Receiving Invalid or unexpected token in my code. Please help
const express = require('express');
const { ApolloServer } = require('apollo-server-express');
const http = require('http');
const path = require('path');
const { fileLoader, mergeTypes, mergeResolvers } = require('merge-graphql-schemas');
require('dotenv').config();
// express server
const app = express();
// typeDefs
const typeDefs = mergeTypes(fileLoader(path.join(__dirname, './typeDefs')));
// resolvers
const resolvers = mergeResolvers(fileLoader(path.join(__dirname, './resolvers')));
// graphql server
const apolloServer = new ApolloServer({
typeDefs,
resolvers
});
// applyMiddleware method connects ApolloServer to a specific HTTP framework ie: express
apolloServer.applyMiddleware({ app });
// server
const httpserver = http.createServer(app);
// rest endpoint
app.get('/rest', function(req, res) {
res.json({
data: 'you hit rest endpoint great!'
});
});
// port
app.listen(process.env.PORT, function() {
console.log(`server is ready at http://localhost:${process.env.PORT}`);
console.log(`graphql server is ready at http://localhost:${process.env.PORT}${apolloServer.graphqlPath}`);
});
Answers
The code provided is missing a closing parenthesis at the end of line 19. To fix the "Invalid or unexpected token" error, you need to add a closing parenthesis ')' at the end of that line.
The error "Invalid or unexpected token" typically occurs when there is a syntax error in the code. In this case, the missing closing parenthesis is causing the error. The code is using the `mergeResolvers` function from the `merge-graphql-schemas` library to merge the resolvers, and the missing parenthesis is breaking the syntax of the code.
By adding the closing parenthesis at the end of line 19, the code will become syntactically correct, resolving the error.
Learn more about code
https://brainly.com/question/15301012
#SPJ11
Related Questions
What are the attacks that can be made against a bluetooth device?
Answers
The various attacks against Bluetooth devices include: Bluejacking, Bluesnarfing, BlueBorne, BlueBugging.
1. Bluejacking: Bluejacking is an attack where an attacker sends unsolicited messages to a Bluetooth-enabled device, such as text messages or images. This is typically done for fun and does not cause significant harm.
2. Bluesnarfing: In Bluesnarfing, an attacker gains unauthorized access to a Bluetooth device and steals sensitive information, such as contacts, emails, and text messages. This is a more serious attack that can compromise user privacy.
3. BlueBorne: BlueBorne is a set of vulnerabilities that allows an attacker to take control of a Bluetooth-enabled device by exploiting its wireless communication capabilities. This can lead to data theft or even remote control of the device.
4. Bluebugging: Bluebugging is an attack where the attacker takes full control of a Bluetooth device by exploiting its security vulnerabilities. This can lead to eavesdropping on phone calls, unauthorized access to data, and even remote control of the device.
To protect your Bluetooth devices from these attacks, always use strong and unique passwords, turn off Bluetooth when not in use, and regularly update your device's firmware to the latest version.
Learn more about Bluetooth: https://brainly.com/question/13072419
#SPJ11
The transportation department plans to build a new high-speed train route between two cities. The transportation department wants to implement a simulation of the train before any construction begins on this project. Which of the following statements is true about the use of a simulation for this project?
a) A simulation cannot be used to test the train under varying weather conditions.
b) Implementing a simulation is likely to increase the overall costs associated with the project.
c) Other high-speed train routes have been constructed in other locations, so a simulation is not needed.
d) Using a simulation may expose potential safety issues that can be corrected before construction begins.
Answers
It should be noted that using of a simulation for this project may expose potential safety issues that can be corrected before construction begins.
What is simulation?A simulation can be regarded as the imitation of the operation of a real-world process with respect to a period of time.
However, transportation department wants to implement a simulation of the train before any construction begins on this project, simulation may expose potential safety issues.
Therefore, option D is correct.
Learn more about simulation at:
https://brainly.com/question/25605883
The economic importance of computer viruses
Answers
Answer:
whats the question?
Explanation:
Answer:
........ . . . ........
Explanation:
...

1. The Bank manager is imposing a 10% interest rate on the new salary loan to every account in the BPI Family Bank. (ANSWER SHOULD BE UPPER CASE OR CAPITAL LETTERS) *
Answers
Hi, you've asked an incomplete question. However, I inferred you want to know the type of accounting activity involved in this process.
Answer:
CALCULATING
Explanation:
The process of imposing a 10% interest rate of course would require calculating how much cash value is to be deducted from the "new salary loan" of the respective accounts in the "BPI Family Bank".
This process in accounting often involves computing the individual loan amount multiplied by the interest percentage. For example, a 10% interest rate on a salary loan of $2000 would be \(\frac{10}{100} * 2000\) = $200
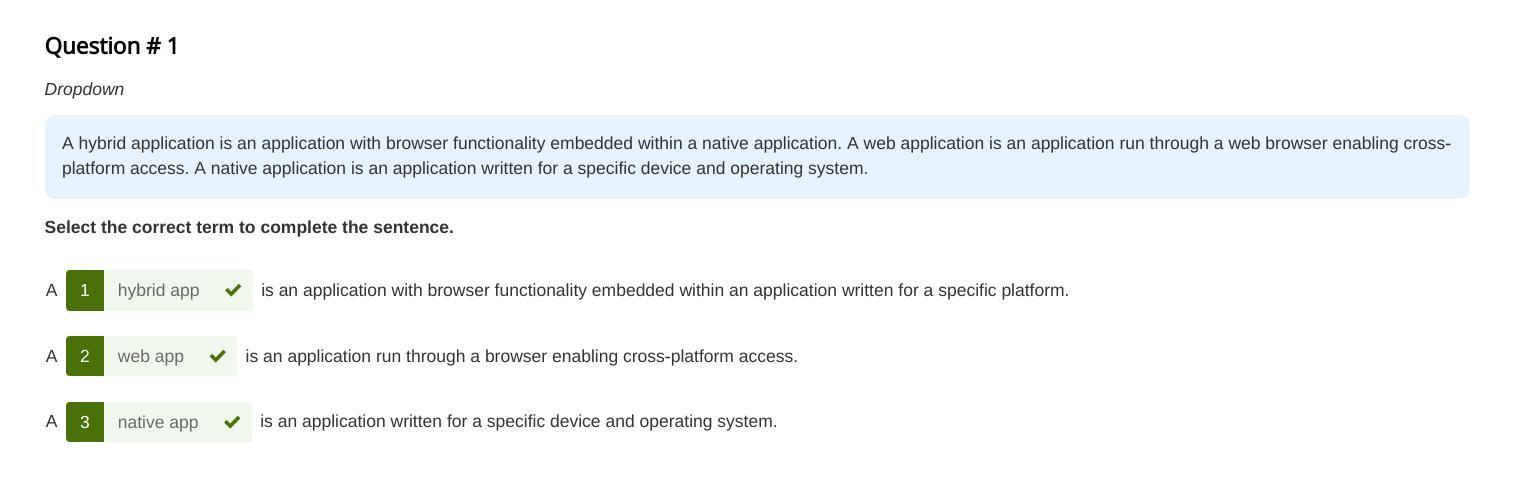
Select the correct term to complete the sentence.
A is an application with browser functionality embedded within an application written for a specific platform.
A is an application run through a browser enabling cross-platform access.
A is an application written for a specific device and operating system.
Answers
Answer:
A program that searches a database for specific words and returns a list of webpages or documents in which the search term was found. ... A _____ is an application that runs in a
Explanation:
First blank: Hybrid App
Second Blank: Web App
Third blank: Native App
PROOF:
Definenation monitor
Answers
Answer:
A computer monitor is an output device that displays information in pictorial form. A monitor usually comprises the visual display, circuitry, casing, and power supply. .
75 POINTS!!
PLS HURRY
Choose the term that best completes each sentence.
___are intentional attacks on a system with the intent to do harm.
a. cyberthreats
b. malware
___ may be intentional like a virus or unintentional like a fire or human error.
a. cyberthreats
b. malware
Answers
Malwares are intentional attacks on a system with the intent to do harm.
Cyberthreats may be intentional like a virus or unintentional like a fire or human error
Hope that helps!
Explain why every email account needs a subject
Answers
Answer:
Every email account needs a subject for the following reasons:
Organization: A subject line provides a brief overview of the content of the email, helping the recipient to quickly identify and organize their emails.
Attention: An email with a clear and relevant subject line is more likely to get the recipient's attention, as they can quickly see if the email is worth their time.
Filter: Email services often have filters that sort emails based on their subject line, allowing the recipient to categorize and prioritize emails.
Searchability: A clear subject line makes it easier for the recipient to search for the email later on, particularly in the case of a large inbox.
Therefore, including a subject in an email is important for effective communication and efficient email management.
Explanation:
Dynamic testing that involves viewing the software unit as a device that has expected input and output behaviors but whose internal workings are unknown. Occurs without the tester having any knowledge of the structure or the nature of the actual code. Usually done with someone other than the code writer.
Answers
Dynamic testing involving viewing a software unit as a device with expected input/output behaviors, but unknown internal workings, is performed without the tester's knowledge of the code structure. It typically involves someone other than the code writer.
In dynamic testing, the focus is on evaluating the behavior of a software unit during runtime, rather than examining its internal implementation details. This approach treats the software unit as a black box, where the tester is only concerned with the expected inputs and outputs, without any knowledge of the underlying code structure. The purpose of this type of testing is to assess the functionality and correctness of the software unit based solely on its observable behavior. By considering the software unit as a device with predetermined behaviors, testers can simulate various input scenarios and verify if the corresponding output matches the expected results.
To ensure impartiality and reduce bias, dynamic testing of this nature is often performed by individuals other than the original code writer. This approach helps uncover potential issues or discrepancies that may have been overlooked by the developer. By conducting tests from an external perspective, it increases the chances of identifying defects or inconsistencies in the software unit's behavior, leading to a more comprehensive evaluation.
Learn more about software here-
https://brainly.com/question/985406
#SPJ11
a bar graph is usually the best choice for graphing one variable to show proportions.
T/F
Answers
True. A bar graph is a visual representation of data that uses bars to compare different categories.
It is an effective way to display one variable and show the proportion of each category. Bar graphs are useful for displaying discrete data and are best suited for comparisons between categories or groups. They are particularly helpful in illustrating changes over time, comparing data across different groups or categories, and identifying trends. The height of each bar represents the frequency or proportion of data in that category, making it easy to compare and interpret. Overall, a bar graph is an effective tool for displaying one variable to show proportions.
learn more about bar graph here:
https://brainly.com/question/30443555
#SPJ11
Prompt the user for the name of their favorite hobby and store it in a variable
java
Answers
Below is an example of how you can prompt the user for their favorite hobby and store it in a variable in Java:
import java.util.Scanner;
public class Main {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
System.out.print("What is your favorite hobby? ");
String hobby = input.nextLine();
System.out.println("Your favorite hobby is: " + hobby);
What is the java about?
This code imports the Scanner class from the java.util package, which allows the program to read input from the user. Then, it creates a new Scanner object called input, which reads input from the standard input stream (usually the keyboard).
The System.out.print() method is used to display the prompt "What is your favorite hobby? " on the screen, and the input.nextLine() method is used to read the input from the user and store it in the variable hobby.
So, After the user inputs their hobby, the program will then print the variable hobby to confirm the input.
Learn more about java from
https://brainly.com/question/26789430
#SPJ1
Analysis tools that support viewing all or selected parts of data, querying the database, and generating reports include query-by-example as well as a specialized programming language called
Answers
Analysis tools such as query-by-example and a specialised programming language called SQL facilitate examining all or selected data, querying the database, and generating reports.
Data collection and analysis technologies are used to collect, evaluate, and present data for a range of applications and industries. They take unprocessed data and turn it into meaningful knowledge that businesses can use to make better choices. A data analyst may operate in a range of sectors, including operations, marketing, and finance. For instance, their findings might result in lower shipping costs. different viewpoints on consumer behaviour. Among the numerous types of data analysis tools, three categories stand out as particularly essential: Applications for Excel, R, Python, and business intelligence (BI).
Learn more about Analysis tools from
brainly.com/question/13994256
#SPJ4
Outline four types of cyber law.
Answers
Answer:
Fraud, Copyright, Defamation, Harassment and Stalking, Freedom of Speech, Trade Secrets, and Contracts and Employment Law.
Explanation:
These are the major areas of cyber law.
Cross-cultural team members might live in different time zones.
Members might send an email to other team members.
Email is a type of ________ communication.
O simoultaneous
O synchronous
O alternating
O asynchronous
Answers
Answer:
d. asynchronous
Explanation:
Which type of cable can transfer data up to 480 megabits per second?
ana
Answers
Answer:
Most suppliers offer three types of cables. USB 1.1 cables support data transfer rates up to 12 megabits per second (Mbps). USB 2.0 cables support data transfer rates up to 480 Mbps. USB 3.0 cables support data transfer rates of up to 5.0 Gbit/s.
Explanation:
Answer:
USB 2.0 cables
Explanation:
This could have been searched by you
All of the following are ways to avoid injuries when working on computers except Select one: O A. taking breaks O B. ensuring proper lighting O so you are looking up at it OD. purchasing an adjustable chair ? Ҷх – 2 O
Answers
The option that is not a way to avoid injuries when working on computers is ensuring proper lighting so you are looking up at it, option C is correct.
Proper lighting is important for computer work to reduce eye strain and prevent visual discomfort, but the specific condition where you are looking up at the lighting, is not a recommended practice.
In fact, it is generally advised to have the lighting positioned in a way that avoids glare on the screen and provides even illumination without causing strain on the neck or eyes.
Regular breaks help reduce eye fatigue, muscle tension, and the risk of repetitive strain injuries (RSIs).
Adequate lighting conditions in the workspace help prevent eye strain and discomfort.
An adjustable chair allows you to maintain proper posture, support your back, and adjust the height and position of your workstation to minimize strain on the body.
To learn more on Computers click:
https://brainly.com/question/32297640
#SPJ4
The most common delimiter is a
-forward slash
-period
-semicolon
-comma
Answers
Answer:
comma
Explanation:
trust me bro
The most common delimiter is a comma. The correct option is d.
What is a delimiter?
Programming languages employ delimiters to define code set characters or data strings, operate as data and code boundaries, and make it easier to comprehend code and divide up distinct implemented data sets and functions.
The values may be separated by any character, however, the comma, tab, and colon are the most often used delimiters. Space and the vertical bar, which is sometimes known as pipe, are occasionally utilized.
With one entry per row, data is organized in rows and columns in a delimited text file. Field separator characters are used to divide each column from the one after it. According to Comma Separated Value, one of the most popular delimiters is the comma.
Therefore, the correct option is d, comma.
To learn more about delimeter, refer to the link:
https://brainly.com/question/14970564
#SPJ2
A linux system that is configured to work in graphical mode, what is the run level?
Answers
A runlevel is a predetermined operating state on a Linux-based system that is used with Unix and Unix-based operating systems. Runlevels have numbers ranging from 0 to 6.
Runlevels control which applications can run after the OS has started. The machine's post-boot status is determined by the runlevel.
For instance, runlevel 4 might be nothing on one distribution and a multi-user GUI no-server configuration on another. Although most runlevels adhere to the fundamental patterns outlined in this article, other distributions use particular setups. Run levels are operational levels on Linux systems that characterize the system's current status in terms of the services that are offered. The first run level is limited and solely used for maintenance; network connections won't work.
Learn more about operating here-
https://brainly.com/question/18095291
#SPJ4
Identify industries and career-based activities in which computer technology makes people's work easier or more efficient.
Answers
Answer:
Those helpful safety or convenience features in modern vehicles? They are all programmed!
Explanation:
Create the candidateRows() function. The purpose of this function is to write individual table rows for each candidate, showing the candidate’s name, party affiliation, vote total, and vote percentage. The candidateRows() function has two parameters named raceNum and totalVotes. Place the commands in the following steps within this function.
Declare a local variable named rowHTML that will contain the HTML code for the table row. Set the initial value of this variable to an empty text string.
Create a for loop in which the counter variablej goes from 0 to 2 in steps of 1 unit. Within the for loop do the following:
Declare a variable named candidateName that retrieves the name of the current candidate and the current race. (Hint : Retrieve the candidate name from the multidimensional candidate array using the reference, candidate[raceNum][j].)
Declare a variable named candidateParty that retrieves the party affiliation of the current candidate in the current race from the multidimensional party array.
Declare a variable named candidateVotes that retrieves the votes cast for the current candidate in the current race from the multidimensional votes array.
Declare a variable named candidatePercent equal to the value returned by the calcPercent() function, calculating the percentage of votes received by the current candidate in the loop. Use candidateVotes as the first parameter value and totalVotes as the second parameter value.
Add the following HTML code to the value of the rowHTML variable
name ( party )
votes ( percent )
where name is the value of candidateName, party is the value of candidateParty, votes is the value of candidateVotes, and percent is the value of candidatePercent. Apply the toLocaleString() method to votes in order to display the vote total with a thousands separator. Apply the toFixed(1) method to percent in order to display percentage values to 1 decimal place.
Return the value of the rowHTML variable.
This is what I have so far-
"use strict";
/*
New Perspectives on HTML5 and CSS3, 7th Edition
Tutorial 10
Case Problem 4
Author:
Date:
Filename: vw_results.js
Functions:
The calcSum() function is a callback function used to
calculte the total value from items within an array
The calcPercent(value, sum) function calculates the percentage given
a value and a sum
The createBar(partyType, percent) function writes a different
table data table based on the candidates party affilication.
*/
var reportHTML = "" + raceTitle + "";
for(var i=0; i
reportHTML += "";
reportHTML += "" + race[i] + "";reportHTML="CandidateVotes";
reportHTML += candidateRows(i, totalVotes);
reportHTML += "";
var totalVotes = 0;
votes[i].forEach(calcSum);
}
document.getElementsByTagName("section")[0].innerHTML = reportHTML;
function candidateRows(raceNum, totalVotes) {
var rowHTML = "";
for (var j = 0; j <= 2; j++) {
var candidateName = candidate[raceNum][j];
var candidateParty = party[raceNum][j];
var candidateVotes = votes[raceNum][j];
var candidatePercent = calcPercent(candidateVotes, totalVotes);
rowHTML += ""+candidateName +"("+candidateParty+")"+ candidateVotes.toLocaleString() + "(" + candidatePercent.toFixed(1)+")";
}
return rowHTML;
}
/* Callback Function to calculate an array sum */
function calcSum(value) {
totalVotes += value;
}
/* Function to calculate a percentage */
function calcPercent(value, sum) {
return (100*value/sum);
Answers
The candidateRows function I added the missing <tr> and <td> tags to properly structure the table rows and cells.
Here's the corrected version of your code:
"use strict";
/*
New Perspectives on HTML5 and CSS3, 7th Edition
Tutorial 10
Case Problem 4
Author:
Date:
Filename: vw_results.js
Functions:
The calcSum() function is a callback function used to
calculate the total value from items within an array
The calcPercent(value, sum) function calculates the percentage given
a value and a sum
The createBar(partyType, percent) function writes a different
table data table based on the candidates party affiliation.
*/
var reportHTML = "" + raceTitle + "";
for (var i = 0; i < race.length; i++) {
reportHTML += "";
reportHTML += "" + race[i] + "";
reportHTML += candidateRows(i, totalVotes);
reportHTML += "";
var totalVotes = 0;
votes[i].forEach(calcSum);
}
document.getElementsByTagName("section")[0].innerHTML = reportHTML;
function candidateRows(raceNum, totalVotes) {
var rowHTML = "";
for (var j = 0; j <= 2; j++) {
var candidateName = candidate[raceNum][j];
var candidateParty = party[raceNum][j];
var candidateVotes = votes[raceNum][j];
var candidatePercent = calcPercent(candidateVotes, totalVotes);
rowHTML += "<tr>";
rowHTML += "<td>" + candidateName + " (" + candidateParty + ")</td>";
rowHTML += "<td>" + candidateVotes.toLocaleString() + " (" + candidatePercent.toFixed(1) + "%)</td>";
rowHTML += "</tr>";
}
return rowHTML;
}
/* Callback Function to calculate an array sum */
function calcSum(value) {
totalVotes += value;
}
/* Function to calculate a percentage */
function calcPercent(value, sum) {
return (100 * value / sum);
}
For similar questions on candidate
https://brainly.com/question/31849676
#SPJ11
PYTHON HELP!
Write a loop that inputs words until the user enters DONE. After each input, the program should number each entry and print in this format:
#1: You entered _____
When DONE is entered, the total number of words entered should be printed in this format:
A total of __ words were entered.
Sample Run
Please enter the next word: cat
#1: You entered the word cat
Please enter the next word: iguana
#2: You entered the word iguana
Please enter the next word: zebra
#3: You entered the word zebra
Please enter the next word: dolphin
#4: You entered the word dolphin
Please enter the next word: DONE
A total of 4 words were entered.
Answers
The code to show the loop that inputs words until the user enters DONE will be:
i = 0
while True:
word = input("Please enter the next word: ")
if word == "STOP":
break
i += 1
print("#{}: You entered {}".format(i, word))
print("All done. {} words entered.".format(i))
What is a loop?A loop is used to execute a block of code several times based on the condition specified in the loop. It means that it executes the same code multiple times, saving code and assisting in traversing the elements of an array.
The loop was illustrated thus:
Words for defining a method
An integer variable "c" and a string variable "word" are declared inside a method, and a while loop is defined.
Within the loop, we input the string value and declare a conditional statement that checks whether the word value is equal to STOP.
It counts the total number of input values and prints the result along with the message.
Finally, we invoke the method.
Learn more about program on:
https://brainly.com/question/18750495
#SPJ1
Christa is designing a web page. She wants an image that reads 5100% Natural!" to be associated in the user's mind with a picture of a new fruit snack. What is the best way for her to do this?
A. use the rule of thirds
B. place the images in close proximity
C. increase the color contrast
D. increase the whitespace
Answers
Answer: B. Please the images in close proximity.
Please tell me if its right so I can update it!
monitor calibration is not enough to ensure total image accuracy through the process. a. evaluation b. manipulation c. output d. input
Answers
Monitor calibration is insufficient to guarantee complete image accuracy during output.
Why does the photograph usually go through the matting process before being framed?The mat, when used in a frame, prevents the picture from contacting and sticking to the glass. Matting can be completed totally with historical materials, unlike other presenting approaches, and it is simple to undo.
What justifications exist for matting an image?Artwork can be protected by matting. Unframed art can be handled by artists and collectors without really touching the piece thanks to a mat. A mat enables airflow between the artwork and the glazing substance.
To know more about output visit:-
https://brainly.com/question/14227929
#SPJ4
WINDOWS FIREWALL • Open Windows Defender Firewall from the Control Panel • Select 'Advanced Settings' & select 'Inbound Rules' Create a new Inbound Rule (right-click to start) What are the various options you can choose when creating/making an Inbound Rule? (List a few) . . Select 'Custom' & then select Protocol and Ports' in the left window Under Protocol Type scroll down and select ICMPv4 & select 'Next' until you get to Action section: . What is default 'ACTION' for Firewall Inbound Rules? If you were to select ‘Block the connection', in your own words what would this rule do? (summarize below)
Answers
When creating an Inbound Rule in Windows Defender Firewall, there are several options that can be chosen. Some of these options include:
Program: Allows you to specify a specific program or executable to which the rule applies.
Port: Allows you to specify a specific port or range of ports to which the rule applies.
Protocol: Allows you to select the protocol (TCP, UDP, ICMP, etc.) to which the rule applies.
Scope: Allows you to specify the IP addresses or range of IP addresses to which the rule applies.
Action: Specifies the action to be taken when the rule matches. This can be either "Allow the connection" or "Block the connection."
The default action for Firewall Inbound Rules is set to "Allow the connection." This means that incoming connections that match the rule will be permitted.
If you were to select "Block the connection" as the action for an Inbound Rule, it means that any incoming connection that matches the rule will be denied or blocked. The firewall will prevent the connection from establishing or reaching the target. This can be used to restrict access to specific ports, protocols, or IP addresses, effectively preventing any communication from unauthorized sources or potentially harmful connections.
Learn more about Windows Firewall here: brainly.com/question/31546387
#SPJ11
What is the first multiple of a bit
Answers
Answer:
The byte
Explanation:
which represents eight bits
A speed limit sign that says "NIGHT" indicates the _____ legal speed between sunset and sunrise.
Answers
Answer:
Maximum
Explanation:
Speed limits indicate the maximum speed you are legally allowed to drive.
briefly explain about five kinds of network topology
Answers
Answer:
The mapping of the LAN (local area network) is design called as Topology.
Explanation:
The network topology is to perform a arrangement of the network to the connect sender and receiver in the network connection, there is a five type of topology is there are:- (1) tree topology (2) star topology (3) ring topology (4) bus topology (5) mesh topology.
(1) Tree topology is the nodes are connecting to the hierarchical form it is called by the hierarchical topology its used in the wide area network, and they are manage and maintain the easily, they work in the group.(2) star topology is to the connected to the all computers in a single hub cable through, it is dedicated to the hub connection, star topology is the setup and modify to the network and nodes and low network, is to expensive to use.(3) Ring topology is tho perform it computer to connect by the another computer for each device, ring topology is the use large number and to star topology is to install and expand, troubleshooting is the difficult in the ring topology.(4) Bus topology is the contain computer network device is connected to the single cable, and this only one direction system, bus topology is used in small networks and bus topology is the cost effective, and the bus topology is the limited length cable.(5) Mesh topology is to perform point to point connection to computer devices, and to transmits data to two ways (1) routing (2) flooding.Mesh routing is network requirement and has information of the broken links.Mesh flooding is transmitted to the all computer network and leads to load over network.Write a half page summary on how to clean a Gaming PC properly.
Answers
Answer:
As a responsible PC gaming enthusiast, you simply cannot wait for spring to do a little routine cleaning on your PC. Regardless of whether you casually play or professionally game, all gaming computers are susceptible to dirt, dust, and other contaminants that can severely impact performance. Dust buildup can cause PC components to retain heat, making it difficult for internal fans to keep the system cool. As a result, the system can become less efficient and unusually slow. However, there are steps you can take to keep your gaming computer in great condition. In this article, we explain how to clean the inside of your gaming computer, so you can keep on fighting the good fight in digital worlds.Assemble the Right ToolsGaming desktops are very complex pieces of technology. Be smart by assembling the necessary tools and supplies before you begin the deep-clean process. Most of the products you need might already be sitting around the house, including compressed air cans, rubbing alcohol, white vinegar, distilled water, microfiber cloths, ear swabs, and tape.How to Clean a Gaming PCFollow these 10 steps to get back on good terms with your gaming rig.1. Disconnect the power cable, USB peripherals, as well as any audio equipment attached to your computer and safely discharge the remaining power.2. Take the computer case outside, so the dust doesn’t settle in the same room that your gaming setup is located.3. Wipe the exterior and interior of the computer case.4. Detach the dust filters and wipe away any accumulated dust. We recommend using compressed air for full coverage. If you have foam filters, gently rinse with water and leave them to dry.5. Wipe down the inside of the case by hand after disconnecting the graphics cards and RAM modules.6. If possible, remove the heatsink entirely to scrub away any gunk or debris.7. Clean off any dust hidden between the cracks of the graphics cards, so you can easily clean the motherboard.8. Remove any big clumps of dust by using a cloth dampened with rubbing alcohol.9. Use the compressed air can to clean nooks, crannies, and the motherboard. For stubborn dust spots, just dampen an ear swab with rubbing alcohol or use a gentle toothbrush to clean.10. Once the case interior is completely clean and free of dust, you can put each component back where it belongs.Routine cleaning and maintenance are important to the health of your gaming PC. We recommend using compressed air every three to six months to prevent dust buildup from impacting your PC components. You should also make an effort to clean your mouse, headphones, keyboard, and monitor to keep your gaming setup looking like new.
Explanation:
Explain how did the internet change the pricing environment.
Answers
Answer:
Explanation:
Here are some of the ways the Internet has changed the pricing environment:
Multiplied rate transparency: consumers can now effortlessly compare costs from exceptional outlets, which places a downward strain on fees.New pricing models: The net has enabled new pricing fashions, which include dynamic pricing and pay-in-keeping with-use, that may result in lower prices for customers.
Decrease entry barriers: The internet has lowered the entry obstacles for new groups, which has improved opposition and caused lower fees.
Information-pushed pricing: The internet has made it less difficult for groups to acquire and examine information about purchaser behavior, which can be used to force greater centered pricing.
To learn more about Internet change,
https://brainly.com/question/15321297
**Random answers to get points will be reported.**
Identify the error in the following block of code.
for x in range(2, 6):
print(x)
The first line is missing quotes.
The first line has a spelling error.
The second line has a spelling error.
The second line needs to be indented four spaces.
Answers
Answer
I think its: The first line is missing quotes
Explanation:
Answer:
B
Explanation:
"(2, 6)" the space in between those numbers create a bad income I tried it and it was the problem so hence its B