Luke believes that he can invest $5000 per year for his retirement in 30 years. How much will he have available for retirement if he can earn 8% on his investment and begins investing one year from now?
A. $566,400
B. $681,550
C. $150,000
D. $162,000
Answers
If Luke invests $5000 per year for his retirement in 30 years, earning an 8% return on his investment starting from next year, he will have approximately $566,400 available for retirement.Therefore, the correct answer is A. $566,400.
To calculate the total amount available for retirement, we can use the formula for the future value of an ordinary annuity. In this case, Luke is investing $5000 per year for 30 years, with an 8% interest rate. The future value can be calculated using the formula:
FV = P * [(1 + r)^n - 1] / r
Where FV is the future value, P is the annual payment, r is the interest rate, and n is the number of years. Plugging in the values, we have:
FV = $5000 * [(1 + 0.08)^30 - 1] / 0.08
Calculating this expression gives us approximately $566,400. Therefore, Luke will have approximately $566,400 available for retirement if he invests $5000 per year for 30 years, earning an 8% return on his investment starting from next year.
learn more about investment here:
https://brainly.com/question/15105766
#SPJ11
Related Questions
chad has written the majority of his code in scratch and is ready to start thinking of test cases to make sure that his program functions properly, and when issues arise, fix them. chad is also going to show his program to his classmate and ask for any feedback or changes he could add to make his program better. this process is known as what?
Answers
The process is known as Iterative Development Process.
What is the meaning of Iterative process?
A project, product, or initiative is built, improved, and refined through the iterative process. The iterative development method calls for teams to produce, test, and rewrite until they are happy with the final product. An iterative approach can be compared to a trial-and-error methodology that advances your project toward its eventual goal.
Iterative processes are a key component of agile project management and lean techniques, although they may be used by any team, not only those that use agile approaches. You will make adjustments to your design, product, or project over the course of the iterative process until you and your team are happy with the project's final deliverable.
To learn more about iterative process, use the link given
https://brainly.com/question/26995556
#SPJ1
HELP ASAP!!!
Write a program that asks the p34won to enter their grade, and then prints GRADE is a fun grade. Your program should repeat these steps until the user inputs I graduated.
Sample Run
What grade are you in?: (I graduated) 1st
1st is a fun grade.
What grade are you in?: (I graduated) 3rd
3rd is a fun grade.
What grade are you in?: (I graduated) 12th
12th is a fun grade.
What grade are you in?: (I graduated) I graduated
It's in python
Answers
def func():
while True:
grade = input("What grade are you in?: (I graduated) ")
if grade == "I graduated":
return
print("{} is a fun grade".format(grade))
func()
I hope this helps!
Hey, My paperclips just stoped producing, does anyone have any idea how to start them up again?

Answers
Answer:
I have no clue how to get that working up again but how does a paperclip relate to that?
calculate the information gain when splitting on a and b. which attribute would the decision tree induction algorithm choose?calculate the gain in the gini index when splitting on a and b. which attribute would the decision tree induction algorithm choose?entropy and the gini index are both monotonously increasing on the range [0, 0.5] and they are both monotonously decreasing on the range [0.5, 1]. is it
Answers
By deducting the gain ratio of the splitting from the index of both the parent node, it is possible to determine the increase in the gain coefficient when dividing on a and b.
What is algorithm?
An algorithm is a set of instructions or steps that are designed to solve a problem or accomplish a task. It is an effective way of performing a task that can be repeated, with the same results each time. Algorithms are commonly used in computer programming and can range from simple to complex. They can be used to solve simple tasks such as sorting a list, to complex tasks such as playing a game of chess. Algorithms are also used in everyday life, such as when a person follows a recipe or drives to a destination. Algorithms help to make tasks easier and more efficient by breaking them down into smaller, manageable steps.
The information gain when splitting on a and b can be calculated by subtracting the entropy or gini index of the split from the entropy or gini index of the parent node. The attribute with the highest information gain would be chosen by the decision tree induction algorithm. The gain in the gini index when splitting on a and b can be calculated by subtracting the gini index of the split from the gini index of the parent node. The attribute with the highest gain in the gini index would be chosen by the decision tree induction algorithm. Yes, entropy and the gini index are both monotonously increasing on the range [0, 0.5] and monotonously decreasing on the range [0.5, 1].
To learn more about algorithm.
https://brainly.com/question/24953880
#SPJ4
How do you reset a g.mail password?
Answers
Answer:
put: forgot password to reset it
Answer:
Change your pass word
Open your Go ogle Account. You might need to sign in.
Under "Security," select Signing in to G oo gle.
Choose Password. You might need to sign in again.
Enter your new password, then select Change Password.
Write a program to calculate the sum of the numbers from 1 till upper bound. if upper bound is 5, sum should be 1 + 2 + 3 + 4 + 5 = 15. if upper bound is 11, sum should be 1 + 2 + ... + 11 = 66. if upper bound is 100, sum should be 1 + 2 + ... + 100 = 5050.
Answers
The formula used to calculate the sum is `(upperBound * (upperBound + 1)) / 2`. This formula is derived from the arithmetic series sum formula. It is valid for any upper bound value and provides a more efficient way to calculate the sum without using a loop.
To calculate the sum of the numbers from 1 till the upper bound, you can use a loop in your program. Here's how you can achieve this:
1. Start by declaring a variable to store the upper bound, for example, `upperBound = 5` or `upperBound = 11`.
2. Initialize a variable to store the sum, for example, `sum = 0`.
3. Use a loop, such as a `for` loop or a `while` loop, to iterate from 1 to the upper bound.
4. In each iteration, add the current number to the sum. For example, in the first iteration, add 1 to the sum, in the second iteration, add 2, and so on.
5. After the loop completes, the sum will hold the total sum of the numbers from 1 to the upper bound.
Here's an example of a program that calculates the sum using a `for` loop in Python:
```python
upperBound = 5
sum = 0
for i in range(1, upperBound+1):
sum += i
print("The sum is:", sum)
```
When you run this program, it will output `The sum is: 15` because the upper bound is set to 5.
You can modify the value of `upperBound` to calculate the sum for different ranges. For example, if you set `upperBound` to 11, the program will output `The sum is: 66`.
The formula used to calculate the sum is `(upperBound * (upperBound + 1)) / 2`. This formula is derived from the arithmetic series sum formula. It is valid for any upper bound value and provides a more efficient way to calculate the sum without using a loop.
Learn more about arithmetic series here:-
https://brainly.com/question/25277900
#SPJ11
if you want to create a click-to-call feature in your mobile site for smartphone users, which protocol should you use to create a phone link
Answers
The protocol you should use to create a click-to-call feature for smartphone users on a mobile site is called tel.
The tel protocol is used to create a link on a web page that will trigger a phone call when tapped or clicked on by a user. When a user clicks on the tel: link, their phone will prompt them to dial a specific phone number. To create a tel: link, you need to include the phone number in the link, like this: 555-123-4567. This link will create a click-to-call feature that will initiate a phone call to the number when clicked. By using the tel: protocol, you can make it easy for mobile users to contact you with a simple tap of the screen.
You can learn more about protocol at: brainly.com/question/27581708
#SPJ11
plz help me I have to submit the work before the day ends
13. (a) State one area where computers are used.
(2 marks)
(b) Give any two advantages of using computers in this area
(4 marks)
(c) Explain three effects of computer technology in the following areas:
(i) Job opportunities
(3marks)
Answers
Answer:
13. (a) One area where computers are used is in the creation of a record of auxiliary workers, doctors, nurses, patients, vendors, and payments that can be easily retrieved at an hospital
(b) Two advantages of using computers in an hospital are;
1) The ability to easily access the health record of a patient by a member of staff involved in treating the patient from any location
2) The reduction in the number of physical files and document kept at the counter or record storage which takes up more space as new patients are registered, even when the number of active patients remains the same
(c) Three effects of computer technology in the following area are;
(i) Job opportunities
1) The introduction of the desktop computer, increased the number of job opportunities in desktop publishing, administrative assistance and secretarial role
2) Computer technology has made more people able to work from home
3) Computer applications use with computer technology and developed to work with production machines has created a large number of machine operator job opportunities
Explanation:
What is the name for the process that A student uses to choose only the relevant bits of information from their research
Answers
Answer:
Narrowing down
you have an apple-based mdm solution and apps you assign to install to the device are not auto-installing. what do you need to check?
Answers
If the apps that you assign to install to the device are not auto-installing, you need to check the configuration of the Apple-based MDM solution.
To resolve this issue, check the following settings:
Verify that the device is assigned to the correct group.Verify that the apps are assigned to the correct group.Verify that the app assignment is completed.Check the device's restrictions and ensure that the user has the necessary permissions to install the app.The certificate for app deployment must be valid.App Store Volume Purchasing needs to be enabled.Check if the Apple push certificate has expired, and if so, renew it.Check if the iOS device is set to the latest firmware version.Updating the mobile device management server may resolve the issue if none of the above troubleshooting steps worked.Additionally, make sure that the devices are using the latest firmware, have a reliable internet connection, and have sufficient storage space.The MDM solution's documentation may be useful in resolving this issue.
Learn more about The MDM solution's:
https://brainly.com/question/29607448
#SPJ11
Which is the most popular language used in game programming?
A.binary
B. C++
C. CGI
D. Flash
Answers
Answer:
B C++
Explanation:
The two most common languages for game designers to learn are C++ and Java, although other languages are popular (such as C# for Unity). Another type of programming you may hear referred to is scripting, but that essentially comes down to a type of systems programming.
Answer:
b
Explanation:
i just know it
In a ________ system configuration, separate information systems are designed and managed by each foreign unit.
Answers
Answer:
In a decentralized system configuration, separate information systems are designed and managed by each foreign unit.
Explanation:
hopes this help (:
24) By definition, a DSS must include ________.
A) business intelligence
B) an expert system
C) an animation system
D) a user interface
Answers
By definition, a DSS must include a d) user interface.
The user interface is a crucial component of a DSS, as it facilitates interaction between the system and its users, enabling them to input data, manipulate the system, and view the generated results.
While a DSS may also incorporate elements of business intelligence (A), expert systems (B), and even animation systems (C), these are not required by definition. Business intelligence refers to the use of data analysis and visualization tools that can help inform decision-making. An expert system is a type of artificial intelligence that emulates the decision-making abilities of a human expert. Animation systems may be used to create visual representations of data or processes.
Other components, such as business intelligence, expert systems, and animation systems, can enhance a DSS's functionality, but they are not mandatory by definition.
Therefore, the correct answer is d) a user interface.
Learn more about user interface here: https://brainly.com/question/29541505
#SPJ11
application software can run without the presence of system software true or false
Answers
Answer:
false
...........
.....
Different between open source software and licensed softwares?
Answers
which two primary capabilities of the internet provide building blocks for buyer-seller relationships? multiple select question. individuality intangibility interactivity inventory
Answers
The two primary capabilities of the internet provide building blocks for buyer-seller relationships are: interactivity, individuality.
What can the internet do and how does it function?A global computer network called the internet transmits many types of data and media between linked devices. It functions by utilizing a packet-routing network that complies with Transport Control Protocol (TCP) and Internet Protocol (IP).
Therefore, In light of this, interaction can improve learning and information processing as users make use of the interface's technological features. In contexts related to health, there is empirical evidence to support the idea that interaction has the ability to improve both information processing and learning.
Learn more about capabilities of the internet from
https://brainly.com/question/29343663
#SPJ1
choices.
1. To check the integrity of your hard disk and fix various file system errors, which
Windows utility should be implemented?
A. Back up B. Check disk C. Defragmentation D. Disk Clean up
2. An event or action took place and it caused damage to data, hardware, software
and processing capability of the computer. From the statement given, which of the
following is being described?
A. logic programs
C. security process
B. security access
D. security risks
3. This software program infect, damage and disrupts the whole computer system.
Which of the following is being described?
A. Malware B. Trojan horse C. Virus D. Worms
4. To protect the whole computer system, which software utility is needed?
A. Anti-virus B. Check disk C. Defragmentation
D. Disk clean up
5. To avoid losing valuable data to your computer, which is the most important thing
A. always save files on the desktop
B. regularly back-up your files
C. always used permanent storage devices in saving files
D. regularly save your files into temporary devices
Answers
Answer:
1. B
2. D
3. C
4. A
5. B
Explanation:
1. To check the integrity of your hard disk and fix various file system errors, the Windows utility which should be implemented is Check disk (Chkdsk). This utility is always used with the command line interface (CLI) with the command "chkdsk."
2. An event or action took place and it caused damage to data, hardware, software and processing capability of the computer. From the statement given, security risks are being described. Any event or action that is capable of causing a problem to a computer system is considered to be a security risk and should be prevented through the use of an appropriate utility software.
3. Virus is a software program that can infect, damage and disrupts the whole computer system.
4. To protect the whole computer system, the software utility which is needed is an Anti-virus.
5. To avoid losing valuable data to your computer, the most important thing to do is to regularly back-up your files.
Write the method drawSquare below.
/** Precondition: 0 ≤ x < 10, 0 < y ≤ 10, and len > 0.
* Draws a square on a 10-by-10 xy-coordinate grid
* and prints the square’s side length and area.
* The upper left corner of the square will be located
* at the coordinate (x, y) and the side length of the * square will be len (or as large as will fit in the grid).
*/
public void drawSquare(int x, int y, int len)
Answers
The method drawSquare is an illustration of functions; functions are named program statements that are executed when called
The method drawSquareThe method drawSquare written in Java, where comments are used to explain each action is as follows:
//This defines the function
public static void drawSquare(int x, int y, int len) {
//This checks if x + len exceeds 10
if(x+len>10){
len = 10-x;}
//This checks if y + len exceeds 10
if(y+len>10){
len = 10-y;}
//The next four lines draw the square
drawLine(x, y, x+len, y);
drawLine(x+len,y,x+len,y-len);
drawLine(x+len, y-len, x, y-len);
drawLine(x, y-len, x, y);
}
Read more about java programs at:
https://brainly.com/question/19271625
Give an example of a positive emotion, a negative emotion, and a neutral emotion. Then give an example of how a game can make you feel each of these emotions.
Think about a good game story that made you feel a mix of positive and negative emotions. What was the story, what emotions did you feel, and how did the game make you feel them? Why did those emotions draw you into the story?
We usually think of conflict as bad or something to be avoided. How can conflict be used to a game’s advantage in game design? Include an example.
Think about what you do each weekday evening, starting with dinner and ending when you go to bed. Describe your activities as a sequence of at least five instructions. Describe at least one way that changing the order of that sequence might mess up your night.
Describe common gaming tasks that would use each of the following: a forever Loop, a conditional-controlled loop, a count-controlled loop.
Answers
Answer:
Explanation:
The give an examples of how a game can make you feel each of these emotions. ... good game story that made you feel a mix of positive and negative emotions.
1. Happy, angry and bored, a game can make you happy if you win, if it is too hard you could get angry and want to rage and if the game just keeps repeating it will get boring !
2. Well in Scratch there was a game that was very interesting. It played a song that made me happy and it was very relaxing. I was so surprised by the game when it started playing funky sounds!
3. For the dungeon dash it wasn't pretty easy to do, but the part that was so cool is that it made some epic sounds and the more time you play the game the fireballs will increase!
4. 1. Brushing my teeth, 2. Eating breakfast, 3.Going to school, 4. Eat lunch, 5. Do homework, 6. Eat Dinner. 7. Go to sleep!
5. A forever loop is a loop that repeat FOREVER, a conditional-controlled loop is a loop that is controlled by the words you gave it, a count-controlled loop is telling it to repeat in numbers!
Given an "out" string length 4, such as "<<>>", and a word, return a new string where the word is in the middle of the out string, e.g. "<>". Note: use str.substring(i, j) to extract the String starting at index i and going up to but not including index j.
makeOutWord("<<>>", "Yay") → "<>"
makeOutWord("<<>>", "WooHoo") → "<>"
makeOutWord("[[]]", "word") → "[[word]]"
Answers
Answer:
The following are the answer to this question.
Explanation:
In the given code, a "makeOutWord and word" is already used to hold some value. In this code, we define a string method "makeOutWord" that accepts two string variables "out and the word" in its parameter.
Inside the method, a return keyword is used that uses the string variable "out and the word" with the "substring" method, this method is used to returns a new string from an old string value, and it also uses the "word" string variable for the return value.
please find the attached file for code:

what is a perfect hash in a hash table? what is a perfect hash in a hash table? a hash table that does not have any primary clustering. two different keys hashing to a value outside of the range of the table.two different keys hashing to a value outside of the range of the table.
Answers
A common method for storing and retrieving data as quickly as feasible is hashing. The primary benefit of employing hashing is that it produces the best results because it uses the best searches.
What is hash table?A hash table, commonly referred to as a hash map, is a type of data structure used in computing to build an associative array or dictionary. It is a type of abstract data that associates values with keys. An array of buckets or slots are used in a hash table to provide an index, also known as a hash code, from which the requested data can be retrieved. The key is hashed during lookup, and the resulting hash shows where the relevant value is kept.Since most hash table designs use an incomplete hash function, hash collisions may occur when the hash function generates the same index for multiple keys. In an ideal world, the hash function would assign each key to a separate bucket. Usually, such encounters are allowedTo learn more about hash table refer to:
https://brainly.com/question/13162118
#SPJ4
why do software engineers use information hiding in object-oriented design? select all that apply. group of answer choices information hiding discourages the use of global data. information hiding leads to encapsulation. information hiding emphasizes communication through controlled interfaces. information hiding discourages encapsulation.
Answers
Information hiding is used in object-oriented design because it emphasizes communication through controlled interfaces and leads to encapsulation. This helps to promote modular and maintainable code by protecting internal data from unintended changes, making it easier to modify or update the code in the future.
Software engineers use information hiding in object-oriented design for several reasons. Firstly, it discourages the use of global data, which can cause issues with data integrity and access control. Instead, information hiding promotes the use of local data, which can be more easily managed and protected. Secondly, information hiding leads to encapsulation, which is the practice of wrapping data and behavior within an object, making it more self-contained and less prone to interference from other parts of the code. This helps to ensure that objects have well-defined responsibilities, making it easier to develop and maintain code. Finally, information hiding emphasizes communication through controlled interfaces, which allows for clear communication between objects without revealing the internal workings of the objects. This makes it easier to make changes to objects without affecting other parts of the code. In summary, information hiding is a useful tool in object-oriented design as it encourages clear communication, data protection, and code maintainability.
To know more about Software Please click on the given link.
https://brainly.com/question/1022352
#SPJ4
which of the following are key considerations for dealing with challenges associated with the development of a business continuity plan for a cloud-based contact center? (choose 2 answers) a. local server backup schedule b. local data center failure plan c. cloud service availability d. functionality of telecommunication solutions
Answers
Correct answer is (C) Cloud service accessibility (D) When developing a business continuity plan for a cloud-based contact center, the functionality of telecom solutions must be taken into account as a major factor.
How accessible are cloud services?When it comes to cloud infrastructure solutions, availability refers to the portion of the service's length that the data center is open to the public or provides the intended IT service.
What roles do telecommunication systems play?A communications system's main function is to facilitate information sharing among its users. A number of methods, including multiparty phone communications, television, electronic mail, and electronic message exchange, can be used to exchange this information.
To know more about Cloud service accessibility visit :-
https://brainly.com/question/28390917
#SPJ4
protected members of a base class are like _, but they may be accessed by derived classes.
Answers
protected members of a base class are like private members, but they may be accessed by derived classes.
How can a derived class access the protected members of a base class?Access to protected members that are also designated as static is granted to each companion function and member of a derived class. Only protected members that are not specified as static may be accessed by friends and member functions of a derived class through a pointer to, reference to, or object of the derived class.
What are the private members of a class?Only member functions that are included within the class can access class members that are designated as private. They are inaccessible to methods or objects outside of the class directly. Only the member functions or the friend functions have access to the private class member data.
To know more about private members visit:
brainly.com/question/30004378
#SPJ4
PLEASE HELP! THIS IS FROM A BEGINNERS COMPUTER SCIENCE CLASS:
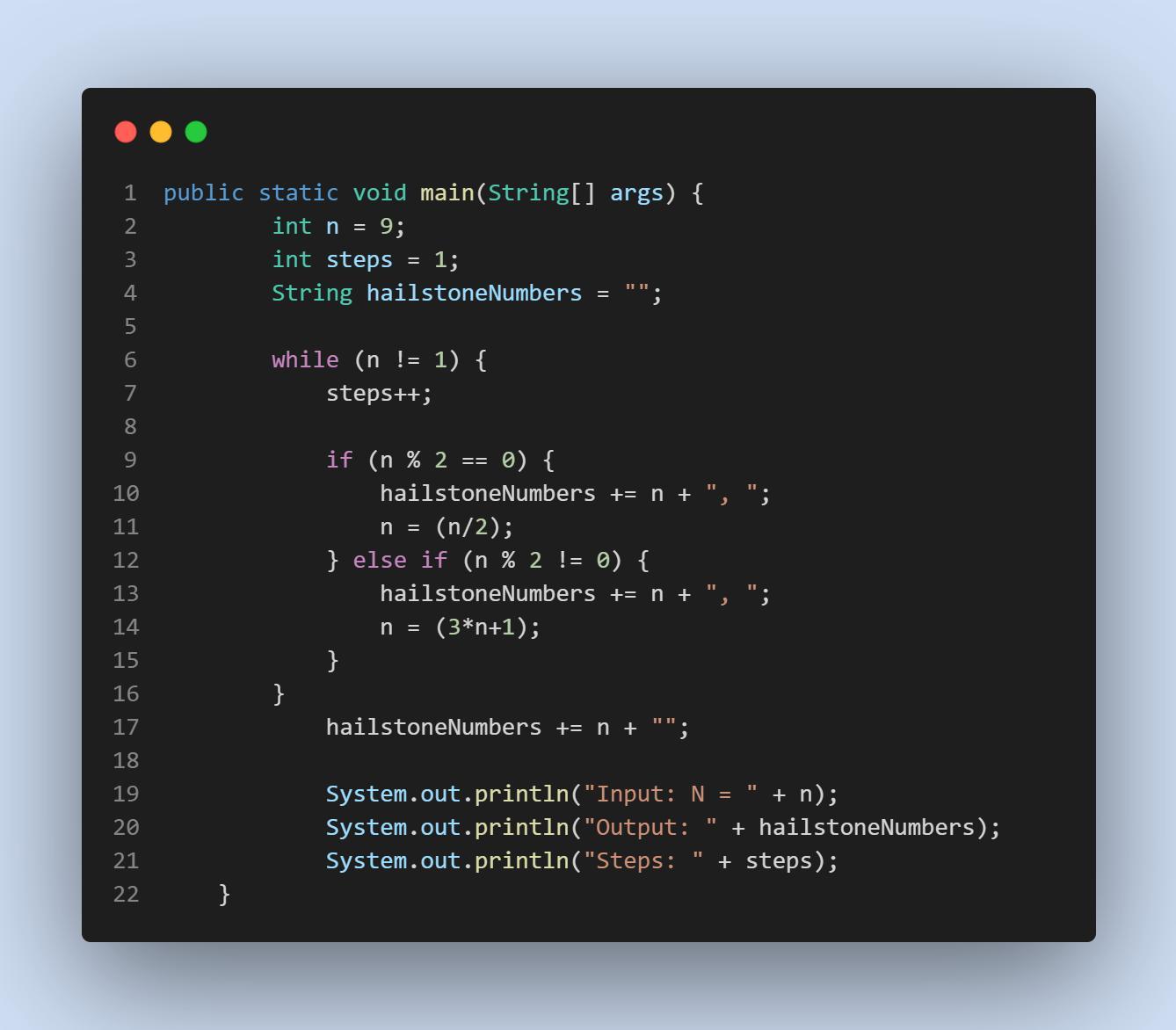
Write a program that generates the "Hailstone series" for any number from 1 to 1000. The Hailstone series is an interesting sequence of numbers, and can be calculated like this:
If the current value of n is even, the next number in the sequence will be n/2 (use integer division)
If the current value of n is odd, the next number in the sequence will be 3*n + 1
This process is repeated until you reach a value of 1. It is theorized that every integer will eventually end at 1. At the time of writing, this has been tested to be true for numbers up to ~1048, but it has never been proven!
Your program should print the Hailstone series for a particular number and the number of steps it took to reach 1.
Answers
Answer:
This is an iterative approach to the problem; you could also have done a recursive approach. This version is easier to think about in my opinion.
can someone helppp!!!!
send the answers!
20 points for u!

Answers
Workbook and worksheet are synonymous, where each workbook will contain only one worksheet
True or false
Answers
50 POINTS TO WHOEVER CAN HELP ME! When your friend Sarah turns on his computer, she hears four beeps. The computer won’t fully boot. Sarah has a Dell computer with a quad-core processor and has recently upgraded her RAM. Apply the troubleshooting methodology to help her understand and resolve this problem; I have them listed below: Identify the Problem Internet Research Establish a Theory of Probable Cause Test the Theory Establish a Plan of Action Implement the Solution or Escalate Verify Full System Functionality Document Findings
Answers
Answer:
Unplug everything
unscrew and remove side panel
pop-out each memory card, blow on them and pop them back in (be sure the tabs lock back down)
Explanation:
Somehow one of the memory cards must have jiggled lose, even though they looked fine at first
Answer:
this is a memory card fail this could mean many different things like dust, but it ussualy isn't that serious if she has a new RAM, and if there is a problem she should have a warranty on her new RAM card
A tornado destroyed many
CORRECT ANSWER GETS BRAINLIEST PLEASE HELP !
structures in a small Texas
town. Which type of engineer should be called in to collect
evidence in order to prevent this level of damage in the future?
A.chemical engineer
B.biomedical engineer
C.materials engineer
D.forensic engineer
Answers
Answer:
D is your answer because I'm an expert
Answer:
D. forensic engineer
Explanation:
Because I know the answer I got it right
Do any one know why people don't buy esobars??
Answers
Answer:
no
Explanation:
this is not a real qestion