is the most widely used language for wrigint system software because it combines the power of a high level language with the ability to circumvent
Answers
The most widely used language for writing system software is C because it combines the power of a high-level language with the ability to circumvent certain restrictions.
1. C is a high-level programming language, meaning it is easier for humans to read and write compared to low-level languages like Assembly.
2. Despite being a high-level language, C allows programmers to access low-level features, such as memory manipulation and hardware control.
3. This combination of high-level language features and low-level capabilities makes C ideal for writing system software, as it provides both ease of use and the ability to fine-tune performance and control hardware components.
4. System software, such as operating systems and compilers, often require close interaction with hardware components, making C a suitable choice for their development.
More On C Language: https://brainly.com/question/26535599
#SPJ11
Related Questions
1.03!! need major help!!
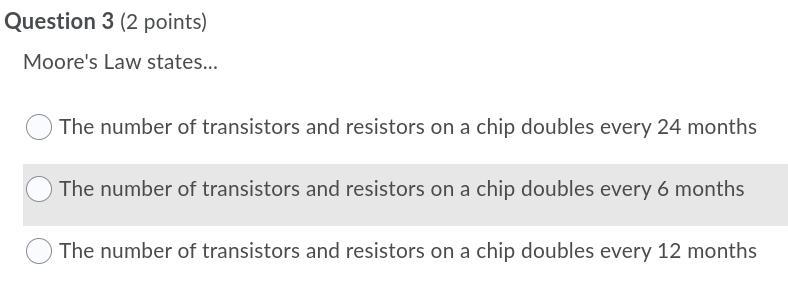
Answers
Answer: the answer is A
Explanation:
Moore's law, prediction made by American engineer Gordon Moore in 1965 that the number of transistors per silicon chip doubles every year. ... Moore observed that the number of transistors on a computer chip was doubling about every 18–24 months.
Who must yeild at T-intersections?
Answers
Answer: the driver on the street
Explanation:
what is the easiest way not to get distracted from doing my school work?
Answers
Answer:
really you want the answer
Answer:
Find a good quiet place, Turn off your phone. put it away, wear comfy clothes, Lock your door. Dont eat, But drink water
Explanation:
Hope this helped!
pls pls pls helppp!! I NEED SOMEONE WHO IS A PRO AT COMPUTER SCIENCE CODING LIKE PYTHON AND STUFF TO CREATE A ZOOM AND HELP ME WITH SOMETHING!! :))) PLEASEEE
Answers
Answer:
?
Explanation:
how does python show that commands belong inside a python structure?
Answers
Python show that commands belong inside a Python structure by using indentation to define the code blocks.
What is Python?Python can be defined as a high-level programming language that is designed and developed to build websites and software applications, especially through the use of dynamic commands (semantics) and data structures.
In Computer programming, Python show that commands belong inside a Python structure by using indentation to define the code blocks.
Read more on Python here: https://brainly.com/question/26497128
#SPJ1
What are 2 ways to send a message to your client when signed in as an accountant user?.
Answers
Answer:
The use of Ask client and request are 2 ways to send a message to your client when signed in as an accountant user.
Isabela wants to add an image to her presentation. Which tab should she use?
Answers
Answer:Insert
Explanation:
Edg. 2021
1.Which one of the following buttons returns a window to its original size?
A.
Maximize button
B.
Close button
C.
Minimize button
D.
Restore button
2.What is the name used to identify the pointer that is controlled by the mouse?
A.
Alert
B.
Boot
C.
Cursor
D.
Drag
3.What is the process called when information from your computer is transferred to another computer?
A.
Upload
B.
Copy
C.
Transfer
D.
Download
4.Which one of the following indicates a file's format?
A.
Icon
B.
Extension
C.
Platform
D.
Driver
5.What term refers to a single directory that can hold a collection of files? A. Platform B. Folder C. Extension D. Icon
6.6.
What term refers to a single directory that can hold a collection of files?
A.
Platform
B.
Folder
C.
Extension
D.
Icon
7.What is the common term used to describe a single computer document?
A.
Driver
B.
File
C.
Screenshot
D.
Icon
8.
What is the main piece of computer software on which every other piece of software relies?
A.
Desktop
B.
Operating system
C.
Database
D.
Driver
BUT DOES ANYONE HAVE AL 20 ANSWERSSSSS I'LL MARK YOU THE BRAINLIEST PLEASEEEE HELPPPP
Answers
Answer:
1. D
2.C
3. D
4. A
5. B
6.B
7.B or D
8.C
Explanation:
Not 100% sure about 3,4, 8
Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time. True or False
Answers
Answer:
true
Explanation:
The statement "Since you have to be cautious about deleting a slide, PowerPoint only allows you to delete one slide at a time" is true.
What is a PowerPoint presentation?G slides can be used to create a PowerPoint presentation. By clicking the large sign at the top left of your screen, you can log in and create a presentation if you have an account. I use slides to create my presentations because it is so simple to use.
You ought to investigate it for yourself. Since it is entertaining, students should enjoy both watching and participating in such presentations. With the right approach, it can assist schools in meeting the needs of all students.
When using PowerPoint, you can project color, images, and video for the visual mode to present information in a variety of ways (a multimodal approach).
Therefore, the statement is true.
To learn more about PowerPoint presentations, refer to the below link:
https://brainly.com/question/16779032
#SPJ2
Tilde is working on a contract with the external penetration testing consultants. She does not want any executives to receive spear-phishing emails. Which rule of engagement would cover this limitation?
A. Scope
B. Exploitation
C. Targets
D. Limitations and exclusions
Answers
The limitation Tilde wants to impose on not having any executives receive spear-phishing emails would be covered under the "Limitations and exclusions" rule of engagement.
Rule of engagement documents in a contract with external penetration testing consultants outline the terms and conditions, rules, and boundaries for the engagement. The "Limitations and exclusions" section specifically lists any constraints or restrictions that need to be followed during the testing process.In this case, Tilde's requirement of not targeting executives with spear-phishing emails is a limitation that falls under the "Limitations and exclusions" rule of engagement. By clearly stating this limitation, Tilde ensures that the consultants are aware of this restriction and will refrain from executing spear-phishing attacks on executives during the engagement.
learn more about limitation here :
https://brainly.com/question/12207539
#SPJ11
a user wants to quickly format a cell and right-clicks the cell to use the features seen in the image. which excel tool is being used?
Answers
Based on the information provided, the Excel tool being used when a user right-clicks a cell to access formatting features is the "Cell Context Menu" or "Cell Right-Click Menu."
The Cell Context Menu in Excel provides quick access to various formatting options and other cell-related functions.
When a user right-clicks on a cell, a context-sensitive menu appears, presenting a range of formatting and manipulation options specific to that cell or cell range.
The image associated with the question may display a snapshot of the Cell Context Menu, showcasing some of the available features.
These features can include options like formatting cell styles, font formatting, alignment settings cell borders and shading, number formatting, and various other formatting and editing options.
The Cell Context Menu is a convenient tool that allows users to quickly access and apply formatting changes without needing to navigate through multiple tabs or menus in the Excel Ribbon.
It provides a streamlined way to modify cell appearance, data representation, and other cell-specific properties.
By utilizing the Cell Context Menu, users can efficiently format cells, customize their appearance, and tailor their content to meet specific presentation and analysis requirements, enhancing the visual clarity and readability of their Excel spreadsheets.
For more questions on Excel
https://brainly.com/question/30886241
Sharing someone else's secrets or embarrassing photos via social media is a form of which type of cyberbullying?
Cyberstalking
Denigration
Outing
Trickery
Answers
Answer:
DenigrationExplanation:
Spreading false or hurtful information about someone with the intention of hurting their reputation or upsetting them constitutes this particular type of cyberbullying. It can involve disclosing private material without the victim's consent, including embarrassing pictures, videos, or other sensitive information. This kind of cyberbullying has the potential to have substantial negative effects on the victim's emotional health and social interactions, both online and off.
To learn more about cyberbullying visit: https://brainly.com/question/24017380
Answer: Outing?
Explanation:
T/F. A subquery in which processing the inner query depends on data from the outer query is called a codependent query.
Answers
False: A subquery in which processing the inner query depends on data from the outer query is called a correlated subquery.
A correlated subquery is a type of subquery in which the inner query depends on data from the outer query. The inner query is evaluated for each row of the outer query, making the two queries codependent on each other. This type of subquery can be useful for filtering or aggregating data based on a specific condition.
The correct term for this type of subquery is a "correlated subquery." A correlated subquery is a subquery that depends on data from the outer query for its execution. Each row of the outer query is evaluated against the inner query, resulting in a more complex and potentially slower process.
To know more about Subquery visit:-
https://brainly.com/question/31540529
#SPJ11
Arturo is a security professional. He is strengthening the security of an information system. His design ensures that if a field should contain a number, the system checks the values that a user enters to make sure that the user actually entered numbers. The design also ensures that only authorized users have the ability to move or delete files. What is Arturo attempting to protect
Answers
Arturo is attempting to protect the database (data) of an information system (IS).
What is an information system?An information system (IS) can be defined as a set of computer systems, that is typically used to collect, store, and process data, as well as the dissemination of information, knowledge, and the distribution of digital products.
In Cybersecurity, there are two (2) main techniques that can be used to check data when inputted in an information system (IS) and these include:
VerificationValidationData validation is a type of check which is primarily performed by a software program (application) to make sure that the data which is entered into an information system (IS) is allowable and sensible.
This ultimately implies that, any data that is not allowed or sensible are rejected and discarded by the computer system.
In conclusion, we can deduce that Arturo is attempting to protect the database (data) of an information system (IS).
Read more on data here: https://brainly.com/question/25885448
Use this option to view your presentation as your audience will see it. a.File menu b.Play button c.Slide Show button d.Tools menu
Answers
Answer:
C. Slide Show Button
Explanation:
Slide show button is used to view the presentation. It is used when presenting the matetial in the form of slides to the audience. You can add various text, images in your slides and also add animation to your slides. In order to view how these slides and animations applied on slides will look and how they will be seen by the audience during presentation, you can use this slideshow option. Slideshow button can be used from quick access toolbar or you can use F5 key to start the slideshow of your presentation or you can select Slide Show view command at the bottom of the PowerPoint window. This is used to start a presentation from the first slide or even from current slide. This is useful in customizing the slides, visualizing and analyzing the slides making changes or adding slides in the presentation.
Answer:
Your answer is C. Slide Show Button.. Hope this helps!
Explanation:
what is the correct java syntax to output the sentence: My dog's name is "dee-dee"?
Answers
Answer:
System.out.println("My dog's name is \"dee-dee\"");
Explanation:
You need to use the backslash to use quotes inside a string.
Write a Python program which accepts a sequence of comma-separated numbers from user and generate a list and a tuple with those numbers.
Sample data : 3, 5, 7, 23Output :List : ['3', ' 5', ' 7', ' 23']Tuple : ('3', ' 5', ' 7', ' 23')
Answers
When you run this program, it will prompt you to enter comma-separated numbers, and then it will display the list and tuple of those numbers.
Hi! I'd be happy to help you with writing a Python program to generate a list and a tuple from comma-separated numbers. Here's a step-by-step explanation:
1. Get user input: Ask the user to enter comma-separated numbers using the `input()` function.
2. Split the input: Use the `split()` method with a comma as the separator to create a list of strings from the user input.
3. Create a tuple: Convert the list of strings into a tuple using the `tuple()` function.
4. Print the list and tuple: Display the list and tuple using the `print()` function.
Here's the code:
python
# Step 1: Get user input
user_input = input("Enter comma-separated numbers: ")
# Step 2: Split the input
number_list = user_input.split(",")
# Step 3: Create a tuple
number_tuple = tuple(number_list)
# Step 4: Print the list and tuple
print("List :", number_list)
print("Tuple:", number_tuple)
When you run this program, it will prompt you to enter comma-separated numbers, and then it will display the list and tuple of those numbers.
To know more about prompt visit:
https://brainly.com/question/8998720
#SPJ11
Write is an ipo cycle? Describe with figure
Answers
Answer:
The input–process–output (IPO) model, or input-process-output pattern, is a widely used approach in systems analysis and software engineering for describing the structure of an information processing program or other process.
PLEASE MARK ME AS BRAINLIEST
WILL MARK BRAINLIEST ONLY ANSWER LAST PART
Create a concept for a new social media service based on new technologies. The service must include functions or features that require using rich media and geolocation or some other location-sharing technology that you have researched.
Submit your plan using both text and visual elements (graphics or drawings).
These are some key points you need to cover in your concept document:
What type of social media service is it?
What is the purpose of the service?
List the functions that the service provides.
List the features that the service provides
What makes the service unique?
Who is the target audience?
What type of layout did you use for the service?
Answers
The concept for a new social media service based on new technologies that i would love to introduce the act of celebrating our social media followers on their birthdays by sending them emails or text offline.
How is the changing technology important for media?The use of technology by mass media users is one that has changed a lot in course of the years and it is still changing.
The use of changing technology or tools can help the media to reach a lot of people and one can get more customers.
Conclusively The use of Email automatic services or messages to target audience such as people between the ages of 18- 50 to celebrate our social media followers can help us to have more customer base as customers often value when they are been celebrated.
Learn more about social media service from
https://brainly.com/question/3653791
Find values of $a$, $b$, and $c$ so that the program: 1 a = # fill in 2 b = # fill in 3 c = # fill in 4 for i in range(a,b,c): 5 print(i, end=' ') outputs: 6 10 14 18 22 26 30 In the boxes below, put your value for $a$ in the first box, your value for $b$ in the middle box, and your value for $c$ in the bottom box.
Answers
Answer:
To find the values of $a$, $b$, and $c$ that satisfy the given program and output, we need to determine the pattern in the printed numbers and derive the corresponding values.
The program uses a for loop with a range that starts at $a$, ends at $b$ (exclusive), and increments by $c$. It then prints each value of $i$ in the range.
From the given output (6 10 14 18 22 26 30), we can observe that the numbers are increasing by 4 in each iteration.
Therefore, we can deduce the values of $a$, $b$, and $c$ as follows:
$a = 6$ (the first printed number)
$b = 31$ (the next number after the last printed number, which is 30, plus the increment of 4)
$c = 4$ (the constant difference between the numbers)
So, the values of $a$, $b$, and $c$ are:
$a = 6$
$b = 31$
$c = 4$
a data mart is a(n): enterprise-wide data warehouse. smaller system built upon file processing technology. data warehouse that is limited in scope. generic on-line shopping site.
Answers
A data mart is a data warehouse that has a limited scope.
Data mart:
A data mart is a structure/access pattern used to retrieve client-facing data in data warehouse systems. While data warehouses have an enterprise-wide depth, data marts only have information for a specific department.
A limited-scope data warehouse whose data are obtained by choosing and summarising data from a data warehouse or via independent extract, transform, and load operations from source data systems. A data mart containing data retrieved from the operational environment that does not have the benefit of a data warehouse.
So, the right answer of the question is C.
To learn more about data mart
https://brainly.com/question/28166657
#SPJ4
what is the purpose of document inspector
Answers
Answer:
to remove any metadata that should be private
Explanation:
Got it right on edg.
How is the aperture speed of three hundred and twentieth of a second displayed on a camera?
Answers
The aperture speed of three hundred and twentieth of a second displayed on a camera is known to be one that the shutter seen in your camera will be open for about three hundred and twentieth of a second of a second.
How is the shutter speed shown?The diameter of the aperture stop is referred to as the "aperture" in photography (sometimes known as the "f-number") (the stop that determines the brightness in a photo at an image point). Contrarily, shutter speed refers to the overall amount of time the camera's shutter is open.
Therefore, Always express shutter speed in seconds or fractions of seconds. For instance, a single number with a quote mark or the letter "s" at the end, such as 1′′ or 1s, is often used to indicate a shutter speed of one second.
Learn more about aperture speed from
https://brainly.com/question/13972212
#SPJ1
The aperture speed of three hundred and twentieth of a second is displayed on a camera as \(f\)/ 320.
What is aperture speed?Aperture speed means how wide the aperture slot is. It's the diameter of the aperture slot. It also intensifies the amount of light that reaches the sensor of the camera.
There are two things displayed on the camera, the aperture speed is written as \(f\) and the number. The other is the shutter speed, which is written as; if the speed is supposed three hundred and twentieth of a second. Then it will be written as 1 / 320.
Therefore, on a camera, the aperture speed is shown as \(f\) / 320, or three hundred and twentieth of a second.
To learn more about aperture speed, refer to the below link:
https://brainly.com/question/28959586
#SPJ1
Where does memory management reside?
Answers
Memory management resides within the kernel of an operating system, which is the core component responsible for managing system resources.
Memory management refers to the process of controlling and coordinating the use of computer memory. It is an essential component of any operating system, including Windows, Linux, macOS, and Android. In most modern operating systems, the kernel is loaded into memory at system boot and remains resident throughout the entire operation of the computer. The kernel provides a range of services, including memory allocation and deallocation, virtual memory management, and memory protection. Memory management ensures that applications have access to the memory they require while preventing conflicts and crashes caused by memory-related issues.
learn more about kernel of an operating system here:
https://brainly.com/question/29977036
#SPJ11
help me pleaseeeeeeeee

Answers
Answer:
Git hub or. Stackoverflow has most of the answers about programming
Explanation:
The average numbers of shares a piece of content receives is known as its:
Answers
Answer:
Amplification.
Explanation:
Social media publishing can be defined as a service that avails end users the ability to create or upload web contents in either textual, audio or video format in order to make them appealing to a target audience.
Thus, these web contents are generally accessed by end users from time to time through the use of various network-based devices. As users access these contents, they're presented with the option of sharing a particular content with several other people a number of times without any form of limitation.
Hence, the average numbers of shares a piece of content receives is known as its amplification. The higher the average numbers of shares a particular content receives, the higher the number of traffic it generates for its publisher.
What command is responsible for shipboard systems and components including weapons systems?
Answers
The command responsible for shipboard systems and components, including weapons systems, is the Combat Systems Command. The Combat Systems Command ensures that these systems are properly functioning, trained personnel are available to operate them, and necessary upgrades are conducted to ensure their effectiveness in combat scenarios.
The Combat Systems Command is responsible for overseeing and managing the operation, maintenance, and readiness of the ship's combat systems and components. This includes weapons systems, sensors, communication systems, command and control systems, and other related equipment.
The Combat Systems Command works in coordination with other commands and departments within the navy or maritime forces to integrate and synchronize the ship's combat capabilities. They collaborate with the ship's commanding officer, weapon officers, combat systems technicians, and other relevant personnel to ensure the ship's combat systems are in a state of readiness.
The Combat Systems Command holds responsibility for shipboard systems and components, including weapons systems. They oversee the operation, maintenance, and readiness of combat systems to ensure the ship's combat capabilities are effective and prepared for various operational scenarios.
To read more about Command, visit:
https://brainly.com/question/31447526
#SPJ11
The Naval Sea Systems Command (NAVSEA) is responsible for shipboard systems and components, including weapons systems, in the United States Navy.
The command responsible for shipboard systems and components including weapons systems is the Naval Sea Systems Command (NAVSEA). Explanation: The United States Naval Sea Systems Command (NAVSEA) is responsible for shipboard systems and components including weapons systems. NAVSEA is the largest of the United States Navy's five systems commands, with an annual budget of nearly $30 billion.
It is a Naval Systems Command responsible for the engineering, construction, and sustainment of the United States Navy's fleet of ships and their systems. It's also in charge of installing new weapons systems and upgrading current ones. NAVSEA is in charge of all naval shipyards, including Portsmouth Naval Shipyard, Puget Sound Naval Shipyard, and Norfolk Naval Shipyard.
Learn more about Command here:
https://brainly.com/question/29627815
#SPJ11
PLEASE HELP I WILL GIVE BRAINLIEST AND 100 POINTS IF U ANSWER COMPLETELY WITHIN 30 MIN
A classmate in your photography class missed several days of class, including the day that the instructor explained the artistic statement. Your classmate asks you to help fill them in so that they can create an artistic statement for an upcoming project. How would you explain this concept and the purpose behind it? What would you tell them to include in their statement? Explain.
Answers
The wat that you explain this concept and the purpose behind it as well as others is that
To create an artistic statement, you should start by thinking about what inspires you as an artist, and what themes or ideas you hope to address in your work. This could be anything from a particular emotion or feeling, to a social or political issue, to a specific artistic style or technique.What is the artistic statement?An artistic statement is a brief description of your artistic goals, inspiration, and vision as an artist. It should outline the themes and ideas that you hope to explore through your work, and explain what you hope to achieve or communicate through your art.
In the above, Once you have a sense of your inspiration and goals, you can start to craft your artistic statement. Some things you might want to include in your statement are:
Therefore, A description of your artistic process, including the mediums and techniques you use to create your work
A discussion of the themes or ideas you hope to explore through your artA statement about your goals as an artist, including what you hope to achieve or communicate through your workA discussion of the influences that have shaped your artistic style, including other artists or movements that have inspired youLearn more about photography from
https://brainly.com/question/13600227
#SPJ1
Answer:
I don't get the other answer :(
Explanation:
Haan creates this table to track his income.
A
1 Month
2 Jan
3 Feb
4 Mar
5 Apr
6 May
7 Jun
8 Jul
9 Aug
10 Sep
11 Oct
12 Nov
13 Dec
14 Year Total
B
Income
$3,800
$3,300
$4,200
$4,900
$2,800
$4,100
$3,000
$4,200
$4,700
$3,600
$5,100
$4,200
Which would give him the total income for the year?
=SUM(B2 B13)
EADD(B1:B14)
SUMB1B14
(B2B13)
Answers
Answer:
Your answer is 42,800.
Explanation:
Add together all the numbers and you get a total income of 42,800.
Answer:
=SUM(B2:B13)
Explanation:
EDGE2021
What do computers use to represent on and off? 0 and 1 1 and 2 RGB Megabyte