question 2 a data analyst wants to store a sequence of data elements that all have the same data type in a single variable. what r concept allows them to do this?
Answers
The concept that allows a data analyst to store a sequence of data elements that all have the same data type in a single variable is known as an array.
An array is a collection of data elements of the same data type in a single variable. In computer programming, arrays are useful because they enable you to keep track of a collection of related values that have the same name.
Instead of keeping track of values with multiple variables, you can use an array to group them together and refer to them using a single name.The elements of an array are stored in contiguous memory locations and can be accessed using an index.
The index is a number that represents the position of the element in the array. The first element in the array has an index of 0, the second element has an index of 1, and so on.
Learn more about Arrays at:
https://brainly.com/question/15849855
#SPJ11
Related Questions
Na2CO3 → Na2O + what
Answers
Answer:
CO3
Explanation:
Answer:
C02
Explanation:
1. 2. 10 Snowflakes CodeHS
Does anyone have the code for this?
Thank you!
Answers
The Snowflakes problem on CodeHS involves using nested loops to create a pattern of snowflakes using asterisks.
Here is one possible solution:
The code starts by asking the user for a size input, which is used to determine the dimensions of the grid. The outer loop iterates through each row of the grid, while the inner loop iterates through each column.Inside the inner loop, there are four conditions to determine when to print an asterisk (*). The first condition checks if the current cell is on the main diagonal or one of the two diagonals next to it, and prints an asterisk if it is. The second and third conditions check if the current cell is in the top or bottom half of the grid and within the range of cells where the snowflake pattern should be printed. If the current cell does not meet any of these conditions, a space is printed instead.Finally, a newline is printed at the end of each row to move to the next line in the output.For such more questions on CodeHS
https://brainly.com/question/15198605
#SPJ11
Question:-Learning Objectives In this challenge we will use our Python Turtle skills to draw a snowflake. We will use iteration (For Loop) to recreate ?
wpa (wi-fi protected access) keys are longer than wep (wired equivalent privacy) keys, and are therefore more difficult to break. a. true b. false
Answers
The correct answer is False Due to the fact that WPA Wi-Fi Protected Access keys are longer than WEP Wired Equivalent Privacy keys, they are more arduous to crack.
By encrypting the data, wired equivalent privacy is intended to safeguard Wi-Fi transmissions by preventing outsiders from reading the messages or data stored therein. Older devices that do not support WPA or WPA2 continue to utilise WEP since it is a better security option than none at all. The following disadvantages of WEP's outdated Wi-Fi encryption technique include: Threat actors are able to access the private communications by just guessing the static key. An attacker has the ability to intercept transmissions and gather data packets. Wired Equivalent Privacy (WEP), which was formerly the norm for encryption, is no longer secure because hackers may now more easily
To learn more about Wired Equivalent Privacy click on the link below:
brainly.com/question/13025767
#SPJ4
1) Man should feed ______ to a computer in order to improve the efficiency of computer vision.
pls plz help me
Answers
Answer:images
Explanation:i saw this on the quizlet for my school
How is video compression accomplished?
Answers
Answer:
using image compression techniques on consecutive video frames
Explanation:
Which of the following best describes professional behavior in the IT field?
O teaching others about technology in order to increase IT knowledge in the community
O discouraging others from pursuing an IT career to secure your own job
O avoiding professional organizations and events to protect sensitive information
O using computer jargon when talking to a non-technical audience to show your knowledge
Answers
Answer: A is the correct answer
Explanation:
Teaching others about technology in order to increase IT knowledge in the community describes professional behavior in the IT field. The correct option is A.
What is professional behavior?Professional conduct is a type of workplace etiquette that is largely associated with polite and professional behaviour.
Whether you believe it or not, acting professionally can advance your career and increase your prospects of success in the future. There are explicit rules of behaviour in place in many organisations, but not all of them.
Professional conduct helps keep personal and professional ties distinct and keeps interactions focused on the current business situation.
Professional ethics are values that guide how an individual or group behaves in a professional setting.
Professional ethics offer guidelines for how one should behave toward other individuals and institutions in such a setting, similar to values.
Professional behaviour in the IT industry is defined as teaching others about technology in order to expand IT knowledge in the community.
Thus, the correct option is A.
For more details regarding professional behavior, visit:
https://brainly.com/question/29603041
#SPJ2
Why error occurs during transmission? Explain different types of errors with suitable examples. 5 (b) How do you detect error using CRC? Generate the CRC code for the data word 1101011011 The divisor is x4+x+1. 7
Answers
During transmission, errors occur due to a variety of factors such as atmospheric conditions, system malfunction, or network errors.
Different types of errors include Single Bit Error, Burst Error, and Burst Error Correction. Here are the different types of errors with suitable examples: Single Bit Error: It occurs when one bit of data is changed from 1 to 0 or from 0 to 1 in data transfer. This type of error is mainly caused by a small amount of interference or noise in the transmission medium. For instance, a parity bit error.Burst Error: It occurs when two or more bits are incorrect during data transmission. A Burst Error occurs when bits of data are lost or changed in groups, which can affect multiple data bits at once. It can be caused by signal loss or attenuation in fiber-optic cables. Burst Error Correction: To overcome the issue of Burst Error, Burst Error Correction is used. This method divides data into blocks to detect and fix errors. Reed-Solomon coding and Viterbi decoding are two types of burst error correction techniques. There are different techniques for error detection, and the Cyclic Redundancy Check (CRC) is one of them. CRC checks the checksum at the receiver's end to ensure that the data was not corrupted during transmission. To detect errors using CRC, follow these steps: Divide the data word by the generator polynomial. Generator polynomial: x4 + x + 1 Divide 1101011011 by x4 + x + 1 and find the remainder by using the modulo 2 division method.1101011011 10011- 10011000- 10011000- 10010100- 10010100- 10000001- 10000001- 1111100- 1111100- 1001The remainder of the above step is the CRC code of the data word, which is 1001. Therefore, the CRC code for the data word 1101011011 is 1001.
know more about type of error.
https://brainly.com/question/31751999
#SPJ11
All my progress drop does it refresh everyday pls answer ASAP
Answers
Plz plz plz help QUICKLY idk the answer and I really need help

Answers
Answer:
productivity is the correct answer
How does Google work, why does it work that way?
Answers
Answer:
Google uses automated programs called spiders or crawlers, just like most search engines, to help generate its search results. Google has a large index of keywords that help determine search results. ... Google uses a trademarked algorithm called PageRank, which assigns each Web page a relevancy score.
Answer: Google uses automated programs called spiders or crawlers, just like most search engines, to help generate its search results. Google has a large index of keywords that help determine search results. ... Google uses a trademarked algorithm called PageRank, which assigns each Web page a relevancy score.
Explanation: Google's algorithm does the work for you by searching out Web pages that contain the keywords you used to search, then assigning a rank to each page based several factors, including how many times the keywords appear on the page. ... Google references this index when a user enters a search query.
Hope this helps^^
Using Python Coding, Problem: Calculate d f /dx of f(x) = cos x + sin x Write a script that will evaluate the approximate derivative of the function f(x) = cos x + sin x, in x from 0 to 2π using 100 points, with the following approximations: • the Forward Difference approximation, d f /dxFD, • the Backward Difference approximation, d f /dxBD, and • the Central Difference approximation, d f /dxCD. Plot in the same figure the function f(x), the analytical derivative d f /dx, the approximated derivatives d f /dxFD, d f /dxBD and d f /dxCD versus x. Your plot must have an appropriate legend, axis labels and a grid. You must write your script using for or while loops.
Answers
Among the four approximations calculated in Parts 1 and 2, the central-difference approximation for both df/dx and d²f/dx² at x=2 contains no error.
To calculate the derivative of a function at a specific point, we can use numerical approximations. In Part 1, we need to calculate df/dx at x=2 using backward-, forward-, and central-difference approximations.
The Forward Difference approximation, d f /dxFD, • the Backward Difference approximation, d f /dxBD, and • the Central Difference approximation, d f /dxCD. Plot in the same figure the function f(x), the analytical derivative d f /dx, the approximated derivatives d f /dxFD, d f /dxBD and d f /dxCD versus x.
Among the four approximations, only the central-difference approximation for both df/dx and d²f/dx² at x=2 gives the correct value of 6 and -2 respectively, without any error. The forward- and backward-difference approximations introduce errors due to the approximation of the derivative using only one-sided information, while the central-difference approximation uses information from both sides, resulting in a more accurate approximation.
Learn more about central-difference approximation here:
brainly.com/question/32577505
#SPJ4
I can''t find my phone and it''s dead. Is there an app or something that you search on your computer and it can help you find it? I''ve been looking for it everywhere!
:(
Answers
Is the color grade of black or white higher?
Answers
Answer: When it comes time to color grade black and white footage, follow this one ... shooting black and white, high contrast almost always looks better.
construct a dfa that accepts all patterns that have an odd number of a’s. assume that the language alphabet only has characters a,b and machine processes an infinite tape of a’s and b’s
Answers
To construct a DFA, Deterministic Finite Automaton, that accepts all patterns with an odd number of a's over the alphabet {a, b} on an infinite tape, follow these steps:
1. Define two states: q0 (initial state) and q1 (accepting state).
2. Define the transition rules:
- If the current state is q0 and the input symbol is 'a', move to state q1.
- If the current state is q0 and the input symbol is 'b', stay in state q0.
- If the current state is q1 and the input symbol is 'a', move back to state q0.
- If the current state is q1 and the input symbol is 'b', stay in state q1.
This DFA will accept all patterns with an odd number of a's, since the state will alternate between q0 and q1 every time an 'a' is encountered, and only strings with an odd number of a's will end in the accepting state q1.
To know more about Deterministic Finite Automaton, click here:
https://brainly.com/question/14507463
#SPJ11
what are the advantages of breaking up any long code into multiple files?
Answers
Breaking up long code into multiple files can provide several advantages to developers. First and foremost, it makes the code more organized and easier to manage. By separating different functions or features into their own files, developers can focus on specific sections of code without being overwhelmed by a massive codebase.
Furthermore, separating code into smaller files can improve the speed of development. Since developers can work on different files simultaneously, it can save time and reduce the likelihood of errors. It can also make debugging and troubleshooting easier, as it is easier to identify and isolate problems when they are contained within smaller files.
Additionally, breaking up code into multiple files can make it easier to reuse code across different projects. If a particular function or feature is useful in multiple projects, it can be saved as a separate file and used as needed. This can save time and effort when developing new projects, as developers can simply reuse existing code rather than writing it from scratch.
Finally, splitting code into multiple files can improve collaboration between developers. By working on separate files, developers can work independently and merge their changes later. This can lead to better communication and collaboration, as developers can work on different parts of the codebase without stepping on each other's toes.
Overall, breaking up long code into multiple files can provide numerous advantages to developers. From organization and management to collaboration and reuse, separating code into smaller files can make development faster, easier, and more efficient.
To know more about Breaking up visit:
https://brainly.com/question/14482282
#SPJ11
What type of pointing device is often used by artists, and why is it ideal for artists?
Answers
Answer:
A drawing/graphics tablet
Explanation:
It is ideal for artists, due to it being very similar to as if you were to draw on paper. The stylus replicates a pencil or pen.
guys tell the answer correctly
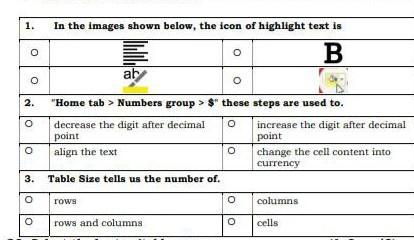
Answers
Answer:
1st ans: where u can see yellow colored line
2nd ans: currency one
3rd ans: cells
Explanation:
a man takes 30 step to cover 18 metre l,how many step he will needed to cover 3003m distance
Answers
166.8 x 30=5004
Answer is 5004
Aking sense of the death, the social consolidation after a death occurs, and caring for the dying are all functions of the: Multiple choice question. Sociology of death. Determinants of death. Death system. Psychology of death
Answers
The Death System is responsible for understanding the death, the social consolidation after a death occurs, and caring for the dying as it is the functions of the Death System.
The Death System comprises funeral homes, hospitals, cemeteries, crematoria, and various other entities that work to address the needs of the dying, the deceased, and the bereaved.A good understanding of the Death System is critical since it will help in comprehending the ways in which death and dying can affect various sectors of society.
The sociology of death is the study of the social structure, processes, and culture that surrounds death and dying. The determinants of death are the factors that cause or contribute to an individual's death. The psychology of death is the study of the psychological and emotional responses to death and dying.
To know more about responsible visit:
https://brainly.com/question/28903029
#SPJ11
Put the steps in order to produce the output shown below. Assume the indenting will be correct in the program.
5 2
5 3
8 2
8 3
Put responses in the correct input to answer the question. Select a response, navigate to the desired input and insert the response. Responses can be selected and inserted using the space bar, enter key, left mouse button or touchpad. Responses can also be moved by dragging with a mouse.
Line 2
Line 1
Line 3
Answers
The correct input to the above question are:
Line 1: for numB in [5,8]Line 3: print (numB, numA)Line 2: for numA in [2,3]What do you mean by program?A program is a set of instructions that a computer uses to carry out a specific task. [Computing] The size of a computer program affects the likelihood of an error occurring.
A computer program is a series of instructions written in a programming language that can be carried out by a computer. Software is made up of both tangible and intangible components, including computer programs as one example.
Looking at the output, it is obvious that the first numbers are repeated twice in a row and the second numbers are repeated in a sequence.
Therefore, note that nested loops are employed. assuming the program's indentation is appropriate. The sequence's code is as written above.
Learn more about program from
https://brainly.com/question/19461804
#SPJ1

Mariel types a sentence. She then decides to include that sentence four more times. She then decides she only
wants the sentence three more times, but changes her mind again to include the last sentence. Which commands
could have been used by Mariel? Check all that apply.
More Symbols
Insert Symbol
Undo
Redo
Repeat
Answers
The commands that could have been used by Mariel are:
UndoRedoWhat is an Undo Command?This refers to the command that is used in a computer environment to remove the last action done and this is usually used in word processing and this is done by pressinf Ctrl + Z which then undoes the action.
Hence, because Mariel typed the sentence and then wants to removes some things and then wants to include the last sentence, she probably used redo and undo commands.
Read more about undo commands here:
https://brainly.com/question/6413908
#SPJ1
you are a developer at a software development firm. your latest software build must be made available on the corporate web site. internet users require a method to ensure that they have downloaded an authentic version of the software. in other words, you want users to be able to be able to check the integrity of the software that they download. what should you do?
Answers
One way to ensure the integrity of the software that users download is by providing them with a cryptographic hash or a checksum value for the software. This value is a unique string of characters that is generated by applying a cryptographic hash function to the software. Users can then verify that the downloaded software is authentic by calculating the hash value of the downloaded file and comparing it to the hash value provided by the developer. If the hash values match, then the downloaded file is authentic.
To implement this, you should:
Calculate the cryptographic hash or checksum value of the software. Common hash functions include SHA-256, SHA-512, and MD5.
Publish the hash value on your corporate website, along with the download link for the software.
Instruct users to calculate the hash value of the downloaded file using a tool such as md5sum, sha256sum, or a similar tool that can be used to calculate the hash of a file.
Provide instructions on how to verify the hash value of the downloaded file against the published hash value on your website.
Learn more about website here:
brainly.com/question/32075231
#SPJ11
2 ways to make your computer work faster ( please help asap )
Answers
Answer:
clean up space or reboot ur computer or delete unwanted apps and files .
Explanation:
Please help quick!!
question: 15
true or false? you can strengthen the encryption of a caesar cipher by shifting the letters twice (using
two keys).
Answers
"You can strengthen the encryption of a caesar cipher by shifting the letters twice (using two keys). The statement true or false? The answer is true.
Wht is Caesar Cipher?The statement is true because to strengthen the encryption we can shift the letters by the method of Caesar Cipher. The Caesar cipher is a method that modifies some text using an encryption algorithm to improve the message's integrity, secrecy, or security. Shift ciphers include the Caesar Cipher. Modulo operators are used by Shift Ciphers to encrypt and decrypt communications. K, the key for the Shift Cipher, is an integer ranging from 0 to 25. The Caesar cipher is named for Julius Caesar, who, according to Suetonius, employed it with a three-shift (A becoming D while encrypting, and D becoming A when decrypting) to safeguard military-related communications.
Learn more about Caesar Cipher: https://brainly.com/question/14298787
#SPJ4
How do graphic designers showcase their work?
Graphic designers create(Blank)
to showcase their work.
THIS IS A BIG TEST IM BEHIND AND CANNOT FAIL PLZ
Answers
Answer:
Platforms!
Explanation:
Answer:
portfolios
Explanation:
A portfolio is a collection of work done by a graphic designer. Graphic designers use them to display their work to their clients.
a hard disk is a _ storage device
Answers
electro-mechanical data storage device
An example of documentary evidence that might be presented at trial for a cyber crime is:
A. None of these choices.
B. data retrieved from slack space on a hard drive.
C. a cellular telephone.
D. a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses.
Answers
An example of documentary evidence that might be presented at trial for cybercrime is a photocopy of a hacker’s spreadsheet of telephone numbers and e-mail addresses. Thus, option D is correct.
What is the evidence?
Evidence is really the data used to attempt to support anything in a court of justice. Evidence is gathered from people, artifacts, and records. The only means through which the court may draw conclusions and reach a ruling is via the use of evidence.
According to the definition of information, it is the demonstration of any claim to be true. A hard copy of a hacker's worksheet with contact information and e-mail accounts is an illustration of documented evidence that might be used in court to prove a cybercrime. Therefore, option D is the correct option.
Learn more about evidence, here:
https://brainly.com/question/14370298
#SPJ2
Can someone please help me with this .

Answers
Answer:
whether or not it is raining outside
if the first letter of your name starts with A
whether or not you were on time to school today
the answer to a yes or no question
whether or not it is monday
Explanation:
notice how all of them are "Whether" or "if" or "yes or no" or "1 or 0"
what is the output of the following code segment? n = 1; for ( ; n <= 5; ) cout << n << ' '; n ;
Answers
The output of the given code segment:n = 1; for ( ; n <= 5; ) cout << n << ' '; n ;The given code prints the numbers 1 through 5.
The `for` loop will run as long as `n` is less than or equal to 5. The `cout` statement will print the current value of `n`, followed by a space character. Since the value of `n` is initially 1, the loop will begin by printing 1. On each iteration, the value of `n` will be incremented by 1, so the loop will eventually print 2, 3, 4, and 5.
Once `n` becomes greater than 5, the loop will terminate, and the program will move on to the next line, which simply evaluates the value of `n` without doing anything with it.Hence, the output of the given code segment is:1 2 3 4 5
Learn more about codes at:
https://brainly.com/question/28590981
#SPJ11
The output of the given code segment will be "1 2 3 4 5" as the for loop will execute until the value of "n" is less than or equal to 5. After the for loop, the value of "n" will be 6.
The given code segment is using a for loop to print the values of variable "n" until it reaches 5. Initially, the value of "n" is set to 1 and the for loop starts. As there is no initialization statement in the for loop, the value of "n" is not changed in the beginning. The condition of the for loop is "n <= 5", which means that the loop will execute until the value of "n" is less than or equal to 5. In each iteration of the loop, the value of "n" is printed using cout and a space character is also printed. After the for loop, the value of "n" will be 6. Therefore, the output of the given code segment will be "1 2 3 4 5".
Thus, the given code segment is using a for loop to print the values of variable "n" until it reaches 5. The loop will execute until the value of "n" is less than or equal to 5 and the value of "n" is printed in each iteration. The output of the given code segment will be "1 2 3 4 5" and the value of "n" will be 6 after the for loop.
To know more about for loop visit:
https://brainly.com/question/31693159
#SPJ11
For quantitative data (e.g. the number of milligrams of a drug) coding your data involves?
Answers
For quantitative data (e.g., the number of milligrams of a drug), coding your data involves:
Dummy coding. Transferring each subject score to codingTransferring each subject's score to a computer coding sheet.What is quantitative data?Data that expresses a definite quantity, amount, or range is known as quantitative data. In most cases, the data is accompanied with measuring units, such as meters in the case of a person's height. Dummy coding offers one method for employing categorical predictor variables in various estimate methods, such as linear regression (see also effect coding).
Dummy coding transmits all the information about group membership using only ones and zeros. In order to satisfy the assumptions of some analyses, it could be required to dummy code variables. Dummy coding a categorical variable for use as a predictor in multiple linear regression is a typical occurrence (MLR). This mock coding contains some redundant code.
Data that can be measured or quantified in numerical terms is referred to as quantitative data. Discrete data and continuous data are the two basic categories of quantitative data. Examples of quantifiable data are height in feet, age in years, and weight in pounds. Data that is descriptive but not numerically expressed is considered qualitative data.
To learn more about quantitative data, refer
https://brainly.com/question/96076
#SPJ4