The landing page of a web site has just been edited. Some users are complaining they do not see the updated content being displayed. What could be the possible reason(s)? (Select TWO responses)
Answers
In Software Engineering, when dealing with UI, there are a lot of attribute particular to text view that if not properly formatted may affect the users experience.
Two possible things that comes to my mind as a software developer are
The text colour may have be altered such that it matches that of the background so that it cannot be seen anymoreThe text View visibility may have been set to "INVISIBLE " or "GONE"A little more checkup and tweaking or a search from online repository can go a long way to help the situation and the right user experience will be delivered.
Learn more about web design here:
https://brainly.com/question/25941596
Related Questions
which of the following data types can be used to create files and read information from them into memory?
Answers
The correct answer for the given question is: False.
What is data?
Data is raw, unprocessed information that has not been organized or analyzed. It is the building blocks of information and can be collected from many sources such as surveys, experiments, and observations.
Data can be qualitative or quantitative, structured or unstructured, and can be used to inform decisions, solve problems, and support research. Data can be stored in databases or spreadsheets, and can be manipulated and analyzed using various tools and algorithms.
Data can also be visualized to help people better understand and interact with it, which can lead to deeper insights and better decision making.
To learn more about data
https://brainly.com/question/27034337
#SPJ4
In this week's readings, you learned about the many features you have the ability to configure. Two examples are font size and a GUI login. What features do you think are important to ensure your users welcome Linux and to provide them with a great working environment?
Answers
It can be hard to get close enough to photograph animals in the wild true or false
Answers
Answer:
True
Explanation:
Answer:
true
Explanation:
Help please!, explain what is missing and what needs to be changed if anything.
Answers
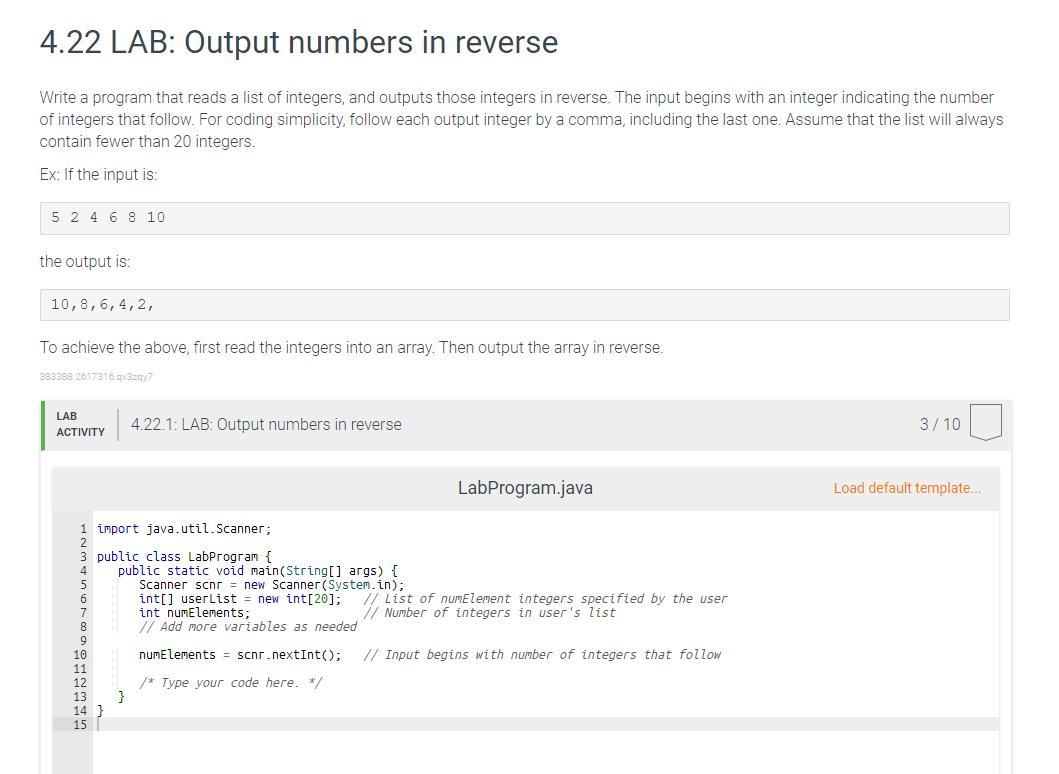
Using the computer language in JAVA to write a function code that output numbers in reverse
Writting the code in JAVA:import java.util.Scanner;
public class LabProgram {
public static void main(String[] args) {
Scanner scnr = new Scanner(System.in);
int[] userList = new int[20];
int numElements;
numElements = scnr.nextInt();
for (int i = 0; i < numElements; ++i) {
userList[i] = scnr.nextInt();
}
for (int i = numElements - 1; i >= 0; --i) {
System.out.print(userList[i] + " ");
}
System.out.println();
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1


What happens after the POST?
Answers
After the POST, the computer is ready for user interaction. Users can launch applications, access files, browse the internet, and perform various tasks depending on the capabilities of the operating system and the installed software.
After the POST (Power-On Self-Test) is completed during a computer's startup process, several important events take place to initialize the system and prepare it for operation. Here are some key steps that occur after the POST:
1. Bootloader Execution: The computer's BIOS (Basic Input/Output System) hands over control to the bootloader. The bootloader's primary task is to locate the operating system's kernel and initiate its loading.
2. Operating System Initialization: Once the bootloader locates the kernel, it loads it into memory. The kernel is the core component of the operating system and is responsible for managing hardware resources and providing essential services.
The kernel initializes drivers, sets up memory management, and starts essential system processes.
3. Device Detection and Configuration: The operating system identifies connected hardware devices, such as hard drives, graphics cards, and peripherals.
It loads the necessary device drivers to enable communication and proper functioning of these devices.
4. User Login: If the system is set up for user authentication, the operating system prompts the user to log in. This step ensures that only authorized individuals can access the system.
5. Graphical User Interface (GUI) Initialization: The operating system launches the GUI environment if one is available. This includes loading the necessary components for desktop icons, taskbars, and other graphical elements.
6. Background Processes and Services: The operating system starts various background processes and services that are essential for system stability and functionality.
These processes handle tasks such as network connectivity, system updates, and security.
For more such questions on POST,click on
https://brainly.com/question/30505572
#SPJ8
Why does sociologist work to create generalizations about social life, rather than hard-and-fast rules

Answers
The reason why sociologists work to create generalizations about social life rather than hard-and fast-rules is this: A. Making generalizations about social life allows sociologists to rely on common sense and their own personal experiences to understand the world.
Why is generalization important?Sociologists realize the fact that we all come from different walks of life. This is why we cannot all fit into rigid rules about life. So, generalizations that look at the sum total or generality of matters attempt to employ flexibility to enable us all to apply our common sense and personal experiences in life.
Option A is a valid reason for the use of generalizations by sociologists.
Learn more about generalizations here:
https://brainly.com/question/12157094
#SPJ1
Briefly explain the conceptual model effective computer based instruction for adults out lining the three units ( output, process and input)
Answers
Based on computer impacts analysis, the conceptual model effective computer-based instruction for adults is the process of uniting various vital parts of computer-based instruction to deliver a well-desired structure for researching CBI for adults.
The Three units of CBIOutputLearning OutcomeProcess External supportCBI DesignInstructional strategy designInputSelf-directednessComputer self-efficacyLearning goal levelHence, in this case, it is concluded that the conceptual model of CBI is a proper way to provide instruction for adults.
Learn more about the computer-based instruction here: https://brainly.com/question/15697793
Evaluate the following descriptions to determine which camera shot is being explained. The camera frames a part of the character or object so tightly that the outer portions of the subject are cut off by the frame. (1 point)
1 close up shot
2extreme close up shot
3 master shot
4point of view shot
Answers
The camera frames a part of the character or object so tightly that the outer portions of the subject are cut off by the frame is called option 2. extreme close up shot.
What is an extreme close-up shot in film?A close-up shot can occasionally just display the subject's eyes in an extreme close-up (ECU) shot.
The subject is tightly framed in close-up views, which fill the entire frame with a specific detail. Sometimes, as in a medium form of close-up shot, the close-up camera shot is known to be altered (MCU).
Therefore, one can say that when taking a picture of any person or an animal, a close up shot that is so extreme is one that tends to capture that special point that the photographer wants such as the face.
Learn more about close up shot from
https://brainly.com/question/28032196
#SPJ1
describe usage about hand geometry biometric?
Answers
Biometrics for hand geometry recognition are less obvious than those for fingerprint or face recognition. Despite this, it is nevertheless applicable in numerous time/attendance and physical access applications.
What is Hand geometry biometric?The concept that each person's hand geometry is distinct is the foundation of hand geometry recognition biometrics.
There is no documented proof that a person's hand geometry is unique, but given the likelihood of anatomical structure variance across a group of people, hand geometry can be regarded as a physiological trait of humans that can be used to distinguish one person from another.
David Sidlauskas first proposed the idea of hand geometry recognition in 1985, the year after the world's first hand geometry recognition device was commercially released.
Therefore, Biometrics for hand geometry recognition are less obvious than those for fingerprint or face recognition. Despite this, it is nevertheless applicable in numerous time/attendance and physical access applications.
To learn more about Hand geometry biometric, refer to the link:
https://brainly.com/question/12906978
#SPJ9
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
Answers
Answer: NAT
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP? One-to-many NAT allows multiple devices on a private network to share a single public IP address.
The following that allows for hundreds of computers all to have their outbound traffic translated to a single IP is the One-to-many NAT. Option C
How does One-to-many NAT works
One-to-many NAT allows hundreds of computers to have their outbound traffic translated to a single IP this is done by designating each computer to a unique port number, that is used to identify the specific device within the the network address transition NAT, where all private network gain access to public network .
The NAT device serves as translator, keeping track of the original source IP and port number in the translation table, translates the source IP address and port number of each outgoing packet to the single public IP address, This allows for a possible multiple devices to share a single IP address for outbound connections.
Learn more about One-to-many NAT on brainly.com/question/30001728
#SPJ2
The complete question with the options
Which of the following allows hundreds of computers all to have their outbound traffic translated to a single IP?
a. Rewriting
b. Port forwarding
c. One-to-many NAT
d. Preservation
Question #2 Dropdown What are the missing words in the program? divide(numA, numB): numA / numb
Answers
Answer:
def
return
Explanation:
I hope this helps!
Technician A says tires that are badly worn, mismatched in size or tread condition, or incorrectly inflated can cause brake problems. Technician B says simple inspection and checking with a pressure and a depth gauge can diagnose many tire problems. Who is correct?
Answers
The technicians are both accurate. Badly worn or underinflated tyres can lead to brake issues, and tyre issues are frequently detectable with a quick checkup and some pressure and depth gauge checks.
What's wrong with tyres that aren't the same size?If you keep using wheels and tyres that aren't compatible, they'll wear down unevenly and might cause issues in the future. The same problems may arise if you decide to drive your car with mismatched wheels. Uneven wear and tear will result from mismatched wheels and tyres.
What is the main reason why tyres wear unevenly?Uneven tyre wear is typically brought on by poor alignment, excessive or inadequate air pressure, or a worn-out suspension. Understanding the various irregular tyre wear patterns shown below can be useful.
To know more about technicians visit:-
https://brainly.com/question/29486799
#SPJ1
Consider this scenario: A major software company finds that code has been executed on an infected machine in its operating system. As a result, the company begins working to manage the risk and eliminates the vulnerability 12 days later. Which of the following statements best describes the company’s approach?
Answers
Answer:
The company effectively implemented patch management.
Explanation:
From the question we are informed about a scenario whereby A major software company finds that code has been executed on an infected machine in its operating system. As a result, the company begins working to manage the risk and eliminates the vulnerability 12 days later. In this case The company effectively implemented patch management. Patch management can be regarded as process involving distribution and application of updates to software. The patches helps in error correction i.e the vulnerabilities in the software. After the release of software, patch can be used to fix any vulnerability found. A patch can be regarded as code that are used in fixing vulnerabilities
the data management body of knowledge (dmbok) defines the planning, implementation, and control of activities that apply quality management techniques to data as
Answers
Data quality is the design, implementation, and control of actions that apply quality management approaches to data in order to ensure that it is fit for consumption and satisfies the needs of data consumers, according to the Data Management Body of Knowledge.
What is Data Management?
The organising carrying out, and supervising of data-related quality management operations. The planning and implementation are defined by the Data Management Body of Knowledge. The Data Management Book of Knowledge is a thorough reference for data management specialists regarding global data management standards and procedures. to share knowledge on maturity models for data management, deliverables and metrics, roles and responsibilities, and best practises to harmonise management techniques across the industry.
To act as a practical foundation for putting these approaches into effect in any kind of business.
To learn more about practises from given link
brainly.com/question/26035095
#SPJ4
What was the Internet originally created to do? (select all that apply)
Answers
The Internet was initially constituted for various purposes. it is was originally created to options a, c and d:
share researchcommunicateshare documentsWhat is InternetCommunication: The Internet was planned to aid ideas and data exchange 'tween analysts and chemists. It proposed to combine various calculating and networks to authorize logical ideas and cooperation.
Research and Development: The Internet's production was driven for one need to share research verdicts, experimental dossier, and possessions among academies, research organizations, and administration institutions.
Read more about Internet here:
https://brainly.com/question/21527655
#SPJ4
You have read about the beginnings of the Internet and how it was created. What was the Internet originally created to do? (select all that apply)
share research.
Play games.
Communicate.
Share documents.
Sell toys
i want code to put in code vision avr for conurrent controling LED lamp and cath-7 segment(without button)
the simulation in proteus should be like that we have one atmega and a led and 7 seg ground and res with one port of 7 seg in connected to micro and one port of led should be connect to micro.
Answers
-------------------------------------------------------------------------------------------------------------
To control a LED lamp and Cath-7 segment concurrently without using any button, we can use Code Vision AVR software. Here is the code for the same:
```
#include <mega16.h>
#include <delay.h>
void main()
{
DDRB = 0xFF; // Set all pins of PORTB as output
DDRC = 0xFF; // Set all pins of PORTC as output
while(1)
{
// Turn on LED lamp
PORTB.0 = 1;
delay_ms(500);
PORTB.0 = 0;
delay_ms(500);
// Display digits on Cath-7 segment
PORTC = 0x3F; // Display 0
delay_ms(1000);
PORTC = 0x06; // Display 1
delay_ms(1000);
PORTC = 0x5B; // Display 2
delay_ms(1000);
PORTC = 0x4F; // Display 3
delay_ms(1000);
PORTC = 0x66; // Display 4
delay_ms(1000);
PORTC = 0x6D; // Display 5
delay_ms(1000);
PORTC = 0x7D; // Display 6
delay_ms(1000);
PORTC = 0x07; // Display 7
delay_ms(1000);
PORTC = 0x7F; // Display 8
delay_ms(1000);
PORTC = 0x6F; // Display 9
delay_ms(1000);
}
}
```
Once you have written the code, you can simulate it in Proteus. Here are the steps to simulate the circuit:
1. Open Proteus and create a new project.
2. Search for "ATmega16" in the components library and add it to the project.
3. Add a LED and Cath-7 segment to the project by searching for them in the components library.
4. Connect the LED to any PIN of PORTB and Cath-7 segment to any PIN of PORTC.
5. Now, double-click on the ATmega16 chip and upload the code to it.
6. Finally, run the simulation and you should see the LED lamp and Cath-7 segment displaying digits concurrently.
Hope this helps!
Consider the following code:
start = int(input("Enter the starting number: "))
stop = int(input("Enter the ending number: "))
x = -10
sum = 0
for i in range (start, stop, x):
sum = sum + i
print(sum)
What is output if the user enters 78 then 45?
Please help me !
Answers
Answer:
The output is 252
Explanation:
To get the output, I'll analyze the lines of code one after the other.
Here, user enters 78. So, start = 78
start = int(input("Enter the starting number: "))
Here, user enters 45. So, stop = 45
stop = int(input("Enter the ending number: "))
This initializes x to -10
x = -10
This initializes sum to 0
sum = 0
This iterates from 78 to 46 (i.e. 45 + 1) with a decrement of -10 in each successive term
for i in range (start, stop, x):
This adds the terms of the range
sum = sum + i
This prints the calculated sum
print(sum)
The range starts from 78 and ends at 46 (i.e. 45 + 1) with a decrement of -10.
So, the terms are: 78, 68, 58 and 48
And Sum is calculated as:
\(Sum = 78 + 68 + 58 +48\)
\(Sum = 252\)
Hence, 252 will be printed
How is a cryptocurrency exchange different from a cryptocurrency
wallet?
A There is no difference since all wallets are hosted on exchanges.
B Exchanges are only used to make transactions, not to store cryptocurrency.
C Exchanges are offline whereas wallets are always connected to the internet.
D An exchange controls your keys but you control your cryptocurrency.
Answers
Exchanges are only used to make transactions, not to store cryptocurrency. Option B
What is Cryptocurrency exchanges versus cryptocurrency wallets?
Cryptocurrency exchanges are platforms that allow users to trade various cryptocurrencies for other digital assets or fiat currency. While some exchanges may offer temporary storage solutions, their primary function is to facilitate transactions between users.
On the other hand, cryptocurrency wallets are designed to store, send, and receive cryptocurrencies securely. Wallets can be hardware-based, software-based, or even paper-based, and they help users manage their private keys, which are essential for accessing and controlling their cryptocurrency holdings.
Find more exercises related to Cryptocurrency exchanges;
https://brainly.com/question/30071191
#SPJ1
Can someone help me? Also, please put it on a coding sheet so they will be no errors.


Answers
Answer:
try this
def sqrt(n):
approx = n / 2.0
better = (approx + n/approx)/2.0
while better != approx:
print (better)
approx = better
better = (approx + n/approx)/2.0
return approx
print (sqrt(25))
def checkout():
total = 0
count = 0
moreitems = True
while moreitems:
price = float(input('Enter price of item (0 when done): '))
if price != 0:
count = count + 1
total = total + price
print('Subtotal: ${:.2f}'.format(total))
else:
moreitems = False
average = total / count
print("Total items:", count)
print("Total price: ${:.2f}".format(total))
print("Average price: ${:.2f}".format(average))
Answer:
See below
Explanation:
For the sqrt(n) method your function call is incorrect. As candlejenner has correctly coded, the function call on line 14 should be
print (sqrt(25))
without quotes
That is my best guess.
For the checkout() method, I can't see the bottom of your code window so I do not know how you are calling this method. My code and run results are in the attached figure. This is from another course but is the exact same thing.
There is absolutely no difference between my code and yours except on line 19 I am calling the checkout() method
So see if that change works
Good Luck

What type of 3-phase connection requires only two transformers?
Answers
The use of two single-phase transformers to step down a high 3-phase voltage to a lower 3-phase voltage is possible using a rudimentary configuration dubbed an "open delta."
What is a single-phase transformer?For industrial applications, three phase transformers perform significantly better. Most heating, air conditioning, lighting, and house applications employ single phase systems in residential settings. When compared to low-power industrial systems and machines, they are less productive. A specific type of transformer called a single phase transformer functions using only one phase of power. This device carries electrical power from one circuit to another by the mechanism of electromagnetic induction. It is a passive electrical device. A transformer cannot change single-phase electricity into three-phase power, even if single-phase power can be produced from a three-phase power source. Phase converters or variable frequency drives are needed to convert single-phase electricity to three-phase power.To learn more about single phase transformers, refer to:
https://brainly.com/question/29665451
when jesus said it is written what was he making refference to
Answers
Answer:
He was referring to the Bible being finished.
Explanation:
Write a C++ program that displays the total running time of a given algorithm based on
different situations such as processor speed, input size, processor load, and software
environment (DOS and Windows).
Answers
Answer: Your welcome!
Explanation:
#include <iostream>
#include <cmath>
using namespace std;
int main()
{
int processorSpeed; //in MHz
int inputSize; //in Kb
int processorLoad; //in %
int softwareEnvironment; //1: DOS, 2: Windows
int runningTime; //in ms
cout << "Enter processor speed (MHz): ";
cin >> processorSpeed;
cout << "Enter input size (Kb): ";
cin >> inputSize;
cout << "Enter processor load (%): ";
cin >> processorLoad;
cout << "Enter software environment (1-DOS, 2-Windows): ";
cin >> softwareEnvironment;
if(softwareEnvironment == 1)
{
//DOS running time calculation
runningTime = (inputSize / processorSpeed) + (processorLoad / 10);
}
else
{
//Windows running time calculation
runningTime = (inputSize / (processorSpeed/2)) + (processorLoad / 10);
}
cout << "Total running time: " << runningTime << "ms" << endl;
return 0;
}
If you have a line that is 2.5 inches in decimal, what is that in fraction form?
2 5/16 inches
2 1/4 inches
2 3/4 inches
2 1/2 inches
If you are asked to measure 9/16th on a ruler how many lines would you have to count?
Answers
Answer: 2 1/2 inches; 9 lines
Explanation:
If one has a line that is 2.5 inches in decimal, this in fraction form will be written as:
= 2.5 inches = 2 5/10 inches.
When we reduce 5/10 to its lowest term, this will be 1/2. Therefore 2.5 inches = 2 1/2 inches.
Since each mark on a ruler is 1/16, therefore 9/16 will be (9/16 ÷ 1/16) = (9/16 × 16/1) = 9 lines
What are the core steps to add revisions or features to a project?(1 point)
Responses
Evaluate feasibility of the goals, create a list of functionality requirements, and develop the requirements of the feature.
Evaluate feasibility of the goals, develop programming solutions, and evaluate how well the solutions address the goals.
understand the goals, evaluate the impact on the project, create a list of functionality requirements, and develop the requirements of the feature.
Communicate with the client, create a sprint backlog, develop the project, and evaluate how well the solution fits the requirements.
Answers
The core steps to add revisions or features to a project are ""Understand the goals, evaluate the impact on the project, create a list of functionality requirements, and develop the requirements of the feature." (Option C)
How is this so?
The core steps to add revisions or features to a project include understanding the goals,evaluating the impact on the project, creating a list of functionality requirements,and developing the requirements of the feature.
These steps ensure that the goals are clear, the impact is assessed, and the necessary functionality is identified and implemented effectively.
Learn more about project management at:
https://brainly.com/question/16927451
#SPJ1
What is the purpose of the property, transition-timing-function?
It sets how many times a transition will play.
It delays the start of a transition by a set number of seconds.
It changes the speed at different stages of the transition.
It adds a pause between steps in an animation.
Answers
Answer:
It changes the speed at different stages of the transition.
Explanation:
HTML is an acronym for hypertext markup language and it is a standard programming language which is used for designing, developing and creating web pages.
Generally, all HTML documents are divided into two (2) main parts; body and head. The head contains information such as version of HTML, title of a page, metadata, link to custom favicons and CSS etc. The body of the HTML document contains the contents or informations that a web page displays.
Basically, the purpose of the property, transition-timing-function is that It changes the speed at different stages of the transition. Thus, it states the values between the beginning and ending of a transition are calculated over its duration.
the differencebetween browser and search engine
please my assignment have50 mark
Answers
Answer:
A browser is a piece of software that retrieves and displays web pages; a search engine is a website that helps people find web pages from other websites.
Which algorithm steps correctly solve the problem: How many occurrences of 2 exist in the array?
(1) increment counter if 2 is found (2) loop through array (3) inspect each array element
(1) inspect each array element (2) loop through array (3) increment counter if 2 is found
(1) loop through array (2) increment counter if 2 is found (3) inspect each array element
(1) loop through array (2) inspect each array element (3) increment counter if 2 is found
Answers
The correct algorithm steps to solve the problem "How many occurrences of 2 exist in the array?" is:
(1) loop through array(2) inspect each array element(3) increment counter if 2 is foundTherefore, option (4) is the correct sequence of steps:
Why is this correct?This is because you need to traverse the entire array and inspect each element to check if it is equal to 2. If an element is equal to 2, then you increment the counter.
1) loop through array
(2) inspect each array element
(3) increment counter if 2 is found
Read more about algorithm here:
https://brainly.com/question/24953880
#SPJ1
Compare and contrast the code of ethics of two professional organizations or regulatory bodies in computer science field. Analyze the similarities and differences between the codes, and discuss their implications for professional practice. Critically evaluate the strengths and weaknesses of each code and propose recommendations for improving ethical standards in the profession.
Answers
Ethical standards upheld in the computer science field are set forth by reputable professional organizations like ACM and AAAI.
How is this so?Both these organizations advocate for values promoting honesty, integrity, privacy protection and respect towards every individual's dignity.
While focus on educational growth is central to the ACM code of ethics, more significant emphasis seems laid down by AAAI for researchers in artificial intelligence fields to consider broader society concerns related to potential impact with AI research practices.
The codes derive their strength from placing significant stress on ethical behavior and acknowledging the influence of technology on society.
Learn more about Ethical Standards;
https://brainly.com/question/28295890
#SPJ1
what is star topology
Answers
How to use this program
Answers
Answer:
there is no problem
Explanation:
but i hope i can help one day