if there is a line of people waiting to purchase movie tickets, and the person at the front of the line is the first to be served and to leave the queue, and any new person would have to join the line at the back, would this be a stack, queue, or a priority queue?
Answers
This scenario represents a queue. A queue is a data structure where elements are inserted at the end and removed from the front in a first-in, first-out (FIFO) order. In this case, people are added to the back of the line as they arrive, and the person at the front of the line is served and leaves first.
For such more question on FIFO
https://brainly.com/question/11493725
#SPJ11
Related Questions
Answer urgently needed!!!
•write 5 differences between pin and password
Answers
Answer: Here Are Some Of Them
a Personal Information Number (PIN) allows you to prove that you're you, so that no one else can access your data. The obvious difference is that a PIN is limited to numerical digits (0-9), while a password can contain numerical digits, upper- and lowercase letters, and punctuation. PINs can facilitate a quicker, more usable experience. Signing in with a shorter PIN code instead of a password might help somewhat with issues related to password usability and fatigue. Signing in with a shorter PIN code instead of a password might help somewhat with issues related to password usability and fatigue
Explanation:
what is full form of RAM???
Answers
Answer:
Random Access Memory, it's used to store working data and machine codes
Explanation:
Hope it helped !
Adriel
what is an inversion in a permutation ? what is the relationship between the running time of bubble sort and number of inversions in the input array ?
Answers
An inversion in a permutation is a pair of elements that are in the opposite order from their desired order.
The running time of bubble sort is proportional to the number of inversions in the input array.
An inversion occurs when two elements in a permutation are not in their correct relative order. For example, in the permutation (4, 2, 3, 1), the pairs (4, 2), (4, 3), and (3, 1) are inversions. The number of inversions in a permutation is a measure of how far it is from being sorted.
Bubble sort is a simple sorting algorithm that repeatedly swaps adjacent elements that are out of order until the array is sorted. Its running time is O(n^2), where n is the number of elements in the input array. The number of inversions in the input array affects the running time of bubble sort because the more inversions there are, the more swaps bubble sort will have to make.
In general, algorithms that are based on comparing elements, such as bubble sort and merge sort, have a running time that is proportional to the number of inversions in the input. Inversions are also used in other areas of computer science, such as in the design and analysis of data structures and algorithms.
Learn more about bubble sort https://brainly.com/question/30395481
#SPJ11
Mr. Morrison wants told Austin there is always going to be some storms that you have to go through what were Austin’s biggest storms 
Answers
Austin, Texas is no stranger to severe weather, such as hurricanes, tornadoes, and snowstorms. Some of Austin's most powerful storms include
storm Carla (1961)Tornado outbreak (1981)How is this so?* storm Carla (1961): On September 11, 1961, a Category 4 storm made landfall in Port O'Connor, Texas. The storm dumped torrential rains and caused floods in Austin, causing significant damage and power disruptions.
* Tornado outbreak (1981): On Memorial Day weekend in 1981, a tornado outbreak occurred, resulting in six tornadoes in the Austin region. The most powerful tornado was an F4 tornado that devastated Georgetown, killing 11 people and injured over 100 others.
* Ice storm (2021): In January 2021, a significant ice storm hit the Austin region, causing extensive power disruptions and destruction. The storm also caused several road accidents and deaths.
*snowfall (2023): In February 2023, a severe snowfall hit the Austin region, dumping several inches of snow on the city. The storm disrupted transport and caused power outages throughout the region.
These are just a few of Austin's most powerful storms. Mr. Morrison is correct in predicting that Austin will face storms in the future. Residents must be prepared for severe storms and have a strategy in place in case they materialize.
Learn more about storms:
https://brainly.com/question/11163773?
#SPJ1
You have created a new storage space using a single 500 GB external USB 3.0 drive. The drive is becoming full, so you add another external 1 TB USB 2.0 drive to the storage pool. Now that you have two drives, you would like to create a volume with storage space resiliency set to two-way mirror. You create the new volume with two-way resiliency and a size limit of 1 TB. As you are copying files from the C: drive to this new volume, you receive a warning that you are running out of space. Only a few hundred megabytes have been copied; why might you be receiving the warning so quickly? What can you do about it?
Answers
Answer:
In the clarification section following, the definition including its query is mentioned.
Explanation:
I believe we possess 2 other discs except for the major memory card-a USB 500 GB USB 3.0 drive, just one TB USB 2.0 drive. So we're making a two-array mirrored storage space resilience kit. We get a warning when we duplicate files from either the C: drive towards this second adaptation that you should be running out of places. That was because these need to have a backup process around each other discs throughout the situation of a two-way mirror.This serves to protect the organization from disc failure and enhances the overall efficiency of the device. Thus, even when copying, even though only several 100 MB has also been cut and pasted to something like the disc, the disc intercepts that the information collected from either the 500 GB drive as well as the major disc must be stored there. And that is how the alert arrives that throughout the new trip, we're running out of space. So this is how they so easily get the alarm.
smart tv has _____ intergrated with it
Answers
Answer:
an operating system
Explanation:
An IT technician is applying a static IP address to a printer. Which piece of IP addressing information on the printer would allow the technician to check connectivity with a PC on a remote network?
Answers
Answer:
ip ADDRESS
Explanation:
These static IP addresses can be established on the device directly, for example using each computer's network settings on Windows, or they can be set at the router level. Although many people (and even some routers) still refer to it as a “static IP address,” doing it at the router level is referred to as assigning a DHCP reservation.
What IT technician is applying a static IP?Your computer's IP address lets the rest of the Internet know if it is running a web server. Internet-connected devices can have either a static IP address, which remains constant over time, or a dynamic IP address, which is subject to change over time.
A gadget with a static IP address assures that it can be found on the network easily because the IP address won't change.
Therefore, IP address allow the technician to check connectivity with a PC on a remote network.
Learn more about static IP here:
https://brainly.com/question/17063812
#SPJ5
please help me very important
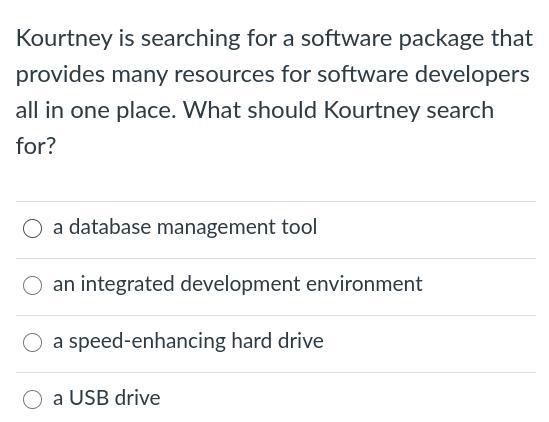
Answers
Answer:
C, Or D.
Explanation:
Because A speed enhancing hard drive Can store any type of quick file if you just click on it will load fast. Same thing goes for a hard drive but you have to transfer the file
Draw a structured flowchart or write structured pseudocode describing your preparation to go to work or school in the morning. Include at least two decisions and two loops.
Answers
The pseudocode for preparing to go to work or school in the morning includes steps to set the alarm, get ready, decide on transportation mode, and eat breakfast, as well as decisions on whether to go back to sleep and what mode of transportation to take, and loops to continue preparing until fully awake and to check the gas level (if driving).
Here's an example of structured pseudocode for preparing to go to work or school in the morning:
Start
Set alarm for desired wake-up time
If alarm goes off:
Turn off alarm
Get out of bed
Else:
Go back to sleep
While not fully awake:
Take a shower
Brush teeth
Get dressed
While breakfast is being prepared:
Decide on transportation mode (car, bike, bus, etc.)
If driving:
Check gas level in car
If low on gas:
Go to gas station
Else:
Leave for work or school
Eat breakfast
End
In this pseudocode, there are two decisions: one to decide whether to go back to sleep after the alarm goes off, and another to decide on the mode of transportation. There are also two loops: one to continue preparing for the day until fully awake, and another to check the gas level and potentially go to a gas station before leaving.
Learn more about structured pseudocode :
https://brainly.com/question/30667511
#SPJ11
What is Relational Computerized Database
Answers
Answer:
Relational computerized database uses tables and columns to store data. each table is composed of records and each record is tied to an attribute containing a unique value. This helps the user use the data base by search query and gives the opportunity to build large and complex data bases
if you have multiple identical outputs that need to be driven off of an audio console (multiple news channel feeds as an example), it would be convenient to have a...
Answers
The Channel way comes first. The section of the console used to send a microphone signal (or synth output) to the multitrack tape machine to, you know, record it is also known as the Record path.
If you've ever paid close attention to microphones, pro audio equipment, or expensive headphone amplifiers, you've probably noticed the phrase "balanced connection" used to describe the equipment's output, input, or both. Each channel has a channel fader and two input paths. The channel (recording) path will typically be controlled by the upper fader. The monitor (after-recorder) signal path will be affected by the lower fader. As in the previous illustration, the signal flow starts with the singer, microphone, microphone preamplifier, EQ, and compressor.
Learn more about microphone here-
https://brainly.com/question/29218032
#SPJ4
FILL IN THE BLANK. This type of software allows students to record, sort, mathematically analyze and represent numerical data in tabular and/or graphical forms. ___
Answers
Spreadsheets software is a type of software allows students to record, sort, mathematically analyze and represent numerical data in tabular and/or graphical forms.
Why do people use spreadsheets?One tool for storing, modifying, and analyzing data is a spreadsheet. A spreadsheet's data is arranged in a series of rows and columns, where it can be searched, sorted, calculated, and used in a number of charts and graphs.
Therefore, A program known as a spreadsheet, also referred to as a tabular form, is used to arrange data into rows and columns. This information can then be arranged, sorted, calculated (using formulas and functions), analyzed, or graphically represented to illustrate.
Learn more about Spreadsheets from
https://brainly.com/question/26919847
#SPJ1
how can we use the output of the floyd-warshall algorithm to detect the presence of a negative-weight cycle?
Answers
The Floyd-Warshall algorithm finds the shortest path between all vertices in a weighted graph. If there is a negative-weight cycle, at least one diagonal element of the distance matrix will be negative.
The Floyd-Warshall algorithm is a dynamic programming algorithm that computes the shortest path between all pairs of vertices in a weighted graph. If the algorithm detects a negative-weight cycle in the graph, it will output a negative value for at least one of the diagonal elements of the distance matrix. This is because a negative-weight cycle means that it is possible to keep reducing the distance between two vertices by repeatedly traversing the cycle, leading to an infinitely negative distance.
Therefore, to detect the presence of a negative-weight cycle using the output of the Floyd-Warshall algorithm, we need to check if there is any negative value in the diagonal elements of the distance matrix. If there is at least one negative value, then there is a negative-weight cycle in the graph. If all diagonal elements are non-negative, then there is no negative-weight cycle in the graph.
learn more about Floyd-Warshall algorithm here:
https://brainly.com/question/31361414
#SPJ11
introduce yourself by following the rule

Answers
My name is Trisha Davis, I am a first year medical student and i love to read and write books. I hate lies and i love anyone who is honest.
What is self introduction?My name is Trisha Davis, I am a first year medical student and i love to read and write books. I hate lies and i love anyone who is honest.
My goal in life is to be a medical doctor and also an entrepreneur. I love to help others and put smile on people's face. What i want from life is good health, favor and avenue to showcase my gifts to the world.
Learn more about self introduction from
https://brainly.com/question/26685169
#SPJ1
Write 2-4 short & energetic sentences to interest the reader! Mention your role, experience & most importantly - your biggest achievements, best qualities and skills about data entry.
Answers
Searching for an information section genius? Look no further! With north of 5 years of involvement and a 99.9% precision rate, I'm the ideal possibility for your information passage needs. My scrupulousness, speed, and proficiency will guarantee that your information is precisely and productively entered, like clockwork. We should cooperate to make your information passage calm!
PLZZZ HELPPPP
Which list can be sorted with a bubble sort?
(4, 5, 6, 7)
('dog', 'cat', 'fish')
['dog', 'cat', 'fish', 'bird']
[2, 5, 'dog', 'cat']
Answers
Answer:
dog cat fish bird
Explanation:
Answer:
dog cat fish bird
Explanation:
i got it right
you are installing a known good nic in a computer, and a spark jumps from your hand to the nic. you install the nic and discover that the nic no longer operates correctly. what has most likely caused the nic to malfunction?
Answers
The most likely caused the nic to malfunction in this scenario is Electrostatic Discharge (ESD). ESD occurs when there is a sudden flow of electricity between two objects that are at different electrical potentials.
In this case, the spark that jumped from your hand to the nic could have caused ESD and damaged the sensitive electronic components within the nic, resulting in it no longer operating correctly. It is important to take precautions to prevent ESD when handling computer components, such as wearing an anti-static wrist strap or grounding yourself before handling the components.
Electrostatic Discharge ESD occurs when there is a sudden transfer of electrostatic charge between two objects. In this case, the spark from your hand to the NIC suggests that ESD occurred during the installation process. ESD can damage sensitive electronic components, such as a NIC, by causing small electrical arcs that can burn or damage the internal circuits, leading to the malfunction you observed. To avoid ESD, it is essential to take proper precautions, such as using an anti-static wrist strap and working on a grounded, static-free surface.
To know more about nic visit :
https://brainly.com/question/29568313
#SPJ11
Use the Macro Recorder
1. Use the macro recorder to create a macro named ClearInvoice, and add the following text in the description box: This macro clears existing values in the current invoice. (include the period).
2. Simultaneously delete the contents of cells C7:C11.
3. Type Name in cell C7 and press ENTER [remaining cell contents will autocomplete].
4. Stop recording the macro.
5. Save the file as an macro enabled template using the default name.
Answers
To complete these steps, you will need to use the Macro Recorder feature in your spreadsheet program. This feature allows you to record a series of actions and create a macro that can be run again in the future.
1. To start, open the spreadsheet where you want to create the macro. Then, go to the Macro Recorder feature and click on "Record Macro." Name the macro "ClearInvoice" and add the description "This macro clears existing values in the current invoice." Don't forget the period at the end.2. With the Macro Recorder still running, highlight cells C7 to C11 and delete their contents simultaneously. This will be recorded as part of the macro.
3. After deleting the contents, type "Name" in cell C7 and press ENTER. The remaining cell contents should autocomplete.
4. When you have finished these steps, stop recording the macro.
5. Finally, save the file as a macro-enabled template using the default name. This will ensure that the macro is available whenever you open this particular template.
Using the Macro Recorder can save you time and effort in the long run by automating repetitive tasks. By following these steps, you can create a useful macro that clears existing values in the current invoice and updates the Name field automatically.
To learn more about Recorder click the link below:
brainly.com/question/29847134
#SPJ11
how to get rid of this weird line at the top of my screen

Answers
It's difficult to provide a solution without more information about the nature of the line you're seeing, the device you're using, and the software you're running.
What is computer screen?However, here are a few general troubleshooting steps you can try:
Restart your device: Sometimes a simple restart can fix many software-related issues.
Check for updates: If you're using a device that's running an operating system, check if there are any available updates. Installing updates can often fix bugs and improve the overall performance of your device.
Run a virus scan: If you suspect that the line may be caused by malware, run a virus scan using your preferred antivirus software.
Check your display settings: Depending on your device and operating system, you may be able to adjust display settings, such as the resolution or refresh rate. Experiment with adjusting these settings to see if it resolves the issue.
Lastly, Seek technical support: If none of the above steps work, consider seeking technical support from the manufacturer of your device or from a qualified technician. They may be able to diagnose and fix the issue more effectively.
Learn more about computer screen from
https://brainly.com/question/9017156
#SPJ1
What is the MOST likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour?
Question 2 options:
It reminds her to stand up for a few minutes each hour.
It signals that it's meal time.
It wakes her up in case she falls asleep.
It reminds her to readjust the position of her monitor.
Answers
The most likely reason for Karla to set an alarm on her work computer for 50 minutes past the hour every hour is option C: It wakes her up in case she falls asleep.
How were people on time for work before alarm clocks?Ancient Greeks as well as Egyptians created sundials and colossal obelisks that would serve as time markers by casting a shadow that changed with the position of the sun.
Humans created hourglasses, water clocks, as well as oil lamps that measured the passage of time by the movements of sand, water, and oil as early as 1500 B.C.
Therefore, An alarm clock, or simply an alarm, is a type of clock used to warn a person or group of people at a certain time. These clocks' main purpose is to wake people up after a night's sleep or a little nap; however, they can also serve as reminders for other things.
Learn more about alarm clock from
https://brainly.com/question/16452153
#SPJ1
Need help fast this is do a 4

Answers
Answer:
I believe the answer is B.
what type of software is an antivirus?
Answers
Answer: what type of software is an antivirus?
Answer: A security software
Explanation:
Antivirus software is a type of security software designed to protect users from multiple types of malware, not just viruses. The software is a risk management tool that scans devices regularly and on-demand for known malware and suspicious behavior associated with malware.
Answer:
It is a security software.
Explanation:
It helps protect your computer from viruses and other things.
Carla is researching temperament by determining the extent to which different babies can focus attention and not be distracted. Which dimension of temperament is Carla assessing
Answers
Carla is assessing the dimension of temperament known as "attention span and persistence." This dimension refers to the ability of babies to focus their attention and resist being easily distracted.
What dimension of temperament is Carla assessing?Carla is assessing the dimension of temperament known as "attention span and persistence." This dimension refers to the ability of babies to focus their attention and resist being easily distracted.
By studying this aspect of temperament, Carla aims to understand variations in how long babies can concentrate on a particular task or stimulus without being easily diverted by external stimuli.
This research helps in identifying individual differences in attentional abilities among infants and provides insights into the development of attention and concentration skills during early childhood.
Learn more about temperament
brainly.com/question/31454664
#SPJ11
How was the creation of the world wide web browser a stepping stone for future scientific breakthroughs?
Answers
Answer:
Following are the point that described the web browser for the stepping stone as a future scientific breakthroughs.
Explanation:
Tim Berners Lee was the founder of world wide web .The Tim Berners Lee is software engineer at CERN they had seen the troubling of exchanging the data .In that time there are various data in various computer .The Tim Berners Lee felt he had found the way for resolving this problem and develop a thing so that we can exchange the data in any where .In that time already lots of computer are already linked each other with the high speed of the internet so tim develop a new technology called hypertext .In the March 1989, in a paper titled known as "Information Management" Tim is developed but this proposal is rejected .In the 1990 Tim is developed the three technology HTML ,URI and HTTP with the help of this the world wide web is developed and we can share the information anywhere in the world .The sharing of information in a easy way gives the future bright the person in anywhere in the world will access the data or the information also We cam communicate anywhere in the world by using email .create the getuserchoice() function. • parameter: menudict is a dictionary for the menu
Answers
The getuserchoice() function is a useful tool for programming in Python. This function takes a dictionary of menu items as its parameter and prompts the user to select an option from the menu. It then returns the user's choice.
To create the getuserchoice() function, you will need to define it and give it a parameter for the menu dictionary. You can then use the input() function to prompt the user for their choice. You will need to loop through the dictionary to display the menu options to the user. Once the user has made their choice, you can use the dictionary to retrieve the corresponding value.
Here's an example implementation of the getuserchoice() function:
```
def getuserchoice(menudict):
for option in menudict:
print(option + ": " + menudict[option])
choice = input("Please enter your choice: ")
while choice not in menudict:
choice = input("Invalid choice. Please enter a valid choice: ")
return menudict[choice]
```
In this example, the function takes a dictionary called menudict as its parameter. The function then loops through the dictionary to display the menu options to the user. The input() function is used to prompt the user for their choice. The while loop ensures that the user enters a valid choice by checking that their choice is in the menu dictionary. Finally, the function returns the value associated with the user's choice in the dictionary.
Remember to test your function thoroughly with different menu dictionaries to make sure it works as expected.
To know more about function visit:
https://brainly.com/question/30721594
#SPJ11
In order for a computer to pass the ________, a human should have a conversation with it and not be able to tell if it was a machine or a human.
Answers
The test that a computer needs to pass after a human's conversation with it and not be able to tell if it was a machine or a human is; Turing Test
Test of ComputersThe correct answer to the blank portion of the question is Turing test. This is because Turing Test is a test of a computer's ability to exhibit intelligent behavior that is equivalent to, or indistinguishable from, that of a human's behavior.
Finally, If the evaluator cannot reliably tell the computer from the human, the machine is said to have passed the test.
Read more about Test of Computer at; https://brainly.com/question/21283135
They removed my other post but I didn't learn my lesson :)
Unblocked web proxy services:
Latest(dot)cf
If that doesn't work then go to
securly(dot)fail
the dot=. So uhm yea. Wont let me put links but its ok :) hope this helps you.
(Games directory is currently down, working on the rammerhead proxy)
Answers
Answer:
thank you so much I'm so bored in class
Explanation:
Business intelligence (BI) is a narrow term that refers to specific architectures, tools, databases, analytical tools, applications, and methodologies. (True/False)
Answers
True. Business intelligence (BI) is a term that specifically refers to the various architectures, tools, databases, analytical tools, applications, and methodologies that are used to gather, store, analyze, and present business information in a way that helps organizations make more informed decisions.
True. Business intelligence (BI) refers to specific architectures, tools, databases, analytical tools, applications, and methodologies that are used to collect, analyze, and present data for better decision-making in a business context. These components work together to help organizations make more informed decisions and improve overall performance.
Business intelligence (BI) includes the techniques and strategies companies use to analyze data and manage business information. The main functions of business intelligence technology include reporting, online analytics, analytics, dashboard development, data mining, mining techniques, complex operations, performance management, metrics, data mining, predictive analytics, and analytics.
Business intelligence (BI) includes the techniques and strategies companies use to analyze data and manage business information. The main functions of business intelligence technology include reporting, online analysis, analytics, dashboard development, data mining, process mining, complex operations, performance management, measurement, data mining, forecasting, and analysis.
Learn more about the Database:
brainly.com/question/30634903
#SPJ11
Tech A says that in mid-engine vehicles, the engine is mounted behind the rear wheels. Tech B says that in rear-engine vehicles, the engine is mounted in front of the rear axle. Who is correct?A) Tech AB) Tech BC) Both Techs A and BD) Neither Tech A nor B
Answers
Regarding the statement of the two technicians about engine of vehicle, Neither Tech A nor B is correct.
So, the answer is option C.
In mid-engine vehicles, the engine is mounted between the front and rear axles, typically behind the driver's seat. This design allows for better weight distribution and handling.
In rear-engine vehicles, the engine is mounted behind the rear axle, which can result in more traction and stability but can also lead to oversteer and other handling issues. It's important for technicians to have a clear understanding of vehicle design and mechanics in order to diagnose and repair issues accurately.
Hence,the option C is correct answer.
Learn more about traction at https://brainly.com/question/26538813
#SPJ11
Suppose cell C5 contains the formula =B$6+C1.
Match each formula with its respective cell if you copied it.
=A$6+B4 =B$6+C6 =C$6+D2 =D$6+E1
Thank you, have a great week.
Answers
Answer:
=A$6+B4 will be in B8
=B$6+C6 will be in C10
=C$6+D2 will be in D6
=D$6+E1 will be in E5
Explanation:
$ sign is used to lock a certain column or row value, with the $ sign we can create an absolute reference which will remain unchanged as we copy our formula from one cell to another.
As formulars are copied, the references change respectively.
With =B$6+C1 in C5 ; As we move up or down of cell C5, only the row numbers will change that is formula in C6 becomes =B$6+C2.
As we move left and right, the column alphabet will also experience change like the rows did.
Only the absolute reference won't change no matter the direction.
Hence,
=A$6+B4 ; A and B means one move to the left of C5 and 4 signifies, 3 moves downward of C5 that gives B8
=B$6+C6 ; B and C means no horizontal change, 6 means 5 moves downward of C5 which gives C10
=C$6+D2 ; C and D means 1 move to the right and 2 means one move downward of C5 which gives D6
=D$6+E1 ; D and E means 2 moves to the right and 1 means no vertical change from C5 ; which gives E5