please describe the role of games in modern society!
Answers
Related Questions
How does a resident virus differ from a non-resident virus? !!!25 POINTS!!!!!
A) Resident viruses simply disrupt operations while non-resident viruses will control hosts.
B)Resident viruses will control hosts while non-resident viruses simply disrupt operations.
C)Resident viruses find networks to infect while non-resident viruses load themselves into memory.
D)esident viruses load themselves into memory while non-resident viruses find networks to infect.
Answers
Answer:
The correct answer is **D)** Resident viruses load themselves into memory while non-resident viruses find networks to infect. A resident virus is a type of computer virus that’s deployed and resides within a computer’s random access memory (RAM). A non-resident computer virus, on the other hand, is a type of computer virus that doesn’t reside within a computer’s RAM. Non-resident computer viruses can still be deployed within RAM, but they don’t stay there.
QUICK ANSWER- what is the function of GUI
Answers
Answer:
GUI stands for graphical user interface. The function of the GUI is almost like when your right click on your computer and click inspect and it pulls up your computers coding, and codes. That is what GUI basically is it shows a visual presentation of all available functions of a software. operating system like ( Windows 7, Windows XP) or program.
Explanation:
Hope this helped : )
how has social media changed my journalism looks like?
A. journalists use poor grammar online
B. journalist can be everyday people
C. Only journalists from major news stations report the news
D. Journalists can dress down while reporting the news
This is for a test, so I need to get answers fast.
Please help me
Answers
Answer d
Explanation:
1. What do you think is the most important event in the history of the internet? What event has had the biggest impact on your daily life?
Answers
Answer:
The biggest event in internet history was YuTubers punching each other in the face. Months of hype came to a peak Saturday for the self-declared “biggest event in internet history” a boxing match between two YuTube celebrities in Manchester, England.
Explanation:
There is no particular event but the whole journey till now which shaped my personality. Every person even if they are the worst has something good in them.
The impact it has had:
Developed into the globally used Internet which is now integrated into modern society and is seen as an essential for good quality of life.
Digital and analog audio recordings have pros and cons. Do you think the pros of digital recordings outweigh the cons and therefore prefer digital audio recordings? Or, do you think the cons outweigh the pros and therefore you prefer analog audio recordings? Explain. ( USE C.E.R *Claim, Evidence, Reasoning* )
Answers
I think the pros of digital recordings outweigh the cons! I prefer digital audio recordings over analog audio recordings because analog recordings require more financing and preservation. Compared to digital recordings, analog recording equipment is more expensive and the tape deteriorates over time. Which to me personally, doesn't seem to be worth the amount of effort since it's such a process to go through. You can possibly go into debt due to that. Digital recording equipment, on the other hand, is more affordable. It's less time-consuming and although it does have its disadvantages, they're minor. Digital recordings can be stored online. Its data get corrupted? You can get it back! It won't cost you anything.
Critical Thinking Questions
1.Can a syntax error occur in a block-based code? Why or why not?
2.What are some strategies that you can use when you debug a program?
3.How would you describe the difference between a syntax error and a logic error?
4.What are some real-life situations that require a program that is iterative? Include at 5.least three examples in your answer.
6.How would you describe the relationship between blocks of code and commands?
Answers
Answer:
If you don’t know the answer, don’t try to answer, *sigh* some people these days...
Can a syntax error occur in a block-based code? Why or why not?
No. Because block code is not actual code, it’s like a simplified version.
What are some strategies that you can use when you debug a program?
When there is a bug, don’t look through the whole code, you should focus on the area that may be causing the bug.
How would you describe the difference between a syntax error and a logic error?
Syntax error is when the rules of the language aren’t followed (like using a variable wrong or forgetting a colon.)
A logic error is a bug within the structure or algorithm of a code.
What are some real-life situations that require a program that is iterative? Include at least three examples in your answer.
Apple releases different version of the iPhone to make it work better.
Coke uses different formulations of Coca Cola to get the best tasing version.
A cook may change a recipe to make it taste better.
How would you describe the relationship between blocks of code and commands?
Code makes the block, commands run the blocks.
Explanation:
What happens when you try mixing colors (color3, Vector3) in tech? What happens
A. It fades with the color
B. It prints an error in output and chooses a random color
C. It reverts itself
D. It layers with a random color
E. None of the above
Answers
Answer:
A
Explanation:
yeah help me please......................
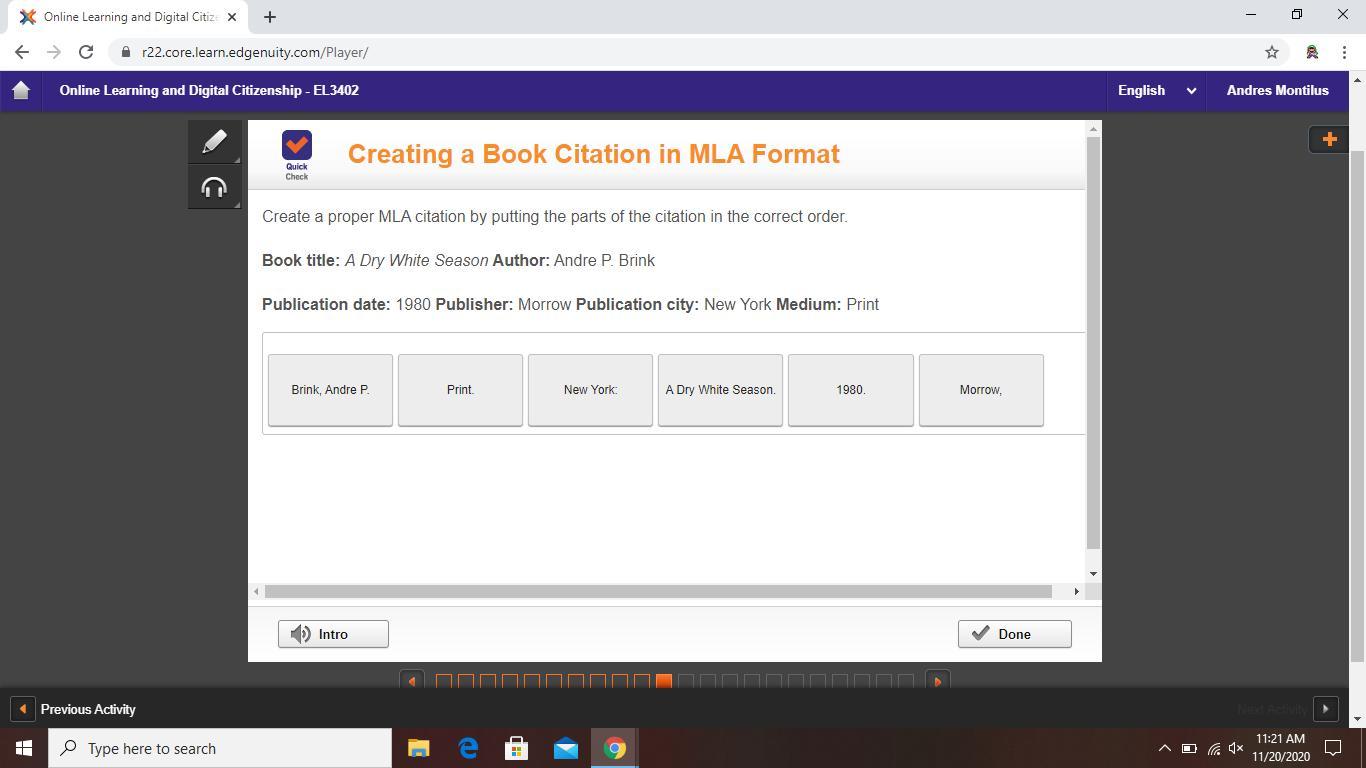
Answers
what computer languages should i start with + learn if i want to be a pentester/programmer and where can i learn them
Answers
Answer:
Chinese
Explanation:
I'm not sure I understand your question. Good day.
How could this situation have been de-escalated?
What could the different people involved have done?
Felicia and Jen are friends from school. They both audition for the lead role in the school play. The next day, the drama teacher, Mr. Adler, posts the final cast list, showing that Felicia was selected for the role. Felicia posts a photo of the list on social media with the caption "Guess who made LEAD ROLE!! ME!" Other students at her school see the post and make comments.
The comments continue to come in. People start responding with #teamjen and #teamfelicia hashtags. Later, in response to Jayden's comments, Felicia posts an embarrassing picture of Jayden and calls him out for failing Mr. Adler's class.
Answers
You can find this out on Brainly! Recycling one glass jar saves enough energy to watch television for _ hours It's one of the fun facts!
Answers
Recycling one glass jar saves enough energy to watch television for 3 hours.
In a minimum of 250 words, discuss the technological problems that can occur when consumers emphasize on speed over security.
Answers
1. Vulnerabilities and Breaches: Emphasizing speed often means sacrificing robust security measures. This can lead to vulnerabilities in software, applications, or systems that attackers can exploit. Without adequate security measures, data breaches become more likely, exposing sensitive information such as personal data, financial records, or trade secrets. The aftermath of a breach can be detrimental, including reputational damage, legal consequences, and financial losses.
2. Malware and Phishing Attacks: When speed takes precedence, consumers may overlook potential malware or phishing attacks. By rushing through security checks or bypassing cautionary measures, they inadvertently expose themselves to malicious software or fraudulent schemes. These attacks can compromise personal information, hijack devices, or gain unauthorized access to networks, resulting in financial losses and privacy violations.
3. Inadequate Authentication and Authorization: Speed-centric approaches might lead to weak or simplified authentication and authorization mechanisms. For instance, consumers may choose easy-to-guess passwords or reuse them across multiple platforms, making it easier for attackers to gain unauthorized access. Additionally, authorization processes may be rushed, granting excessive privileges or overlooking necessary access controls, creating opportunities for unauthorized users to exploit system vulnerabilities.
4. Neglected Updates and Patches: Prioritizing speed often means neglecting regular updates and patches for software and systems. By delaying or avoiding updates, consumers miss out on critical security fixes and vulnerability patches. Hackers actively exploit known vulnerabilities, and without timely updates, devices and systems remain exposed to these threats, making them easy targets.
5. Lack of Secure Development Practices: When speed becomes the primary concern, secure development practices might take a backseat. Security testing, code reviews, and quality assurance measures may be rushed or ignored, leading to the inclusion of vulnerabilities in the software or application itself. These vulnerabilities can be exploited by attackers to gain unauthorized access or execute malicious activities.
To mitigate these problems, it is essential to strike a balance between speed and security. Consumers should prioritize security measures such as using strong passwords, enabling multi-factor authentication, regularly updating software, and being cautious of suspicious links or emails. Service providers and developers must also prioritize security in their products and services by implementing secure coding practices, conducting thorough security assessments, and promptly addressing vulnerabilities. Ultimately, a comprehensive approach that values both speed and security is crucial for maintaining a safe and efficient technological ecosystem.
Explanation:
--> used brainly simplify :D
Consumers prioritizing speed over security can lead to several technological problems. This includes vulnerabilities and breaches where attackers can exploit weaknesses in software or systems. Malware and phishing attacks become more likely when security measures are overlooked. Weak or simplified authentication and authorization methods can make it easier for unauthorized users to gain access. Neglecting updates and patches leaves devices and systems vulnerable to known threats. Lastly, rushing through secure development practices may result in the inclusion of vulnerabilities in the software itself. To address these issues, consumers should use strong passwords, update their software regularly, and be cautious of suspicious links or emails. Service providers and developers should prioritize security by conducting thorough security assessments and promptly addressing vulnerabilities. Striking a balance between speed and security is crucial for a safe and efficient technological environment.
Walt needs to ensure that messages from a colleague in another organization are never incorrectly identified as spam. What should he do?
A.Configure a safe recipient.
B.Configure a blocked sender.
C.Configure a safe sender.
D.Do nothing.
Answers
Answer:
C. Configure a safe sender
Explanation:
It’s dabest thing to do
As per the given scenario, Walt should need to configure a safe sender. The correct option is C.
What is configuration?A system's configuration in communications or computer systems refers to how each of its functional elements is organised in relation to their nature, number, and distinguishing features.
Configuration frequently involves picking the right hardware, software, firmware, and documentation.
A person, group, or organisation that starts the communication is known as the sender. The success of the message stems primarily from this source.
The communication is influenced by the sender's experiences, attitudes, knowledge, competence, perspectives, and culture.
Walt must take care to prevent messages from a colleague in a different organisation from ever being mistakenly classified as spam. He ought to set up a secure sender.
Thus the correct option is C.
For more details regarding configuration, visit:
https://brainly.com/question/13410673
#SPJ2
Experts believe robots and AI will continue taking over many of the human jobs we know today. What changes should be made to K-12 education to ensure students are prepared for the future? What courses or skills should be added? WHat should be removed? Why?
Answers
Answer:
I think they should show one subject per month so students are more prepared
Answer: some changes that should be made are dresscode , some courses should be more sports . Nothing should be removed because the kids in the future need to learn more .
Explanation:
A large company has extensive downtown office space with many conference rooms. To lower their electric bill, the company has installed a new system that automatically turns off the heat and lights in a conference room when no one is in the room. What is the simplest explanation for how the system works?
A camera in each room is connected to the security desk. When the officer on duty sees that a room is empty, they turn off the heat and lights in that room.
A small robotic device on wheels knows the building layout. It roams the offices, peeking into each conference room to see if anyone is using it. If not, the robot turns off the lights and heat.
A sensor detects and reports on movement in the room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
Every hour, the system emits a loud sound in each room. Pressing a large red button in the middle of the table turns off the sound in that room. If nobody does so within 30 seconds, the system turns off the heat and lights.
Answers
The simplest explanation for how the system works is option C: a sensor detects and reports on movement in the conference room. If there is no movement for a few minutes, the system assumes the room is empty and turns off the heat and lights.
What is the office space about?The system that automatically turns off the heat and lights in a conference room when no one is in the room is commonly referred to as an occupancy sensor. An occupancy sensor uses various technologies, such as infrared or ultrasonic, to detect the presence or absence of people in a room.
Therefore, Once the sensor detects that no one is in the conference room, it sends a signal to the control system, which then turns off the heat and lights. When someone enters the room again, the sensor detects their presence and sends a signal to turn the heat and lights back on. This system is designed to save energy by ensuring that heating and lighting are only used when needed.
Learn more about office space from
https://brainly.com/question/28885269
#SPJ1
Tests, fixes, and maintains network systems:

Answers
60 POINTS IF YOU GET IT RIGHT
PLEASE HELP ASAP!!!!!!!!
I already did the trials, and I found the loudest sound.
I will ask another question that includes the rest of the screen shots.





Answers
Answer:
You said this was 60 points but it is only 30 points :(
Explanation:
PLEASE HELP!!! What is one game you think would be hard for computers to play? (AI)
Answers
Answer:
I would say the game "Go" because it requires intuition to play.
Explanation:
Answer:
I dont play much games but probaly a game you need to think outside of the box for
Explanation:
robots arent creative
One student will be stationed near you in a coffee shop. The other student will be located two miles away from your school. You will need to communicate with one another as you coordinate this event. Pretend you have been given $650 to develop this hunt.
Research the costs of various mobile computing devices.
Write, in a report of at least 250 words, your mobile device purchase recommendations that will best suit the student communication needs of your assignment.
Upload a 250-word report about the geocache treasure hunt that includes the following:
In light of your budget, which device is the best buy for communicating with your fellow student in the coffee shop?
Which device is the best choice for communicating with your fellow student located at your school?
What trade-offs do you need to consider, such as the size of the device vs. features?
Answers
Answer:
A LG K92 5G titan Gray that also uses cricket wireless network
Explanation:
It cost 160 bucks plus tacks.
Coding with Loops Worksheet
Print | Save
Output: Your goal
You will complete a program that asks a user to guess a number.
Part 1: Review the Code
Review the code and locate the comments with missing lines (# Fill in missing code). Copy and paste the code into the Python IDLE. Use the IDLE to fill in the missing lines of code.
On the surface this program seems simple. Allow the player to keep guessing until he/she finds the secret number. But stop and think for a moment. You need a loop to keep running until the player gets the right answer.
Some things to think about as you write your loop:
The loop will only run if the comparison is true.
(e.g., 1 < 0 would not run as it is false but 5 != 10 would run as it is true)
What variables will you need to compare?
What comparison operator will you need to use?
# Heading (name, date, and short description) feel free to use multiple lines
def main():
# Initialize variables
numGuesses = 0
userGuess = -1
secretNum = 5
name = input("Hello! What is your name?")
# Fill in the missing LOOP here.
# This loop will need run until the player has guessed the secret number.
userGuess = int(input("Guess a number between 1 and 20: "))
numGuesses = numGuesses + 1
if (userGuess < secretNum):
print("You guessed " + str(userGuess) + ". Too low.")
if (userGuess > secretNum):
print("You guessed " + str(userGuess) + ". Too high.")
# Fill in missing PRINT statement here.
# Print a single message telling the player:
# That he/she guessed the secret number
# What the secret number was
# How many guesses it took
main()
Part 2: Test Your Code
Use the Python IDLE to test the program.
Using comments, type a heading that includes your name, today’s date, and a short description.
Run your program to ensure it is working properly. Fix any errors you observe.
Example of expected output: The output below is an example of the output from the Guess the Number game. Your specific results will vary based on the input you enter.
Output
Your guessed 10. Too high.
Your guessed 1. Too low.
Your guessed 3. Too low.
Good job, Jax! You guessed my number (5) in 3 tries!
When you've completed filling in your program code, save your work by selecting 'Save' in the Python IDLE.
When you submit your assignment, you will attach this Python file separately.
Part 3: Post Mortem Review (PMR)
Using complete sentences, respond to all the questions in the PMR chart.
Review Question Response
What was the purpose of your program?
How could your program be useful in the real world?
What is a problem you ran into, and how did you fix it?
Describe one thing you would do differently the next time you write a program.
Part 4: Save Your Work
Don't forget to save this worksheet. You will submit it for your assessment.
Answers
Bloxburg Build can anyone help me
Answers
PLEASE I NEED HELP WITH THIS, IS FOR TODAY

Answers
Answer:
b
Explanation:
Vocabulary List
precipitate
descent
ascent
maneuver
contemplate
enveloped
nucleus
exertion
perilous
manifestly
perpendicular
predicament
Answers
.sjjejekeiwiwkkskskdidieiiei
A data collection tool was developed to allow a small piece of data to be sent from a website to advertisers to track consumers' shopping and buying habits. This tool is called a:
A.
digital tracer.
B.
data analysis.
C.
cookie.
D.
network.
Answers
Answer:
C. cookie.
Explanation:
The data collection tool that allows a small piece of data to be sent from a website to advertisers to track consumers' shopping and buying habits is called a "cookie".
In which view are fields set up in MS Access?
Answers
Answer:On the Home tab, in the Views group, click View, and then click Design View. In the table design grid, select the field or fields that you want to use as the primary key. To select one field, click the row selector for the field that you want.
Explanation:
Answer:
Layout view and Design view are the two views in which you can make design changes to forms and reports in Microsoft Access. Though you can use either view to perform many of the same design tasks, certain tasks are easier to perform in one view than they are in the other.
Brainlist Pls!
Here, Do this for 100 points its simple just know how to use flowchart


Answers
Answer:
i dont get whats supposed to be done. If you tell me if can give u an answer, i gotchu.
Explanation:
Please specify what you need help in...
I don't see any question..
Write code that does the following: opens the number_list.txt file, reads all of the numbers (1 to 100) from the file, adds all of the numbers read from the file and displays their total. then closes the file.
Answers
The code that does the following: opens the number_list.txt file, reads all of the numbers (1 to 100) from the file, adds all of the numbers read from the file and displays their total. then closes the file is given below.
What is the code about?Below is an example Python code that should accomplish this task:
python
# Open the file for reading
with open("number_list.txt", "r") as file:
# Read all the lines and convert them to integers
numbers = [int(line) for line in file.readlines()]
# Sum up the numbers and display the total
total = sum(numbers)
print("The total is:", total)
# Close the file
file.close()
Therefore, Assuming that the number_list.txt file contains one number per line from 1 to 100, the code should read all the numbers from the file, sum them up, and display the total. Finally, the file is closed automatically when the with block is exited.
Read more about code here:
https://brainly.com/question/26134656
#SPJ1
Answer
Explanation:
I don't know
Please Help me I need it done in a few minutes Thanks

Answers
Why isn't my brainly post being answered?
Answers
Try deleting then reposting, it may not always pop up in new questions, I will have a look at the question anyway.
Hope this helps!
The variable points stores data that the user has input. what is the data type of this variable?
Answers
Answer:
Each variable has a name, a value, and a type. The value might change over time, and that's why its “variable.” Many variables store numbers and strings, like the ones above. Variables can also store other types of data, like lists, dictionaries, and Boolean values
Explanation: