how to play powerpoint slides automatically without clicking 2021?
Answers
Answer:
Turn on autoplay it is at the bottom of the screen
Explanation: Press the 3 dots at the bottom of the screen. Then click autuplay.
Also set the amount of seconds.
Related Questions
A key component of the u. S. Government under the constitution is.
Answers
Answer:
a legislative, an executive, and a judicial branch
You have a Windows 10 computer at home.
You are concerned about privacy and security while surfing the web, so you decide to block cookies from banner ad companies. However, you still want your computer to accept cookies from legitimate sites, like your bank's website.
In this lab, your task in this lab is to configure the settings in Internet Explorer as follows:
Override automatic cookie handling with the following settings:Always allow first-party cookies.Always block third-party cookies.Accept session cookies.
Configure an exception to allow cookies from mybank.com.
Answers
To configure the settings in Internet Explorer on a Windows 10 computer to enhance privacy and security while surfing the web, you need to override automatic cookie handling and configure an exception for mybank.com.
In order to configure the settings in Internet Explorer on a Windows 10 computer follow these steps:
1. Open Internet Explorer on your Windows 10 computer.
2. Click the gear icon in the upper-right corner to open the settings menu, and then select "Internet options."
3. In the "Internet Options" dialog, click on the "Privacy" tab.
4. Click the "Advanced" button under the "Settings" section to override automatic cookie handling.
5. In the "Advanced Privacy Settings" dialog, check the box next to "Override automatic cookie handling."
6. Set the following options:
- For "First-party Cookies," select "Accept."
- For "Third-party Cookies," select "Block."
- Check the box next to "Always allow session cookies."
7. Click "OK" to save your settings in the "Advanced Privacy Settings" dialog.
8. Back in the "Privacy" tab of the "Internet Options" dialog, click on the "Sites" button.
9. In the "Per Site Privacy Actions" dialog, enter "mybank.com" in the "Address of website" field, and then click "Allow."
10. Click "OK" to close the "Per Site Privacy Actions" dialog.
11. Click "OK" again to close the "Internet Options" dialog and apply your settings.
Now, your Windows 10 computer is configured to always allow first-party cookies, always block third-party cookies, accept session cookies, and specifically allow cookies from mybank.com in Internet Explorer.
To learn more about Windows 10 visit : https://brainly.com/question/29892306
#SPJ11
A message is sent over a noisy channel. The message is a sequence x1,x2,…,xn of n bits (xi∈(0,1)). Since the channel is noisy, there is a chance that any bit might be corrupted, resulting in an error (a 0 becomes a 1 or vice versa). Assume that the error events are independent. Let p be the probability that an individual bit has an error (0
Answers
The probability of at least one error occurring in the message is 1 minus the probability of no errors, which is given by 1 - (1 - p)^n.
The probability that an individual bit is transmitted without error is (1 - p), where p is the probability of an error occurring for each bit. Since the error events are assumed to be independent, the probability of no errors occurring in all n bits is the product of the probabilities of each bit being transmitted without error:
P(no errors) = (1 - p) * (1 - p) * ... * (1 - p) (n times)
= (1 - p)^n
On the other hand, the probability of at least one error occurring in the n bits is equal to 1 minus the probability of no errors:
P(at least one error) = 1 - P(no errors)
= 1 - (1 - p)^n
To know more about probability
https://brainly.com/question/31828911
#SPJ11
Check the devices that are external peripheral devices:

Answers
Answer:
Mouse, and keyboard
Explanation:
Common Sense
Reggie is having trouble signing into his email account at work. He picks up the phone to call someone in IT, and then checks the phone list to see who to call. Which IT area should Reggie call
Answers
The IT area that Reggie should call is called; Information Security
What are the functions of an Information Technology Department?The IT department that Reggie should call is called Information Security department.
This is because Information security protects sensitive information from unauthorized activities such as inspection, modification, recording, and any disruption or destruction.
The aim of this department is to make sure that the safety and privacy of critical data such as customer account details, financial data or intellectual property are safe.
Read more about information technology at; https://brainly.com/question/25920220
identify all of the data dependencies in the following code. which dependencies are data hazardsthat will be resolved via forwarding? which dependencies are data hazards that will cause a stall? s1: add $3, $4, $6 s2: sub $5, $3, $2 s3: lw $7, 100($5) s4: add $8, $7, $2
Answers
Through line biomechanics concentration and observation magic if International Society of Biomechanics in sports.
What is "International Society of Biomechanics in sports"?The recently developed professional association in biomechanics is the "International Society of Biomechanics in sports".It is the professional association in bio-mechanics.
It is an international society which is dedicated to bio-mechanics to sports. The main purpose of the society is to understand and study the human movement and its relation to sport bio-mechanics. They provide information regarding bio-mechanics in sports.
Therefore, Through line biomechanics concentration and observation magic if International Society of Biomechanics in sports.
Learn more about biomechanics on:
https://brainly.com/question/13898117
#SPJ1
Three different numbers need to be placed in order from least to greatest. For example, if the numbers are ordered 9, 16, 4, they should be reordered as 4, 9, 16. Which of the following algorithms can be used to place any three numbers in the correct order?
If the first number is greater than the last number, swap them. Then, if the first number is greater than the middle number, swap them.
If the first number is greater than the last number, swap them. Then, if the first number is greater than the middle number, swap them.
A
If the first number is greater than the middle number, swap them. Then, if the middle number is greater than the last number, swap them.
If the first number is greater than the middle number, swap them. Then, if the middle number is greater than the last number, swap them.
B
If the first number is greater than the middle number, swap them. Then, if the middle number is greater than the last number, swap them. Then, if the first number is greater than the last number, swap them.
If the first number is greater than the middle number, swap them. Then, if the middle number is greater than the last number, swap them. Then, if the first number is greater than the last number, swap them.
C
If the first number is greater than the middle number, swap them. Then, if the middle number is greater than the last number, swap them. Then, if the first number is greater than the middle number, swap them.
Answers
Answer:A
Explanation:
While investigating a 4-year-old PC that is taking an unusually long time to boot, a technician discovers that the BIOS is rediscovering the hardware system at every boot. What should the technician do to resolve the problem
Answers
Answer:
learn and train it to make it boot faster
Explanation:
Well we know that the PC is old and it takes a long time to boot also the BIOS is rediscovering the hardware system at every boot so he should make it reboot and learn and train it to make it boot faster
what is
Force (N) = Mass (kg) x acceleration (m/s)
If a 80-kg swimmer pushes off a pool wall with a force of 225 N, at what rate with the swimmer
accelerate forward?
Answers
225/80=2.8125m/s
Which of marcia’s identity statuses are associated with higher self-esteem, security, and conscientiousness?.
Answers
The Marcia's identity statuses that are associated with higher self-esteem, security, and conscientiousness is Identity Achievement.
What was Marcia's Concept?Marcia thinks that our jobs and core beliefs make up our identity.
James Marcia is arguably the most well-known person to have investigated how identities are formed. Marcia made the decision to conduct a wide variety of interviews with people to learn more about how they formed their opinions and preferences. He thought that two factors primarily determine one's identity. The first is what he referred to as occupation, which is the primary position one holds in society.
Note that Identity exploration and the subsequent comprehension of that identity's significance in one's own life are two steps in the cognitive process known as "identity accomplishment."
Learn more about Marcia's identity statuses from
https://brainly.com/question/17485587
#SPJ1
What do you guys think of my wallpaper for my phone?

Answers
It's cool!
do you have any questions for your homeworks?
Apple Inc.: Prior to the company's 2017 move to Apple Park, on what street in Cupertino was Apple's headquarters located? It shares a name with a construct that mischievous young programmers may have learned by typing the following into the BASIC prompt on an Apple ][:
10 PRINT "BUTTS "
20 GOTO 10?
Answers
According to the question of programmers, apple's headquarters was located on Infinite Loop in Cupertino.
What is programmers?Programmers are professionals who write code to create software programs, applications, and websites. They use programming languages to instruct computers to perform specific tasks. Programmers analyze user needs and develop software solutions. They also design, test, and debug software, as well as perform maintenance and upgrades. Programmers use problem-solving and analytical skills to design and develop software that meets user needs. They must stay up-to-date on the latest technology and programming languages to create the most efficient and effective solutions. Programmers must also be able to understand customer requirements and develop a plan to meet those needs.
To learn more about programmers
https://brainly.com/question/30168154
#SPJ1
in an instant runoff election, what does the computerized voting machine do?
Answers
In an instant runoff election, the computerized voting machine automatically redistributes the votes of the candidate with the fewest first-place votes to the remaining candidates based on the voters' ranked preferences
This process is repeated until a candidate receives a majority of the votes. The computerized voting machine makes the process of vote redistribution instant and efficient, eliminating the need for multiple rounds of voting.
The process of eliminating the candidate with the fewest votes and redistributing their votes to the remaining candidates based on the voters' next preferences continues until one candidate receives a majority of the votes. The computerized voting machine would keep track of all the votes, the candidates' rankings, and the round-by-round eliminations and redistributions. It would then calculate the final results and declare the winner.
learn more about computerized voting machine here:https://brainly.com/question/29756985
#SPJ11
When trying to upload assignment on canvas wont let me click choose file.
Answers
What is an example of a composite key in a database table?
InvoiceID
CustomerID
ProductID
OrderID + ProductID
Answers
Answer:
b
Explanation:
OrderID + ProductID is an example of a composite key in a database table. The correct option is 4.
What is composite key?A composite key is a key in a database table that consists of two or more columns that uniquely identify each row.
In a database table, a composite key is the combination of OrderID and ProductID in a table that tracks sales transactions.
Because a single order can contain multiple products and multiple orders can contain the same product, neither column can uniquely identify a row by itself.
However, by combining the two columns, each row can be uniquely identified, ensuring that the data is accurate and complete.
Similarly, a combination of CustomerID and ProductID might be used in a sales system to track the products purchased by each customer.
Thus, the correct option is 4.
For more details regarding composite key, visit:
https://brainly.com/question/10167757
#SPJ3
which sales hub tool would you use to add products to a deal?
Answers
The sales hub tool you would use to add products to a deal is called the Products tool.
In HubSpot's Sales Hub, the "Products" tool is where you can add products to deals. This tool allows you to create a catalog of products and services that you offer, and associate them with specific deals. By adding products to a deal, you can easily track the products and services that are being sold as part of the deal.
This information is important for tracking sales performance and understanding which products are driving revenue. To add products to a deal, simply navigate to the "Products" tool within HubSpot's Sales Hub, select the product or products that you want to associate with the deal, and then save your changes. From there, you'll be able to view and manage the products associated with the deal directly from the deal record.
Learn more about tracking here:
https://brainly.com/question/32290034
#SPJ11
Who designs online portals for companies? A. illustrator B. video editor C. storyboard artist D. web designer
Answers
Have a good day
OkkKkkkkkEYEYYEYEYEY BYEYYEYEYEyeeyeyyeEYEy if you know you know
Answers
Answer:
okkkkkkkkkkeyyyyyyy
Explanation:
byeeeee
The normal time to perform a repetitive manual assembly task is 4.25 min. In addition, an irregular work element whose normal time is 1.75 min must be performed every 8 cycles. Two work units are produced each cycle. The PFD allowance factor is 16%. Determine (a) the standard time per piece, (b) how many work units are produced in an 8-hour shift at standard performance, and (c) the anticipated amount of time worked and the amount of time lost per 8-hour shift that corresponds to the PFD allowance factor of 16%.
Answers
The standard time per piece in a manual assembly task is 7.75 minutes, which includes a repetitive task time of 4.25 minutes and an irregular work element time of 3.5 minutes. In an 8-hour shift, at standard performance, 60 work units are produced considering a cycle time of 8 cycles and two units per cycle. The PFD allowance factor of 16% accounts for anticipated time lost due to personal needs, fatigue, and minor delays.
(a) Standard Time per Piece: Repetitive Task Time = 4.25 min.
Irregular Work Element Time = 1.75 min * 2 units (since two work units are produced each cycle) = 3.5 min.
Total Standard Time per Piece = Repetitive Task Time + Irregular Work Element Time.
= 4.25 min + 3.5 min.
= 7.75 min.
(b) Number of Work Units Produced in an 8-Hour Shift:
Cycle Time = 8 cycles (since the irregular work element is performed every 8 cycles).
Working Time = 8 hours = 8 * 60 minutes = 480 minutes.
Number of Work Units Produced = (Working Time) / (Cycle Time) * (Work Units per Cycle).
= 480 min / 8 cycles * 2 units.
= 60 units.
(c) Time Worked and Time Lost:
PFD (Performance Factor with Delay) allowance factor is 16%. This factor represents the anticipated amount of time lost due to personal needs, fatigue, and minor delays.
Time Worked = Working Time * (1 - PFD allowance factor).
= 480 min * (1 - 0.16).
= 480 min * 0.84.
= 403.2 min.
Time Lost = Working Time - Time Worked.
= 480 min - 403.2 min.
= 76.8 min.
Read more about Manual assembly tasks.
https://brainly.com/question/28605071
#SPJ11
First Person Who Answers Fast As Possible Will Be Marked As Brainiest
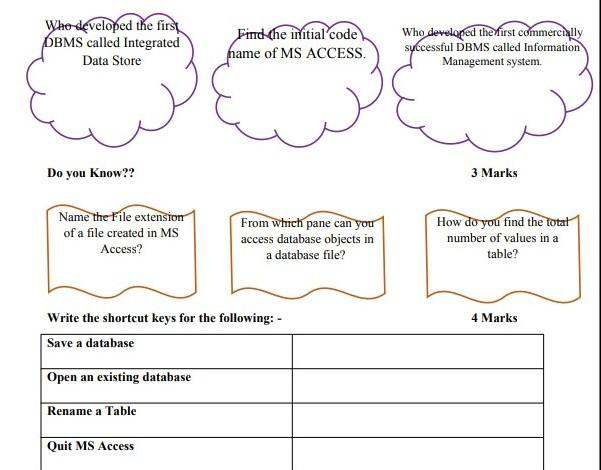
Answers
Answer:
Save a database object Ctrl+S or Shift+F12
Open an existing database Ctrl+O or Ctrl+F12
To quit MS Access ALT+F4
Explanation:
System A takes 80 seconds to run a program. The same program takes 50 seconds to run on a new system B. What is the speedup provided by B over A
Answers
The speedup is 1.6, indicating that System B is 1.6 times faster than System A in running the program.
The speedup provided by system B over A when System A takes 80 seconds to run a program and the same program takes 50 seconds to run on a new system B is 1.6.
The speedup calculation compares the time taken by two systems, A and B, to run a program.
When System A takes 80 seconds and System B takes 50 seconds, the speedup provided by System B over A is calculated as the ratio of the time taken by the old system to the time taken by the new system.
In this case, the speedup is 1.6, indicating that System B is 1.6 times faster than System A in running the program.
The speedup formula, Speedup = Time taken by old system / Time taken by new system, helps quantify the improvement in performance between the two systems.
Speedup can be calculated using the formula: Speedup = Time taken by old system/ Time taken by new system= 80/50= 1.6.
Therefore, the speedup provided by B over A is 1.6.
Learn more about speedup : brainly.com/question/31176774
#SPJ11
hp delays customization of its laser printers as long as possible. this is an example of .
Answers
The customization of Hewlett-laser Packard's printers is postponed as long as feasible. Postponement like this is exemplified.
What is meant by postponement?When an activity is postponed to the furthest point in time, for instance when a customer's demand is satisfied, this is referred to as postponement.
By delaying the business investment in goods and services, postponement is one sort of business strategy that aids in maximizing different types of advantages and risk in the enterprise.
In the supply chain management concept, postponement is crucial since it aids in the production of many generic product kinds.
The customization of the laser printer was delayed by Hewlett-Packard, and this is an example of a postponement, according to the query.
Therefore, the correct answer is Option B. postponement.
The complete question is:
Hewlett-Packard delays customization of its laser printers as long as possible. This is an example of which of the following?
A. standardization
B. postponement
C. timely customization
D. backward integration
E. vendor-managed inventory
To learn more about postponement refer to:
https://brainly.com/question/5141180
#SPJ4
What is micro computer? List out the types of microcomputer. What is micro computer ? List out the types of microcomputer .
Answers
A full-featured computer designed for single-use on a smaller size is known as a microcomputer.
What exactly is a microcomputer?A full-featured computer designed for single-use on a smaller size is known as a microcomputer.
A single-chip microprocessor-based device is now more commonly referred to as a PC, replacing the outdated name "microcomputer." Laptops and desktops are examples of typical microcomputers.
The types of microcomputers are;
Desktop Computer
Laptop
Smartphone
Notebook
Tablet
Hence, a full-featured computer designed for single-use on a smaller size is known as a microcomputer.
To learn more about the microcomputer refer;
https://brainly.com/question/21219576
#SPJ1
What is the name of the device that allows you to speak and hear the voice of a distant person?
Answers
The device that allows you to speak and hear the voice of a distant person is called a telephone.
What is telephone ?Telephone is a device used for communication over a distance. It consists of a transmitter, which converts sound into an electrical signal, and a receiver, which converts the electrical signal back into sound. When two people speak on a telephone, their voices are transmitted through a network of wires and switching systems, allowing them to communicate without being in the same room. The telephone has been an integral part of communication since its invention in the late 19th century, and remains a vital tool for communication today.
It works by converting sound waves into electrical signals which are sent over a telephone line, and then converted back into sound waves at the other end.
To learn more about telephone.
https://brainly.com/question/28039913
#SPJ4
because of its ubiquity in unix/linux systems, ____ has become the de facto standard in network sniffing.
Answers
The Wireshark, a popular open-source network sniffing tool, has become the de facto standard in Unix/Linux systems due to its widespread use and compatibility. Its open-source nature ensures regular updates and compatibility with evolving network technologies in Unix/Linux environments, making it a reliable choice for network analysis tasks. Wireshark's rich feature set, including real-time packet capture, protocol analysis, and customizable filters, provides deep insights into network traffic, making it suitable for diverse network configurations.
Wireshark's user-friendly interface and intuitive workflow make it accessible to both experienced and novice users in the Unix/Linux community. Its graphical user interface (GUI) allows for convenient capture, analysis, and visualization of network traffic. Additionally, Wireshark's command-line tools offer flexibility for different use cases, making it adaptable to various scenarios in Unix/Linux environments.
The extensive documentation, online resources, and community support available for Wireshark further contribute to its adoption as the de facto standard in network sniffing for Unix/Linux systems. The Wireshark community provides ample documentation, tutorials, forums, and mailing lists, which offer support and guidance to users. This wealth of resources makes it easier for network administrators and security analysts to learn and effectively utilize Wireshark in their Unix/Linux environments.
Know more about Unix/Linux systems:
https://brainly.com/question/29648132
#SPJ11
what is a computer class from 8
Answers
Explanation:
computer is an electronic machine which category write in computer data
1 What do you understand by navigation through form?
Answers
Answer:
A navigation form is simply a form that contains a Navigation Control. Navigation forms are a great addition to any desktop database. Microsoft Access offers several features for controlling how users navigate the database.
Why should we follow the codes of conduct while using technology that provides us information
Answers
Codes of conduct are guidelines that outline appropriate behavior and actions when using technology. They are established to ensure that the use of technology is ethical, responsible, and respectful of others. Following codes of conduct while using technology that provides information is important for several reasons:
Respect for privacy and personal information: Codes of conduct help protect individuals' privacy and personal information, by outlining guidelines for collecting, storing, and sharing data.
Ethical use of information: Codes of conduct help ensure that the information provided is used ethically and in a manner that is not harmful to others.
Fairness and accuracy: Codes of conduct help ensure that information is presented in a fair and accurate manner, avoiding bias, manipulation and spreading misinformation.
Maintaining trust: By following codes of conduct, individuals and organizations can maintain the trust of the public by being transparent and accountable in their use of technology and information.
Compliance with laws and regulations: Codes of conduct also help individuals and organizations comply with laws and regulations related to the use of technology and information.
Overall codes of conduct help to promote responsible and ethical behavior in the use of technology and information, which can have a positive impact on society as a whole.
Leonard doesn't like to take the time to update software that is installed
on his computer or mobile phone. In fact, when an update remind pops
up, he always declines the update. How could you convince Leonard that
updating is important?
O Updates often fix vulnerabilities and bugs and make the software more secure.
Updates will lengthen the life of your computer.
Updates are a way to send important information to the software vendor.
Updating frequently will make you eligible for a rewards program.
2 points
Answers
Leonard may not realize that by declining updates on his mobile phone or computer, he is potentially putting his personal data at risk.
Hackers often exploit vulnerabilities in outdated software, so updating frequently is essential to keep your devices secure. In addition to security benefits, updates often improve the performance and functionality of software. By declining updates, Leonard may be missing out on new features and improved usability. It's important to also highlight the benefits of updating software on mobile phones specifically. Mobile phones are frequently targeted by hackers, and updating regularly can help protect against malware and data theft. Additionally, updates can improve battery life and performance, which can extend the life of the phone. Finally, many software vendors offer rewards programs for users who update frequently. These rewards can include free upgrades, exclusive features, or even discounts on future purchases. By updating regularly, Leonard could potentially benefit from these rewards and save money in the long run.
Overall, updating software frequently is important for security, performance, and potential rewards. By explaining these benefits to Leonard, he may be more willing to take the time to update his devices.
Learn more about software here: https://brainly.com/question/985406
#SPJ11
Microsoft .NET Framework 1.1 security Configuration/Wizards
Answers
NET Framework applications and protect them from unauthorized access or tampering.
What are some of the security configuration tools and wizards included in the Microsoft .NET Framework 1.1?The Microsoft .NET Framework 1.1 includes several wizards and configuration tools that can be used to enhance the security of applications developed on this platform. Some of these tools include:
NET Configuration tool: This tool allows you to configure security settings for individual applications running on the .NET Framework. It provides an easy-to-use interface for modifying permissions, trust levels, and other security-related settings. Code Access Security Policy tool: This tool lets you specify a set of security policies that determine what permissions your application can have. It helps you to define what your application can do and what resources it can access. Strong Name tool: This tool is used to sign assemblies with a strong name, which is a unique identifier that helps prevent tampering and ensures that the code you are running is authentic. Assembly Registration tool: This tool registers assemblies and COM components on a computer, allowing them to be accessed by other applications. XML Schema Definition Tool: This tool generates XML schema definitions from CLR types, enabling you to create XML documents that conform to your application's data format.By using these tools and configuring your applications appropriately, you can enhance the security of your .NET Framework applications and protect them from unauthorized access or tampering.
Learn more about NET Framework
brainly.com/question/30030987
#SPJ11