IM in high school (freshmen) and I started using brainly when I was in middle school, haven't made much friends but im ok with who I have! Anyways question is abt career management!
In Stage 2, the Thinking stage, John would probably:
Research ways to quit smoking.
Switch over to nicotine gum or e-cigs.
Blame it on pollution in the air
Admit he has a problem, but put off doing anything.
Answers
Answer:
My Spring 2018 Sabbatical Project was to study techniques and ideas of classroom management. The result was a set of documents and resources that I am placing here in blog format to easily share with my colleagues and any other interested party.
Comments and questions are welcome, and I will respond as time allows. Feel free to share these posts.
Sincerely,
Tracy Johnston
Palomar College Mathematics Department
Answer:
The more sane thing that he should do is to research ways to quit smoking.
Explanation:
Smoking is not good for you, nor are e-cigs
Nicotine gum is just as addictive and is quite expensive
There really isn't much pollution in the air, mostly allergens
You gotta do something, you'll die if you keep smoking/vaping or whatever he is doing
Related Questions
B. State True or False: 1. 'Date within' option allows you to search an email within a specified date range.
Answers
Answer + Explanation:
his topic describes the email and document properties that you can search for in email items in Exchange Online and documents stored on SharePoint and OneDrive for Business sites by using the Content Search feature in the Security & Compliance Center. You can also use the *-Compliance Search cmdlets in Security & Compliance Center PowerShell to search for these properties
Please have a great day <3
Network layer protocols specify the _______ structure and processing used to carry data between hosts.
Answers
Network layer protocols specify the packet structure and processing used to carry data between hosts.
What is the Network layer protocols about?The header, payload, as well as the trailer of a network packet are its three component pieces. The underlying network architecture or protocol employed determines the format and size of a network packet. A network packet resembles a package in concept.
Therefore, Network layer protocols define the packet format and processing needed to transfer data from one host to another host, in contrast to the Transmission layer (OSI Layer 4), which controls the data transport between the programs operating on each end computer.
Learn more about Network layer from
https://brainly.com/question/14476736
#SPJ1
If you need to modify a features in a part created using the Mirror tool, you can make the change in the original feature and the feature on the other side of the mirror plane will be modified automatically.
Select Answer
False
True
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
The correct answer to this question is TRUE.
Because when you are designing something and drawing anything and it is symmetric in shape and half of the part is created, then if you use mirror features, then the other half part will get created automatically.
If you need to modify the features in the original part of the drawing or design then the other side of the mirror plane will be modified automatically.
Because whatever you will make changes in the original part of the design, then the other part that is created by using mirror features will get modified automatically.
Nanotechnology is a scientific area that deals with making or changing things that are incredibly _______________.
Answers
Answer:
small
Explanation:
Nanotechnology deals with incredibly small things on the nanoscale.
which approach to data analytics attempts to characterize the typical behavior of an individual, group or population by generating summary statistics about the data?
Answers
The approach to data analytics that attempts to characterize the typical behavior of an individual, group, or population by generating summary statistics about the data is called descriptive analytics.
Descriptive analytics focuses on understanding and summarizing data to gain insights into patterns, trends, and central tendencies. It involves the use of statistical techniques to calculate measures such as mean, median, mode, standard deviation, and percentiles. These summary statistics provide a high-level overview of the data and help in describing the characteristics and behavior of the individuals, groups, or populations under study.
By analyzing and interpreting these summary statistics, analysts can identify key features of the data, detect outliers, and make informed decisions based on the observed patterns and trends. Descriptive analytics serves as a fundamental step in data analysis, providing a foundation for further exploration and inference.
Learn more about data analytics here:
https://brainly.com/question/23860654
#SPJ11
Cheryl is responsible for cybersecurity at a mid-sized insurance company. She has decided to use a different vendor for a network antimalware than she uses for host antimalware. Is this a recommended action, why or why not
Answers
yes, this a recommended action and this is known to be best described as vendor diversity.
What is Vendor diversity?This is known to be one that gives two security benefits in regards to the fact that it does not have a single point of failure if one vendor cease operations and also each vendor has their own methodology and algorithms used for known or seeing malware.
Hence in the above case, yes, this a recommended action and this is known to be best described as vendor diversity.
learn more about cybersecurity from
https://brainly.com/question/12010892
#SPJ1
____ operation codes are restricted to be used in the operating system or other system software.
Answers
Privileged operation codes are restricted to be used in the operating system or other system software.
Operation codes, also known as opcodes, are used to represent specific computer instructions. These instructions are used by the CPU to execute specific tasks. Operation codes are often associated with assembly language programming. They are restricted to be used only in operating systems and other system software.
Applications and other user-level programs do not use operation codes directly, but instead use high-level programming languages that are compiled or interpreted into machine code that uses operation codes. The use of operation codes is restricted in order to maintain the stability and security of the operating system and prevent unauthorized access or modification of system resources.
Know more about Operation codes, here:
https://brainly.com/question/32222843
#SPJ11
Which game is better? Among us or ROBLOX -
Answers
Answer:
Both are equally good, but Roblox is better for kids
Explanation:
This is because when you are imposter and kill someone it shows a bone and there is a bit of blood!
Answer:
Gud question...
Explanation:
Among us is violent
Roblox is good for kids
so 50 50
Implement the method countSecondInitial which accepts as parameters an ArrayList of Strings and a letter, stored in a String). (Precondition: the
String letter has only one character. You do not need to check for this.) The method should return the number of Strings in the input ArrayList
that is in the second index with the given letter. Your implementation should ignore the case of the Strings in the ArrayList
Sample Run:
Please enter words, enter STOP to stop the loop.
find
dice
hi
dye
STOP
Enter initials to search for, enter STOP to stop the loop.
1
Search for 1: 3
Hint - the algorithm to implement this method is just a modified version of the linear search algorithm.
Use the runner class to test your method but do not add a main method to your U7_14_Activity One.java file or your code will not be scored
correctly.
We have provided a couple of sample runs that can be used to test your code, but you do not need to include a Scanner and ask for user input when
submitting your code for grading because the grader will test these inputs automatically.
Answers
Answer:
import java.util.ArrayList;
public class U7_L4_Activity_One
{
public static int countSecondInitial(ArrayList<String> list, String letter)
{
char letter1 = letter.toLowerCase().charAt(0);
int count = 0;
String phrase = "";
for(int i = 0; i < list.size(); i++)
{
phrase = list.get(i).toLowerCase();
if(phrase.charAt(1) == letter1)
{
count++;
}
}
return count;
}
}
Explanation:
I genuinely couldn't tell you why the program cares, but it worked just fine when I ran the search word as a char variable as opposed to a 1-length string variable, i.e. the inputted 'letter' parameter.
If it works, it works.
PS. You got 33% RIGHT because you didn't have a 'public static void main' as the method header. I don't doubt your code works fine, but the grader is strict about meeting its criteria, so even if your code completed it perfectly and THEN some, you'd still get the remaining 66% wrong for not using a char variable.
NEED THIS ASAP!!) Which of the following are major types of models used to distribute proprietary software? Select Two Options.
A colony
B Dividend
C Demoware
D freemium
E census
Answers
Demoware are the models of proprietary software. Demoware is a method of distributing computer software.
What is software model?Software designs can be expressed through software models. Typically, the program design is expressed using an abstract language or images. An object modeling language, such as UML, is used to create and express the program design for object-oriented software.
An abstraction of the software development process is a software process model. The stages and sequence of a process are described by the models. Consider this then as a depiction of the order of the process's actions and the order in which they are carried out. The following will be defined by a model: The things that need to be done.
To learn more about software model refer to:
https://brainly.com/question/28163689
#SPJ1
Can you write a story about any princess?
Mark brainiest. Please
Answers
Okay well here's a short one. The main problem in Cinderella is that she wants to go to the ball but her stepsisters prevent her from going because they wanna marry the prince-
Cinderella is a beautiful kind daughter sees the world upside down when her mother dies and so her father in pain marries another woman who is wicked and the name is "Lady Termaine" she has two cruel daughters who get so jealous so easily. The daughters are named Drizella & Anastasia.
An android user recently cracked their screen and had it replaced. If they are in a dark room, the phone works fine. If the user enters a room with normal lights on, then the phone's display is dim and hard to read. What is most likely the problem?
Answers
There are two possibilities for the problem in the given scenario. The first and most probable cause of the problem is that the replaced screen was of low quality or did not meet the device's standards.
Therefore, the screen is not transmitting light properly and is producing dim or blurry images.The second possibility for the problem is that the light sensor of the phone might be affected by the screen replacement. The phone might be adjusting the brightness levels based on the low light environment in the dark room and not adjusting correctly in the normal light environment.
This can result in the phone being too bright or too dim, making it difficult to read the display.However, both of these possibilities can be avoided by purchasing a high-quality replacement screen or seeking professional assistance to fix the problem. In such cases, it is recommended to have an expert inspect the device for any faults and repair it accordingly.Moreover, one can also try to adjust the screen brightness levels manually to make the display more readable in the normal light environment.
To know more about visit:
https://brainly.com/question/32730510
#SPJ11
You can switch to Page Layout view by clicking the Page Layout button ____.
Answers
You can switch to Page Layout view by clicking the Page Layout button in MS Word.
The Page Layout View is a new feature of Microsoft Word 2007 that enables you to view and modify pages as they will appear when printed. Page Layout view displays all formatting, such as margins, headers, and footers, as they appear on the printed page. This view is similar to Print Layout view, except that it displays a more detailed preview of the printed page, which can be helpful in formatting a document for printing.
In Microsoft Word, there are three primary modes for viewing your document: Normal, Web Layout, and Page Layout. Page Layout view is a great way to examine your document's layout. It enables you to display headers and footers, margins, and page orientation more effectively. The zoom level in this view is set by default to show the entire page, but you can adjust it to suit your preferences. With Page Layout view, you can see how the text on your document is positioned on the page and how graphics, such as pictures and charts, appear within the text.
Learn more about Page Layout: https://brainly.com/question/27964724
#SPJ11
suppose you are working with the tiny clothes database. write one sql query to find the name and address of everyone who bought pants.
Answers
SELECT Name, AddressFROM Customers
JOIN Orders ON Customers.CustomerID = Orders.CustomerIDJOIN OrderItems ON Orders.OrderID = OrderItems.OrderID
JOIN Products ON OrderItems.ProductID = Products.ProductIDWHERE Products.ProductType = 'pants';
The SQL query above retrieves the Name and Address of customers who bought pants from the Tiny Clothes database.
by joining multiple tables: Customers, Orders, OrderItems, and Products. The query links the CustomerID in the Customers table to the CustomerID in the Orders table, then joins the OrderID in Orders with the OrderID in OrderItems, and finally links the ProductID in OrderItems with the ProductID in Products. The WHERE clause filters the results to only include products with the ProductType of 'pants'. This query provides the desired information about customers who pants.
Learn more about SQL here:
https://brainly.com/question/31663284
#SPJ11
given: use the following (short) document corpus for the remaining part of the homework. d1 higher term frequenc longer document d2 repeat term give higher term frequenc d3 term frequenc import term document d4 invers document frequenc import term corpu
Answers
The provided document corpus is used to study various aspects of document analysis, including term frequency, document length, and importance of terms in a document and in the corpus.
What is the purpose of the provided document corpus in document analysis?The paragraph provides a document corpus consisting of four documents, each with a different characteristic. Document d1 has higher term frequency and is a longer document, while d2 has a repeat term that gives it higher term frequency.
Document d3 has a term frequency that emphasizes the importance of a term in a document, while d4 has an inverse document frequency that emphasizes the importance of a term in the corpus as a whole.
This corpus can be used to study various aspects of document analysis, including term frequency, document length, and importance of terms in a document and in the corpus.
Learn more about document corpus
brainly.com/question/31219209
#SPJ11
Match the learning styles with the example.
Column B
Column A
a. Visual
1.
b. Auditory
2.
C. Kinesthetic
3.
Angela likes to review graphs and articles.
Which learning style do you think best matches
this student?
Helga likes to take notes and do fun activities.
Which learning style do you think best matches
this student?
Armando creates pictures to help remember his
math concepts. Which learning style do you
think best matches this student?
Hannah likes group discussions and oral
presentations from her teacher. Which learning
style do you think best matches this student?
Enjoy discussions and talking things through
and listening to others.
Benefit from illustrations and presentations,
and especially those in color.
Likes to move around a lot.
4.
5.
6
7
Answers
Answer
it would be c
Explanation:
what is the base number of binary, decimal and octal?
Answers
Answer:
Explanation:

Answer:
0 and 1
Explanation:
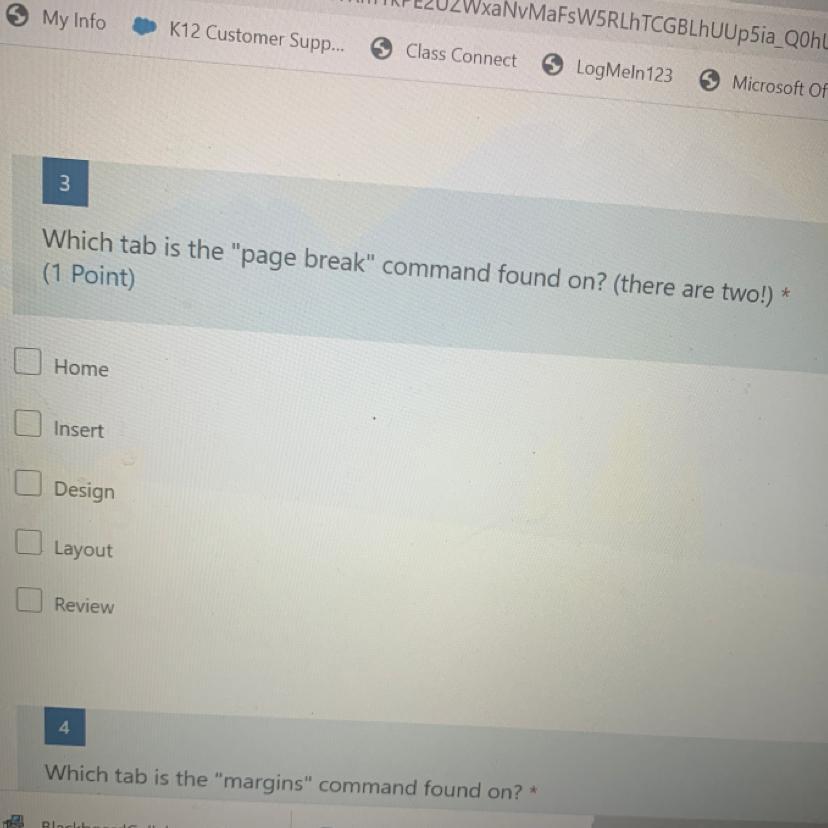
Which tab is the "page break" command found on? (there are two!) *
(1 Point)
Home
Insert
Design
Layout
Review
Answers
Answer:
home and layout
Explanation:
Are DVD players, USBs, printers/scanners, guitar amps, satellite dishes, headphones, dishwashers, radios, and modern cars considered computers?
Answers
Answer:
yes
Explanation:
um ik for sure that a printer/scanner is a computer in a way^^
Answer:
yes they are considered!
Explanation:
they are conisdered computers due to having an interioir machine, which has been engineered to perfrom certain tasks, just like a computer.
i need help with this my laptop is not let me connet to my wifi and when i try to add out wifi if says "connect Failed" please help i need it to work

Answers
Answer: try taking it to your media center for help or maybe try connecting to different wifi
Explanation:
In the lesson, you learned about the various uses of computers in manufacturing, from design to the control of manufacturing processes. Write a short report about the advantages and main features of CAD. Discuss the main applications of CAM as well.
Answers
Some of the main features of Computer Aided Design:
(CAD) are:
Glassworking, woodturning, metallurgy and spinning, and graphical refinement of the entire production technique are some of the key uses of the Computer Aided Manufacturing (CAM) system. CAM systems are used to create solids of rotation, flat surfaces, and screw threads.
What is CAD?The use of computers to help in the development, alteration, analysis, or optimization of a design is known as computer-aided design.
This program is used to boost the designer's efficiency, improve design quality, improve communication through documentation, and develop a database for production.
Learn more about Computer Aided Manufacturing:
https://brainly.com/question/14039774
#SPJ1
Which of the following data structures can erase from its beginning or its end in O(1) time?
Answers
Where all "the following" i can help you but you said which of the folllowing and ther no picture or anything?
The stack data structure can erase from its beginning or its end in O(1) time.
The O(1) complexity is an illustration of getting operations done in a constant time.
Stack data structure uses the push and pop operations for inserting and deleting items in a linear or constant time.
This implies that, inserting an item into a stack happens in O(1) time, and also; removing an item from the stack, irrespective of the item location (beginning, end, or in between) happens in O(1) time.
Read more about data structure at:
https://brainly.com/question/21287881
What are the values of a and b after the for loop finishes? int a = 10, b = 3, t; for (int i=1; i<=6; i++) tha; a = i + b; b = t - i; (1 point) A.a = 6 and b = 13 B.a = 6 and b = 7 C.a = 13 and b = 0 D.a = 6 and b = 0 E.a = 0 and b = 13
Answers
At the end of the for loop, the values of a and b will be 6 and 0, respectively. The correct answer is D. a = 6 and b = 0.
Before the for loop starts, a = 10 and b = 3. The for loop will run 6 times, and each time it will execute the following code:
t = a;
a = i + b;
b = t - i;
Let's see what happens to the values of a and b after each iteration:
Iteration 1:
t = 10;
a = 1 + 3 = 4;
b = 10 - 1 = 9;
Iteration 2:
t = 4;
a = 2 + 9 = 11;
b = 4 - 2 = 2;
Iteration 3:
t = 11;
a = 3 + 2 = 5;
b = 11 - 3 = 8;
Iteration 4:
t = 5;
a = 4 + 8 = 12;
b = 5 - 4 = 1;
Iteration 5:
t = 12;
a = 5 + 1 = 6;
b = 12 - 5 = 7;
Iteration 6:
t = 6;
a = 6 + 7 = 13;
b = 6 - 6 = 0;
So after the for loop finishes, a = 13 and b = 0.
Therefore, the correct answer is D. a = 6 and b = 0.
Learn more about loops: https://brainly.com/question/26568485
#SPJ11
State Whether the given statement are TRUE OR FALSE. 13X1=13
23] The result of any condition is true ,false or unknown.
24] The WHILE and UNTIL can be placed at the end of DO….LOOP.
25] When a program contains a loop , it means it can repeat statements only
once.
26] The first version of visual basic was VB. Net
`27] The name of the form 1 dialog box which appears by default can be
changed .
28] The Error window opens when there are some coding mistakes.
29] E.F Codd proposed the first type of relational database model.
30] there is a way to rename the tables in Access.
31] One row will have one unit of complete information .
32] The text can be only numerical
33] currencies cannot be stored in Access
34] A number of list items go within the <ul> tags give right
Answers
Answer:
true
Explanation:
because everyone know that 13x1=13
You are concerned that there are connectivity problems between your location and your hosted servers. Which command will display the route that packets take from one location to the host being attempted
Answers
To display the route that packets take from one location to a host being attempted, you can use the "traceroute" command. Traceroute is a network diagnostic tool that allows you to trace the path of network packets from your location to a specific destination host.
In most operating systems, including Windows, macOS, and Linux, the traceroute command is available. The syntax of the command may slightly vary across different systems, but the basic usage remains the same.
For example, in a Windows Command Prompt or PowerShell, you can use the "tracert" command followed by the IP address or hostname of the destination host. The command would look like this:
```
tracert <destination_host>
```
Similarly, in a macOS or Linux terminal, you can use the "traceroute" command followed by the IP address or hostname of the destination host:
```
traceroute <destination_host>
```
Running the traceroute command will provide you with a list of intermediate network devices (routers) and their IP addresses along the path to the destination host. This information helps you identify any connectivity issues or network bottlenecks between your location and the hosted servers.
By analyzing the output of the traceroute command, you can determine the network latency, packet loss, and the specific hops where connectivity problems may be occurring.
Learn more about "traceroute" command here:
https://brainly.com/question/28333920
#SPJ11
Explain the "no read-up, no write-down approach." (Bell-LaPadula model)
Answers
The Bell-LaPadula policy is provided through a computer system. The virus spreads if the virus is deployed on the system at a low level.
What is a computer virus?When run, a computer virus is a sort of computer program that repeats itself by altering other computer programs and inserting its own code. If the replication is successful, the afflicted regions are considered to be "infected" with a computer virus, a term inherited from biological viruses.
The computer may act weirdly, glitch, or operate abnormally slowly if you have an infection.
Therefore, The Bell-LaPadula policy is provided through a computer system. The virus spreads if the virus is deployed on the system at a low level.
Learn more about computer on:
https://brainly.com/question/13805692
#SPJ1
If something is sustainable, then what is it?
Enduring
Brittle
Expensive
Short-term
Answers
Which of the following described a global network connecting billions of computers and other
devices?
A) WiFi
B
ISP
C
World Wide Web
D
Internet
Answers
Stephen is slowing down as he approaches a red light. He is looking in his mirror to switch lanes and misjudges how close Keisha's car is, rear-ending her car. When
they get out and assess the damage, Keisha's bumper will need to be replaced. What type(s) of insurance could Stephen use to cover this accident? Explain.
Krisha had some discomfort in her neck at the time of the accident but thought it was minor and would go away. A week or so after the accident, Keisha finally goes
What t) of insurance could Keisha use to cover this accident?
Answers
The type of insurance that Stephen could use to cover this accident is known as liability coverage
What t) of insurance could Keisha use to cover this accident?The insurance that Keisha could use to cover this accident is personal injury protection.
In the case above, The type of insurance that Stephen could use to cover this accident is known as liability coverage as damage was one to his property.
Learn more about Property Damage from
https://brainly.com/question/27587802
#SPJ1
When downloading a large file from the iniernet Alexis interrupted the download by closing ber computer, Later that evening she resumed tbe download and noticed that the file was bowniosding at a constant rate of change. 3 minutes since resaming the download 7440 total MegaBytes (MB) of the file had been downloaded and 6 mintues siace resuming the download 13920 total MesaBytes (MB) of the file had been donstoaded A. From 3 to 6 minutes after she resumed downlooding, how many minutcs elapod? misules b. From 3 to 6 minutes after she resumed downloading, how many total MB of the file were dowaloaded? MB c. What is the consuant rate at which the file downloads? MegaByes per minule d. If the file continues downloadisg for an additional 1.5 minner (after tbe 6 mimutes afts she feramed downloading). 4. How many aditipeal MB of the flie were downloaded? MIB 14. What is the new total number of MB of the file Bhat have been downloaded? MEI
Answers
a) From 3 to 6 minutes after resuming the download, 3 minutes elapsed.
b) From 3 to 6 minutes after resuming the download, 6,480 MB of the file were downloaded.
c) The constant rate at which the file downloads is 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, an additional 3,240 MB of the file will be downloaded.
e) The new total number of MB of the file that have been downloaded will be 17,160 MB.
a) From the given information, we can determine the time elapsed by subtracting the starting time (3 minutes) from the ending time (6 minutes), resulting in 3 minutes.
b) To calculate the total MB downloaded, we subtract the initial downloaded amount (7,440 MB) from the final downloaded amount (13,920 MB). Therefore, 13,920 MB - 7,440 MB = 6,480 MB were downloaded from 3 to 6 minutes after resuming the download.
c) The constant rate at which the file downloads can be found by dividing the total MB downloaded (6,480 MB) by the elapsed time (3 minutes). Therefore, 6,480 MB / 3 minutes = 2,160 MB per minute.
d) If the file continues downloading for an additional 1.5 minutes, we can calculate the additional MB downloaded by multiplying the constant rate of download (2,160 MB per minute) by the additional time (1.5 minutes). Hence, 2,160 MB per minute * 1.5 minutes = 3,240 MB.
e) The new total number of MB of the file that have been downloaded can be found by adding the initial downloaded amount (7,440 MB), the MB downloaded from 3 to 6 minutes (6,480 MB), and the additional MB downloaded (3,240 MB). Thus, 7,440 MB + 6,480 MB + 3,240 MB = 17,160 MB.
In summary, Alexis resumed the download and observed a constant rate of download. By analyzing the given information, we determined the time elapsed, the total MB downloaded, the rate of download, the additional MB downloaded, and the new total number of MB downloaded. These calculations provide a clear understanding of the file download progress.
Learn more about constant rate
brainly.com/question/32636092
#SPJ11