open the word document student word comp cap1 employee handbook.docx downloaded with this project. be sure that rulers and formatting marks display.
Answers
The internet has a ton of functions. Anyone may access a free version of Microsoft Word online thanks to Microsoft.
Why would someone utilize a word document?Microsoft Word, sometimes known as MS Word, is a well-known word processing tool that is mostly used to create documents, including brochures, letters, learning activities, quizzes, tests, and homework assignments for students. It was first made available in 1983 and is a part of the Microsoft Office package.
A word document format is what?Microsoft Word documents, which are a component of the Microsoft Office Suite of programs, use the DOC and DOCX file extensions. Data for word processing is stored in DOCX/DOC files.
To know more about Microsoft Word visit :-
https://brainly.com/question/1423849
#SPJ4
Related Questions
Under the rules of parliamentary procedure, it is the responsibility of the secretary to keep accurate notes of the meeting.
A.
True
B.
False
Answers
It TRUE to state that Uunder the rules of parliamentary procedure, it is the responsibility of the secretary to keep accurate notes of the meeting.
What is parliamentary procedure?Parliamentary process refers to the recognized norms, ethics, and practices that govern meetings of a legislature or institution. Its goal is to allow for orderly discourse on issues of relevance to the organization, and so to arrive at the majority's sense or will on these issues.
Subsidiary motions that influence the primary motion under consideration. Privileged motions are critical problems that must be addressed swiftly, even if they disrupt ongoing activity. Incidental motions that are related to the company in various ways. Motions to reconsider a matter before the assembly
Learn more about parliamentary procedure:
https://brainly.com/question/23265511
#SPJ1
on React
1) Create counter and an increment button, default value of the counter would be 1, clicking on increment button adds 5 to the counter. The max value of the counter would be 20, after reaching this value , counter would not increment. Add a reset button which would set the counter value to 1.
[8:53 PM]
2) Create a button with label “true” , clicking on the button toggle the value from “true” => “false” and “false” => “true”.(edited)
techsith (patel) — 03/03/2021
3) Create a counter and a button. clicking on the button increments the counter by one. double clicking on the button resets the counter to 0
Answers
Answer:too many words ahhh
Explanation:
(assuming jsx)
function Buttons (props) {
return(
{props.counterValue}
counter
increment
reset
);
}
var counterValue = 1;
function addup(a){
if(counterValue + a <= 20){
counterValue += a;
} else if (counterValue + a > 20){
//do nothing
}
ReactDOM.render(
,
document.getElementById('root')
);
}
function reset() {
counterValue = 1;
ReactDOM.render(
,
document.getElementById('root')
);
}
How does Wireshark differ from NetWitness Investigator?
Answers
Answer is given below
Explanation:
Wireshark differ from NetWitness Investigator because Windshark shows a detailed view of individual packets. WireShark captures live traffic and displays the results at the packet level. Netwitness shows a high-level view and can be compared to the new packet capture NetWitiness Investigator provides a comprehensive overview of previously tracked traffic that can be used to view anomalies, compliance and attacks.https://www.celonis.com/solutions/celonis-snap
Using this link
To do this alternative assignment in lieu of Case 2, Part 2, answer the 20 questions below. You
will see on the left side of the screen a menu for Process Analytics. Select no. 5, which is Order
to Cash and click on the USD version. This file is very similar to the one that is used for the BWF
transactions in Case 2, Part 2.
Once you are viewing the process analysis for Order to Cash, answer the following questions:
1. What is the number of overall cases?
2. What is the net order value?
Next, in the file, go to the bottom middle where you see Variants and hit the + and see what it
does to the right under the detail of variants. Keep hitting the + until you see where more than a
majority of the variants (deviations) are explained or where there is a big drop off from the last
variant to the next that explains the deviations.
3. What is the number of variants you selected?
4. What percentage of the deviations are explained at that number of variants, and why did you
pick that number of variants?
5. What are the specific variants you selected? Hint: As you expand the variants, you will see on
the flowchart/graph details on the variants.
6. For each variant, specify what is the percentage of cases and number of cases covered by that
variant? For example: If you selected two variants, you should show the information for each
variant separately. If two were your choice, then the two added together should add up to the
percentage you provided in question 4 and the number you provided in question 3.
7. For each variant, how does that change the duration? For example for the cases impacted by
variant 1, should show a duration in days, then a separate duration in days for cases impacted
by variant 2.
At the bottom of the screen, you see tabs such as Process, Overview, Automation, Rework, Benchmark,
Details, Conformance, Process AI, Social Graph, and Social PI. On the Overview tab, answer the
following questions:
8. In what month was the largest number of sales/highest dollar volume?
9. What was the number of sales items and the dollar volume?
10. Which distribution channel has the highest sales and what is the amount of sales?
11. Which distribution channel has the second highest sales and what is the amount of sales?
Next move to the Automation tab and answer the following questions:
12. What is the second highest month of sales order?
13. What is the automation rate for that month?
Nest move to the Details tab and answer the following questions:
14. What is the net order for Skin Care, V1, Plant W24?
15. What is the net order for Fruits, VV2, Plant WW10?
Next move to the Process AI tab and answer the following questions:
16. What is the number of the most Common Path’s KPI?
17. What is the average days of the most Common Path’s KPI?
18. What other information can you get off this tab?
Next move to the Social Graph and answer the following questions:
19. Whose name do you see appear on the graph first?
20. What are the number of cases routed to him at the Process Start?
Answers
1. The number of overall cases are 53,761 cases.
2. The net order value of USD 1,390,121,425.00.
3. The number of variants selected is 7.4.
4. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. Seven variants explain 87.3% of the total variance, including order, delivery, credit limit, material availability, order release, goods issue, and invoice verification.
10. January recorded the highest sales volume, with 256,384 items sold for USD 6,607,088.00. Wholesale emerged as the top distribution channel, followed by Retail.
12. December stood out as the second-highest sales month,
13. with an automation rate of 99.9%.
14. Notable orders include Skin Care, V1, Plant W24 (USD 45,000.00) and
15. Fruits, VV2, Plant WW10 (USD 43,935.00).
17. The most common path had a KPI of 4, averaging 1.8 days.
18. This data enables process analysis and improvement, including process discovery, conformance, and enhancement.
19. The Social Graph shows Bob as the first name,
20. receiving 11,106 cases at the Process Start.
1. The total number of cases is 53,761.2. The net order value is USD 1,390,121,425.00.3. The number of variants selected is 7.4. The percentage of the total variance explained at 7 is 87.3%. Seven variants were selected because it provides enough information to explain the majority of the deviations.
5. The seven specific variants that were selected are: Order, Delivery and Invoice, Check credit limit, Check material availability, Order release, Goods issue, and Invoice verification.6. Below is a table showing the percentage of cases and number of cases covered by each variant:VariantPercentage of casesNumber of casesOrder57.2%30,775Delivery and Invoice23.4%12,591Check credit limit5.1%2,757
Check material availability4.2%2,240Order release4.0%2,126Goods issue2.4%1,276Invoice verification1.7%9047. The duration of each variant is as follows:VariantDuration in daysOrder24Delivery and Invoice3Check credit limit2Check material availability1Order release2Goods issue4Invoice verification1
8. The largest number of sales/highest dollar volume was in January.9. The number of sales items was 256,384, and the dollar volume was USD 6,607,088.00.10. The distribution channel with the highest sales is Wholesale and the amount of sales is USD 3,819,864.00.
11. The distribution channel with the second-highest sales is Retail and the amount of sales is USD 2,167,992.00.12. The second-highest month of sales order is December.13. The automation rate for that month is 99.9%.14. The net order for Skin Care, V1, Plant W24 is USD 45,000.00.15.
The net order for Fruits, VV2, Plant WW10 is USD 43,935.00.16. The number of the most common path’s KPI is 4.17. The average days of the most common path’s KPI is 1.8 days.18. Additional information that can be obtained from this tab includes process discovery, process conformance, and process enhancement.
19. The first name that appears on the Social Graph is Bob.20. The number of cases routed to Bob at the Process Start is 11,106.
For more such questions deviations,Click on
https://brainly.com/question/24251046
#SPJ8
In the space below, write the formula that needs to be added to the blank cells under the fourth column of the table. E2020 computer apps hands on assignment will mark brainliest
Answers
Answer:
=SUM(LEFT)*1.15
Explanation:
What's the best way to automatically space many vector objects evenly?
Layer palette
I Align tool
Manually measure using rulers
Distribute tool
Answers
Answer:
Explanation:
The best way to automatically space many vector objects evenly in most vector graphic design software would be to use alignment tools or distribute spacing options.
For example, in Adobe Illustrator, you can select multiple objects, go to the "Align" panel, and choose the "Distribute Horizontally" or "Distribute Vertically" option to distribute the objects evenly based on the spacing between their edges. Some software also has "Distribute Space" options which allow you to set a specific amount of space between objects.
In Inkscape, you can use the "Distribute Nodes Equidistantly" feature in the "Extensions" menu to evenly distribute objects along a path.
It's always a good idea to experiment with different options in your software to determine what works best for your specific project.
open the taxformwithgui.py file and write a GUI-based program that implements the tax calculator program shown in the figures below
Answers
Using the knowledge in computational language in python it is possible to write a code that open the taxformwithgui.py file and write a GUI-based program that implements the tax calculator.
Writting the code:Class TaxCalculator(EasyFrame):
def __init__(self):
"""Sets up the window and the widgets."""
EasyFrame.__init__(self, title="Tax Calculator")
# Label and field for the income
self.addLabel(text="Income", row=0, column=0)
# Label and field for the tax
# The event handler method for the button
def computeTax(self):
"""Obtains the data from the input fields and uses
See more about python at brainly.com/question/18502436
#SPJ1


A Meera array is defined to be an array containing only numbers as its elements and for all n values in the array, the value n*2 is not in the array. So [3, 5, -2] is a Meera array because 3*2, 5*2 or 2*2 are not in the array. But [8, 3, 4] is not a Meera array because 2*4=8 and both 4 and 8 are elements found in the array. Write a function that takes an array of numbered elements and prints “I am a Meera array” in the console if its array does NOT contain n and also n*2 as value. Otherwise, the function prints “I am NOT a Meera array” ○ Test 1: checkMeera([10, 4, 0, 5]) outputs “I am NOT a Meera array” because 5 * 2 is 10 ○ Test 2: checkMeera([7, 4, 9]) outputs “I am a Meera array” ○ Test 1: checkMeera([1, -6, 4, -3]) outputs “I am NOT a Meera array” because -3 *2 is -6
Answers
The program based on the question requirements:
The Programfunction checkMeera(arr) {
for (let num of arr) {
if (arr.includes(num*2)) {
console.log("I am NOT a Meera array");
return;
}
}
console.log("I am a Meera array");
}
The function takes an array as input and iterates through each element using a for-of loop.
For each element, it checks if its double is also present in the array using the includes() method.
If found, the function prints "I am NOT a Meera array" and returns. If no such element is found, the function prints "I am a Meera array".
Read more about programs here:
https://brainly.com/question/23275071
#SPJ1
If a business wanted to play an artist's song in the background of their website, it must first consider the ? of the music to ensure no laws are being brokeb
Answers
Answer:
copyright
Explanation:
The main issues covered by IT law are: Hardware licensing Data privacy Department security True False
Answers
The main issues covered by IT law are: Hardware licensing, Data privacy, Department security is a true statement.
What topics are addressed by cyber law?There are three main types of cyberlaw:
Human-targeted crimes (e.g.: harassment, stalking, identity theft) Vandalism of property (e.g.: DDOS attacks, hacking, copyright infringement) The theft from the govt (e.g.: hacking, cyber terrorism)Cyber law includes provisions for intellectual property, contracts, jurisdiction, data protection regulations, privacy, and freedom of expression. It regulates the online dissemination of software, knowledge, online safety, and e-commerce.
Note that some Internet security issues that must be considered are:
Ransomware Attacks. IoT Attacks. Cloud Attacks. Phishing Attacks.Software Vulnerabilities, etc.Learn more about IT law from
https://brainly.com/question/9928756
#SPJ1
When law enforcement becomes involved, the need may arise to freeze systems as part of the evidence. There is also the likelihood that the incident will become known publicly. Do you think these issues play a significant part in the decision to involve law enforcement? Why or why not? Can you name some situations in which you believe that large organizations have decided not to involve law enforcement?
Answers
Answer:
Costs will cover a need for more customer data. The further explanation is given below.
Explanation:
It's the greatest problem for almost every company to provide the data with security. This is possible for highly trained practitioners and the technical staff to take charge of it. Complicated technologies would have been going to run together again to withstand these types of jobs.Such problems play a major part in the decision-making process affecting the law enforcement authorities to locate the suspects to strengthen the organization.To do something like this, there seem to be a lot of other good initiatives out there doing it.There have been some cases in which major corporations have chosen not to include law enforcement:
There are many more electronic corruption going on, including money robbery, asset fraud, as well as machine assaults. In such a bigger case, numerous institutions, such as large-scale ones, have gone through these circumstances to evaluate law enforcement to come to terms with cybersecurity.what two QuickBooks Online payroll subscription levels include QuickBooks time
Answers
The two QuickBooks Online payroll subscription levels include QuickBooks time are:
Online Payroll Premium Elite subscriptionWhat is this about?QuickBooks Time mobile access is known to be commonly made up of one's QuickBooks Online Payroll Premium and also one's QuickBooks Elite subscription that is said to be given at no additional cost.
Therefore, The two QuickBooks Online payroll subscription levels include QuickBooks time are:
Online Payroll Premium Elite subscriptionLearn more about QuickBooks from
https://brainly.com/question/24441347
#SPJ1
What is the relationship model in this ER digram?

Answers
Answer:
ER (ENTITY RELATIONSHIP)
Explanation:
An ER diagram is the type of flowchart that illustrates how "entities" such a person, object or concepts relate to each other within a system
1. Design a DC power supply for the Fan which have a rating of 12V/1A
Answers
To design a DC power supply for a fan with a rating of 12V/1A, you would need to follow these steps:
1. Determine the power requirements: The fan has a rating of 12V/1A, which means it requires a voltage of 12V and a current of 1A to operate.
2. Choose a transformer: Start by selecting a transformer that can provide the desired output voltage of 12V. Look for a transformer with a suitable secondary voltage rating of 12V.
3. Select a rectifier: To convert the AC voltage from the transformer to DC voltage, you need a rectifier. A commonly used rectifier is a bridge rectifier, which converts AC to pulsating DC.
4. Add a smoothing capacitor: Connect a smoothing capacitor across the output of the rectifier to reduce the ripple voltage and obtain a more stable DC output.
5. Regulate the voltage: If necessary, add a voltage regulator to ensure a constant output voltage of 12V. A popular choice is a linear voltage regulator such as the LM7812, which regulates the voltage to a fixed 12V.
6. Include current limiting: To prevent excessive current draw and protect the fan, you can add a current-limiting circuit using a resistor or a current-limiting IC.
7. Assemble the circuit: Connect the transformer, rectifier, smoothing capacitor, voltage regulator, and current-limiting circuitry according to the chosen design.
8. Test and troubleshoot: Once the circuit is assembled, test it with appropriate load conditions to ensure it provides a stable 12V output at 1A. Troubleshoot any issues that may arise during testing.
Note: It is essential to consider safety precautions when designing and building a power supply. Ensure proper insulation, grounding, and protection against short circuits or overloads.
For more such answers on design
https://brainly.com/question/29989001
#SPJ8
Which results are expected in a personality test but not a skills assessment?
Answers
Answer:
openness, conscientiousness, extraversion
Explanation:
A personality test is defined as a test that is used to assess the human personality. It is designed as the techniques to measure characteristics patterns of the traits that various people shows at different situations or environments.
A skill assessment test is used to test the abilities and the skill sets of people to perform a particular tasks given to them. It is measuring the knowledge and skills of a person.
The personality test are carried out to test how human behave and what traits they show in certain conditions. Thus openness, extra version and conscientiousness are some of the traits that people usually shows in a personality test. Thus they are the results that are expected by an individual of a personality test.
Create a Java program that takes a list of integers as input from the user and outputs whether the list contains all even numbers, odd numbers, or neither. The input begins with the number of integers that will be stored in the list followed by the numbers to be stored in the array.
Answers
Answer:
This question is answered in Java programming language
import java.util.Scanner;
public class Main{
public static void NumberTypes(int[]myarray){
int evennum = 0; int oddnum = 0;
for(int i = 1;i<=myarray[0];i++){
if(myarray[i]%2==0){ evennum++;}
else{ oddnum++;}
}
if(evennum == 0 && oddnum!=0){ System.out.print("Odd List"); }
else if(evennum != 0 && oddnum==0){ System.out.print("Even List"); }
else if(evennum != 0 && oddnum!=0){ System.out.print("None"); }
}
public static void main(String [] args){
int num;
Scanner input = new Scanner(System.in);
System.out.print("Length of list: ");
num = input.nextInt();
int [] myarray = new int[num+1];
myarray[0] = num;
for(int i = 1;i<num+1;i++){
myarray[i] = input.nextInt();
}
NumberTypes(myarray);
}
}
Explanation:
This question is answered in Java and it uses function to answer the question.
The name of the function is NumberTypes
The program starts here
import java.util.Scanner;
public class Main{
The function NumberTypes starts here
public static void NumberTypes(int[]myarray){
This line initializes even and odd to 0
int evennum = 0; int oddnum = 0;
The following iteration iterates through the array
for(int i = 1;i<=myarray[0];i++){
This checks if current array element is even. If yes, even variable is incremented by 1
if(myarray[i]%2==0){ evennum++;}
This checks if current array element is odd. If yes, odd variable is incremented by 1
else{ oddnum++;}
}
If even is 0 and odd is not 0. The list is purely even number
if(evennum == 0 && oddnum!=0){ System.out.print("Odd List"); }
If odd is 0 and even is not 0. The list is purely odd number
else if(evennum != 0 && oddnum==0){ System.out.print("Even List"); }
If even and odd are not 0. The list is purely neither even nor odd
else if(evennum != 0 && oddnum!=0){ System.out.print("None"); }
}
The main method begins here
public static void main(String [] args){
This declares num; the length of array as integer
int num;
Scanner input = new Scanner(System.in);
This prompts the user for length of the array
System.out.print("Length of list: ");
This gets the length of the array
num = input.nextInt();
This declares the array as integer
int [] myarray = new int[num+1];
This initializes index 0 as the length of the array
myarray[0] = num;
The following iteration gets input for the array
for(int i = 1;i<num+1;i++){
myarray[i] = input.nextInt();
}
This calls the function
NumberTypes(myarray);
}
}
dion training has recently replaced the batteries in their rack-mounted ups in their data center. which of the following should their technicians do to dispose of the depleted batteries?
Answers
Li batteries cannot be recycled at many facilities. They need safe disposal because it allows them to safely segregate the materials for later usage.
Which of the following methods is appropriate for battery disposal?Do not dispose of lead-acid batteries in the garbage or municipal recycling bins; instead, return them to a battery retailer or your community's household hazardous waste collection programme.
How should a bad battery be disposed of?Instead, transport the battery or gadget to your local household hazardous waste (HHW) recycling facility by placing it in a clear plastic bag (one per bag). Inquire if damaged batteries are accepted at a Call2Recycle drop-off location in your area. For any reason, don't throw them out.
To know more about recycled visit:-
https://brainly.com/question/29972832
#SPJ1
Should one own a smart home device
What are some security issues that one can find bothersome with these types of devices?
Answers
Yes, one can have or should one own a smart home device
Some security issues that one can find bothersome with these types of devices are:
Privacy concernsVulnerabilities to hackingLack of updatesWhat are the security issues?Smart home tools offer usefulness and can help create growth easier, but they further create freedom risks that should be deliberate.
Some freedom issues so that find bothersome accompanying smart home tools contain:
Lastly, in terms of Privacy concerns: Smart home ploys may accumulate individual dossier, such as custom patterns and choices, that could be joint accompanying after second-party parties for point or direct at a goal buildup or added purposes.
Learn more about security issues from
https://brainly.com/question/29477357
#SPJ1
If you buy $1000 bicycle, which credit payoff strategy will result in your paying the least
Answers
If you buy $1000 bicycle, the credit payoff strategy that will result in your paying the least is option c) Pay $250 per month until it's paid off.
Which credit card ought to I settle first?You can lower the total amount of interest you will pay over the course of your credit cards by paying off the one with the highest APR first, then moving on to the one with the next highest APR.
The ways to Pay Off Debt More Quickly are:
Pay more than the required minimum.more than once per month.Your most expensive loan should be paid off first.Think about the snowball approach to debt repayment.Keep track of your bills so you can pay them faster.Learn more about credit payoff strategy from
https://brainly.com/question/20391521
#SPJ1
See full question below
If you buy $1000 bicycle, which credit payoff strategy will result in your paying the least
a) Pay off the bicycleas slowly as possible
b) Pay $100 per month for 10 months
c) Pay $250 per month until it's paid off
What is meant by computer generation?
Answers
Answer:
The development of computer took place into 5 phases which is known as generation of computer.
Explanation:
From first generation computer till now, development of computer took place in 5 distinct which is also know as generation of computer.
Generation in computer terminology is a change in technology a computer is/was being used. Initially, the generation term was used to distinguish between varying hardware technologies. Nowadays, generation includes both hardware and software, which together make up an entire computer system.
Which of the following techniques is the best fit for monitoring traffic on switches with large volumes of traffic? A) SFTP;B) portTAP C)SRTP
Answers
B) portTAP techniques is the best fit for monitoring traffic on switches with large volumes of traffic.
The most common methods for gaining access to monitoring data are a test access port (Tap) or a switched port analyzer (SPAN) port. A tap is a device that copies network data passively without changing anything. Once you have installed it, you are finished. Network TAPs are a piece of equipment that sits in a business segment, between two machines (such as a switch, firewall, or switch), allowing you to access and monitor company traffic. They are meticulously designed. By transmitting both the send and receive data streams simultaneously on separate dedicated channels, TAPs guarantee that all data reaches the monitoring or security device in real time. A network appliance (switch) has designated ports that are programmed to send a copy of network packets (or an entire VLAN) seen on one port to another port, where they can be analyzed. SPAN, or Switch Port Analyzer, is another name for port mirroring. TAP and/or SPAN are the first steps in achieving pervasive visibility across your entire network infrastructure. You can send traffic that has been detected over one or more Range ports or TAPs to the Gigamon Bird of Prey Profound Recognizability Pipeline for evaluation, monitoring, and retrieval.
To know more about portTAP visit
brainly.com/question/13025421
#SPJ4
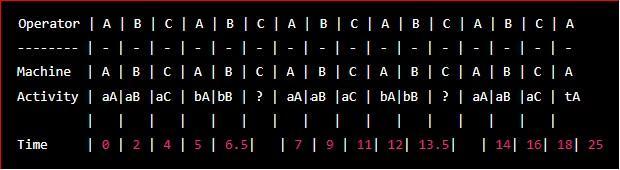
use a multiple activity chart to illustrate how one operator can tend machine A,machine B and machine C during repeating cycle , based on the following data:aA=2 minute,aB=2.5 minute, aC =3minute ;bA =1 minute,bB =1.5 minute ;tA=7 minute ,tB=8minute and tc=9 minute.what is the length of the repeating cycle?
Answers
The operator will tend machines A, B, and C in a repeating cycle with a length of 24 minutes.
What is length of repeating cycle?
A multiple activity chart is a useful tool for visualizing and analyzing the activities of one or more operators performing different tasks during a cycle.
In this scenario, we have one operator who is tending three machines, A, B, and C.
The operator spends different amounts of time at each machine, as follows:
aA = 2 minutes, aB = 2.5 minutes, and aC = 3 minutes.
The machines themselves have different processing times, bA = 1 minute, bB = 1.5 minutes, and bC = unknown.
To create a multiple activity chart, we first create a horizontal axis representing time, and then plot each activity as a vertical line.
The length of each line corresponds to the time required for that activity, and the position of each line indicates when the activity occurs relative to the other activities.
Based on the data provided, we can create the following multiple activity chart:
figure of multiple activity chart is attested.
The chart shows that the operator begins at machine A, spending 2 minutes performing activity aA before moving on to machine B for 2.5 minutes to perform activity aB. They then move to machine C for 3 minutes to perform activity aC before returning to machine A for another cycle.
The processing times for machines A and B are known, so we can calculate the time it takes to complete one cycle as follows:
Cycle time = (aA + bA + aB + bB + aC + bC) x n
= (2 + 1 + 2.5 + 1.5 + 3 + bC) x n
= (10 + bC) x n
where n is the number of cycles. To determine the value of bC, we can use the fact that the total cycle time must be a multiple of the individual machine cycle times, tA, tB, and tC:
LCM(tA, tB, tC) = LCM(7, 8, 9) = 504
Therefore, the operator shall tend machines A, B, and C in a repeating cycle with a length of 24 minutes.
To know more about Cycle time, visit: https://brainly.com/question/29310532
#SPJ1
Adam is so good at playing arcade games that he will win at every game he plays. One fine day as he was walking on the street, he discovers an arcade store that pays real cash for every game that the player wins - however, the store will only pay out once per game. The store has some games for which they will pay winners, and each game has its own completion time and payout rate. Thrilled at the prospect of earning money for his talent, Adam walked into the store only to realize that the store closes in 2 hours (exactly 120 minutes). Knowing that he cannot play all the games in that time, he decides to pick the games that maximize his earnings
Answers
Answer:
line = sys.stdin.readline()
print(line)
Explanation:
The first line of input is always an integer denoting many lines to read after the first line. In our sample test case, we have 6 in the first line and 6 lines after the first line, each having a game, completion_time and payout_rate.
In each data line, the game, completion_time and payout_rate are separated by a ','(comma).
The games board may change but the store still closes in 120 minutes.
Input
6
Pac-man,80,400
Mortal Kombat,10,30
Super Tetris,25,100
Pump it Up,10,40
Street Fighter II,90,450
Speed Racer,10,40
Output Explanation
Print the game names that earn him the most into the standard output in alphabetical order
Output
Mortal Kombat
Pump it Up
Speed Racer
Street Fighter II
Python:
import sys
line = sys.stdin.readline()
print(line)
What was the in-app phrase listed as SC answer?
A) MasterCard
B) No fee
C) Apple Pay
Answers
Answer:
A.master card
Explanation:
masterCard because
Write an if-else statement with multiple branches. If year is 2101 or later, print "Distant future" (without quotes). Otherwise, if year is 2001 or greater, print "21st century". Otherwise, if year is 1901 or greater, print "20th century". Else (1900 or earlier), print "Long ago". Sample output with input: 1776 Long ago
Answers
Answer:
year = int(input("Enter a year: "))
if year >= 2101:
print("Distant future")
elif year >= 2001:
print("21st century")
elif year >= 1901:
print("20th century")
else:
print("Long ago")
Explanation:
*The code is in Python.
Ask the user to enter a year
Use if-else statement to check the year and print the appropriate message given for each condition. If year is greater than or equal to 2101, print "Distant future". If year is greater than or equal to 2001, print "21st century". If year is greater than or equal to 1901, print "20th century". Otherwise, print "Long ago".
What type of memory can support quad, triple, and dual channels?
Answers
Answer:
The type of memory can support quad, triple, and dual channels is DDR3
Explanation:
The type of memory that can support quad, triple, and dual channels is DDR3 memory.
What is multichannel memory?Multichannel memory architecture is a technology in the domains of digital electronics and computer hardware that boosts the data transfer rate between the DRAM memory and the memory controller by adding more channels of communication between them.
Dual-channel memory, also known as multichannel memory, is a DDR, DDR2, or DDR3 chipset installed on a computer's motherboard that provides random access memory (RAM) with two dedicated data channels to improve speed.
DDR3 Synchronous Dynamic Random-Access Memory, which has been in use since 2007, is a form of synchronous dynamic random-access memory with a high bandwidth interface.
Therefore, DDR3 memory is a type of memory that can support quad, triple, and dual channels.
To learn more about multichannel memory, refer to the link:
https://brainly.com/question/19403943
#SPJ6
cutting of trees is bad or not bad
Answers
Answer:
bad
Explanation:
it gives out air and oxygen
Flowchart in programming
Answers
Answer:
?
Explanation:
The software used to provide visual support such as slide show during lectures
Answers
Answer:
microsoft powerpoint
Explanation:
why it is important to follow the procedures and techniques inmaking paper mache?
pleaseee help i needed it right now
Answers
Answer:
otherwise it will go wrong