Information security attacks may leave the organization disabled as they disrupt the working of an entire organizational network. This type of attack affects the processes of the organization by causing degradation in the quality of services, inability to meet service availability requirements, and decrease in staff efficiency and productivity. Which of the following statements is an example of which category of impact of information security attacks?
Answers
The statement "decrease in staff efficiency and productivity" is an example of which category of impact of information security attacks is an availability impact.
The statement "decrease in staff efficiency and productivity" is an example of which category of impact of information security attacks .Information security attacks can harm an organization in several ways. When these attacks occur, the organization may be disabled as they disrupt the operations of an entire organizational network. Information security attacks have a variety of consequences, including degradation in the quality of services, inability to meet service availability requirements, and reduction in staff efficiency and productivity. The impacts of these types of attacks are categorized as follows:
Confidentiality: This impact is when the confidentiality of data is breached. Confidentiality is the assurance that data is secure and cannot be accessed by unauthorized personnel. When the confidentiality of data is breached, sensitive information is exposed.
Integrity: This category of impact occurs when the data's integrity is compromised. Data integrity is the assurance that data is accurate, complete, and reliable. Data can be modified, deleted, or stolen, making it impossible to rely on.
Availability: Information security attacks may result in a decrease in system availability, making it impossible for users to access the system. This type of impact affects the processes of the organization by causing degradation in the quality of services, inability to meet service availability requirements, and a decrease in staff efficiency and productivity.
To know more about productivity visit:
brainly.com/question/30333196
#SPJ11
Related Questions
Naseer has inserted an image into his document but needs the image to appear on its own line.
Which option should he choose?
Top and Bottom
Tight
Through
In front of text
Answers
Assume a 4KB 2-way set-associative cache with a block size of 16 bytes and physical address of 32 bits.
- How many sets are there in the cache?
- How many bits are used for index, tag, and offset, respectively?
Answers
Thus, there are 128 sets in the cache, and the number of bits used for index, tag, and offset are 7, 21, and 4, respectively.
In a 4KB 2-way set-associative cache with a block size of 16 bytes and a physical address of 32 bits:
1. To calculate the number of sets in the cache, first find the total number of blocks in the cache. The cache size is 4KB, which is equal to 4 * 1024 = 4096 bytes.
Since each block has a size of 16 bytes, the total number of blocks is 4096 / 16 = 256. As it's a 2-way set-associative cache, we divide the total number of blocks by 2, which gives us 256 / 2 = 128 sets in the cache.
2. To determine the number of bits used for index, tag, and offset:
- Offset: Since each block is 16 bytes, we need 4 bits to represent the offset (2^4 = 16).
- Index: As there are 128 sets, we need 7 bits for the index (2^7 = 128).
- Tag: The physical address is 32 bits, and we've already used 4 bits for offset and 7 bits for index, so the remaining bits for the tag are 32 - 4 - 7 = 21 bits.
In summary, there are 128 sets in the cache, and the number of bits used for index, tag, and offset are 7, 21, and 4, respectively.
Know more about the set-associative cache
https://brainly.com/question/23793995
#SPJ11
which of the following takes a dict of dicts or a dict of array-like sequences and returns a dataframe? question 2 options: dataframe.from items dataframe.from records dataframe.from dict all of the above
Answers
a) DataFrame.from_items returns a DataFrame from a dict of dicts or a dict of array-like sequences.
What is a DataFrame?Similar to a spreadsheet, a DataFrame is a data structure that organizes data into a two-dimensional table with rows and columns. Because of their adaptability and ease of use, DataFrames are one of the most widely used data structures in modern data analytics.
The name and data type of each column are specified in a blueprint known as a schema that is contained within each DataFrame. Spark DataFrames can contain both Spark-specific data types like StructType and universal data types like StringType and IntegerType. The DataFrame stores null values for values that are either missing or incomplete.
A DataFrame can be compared to a spreadsheet with named columns for simplicity's sake. A DataFrame, on the other hand, can span thousands of computers, whereas a spreadsheet only exists on one computer in one specific location.
To learn more about DataFrame visit :
https://brainly.com/question/28190273
#SPJ4
Complete question-
Which of the following takes a dict of dicts or a dict of array-like sequences and returns a DataFrame?
a) DataFrame.from_items
b) DataFrame.from_records
c) DataFrame.from_dict
d) All of the mentioned
Mood is established by not just images but also sounds, music, and even movements.
A.
True
B.
False
Answers
Answer:
true
Explanation:
Please i relly need this!

Answers
Answer:
Kindly check explanation
Explanation:
The question requires taking the measurements of the lumber ; however the lumber isn't displayed here ;
Since the formula has been provided for obtaining the Board foot :
A measuring device could be a measuring tape :
If the hypothetical dimensions obtained goes thus :
Thickness, T = 2 ft
Length, L = 12 fts
Width, W = 8 fts
Board foot = (T * W * L) / 12
Board foot = (2 * 12 * 8) / 12
Board foot = 192 / 12
Board foot = 16
Recall: this is just an hypothetical answer, all you need to do is take the measurementof board and insert into the formula.
Please its argent and I will give you BRAINLIEST ANSWER 6. How would you confirm that a colourless liquid given to you is pure water?
Answers
Answer:
Evaporate the colourless liquid on a low flame. If no residue is left and boiling exactly at 100 ºC then it is pure water otherwise not.
Explanation:
The capability of moving a completed programming solution easily from one type of computer to another is known as ________.
Answers
Answer:
The functionality of transferring finished programming answer without difficulty from one form of laptop to some other is referred to as Portability. Portability is a function of laptop programming that allows you to offer the benefit that if we make a programming answer for one device it could be used for numerous structures also.
Explanation:
Hope this helps :)
What type of cost will reduce with the introduction of a CAM system in a manufacturing plant?
A.
capital cost
B.
fixed cost
C.
labor cost
D.
material cost
Answers
Answer:
a.capital cost
Explanation:
because capital cost is to reduce introduction of CAM system
Create at least 5 Functional UPDATE Statements for the Homework Database Each of the UPDATE Statements must be preceded by a SELECT Statement that lists the rows/tuples that are going to be updated ba
Answers
Here are five functional UPDATE statements for the Homework Database:
1. UPDATE Students SET grade = 'A' WHERE grade = 'B';
2. UPDATE Assignments SET status = 'Completed' WHERE deadline < NOW();
3. UPDATE Teachers SET salary = salary * 1.1 WHERE experience > 5;
4. UPDATE Courses SET capacity = capacity - 1 WHERE course_id = 'C001';
5. UPDATE Grades SET score = score + 5 WHERE student_id = 'S001';
To update rows/tuples in the Homework Database, we can use the UPDATE statement along with a preceding SELECT statement to identify the specific rows that need to be updated based on certain conditions.
In the first UPDATE statement, we are changing the grade of students who currently have a grade of 'B' to 'A'. This could be used to reflect improved performance.
The second UPDATE statement updates the status of assignments to 'Completed' for those that have passed their deadline. This can be useful for tracking overdue assignments.
The third UPDATE statement increases the salary of teachers by 10% for those with more than five years of experience. This allows for salary adjustments based on tenure.
The fourth UPDATE statement reduces the capacity of a course by one when the course ID matches 'C001'. This can be helpful for managing course enrollment.
Finally, the fifth UPDATE statement increases the score of a student by 5 when the student ID matches 'S001'. This could be used to award extra credit.
Learn more about UPDATE statements
brainly.com/question/30391230
#SPJ11
How does taking notes improve academic success? Check all that apply.
It helps you retain information.
It gives you all the answers to the tests.
It allows you to review information for tests.
It shows you connections between ideas.
It helps you grasp overall concepts.
It makes you study longer for tests.
Answers
Answer:
Taking notes helps you improve in your academic success because 1. it It helps you retain information , 2. It allows you to review information got test, 3.It helps you grasp overall concepts. These are all correct answers why taking notes can improve and get better for your academic success, also it is missing some. 4.Taking good notes in class is an important part of academic success in college. 5Actively taking notes during class can help you focus and better understand main concepts. 6. Good note-taking will improve your active listening, comprehension of material, and retention.
Answer:
The answer is A C D E i just took it on edge trust me
What do computers use to represent on and off? 0 and 1 1 and 2 RGB Megabyte
Answers
Describe a situation in which you would want to use integer division in a program. Then, write the line of code that would use integer division.
Answers
The description of a situation in which you would want to use integer division in a program is that they would give you the exact answer you want when performing addition, division, etc, and is more reliable than using floating point math.
What is Integer Division?This refers to the term that is used to describe the operator divides two numbers and returns a result and its symbol is %
The Program that uses an integer division is given below:
int a = 25;
int b = 5;
int c = a / b ;
System. out. println(c);
Read more about integer division here:
https://brainly.com/question/28487752
#SPJ1
Will give Brainlets: I am creating a resumé in computers, the cover letter we are allowed to use a fake job. What are some ideas for a fake job I can use that are not real companies or businesses? We are not having a job interview with these cover letters. These are for practice. Please include what the fake job does.
Answers
having a legitimate reason for approaching someone to ask for sensitive information is called what?
Answers
FILL IN THE BLANK. one task of the ____ layer in a lan is to handle error detection using a crc.
Answers
One task of the data link layer in a lan is to handle error detection using a crc.
When data is transmitted between devices in a LAN, it is broken down into smaller frames at the data link layer. Each frame contains a header, data, and a trailer. The trailer includes a CRC, which is a mathematical calculation of the data in the frame.
When the receiving device receives the frame, it calculates its own CRC and compares it to the CRC in the trailer. If the two CRCs match, the data is assumed to be error-free and is passed up to the next layer. However, if the CRCs do not match, an error is assumed to have occurred during transmission and the frame is discarded.
Learn more about data link: https://brainly.com/question/31391230
#SPJ11
You receive an email from your school's head of IT. There is a concern for a potential hack to the school's servers. IT knows some accounts have been compromised, with their login and passwords overwritten by the hackers. They need to reset the accounts that the hackers have changed the passwords on. However, they don't have access to the passwords directly, and the change records were corrupted by the attack. They need students and staff to confirm their passwords by logging into a secure site. If the login fails, they'll know your account was compromised and reset your account immediately.
a.) This could be a phishing attempt. If the situation is as described in the email, this is also serious, but the method suggested is the same methods used by social hackers. Look up your IT Departments phone number and call them about the email.
b.) This is a serious issue, and the email came from the head of IT. The site also shows that it's secure. The longer it takes to reset accounts, the longer the hackers will have access to your account. Follow the instructions in the email from the head of IT.
Answers
Answer:
a.) This could be a phishing attempt. If the situation is as described in the email, this is also serious, but the method suggested is the same methods used by social hackers. Look up your IT Departments; phone number and call them about the email.
Explanation:
This makes sense because many people do these types of scams to trick people into logging into their accounts and actually hack them from there, I actually got an email like this last week to my iCloud address. Make sure that the email actually came from the IT department by checking the domain the email comes from, and call the IT department to make sure.
Hope this helps!
a strip of film- or digital images- produced by a single continuous run of the camera that is the basic unit with which the editor works is called a ...
Answers
The fundamental unit with which the editor works is a shot, which is a strip of film or digital images created by a single continuous run of the camera.
What is editor?
An editor is a person responsible for revising, correcting, and preparing written material for publication. They may work with text, images, audio, or video, depending on the type of publication. Editors are responsible for ensuring the accuracy, quality, and completeness of the material before publication. They may review and edit the material for grammar, punctuation, clarity, and readability. They may also suggest changes to the material to make it more effective or interesting. An editor must also be familiar with the company’s style guide and make sure the material follows it. They must also be aware of the company’s copyright policies to ensure that the material does not infringe on any other person’s rights. Editors often work with authors to help them craft their stories and make them more meaningful. Finally, when the material is ready, the editor is responsible for submitting it to the publisher or other outlet.
To learn more about editor
https://brainly.com/question/28423864
#SPJ4
You administer your company's 100BaseTX Ethernet network. TCP/IP is the networking protocol used on the network. You want the routers on the network to send you notices when they have exceeded specified performance thresholds. Which protocol should you use to enable the routers to send the notices
Answers
Complete Question:
You administer your company's 100BaseTX Ethernet network. TCP/IP is the networking protocol used on the network. You want the routers on the network to send you notices when they have exceeded specified performance thresholds. Which protocol should you use to enable the routers to send the notices?
Group of answer choices
A. ARP
B. SMTP
C. SNMP
D. Telnet
Answer:
C. SNMP.
Explanation:
In this scenario, you administer your company's 100BaseTX Ethernet network. TCP/IP is the networking protocol used on the network. Also, you want the routers on the network to send you notices when they have exceeded specified performance thresholds. Hence, you should use the SNMP to enable the routers to send the notices.
SNMP is an acronym for simple network management protocol, which is a standardized application-layer protocol that is used for monitoring and organizing management information about network devices on either a wide area network (WAN) or local area network (LAN).
Basically, the SNMP helps to provide a common language for network devices such as switches, routers, printers, servers etc to share information with a network management system.
A simple network management protocol (SNMP) is part of the Transmission Control Protocol and Internet Protocol (TCP⁄IP) suite.
if ordertotal has a value of 50 and quantity has a value of 10, what is the value of discount after these statements are executed? if (quantity
Answers
In order to answer this question, we need to know what the statements following "if (quantity" are. Without knowing the full condition and subsequent action in the if statement, it is not possible to determine the value of discount.
Please provide the full code for us to accurately answer your question.
In general, if statements are used to execute a specific action or set of actions when a certain condition is met. The condition is typically a comparison of two values, and the action is a statement or set of statements that are executed when the condition is true.
For example, if we have the following if statement:
if (quantity > 5) {
discount = ordertotal * 0.1;
}
This would set the value of discount to 10% of the ordertotal if the quantity is greater than 5. However, without knowing the full if statement in your question, we cannot accurately determine the value of discount.
Learn more about programming: https://brainly.com/question/26134656
#SPJ11
Write a program to display the series 100 ,98,96,94.....50.(use DO..WHILE statement)
Answers
Answer:
Explanation:
a = 100
while a != 50:
print(a)
a-=2
State a conceptualized service that can be easily created for students. With product specification.
DO FAST AND NEED CORRECT ANSWER
** need correct answer **
no plagrism
Answers
A conceptualized service that can be easily created for students is an online tutoring platform. This service would provide personalized and interactive tutoring sessions to students of various subjects and grade levels.
Product Specifications:
1. User-friendly interface: The online tutoring platform should have a simple and intuitive interface that is easy for students to navigate.
2. Live video sessions: The platform should allow for live video sessions between students and tutors, enabling real-time communication and interaction.
3. Subject-specific tutors: The service should have a pool of qualified tutors specialized in different subjects to cater to the specific needs of students.
4. Scheduling flexibility: The platform should provide options for students to schedule tutoring sessions at their convenience.
5. Progress tracking: The service should have a feature to track students' progress and provide regular feedback to both students and parents/guardians.
6. Resource library: The platform should offer a comprehensive resource library with study materials, practice tests, and educational resources to supplement the tutoring sessions.
7. Mobile compatibility: The service should be accessible through mobile devices, allowing students to receive tutoring on-the-go.
8. Affordable pricing options: The platform should offer flexible pricing options to accommodate students with different budgets.
9. Secure payment system: The service should have a secure payment system for hassle-free transactions.
10. Customer support: The platform should provide responsive customer support to address any queries or concerns of students and their parents/guardians.
To know more about conceptualized service refer for :
https://brainly.com/question/28030134
#SPJ11
What is the best CPU you can put inside a Dell Precision T3500?
And what would be the best graphics card you could put with this CPU?
Answers
Answer:
Whatever fits
Explanation:
If an intel i9 or a Ryzen 9 fits, use that. 3090's are very big, so try adding a 3060-3080.
Hope this helps!
encryption and decryption technology are example of safeguards? physical, administrative, technical network
Answers
Encryption and decryption technology are an example of technical safeguards. Technical safeguards are measures to protect data stored in an information system from unauthorized access.
Decryption is the process of converting encrypted data back to its original form, while encryption is the process of converting plain text into cipher text that is unreadable by unauthorized parties. Technical safeguards also include firewalls, intrusion detection systems, and access controls. Technical safeguards are just one aspect of a comprehensive information security program. Physical, administrative, and network safeguards are also important to consider in ensuring that data is protected from unauthorized access.
Encryption is, at its most fundamental level, the process of scrambling data or information using mathematical models in such a way that only those parties who possess the key to unscramble it can access it.
Know more about Encryption, here:
https://brainly.com/question/30225557
#SPJ11
A screw has 4 threads per centimeter and a circumference of 2 centimeters. What is the mechanical advantage of the screw? 2 4 6 8
Answers
Answer:
M.A = 8
Explanation:
Given the following data;
Circumference = 2cm
Number of threads = 4
To find the mechanical advantage (M.A);
\( Mechanical \; advantage = \frac {Circumference}{Pitch} \)
But, \( Pitch = \frac {1}{number \; of \; threads} \)
\( Pitch = \frac {1}{4} \)
Pitch = 0.25
Substituting the values into the equation, we have;
\( M.A = \frac {2}{0.25} \)
M.A = 8
Therefore, the mechanical advantage of the screw is 8.
Answer:A screw has 4 threads per centimeter and a circumference of 2 centimeters. What is the mechanical advantage of the screw?
2
4
6
8 THIS IS THE CORRECT ANSWER
Explanation:
Edge 2021 Test Correct
Which term describes how content in an array is accessed?
brackets
string
subscript
class
Answers
Answer:
the answer is subscript
Explanation:
I need help I did not mean to do that to my computer

Answers
Answer:
Man...I don't think you can fix that yourself..
Play to end-
Back to beginning
Answer the following questions about representing repetition algorithmically with programming
1) In order for a repetition to be reproduced unambiguously, what three attributes are needed to convey
the proper instructions?
2) How are these three attributes conveyed in the music notation above?
3) Find and record a set of instructions containing a repetition clause (eg, instructions on a shampoo
bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader
infer them?
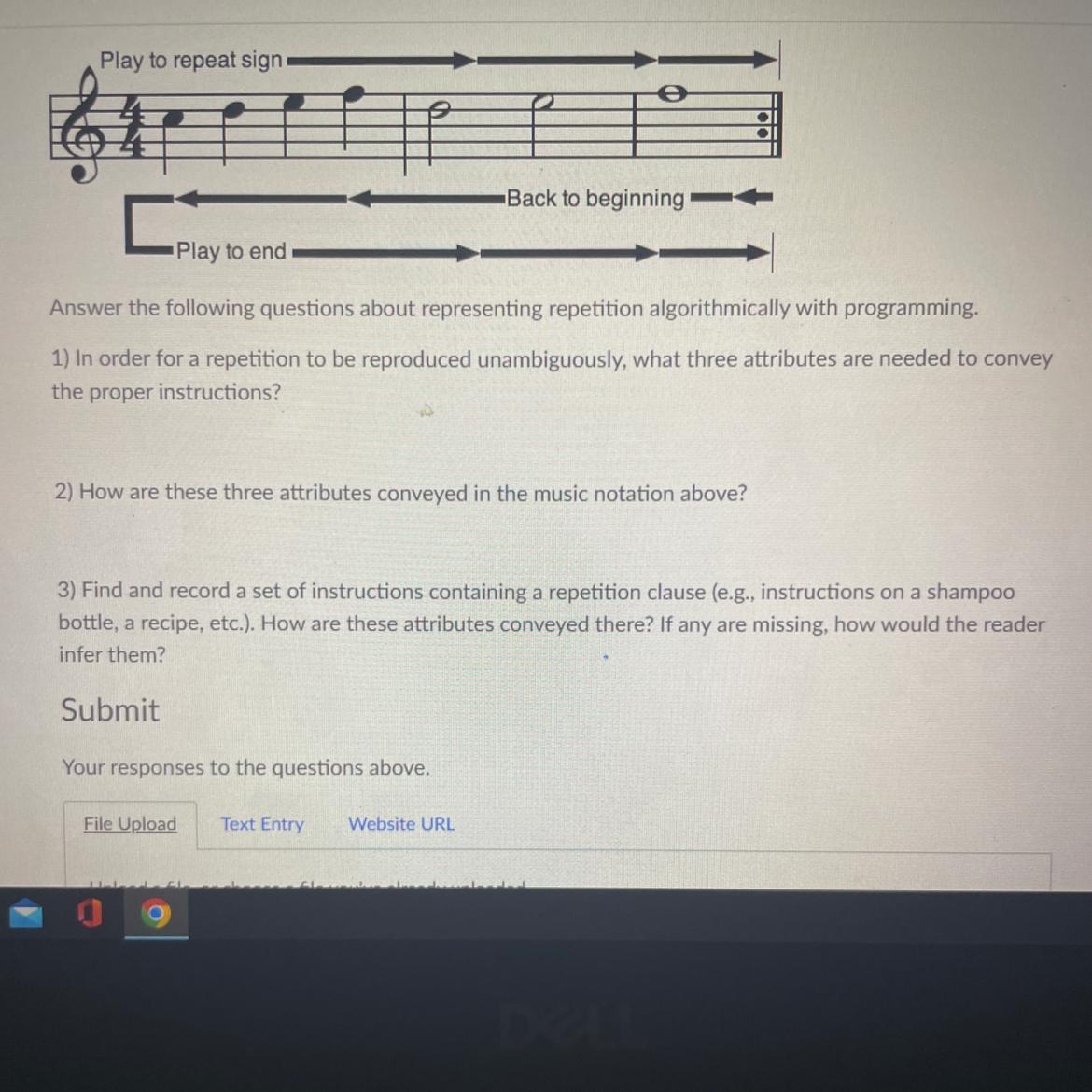
Answers
There must be a starting point, a point where the code ends, and it restarts back to the beginning.
2) How are these three attributes conveyed in the music notation above?
The starting point is the beginning of the phrase, the point of where it gets sent back is the is represented by the colon symbol at the end, and thus it starts again at the beginning of the phrase.
3) Find and record a set of instructions containing a repetition clause (e.g., instructions on a shampoo bottle, a recipe, etc.). How are these attributes conveyed there? If any are missing, how would the reader infer them?
How to download the McDelivery app from a McDonalds bag
- Download the uber eats app
- Select “McDonald’s”
- Order your favorite foods
In this set of instructions, it has a start where you download or open up the uber eats app, selecting the “McDonalds” option for delivery is part of the start or the middle part, and the point of repetition where the instructions can be a repeated is the ordering the food. It would’ve just been in a constant loop afterwards because the first two instructions have already been pre-completed.
hope this helps :)
In python please!! Write the definition of a function named countPos that needs integer values from standard input until there are none left and returns the number that are positive. The function must not use a loop of any kind.
Answers
Answer:
Explanation:
The following code is written in Python it doesn't use any loops, instead it uses a recursive function in order to continue asking the user for the inputs and count the number of positive values. If anything other than a number is passed it automatically ends the program.
def countPos(number=input("Enter number: "), counter=0):
try:
number = int(number)
if number > 0:
counter += 1
newNumber = input("Enter number: ")
return countPos(newNumber, counter)
else:
newNumber = input("Enter number: ")
return countPos(newNumber, counter)
except:
print(counter)
print("Program Finished")
countPos()

a communications engineer notices that every time it rains the signal becomes very degraded. which layer of the osi model is the engineer most likely troubleshooting?
Answers
A communications engineer is likely debugging the physical layer of the OSI model when they notice that the signal is significantly reduced whenever it rains.
What is the physical layer of the OSI model?Hardware security is provided via the Physical Layer (L1), which is the lowest layer in the OSI model.
By identifying the hardware used for the data transfer, this layer manages the actual physical connection between the devices.
Hardware components, cables, wiring, frequencies, and pulses are all defined by Layer 1.
The OSI model's physical layer is the bottom layer.
This layer regulates the transmission and reception of raw, unstructured bit-stream data through physical media.
The network's physical, optical, and electrical components are included in this layer.
When a communications engineer detects that the signal is severely weakened whenever it rains, the engineer is probably troubleshooting the physical layer of the OSI model.
Therefore, a communications engineer is likely debugging the physical layer of the OSI model when they notice that the signal is significantly reduced whenever it rains.
Know more about the physical layer of the OSI model here:
https://brainly.com/question/30192762
#SPJ4
Match each definition with the term it describes. A(n) ______ provides identification and addressing information for computers and devices on a network. A(n) ________ is a network that covers an area of less than a mile. The Internet is an example of a(n) ______.
Answers
Answer:
IP address, LAN, WAN
Explanation:
Answer:
Sentence 1: IP Address
Sentence 2: LAN
Sentence 3: WAN
Explanation:
Edge 2022