Small organizations with only a few computers can manage each device in an ad hoc way without standardization. Larger organizations need to use standardization to scale their ability to support many users. Consider what you’ve learned about Active Directory and Group Policy and how they can be used to simplify user support and desktop configuration. You can search the Internet for examples. Create a posting that describes your thoughts on how Active Directory and Group Policy improve management in large organizations.
Answers
Organizational security is the principal application of Group Policy Management. Group policies, also known as Group Policy Objects (GPOs), enable decision-makers and IT professionals to deploy critical cybersecurity measures throughout an organization from a single place.
What is an Active Directory?Microsoft Active Directory has a feature called Group Policy. Its primary function is to allow IT administrators to manage people and machines throughout an AD domain from a single location.
Microsoft Active Directory is a directory service designed for Windows domain networks. It is featured as a set of processes and services in the majority of Windows Server operating systems. Active Directory was initially exclusively used for centralized domain management.
Group Policy is a hierarchical framework that enables a network administrator in charge of Microsoft's Active Directory to implement specified user and computer configurations. Group Policy is essentially a security tool for applying security settings to people and machines.
Learn more about Active Directories:
https://brainly.com/question/14469917
#SPJ1
Related Questions
1
Select the correct answer from each drop-down menu.
What Is DHTML?
DHTML Is
It allows you to add functionality such as
Reset
Next
Answers
Answer:
DHTML (Dynamic HTML) is a collection of a few different languages
Explanation:
Dynamic HTML is a collection of HTML, DOM, JavaScript, and CSS.
It allows for more customizability than regular HTML. It allows scripts (JavaScript), webpage styling (CSS), manipulation of static objects (DOM), and building of the initial webpage (HTML).
Since the question is incomplete, I'm not really sure what all you need answered - please leave a comment if you would like something else explained. :)
Question 6 of 10
If you want to design computing components for cars and medical
equipment, which career should you pursue?
A) hardware design
B) systems analysis
C) telecommunications
D) machine learning
Answers
Answer:
Hardware design.
Explanation:
When dealing with components to deal with computing, you need to deal with hardware. Ergo: if you're designing computing components for cars an medical equipment, you will need to pursue hardware design.
if-else AND if-elif-else
need at minimum two sets of if, one must contain elif
comparison operators
>, <, >=, <=, !=, ==
used at least three times
logical operator
and, or, not
used at least once
while loop AND for loop
both a while loop and a for loop must be used
while loop
based on user input
be sure to include / update your loop control variable
must include a count variable that counts how many times the while loop runs
for loop must include one version of the range function
range(x), range(x,y), or range(x,y,z)
comments
# this line describes the following code
comments are essential, make sure they are useful and informative (I do read them)
at least 40 lines of code
this includes appropriate whitespace and comments
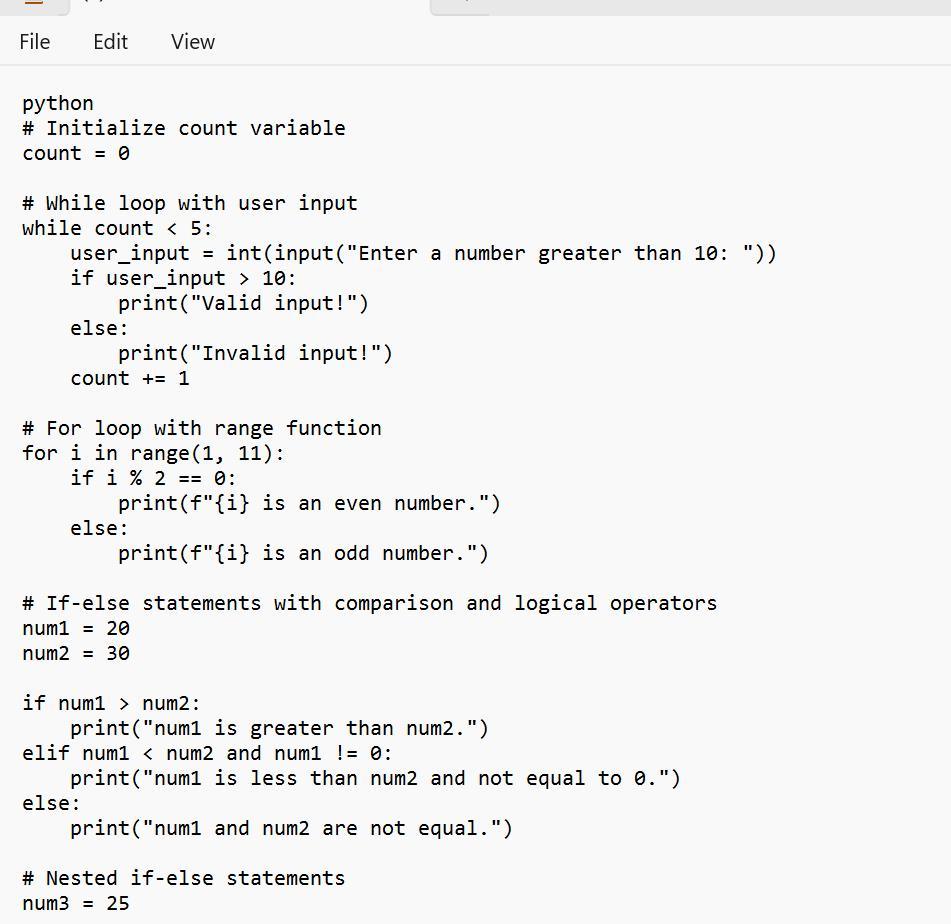
python
Answers
Based on the image, one can see an example of Python code that is said to be able to meets the requirements that are given in the question:
What is the python?The code given is seen as a form of a Python script that tells more on the use of if-else as well as if-elif-else statements, also the use of comparison operators, logical operators, and others
Therefore, one need to know that the code is just a form of an example and it can or cannot not have a special functional purpose. It is one that is meant to tell more on the use of if-else, if-elif-else statements, etc.
Learn more about python from
https://brainly.com/question/26497128
#SPJ1

What is the difference between an IP address and an IP Packet?
Answers
Answer:
The IP address is a numerical number assigned to a device when connected to the internet for better identification. Whereas, the IP packet is the packet which contains the total information of the content that is carried over the network from host to destination and vice versa.
Explanation:
I hope this helped and plz give brainliest!
how would you feel if the next version of windows becomes SaaS, and why?
Answers
If the next version of Windows becomes SaaS, SaaS or Software as a Service is a software delivery model in which software is hosted on the cloud and provided to users over the internet.
Moving Windows to a SaaS model means that Microsoft will continue to deliver updates and new features through a subscription-based service rather than through major new versions of the operating system.
This approach has its own advantages and challenges.
Benefits of the SaaS model for Windows:
Continuous Updates: Users receive regular updates and new features, ensuring they always have access to the latest improvements and security patches.
Flexibility: Subscriptions offer different tiers and plans so users can choose the features they need and customize their experience.
Lower upfront costs: A subscription model could reduce the upfront cost of purchasing Windows, making Windows more accessible to a wider audience.
Improved security: Continuous updates can help address vulnerabilities and security threats more rapidly, enhancing overall system security.
Challenges and concerns with a SaaS model for Windows:
Dependency on internet connectivity: Users would need a stable internet connection to receive updates and access features, which may not be ideal for those in areas with limited or unreliable internet access.
Privacy and data concerns: Users might have concerns about data collection, privacy, and the potential for their usage patterns to be monitored in a subscription-based model.
Cost considerations: While a subscription model may provide flexibility, some users may find it less cost-effective in the long run compared to purchasing a traditional license for Windows.
Compatibility issues: Continuous updates could introduce compatibility challenges for legacy software and hardware that may not be updated or supported in the new model.
Whether you view Windows' migration to a SaaS model as a positive or negative is ultimately determined by your personal perspective and specific implementations by Microsoft.
Cost: SaaS is a subscription-based model, which means users have to pay recurring fees to use the software.
They have to rely on the provider to update, maintain, and improve the software.To sum up, I would feel hesitant about using SaaS if the next version of Windows becomes SaaS.
For more questions on Software as a Service:
https://brainly.com/question/23864885
#SPJ8
Which of the following is NOT a benefit of pair-programming?
Code takes 15% less time to write than with a solo programmer.
Programs have fewer bugs than if written by a single programmer.
Code solutions are more creative.
o o
Bias in programs is reduced.
Answers
Answer:
Programs have fewer bugs than if written by a single programmer.
Explanation:
this is what I think personally
Coupled with risk reduction and knowledge sharing within an organization, pair programming is a key technique for producing faster, higher quality code. Thus, option B is correct.
What is the role pair programmer in the programs?Two programmers collaborate at the same workstation while using the agile software development technique known as pair programming.
The observer or navigator reads each line of code as it is entered while the driver, who is also the code writer, types it in.
Pair programming is a method where two programmers collaborate on the same block of code while using just one computer.
This introduces the idea of pair programming roles, where one performs the function of the driver (writing code) and the other that of the navigator (ensuring the accuracy of the code).
Therefore, Programs have fewer bugs than if written by a single programmer.
Learn more about pair programmer here:
https://brainly.com/question/14190382
#SPJ2
Rizwan, a data analyst, is generating a report by pulling data from multiple databases and analyzing it. The data processing application is resource-intensive, so Rizwan wants to ensure that other applications do not consume resources that this application needs.How can Rizwan boost the performance of the data processing application?
Answers
Reduce the actual memory while increasing the virtual memory Rizwan boost the performance of the data processing application.
What is a data analyst?
To find the solution to a problem or provide an answer to a question, a data analyst gathers, purifies, and analyses data sets. They work in a variety of fields, including as government, business, finance, law enforcement, and science.
What types of clients ought a company to focus on in its upcoming advertising campaign? Which age range is most susceptible to a specific disease? What behavioural trends are associated with financial fraud?
As a data analyst, you might have to respond to inquiries like these. Learn more about what a data analyst does, what skills you'll need, and how to get started on your path to becoming one by reading on.
Read more about data analyst:
https://brainly.com/question/28375055
#SPJ4
A _____ derives its name from the fact that a collection of multiple entries of the same type can exist for any single key attribute occurrence.
Answers
give one major environmental and
one energy problem kenya faces as far as computer installations are concerned?
Answers
One considerable predicament that Kenya encounters pertaining to the utilization of computers is managing electronic waste (e-waste).
Why is this a problem?The mounting number of electronic devices and machines emphasizes upon responsibly discarding outdated or defective hardware in order to avoid environmental degradation.
E-waste harbors hazardous materials such as lead, mercury, and cadmium which can pollute soil and water resources, thereby risking human health and ecosystem sustainability.
Consequently, a significant energy drawback with computer use within Kenya pertains to the insufficiency or instability of electrical power supply.
Read more about computer installations here:
https://brainly.com/question/11430725
#SPJ1
Insertion sort in java code. I need java program to output this print out exact, please.
When the input is:
6 3 2 1 5 9 8
the output is:
3 2 1 5 9 8
2 3 1 5 9 8
1 2 3 5 9 8
1 2 3 5 9 8
1 2 3 5 9 8
1 2 3 5 8 9
comparisons: 7
swaps: 4
Here are the steps that are need in order to accomplish this.
The program has four steps:
1 Read the size of an integer array, followed by the elements of the array (no duplicates).
2 Output the array.
3 Perform an insertion sort on the array.
4 Output the number of comparisons and swaps performed.
main() performs steps 1 and 2.
Implement step 3 based on the insertion sort algorithm in the book. Modify insertionSort() to:
Count the number of comparisons performed.
Count the number of swaps performed.
Output the array during each iteration of the outside loop.
Complete main() to perform step 4, according to the format shown in the example below.
Hints: In order to count comparisons and swaps, modify the while loop in insertionSort(). Use static variables for comparisons and swaps.
The program provides three helper methods:
// Read and return an array of integers.
// The first integer read is number of integers that follow.
int[] readNums()
// Print the numbers in the array, separated by spaces
// (No space or newline before the first number or after the last.)
void printNums(int[] nums)
// Exchange nums[j] and nums[k].
void swap(int[] nums, int j, int k)
Answers
Answer:
Here is the Java code for the insertion sort algorithm with the required modifications:
```
import java.util.Scanner;
public class InsertionSort {
// Static variables to count comparisons and swaps
static int comparisons = 0;
static int swaps = 0;
public static void main(String[] args) {
// Step 1: Read the size and elements of the array
Scanner scanner = new Scanner(System.in);
int size = scanner.nextInt();
int[] nums = new int[size];
for (int i = 0; i < size; i++) {
nums[i] = scanner.nextInt();
}
scanner.close();
// Step 2: Output the initial array
printNums(nums);
// Step 3: Perform insertion sort with modifications
insertionSort(nums);
// Step 4: Output the sorted array and counts
printNums(nums);
System.out.println("comparisons: " + comparisons);
System.out.println("swaps: " + swaps);
}
public static void insertionSort(int[] nums) {
for (int i = 1; i < nums.length; i++) {
int j = i;
while (j > 0 && nums[j] < nums[j-1]) {
// Swap nums[j] and nums[j-1] and count swaps
swap(nums, j, j-1);
swaps++;
// Increment j and count comparisons
j--;
comparisons++;
}
// Output the array during each iteration of the outside loop
printNums(nums);
}
}
public static int[] readNums() {
Scanner scanner = new Scanner(System.in);
int size = scanner.nextInt();
int[] nums = new int[size];
for (int i = 0; i < size; i++) {
nums[i] = scanner.nextInt();
}
scanner.close();
return nums;
}
public static void printNums(int[] nums) {
System.out.print(nums[0]);
for (int i = 1; i < nums.length; i++) {
System.out.print(" " + nums[i]);
}
System.out.println();
}
public static void swap(int[] nums, int j, int k) {
int temp = nums[j];
nums[j] = nums[k];
nums[k] = temp;
}
}
```
When the input is "6 3 2 1 5 9 8", this program outputs the desired result:
```
6 3 2 1 5 9 8
3 6 2 1 5 9 8
2 3 6 1 5 9 8
1 2 3 6 5 9 8
1 2 3 5 6 9 8
1 2 3 5 6 8 9
comparisons: 7
swaps: 4
```
all flowcharts begin with me.i am elliptical in shape.
Answers
Note that it is FALSE to state that "all flowcharts begin with me.i am elliptical in shape."
How is this so?While it is common for flowcharts to start with a shape, typically represented as an oval or rounded rectangle, it is not always an elliptical shape.
The starting point of a flowchart can vary depending on the specific system or process being depicted.
The purpose of the initial shape is to indicate the beginning or initiation of the flowchart, and it can take various forms depending on the conventions and preferences of the flowchart designer.
Learn more about flow charts at:
https://brainly.com/question/6532130
#SPJ1
Full Question:
Although part of your question is missing, you might be referring to this full question:
All flowcharts begin with me.i am elliptical in shape. True or False?
What does influence mean in this passage i-Ready
Answers
In the context of i-Ready, "influence" refers to the impact or effect that a particular factor or element has on something else. It suggests that the factor or element has the ability to shape or change the outcome or behavior of a given situation or entity.
In the i-Ready program, the term "influence" could be used to describe how various components or aspects of the program affect students' learning outcomes.
For example, the curriculum, instructional methods, and assessments implemented in i-Ready may have an influence on students' academic performance and growth.
The program's adaptive nature, tailored to individual student needs, may influence their progress by providing appropriate challenges and support.
Furthermore, i-Ready may aim to have an influence on teachers' instructional practices by providing data and insights into students' strengths and areas for improvement.
This can help educators make informed decisions and adjust their teaching strategies to better meet their students' needs.
In summary, in the context of i-Ready, "influence" refers to the effect or impact that different elements of the program have on students' learning outcomes and teachers' instructional practices. It signifies the power of these components to shape and mold the educational experiences and achievements of students.
For more such questions element,Click on
https://brainly.com/question/28565733
#SPJ8
Submit your three to five page report on three manufacturing careers that interest you.
Answers
Answer:
Manufacturing jobs are those that create new products directly from either raw materials or components. These jobs are found in a factory, plant, or mill. They can also exist in a home, as long as products, not services, are created.1
For example, bakeries, candy stores, and custom tailors are considered manufacturing because they create products out of components. On the other hand, book publishing, logging, and mining are not considered manufacturing because they don't change the good into a new product.
Construction is in its own category and is not considered manufacturing. New home builders are construction companies that build single-family homes.2 New home construction and the commercial real estate construction industry are significant components of gross domestic product.3
Statistics
There are 12.839 million Americans in manufacturing jobs as of March 2020, the National Association of Manufacturers reported from the Bureau of Labor Statistics.4 In 2018, they earned $87,185 a year each. This included pay and benefits. That's 21 percent more than the average worker, who earned $68,782 annually.5
U.S. manufacturing workers deserve this pay. They are the most productive in the world.6 That's due to increased use of computers and robotics.7 They also reduced the number of jobs by replacing workers.8
Yet, 89 percent of manufacturers are leaving jobs unfilled. They can't find qualified applicants, according to a 2018 Deloitte Institute report. The skills gap could leave 2.4 million vacant jobs between 2018 and 2028. That could cost the industry $2.5 trillion by 2028.
Manufacturers also face 2.69 million jobs to be vacated by retirees. Another 1.96 million are opening up due to growth in the industry. The Deloitte report found that manufacturers need to fill 4.6 million jobs between 2018 and 2028.9
Types of Manufacturing Jobs
The Census divides manufacturing industries into many sectors.10 Here's a summary:
Food, Beverage, and Tobacco
Textiles, Leather, and Apparel
Wood, Paper, and Printing
Petroleum, Coal, Chemicals, Plastics, and Rubber
Nonmetallic Mineral
Primary Metal, Fabricated Metal, and Machinery
Computer and Electronics
Electrical Equipment, Appliances, and Components
Transportation
Furniture
Miscellaneous Manufacturing
If you want details about any of the industries, go to the Manufacturing Index. It will tell you more about the sector, including trends and prices in the industry. You'll also find statistics about the workforce itself, including fatalities, injuries, and illnesses.
A second resource is the Bureau of Labor Statistics. It provides a guide to the types of jobs that are in these industries. Here's a quick list:
Assemblers and Fabricators
Bakers
Dental Laboratory Technicians
Food Processing Occupations
Food Processing Operators
Jewelers and Precious Stone and Metal Workers
Machinists and Tool and Die
Medical Appliance Technicians
Metal and Plastic Machine Workers
Ophthalmic Laboratory Technicians
Painting and Coating Workers
Power Plant Operators
Printing
Quality Control
Semiconductor Processors
Sewers and Tailors
Slaughterers and Meat Packers
Stationary Engineers and Boiler Operators
Upholsterers
Water and Wastewater Treatment
Welders, Cutters, Solderers
Woodworkers11
The Bureau of Labor Statistics describes what these jobs are like, how much education or training is needed, and the salary level. It also will tell you what it's like to work in the occupation, how many there are, and whether it's a growing field. You can also find what particular skills are used, whether specific certification is required, and how to get the training needed.11 This guide can be found at Production Occupations.
Trends in Manufacturing Jobs
Manufacturing processes are changing, and so are the job skills that are needed. Manufacturers are always searching for more cost-effective ways of producing their goods. That's why, even though the number of jobs is projected to decline, the jobs that remain are likely to be higher paid. But they will require education and training to acquire the skills needed.
That's for two reasons. First, the demand for manufactured products is growing from emerging markets like India and China. McKinsey & Company estimated that this could almost triple to $30 trillion by 2025. These countries would demand 70 percent of global manufactured goods.12
How will this demand change manufacturing jobs? Companies will have to offer products specific to the needs of these very diverse markets. As a result, customer service jobs will become more important to manufacturers.
Second, manufacturers are adopting very sophisticated technology to both meet these specialized needs and to lower costs.
How can organizations leverage information systems to gain a competitive advantage in today's business landscape? Provide examples to support your answer.
Answers
Organizations can leverage information systems to gain a competitive advantage in several ways in today's business landscape. Here are some examples:
Improved Decision-Making: Information systems can provide timely and accurate data, enabling organizations to make informed decisions quickly. For example, a retail company can use point-of-sale systems and inventory management systems to track sales data and inventory levels in real-time.Enhanced Customer Relationship Management: Information systems can help organizations manage and analyze customer data to personalize interactions, provide better customer service, and build strong customer relationships.Streamlined Operations and Efficiency: Information systems can automate and streamline business processes, improving operational efficiency. For example, manufacturing organizations can implement enterprise resource planning (ERP) systems.Data-Driven Insights and Analytics: Information systems enable organizations to collect, store, and analyze vast amounts of data to gain valuable insights. By using business intelligence tools and data analytics, organizations can uncover patterns, trends, and correlations in data, which can inform strategic decision-making. Agile and Collaborative Work Environment: Information systems facilitate collaboration and communication within organizations. For example, cloud-based project management tools enable teams to collaborate in real-time, track progress.These are just a few examples of how organizations can leverage information systems to gain a competitive advantage. By harnessing technology effectively, organizations can improve decision-making, customer relationships.
for similar questions on organizations.
https://brainly.com/question/30402779
#SPJ8
In this question, you will experimentally verify the sensitivity of using a precise Pi to the accuracy of computing area. You need to perform the following activities with Python program:
a. Compute the area of a circle with radius 10 using Pi from the Python Math Module. Assign the area to a variable, say realA.
b. Now compute the area of the circle using the Pi value with precision 1,2, and 3 points after the decimal place. (i.e., Pi = 3.1, 3.14 & 3.141). Then Print the percentage difference between each of the areas calculated using each of these values of Pi and realA.
Answers
Answer:
Follows are the code to this question:
import math as x #import math package
#option a
radius = 10#defining radius variable
print("radius = ", radius)#print radius value
realA = x.pi * radius * radius#calculate the area in realA variable
print("\nrealA = ", realA)#print realA value
#option b
a1 = 3.1 * radius * radius#calculate first area in a1 variable
print("Area 1= ", a1)#print Area
print("Percentage difference= ", ((realA - a1)/realA) * 100) #print difference
a2 = 3.14 * radius * radius#calculate first area in a2 variable
print("Area 2= ", a2)#print Area
print("Percentage difference= ", ((realA - a2)/realA) * 100)#print difference
a3 = 3.141 * radius * radius#calculate first area in a2 variable print("Area 3= ", a3)#print Area
print("Percentage difference= ", ((realA - a3)/realA) * 100) #print difference
Output:
please find the attached file.
Explanation:
In the given Python code, firstly we import the math package after importing the package a "radius" variable is defined, that holds a value 10, in the next step, a "realA" variable is defined that calculate the area value.
In the next step, the "a1, a2, and a3" variable is used, which holds three values, that is "3.1, 3.14, and 3.141", and use the print method to print its percentage difference value.

Convert the following to CNF: S→SS|AB|B A→aAAa B→ bBb|bb|Ꜫ C→ CC|a D→ aC|bb
Answers
To convert the given grammar into Chomsky Normal Form (CNF), we need to rewrite the rules and ensure that each production has only two non-terminals or one terminal on the right-hand side. Here is the converted CNF grammar:
1. S → SS | AB | B
2. A → AA
3. A → a
4. B → bBb | bb | ε
5. C → CC | a
6. D → aC | bb
Explanation:
1. The production S → SS has been retained as it is.
2. The production A → aAAa has been split into A → AA and A → a.
3. The production B → bBb has been split into B → bB and B → b.
4. The production B → bb has been kept as it is.
5. The production B → ε (empty string) has been denoted as B → ε.
6. The production C → CC has been retained as it is.
7. The production C → a has been kept as it is.
8. The production D → aC has been kept as it is.
9. The production D → bb has been kept as it is.
In summary, the given grammar has been converted into Chomsky Normal Form (CNF), where each production has either two non-terminals or one terminal on the right-hand side. This form is useful in various parsing and analysis algorithms.
For more questions on parsing, click on:
https://brainly.com/question/13211785
#SPJ8
Answer:
Explanation:
To convert the given grammar to Chomsky Normal Form (CNF), we need to follow a few steps:
Step 1: Eliminate ε-productions (productions that derive the empty string).
Step 2: Eliminate unit productions (productions of the form A → B).
Step 3: Convert long productions (productions with more than two non-terminals) into multiple productions.
Step 4: Convert terminals in remaining productions to new non-terminals.
Step 5: Ensure all productions are in the form A → BC (binary productions).
Applying these steps to the given grammar:
Step 1: Eliminate ε-productions
The given grammar doesn't have any ε-productions.
Step 2: Eliminate unit productions
The given grammar doesn't have any unit productions.
Step 3: Convert long productions
S → SS (Remains the same)
S → AB
A → aAAa
B → bBb
B → bb
C → CC
C → a
D → aC
D → bb
Step 4: Convert terminals
No changes are needed in this step as all terminals are already in the grammar.
Step 5: Ensure binary productions
The given grammar already consists of binary productions.
The converted grammar in Chomsky Normal Form (CNF) is:
S → SS | AB
A → aAAa
B → bBb | bb
C → CC | a
D → aC | bb
Note: The original grammar didn't include the production rules for the non-terminals 'S', 'C', and 'D'. I assumed the missing production rules based on the provided information.
Question 6 (5 points)
Raquel is searching for jeans online. She wants to make sure that she protects her
private information when she purchases items online. How can Raquel find out if her
private information will be safe on a particular website?
Asking her friends if they've used this website
Buying the jeans and checking her bank account occasionally
Requesting an email from the company for more information
Reading the website's privacy policy
Answers
While buying jeans online, Raquel find out if her private information will be safe on a particular website by reading website's privacy policy.
What is private information?The information like phone number, passwords, birthdates or IP address about an individual person has entered while logging or signing up on a website.
When Raqual is signing up on the shopping website, she must read the company's website privacy policies appeared before making any orders and start using the interface.
Thus, Raquel must read website's privacy policy.
Learn more about private information.
https://brainly.com/question/12839105
#SPJ2
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
which part of the image window is surrounded by a yellow dotted line
the menu bar
the toolbox
the ruler
the canvas
Answers
Answer:
the canvas
Explanation:
Answer:
D: Canvas
Explanation:
Which of the following groups might sign a non-disclosure agreement between them?
the local government and its citizens
a group of employees or contractors
a company and an employee or contractor
two competing businesses or companiesc
Answers
Answer: I believe the right answer is between a company and employee or contractor.
Explanation: I think this is the answer because a non-disclosure is a legal contract between a person and a company stating that all sensitive. information will be kept confidential.
Answer:a
Explanation:
Function of operating system in 150 words. Help pls
Answers
Functions of the Operating System and how it Works
The OS plays a vital role when it comes to starting and shutting down the computer which is also known as booting. Six steps take place when a computer is booting: The first step begins as soon as the computer is turned on, the electrical signal reaches to the components in the system unit through the power supply. During the second step, the processor chip is reset due to the electric signal and then it locates the ROM that contains the basic input/output system (BIOS), which is a firmware that contains the startup instructions of the computer. Next, the BIOS launches a series of tests to ensure hardware are working and connected properly, known as the power on self-test (POST), usually when the POST launches, the LED lights of the devices flicker, at times there will be messages displaying on the screen. The forth step takes place when the POST compares the result with the complementary metal-oxide-semiconductor (CMOS) chip data. CMOS uses battery power to preserve the information, data, and memory when the computer shut down. Besides that, it detects new devices and identifies them when these devices are connected to the computer. The “beep” sound usually results when the CMOS detects which later followed by the error messages. The fifth step proceeds when the POST completes without any interference where the BIOS will locate the OS files also known as the system files from any source of drive. The sixth steps occurs when the system file is located, which is then loaded into the RAM from its storage along the kernel of the OS. The system file then launches, and finally, the OS which was stored in memory takes control of the whole computer system. During the final step, the OS loads the information setting. Certain OS may request for user ID and password. After the OS loads, it displays the desktop screen and it starts up background processes.
The second function of the OS is by providing a user interface. The two types of user interface are the graphical user interface (GUI) and the command-line interface. The GUI basically provides user with an easy way to perform a command or task by having the menus with buttons or other pictures to allow user to click it with ease. Instead of having simple buttons to click on, advance users work with command-line interface to configure, manage and troubleshoot devices and other software. The command-line interface works only with commands by using the keyboard. To perform such command, one must type in the commands accurately with the exact spellings and punctuations.
OS also manages programs. It depends on certain OS, some OS can only run one program at a time, while some can run up to thousands of programs at the same time with one or multiple users. There are the single user/single tasking OS, single user/multitasking OS, multiuser OS, and the multiprocessing OS. When one multitasks, the program that is actively used by the user is said to be in the foreground, while the other programs are known to be in the background.
The OS’s fourth function is memory management. The OS does so by transferring the data and program instructions from the RAM to the hard disk when they are not needed at the moment because at times there is only limited space for the RAM when it has to perform other functions, when the same data and program instructions is needed again, the OS then transfer them from the hard disk to the RAM.
The fifth function of the OS is coordinating tasks. As the phrase implies, the OS determines the order of the tasks which are processed. User can adjust or set the priority of certain tasks, in which result the other tasks to queue up until the preceding task is performed.
Every hardware has a driver which acts like a manual. The sixth function in this case, allows the computer to identify and install it without having the computer to thoroughly “learn” all the details of the hardware. With the Plug and Play technology today, the OS can automatically configure the new devices as the devices are installed on the computer.
The OS is also very important by providing a consistent way for software to deal with hardware without having the computer to thoroughly learn all the details of hardware. The OS interacts with the hardware via drivers. An easy example would be installing a printer to many computers.
The seventh function allows user to easily connect to the internet instead of having to configure the tedious broadband service. OS can automatically configure the internet connection.
The OS also function as a performance monitor, which in this case identify and reports information about the software or the devices of the computer.
Without the OS, the computer is said to be useless and unable to perform. The example of a personal computer OS are: Windows7, Mac OS X, Linux, Amigo
Review how to write a for loop by choosing the output of this short program.
for counter in range(3):
print(counter * 2)
2
3
4
0
2
4
0
1
2
2
4
6
Answers
Answer:
The answer is 0 2 4. I hope this helps you out. Have a wonderful day and stay safe.
Explanation:
Answer: 0 2 4
Explanation: got it right on edgen
Type the correct answer in the box. Spell all words correctly.
Julio Is a manager in an MNC. He has to make a presentation to his team regarding the life cycle of the current project. The life cycle should
follow a specific sequence of steps. Which style of presentation is best suited for Julio's purpose?
Jullo should make a presentation
Reset
Next
s reserved.
Answers
Answer:
Julio is a manager at an MNC. He has to make a presentation to his team regarding the life cycle of the current project. The life cycle should follow a specific sequence of steps. Which style of presentation is best suited for Julio's purpose? Jullo should give a speech.
Explanation:
Answer: linear
Explanation:
Just got it right. Linear presentations are sequential.
Which of the following is true regarding technical writing? Only subject matter experts need to use it. It is useful in comparing the effectiveness of your method to other's methods. It should not be used to analyze the thinking of others. It's only useful for relaying information to college graduates.
Answers
The option that is true regarding technical writing is B. It is useful in comparing the effectiveness of your method to other's methods.
What is technical writing?Technical writing is an undoubtedly essential form of communication, primarily used to exposit intricate and technical information to a limited or wide-ranging assemblage. It is not necessarily intended for specialists alone, since comprehension and understanding of various technological concepts are often necessary in everyday life.
This type of writing allows one to thoroughly scrutinize and evaluate distinctive arrangements and approaches, while also comprehensively analyzing the thoughts and rationale behind different technical distributions.
Learn more about writing on
https://brainly.com/question/1643608
#SPJ1
Because of inability to manage those risk. How does this explain the team vulnerability with 5 points and each references
Answers
The team is vulnerable due to a lack of risk assessment. Without risk understanding, they could be caught off guard by events. (PMI, 2020) Ineffective risk strategies leave teams vulnerable to potential impacts.
What is the inability?Inadequate contingency planning can hinder response and recovery from materialized risks. Vulnerability due to lack of contingency planning.
Poor Communication and Collaboration: Ineffective communication and collaboration within the team can make it difficult to address risks collectively.
Learn more about inability from
https://brainly.com/question/30845825
#SPJ1
4. SHORT ANSWERS:
i. Suppose tree T is a min heap of height 3.
- What is the largest number of nodes that T can have? _____________________
- What is the smallest number of nodes that T can have? ____________________
ii. The worst case complexity of deleting any arbitrary node element from heap is ___________
Answers
Answer:
i. A min heap of height 3 will have a root node with two children, each of which has two children of its own, resulting in a total of 7 nodes at the bottom level. Therefore:
The largest number of nodes that T can have is 1 + 2 + 4 + 7 = 14.
The smallest number of nodes that T can have is 1 + 2 + 4 = 7.
ii. The worst case complexity of deleting any arbitrary node element from a heap is O(log n), where n is the number of nodes in the heap. This is because deleting a node from a heap requires maintaining the heap property, which involves swapping the deleted node with its child nodes in order to ensure that the heap remains complete and that the heap property is satisfied. This process requires traversing the height of the tree, which has a worst-case complexity of O(log n).
Explanation:
Convert (3ABC) 16 to decimal number systam
Answers
System testing – During this stage, the software design is realized as a set of programs units. Unit testing involves verifying that each unit meets its specificatio
Answers
System testing is a crucial stage where the software design is implemented as a collection of program units.
What is Unit testing?Unit testing plays a vital role during this phase as it focuses on validating each unit's compliance with its specifications. Unit testing entails testing individual units or components of the software to ensure their functionality, reliability, and correctness.
It involves executing test cases, evaluating inputs and outputs, and verifying if the units perform as expected. By conducting unit testing, developers can identify and rectify any defects or issues within individual units before integrating them into the larger system, promoting overall software quality.
Read more about System testing here:
https://brainly.com/question/29511803
#SPJ1
Write first 20 decimal dijits in the base 3
Answers
Answer:
first 20 decimal dijits in the base 3
Explanation:
i wrote what you said
can anyone teach me the basics of lua scripts 50 points
like how do i tell lua to move a object or send me a prompt asking me to do something
Answers
Answer:
are you talking about about a game, or coding?