T/F,when processing cloud evidence, in addition to the cloud artifacts, axiom will automatically select and search for all computer and mobile artifacts across the cloud evidence.
Answers
True/False: When processing cloud evidence, in addition to the cloud artifacts, Axiom will automatically select and search for all computer and mobile artifacts across the cloud evidence.It is True.
Explanation: When processing cloud evidence in Axiom, the software automatically analyzes the collected data. An artifact is anything that is made by humans. it can be discovered during an archeological gig, but the hand drawing you made in your kindergarten is also an artifact!.The best example of an artifact is SigThe fact that the milk bottle was empty and the cap was gone suggests that Sig may have used the milk recently and forgot to put the cap back on, or possibly that someone else in the household used it. In addition to cloud artifacts, Axiom will search for all relevant computer and mobile artifacts that may be present within the cloud evidence, This allows for a comprehensive analysis of all available data, ensuring a thorough investigation of the cloud evidence.
Learn More About Artifact: https://brainly.com/question/681742
#SPJ11
Related Questions
2. According to the U.S. Department of Labor Statistics, which field of drafting has the highest median
salary:
a.Architectural
b.Mechanical
c.Electronics
d. Radiological
Answers
What are the three main elements common to all radio ads?
Answers
If my answers wrong please tell me :D
have you gone/done into things that you forget to close/settle?
Answers
Answer: AT SOME CIRCUMSTANCES YES
Explanation: WELL ONE EXAMPLE WAS OUR GAMING GROUP WHICH WAS MADE OF ABOUT 2 YEARS AGO AND THERE ARE STILL TO PEOPLE IN THE GROUP WHEN WE DON'T EVEN USE ANYMORE , CAN YOU BELIEVE IT ?
need help on question 5! no links pls

Answers
Answer: less than 50%, it’s about 49%
Explanation:
Answer:
59.5
so I would say the 3 third option
hris has received an email that was entirely written using capitalization. He needs to paste this text into another document but also ensure that the capitalization is removed.
What should Chris do?
Answers
JAVA
Write a program to find the sum of the given series:
S = 1 + (1*2) + (1*2*3) + --------- to 10 terms.
plz help....
Answers
public class MyClass {
public static void main(String args[]) {
int x = 1;
int total = 0;
for (int i = 1; i <= 10; i++){
x *= i;
total += x;
}
System.out.println(total);
}
}
This program finds the sum of that series to the tenth term, the sum is: 4037913. I hope this helps.
explain whether the information in the microsoft office file properties is reliable for forensic purposes.
Answers
The information found in Microsoft Office file properties may not always be reliable for forensic purposes.
While these properties can provide valuable information such as the file creator, creation and modification dates, and version, they can also be easily manipulated or deleted. In addition, metadata stored in file properties may not be comprehensive and may not capture all actions taken on the file.
Therefore, it is important to supplement the information found in file properties with other forensic techniques and tools to ensure the accuracy and reliability of the evidence collected.
You can learn more about Microsoft Office at: brainly.com/question/14984556
#SPJ11
Which type of chart is used to chart progress over time?
Answers
Answer: Timeline
Explanation:
a security clearance is a component of a data classification scheme that assigns a status level to systems to designate the maximum level of classified data that may be stored on it. false true
Answers
The given statement "a security clearance is a part of a data categorization scheme that gives systems a status level in order to specify the highest level of classified material that can be stored on it" is FALSE.
What is a security clearance?After passing a rigorous background check, individuals are given the status of having access to restricted locations or to classified information (state or organizational secrets).
The phrase "security clearance" is also occasionally used in private businesses that follow a systematic procedure to screen applicants for access to confidential data.
A security clearance is not a component of the data classification system that assigns systems a status level to indicate the greatest level of classified data that can be kept on them.
In most cases, a clearance is not enough to grant access; the organization must additionally decide that the cleared person needs to know a certain amount of information.
No one should be given automatic access to classified material due to their position, rank, or security clearance.
Therefore, the given statement "a security clearance is a part of a data categorization scheme that gives systems a status level in order to specify the highest level of classified material that can be stored on it" is FALSE.
Know more about security clearance here:
https://brainly.com/question/25720881
#SPJ4
rapid growth in the computer security industry has largely occurred without adequate research on the nature of cybercrimes and criminals.
Answers
The rapid growth in the computer security industry has indeed occurred without adequate research on the nature of cybercrimes and criminals.
While the industry has focused on developing and implementing security measures to protect against cyber threats, there has been a lack of comprehensive research into the motivations, techniques, and profiles of cybercriminals. This gap in knowledge hinders our ability to effectively combat cybercrimes. Allocate resources towards research on cybercrimes and criminals.
By studying their tactics, motivations, and patterns, we can better understand and anticipate cyber threats, leading to more effective security measures. Delve into specific research areas, methodologies, and potential collaborations between industry and academia. However, it is important to acknowledge that cybersecurity research is an ongoing and evolving field that requires continuous efforts to keep pace with the ever-changing landscape of cyber threats.
To know more about security visit:
https://brainly.com/question/32133916
#SPJ11
Please show work with excel formulas
Esfandairi Enterprises is considering a new three-year expansion project that requires an initial fixed asset investment of \( \$ 2.18 \) million. The fixed asset will be depreciated straightline to z
Answers
The annual straight-line depreciation expense for the fixed asset is $726,667.
To calculate the annual straight-line depreciation expense, we need to divide the initial fixed asset investment by the useful life of the asset. In this case, the initial fixed asset investment is $2.18 million and the project's duration is three years.
Using the straight-line depreciation method, the annual depreciation expense is determined by dividing the initial investment by the useful life:
Depreciation Expense = Initial Investment / Useful Life
Depreciation Expense = $2,180,000 / 3
Depreciation Expense = $726,667
This means that Esfandairi Enterprises can expect an annual depreciation expense of $726,667 for the three-year duration of the project.
Learn more about fixed asset
brainly.com/question/14392032
#SPJ11
PLEASE HELP! WILL GIVE BRAINLIEST

Answers
Answer:
Explanation:find out
Amara is designing a website to encourage people in a city to vote in local elections. She wants to include a web page that shows first-time voters the steps to follow to register and vote in the elections. How can Amara best use multimedia to show the voting process on the web page?
A.
by providing a paragraph of instructions with pictures
B.
by providing an audio file along with downloadable pictures
C.
by creating a brief animation with optional text instructions
D.
by creating a static slideshow of the steps showing just pictures
E.
by adding automatically playing audio with text instructions
Answers
Answer:
c.
by creating a brief animation with optional text insturctions
Hope this helps! Brainliest please
are a fast and efficient way of transmitting frequently recurring messages to which receiver reaction is likely favorable or neutral.
Answers
Automated email campaigns are a fast and efficient way to transmit recurring messages, likely to receive favorable or neutral reactions from recipients.
Automated email campaigns are a fast and efficient way of transmitting frequently recurring messages to which receiver reaction is likely favorable or neutral.
These campaigns involve sending pre-designed and pre-scheduled emails to a targeted audience. Here are some reasons why automated email campaigns are effective:
1. Time and Resource Efficiency: Automated email campaigns eliminate the need for manual, one-by-one email sending, saving time and resources. Once the campaign is set up, the emails are sent automatically based on predefined triggers or schedules.
2. Personalization and Segmentation: By leveraging customer data and segmentation, automated email campaigns allow for personalized messaging.
Tailoring the content to specific customer interests, preferences, or behaviors increases the relevance of the emails and improves the chances of a positive or neutral reaction.
3. Consistency and Timeliness: Automated campaigns ensure consistent delivery of messages at the right time.
Whether it's sending welcome emails, product recommendations, or transactional notifications, the timely and consistent communication helps maintain engagement and foster positive customer experiences.
4. Testing and Optimization: Automated campaigns enable marketers to test different email variations and track performance metrics.
By analyzing open rates, click-through rates, and conversions, they can optimize the campaign content, design, and timing to maximize favorable or neutral receiver reactions.
5. Scalability: Automated campaigns can handle a large volume of emails without significant manual effort. This scalability makes them ideal for businesses with a growing customer base or those looking to reach a broader audience.
Overall, automated email campaigns offer a streamlined approach to engage with customers, deliver targeted messages, and achieve favorable or neutral receiver reactions.
By leveraging technology and data-driven strategies, businesses can effectively communicate with their audience and drive desired outcomes.
Learn more about email:
https://brainly.com/question/31206705
#SPJ11
Saving space is not an ideal reason for cropping a photo to be used in technical communication. What is a better reason?.
Answers
Saving space is not an ideal reason for cropping a photo to be used in a technical document is a false statement and a better reason is that if you as a person is doing so, it helps you make your point.
What do you mean by technical document?Technical writing is any form of writing that explains the use, intent, design, or architecture of a good or service. Its objective is to describe a service that a company provides. Technical publications come in a variety of formats, each tailored to a certain audience.
Technical documentation is a catch-all word for the various types of data produced to explain the functionality, use, or architecture of a given good, system, or service.
The point you made mean effectively communicate an idea, as in I understand your point about skateboards being risky; your argument has been conveyed. In this phrase, "point" refers to "an important or crucial argument or suggestion.
Learn more about technical document from
https://brainly.com/question/7805567
#SPJ1
a user called to inform you that the laptop she purchased yesterday is malfunctioning and will not connect to her wireless network. you personally checked to verify that the wireless worked properly before the user left your office. the user states she rebooted the computer several times but the problem still persists.
Answers
The user should enable the wireless radio by pressing the proper function keys, and then they should try to connect to the wireless network.
What should one do as soon as possible when using a computer for work?Turning on the computer is the first thing to do. Locate and push the power button to accomplish this. Every computer has a power button, albeit it is located differently on each one. Your computer takes a while to start up after being turned on.
What indicate a computer is about to fail?Your computer may start to lag, freeze, crash, or start to send error messages. If numerous programs are performing strangely and the issues continue even after rebooting, this is quite concerning.
To know more about wireless network visit:-
https://brainly.com/question/14921244
#SPJ4
Question:-
A user called to inform you that the laptop she purchased yesterday is malfunctioning and will not connect to the wireless network. You personally checked to verify that the wireless worked properly before the user left your office. The user states she rebooted the computer several times but the problem still persists. Which of the following is the first step you should take to assist the user in resolving this issue?
Task
Ask for the total price of the bill, then ask how many diners there are. Divide the total bill by the number of diners and show how much each person must pay.
I need code for this on Repl.it python
Answers
Answer:
Please see the full code in explanation
Explanation:
#This is a console program
def bill_calculator():
print("Enter the Total value of the bill:\n")
bill_total = float(input())
print("Enter total number of dinners:\n")
total_dinner = int(input())
bill_per_person = bill_total / total_dinner
result = ("Bill total: {} \n"
"Total dinners: {} \n"
"Bill per person: {} ").format(bill_total,total_dinner, bill_per_person)
print(result)
if __name__ == '__main__':
bill_calculator()
Which descriptive research method aims to conduct data in a naturalistic setting without influencing or controlling the research participants?
Answers
A study technique called naturalistic observation involves observing participants in their natural settings. Many psychologists and other social scientists employ this strategy.
What kind of research technique uses a detailed examination of a single subject or circumstance in the pursuit of a general principle?A descriptive method in which a single person is carefully examined in the pursuit of elucidating general truths. Naturalistic, observing and documenting behaviour in settings that arise spontaneously, without interfering with or altering the circumstances.
What are the four different categories of descriptive study?Case reports, case series, cross-sectional studies, and ecological studies are a few examples of descriptive studies. Individual data are collected for the first three of these, whilst the final one makes use of aggregated.
To know more about data visit:-
https://brainly.com/question/13650923
#SPJ4
.Explain how encrypting data during transmission protects it from being read by an unauthorised person who intercepts the transmission.
Answers
Answer:
Encryption is an effective and efficient technique used to prevent unauthorized access to informations transmitted over the internet.
Explanation:
Encryption is a form of cryptography and typically involves the process of converting or encoding informations in plaintext into a code, known as a ciphertext. Once, an information or data has been encrypted it can only be accessed and deciphered by an authorized user.
Some examples of encryption algorithms are 3DES, AES, RC4, RC5, and RSA.
SSL/TLS are standard protocols that provides link encryption for the transmission of messages over the internet such as electronic mail (e-mail).
SSL is an acronym for Secured Socket Layer and it is one of the secured way of authenticating and encrypting data between a computer and the mail server.
In the case of TLS, it is an acronym for Transport Layer Security and it basically is used for providing authentication and encryption of data between two communicating systems on a network.
This ultimately implies that, SSL/TLS are standard network protocols that provides data integrity and privacy to users when communicating over the internet or networking devices as they're made to encrypt user credentials and data from unauthorized access. The SSL/TLS are an application layer protocol used for the encryption of mails sent over the internet, in order to protect user information such as username and password.
4.11 lesson practice edhesive questions 4 and 5

Answers
Answer:
It may just be me but I can't see the picture
Explanation:
Answer:
4. Monte carlo simulations
I need the answer for number 5 please.
Explanation:
Help me!!
Which Windows Server core technology can you use to install, configure, and remove server roles and features?
a. AD DS
b. NTFS
c. Microsoft Management Console
d. Server Manager
Answers
The correct answer is d. Server Manager. Server Manager is a Windows Server core technology that allows users to install, configure, and remove server roles and features. It provides a centralized management interface for managing server roles, features, and server groups.
Windows Server includes a variety of core technologies that facilitate different aspects of server management. In this case, the technology that allows the installation, configuration, and removal of server roles and features is Server Manager. Server Manager is a graphical management tool that provides a centralized interface for managing server roles and features in Windows Server.
Server Manager simplifies the process of managing server functionalities by allowing administrators to easily install or remove roles and features with just a few clicks. It provides a comprehensive view of the server's configuration, allowing administrators to monitor and manage various aspects, such as roles, services, and resources.
Server Manager is designed to streamline server management tasks, enabling administrators to efficiently configure and maintain server roles and features. It offers a user-friendly interface and powerful tools that help simplify the deployment and management of server functionalities in Windows Server environments.
know more about Server Manager :brainly.com/question/30608960
#SPJ11
people who use a/an ________________ design logic believe that the given context determines what type of communication is appropriate.
Answers
People who use a/an contextual design logic believe that the given context determines what type of communication is appropriate.
Contextual design logic emphasizes the importance of considering the specific situation, environment, and audience when determining the most effective and appropriate means of communication. It recognizes that different contexts require different communication strategies and channels to convey information effectively.
By adopting a contextual design logic, individuals or organizations take into account factors such as cultural norms, social dynamics, communication goals, and the characteristics of the intended recipients. This approach helps ensure that the communication is tailored to the specific context, taking into consideration factors such as language, tone, medium, and level of formality.
Contextual design logic encourages a more nuanced and adaptable approach to communication, recognizing that what may be suitable in one context may not be effective or appropriate in another. It promotes sensitivity and responsiveness to the context in order to achieve clear, meaningful, and impactful communication.
learn more about "communication ":- https://brainly.com/question/28153246
#SPJ11
Which HTML tag is formatted correctly?
NEED ANSWER ASAP PLZ HELP ME IDONT UNDERETAND IT
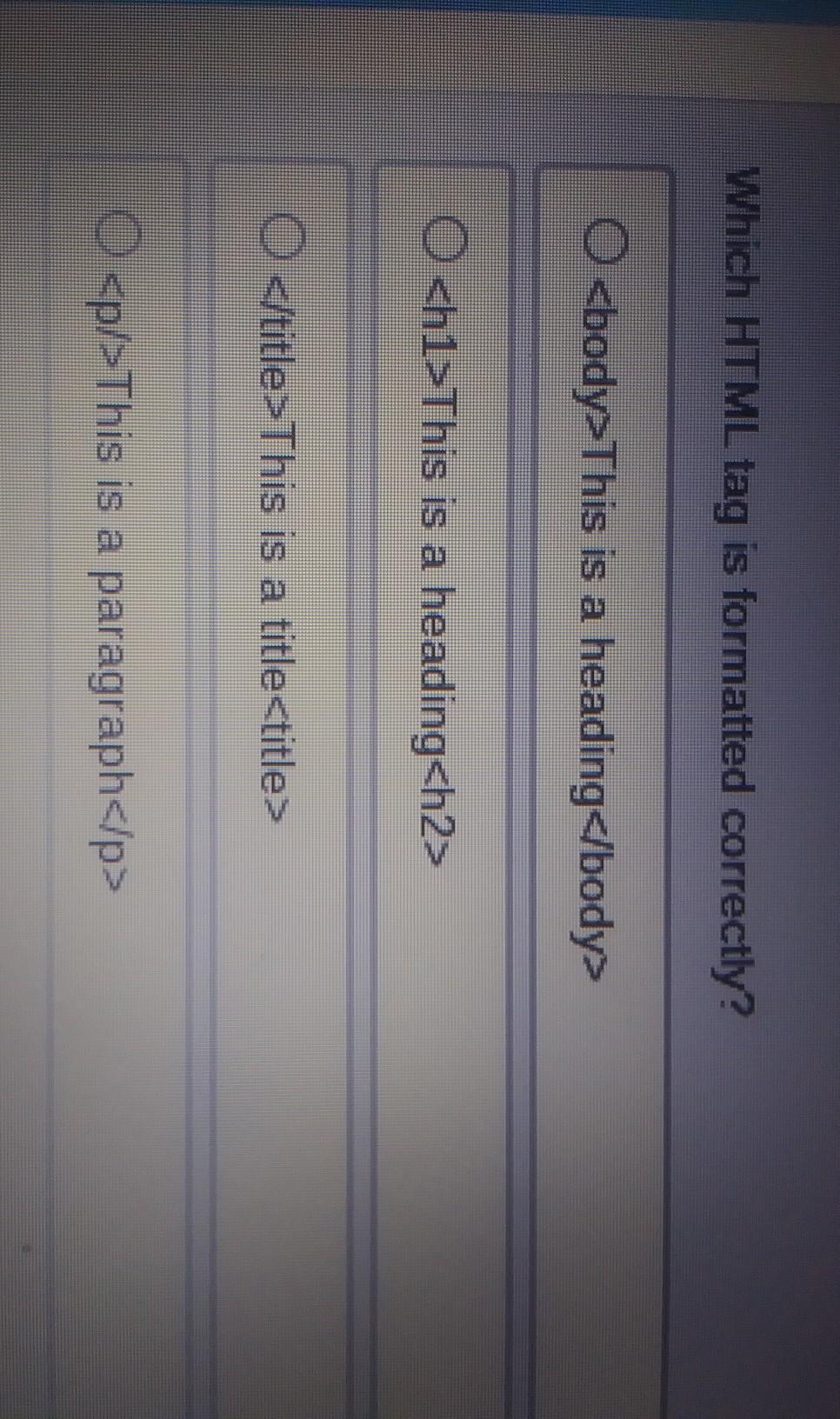
Answers
I think the last one is the correct one
Answer:
D
Explanation:
All others don't work
how to use function in python
Answers
Answer:
Use the keyword def to declare the function and follow this up with the function name.
Add parameters to the function: they should be within the parentheses of the function. ...
Add statements that the functions should execute.
How do I put this kind of question into an sqldeveloper (How many country names do not start with an 'A' or an 'E' letter?)
Answers
Answer:
In short names, there is Cyprus, Comoros, DRC, Morocco, Djibouti, Burundi, Togo, Congo, Fiji, and Kosovo. However if we use only official names, there is only one country on the whole planet that has no A's and E's, and that country is the Kingdom of Morocco.
Explanation:
hope it helps
Answer:
select * from country where name not like 'A%' and loginid not like 'E%'
Explanation:
The percent sign acts as a wildcard, but it only works in conjunction with the 'like' construct.
indexing of a string starts at 1 so the index of the first character is 1, the index of the second character is 2, and so forth.
Answers
In many programming languages, the indexing of a string starts at 1. This means that the index of the first character in the string is 1, the index of the second character is 2, and so on.
To find the index of a specific character in a string, you can use the indexing notation.
For example, if we have a string "Hello", the index of the letter 'H' is 1, the index of the letter 'e' is 2, and so on.
Here is a step-by-step explanation on how to find the index of a character in a string:
1. Start by identifying the string you want to find the index in. Let's use the string "Hello" as an example.
2. Count the characters in the string from left to right, starting with 1. In our example, the first character 'H' is at index 1, the second character 'e' is at index 2, and so on.
3. Continue counting until you reach the desired character that you want to find the index of.
Remember that not all programming languages follow the convention of starting indexing at 1.
Some programming languages, like Python, start indexing at 0.
It's important to consult the documentation or resources specific to the programming language you are using to determine the indexing convention.
To know more about Python visit;
https://brainly.com/question/30391554
#SPJ11
int a = 6; int b = 0; while (a < 20) { b = 10; while (b > a) { b−−; } a += b; } System.out.println(a);
Answers
The code you provided will print the value 22. The variable a starts at 6, and the variable b starts at 0. The while loop on line 3 will continue to run as long as a is less than 20.
Inside the while loop, the variable b is set to 10, and the while loop on line 5 will continue to run as long as b is greater than a. Inside the inner while loop, b is decremented by 1. After the inner while loop terminates, a is incremented by b.
This process repeats until a is equal to or greater than 20. When a is equal to 20, the outer while loop terminates, and the value of a is printed.
The code you provided uses a nested while loop to repeatedly add the value of b to a until a is equal to or greater than 20. The outer while loop ensures that the inner while loop runs at least once.
The inner while loop ensures that b is decremented by 1 before it is added to a. This ensures that the value of a increases by 1 each time the inner while loop terminates.
Learn more about nested loop here:
brainly.com/question/29532999
#SPJ11
one security component that doubles as a network component
Answers
Answer:
is the sentence above the question?
Answer:
It is to enter the site and then it will protect you in terms of form and appearance, and so on as required
Which one is the correct definition of MOSFET operation regions, and what is the value of IG (gate current) if VGS VGS-Vthreshold (V gs is the voltage between gate and source)
A. VDS > VGS Vthreshold for saturation, VDS ,VGSVthresold for triode, IG>0
B. VDS > VGS Vthreshold for triode VDS ,VGS=Vthresold for triode, IG>0
C. VDS > VGS Vthreshold for saturation, VDS ,VGS=Vthresold for triode, IG=0
D. VDS > VGS Vthreshold for triode, VDS ,VGS=Vthresold for triode, IG=0
Answers
The correct definition of MOSFET operation regions depends on the values of VDS (the voltage between drain and source) and VGS (the voltage between gate and source) compared to the threshold voltage (Vthreshold) of the MOSFET.
So, the correct answer is A.
Understanding MOSFET operation regionsIn saturation region, VDS is greater than VGS-Vthreshold, while in the triode region, VDS is less than VGS-Vthreshold. Therefore, option A is the correct definition for MOSFET operation regions.
The value of IG (gate current) will be greater than zero in the saturation region, as the MOSFET is conducting current and the gate is supplying a current to maintain that conduction.
However, in the triode region, IG will also be greater than zero as the gate is still controlling the current flow. Therefore, the value of IG is not zero in either operation region.
Learn more about MOSFET at
https://brainly.com/question/17417801
#SPJ11
how do I fix when it hits the second session it skips scanf.
#include <stdio.h>
#include <unistd.h>
#include <ctype.h>
main() {
double first, second;
while(1){
printf(" Calculator\n");
printf("\n 7 8 9 / \n 4 5 6 x \n 1 2 3 - \nEnter operator: ");
char op;
scanf("%c" ,&op); //entering operators such as + - \ *
printf("Enter two operands:");
scanf("%lf %lf", &first, &second); //entering operands such as 1 2 5 8 12 414
switch (op) { // printing the math
case '+'://if its +
printf("%.1lf + %.1lf = %lf\n\n", first, second, first + second);
break;
case '-'://if its -
printf("%.1lf - %.1lf = %lf\n\n", first, second, first - second);
break;
case '*'://if its *
printf("%.1lf * %.1lf = %lf\n\n", first, second, first * second);
break;
case '/'://if its :
printf("%.1lf / %.1lf = %lf\n\n", first, second, first / second);
break;
default://if its not + - / *
printf("error!");
}
}
}
Answers
Answer:
scanf(" %c" ,&op); //entering operators such as + - \ *
Explanation:
put space before %c