how do we make a acount
Answers
Answer:
put your details in and chose your username and password and your account is made
Explanation:
Related Questions
Who plays Among Us?
who answered first will get a Surprise! :)
Answers
Answer:
mE now whats the surprise? :P
Explanation:
you work at a computer repair store. you are in the process of building a new computer system. the customer wants a motherboard with the following features: 16x pci express slot for video card support m.2 storage support support for 64-bit processors dual-channel memory support support for up to 64 gb of memory in this lab, your task is to: select and install the motherboard that meets the scenario requirements. connect the following computer case cables: power switch power led 3-1 pin hdd led speaker fan front fan rear usb (black cable- 2.0) front panel audio usb 3.0 connect the following connectors from the power supply: cpu power main motherboard power
Answers
A motherboard featuring a dual-core, 64-bit processor, 8 GB of dual-channel RAM, a 16x PCI Express slot for a video card, and support for firewire.
Choose the motherboard, then install it as follows:
Expand Motherboards in the Shelf.
-Click Details for a motherboard.
The Specifications tab should be chosen.
-To find the features that are supported, consult the motherboard documentation.
To determine the features for each motherboard, repeat steps 2-4.
-Once you've located a motherboard that satisfies the scenario's requirements, click Motherboard in the computer's top-right corner to move to the motherboard view.
From the shelf, move the motherboard with Socket 1151 to the motherboard plate inside the computer case.
Connect the connectors on the system casing as shown:
-Click Details next to Selected Components for the motherboard.
The Specifications tab should be chosen.
Learn more about motherboard:
https://brainly.com/question/15058737
#SPJ4
What is the name of an app that filters away internet connections from advertisers and trackers on your smartphone?
Answers
The app is called Disconnect Mobile. It is available for both Android and iOS devices.
The Benefits of Using Disconnect Mobile:An Essential Tool to Protect Your Privacy OnlineNowadays, with the rise of the internet and the digital age, it is becoming increasingly important to protect our online privacy. Advertisers and trackers are constantly looking for ways to access our data and use it for their own benefit. Fortunately, there is a solution to this problem: the Disconnect Mobile app.
Disconnect Mobile is an app that filters away internet connections from advertisers and trackers on your smartphone. It is designed to give users the power to control their online privacy and protect their data from advertisers and trackers. Disconnect Mobile works by blocking and redirecting traffic from ads and trackers which allows users to browse the web without being tracked or targeted. This means that users can browse the web without worrying about their personal data or information being used without their consent.
Learn more about mobile app:
https://brainly.com/question/26052911
#SPJ4
What was the farthest distance your skimmer traveled?what are some adjustments that you might consider if you were to make a new skimmer
Answers
They begin by constructing a hull using the Skimmer Hull Pattern and the guidelines provided in Building the Skimmer Hull. They then follow the directions on Making a Sail Structure to construct a stand.
A skimmer is made by What function do the fins serve?It is kept straight while gliding by the fins. The bottom of the main body is then positioned on the side facing the front, with the air scoop's thinner diagonal side facing up.
How are air skimmers used?This method takes use of the propensity of organic waste to adsorb to air bubbles. In essence, a column of air bubbles reacts with aquarium water that contains organic material, causing the trash to cling to the foam and the foam to be collected.
To know more about Skimmer visit :-
https://brainly.com/question/9835238
#SPJ1
In every sprint, the working increment should be tested progressively from unit testing, to integration testing, and then user acceptance testing.
a) Yes, It is the Prescribed method.
b) No, the Test strategy is decided by Quality Assurance lead.
c) Not Necessary, While the team need to ensure that each increment is thoroughly tested, all increments work together and meets the definition of done, it is up to the team to find the best method to achieve this.
d) Incorrect, it should also include non functional testing.
Answers
Answer:c) Not Necessary, While the team need to ensure that each increment is thoroughly tested, all increments work together and meets the definition of done, it is up to the team to find the best method to achieve this.
The Agile methodology values individuals and interactions over processes and tools. It encourages self-organizing and cross-functional teams to work together and find the best approach to deliver working software incrementally. While it is important to test each increment thoroughly, including non-functional testing, the specific testing strategy is not prescribed. The team can choose the best method to achieve their goals based on their context and needs.
A special space on a social media site in which users can post what they are
doing is called a:
OA. blog comment.
OB. RSS feed.
OC. status update.
OD. text message.
Answers
Answer: It's a status update
Explanation: because you're explaining what you're doing right now
PART 1: TRUE OR FALSE ITEMS
1. Computers in Medicine Information technology plays an important role in medicine
2. Most people use data and information interchangeably
3. Data processing: is the process of converting data into information
4. Accurate-information is error free
5. The ALU and the CU of a computer system are jointly known as the central processing unit.
6. ROM With every new application and software there is greater demand for memory capacity
7. Laser printers produce a very high quality output, are very quiet and very fast.
8. There are two major types of programming languages.
9. The symbolic programming of Assembly Language is easier to understand and save a lotof time and effort of the programmer.
10. The Vertical scrollbar is used to scroll up and down the page
Answers
Answer:
1. True
2. False
3. True
4. False
5. True
6. False
7. True
8. True
9. False
10. True
Explanation:
1. True - Computers and information technology play a crucial role in various aspects of medicine, including patient record management, diagnostic tools, medical imaging, research, and telemedicine.
2. False - Data and information are distinct concepts. Data refers to raw facts and figures, while information is processed and organized data that provides meaning and context.
3. True - Data processing involves transforming raw data into meaningful information through various operations such as organizing, analyzing, and summarizing.
4. False - Accurate information is free from errors or mistakes, but achieving complete accuracy is challenging, and there is always a possibility of errors.
5. True - The ALU (Arithmetic Logic Unit) and the CU (Control Unit) together form the central processing unit (CPU) of a computer system, responsible for executing instructions and performing calculations.
6. False - ROM (Read-Only Memory) is a non-volatile memory that stores permanent instructions and data. It does not change with new applications or software installations.
7. True - Laser printers are known for their high-quality output, quiet operation, and fast printing speed compared to other types of printers.
8. True - There are two major types of programming languages: high-level languages and low-level languages. High-level languages are more user-friendly and closer to human language, while low-level languages are closer to the computer's native language and require more technical knowledge.
9. False - Assembly language programming, although more low-level and closer to machine language, is considered more complex and time-consuming compared to higher-level symbolic programming languages.
10. True - The vertical scrollbar is typically used to scroll up and down a page or document, allowing users to view content that extends beyond the visible area of a window or screen.
Some one help pls will mark brainless !!!!!
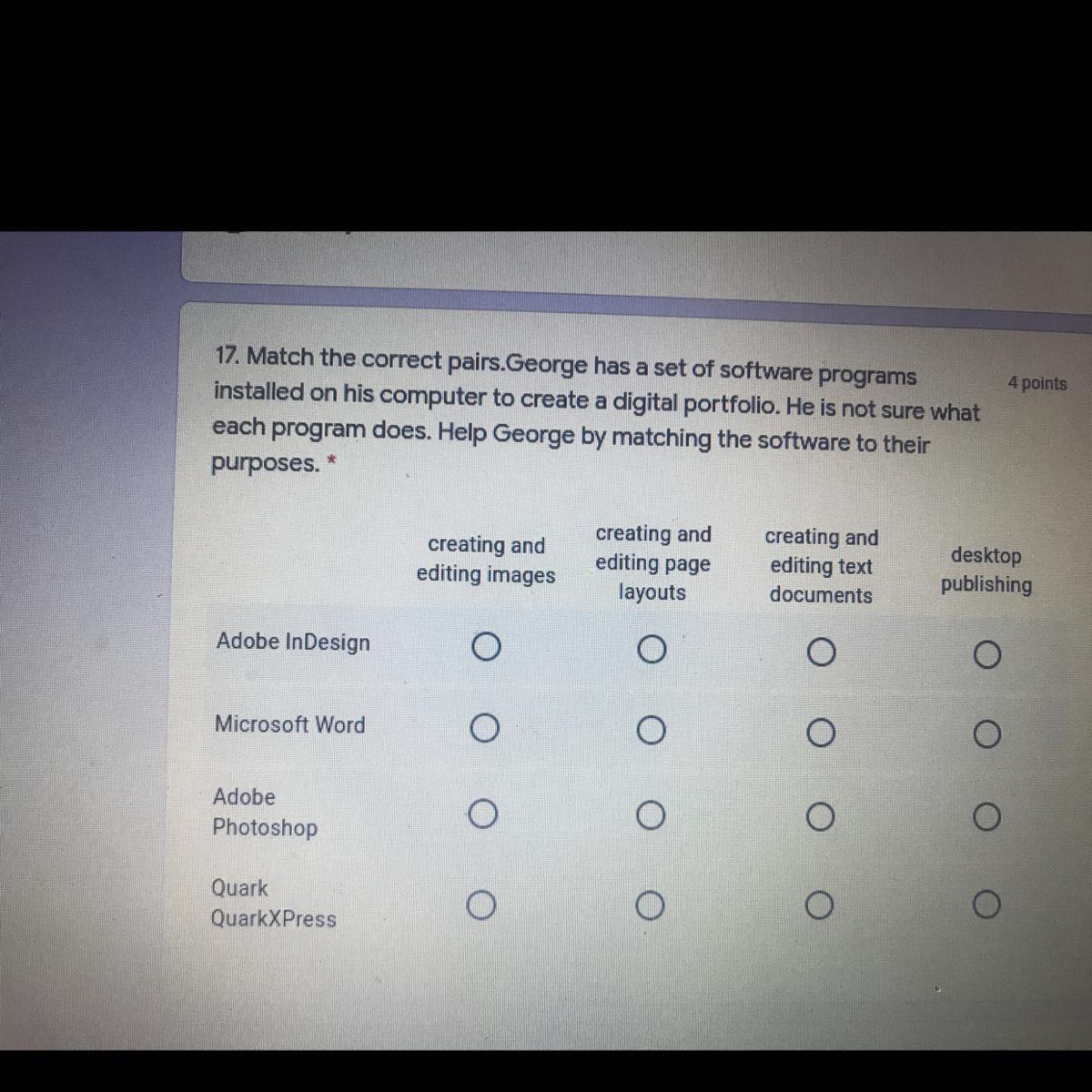
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
The normal time to perform a repetitive manual assembly task is 4.25 min. In addition, an irregular work element whose normal time is 1.75 min must be performed every 8 cycles. Two work units are produced each cycle. The PFD allowance factor is 16%. Determine (a) the standard time per piece, (b) how many work units are produced in an 8-hour shift at standard performance, and (c) the anticipated amount of time worked and the amount of time lost per 8-hour shift that corresponds to the PFD allowance factor of 16%.
Answers
The standard time per piece in a manual assembly task is 7.75 minutes, which includes a repetitive task time of 4.25 minutes and an irregular work element time of 3.5 minutes. In an 8-hour shift, at standard performance, 60 work units are produced considering a cycle time of 8 cycles and two units per cycle. The PFD allowance factor of 16% accounts for anticipated time lost due to personal needs, fatigue, and minor delays.
(a) Standard Time per Piece: Repetitive Task Time = 4.25 min.
Irregular Work Element Time = 1.75 min * 2 units (since two work units are produced each cycle) = 3.5 min.
Total Standard Time per Piece = Repetitive Task Time + Irregular Work Element Time.
= 4.25 min + 3.5 min.
= 7.75 min.
(b) Number of Work Units Produced in an 8-Hour Shift:
Cycle Time = 8 cycles (since the irregular work element is performed every 8 cycles).
Working Time = 8 hours = 8 * 60 minutes = 480 minutes.
Number of Work Units Produced = (Working Time) / (Cycle Time) * (Work Units per Cycle).
= 480 min / 8 cycles * 2 units.
= 60 units.
(c) Time Worked and Time Lost:
PFD (Performance Factor with Delay) allowance factor is 16%. This factor represents the anticipated amount of time lost due to personal needs, fatigue, and minor delays.
Time Worked = Working Time * (1 - PFD allowance factor).
= 480 min * (1 - 0.16).
= 480 min * 0.84.
= 403.2 min.
Time Lost = Working Time - Time Worked.
= 480 min - 403.2 min.
= 76.8 min.
Read more about Manual assembly tasks.
https://brainly.com/question/28605071
#SPJ11
What is the average amount of time that it will take a device to recover from a failure that is not a terminal failure
Answers
The average amount of time that it will take a device to recover from a failure that is not a terminal failure can vary depending on the severity and complexity of the issue.
In general, most devices are designed to have built-in mechanisms for self-recovery or automated repair processes that can help to minimize downtime. For simple failures such as a software glitch, recovery time can be a matter of minutes to a few hours. For more complex hardware failures, such as a component malfunction, recovery time may take longer and may require the assistance of a trained technician. In most cases, the recovery time for non-terminal failures should be relatively short as long as the issue is identified and addressed promptly.
Learn more about amount here:
https://brainly.com/question/13024617
#SPJ11
The average amount of time it takes for a device to recover from a non-terminal failure of system varies depending on the severity of the issue. It ultimately depends on the nature of the failure.
In some cases, it may only take a few minutes to fix, while in others it could take hours or even days. It ultimately depends on the nature of the failure and the resources available to address it.
The average recovery time for a device experiencing a non-terminal failure of system varies depending on the device and issue. Generally, it can take anywhere from a few minutes to several hours. Swift troubleshooting and maintenance can help minimize downtime and restore the device to normal functioning.
To learn more about non-terminal failure of system:
https://brainly.com/question/14103186
#SPJ11
Which yum commands in Linux do I use to answer the following questions?Which packages of the Printing client group are optional?Which security scanner software is available?Which package provides the Apache Web Services? (Hint: The Web protocol is HTTP.)
Answers
To answer the questions above, you will need to use the yum command in Linux. To determine which packages of the Printing client group are optional, you can use the command yum grouplist 'Printing Client' to view the packages and their status.
To find out which security scanner software is available, you can use the command yum list 'security-scanner*' to view the available packages. Finally, to determine which package provides the Apache Web Services, you can use the command yum search 'httpd', which will search for packages related to the web protocol HTTP.
Learn more about software
https://brainly.com/question/28224061
#SPJ11
B. State True or False: 1. 'Date within' option allows you to search an email within a specified date range.
Answers
Answer + Explanation:
his topic describes the email and document properties that you can search for in email items in Exchange Online and documents stored on SharePoint and OneDrive for Business sites by using the Content Search feature in the Security & Compliance Center. You can also use the *-Compliance Search cmdlets in Security & Compliance Center PowerShell to search for these properties
Please have a great day <3
what is meant by internet surveillance?....ONLY ANSWER IF YOU KNOW
Answers
Answer:
As a brief definition, Internet surveillance refers to your computer and online activity, online and offline data, and Internet traffic being monitored and logged by government agencies, ISPs, and – potentially – cybercriminals.
Explanation:
can I have brainliest
Answer: I LIKE EM BIG AND JUCIY
Explanation:
¿Cuanto cuesta un procesador de textos?
Answers
Answer:
Too Much
demasiado
Explanation:
Differences of a desktop computer and a laptop
Answers
Answer:
Desktop can't move easily, not portable. Laptop very portable.
Explanation:
Compare the freedom available to the American media with the freedom available to media in other parts of the world. How does a country’s political scenario affect the freedom of media?
ASAP
Answers
in america we are free to say most of whatever we want in media becuase we have free speech here. in other countries, they don't have freedom of speech,and sometimes it also has to do with the political situation. like say in china, where teenagers arent allowed to use the internet for more than a certain amount of time,and arent allowed to talk to each other. thats becuase of the fact that that country is a communist country and the government wants much more control than in other countries.
How would i give someone a ¨brainliest¨
Answers
Answer:
by clicking on the crown
Explanation:
Answer:
just click on the crown that should be at the bottom right of their answer
Explanation:
Carmen wanted to clear up space on her computer and remove unwanted files. What would be the best for her to delete?
junk files
audio files
video games
anti-virus programs
Answers
Answer:
junk files
Explanation: if a file is in a junk file it is most likely unwanted
Answer:
A. junk files
Explanation:
I just took the test :)
what does imma go slide on sum sh mean
Answers
Answer:
Something inappropriate.
Explanation:
On a Saturday night, you should spend time turning in your homework.
A packet switch receives a packet and determines the outbound link to which the packet should be forwarded. When the packet arrives, one other packet is halfway done being transmitted on this outbound link and six other packets are waiting to be transmitted. Packets are transmitted in order of arrival. Suppose all packets are 2,000 bytes and the link rate is 2 Mbps. Considering the queuing delay defined in the previous question, what is the queuing delay for the packet
Answers
The queuing delay for the packet in this case will be:
Queuing Delay = Transmission Time of the Halfway done packet + Transmission Time of the 6 waiting packets Note:
We have to find the transmission time of the Halfway done packet. This is because when a packet is halfway done being transmitted, we need to know how much time it will take to finish transmission of that packet.
So let's first find the transmission time of a packet of size 2,000 bytes.
We know that the link rate is 2 Mbps which means 2,000,000 bits per second. Transmission time of one packet = Packet size / Transmission rate= \(2000*8 / 2,000,000= 0.008\) seconds
Now, the transmission time of the halfway done packet is: 0.008/2 = 0.004 seconds (since it is halfway done)And the total transmission time of the 6 waiting packets is: \(6*0.008 = 0.048\)seconds
So, Queuing Delay = Transmission Time of the Halfway done packet + Transmission Time of the 6 waiting packets= 0.004 + 0.048= 0.052 seconds
the queuing delay for the packet is 0.052 seconds.
To know more about queuing delay visit:-
https://brainly.com/question/30643647
#SPJ11
30 POINTS
What is relative referencing?
a system of referring to cells using letters for columns and numbers for rows
a method of formatting text in spreadsheet cells so none of it is cut off
a formula for calculating the optimal width of columns and height of rows
a bulleted list of all of the information included in a spreadsheet
Answers
Answer:
A. A system of referring of cells using letters for columns and numbers for rows
Explanation:
Got it right on Egde 2020
Relative referencing is a system of referring to cells using letters for columns and numbers for rows. Thus, option A is correct.
What is cell?All living creatures and bodily tissues are made up of the smallest unit that can live on its own. A cell is the tiniest, most fundamental unit of life, responsible for all of life's operations.
Absolute cells, do not change regardless of where they are replicated. When a formula is transferred to some other cell, the cell size references change. In the field, they are diametrically opposed. As a result, the absolute cell referencing is constant and the relative cell referencing formula is copied to another cell.
Therefore, Relative referencing is a system of referring to cells using letters for columns and numbers for rows. Thus, option A is correct.
Learn more about on cell, here:
brainly.com/question/3142913
#SPJ3
You are performing computer forensics. you just transferred data from the victim's hard disk to a forensic system. what is the next step you should perform
Answers
On transferring data from the victim's hard disk, you should create a checksum file.
What exactly is a checksum and why is it used?IT professionals use checksums to detect high-level errors in data transmissions. A checksum is a value that represents the number of bits in a transmission message. Each piece of data or file can be assigned a checksum value prior to transmission by running a cryptographic hash function.
What is an example of a checksum?Example. Assume the sender wishes to send four frames of eight bits each, with the frames being 11001100, 10101010, 11110000, and 11000011. The bits are added by the sender using 1s complement arithmetic. If there is a carryover when adding two numbers using 1s complement arithmetic, it is added to the sum.
To know more about checksum files visit:
https://brainly.com/question/28454591
#SPJ4
Does any one know how to code? If you do can you help me with my project?
Answers
Answer:
kinda look it up!!!
Explanation:
go to code.org free coding
i can help you man
-scav aka toby
given the task of finding words that share a common prefix with a given word, which data structure would have the optimal expected asymptotic runtime performance?
Answers
The data structure that would have the optimal expected asymptotic runtime performance is a sorted array. The correct option is b.
What is data structure?An expertly designed format for arranging, processing, accessing, and storing data is called a data structure.
Data structures come in both simple and complex forms, all of which are made to organize data for a certain use. Users find it simple to access the data they need and use it appropriately thanks to data structures.
Therefore, the correct option is b. sorted array.
To learn more about data structure, refer to the link:
https://brainly.com/question/13439802
#SPJ1
The question is incomplete. Your most probably complete question is given below:
trie
sorted array
binary tree
hash set
what is the command to conditionally create a database called loudacre in case the database already exists?
Answers
The command to conditionally create a database called loudacre in case the database already exists is "CREATE DATABASE IF NOT EXISTS loudacre;"
To conditionally create a database called loudacre in case the database already exists, we can use the "CREATE DATABASE" command. The syntax is: CREATE DATABASE IF NOT EXISTS loudacre; The above command will create the database named loudacre only if it does not exist already. If the database already exists, then the command will not do anything. The "IF NOT EXISTS" clause is used to avoid any errors that might occur if the database is already present. The "CREATE DATABASE" command is used to create a new database in MySQL. It is followed by the name of the database that we want to create. The name of the database should follow the naming conventions of MySQL.
Learn more about command here:
https://brainly.com/question/13267411
#SPJ11
3 difference between single user operating system and multi user operating system
Answers
Answer:
Explanation:
A Single User Operating System is designed for use by only one person at a time. This type of OS is typically used on desktop or laptop computers and not typically used on servers. Single User Operating Systems are generally more user-friendly and easier to use than Multi User Operating Systems.
A Multi-User Operating system allows multiple users to access the same computer system at the same time. Multi User Operating Systems have many uses but are particularly popular in business and educational settings where multiple people need to access a single computer system.
What is the full form of WWW
Answers
Answer:
world wide web
Explanation:
hi hello world wide web
Answer:
WWW = world wide web
Explanation:
Hope it is helpful....
FILL IN THE BLANKS : The choice of control limits ensures that 99.7% of the sample points are expected to fall ________ the LCL and the UCL.
Answers
The choice of control limits ensures that 99.7% of the sample points are expected to fall between the LCL and the UCL.
The control limits in statistical process control (SPC) are used to monitor and assess the stability and variability of a process over time. The LCL (Lower Control Limit) and UCL (Upper Control Limit) define the range within which data points are expected to fall if the process is in control.
When it is stated that the choice of control limits ensures that 99.7% of the sample points are expected to fall between the LCL and UCL, it means that under normal conditions, the variation in the process will result in most data points falling within this range. This is based on the assumption of a normal distribution of data, where approximately 99.7% of the data falls within three standard deviations of the mean.
By setting the control limits at this level, any data points that fall outside this range are considered to be indicative of special causes of variation or non-random patterns in the process. These points are signals for further investigation to identify and address the underlying causes of the variation.
Learn more about Control limits: https://brainly.com/question/29512700
#SPJ11
Only about 10 percent of the world’s population uses the internet.
A.
True
B.
False
Answers
Because look on our own Brainly there are more than 1,000 people
MARK ME BRAINLEST
Coin Changing Problem.a) For an arbitrary denomination set {d1,d2,...,dk}, give an algorithm to optimally solve (using the fewest number of coins) the coin-changing problem studied in class. That is, give an algorithm to make up v value using the fewest number of coins. The Bellman equation for this problem is given on slide 40-41 of "06DynamicProgrammingI.pdf". (Note: the ci on the slide should be di.) Your algorithm should calculate the fewest number of coins to make up value v. Can you solve in space complexity θ(v)?(b) Give the algorithm to print out the set of coins in the optimal solution. For example, if the denomination is the US denomination and v = 19, you should print out {1, 1, 1, 1, 5, 10}.
Answers
The Coin Changing Problem involves finding the minimum number of coins required to make up a certain value, and the objective of the given algorithm is to optimally solve the problem using the fewest number of coins and in a space complexity of θ(v).
What is the Coin Changing Problem and what is the objective of the given algorithm?The given paragraph is about the Coin Changing Problem, where we need to find an algorithm to make up a value v using the fewest number of coins from a given arbitrary denomination set.
The Bellman equation for this problem is provided on slide 40-41 of "06DynamicProgrammingI.pdf".
The algorithm should calculate the fewest number of coins required to make up the given value v, and it should solve in space complexity θ(v).
Additionally, the paragraph also requires us to provide an algorithm to print out the set of coins in the optimal solution.
The overall goal is to optimize the coin-changing problem by finding the fewest number of coins required to make up a given value, using a given denomination set.
Learn more about Coin Changing Problem
brainly.com/question/29408899
#SPJ11