Task:
Lab – 14
String Helper
Write a Java program that creates a helper class called StringHelper. This class has methods not already built into strings, but should be because they are super useful.
First create a class called StringHelper which has the following static methods
meshStrings: This method takes in two strings as parameters, meshes them together, and returns
the meshed strings. Meshing alternates the each character in the first string with every character in the next string. If there are not enough characters to fully mesh then the rest will be appended to the end. For instance if the two strings were "harp" and "fiddle" the returned string will be "hfairdpdle".
replaceVowelsWithOodle: This method takes in one string as a parameter, and returns the string with every vowel (a,e,i,o,u) replaced by the phrase "oodle". For instance if the string is "burrito" then the returned string would be "boodlerroodletoodle". Also, case does not matter.
weight: Much like length returns the number of characters in a string, the weight gives the weight in kilograms. This method takes in a string and returns a double value corresponding to its weight. Everyone knows that a word’s weight is determined by
each vowel (a,e,i,o,u) counting as 2.5 kilograms and
each consonant as 3.4 kilograms.
create a class called StringHelperTester
Finally
This class DOES HAVE a main method
Test each method multiple times to determine if they work.
Sample Output:
Welcome to the String Helper Tester! Enter any two words:
harp fiddle
Meshing harp with fiddle
hfairdpdle
Enter a word:
burrito
Replacing vowels with oodle in the word burrito Boodlerroodletoodle
Enter a word to determine its weight:
taco
The weight of the word taco is 11.8
Answers
The given task requires the creation of a Java program with a helper class called StringHelper. The StringHelper class should have static methods to perform useful operations on strings. The methods include meshing two strings together, replacing vowels with the phrase "oodle" in a string, and calculating the weight of a string based on the number of vowels and consonants.
To accomplish the task, you need to create a class called StringHelper with three static methods: meshStrings, replaceVowelsWithOodle, and weight. The meshStrings method takes two strings, alternates their characters, and returns the meshed string. The replaceVowelsWithOodle method replaces vowels in a string with "oodle" and returns the modified string. The weight method calculates the weight of a string based on the number of vowels and consonants.
To test these methods, create a separate class called StringHelperTester with a main method. Inside the main method, prompt the user for inputs, call the respective methods, and display the results.
To know more about static methods here: brainly.com/question/31454032
#SPJ11
Related Questions
Write a script that takes a path to the folder as an argument, and prints the highest build number
Answers
The script uses the `os` and `glob` modules to find the files in a folder that match a specific pattern, extract the build numbers from the file names, and find the highest build number. By following these steps and using the provided example, you can write a script that takes a path to the folder as an argument and prints the highest build number.
To write a script that takes a path to the folder as an argument and prints the highest build number, you can follow these steps:
1. First, import the necessary modules for working with files and folders in Python, such as `os` and `glob`.
2. Define a function, let's say `get_highest_build_number`, that takes the folder path as an argument.
3. Inside the function, use the `glob` module to get a list of all the files in the folder that match a specific pattern, such as `build*.txt`. This assumes that the build numbers are included in the file names and follow a consistent pattern.
4. Create an empty list, let's call it `build_numbers`, to store the extracted build numbers.
5. Iterate over the list of files obtained from the previous step. For each file, extract the build number from the file name by splitting the file name on a delimiter (such as '-') and taking the portion that corresponds to the build number.
6. Convert the extracted build number to an integer and append it to the `build_numbers` list.
7. Use the `max` function to find the highest build number in the `build_numbers` list.
8. Finally, return or print the highest build number.
To write a script that takes a path to the folder as an argument and prints the highest build number, you can use Python's `os` and `glob` modules. The `os` module provides a way to interact with the operating system, while the `glob` module is used to find all the pathnames matching a specified pattern.
First, import the necessary modules:
```python
import os
import glob
```
Next, define a function that takes the folder path as an argument:
```python
def get_highest_build_number(folder_path):
# code goes here
```
Inside the function, use the `glob` module to get a list of all the files in the folder that match a specific pattern. In this case, we can use the pattern `'build*.txt'`, assuming that the build numbers are included in the file names and follow a consistent pattern. This will return a list of file paths:
```python
files = glob.glob(os.path.join(folder_path, 'build*.txt'))
```
Create an empty list to store the extracted build numbers:
```python
build_numbers = []
```
Now, iterate over the list of files and extract the build numbers from the file names. To do this, split the file name on a delimiter (such as '-') and take the portion that corresponds to the build number. Convert the extracted build number to an integer and append it to the `build_numbers` list:
```python
for file in files:
file_name = os.path.basename(file)
build_number = int(file_name.split('-')[1]) # Assuming the build number is after the first '-'
build_numbers.append(build_number)
```
After extracting all the build numbers, use the `max` function to find the highest build number in the `build_numbers` list:
```python
highest_build_number = max(build_numbers)
```
Finally, return or print the highest build number:
```python
return highest_build_number
```
To use the script, provide the folder path as an argument and call the function:
```python
folder_path = '/path/to/folder'
highest_build = get_highest_build_number(folder_path)
print("The highest build number is:", highest_build)
```
This will output the highest build number in the given folder path.
The script uses the `os` and `glob` modules to find the files in a folder that match a specific pattern, extract the build numbers from the file names, and find the highest build number. By following these steps and using the provided example, you can write a script that takes a path to the folder as an argument and prints the highest build number.
To learn more about operating system visit:
brainly.com/question/29532405
#SPJ11
you have instructed users not to store passwords for websites on their computers. you need to examine a user's computer to determine if the policy is being followed
Answers
Yes, I can help you examine a user's computer to determine if the policy of not storing passwords for websites is being followed.
How can we examine a user's computer to determine if the policy of not storing passwords for websites is being followed?To examine a user's computer and determine if the policy of not storing passwords for websites is being followed, we can follow these steps:
1. Check browser settings: Verify if the user's web browser has the option to save passwords disabled. This can be done by accessing the browser's settings and checking the password management section.
2. Review stored passwords: Look for any saved passwords within the browser or any password management applications installed on the computer. Evaluate the list of stored passwords to identify if there are any website passwords saved.
3. Search for password manager software: Scan the computer for any password manager software or applications that may be used to store website passwords. Check the software settings and stored passwords, if applicable.
4. Assess browser extensions: Examine the installed browser extensions or add-ons for any password management tools. These extensions might indicate that passwords are being stored.
5. Analyze browser history: Review the user's browsing history to identify any patterns or indications of password storage, such as repeated automatic logins without requiring manual entry of credentials.
6. Check system files: Look for any text files or documents that may contain passwords. Users sometimes store passwords in local files, so a thorough search should be conducted.
Learn more about storing passwords
brainly.com/question/33644617
#SPJ11
what part of the meat help you identify the less tender cuts
Answers
If a muscle gets a lot of exercise in an animal it will be a less tender cut of meat.
recall that the uart base address is 0xf0000000 and the uart registers and buffers used in project 3, in order, are the command register, status register, and receive buffer. if register $s0 contained 0xf0000000, what address offset from $s0 would need to be used in order to access the status register? group of answer choices -8 -4 0 4 8 none of the above
Answers
We want to access the status register, we would need to use the address offset of 4 from register $s0.
If register $s0 contains the base address of the UART, which is 0xf0000000, then we need to calculate the offset required to access the status register.
Recall that the order of the UART registers and buffers used in project 3 is the command register, status register, and receive buffer. The size of each register is 4 bytes, which means that the status register is located 4 bytes after the command register.
To calculate the offset required to access the status register, we simply add 4 to the base address stored in register $s0. This means that the correct answer is option (D) 4.
Therefore, if This would give us the address of the status register, which we could use to read or write data from or to the register.
To learn more about : address
https://brainly.com/question/30630608
#SPJ11
What is a border line
Answers
Answer:
a border line is what separates to places from one another like if i were to go to mexico i would have to cross the border
Explanation:
Depends on context.
- Could be a line marking a border
- Barely acceptable; borderline
Example:
She was a borderline candidate.
This means that she barely made it as a candidate role.
Which of the components of the systems model provides information so
the system can adjust its function? *
A. input
B. feedback
C. process
D. output
Answers
Answer: Feedback
Explanation:
The input components of the systems model can consist of resources like people, energy, tools, capital, etc.
The feedback components of the systems model provides information so
the system can adjust its function. An example of the feedback mechanism for a system is the progress bar which shows when one is downloading a file on iTunes.
one everyday example of a VR schedule is the lottery true false
Answers
one everyday example of a VR schedule is the lottery This statement is False.
The statement "One everyday example of a VR schedule is the lottery" is false. VR (Variable Ratio) schedule refers to a type of reinforcement schedule used in operant conditioning, where reinforcement is provided after a varying number of responses. It is commonly associated with maintaining high rates of behavior.
The lottery, on the other hand, is a form of gambling and a random chance-based activity where participants purchase tickets with the hope of winning a prize. It does not follow the principles of a VR schedule as defined in behavioral psychology.
In the context of everyday examples of VR schedules, it is more appropriate to consider scenarios such as slot machines in casinos, video game rewards, or certain types of sales promotions that offer rewards or discounts based on a variable and unpredictable pattern of behavior or purchases.
learn more about "lottery":- https://brainly.com/question/9216200
#SPJ11
Write a program that accepts the lengths of three sides of a triangle as inputs. the program output should indicate whether or not the triangle is a right triangle. recall from the pythagorean theorem that in a right triangle, the square of one side equals the sum of the squares of the other two sides. use the triangle is a right triangle. and the triangle is not a right triangle. as your final outputs.
Answers
The code will have to obey the Pythagorean theorem that says square of the hypotenuse side is equals to the sum of the squares of the other legs.
How to write a code that check if a triangle is a right angle by using Pythagoras theorem?
The code is written in python.
def right_triangle(x, y, z):
if x**2 + y**2 == z**2 or y**2 + z**2 == x**2 or z**2 + x**2 == y**2:
print("it is a right angle triangle")
else:
print("it is not a right angle triangle")
right_triangle(6, 10, 8)
Code explanationwe defined as function named "right_triangle". x, y and z are argument which are the length of the triangle.Then we check if the sides obeys Pythagoras theorem.If it does we print a positive statement else we print a negative statement.Learn more about python at: https://brainly.com/question/21437082
#SPJ4

Name the substance you think is in the cylinder that you cannot see and prevents the plunger from going all the way in even when you push the plunger hard
Answers
The substance I think is in the cylinder that you cannot see and prevents the plunger from going all the way in even when you push the plunger hard is Air.
What do you feel as when one push the plunger?When a person push on the plunger, the person can feel the air pushing it back. When a person has stop pushing, the air inside the syringe will tend to return to its normal size.
Note that there are a lot of ways to compress air. A person can do so by squeezing a specified volume of air into a smaller space.
Learn more about cylinder from
https://brainly.com/question/26806820
Which of the following can be used to locate data in a particular column?
A. VLOOKUP
B. HLOOKUP
C. CLOOKUP
D. RLOOKUP
Answers
Answer:
A. VLOOKUP
Explanation:
VLOOKUP is an Excel function to look up data in a table organized vertically. VLOOKUP supports approximate and exact matching, and wildcards (* ?) for partial matches. Lookup values must appear in the first column of the table passed into VLOOKUP.
Purpose
Lookup a value in a table by matching on the first column
Return value
The matched value from a table.
Syntax
=VLOOKUP (value, table, col_index, [range_lookup])
Arguments
value - The value to look for in the first column of a table.
table - The table from which to retrieve a value.
col_index - The column in the table from which to retrieve a value.
range_lookup - [optional] TRUE = approximate match (default). FALSE = exact match.

which term describes a means of separating the operation of an application from the rest of the operating system?
Answers
The term describes a means of separating the operation of an application from the rest of the operating system Sandboxing.
What is Sandboxing?Sandboxing is a cybersecurity technique in which code is executed, observed, and analyzed in a secure, isolated setting on a network that resembles end-user operating systems. Sandboxing is widely used to analyse untested or untrusted code and is intended to stop dangers from entering the network. Users can execute applications or browse files in a sandbox, an isolated testing environment, without having any negative effects on the platform, system, or application on which they are running. Sandboxes are used by software developers to test new computer code. Sandboxes are used by cybersecurity experts to evaluate potentially harmful software.To learn more about Sandboxing refer to:
https://brainly.com/question/28232519
#SPJ4
what term is used to express the thickness or height of a switch?
Answers
A common term used to describe the thickness or height of a switch is "profile."
What is the term used to denote the dimensions or stature of a switch?The profile of a switch refers to its thickness or height, which determines its physical dimensions and how it fits into a device or a circuit. It is an essential factor to consider when designing or selecting switches for various applications.
The profile can vary depending on the specific type of switch and its intended use, such as low-profile switches for compact devices or high-profile switches for applications requiring a more substantial physical presence.
Learn more about Physical dimensions
brainly.com/question/28862417
#SPJ11
Write a pseudo code to complete the factorial of 5 recursively and print the value on the screen. I’ll mark brianliest
Answers
Answer:
number = int(input('Enter number: '))
factorial = 1
for i in range(1, number + 1):
factorial = factorial * i
print(factorial)
You will need to input 5 when you run the code. Or you can add change the "number" to "number = 5"
1-5 Safety measures in the use of kitchen tools and equipment.
Answers
Answer:
Safety measures are as follows;
Explanation:
Hold the delicate instruments cautiously to use them.Require appropriate use of the equipment in the kitchen.Users should remove these defective instruments or discard of them.During and before use, check that perhaps the resources that will be used are indeed safe.In a cold and dry spot, all equipment must be kept.How to make 4k quality in cc
Answers
Answer:
become professional
Explanation:
it is essential that you do practice hard
During Program Increment (PI) execution, the System Team is unclear about how to test some of the larger Features. What should a Release Train Engineer do?
a) Escalate the problem to senior management to get the required action
b) Allow the problem to reach a critical point knowing that a minor failure is a technique for learning
c) Direct Product Management to define the use cases for the Features
d) Encourage the System Team and Product Management to meet and collaborate on a solution
Answers
The System Team is unclear about how to test some of the larger Features. What should a Release Train Engineer do is: d) Encourage the System Team and Product Management to meet and collaborate on a solution.
During Program Increment (PI) execution, it is not uncommon for the System Team to face challenges when testing larger Features. In such a situation, a Release Train Engineer (RTE) should encourage the System Team and Product Management to meet and collaborate on a solution. This approach promotes teamwork and ensures that everyone involved is working towards a common goal of delivering high-quality Features.
The collaboration between the System Team and Product Management can help identify gaps in testing and define the use cases for the Features. This can be an iterative process that involves regular feedback and discussions to ensure that the testing strategy is effective and aligned with the business goals. So the answer is D.
Learn more about System Team: https://brainly.com/question/30456614
#SPJ11
iifes are one way to prevent the pollution of the global namespace by creating functions and variables that will disappear after the iife has been invoked.
Answers
The global namespace in JavaScript is the space where all variables, functions, and objects defined without a specific scope reside. When multiple scripts or libraries are used within the same application, there is a possibility of naming conflicts and unintended overwriting of variables.
The benefit of using an IIFE is that any variables or functions defined within it are kept separate from the global namespace. They only exist and are accessible within the scope of the IIFE, avoiding potential naming conflicts with other scripts or libraries.
By using IIFEs, developers can create modular and self-contained pieces of code that don't pollute the global namespace. This helps maintain code organization, reduces the likelihood of naming collisions, and improves code encapsulation and reusability.
Learn more about global namespace https://brainly.com/question/14330126
#SPJ11
Which of the following will uniquely select the div tag located on line 7? 1. c 3. = 1 Down the Rabbit-Hole
Alice was beginning to get very tired ...
Alice
Down, down, down. Would the fall never come to an end
I wonder if I shall fall right ..
Select one: a. #aa O b..aa OOO d. aa.div e divAnswers
The term that will uniquely select the div tag located on line 7 is :
(e) div
The div tag on line 7 can be uniquely selected using the tag name "div".
Option a) uses an ID selector (#aa) which is not present in the HTML code provided.
Option b) uses a class selector (.aa) which is also not present.
Option d) uses a descendant selector (aa div) which assumes that there is an "aa" element that is a parent or ancestor of the "div" element, which is not present in the code.
Therefore, the the term that will uniquely select the div tag located on line 7 is div. Hence, the correct option is e) div.
To learn more about ID selector visit : https://brainly.com/question/24204870
#SPJ11
Common Gateway interface
_____ is a standard method or protocol for web pages to request special processing on the web server, such as database queries, sending e-mails, or handling form data.
Answers
Web pages can use the Common Gateway interface, a common method or protocol, to ask the web server to perform specific tasks, like running database queries, sending emails, or handling form data.
What is the meaning of interface?In the Java programming language, an interface is an abstract type used to specify a behaviour that classes must implement. They are a lot like protocols. Only method signature and constant declarations may be included in interfaces, which are declared using the interface keyword.
When a class implements an interface, it can be more formal about the behaviour it guarantees to deliver. The contract that interfaces create between a class and the outside world is upheld at build time by the compiler.
Learn more about interface from here:
https://brainly.com/question/14235253
#SPJ1
write a matlab program that determines and displays all the keith numbers betwenn 10 and 99
Answers
```matlab
function findKeithNumbers()
for num = 10:99
digits = num2str(num) - '0'; % Convert number to an array of its digits
sequence = digits; % Initialize the Fibonacci-like sequence with the digits
while sequence(end) < num % Continue generating sequence until it reaches or exceeds the number
nextElement = sum(sequence(end-1:end)); % Calculate the next element as the sum of the previous two
sequence = [sequence, nextElement]; % Append the next element to the sequence
end
if sequence(end) == num % Check if the number is a Keith number
disp(num); % Display the Keith number
end
end
end
```
To run the program, simply call the `findKeithNumbers` function in the MATLAB command window:
```matlab
findKeithNumbers()
```
This program iterates through the numbers from 10 to 99. For each number, it generates a Fibonacci-like sequence based on the tens and unit digits. If the last element of the sequence matches the original number, it is considered a Keith number and displayed.
Know more about Keith numbers:
https://brainly.com/question/31480036
#SPJ4
hello guys,
What is the features of c programming language? explain all point.
Answers
Answer: Most peoples opinions say "Simple and Efficient. The basic syntax style of implementing C language is very simple and easy to learn"
Some say "Fast to learn"
Explanation:
It is a very low-level access to memory, a simple set of keywords, and a clean style. so many features make C language suitable for system programmings like an operating system.
c programming language and it gives it an edge over other dynamic languages.
Answer: This is the most important features of C programming language.
Explanation:
It is a well-known fact that statically typed programming languages are faster than dynamic ones. (A statically-typed language is a language (such as Java, C, or C++) where variable types are known at compile time.)
Which of the following are characteristics of the Boolean data type? Check all that apply
It holds infinite values.
It uses operators such as AND, OR, and NOT
It holds a TRUE or FALSE value.
It is named after a nineteenth-century mathematician and logician
Help I’m timed !!
Answers
Answer:
It uses operators such as AND, OR, and NOT.
It holds a TRUE or FALSE value.
It is named after a nineteenth-century mathematician and logician
Explanation: Just did it on edg
Answer:
It uses operators such as AND, OR, and NOT.
It holds a TRUE or FALSE value.
It is named after a nineteenth-century mathematician and logician
Explanation:
Got it correct on edge
Where does Reiner take eren after they have a fight?
Answers
Answer:
So Reiner And Bertoldt wanted to take Eren and Ymir to Marley, a nation on the other side of the ocean so they can be devoured and there power can be given to a warrior canidate.
Answer:
what season tho?
Explanation:
Reiner took eren to the Forest
PLEASE HELP ASAP (answer is needed in Java) 70 POINTS
In this exercise, you will need to write a program that asks the user to enter different positive numbers.
After each number is entered, print out which number is the maximum and which number is the minimum of the numbers they have entered so far.
Stop asking for numbers when the user enters -1.
Possible output:
Enter a number (-1 to quit):
100
Smallest # so far: 100
Largest # so far: 100
Enter a number (-1 to quit):
4
Smallest # so far: 4
Largest # so far: 100
Enter a number (-1 to quit):
25
Smallest # so far: 4
Largest # so far: 100
Enter a number (-1 to quit):
1
Smallest # so far: 1
Largest # so far: 100
Enter a number (-1 to quit):
200
Smallest # so far: 1
Largest # so far: 200
Enter a number (-1 to quit):
-1
Answers
import java.util.Scanner;
public class MyClass1 {
public static void main(String args[]) {
Scanner scan = new Scanner(System.in);
int smallest = 0, largest = 0, num, count = 0;
while (true){
System.out.println("Enter a number (-1 to quit): ");
num = scan.nextInt();
if (num == -1){
System.exit(0);
}
else if (num < 0){
System.out.println("Please enter a positive number!");
}
else{
if (num > largest){
largest = num;
}
if (num < smallest || count == 0){
smallest = num;
count++;
}
System.out.println("Smallest # so far: "+smallest);
System.out.println("Largest # so far: "+largest);
}
}
}
}
I hope this helps! If you have any other questions, I'll do my best to answer them.
Java exists a widely utilized object-oriented programming language and software platform. Sun Microsystems initially introduced Java, a programming language and computing platform, in 1995.
What is meant by java?Sun Microsystems initially introduced Java, a programming language and computing platform, in 1995. It has grown from its modest origins to power a significant portion of the digital world of today by offering the solid foundation upon which numerous services and applications are developed.
The object-oriented programming language and software platform known as Java are used by millions of devices, including laptops, cellphones, gaming consoles, medical equipment, and many others. The syntax and guiding ideas of Java are derived from C and C++.
The program is as follows:
import java.util.Scanner;
public class MyClass1 {
public static void main(String args[]) {
Scanner scan = new Scanner(System.in);
int smallest = 0, largest = 0, num, count = 0;
while (true){
System.out.println("Enter a number (-1 to quit): ");
num = scan.nextInt();
if (num == -1){
System.exit(0);
}
else if (num < 0){
System.out.println("Please enter a positive number!");
}
else{
if (num > largest){
largest = num;
}
if (num < smallest || count == 0){
smallest = num;
count++;
}
System.out.println("Smallest # so far: "+smallest);
System.out.println("Largest # so far: "+largest);
}
}
}
}
To learn more about Java refer to:
https://brainly.com/question/25458754
#SPJ2
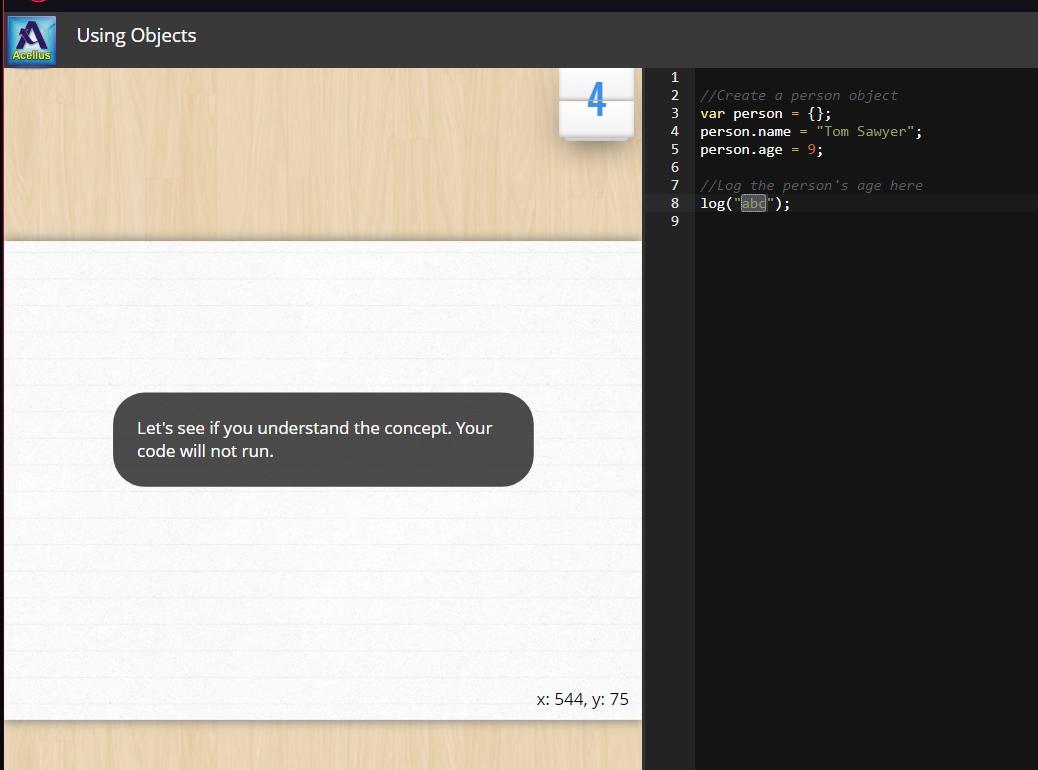
log the 'age' property of the 'person' object
Answers
Answer:
vauwnwkwiauauwiajhwbwbw
Escribe un ejemplo de:• Software de aplicación. • Software de diagnóstico. • Software de sistema. ayudenme plis, me toca entregar esto hoy. >﹏<
Answers
Answer:
1. Software de aplicación: Microsoft Word.
2. Software de diagnóstico: Speccy.
3. Software de sistema: Windows operating system (OS).
Explanation:
Un software puede definirse como un conjunto de instrucciones ejecutables (códigos) o una colección de datos que se utiliza normalmente para instruir a una computadora sobre cómo realizar una tarea específica y resolver un problema en particular.
Básicamente, los softwares se clasifican en tres (3) categorías principales y estas son;
1. Software de aplicación: es un software de usuario final que normalmente está diseñado para realizar tareas y funciones específicas.
Algunos ejemplos de software de aplicación son Microsoft PowerPoint, Notepad, Windows Media player, Firefox, Go-ogle Chrome, Adobe Photoshop, AutoCAD, etc.
2. Software de diagnóstico: estos son programas de software que se utilizan para solucionar problemas y posiblemente reparar un sistema informático.
Algunos ejemplos de software de diagnóstico son Speccy, Windows Sysinternals Suite, System Explorer, hddscan, HWiNFO, SIW (System Information for Windows), CPU-Z, HD Tune, etc.
3. Software de sistema: es un software que normalmente está diseñado para ejecutar el hardware de la computadora y todas las demás aplicaciones de software.
Algunos ejemplos de software del sistema son Linux, Windows OS, Mac OS, WinZip, McAfee antivirus, Norton antivirus, Avast antivirus, Piriform CCleaner, Ubuntu, etc.
List six characteristics you would typically find
in each block of a 3D mine planning
block model.
Answers
Answer:
Explanation:
In a 3D mine planning block model, six characteristics typically found in each block are:
Block Coordinates: Each block in the model is assigned specific coordinates that define its position in the three-dimensional space. These coordinates help locate and identify the block within the mine planning model.
Block Dimensions: The size and shape of each block are specified in terms of its length, width, and height. These dimensions determine the volume of the block and are essential for calculating its physical properties and resource estimates.
Geological Attributes: Each block is assigned geological attributes such as rock type, mineral content, grade, or other relevant geological information. These attributes help characterize the composition and quality of the material within the block.
Geotechnical Properties: Geotechnical properties include characteristics related to the stability and behavior of the block, such as rock strength, structural features, and stability indicators. These properties are important for mine planning, designing appropriate mining methods, and ensuring safety.
Resource Estimates: Each block may have estimates of various resources, such as mineral reserves, ore tonnage, or grade. These estimates are based on geological data, drilling information, and resource modeling techniques. Resource estimates assist in determining the economic viability and potential value of the mine.
Mining Parameters: Mining parameters specific to each block include factors like mining method, extraction sequence, dilution, and recovery rates. These parameters influence the extraction and production planning for the block, optimizing resource utilization and maximizing operational efficiency.
These characteristics help define the properties, geological context, and operational considerations associated with each block in a 3D mine planning block model. They form the basis for decision-making in mine planning, production scheduling, and resource management.
what is modem please give me answer
Answers
Answer:
a combined device for modulations and demodulations
Write a program in java to input N numbers from the user in a Single Dimensional Array .Now, display only those numbers that are palindrome
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that input N numbers from the user in a Single Dimensional Array .
Writting the code:class GFG {
// Function to reverse a number n
static int reverse(int n)
{
int d = 0, s = 0;
while (n > 0) {
d = n % 10;
s = s * 10 + d;
n = n / 10;
}
return s;
}
// Function to check if a number n is
// palindrome
static boolean isPalin(int n)
{
// If n is equal to the reverse of n
// it is a palindrome
return n == reverse(n);
}
// Function to calculate sum of all array
// elements which are palindrome
static int sumOfArray(int[] arr, int n)
{
int s = 0;
for (int i = 0; i < n; i++) {
if ((arr[i] > 10) && isPalin(arr[i])) {
// summation of all palindrome numbers
// present in array
s += arr[i];
}
}
return s;
}
// Driver Code
public static void main(String[] args)
{
int n = 6;
int[] arr = { 12, 313, 11, 44, 9, 1 };
System.out.println(sumOfArray(arr, n));
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Which expression is equivalent to 0.09 X 27.3?
Answers
Answer:
2.457 that the answer
Explanation:
I hope it helps