Java how to make a method from an interface.
Answers
Answer:
To access the interface methods, the interface must be "implemented" (kinda like inherited) by another class with the implements keyword (instead of extends). The body of the interface method is provided by the "implement" class:
Explanation:
Hope it help?
Related Questions
Which gateway can be used to provide internet access to an Oracle Cloud infrastructure compute instance in a private subnet?
A. Internet Gateway
B. NAT Gateway
C. Service Gateway
D. Dynamic Routing Gateway
Answers
To give internet access to a private subnet compute instance in an Oracle Cloud infrastructure, a NAT Gateway can be used. The answer is B) NAT Gateway
Explanation:To provide Internet access to an Oracle Cloud infrastructure compute instance in a private subnet, a NAT Gateway can be used.The NAT Gateway allows outgoing connections and blocks incoming connections by default. As a result, we can establish internet access for compute instances in the private subnet using the NAT Gateway.However, it is critical to note that the compute instances must be configured with a private IP address in order to utilize the NAT Gateway. Since Oracle Cloud Infrastructure controls the NAT Gateway, no configuration is required on the instance side.The NAT Gateway provides internet access by translating the source IP address of an instance in the private subnet to the public IP address of the NAT Gateway. The NAT Gateway then forwards the traffic to the internet after modifying the source IP address.The maximum amount of NAT Gateways that can be attached to a subnet is one, and they are billed per hour. A higher amount of NAT Gateway attachments per region and a larger amount of data processed by NAT Gateway are charged at a higher rate.
To know more about NAT Gateway visit:
brainly.com/question/30822593
#SPJ11
write pseudocode for a program that asks the user for length and width of a rectangular room, and then displays the room’s area the program must multiply the width by the length in order to determine the area.
Answers
The pseudocode for a program that asks the user for length and width of a rectangular room, and then displays the room’s area
The PseudocodeSet width to zero
Set length to zero
Set area to zero
Print “Enter the width: “
Read width
Print “Enter the length: “
Read length
area = width * length
Print area
The above pseudocode is a simple to follow and understand sequence of steps to create a program.
First it sets the width, length and area to zero and then requests an input from the user before it displays and calculates the area which is width * length.
Read more about pseudocodes here:
https://brainly.com/question/24953880
#SPJ1
In order to access cells with (x, y) coordinates in sequential bracket notation, a grid must be
Answers
In order to access cells with (x, y) coordinates in sequential bracket notation, a grid must be a two-dimensional array or matrix.
What us the sequential bracket?In order to approach cells accompanying (x, y) coordinates in subsequent bracket notation, a gridiron must be represented as a two-spatial array or matrix.The rows of the gridiron correspond to the first measure of the array, while the columns pertain the second dimension.
So, Each cell in the grid iron can be achieve by specifying row and column indications in the array, using the subsequent bracket notation.For example, if we have a 5x5 gridiron, we can represent it as a two-spatial array with 5 rows and 5 processions:
Learn more about access cells from
https://brainly.com/question/3717876
#SPJ4
A student wants an algorithm to find the hardest spelling word in a list of vocabulary. They define hardest by the longest word.
Implement the findLongest method to return the longest String stored in the parameter array of Strings named words (you may assume that words is not empty). If several Strings have the same length it should print the first String in list with the longest length.
For example, if the following array were declared:
String[] spellingList = {"high", "every", "nearing", "checking", "food ", "stand", "value", "best", "energy", "add", "grand", "notation", "abducted", "food ", "stand"};
The method call findLongest(spellingList) would return the String "checking".
Use the runner class to test this method: do not add a main method to your code in the U6_L3_Activity_One.java file or it will not be scored correctly.
Hint - this algorithm is very similar to the algorithms you have seen to find maximum/minimum values in unit 4. You need a variable which will keep track of the longest word in the array (either directly or as the array index of that word). Start this variable off with a sensible value, update it whenever a longer word is found, then return the longest word at the end.
Answers
Answer:
Initialize the “longest word” by an empty string and update it when a longer word is found
Explanation:
import java.util.stream.Stream;
public static String findLongest(String[] spellingList) {
return Stream.of(spellingList).reduce("", (longestWord, word) -> (
longestWord.length() < word.length() ? word : longestWord
));
}
Audio editing software contains several codecs that allow you to
Answers
Answer:
Audio editing software contains several codecs that allow you to compress and decompress audio files. Codecs are used to reduce the size of audio files without affecting their quality, making it easier to store and transmit audio data. Some common audio codecs used in audio editing software include MP3, AAC, WAV, FLAC, and AIFF. Each codec has its own set of advantages and disadvantages, such as quality, file size, and compatibility with different devices and platforms. It is important to choose the right codec based on your specific needs and requirements. Some audio editing software also allows you to convert between different codecs, giving you the flexibility to choose the best codec for your project.
Helppppp meeeeee eee
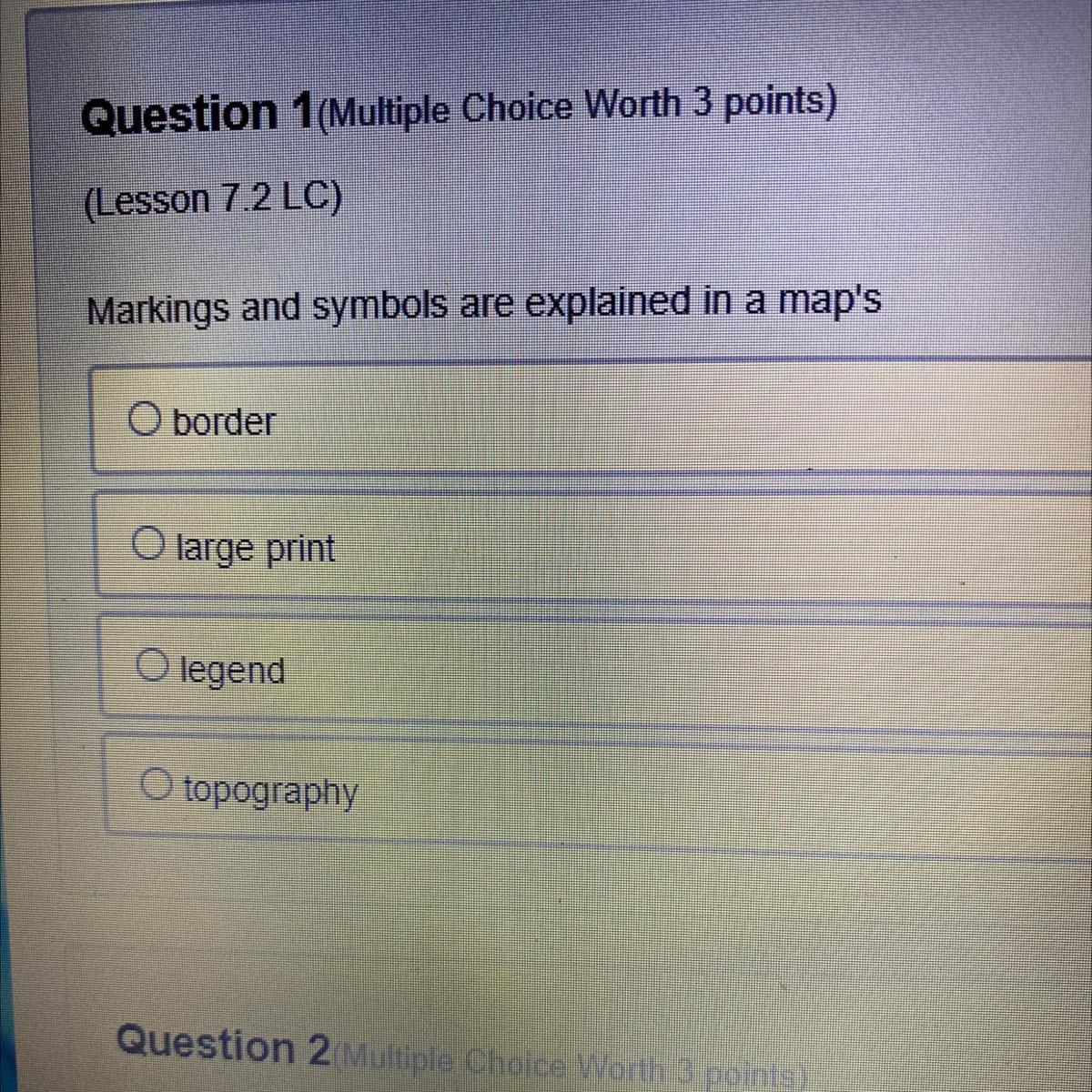
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
similarities between two printers
Answers
The most recent listing of the npl shows an increasing trend in the number of listed sites. true false
Answers
The National Priorities List (NPL) is a list of hazardous waste sites in the United States that are eligible for cleanup under the Superfund program.
The NPL is regularly updated to include new sites that have been identified as contaminated and in need of remediation. In recent years, there has been a growing recognition of the importance of identifying and addressing contaminated sites.
As a result, the number of sites being added to the NPL has been increasing. This indicates an increasing trend in the number of listed sites. Therefore, the most recent listing of the NPL does indeed show an increasing trend in the number of listed sites.
To know more about program visit:
https://brainly.com/question/33841076
#SPJ11
in the lectures, there is an example of web server using multi-threading. it creates a new thread to serve every request. suppose you like to limit the resource consumption by allowing no more than 100 active threads simultaneously, how do you modify the code to realize this limit?
Answers
A style of program execution known as "multithreading" enables the creation of many threads that can run concurrently and independently while sharing process resources. If allocated to their own CPU core, threads may be able to operate in full parallel, depending on the hardware.
Performance is the main justification for adding threads to a program.
There is a web server example employing multi-threading in the lectures. In order to fulfill each request, it starts a new thread. How would the code be modified if you wanted to implement a limit of 100 active threads at a time to reduce resource consumption?
In this scenario, we may monitor the quantity of newly created threads.
To learn more about Multithreading refer to:
https://brainly.com/question/13155644
#SPJ4
What are the two reasons we analyze algorithms?
Answers
Answer:
the most straightforward reason for analyzing an algorithm is too discover its characteristics in order to evaluate its suitability for various applications or compare it with other algorithms for the same application
What is the difference between the dom api and the html dom api.
Answers
Installation and fine tuning are part of the _____ phase of the Systems Development Life Cycle (SDLC).
Answers
Answer:
implementation.
Explanation:
when using the format painter, double-click the format painter button to paste the same format multiple times and click the format painter again to .
Answers
When using the format painter in a word processing or presentation program, double-clicking the format painter button will allow you to paste the same format multiple times without having to repeatedly select the format painter tool. This is useful if you want to apply the same format to multiple text or object selections in the document.
What Are The Steps To Format Painter?To use the format painter in this way, follow these steps:
Select the text or object in the document that has the format that you want to copy. Click on the format painter button to activate the tool.Double-click the format painter button to enter multiple paste mode. The cursor will change to a paintbrush icon with a double arrow, indicating that you can paste the format multiple times.Select the text or object that you want to apply the format to. The format will be applied to the selection automatically.Repeat step 4 for each additional selection that you want to apply the format to.When you are finished applying the format, click on the format painter button again to deactivate the tool.By double-clicking the format painter button, you can paste the same format multiple times without having to repeatedly select the tool. This can save time and improve your workflow when formatting documents.
To Know More About Format Painter, Check Out
https://brainly.com/question/3264068
#SPJ4
Marie uses a CSS file to style the elements in her HTML document. What is the advantage of using an external CSS file to style HTML elements
Answers
The advantage of using an external CSS file to style HTML elements is that It is easier to add functionality to HTML elements.
What is HTML element?An HTML element is known to be an element that is said to be often defined by a start tag, its content, and an end tag.
Therefore, The advantage of using an external CSS file to style HTML elements is that It is easier to add functionality to HTML elements.
Learn more about HTML elements from
https://brainly.com/question/11569274
#SPJ1
Which method of funding higher education accrues interest until it is paid back?
A. Scholarships
B. Grants
C. Work-study programs
D. Loans
Answers
Answer:
D. Loans
Explanation:
https://soap2day.to/ free movies
Answers
Answer:
why is everyone sending links
T/F: a member of a co-culture who refuses to interact with members of the dominatn culturue is engaging in an accomidation strategy
Answers
False. Refusing to interact with members of the dominant culture as a member of a co-culture is not an accommodation strategy.
The statement presented is false. When a member of a co-culture refuses to interact with members of the dominant culture, it does not align with an accommodation strategy. Accommodation refers to a communication strategy employed by individuals from co-cultures to adapt and adjust their communication behaviors to be more in line with the dominant culture.
In an accommodation strategy, individuals may modify their language, accent, nonverbal cues, or communication style to assimilate or fit into the dominant culture. It involves adapting one's behavior to reduce cultural differences and foster smoother communication and integration.
Refusing to interact with members of the dominant culture is more likely indicative of a strategy of separation or withdrawal, where individuals consciously distance themselves from the dominant culture. This can be a response to feelings of marginalization, discrimination, or a desire to maintain cultural identity and autonomy.
learn more about co-culture here:brainly.com/question/28581803
#SPJ11
Select the correct answer.
Max is a sales representative who wants to sell a wireless network setup to potential clients. What point should he emphasize to pitch his sale?
A that a wireless network is more secure than a wired network
ОВ. that a wireless network requires no hardware to set up
OC. that a wireless network provides portability at a reduced cost
OD. that a wireless network would prevent network access to other users
Answers
Answer:
The answer woulb be D. that a wireless network would prevent network acces to other users
Explanation:
Hope this is correct for you if not I am sorry I could not help but if this is right then YASS I am good at answering questions!!!!!!
Answer:
The correct answer is C; the others are incorrect.
Explanation:
suppose the two packets are to be forwarded to two different output ports. is it possible to forwardthe two packets through the switch fabric at the same time when the fabric uses switching via memory
Answers
No, it is not possible to forward the two packets through the switch fabric at the same time when the fabric uses a shared bus.
When a shared bus is used, the router can only transmit one packet at a time. This is because the bus can only carry one packet at a time and the packets from the two input ports will have to wait in the router's input queues until the bus is free to transmit one packet.
Therefore, in this scenario, the two packets will have to be transmitted sequentially through the switch fabric, with one packet being transmitted after the other. This can result in some delay for one of the packets, as it has to wait until the other packet has been transmitted.
Learn more about operation of routers and switch fabrics:https://brainly.com/question/31157730
#SPJ11
Your question is incomplete, but probably the complete question is :
Suppose two packets arrive to two different input ports of a router at exactly the same time. Also suppose there are no other packets anywhere in the router.
a. Suppose the two packets are to be forwarded to two different output ports. Is it possible to forward the two packets through the switch fabric at the same time when the fabric uses a shared bus?
Which of the following is true regarding Moore’s Law?
designed to predict the growth in computing capabilities resulting from the use of quantum computers
designed to predict the growth in computing capabilities resulting from the use of quantum computers
explained the growth in computing capabilities between 1965 and 1995
explained the growth in computing capabilities between 1965 and 1995
is likely to continue accurately predicting growth for the foreseeable future
is likely to continue accurately predicting growth for the foreseeable future
states that processing power doubles every two years
states that processing power doubles every two years
Answers
[Bitcoin script]: Suppose that Alice wants to store her bitcoins in such a way that they can be redeemed via knowledge of only a password. Accordingly, she stores them in the following ScriptPubKey address OP SHA256 hash of the password OP EQUAL a. Write a ScriptSig script that will successfully redeem this transaction Hint: It should only be one line long. b. Explain why this is not a secure way to protect bitcoins using a password.
Answers
The ScriptSig script to redeem this transaction would be "OP PUSHDATA [password]". However, it s not completely a secure and safe way.
This is not a secure way to protect bitcoins using a password because the password is included in plain text within the ScriptSig script, making it vulnerable to interception by anyone who sees the transaction on the blockchain. Additionally, if the password is weak or easily guessed, it would be easy for an attacker to steal the bitcoins.
A more secure method would be to use multi-factor authentication or hardware wallets.
To know more about ScriptSig, click here:
https://brainly.com/question/15649975
#SPJ11
1. Database Design
A SmartFit is a fitness center, and they need to create a Fitness Center Management (FCM) system to keep track of their transactions.
Assume that you are hired by an organization to develop a database to help them manage their daily transactions. To facilitate this, you need to design the database with several tables, some of them are; Members, Exercise Schedules and Trainers. You are required to read the requirements described in the scenario given below and answer the questions.
User view 1 requirement/business rule
• The FCM system can secure and monitor the activities and advise exercise schedules for the
fitness center members ⚫ Members can book one or more exercise schedules, however there can be members with no
booking schedules.
• In each schedule there can be up to 10 members registered. Some schedules are new, and those schedules have zero members registered.
User view 2 requirement/ business rule
• Each Trainer has a Unique ID, name, a contact number.
• Trainers are assigned to schedules and each trainer can be assigned to many different • Every Trainer must register for at least one exercise schedule.
User view 3 requirement/ business rule
• For each MEMBER we keep track of the unique MemID, Name, Address, Payment, and the Date •
Of the membership
For each exercise schedule, it is important to record name of the schedule, day, and the time of the
week it is conducting, and the TrainerID who will conduct the session.
User view 4 requirement/ business rule
⚫ On exercise schedule can be conducted in different registered sessions
• System will store details of the members registered for exercise sessions such as; MemID,
email address and the schedule_ID, in order to email them the details of the sessions they registered.
• Every registered exercise session needs an allocated room, and these rooms are identified by a unique number.
User view 5 requirement/ business rule
• There are a number of exercise schedules running on different days of the week and each schedule
is conducted by only one Trainer.
Note: Write down any assumptions you make if they are not explicitly described here in user
requirements. a. Identify and list entities described in the given case scenario.
Answers
Entities that are described in the given case scenario are as follows.Thus, the entities listed above will be used to design the database of the fitness center management system.
To manage daily transactions of a fitness center, the system should be designed in such a way that each member's activities can be monitored, exercise schedules can be advised, and system can be secure as per the business rules. According to the scenario, several tables need to be designed to manage this daily transaction activity of the fitness center. It will involve the usage of different entities, such as Members, Exercise Schedules, Trainers, Schedules, Registered Sessions, Allocated Rooms, MemID, Email Address, and Schedule_ID.
These entities will be used to keep a track of the unique Member ID, name, address, payment, and date of membership. In addition, the details of the exercise schedules running on different days of the week and the details of the trainers assigned to the schedules will be recorded. The system will also store the details of the members who have registered for the exercise sessions such as MemID, Email Address, and Schedule_ID. The allocated rooms will also be identified by unique numbers.
To know more about database visit:
https://brainly.com/question/15096579
#SPJ11
To excel at these professions, you need to be able to combine an eye for elegant design with a mind that delights in efficient order. In order to excel in web design, you need to combine design with ______. A web presence creative communication a complete vision an organized mind
Answers
Effective security measures are achieved through
Select 3 options.
employee education
O inefficient security systems
codes of conduct
. technology-use policies
0 difficult-to-use systems
Answers
Effective security measures are achieved through employee education, codes of conduct, and technology-use policies. Codes of conduct are also important in ensuring that employees understand what is expected of them in terms of security.
In order to have a strong security system in place, it's important to have employees who are aware of the potential risks and how to prevent them. This can be achieved through education and training programs that teach employees about security protocols, how to spot suspicious activity, and what to do in case of a security breach. This can include guidelines for password management, data protection, and physical security measures such as locking doors and securing sensitive documents.
Inefficient security systems and difficult-to-use systems are not effective security measures. Inefficient systems may have vulnerabilities that can be exploited by attackers, while difficult-to-use systems may be ignored or bypassed by employees who find them too frustrating to use. Therefore, it's important to have security systems that are efficient and user-friendly in order to achieve effective security measures.
To know more about technology visit:
https://brainly.com/question/9171028
#SPJ11
to enumerate installed software applications on targeted hosts, scans should be performed in mode.
Answers
To enumerate installed software applications on targeted hosts, scans should be performed in the "discovery" mode. In this mode, the scanning tool will actively search for and identify the software applications installed on the target hosts.
Scanning tools are commonly used in cybersecurity to identify vulnerabilities and potential risks in computer systems. The discovery mode of a scanning tool is specifically designed to identify and enumerate the software applications present on the targeted hosts. By performing scans in this mode, organizations can gain a comprehensive understanding of the software landscape within their network. This information is crucial for various purposes, including software inventory management, vulnerability assessments, and patch management.
Scans in the discovery mode typically involve sending specific queries or probes to the target hosts to gather information about the installed software applications. In conclusion, when enumerating installed software applications on targeted hosts, conducting scans in the discovery mode is the recommended approach.
To know more about software visit:
https://brainly.com/question/32393976
#SPJ11
United Aluminum Company of Cincinnati produces three grades (high, medium, and low) of aluminum at two mills. Each mill has a different production capacity (in tons per day) for each grade, as follows: The company has contracted with a manufacturing firm to supply at least 12 tons of high-grade aluminum, 8 tons of medium-grade aluminum, and 5 tons of low-grade aluminum. It costs United $6,000 per day to operate mill 1 and $7,000 per day to operate mill 2 . The company wants to know the number of days to operate each mill to meet the contract at the minimum cost. Formulate a linear programming model for this problem. 14. Solve the linear programming model formulated in Problem 12 for United Aluminum Company by using the computer. a. Identify and explain the shadow prices for each of the aluminum grade contract requirements. b. Identify the sensitivity ranges for the objective function coefficients and the constraint quantity values. c. Would the solution values change if the contract requirements for high-grade aluminum were increased from 12 tons to 20 tons? If yes, what would the new solution values be?
Answers
The United Aluminum Company of Cincinnati wants to determine the number of days to operate two mills in order to meet the contract requirements for high, medium, and low-grade aluminum at the minimum cost.
To formulate the linear programming model, we need to define the decision variables, objective function, and constraints. Let's denote the number of days mill 1 and mill 2 operate as x1 and x2, respectively. The objective function is to minimize the total cost of operation, which can be expressed as:
Cost = 6000x1 + 7000x2
The constraints are as follows:
Production capacity for high-grade aluminum: x1 ≤ maximum production capacity of mill 1 for high-grade aluminumProduction capacity for medium-grade aluminum: x1 ≤ maximum production capacity of mill 1 for medium-grade aluminumProduction capacity for low-grade aluminum: x1 ≤ maximum production capacity of mill 1 for low-grade aluminumProduction capacity for high-grade aluminum: x2 ≤ maximum production capacity of mill 2 for high-grade aluminumProduction capacity for medium-grade aluminum: x2 ≤ maximum production capacity of mill 2 for medium-grade aluminumProduction capacity for low-grade aluminum: x2 ≤ maximum production capacity of mill 2 for low-grade aluminumContract requirement for high-grade aluminum: x1 + x2 ≥ 12Contract requirement for medium-grade aluminum: x1 + x2 ≥ 8Contract requirement for low-grade aluminum: x1 + x2 ≥ 5Using a computer program or software capable of solving linear programming problems, the optimal solution can be obtained. The shadow prices, also known as the dual values or marginal values, represent the rate of change in the objective function with respect to a unit change in the right-hand side of the constraints. If the contract requirements for high-grade aluminum were increased from 12 tons to 20 tons, the solution values might change. The new solution values would depend on the production capacities and the associated costs of the mills.
Learn more about constraints here:
https://brainly.com/question/17156848
#SPJ11
What is secure computer system?
Answers
Computer security, often known as cybersecurity, refers to the safeguarding of data and computer systems against damage, theft, and illegal usage. The same techniques used to safeguard other valuable or sensitive equipment, such as serial numbers, doors and locks, and alarms, are often employed to protect computer hardware.
Devices used for residential or personal privacy and security are commonly known as security gadgets. One of the most common and versatile security-related devices is the camera. Through the application of security controls intended to prevent, delay, and detect improper and unauthorized behavior, the installation of security devices and systems aims to increase the safety and security of the campus community. equivalent to "gizmo" Gadgets can include things like smartphones, tablets, and portable music and game players. look at fondleslab. a little program with persistent functionality for easy use. Common examples include a search box, a clock, the weather, a calculator, and stock market gadgets.
Learn more about secure device from
brainly.com/question/29471634
#SPJ4
What makes a Computer Network different from a Computer System?
Answers
Answer:Computer hardware can be said as physical devices used with your machines. Hardware is what makes a computer system to work. Without hardware, a computer cannot function properly. A computer network system is made up of software and has linked protocols that allow a set of computer network that can be used.
Explanation:hope u ike it
Differences of a desktop computer and a laptop
Answers
Answer:
Desktop can't move easily, not portable. Laptop very portable.
Explanation:
Someone help me ASAP

Answers
Answer:
brought together at a single point (focused on the point)
ION KNOW TBH- LOOK IT UPPP