) Java.Create a tree set with random numbers and find all the
numbers which are less than or equal 100 and greater than 50 Input:
3, 56, 88, 109, 99, 100, 61, 19, 200, 82, 93, 17 Output: 56, 88,
99, 1
Answers
An example Java code snippet that creates a TreeSet with the given numbers and finds all the numbers that are less than or equal to 100 and greater than 50 is:
import java.util.TreeSet;
public class Main {
public static void main(String[] args) {
TreeSet<Integer> numbers = new TreeSet<>();
numbers.add(3);
numbers.add(56);
numbers.add(88);
numbers.add(109);
numbers.add(99);
numbers.add(100);
numbers.add(61);
numbers.add(19);
numbers.add(200);
numbers.add(82);
numbers.add(93);
numbers.add(17);
TreeSet<Integer> result = new TreeSet<>();
// Iterate through the TreeSet and find the numbers
for (Integer num : numbers) {
if (num <= 100 && num > 50) {
result.add(num);
}
}
// Print the output
for (Integer num : result) {
System.out.print(num + " ");
}
}
}
The tree set is a part of the Java Collection framework and it is used to store a sorted set of elements. The provided Java code demonstrates how to create a TreeSet, add random numbers to it, and find the numbers that satisfy a specific condition.
By iterating through the TreeSet, the code identifies the numbers that are both less than or equal to 100 and greater than 50. These numbers are stored in another TreeSet called "result" and then printed out in ascending order. The code showcases the use of TreeSet's sorting capability and demonstrates how to perform conditional filtering on the elements.
Learn more about TreeSet https://brainly.com/question/13147802
#SPJ11
Related Questions
Some one help pls will mark brainless !!!!!
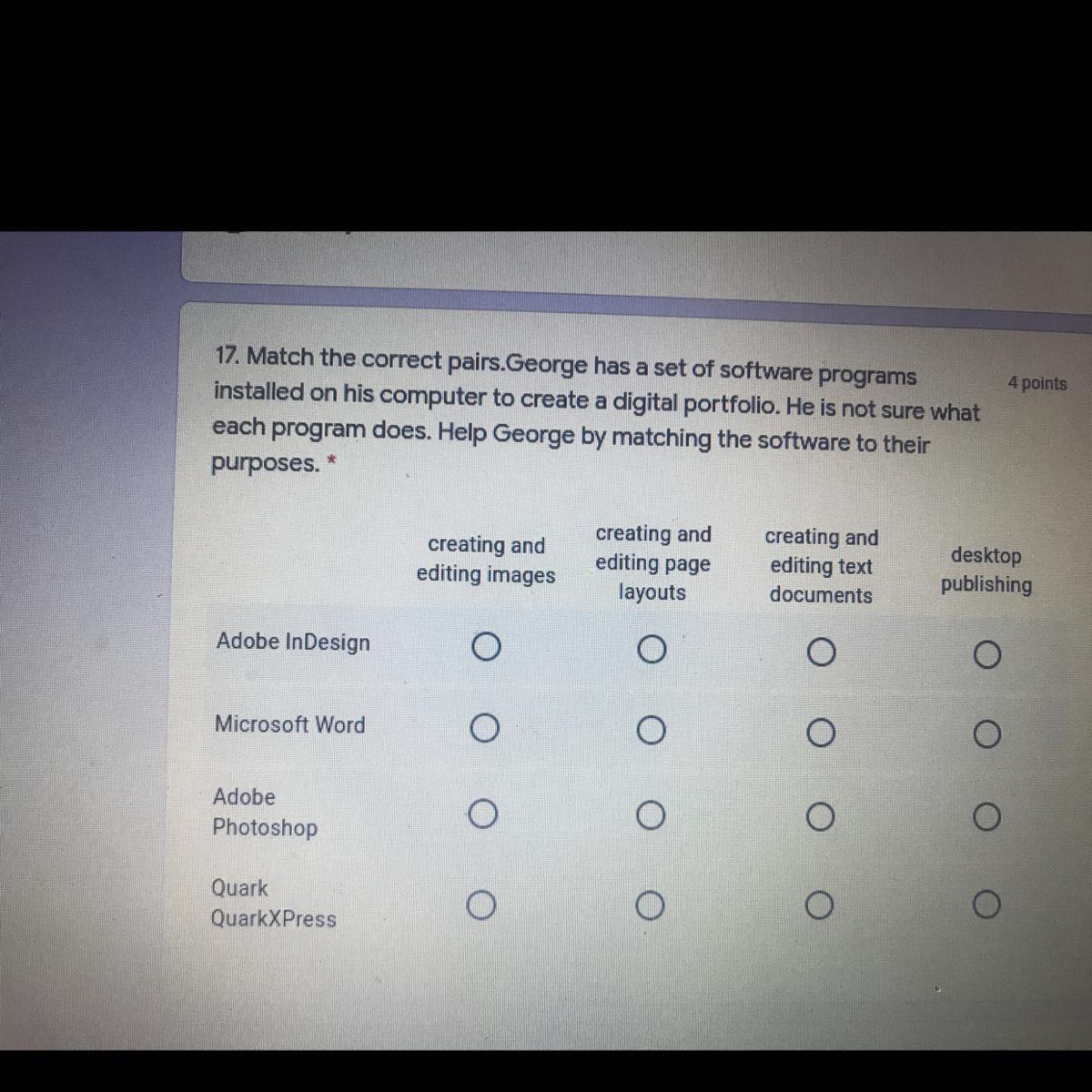
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
What should be the primary concern when using machinery or project tools in class? (Choose the best answer.)
* 4 points
working to find a shortcut
A safe work environment for everyone.
working quickly
fun
Answers
Answer:
First number
Explanation:
bcoz it help us to find a shorcut our work then other methods.
The primary concern when using machinery or project tools in class should be "A safe work environment for everyone."
Safety is of utmost importance when operating machinery or tools, especially in an educational setting where students may have limited experience or training in handling such equipment.
The well-being of students and teachers should always be the top priority to prevent accidents, injuries, or damage to property.
Educators must ensure that students are properly trained on how to use the machinery or tools safely and follow all safety guidelines and protocols. It is crucial to provide adequate supervision, proper safety equipment, and clear instructions to minimize risks and create a secure learning environment.
To learn more about safe work environment;
https://brainly.com/question/29335222
#SPJ3
Which three events occur when a DNS request is processed?
A. A local DNS server sends the IP address back to the requesting
device for access.
B. A local DNS server checks to see if it knows the IP address for the
site requested.
C. A subdomain DNS server defines how data will be transferred
over the internet.
D. Top-level domain DNS servers look up the site and return the IP
address.
Answers
The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.What are the types of DNS queries?There are known to be 3 types of DNS queries which are:
Recursive iterativenon-recursive.Therefore, The three events occur when a DNS request is processed is that
A local DNS server sends the IP address back to the requesting device for access. A local DNS server checks to see if it knows the IP address for the site requested.Top-level domain DNS servers look up the site and return the IP address.Learn more about DNS from
https://brainly.com/question/12465146
#SPJ1
Which is true about arrays and methods? Group of answer choices Arrays cannot be passed to methods An array is passed to a method as a reference Passing an array to a method creates a copy of the array within the method A programmer must make a copy of an array before passing the array to a method
Answers
Answer:
Correct option is: Arrays are passed to methods by reference.
Explanation:
Arrays are passed to methods by reference. This means that if the content of the array is changed in a method, the change will be reflected in the calling method.
What is a "Top-Level Domain Name"?
Answers
A top-level domain is known to be an aspect of a domain that quickly follows the last dot symbol that is seen in a domain name.
What is a "Top-Level Domain Name"?This is known to be the biggest level in terms of the hierarchical Domain Name System of the Internet.
Note that TLD (top-level domain) is said to be the most generic domain that is seen on the Internet's hierarchical DNS (domain name system) as A top-level domain is known to be an aspect of a domain that quickly follows the last dot symbol that is seen in a domain name.
Learn more about Domain Name from
https://brainly.com/question/13437432
#SPJ1
write a program that prints a giant letter a like the one below. allow the user to specify how large the letter should be.
Answers
Here's an example Python program that allows the user to specify the size of the letter A and then prints it out using asterisks:
size = int(input("Enter the size of the letter A: "))
# print the top half of the letter A
for i in range(size):
for j in range(size - i):
print(' ', end='')
for k in range(i + 1):
if k == 0 or k == i:
print('*', end=' ')
else:
print(' ', end=' ')
print()
# print the bottom half of the letter A
for i in range(size // 2):
for j in range(size // 2):
print(' ', end='')
print('*', end='')
for k in range(size // 2, size - 1):
print(' ', end=' ')
print('*')
When you run this program, it will prompt the user to enter the size of the letter A. Based on the input size, the program will print out the corresponding letter A using asterisks.
Note that the program uses nested loops to iterate over each row and column of the letter A, and uses if/else statements to determine whether or not to print an asterisk or a space at each position.
The complete question
Write a program that prints a giant letter A like the one below. Allow the user to specify how large the letter should be.
*
* *
* * * * *
* *
* *
Learn more about coding: https://brainly.com/question/20712703
#SPJ4

"You need to prove ownership of a domain name for an upcoming transfer to a new registrar. Which Domain Name System (DNS) record do you create to prove ownership?"
Answers
Answer:
Canonical Name Record (CNAME)
Explanation:
The Canonical Name Record also known as CNAME Record is a Domain Name System (DNS) record, that allows mapping of a domain name to another domain name. The CNAME record is useful when several services are hosted under one IP address.
The CNAME record allows the specification of a domain name as another name for another domain name. The CNAME record enables an alias name to be mapped to the actual canonical domain name.
How do u set up a Wi-Fi network on Android
Answers
Answer:
These are some way I know

________ service consists of two types of channels: bearer (b) channels and delta (d) channels.
Answers
The service that consists of two types of channels: bearer (b) channels and delta (d) channels is called ISDN (Integrated Services Digital Network).
ISDN is a digital communication network that allows for voice, data, video, and other services to be transmitted simultaneously over the same line. Bearer channels are used for carrying the user's information, while delta channels are used for signaling and control purposes.
Bearer channels can transmit data at a speed of 64 kbps (kilobits per second) and can be combined to provide higher bandwidths. The number of bearer channels that can be used together depends on the type of ISDN service being used. For example, Basic Rate Interface (BRI) service provides two bearer channels (2B) while Primary Rate Interface (PRI) service provides 23 bearer channels (23B).
Delta channels, on the other hand, are used for signaling and control purposes. Delta channels carry information about call setup, call teardown, and other control information related to the ISDN network. Delta channels are used to establish a connection between two devices, to transfer data about the call, and to manage the call during its duration.
Overall, the combination of bearer and delta channels in ISDN allows for efficient and effective communication of various types of data over a digital network.
Learn more about channels here:
https://brainly.com/question/30702464
#SPJ11
In python
BINGO! - Create a piece of code that meets the following requirements:
Asks the user to enter their name.
The code should then ask the user to enter their lucky number (it should tell them it must be between 1 - 10).
The code should then randomly generate and output a number between 1 - 10. If the number is a match, it should display the message “BINGO!”. However if it does not match, the code should continue until the two numbers match.
At the end of the code it should display how many numbers it took until the user got a match.
Answers
Using the knowledge in computational language in python it is possible to write a code that Create a piece of code that meets the following requirements: Asks the user to enter their name.
Writting the code:import random
name = input("What is your name? ")
print("Good Luck ! ", name)
words = ['rainbow', 'computer', 'science', 'programming',
'python', 'mathematics', 'player', 'condition',
'reverse', 'water', 'board', 'geeks']
word = random.choice(words)
print("Guess the characters")
guesses = ''
turns = 12
while turns > 0:
failed = 0
for char in word:
if char in guesses:
print(char, end=" ")
else:
print("_")
print(char, end=" ")
failed += 1
if failed == 0:
print("You Win")
print("The word is: ", word)
break
print()
guess = input("guess a character:")
guesses += guess
if guess not in word:
turns -= 1
print("Wrong")
print("You have", + turns, 'more guesses')
if turns == 0:
print("You Loose")
See more about python at brainly.com/question/18502436
#SPJ1


A group of small local businesses have joined together to share access to a cloud-based payment system. Which type of cloud is most likely being implemented?
Answers
The type of cloud that is most likely being implemented when a group of small local businesses has joined together to share access is community cloud service. The correct option is C.
What is cloud service?Cloud services have a wide variety of services for companies and businesses. They provide applications and software with resources. They provide easy and affordable services.
Community cloud service is a shared type of cloud service that helps banks and heads of trading firms.
Thus, the correct option is C. Community.
To learn more about cloud service, refer to the below link:
https://brainly.com/question/24227961
#SPJ1
The question is incomplete. Your most probably complete question is given below:
Public
Private
Community
Hybrid
When you fully engage NAP for remediation enforcement, what mode do you place the policy in? a. assessment. b. compliment. c. enforcement . d. isolation
Answers
When fully engaging NAP (Network Access Protection) for remediation enforcement, the mode that is used is c. enforcement. NAP is a feature in Microsoft Windows Server that allows administrators to set policies that enforce compliance with system health requirements for network access.
The enforcement mode allows the NAP server to block or restrict access to non-compliant computers until the issues are resolved. This mode ensures that only healthy and compliant devices are allowed to access the network resources. The assessment mode, on the other hand, is used to evaluate the compliance status of client computers without enforcing any restrictions or blocking access to the network. It provides a way for administrators to evaluate the current state of client computers before enforcing NAP policies.
The compliment and isolation modes are not related to NAP enforcement. The compliment mode is used for compatibility with existing network security systems, while the isolation mode is used to isolate non-compliant computers from the network without actually enforcing compliance. In summary, when fully engaging NAP for remediation enforcement, the policy is placed in the enforcement mode, which allows the NAP server to block or restrict access to non-compliant computers until the issues are resolved.
Learn more about Network Access Protection here-
https://brainly.com/question/30511393
#SPJ11
i need help. match the commands to the task it helps to complete

Answers
1:4
2:3
3:2
4:1
Describe types of hardware used for output
Answers
Do you think that smart televisions are going to replace media players?
Answers
Answer:
yes because smart television give more information
Identify the following as being an advantage or not being an advantage of rfid systems used by zara.
a. Can reduce the time needed to take store inventory b. Can help find a product a customer wants that isn't available in store
c. Can eliminate the need for PoS systems
d. Can lower advertising co
Answers
The advantages of RFID system used by Zara are that it can reduce the time needed to take store inventory, and can help find a product a customer wants that isn't available in store.
It can eliminate the need for POS systems, can lower advertising costs are NOT an advantage of RFID systems used by Zara
Radio Frequency Identification System is referred to as an RFID system. It is an "Identification system employing wireless communication" that enables data to be transferred between "Antenna (or Reader/Writers)" and "RF Tags (or Data Carriers)," which are held by people or affixed to things. A radio communication system, in a sense.
There are several uses for RFID systems including consolidated administration of things and information is possible with an RFID system.
The following applications make up the majority of the uses for RFID in a production plant.
Workplace training (destination instruction)management of history (production history, work history, inspection history, etc.)ID (identification) typically refers to the specific identification of individuals or things.RFID is used to identify objects, just like barcodes and two-dimensional codes.Fingerprints and the iris of the eye are examples of biometrics used to identify persons in a unique way.The identification system is known as ID system. It is a method for reading and recognizing data on people and things, including AIDC (Automatic Identification & Data Capture).
AIDC uses devices that combine hardware and software to identify data acquired from media such as barcodes, 2-dimensional codes, RFID systems, iris, fingerprints, voice, etc. without the need for human participation.
To learn more about RFID system click here:
brainly.com/question/25705532
#SPJ4
Which file organisation has the quickest access to data files? *
1 point
a)Direct
b)Serial
c)Sequential
d)Transaction
Answers
the information security principle that requires significant tasks to be split up so that more than one individual is required to complete them is called isolation of duties.
Answers
The given statement is true because the information security principle that requires significant tasks to be split up so that more than one individual is required to complete them is called the isolation of duties.
In information security, isolation of duties is the security principle that forbids one individual from controlling more than one aspect of a process. The objective of the concept of separating tasks is to avoid fraud, errors, or misunderstandings as a result of human error, among other things.
This principle is founded on the idea that the lack of check-and-balance mechanisms creates the possibility of wrongdoing. In the most basic sense, it is a preventive measure that is intended to eliminate single-point vulnerabilities by imposing restrictions on who can perform specific operations or gain access to certain areas of the system.
You can learn more about information security at
https://brainly.com/question/28004913
#SPJ11
Suppose that there are a group of n people. Some of them meet, some of them don't. Your goal is to select m people such that for each person i; i is either among the ones that are selected, or is known by someone in the selected group
Answers
The problem can be solved using the concept of graph theory. We can represent the group of people as a graph, where each person is a node, and there is an edge between two nodes if they know each other.
If a person is not connected to anyone else, we can consider them as a separate connected component.To select m people such that each person i is either selected or knows someone in the selected group, we can use a modified version of the Breadth-First Search algorithm. We start by selecting the first person arbitrarily and add them to the selected group. We then perform a Breadth-First Search, starting from this person, and adding all the people we encounter to the selected group, up to a total of m people.During the Breadth-First Search, we can maintain a list of people who have already been added to the selected group, and skip them if we encounter them again. This ensures that we only select people who are not already known by someone in the selected group.If we are unable to select m people using this approach, we can increase the number of selected people and repeat the process until we have selected the required number of people. this approach ensures that we select a group of m people such that each person i is either in the selected group or known by someone in the group.
To learn more about nodes click the link below:
brainly.com/question/28269884
#SPJ4
which of these lines will not result in a syntax error?
A. if 10 > 3
B. if 10 > 3:
C. of 10 > 3:
D. if 10 >< 3:
please answer
Answers
The lines that will not result in a syntax error is option A. if 10 > 3.
What does C language syntax mistake mean?Syntax errors are mistakes that happen when you don't follow the guidelines for writing C/C++ syntax. A fix must be made before the code may be compiled, according to this compiler issue. These are all compile-time faults since the compiler can identify them all.
Therefore, The typical syntactic mistakes are:
incorrect use of the comma. Punctuation that is misplaced or used improperly can drastically alter the meaning of words and how a sentence sounds when spoken aloud.utilizing language fragments rather than full phrases.Modifiers for squinting.Learn more about syntax error from
https://brainly.com/question/24822807
#SPJ1
you want to copy the march worksheet to use it to enter data for april. after you right-click the march sheet tab and select move or copy, you click ok in the move or copy dialog box without changing any settings. what happens?
Answers
When you click OK in the Move or Copy dialog box without changing any settings, the March worksheet will be copied to create a new worksheet with the same sheet name and the same content as the original sheet.
The new sheet will be placed on the bottom of the workbook and will be ready to be used to enter data for April.
A worksheet is a sheet of paper, typically with questions or tasks printed on it, used for a variety of educational or instructional purposes. Worksheets are often used in the classroom to help students practice or learn a variety of topics, such as math, reading, writing, science, and social studies.
Learn more about worksheet :
https://brainly.com/question/30142678
#SPJ4
Which term describes unjust behavior due to a person’s gender or race
Answers
Answer:
Discrimination
Explanation:
Answer:
Discrimination
Explanation:
Write the definition of a public class Simple. The class has no constructors, methods or instance variables.
Answers
Answer:
public class Simple{}
Explanation:
Which word should a programmer use to describe what should happen when the condition of an if statement is NOT met?
A.
iterative
B.
when
C.
else
D.
also
Answers
The word that should a programmer use to describe what should happen when the condition of an if statement is NOT met is option C. else.
Why are conditional statements used in programming?When a condition is true or false, a conditional statement instructs a program to take a certain action. If-then or if-then-else statements are frequently used to represent it. The preceding example is a block of code that employs a "if/then" conditional statement.
Therefore, the else statement is used, "to indicate what should happen when the condition of an if statement is not fulfilled," is the proper response since the otherwise statement is typically used when computations are still necessary when a condition in an if and else-if statement is not met.
Learn more about programmer from
https://brainly.com/question/22654163
#SPJ1
The ______ interprets and carries out the basic instructions that operate a computer.
Answers
The processor interprets and carries out the basic instructions that operate a computer.
What is Processor?
An integrated electronic circuit called a processor is what does the calculations for a computer. A processor executes basic instructions given from an operating system, including mathematical, logical, input/output (I/O), and other operations (OS). The majority of other processes rely on the actions of a processor.
What is Operating System?
An operating system (OS) is a piece of software that controls all other application programs in a computer after being originally loaded by a boot program. Through a specified application program interface, the application programs use the operating system by requesting services (API).
CPUs will perform most basic arithmetic, logic and I/O operations, as well as allocate commands for other chips and components running in a computer. The term processor is used interchangeably with the term central processing unit (CPU), although strictly speaking, the CPU is not the only processor in a computer.
Learn more about processor click on this:
https://brainly.com/question/474553
#SPJ4
the attributes of an object/class are often coded as group of answer choices static variables methods static methods instance variables
Answers
The attributes of an object/class are often coded as instance variables.
Understanding instance variable
Instance variable is a type of variable that is declared in a class, diluar method, constructor or other method.
Characteristics of instance variable
In addition, this variable type has its own characteristic that distinguishes it from other variable types, as follows:
• If a space object is available in the heap, this slot instance variable will be created.
• Instance variable will be created as object also created using keyword new.
• Instance variables are executed when objects are also executed.
• Instance variables must be given access modifiers.
• Instance variables cannot be declared with the keyword static.
• Instance variables must be used by methods, either constructors or other methods.
• Instance variables must have a default value.
• For type data number, in the declaration instance variable is initialized with the value 0.
• For the Boolean data type, in the declaration instance variable is initialized with the value false.
• For the type of data reference or object, in the declaration instance variable is initialized with the value null.
• Values in instance variables are initialized through the declaration process or through the constructor.
Learn more about instance variable https://brainly.com/question/20658349.
#SPJ4
Instructions: In Visual Studio, under your solution called FirstSolution, create a new project using the Windows Forms App template and name it FirstFormsApplication. For this part of the assignment, you will create a Windows forms application that will implement the same functionality you implemented in your console application in Part 2 in a visual manner.
Requirements:
‐ Your form should contain three textboxes, a button and a label. Two of the textboxes will be used to enter numbers, and the third will be used to enter an operation to perform (addition, subtraction, or multiplication). ‐The program will output the result of performing the selected operation on the two numbers to the label.
Answers
The question requests to develop a Windows forms application using Visual Studio and the Windows Forms App template. The program should perform the same functions as a previously constructed console application.
Follow these instructions to finish this assignment in Visual Studio:
Create a new solution called FirstSolution in Visual Studio.On the Solution Explorer, right-click the solution and choose Add > New Project.Choose Windows Forms App from the template selection and call it FirstFormsApplication.Open the Form1.cs file after the project has been created.Add three text boxes, a button, and a label from the Toolbox to the Form1 design view.Set the textbox and button attributes as follows:TextBox1 and TextBox2: Rename them num1TextBox and num2TextBox.TextBox3: Give it the name operationTextBox.CalculateButton: Give it a name and set its Text attribute to "Calculation."Create a Click event handler for the calculateButton by double-clicking it.Parse the values from the num1TextBox, num2TextBox, and operationTextBox in the event handler method and apply the necessary arithmetic operation depending on the value in the operationTextBox.Set the Text attribute of the label to show the result.To test the application, run it.
Remember to handle any exceptions that may arise when parsing or performing arithmetic operations. Consider adding features like validation and error warnings to improve the user experience.
Learn more about Visual Studio
https://brainly.com/question/24981686:
#SPJ11
can someone help? is this a series circuit or a parallel circuit? and why?

Answers
Based on the information, it should be noted that the diagram is a parallel Circuit.
What is the circuit about?A series circuit is an electrical circuit where the components, such as resistors, capacitors, and inductors, are connected one after the other in a single path, so that the same current flows through each component. If one component fails or is disconnected, the entire circuit will be broken, and no current will flow
The amount of current flowing through each component in a series circuit is the same. In contrast, the components in parallel circuits are arranged in parallel with one another, which causes the circuit to divide the current flow. This is shown in the diagram.
Learn more about Circuit on;
https://brainly.com/question/24088795
#SPJ1
explain the role of role of programming language in computer system .
Answers
Answer:
Explanation:
A programming language is a language used to write computer programs, which instruct a computer to perform some kind of computation, and/or organize the flow of control between external devices A programming language is a language used to write computer programs, which train a computer to perform some kind of computation, and/or organize the flow of control between external devices. there are 5 main programming languages; Java, SQL, Javascript, C++, and Python. Java is the most popular and number 1 skill tech companies use this language and over 3 billion phones run on Java. SQL pronounced sequel is a special-purpose programming language used for getting information from and updating databases because all businesses run a database system of some kind. It’s also one of the easier tech skills to learn, with numerous tutorials and free resources online. Javascript is a scripting language, often used to make web pages interactive. It’s text-based, written in an HTML document, and run through a web browser. C++ is a general-purpose programming language that can be used to create small programs or large applications. In 2013, C++ was CyberCoders’ most in-demand programming language skill. As an extension of C, one of the oldest coding languages, C++ provides a foundation for many newer, more popular ones. Python is a general-purpose, high-level programming language with an emphasis on code readability. It’s one of the easier programming languages to learn, with its use of common words and expressions, more white space, and fewer curly brackets.
A programming language is a language that is used to create computer programs that direct a computer to carry out calculations or manage the control flow between external devices.
What is Computer system?A programming language is a language that is used to create computer programs that instruct a computer to carry out specific computations and/or manage the operation of external devices.
There are five main programming languages: Python, Java, SQL, and Javascript. Around 3 billion phones operate on Java, making it the most utilized language in the computer industry.
As all businesses need some sort of database system, SQL, which is pronounced sequel, is a special-purpose computer language used for obtaining information from and updating databases.
Therefore, A programming language is a language that is used to create computer programs that direct a computer to carry out calculations or manage the control flow between external devices.
To learn more about Programming, refer to the link:
https://brainly.com/question/11023419
#SPJ3
The driver ____.
sits beside the person programming
makes suggestions as the code is written
reviews the code as it is written
sits at the computer
Answers
The navigator plans the operation after reviewing the code that the driver has written.
What do you name those who write computer programs?Programmer A person who creates computer software or programs is referred to as a programmer. You can also identify as a programmer if you create software for mobile devices. Computer programmers create the code (or instructions) that enable computers to carry out the tasks that their users teach them to.
Which method of software development involves two developers working together while coding?Pair programming is an Agile software development technique where two developers work together on a single computer in conjunction with Extreme Programming (XP). Together, the two work on user story creation, programming, and testing.
To know more about programming visit:-
https://brainly.com/question/11023419
#SPJ1