Answers
Answer:
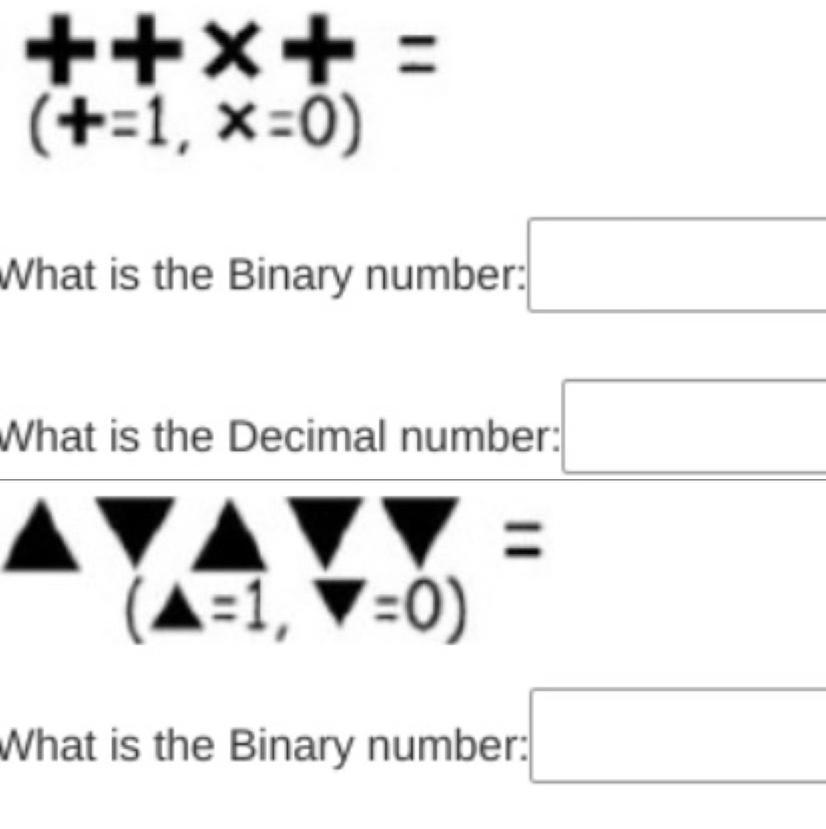
the binary for the first one is 1101
and the binary for the second one is 10100
Explanation:
Related Questions
Select the education and qualifications that are most helpful for Insurance Services careers. Check all that apply.
leadership skills
critical thinking skills
knowledge of credit systems
research skills
O certification and licensure
bachelor's and master's degrees
Answers
Answer:
critical thinking skills
research skills
certification and licensure
bachelor's and master's degree
Explanation: edge 2020
The education and qualifications that are most helpful for Insurance Services careers are as follows;
Critical thinking skills.Research skills.Certification and license.Bachelor's and master's degrees.Thus, the correct options for this question are B, D, E, and F.
What is the significance of Insurance Services careers?The significance of Insurance Services careers is understood by the fact that it is one of the most lucrative sectors in the entire world. The demand for this sector is rapidly growing. It provides various opportunities in specific countries along with global levels like World Monetary funds, world banks, etc.
It is required for all sectors to have particular criteria and eligibility. So, if you are interested to make your career in Insurance Services you definitely have bachelor's and master's degrees along with certain certifications and licensure.
Therefore, the correct options for this question are B, D, E, and F.
To learn more about Insurance services, refer to the link:
https://brainly.com/question/25855858
#SPJ5
One part of a development team has completed an algorithm. Why is it important to share it with others on the team? Choose all that apply. If it is easy to understand, no one will dispute what is included in the algorithm. It will give everyone else an opportunity to comment on the process described in the algorithm. It will serve as the starting point for all future activity. It communicates the consecutive instructions of the solution.
Answers
Answer: B,C,D
Explanation:
Answer:
the answer is B,C,D
Explanation:
A local variable and a global variable may not have the same name within a program. Group of answer choices True False
Answers
True. A local variable and a global variable cannot have the same name within a program.
Explanation:
- Local variables are defined within a specific block or function and can only be accessed within that block or function. They have a limited scope and exist only for the duration of that block or function.
- Global variables, on the other hand, are defined outside of any specific block or function and can be accessed by any part of the program. They have a global scope and exist throughout the entire program.
Since local and global variables have different scopes, they are considered as separate entities within a program. Therefore, they cannot share the same name. Using the same name for both a local and a global variable would create a naming conflict and can lead to errors or unexpected behavior in the program.
To know more about variable visit:
https://brainly.com/question/15078630
#SPJ11
Create a paper of at least 1,800 words describing the situation you selected and explaining the logic that would support an array.
Answers
Answer:
I dont know about 1800 words but I sure can tell you abit about array
Explanation: Array in simple sense refers to a collection of similar data. It holds data which is homogeneous in nature, meaning they are all alike. The use of array provide a lot of advantages in the fields of computer programming. When you declare a variable for an array, you can store as much data as you wish in the same variable without having to declare many variables. A 2X2 dimensional array can also be used in programming which represents matrices as well. The search process in an array too is really convenient and time saving. Also in an array, accessing an element is very easy by using the index number.
10 identical copies of a movie will be stored on 40 computers such that each computer has at most 1 copy. how many different ways can the 10 copies be stored? group of answer choices
Answers
10 identical copies of a movie will be stored on 40 computers such that each computer has at most 1 copy that will be (40 10).
An unofficial replication or imitation. a collection of genetically identical cells or creatures produced through some form of asexual reproduction from a single cell or individual.
Twins that are identical to one another but different from their parents share the same DNA. But a clone only has one parent and shares that parent's DNA perfectly.
Making numerous, exact copies of a specific segment of DNA is known as DNA cloning. The gene or other DNA fragment of interest (perhaps a gene for a therapeutically significant human protein) is first put into a circular piece of DNA called a plasmid in a DNA cloning method.
Learn more about identical copies:
https://brainly.com/question/13411887
#SPJ4
What is an example of an action that takes advantage of cloud computing?
Answers
The cloud gives you total access to and control over your data. Choosing which users have access to what data and at what level is a simple process.
What is the importance of cloud computing?The ability to scale, preserve flexibility, and concentrate resources on business operations rather than managing complicated IT infrastructure are the key benefits of cloud computing for businesses.
Therefore, working with a cloud partner is one of the greatest methods to maximize cloud computing for your company.
Resources are instantly accessible with cloud computing, allowing businesses to react to new market developments much more quickly.
Learn more about cloud computing here:
https://brainly.com/question/24212284
#SPJ1
a school principal trying to find out if parents will help buy new playground equipment shows digital leadership by.
A. asking the school board to ask parents
B. Creating a email survey for parents
C. Ordering the equipment and asking parents to contribute
D. Setting up a web conference for a small group of parents
Answers
Answer:
D. is the correct answer!
Answer:
B. Creating a email survey for parents
Explanation:
I did this on edg
write a program that will ask a user to enter a number between 1 and 10,000 and then report whether the number is prime.
Answers
To check if an integer n is prime, a rather straightforward approach is to verify if it is evenly divided by any integer from 2 to rootn. If none of them do, it is a prime; when you discover one that does, raise n.
What five prime numbers come to mind?A whole number greater than 1 with only the number 1 and itself as factors is known as a prime number. A complete number that divides into another number equally is referred to as a factor. These are the first few prime numbers: 2, 3, 5, 7, 11, 13, 17, 19, 23, and 29.
What kind of program is this example of?Users can generate and write documents using Microsoft Word, a word processing tool.
To know more about integer visit :-
https://brainly.com/question/15276410
#SPJ4
Hope wants to add a third use at the end of her nitrogen list.
What should Hope do first?
What is Hope’s next step?
Answers
Answer:the first answer is put it at the end of 2b
the second answer is press enter
Explanation:
Answer:
1, put it at the end of 2b 2, press enter key
Explanation:
Introduction
In this unit, you learned about careers related to web technology. You also learned about common skills required for any professional in this field. In this activity, you will interview a professional from the web technology sector. __________________________________________________________________________
Directions and Analysis
Task: Careers in Web Design
You have learned about different careers in web technology. Now, interview any professional from the field of web technology and obtain information on aspects like career opportunities, required experience, responsibilities, technical skills, and soft skills. Prepare a questionnaire with questions you wish to ask and leave enough space to note down the professional’s responses. Once you are done, briefly describe the information you gathered from the interview.
Type your response here:
Answers
The Careers in Web Design are:
Applications developer.Game developer.Multimedia programmer.Multimedia specialist.SEO specialist.UX designer.UX researcher.The career that the interview will be given on is Game developer.
What are likely questions to ask Game developer?The likely questions to ask Game developer are:
What game are you very proud of creating and why? What systems type do you use to make game ideas as well as the story characters? How do you put together and plan your project work? What are the most difficult things about video game design?The response are:
The game that I am very proud of creating is Uniz6 and it is special because it uses life events in its storyline.The system type is Cerberus X. because it is Light as well as Intuitive.I carefully planned it and them after putting the resources together, i began working on it.The most difficult things about video game design is most times is usable doors as well as when one Underestimate things that are important.Therefore, The Careers in Web Design are:
Applications developer.Game developer.Multimedia programmer.Multimedia specialist.SEO specialist.UX designer.UX researcher.Learn more about Game developer from
https://brainly.com/question/15855357
#SPJ1
what is the most popular game design engine today
Answers
Unreal Engine and Unity
Answer:
i think its an gamemaker
Explanation:
You receive a worksheet in which the rows are numbered 1, 2, 3, 5,6. This means that row 4 is _____.
Answers
People often hide cells of worksheet due to different reasons. This means that row 4 is hidden.
A worksheet is commonly know as a sheet of paper/computer sheet with which work is done or performed.
An individual can hide any worksheet so that it can be removed from their view. The data in hidden worksheets is not visible to the person, but it can still be referenced from other worksheets and workbooks. One can unhide hidden worksheets if need be.
Learn more from
https://brainly.com/question/17106092
Different types of computer and state the major difference between them
Answers
Desktop computers are typically larger, stationary computers that sit on a desk or table, while laptops are smaller, portable computers that can be carried around.
What is the computers?Servers are powerful computers designed to handle network resources and provide services to other computers, while workstations are high-performance computers used for specialized tasks such as graphic design or video editing.
Gaming computers are optimized for gaming performance with high-end hardware, while business computers are designed for productivity and typically come with business-oriented features such as security and manageability.All-in-one computers combine the monitor and computer components into a single unit, while traditional desktop computers have separate monitors and system units.Tablets are portable touchscreen devices that are smaller and more lightweight than laptops, and they are typically used for browsing, media consumption, and casual computing tasks.Embedded systems are specialized computers integrated into other devices, such as appliances, cars, and industrial equipment, and they are designed for specific tasks and functions.Lastly, Wearable computers are small, portable devices that can be worn on the body, such as smartwatches or fitness trackers, and they are designed for monitoring health, fitness, or other specialized functions.
Read more about computer here:
https://brainly.com/question/24540334
#SPJ1
Usually a ________ in Java code indicates the end of a data structure. Group of answer choices backslash character forward slash character null reference null pointer
Answers
Answer:
null reference.
Explanation:
assuming that nothing else changes, which one of the following is a correct statement concerning the relationship between the variables in present value and future value?
Answers
The relationship between present value (PV) and future value (FV) can be described by the following statement: As the present value increases, the future value also increases.
The present value represents the current worth or value of an asset or investment, while the future value represents the value of that asset or investment at a specified future date, taking into account factors such as interest or growth. When the present value increases, it means that more funds are being allocated or invested upfront, which allows for potential growth or returns over time. Consequently, this higher initial value contributes to a higher future value, reflecting the compounded effect of interest or growth over the given time period.
To know more about compounded effect, visit,
https://brainly.com/question/30364118
#SBJ11
when tejay started his new job, he found the step-by-step process for logging into the company server set forth in a laminated document by computer. what type of information is represented by this document?
Answers
This document represents a procedural guide, A Standard Operating Procedure (SOP), which outlines the steps needed to successfully log into the company server. It serves as a reference for employees and helps them understand the steps to complete the task.
When Tejay started his new job, he found the step-by-step process for logging into the company server set forth in a laminated document by computer. This document represents a Standard Operating Procedure (SOP).
A Standard Operating Procedure (SOP) is a comprehensive and step-by-step set of written instructions designed to serve as a guide for employees on how to perform routine or complex procedures or practices effectively and safely.
In any organization or business, Standard Operating Procedures (SOPs) are essential for consistent quality, efficient execution, and to meet regulatory requirements. They offer a step-by-step guide to facilitate consistency, reduce variability, and enhance productivity in various business operations.
For more such questions on Standard Operating Procedure (SOP) , Visit:
https://brainly.com/question/13530380
#SPJ11
3.23.1: Conditional expression: Print negative or non-negative.Create a conditional expression that evaluates to string "negative" if user_valis less than 0, and "non-negative" otherwise.Sample output with input: -9
Answers
With an input of -9, the output will be: negative
Create a conditional expression that evaluates to the string "negative"?
To create a conditional expression that evaluates to the string "negative" if user_val is less than 0 and "non-negative" otherwise, you can use the following
Obtain the user input value as user_val.
Use a conditional expression to evaluate the result.
Print the result based on the evaluation.
Here's the step-by-step code:
user_val = int(input("Enter a number: "))
result = "negative" if user_val < 0 else "non-negative"
print("Your answer:", result)
With an input of -9, the output will be:
negative
Learn more about conditional expression.
brainly.com/question/24172149
#SPJ11
To figure out how to use her MacBook Pro graphics software to update designs originally created on a DEC10, Marianne needs to use a ______ language?
Answers
Answer:
Glue Language
Explanation:
I'm not 100% sure, but here is the definition.
Glue language- A programming language that can be used to provide interoperability between systems not originally intended to work together
programmers often use a powerful programming paradigm that consists of three key features — classes, inheritance, and abstract classes. what is the paradigm called?
Answers
Programmers often use a powerful programming paradigm that consists of three key features — classes, inheritance, and abstract classes. The paradigm is called object-oriented programming.
Object-oriented programming is the most popular programming paradigm because of its powerful features, A class is a blueprint for creating objects that have their own properties and methods. Inheritance enables programmers to create new classes based on existing classes. An abstract class serves as a base class for other classes and can't be instantiated.Object-oriented programming has become popular because of its many advantages. It makes the code more organized, easier to maintain and read, and also makes it reusable. By creating classes, the code can be compartmentalized into logical sections. Then, each section can be managed as its own entity, which makes the code more manageable in large programs.
object-oriented programming is a programming paradigm that consists of classes, inheritance, and abstract classes. The programming paradigm has powerful features that make it more organized, easier to maintain, and reusable. By creating classes, the code can be compartmentalized into logical sections. This makes it easier to manage the code, especially in large programs.
To know more about paradigm visit:
brainly.com/question/7463505
#SPJ11
Applications and services can be assigned to a _____ in order to assign permissions to the application or service.
Answers
Applications and services can be assigned to a role in order to assign permissions to the application or service.
Check more about Computer Application below.
What are Computer Application?This is known to be a Software classification. An application program is a seen as computer program set up to do a specific task in a system.
A software are system packages that are often made by people to address some particular issues in regards to computing.
Hence, Applications and services can be assigned to a role in order to assign permissions to the application or service and this is what hey work as.
Learn more about Applications from
https://brainly.com/question/24264599
#SPJ1
Congratulationsill You have just been hired on as a Network Specialist by MW5G Network Consulting. The police have asked for the wireless support staff for Melille's Coffee Cale to meet with them; you are sent on behalf of MWSG as their representative. Apparently three customers of Melville's coffee Gafe have had their identity stolen and it seems they were all at the colfee shop during the first week of November of this year, and they were all using their laptops. The police suspect someone at the cafe was somehow snooping on the customer's computers. They hwe a suspect from the video survellance camera, but they want to know how the bad gay did it. 1. You take a look at the router at Metvite's Coffee Cafe: it's using Channel 1, has an SS1D of MELVILIFSCAFE, and the WEP security key is 17 characters long ["AhoyYetandlubbers") Do you Mee any issues here? does x −1 have ony gseriol charotius. [wrak passue 2. What do you think the method of attack was? - mion in the ridelle. 3. Explain how the bad guy did it. - Attaetur just bijak the wite. 4. The police are confused - why wouldn't the custemers have been aware of the attack? - Pecause we disn't trel mon in the middle a thaw no delay. 5. What steps will you take to try to ensure the problem stops?
Answers
From the information provided, it appears that there are several issues with the router at Melville's Coffee Cafe. Firstly, it is using channel 1 which is a common channel and can cause interference with other devices in the area.
Additionally, the SSID (MELVILIFSCAFE) is easily guessable and the WEP security key is only 17 characters long which is not considered secure. This makes it relatively easy for an attacker to gain access to the network.
What is Network Specialist?Based on the information provided, it is likely that the method of attack was a "man-in-the-middle" attack. This type of attack involves intercepting and manipulating communication between two parties without either party being aware of the attack.
The bad guy likely used tools such as a wireless sniffer to gain access to the network and intercept the communication between the customers' laptops and the router. They may have also used techniques such as ARP spoofing to redirect the traffic to a device under their control, allowing them to intercept and read the data.
The customers may not have been aware of the attack because the man-in-the-middle attack likely did not cause any noticeable changes to their experience, such as delays or connectivity issues. Additionally, the attacker may have been able to hide their actions by encrypting the intercepted data.
To try to ensure that the problem stops, I would take several steps:
Change the SSID and WEP key to something more secureConfigure the router to use a different channel to avoid interferenceImplement a more secure encryption method such as WPA2Monitor the network for suspicious activity and take appropriate actionLearn more about Network Specialist from
https://brainly.com/question/29352369
#SPJ1
Lập trình đếm xem có bao nhiêu số chẵn , bao nhiêu số lẻ trong đoạn từ M đến N
Answers
if i have 10 processors, what fraction of a program must be parallelizable in order to get a speedup of 5?
Answers
Approximately 89% of the program must be parallelizable to achieve a speedup of 5 with 10 processors.
How to find the fraction of a programTo determine the fraction of a program that must be parallelizable to achieve a speedup of 5 with 10 processors, we can use Amdahl's Law.
Amdahl's Law is defined as:
Speedup = 1 / (1 - P + P/N)
where P is the parallelizable fraction of the program, N is the number of processors, and Speedup is the desired speedup factor.
In this case, the desired speedup is 5, and the number of processors is 10.
Plugging these values into the formula: 5 = 1 / (1 - P + P/10).
To solve for P, first multiply both sides by the denominator: 5(1 - P + P/10) = 1.
Next, simplify and solve for P: 5 - 5P + 0.5P = 1, 4 = 4.5P, P ≈ 0.89.
Learn more about processor at
https://brainly.com/question/31786355
#SPJ11
Genres are useful for many reaseons. What are some explanations you can think of for how genres can be useful to players, game designers, and game publishers? this if for a video game design class
Answers
Answer:
Genres are used in Readers as well as writers.
By using genre patterns in writers it has been accepted by readers for accomplishing their purposes.
Genres allow both writers and readers to establish a working relationship between each other.
Both writers and readers are required for gamers and game publishers.
So Genres are very useful to them.
Explanation:
what is storage unit in computer and five examples of storage units.
Answers
Answer:
the storage unit of a computer is known as the term which is used to indicate storage capacity.
Explanation:
Five units of storage units are:-
1) byte
2) kilobyte
3) megabyte
4) gigabyte
5) terabyte
Which of the following statements about meta tags is TRUE?
A.Meta tags are a way of filtering items online so that you only see the items that connect to your interests.
B.Meta tags are large amounts of data that websites collect from their users. C.Meta tags are snippets of text that describe the content of a page or object. D.All of the above are true
Answers
Answer:
I guess c no. is the answer
your client has hired you to troubleshoot a network error. on inspection, it can be seen that the client has a static ip address, subnet mask, and default gateway all configured correctly. you open a browser to check the connection, and you can't get to a web page. you open a powershell window, ping the gateway, and ping 's public dns server, and everything is working. but you still can't navigate to websites. what kind of problem are you most likely to be experiencing?
Answers
Answer: Incorrect DNS
Explanation:
you have just downloaded a game onto your laptop. when you are not using the device, it unexpectedly downloads new content. which of these is the most likely cause of the issue
Answers
Answer:
deceptive software installed with the game.
Explanation:
There is a feature that allows you to lock the document, to avoid others making changes. t/f
Answers
Answer:
true
Explanation:
i have the same class
Answer:true
Explanation:
I took the test and it was correct
when ranking websites on search engine results pages, which element of a website do search engines value the most?
Answers
The component of a website that search engines appreciate the most is its content. It should have the right structure, keywords, and content to be relevant, distinctive, and helpful to users.
The content quality and relevancy of a website are important factors in search engine rankings, which are determined by complicated algorithms. The likelihood of content ranking higher on search engine results pages increases with its originality, information, and engagement (SERPs). In order to determine the worth and relevancy of a website's content, search engines additionally consider elements such as keyword use, content organisation, and website design. High-quality content is crucial for SEO since search engines' main objective is to give users the most pertinent and helpful results.
learn more about website here:
https://brainly.com/question/19459381
#SPJ4