as the current's frequency. This knowledge is crucial for various aspects of electrical engineering and power systems. Therefore, the correct answer is frequency. (option c)
For more such questions on AC cycles, click on:
https://brainly.com/question/15850980
#SPJ8
Benjamin's company has asked him to start migrating the company's office productivity suite and e-mail to a cloud-based solution. He knows this means that users need to be able to log into the cloud platform, but doesn't want them to have to use a separate account to do so. Which of the following could he configure to meet that goal?
Answers
please help me with this coding assignment :)
What values are stored in nums after the following code segment has been executed?
int[] nums = {50, 100, 150, 200, 250};
for (int n : nums)
{
n = n / nums[0];
}
[1, 2, 3, 4, 5]
[1, 1, 1, 1, 1]
[1, 100, 150, 200, 250]
[50, 100, 150, 200, 250]
Answers
Answer:
D. [50, 100, 150, 200, 250]
Explanation:
This is a trick question because the integer n is only a counter and does not affect the array nums. To change the actual array it would have to say...nums[n] = n/nums[0];
The agency that started ARPANET was looking for
technologies that could be used by
O the military
O farmers
O transportation.
O electronics
Answers
Answer:the military
d
Answer:
A
Explanation:
match the following Microsoft Windows 7
Answers
Answer:
Explanation: will be still function but Microsoft will no longer provide the following: Technical support for any issues
((Excel)) please help, 100 points, and brain crown thingy, not only that, i will make several of these so you can get several hundred points just for one question if you find them all, that being said... please help me...
just please..
Answers
Answer:
First you read the question and numbers, then you use the numbers in the correct way and you try reallllyyy hard, you will find your answer! Hope this helps! :D
How to use this program
Answers
Answer:
there is no problem
Explanation:
but i hope i can help one day