this allows you to draw on your slide for emphasis when making a presentation. spell check smartart drawing tool annotate
Answers
When making a presentation, a "drawing tool" such a pen, highlighter, or laser pointer is used to annotate on a presentation slide to highlight topics.
How to annotate on slides during a presentation?
To accentuate a point or demonstrate connections when presenting, you can sketch digitally on the screen.
Activate the pen and scribble in the slide show:
Make sure Use Presenter View is selected on the Slide Show tab.To begin your slide show, select From Beginning or From Current Slide on the Slide Show page.Some helpful buttons are visible in Presenter view in the lower left corner of your presentation. The one that resembles a pen To customize the appearance of the mouse pointer on-screen, use the Pen assistance button.It is possible to construct presentations of ideas by combining text, graphics, and audio or video using presentation software, a subcategory of application software.
The two types of presentation software—business presentation software and general multimedia authoring software—can be distinguished, although the majority of these programs already come with capabilities that let users make both polished business presentations and broad multimedia presentations.
To know more about presentation software, visit: https://brainly.com/question/2289636
#SPJ4
Related Questions
Define a function calc_pyramid_volume with parameters base_length, base_width, and pyramid_height, that returns the volume of a pyramid with a rectangular base.
Sample output with inputs: 4.5 2.1 3.0
Volume for 4.5, 2.1, 3.0 is: 9.45
Relevant geometry equations:
Volume = base area x height x 1/3
Base area = base length x base width.
given to me
''' Your solution goes here '''
length = float(input())
width = float(input())
height = float(input())
print('Volume for', length, width, height, "is:", calc_pyramid_volume(length, width, height))
Answers
The missing segment of the code illustrates the use of functions.
Functions are also referred to as procedures or methods; they are set of instructions that act as one.
The code segment that complete the code in the question is as follows:
def calc_pyramid_volume(length, width, height):
baseArea = length * width
Volume = baseArea * height * 1/3
return Volume
The first line of the code segment declares the function itself
def calc_pyramid_volume(length, width, height):
Then, the base area of the pyramid is calculated
baseArea = length * width
Then, the volume of the pyramid is calculated
Volume = baseArea * height * 1/3
Lastly, the volume is returned to the main method
return Volume
So, the complete code (without comments) is:
def calc_pyramid_volume(length, width, height):
baseArea = length * width
Volume = baseArea * height * 1/3
return Volume
length = float(input())
width = float(input())
height = float(input())
print('Volume for', length, width, height, "is:", calc_pyramid_volume(length, width, height))
See attachment for the sample run
Read more about functions at:
https://brainly.com/question/17225124

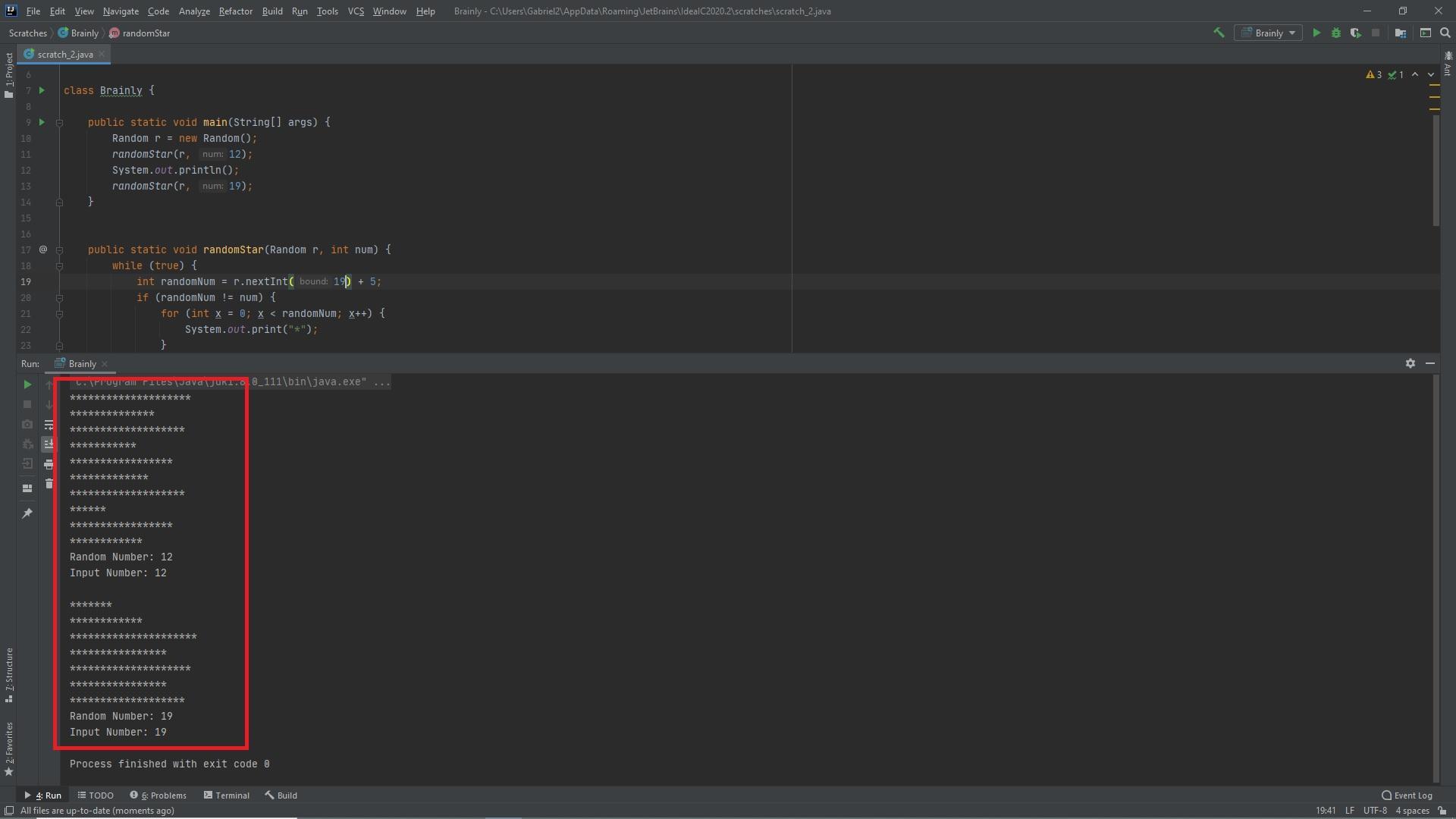
Random Star
Write a method named randomStar that takes two parameters, a Random object r and an integer num. The method should keep printing lines of * characters, where each line has between 5 and 19 * characters inclusive, until it prints a line with greater than or equal to num characters. num is guaranteed to be between 5 and 19. For example, the method call randomStar(14) will print:
import java.util.*;
public class RandomStar {
public static void main(String[] args) {
Random r = new Random(2063064142); // ignore the 2063064142
randomStar(r, 12);
System.out.println();
randomStar(r, 19);
}
public static void randomStar(Random r, int num) {
}
}
Answers
Answer:
Explanation:
The following code is written in Java. The function takes in the random object and creates a random number where it generates a random number and prints out the * characters, if the random number and the input num are the same it prints out both values and ends the function.
import java.util.Random;
class Brainly {
public static void main(String[] args) {
Random r = new Random();
randomStar(r, 12);
System.out.println();
randomStar(r, 19);
}
public static void randomStar(Random r, int num) {
while (true) {
int randomNum = r.nextInt(19) + 5;
if (randomNum != num) {
for (int x = 0; x < randomNum; x++) {
System.out.print("*");
}
System.out.print("\n");
} else {
for (int x = 0; x < randomNum; x++) {
System.out.print("*");
}
System.out.print("\n");
System.out.println("Random Number: " + randomNum);
System.out.println("Input Number: " + num);
break;
}
}
}
}
Elaborate me rale OF ICT in Education.
Answers
Information and Communication Technology (ICT) plays a crucial role in transforming education by enhancing teaching and learning processes,
Elaborations on the role of ICT in education:Access to Information and Resources: ICT provides students and educators with access to a vast amount of information and educational resources. Through the internet, digital libraries, and online databases, learners can access a wide range of educational materials, research articles, e-books, videos, and interactive content. This enables them to explore diverse topics, conduct research, and stay updated with the latest information in their respective fields.
Enhancing Teaching and Learning: ICT tools and technologies enhance teaching and learning experiences. Multimedia presentations, educational software, simulations, and virtual reality applications engage students and make learning interactive and dynamic. Online platforms and learning management systems provide educators with the ability to deliver course materials, assignments, and assessments in a structured and organized manner. This fosters active learning, critical thinking, and problem-solving skills among students.
Learn more about ICT at
https://brainly.com/question/13724249
#SPJ1
complete question
Elaborate on the role OF ICT in Education
give 2 reasons why 3D printers are not commonly used in a home office other than the cost
Answers
Answer:
Skill/ Material
Explanation:
The skills needed to design a model for a 3D printer to print is rare, and takes alot of practice.
Filling is also needed for the printer, which is an additonal cost besides mantience, and the original fee.
Answer:
The use of 3D printers can be complex, with much prerequisite knowledge being required. They are time-consuming to maintain.Explanation:
3D printers are a versatile technology with a multitude of use cases, from designing models and prototypes to creating components used in vehicles. This begs the question, why are they not common in home offices everywhere?
Firstly, while they are incredibly useful, they are pretty complex, with prior knowledge of CAD (computer-aided design) software often required. This complexity can make its use challenging for the average person.
Another reason they are uncommon in home offices is their need for maintenance. 3D printers, like all machinery, require regular maintenance to ensure smooth operation. However, maintenance of 3D printers can be time-consuming, coupled with an overall lack of need within a home office, making them off-putting to buyers.
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
Comprehension s best described as the ability to
Answers
Answer:
The ability to understand
Explanation:
Answer:
recognize reading strategies.
Explanation:
consider this list of numbers: 9 3 6 8 4 7. after three comparisons have been made the list is 3 6 9 8 4 7 . which algorithm is being applied
Answers
Answer: The algorithm being applied is "Insertion Sort".
Explanation:
Insertion sort works by iteratively inserting each element of the input list into its proper place in a growing sorted list. In each iteration, the algorithm selects the first unsorted element and compares it with each element in the sorted portion of the list until it finds its correct position. It then inserts the element into the sorted portion of the list and moves on to the next unsorted element.
In the given example, the first three elements of the list (9, 3, and 6) are compared and swapped to produce the partially sorted list 3 9 6 8 4 7. Then, the next unsorted element (6) is compared with the sorted elements (3 and 9) and inserted in its correct position between 3 and 9, resulting in the list 3 6 9 8 4 7.
Use cin to read integers from input until 999 is read. For each remaining integer read before 999, if the integer is equal to 25, output "25 occurs" followed by a newline and increment numDetections.
Ex: If the input is 25 25 -6 25 25 999, then the output is:
25 occurs
25 occurs
25 occurs
25 occurs
4 time(s)
Answers
Ex: If the input is 25 25 -6 25 25 999, then the output is:4 time(s)
What is the code about?By using a while loop in this code, we can utilize the cin function to retrieve integers from input until the sentinel value 999 is reached. We verify the equality of every integer read with the value of 25.
Therefore, We issue the statement "25 is present" and increase the numDetections count if applicable. After completion of integer reading, we display the overall count of occurrences of the value 25. It should be noted that we utilize "endl" to add a line break character at the end of every line of output.
Learn more about code from
https://brainly.com/question/26134656
#SPJ1

Using the in databases at the , perform the queries show belowFor each querytype the answer on the first line and the command used on the second line. Use the items ordered database on the siteYou will type your SQL command in the box at the bottom of the SQLCourse2 page you have completed your query correctly, you will receive the answer your query is incorrect , you will get an error message or only see a dot ) the page. One point will be given for answer and one point for correct query command

Answers
Using the knowledge in computational language in SQL it is possible to write a code that using the in databases at the , perform the queries show belowFor each querytype.
Writting the code:Database: employee
Owner: SYSDBA
PAGE_SIZE 4096
Number of DB pages allocated = 270
Sweep interval = 20000
Forced Writes are ON
Transaction - oldest = 190
Transaction - oldest active = 191
Transaction - oldest snapshot = 191
Transaction - Next = 211
ODS = 11.2
Default Character set: NONE
Database: employee
Owner: SYSDBA
PAGE_SIZE 4096
...
Default Character set: NONE
See more about SQL at brainly.com/question/19705654
#SPJ1

how can you say that a painting is real?

Answers
Answer:Know the Artist. Prior to buying an artist's work, become familiar with their oeuvre. ...
Use a Magnifying Glass. Looking at the surface of a painting with a magnifying glass is one of the best ways to spot a print. ...
Turn the Painting Over.
Explanation:brainliest
See from the way they paint. You can see from the picture that its way different. Each artist has different way to paint. see the colour also
Identify the following verb by number and person by checking on the appropriate boxes.
SHE WANTS!!
second person
singular
plural
same form for both singular and plural
third person
first person PLEASE HELP!!!!!! LAUNGUAGE ARTS
Answers
Answer:
Singular and third person
Explanation:
Second person: this answer is not correct as second person refers to pronouns such as “you, yourself” like in a recipe.
Singular: this is correct as a singular verb is when there is only one subject. You can also tell it’s a singular verb as the present tense ends with a “s”.
Plural: this is not plural because there is only one subject. Plus the present tense of the verb ends with an s so it’s not a plural verb. Plural verb’s present tense never ends with an s.
Third person: this is correct because the subject of the sentence is someone else. Third person pronouns include: “her, she, he, him, they, then” basically, third person is when you talk about someone else.
First person: this answer is not correct because first person refers to one’s self. So first person pronouns are: “I, me, myself”
for the pasted by value parameter passing method, what are all of the values of the variables value and list after the call to swap
Answers
The properties of the values value and record after the call swap, according to the question, are Call 1: value = 2, List = 1,3,5,7,9, Call 2: value = 2, List = 1,3,5,7,9, and Call 3: value = 2.
Why do people utilize parameter passing?Without having to establish or use global variables, parameter passing enables the values on local variables inside an actual program to still be accessed, modified, and used throughout several sub-programs.
Briefing :Call 1: value = 2, List = 1,3,5,7,9,
Call 2: value = 2, List = 1,3,5,7,9, and
Call 3: value = 2.
To know more about Parameter visit :
https://brainly.com/question/29034395
#SPJ4
The complete Question :
Consider the following program written in C syntax:
void main () {
int value = 2, list[5] = {1, 3, 5, 7, 9};
swap (value, list[0]);
swap (list[0], list[1]);
swap (value, list[value]);
}
void swap (int a, int b) {
int temp;
temp = a;
a = b;
b = temp;
}
For each of the following parameter-passing methods, what are all of the values of the variables value and list after each of the three calls to swap?
a. Passed by value
With pass by value, none of the actual arguments are changed, so the variables retain the values they were initialized with.
b. Passed by reference
With pass by reference, the arguments are changed. After the first call to swap, value == 1 and list[0] == 2. After the second call to swap, list[0] == 3 and list[1] == 2. After the third call, value == 2 and list[1] == 1.
c. Passed by name
With pass by name, it%u2019s as if the text of the arguments is inserted in the text of the subprogram. For the first two calls to swap, behavior is just like pass by reference. For the third call, swap acts as if it has the body
temp = value; value = list[value]; list[value] = temp; and as a result, value == 2 (what was stored in list[1]) and list[2] == 1. List[1] remains 2.
d. Passed by value-result
In this case, value-result has the same effect as reference.
write a code palindrome in python
Answers
Answer:
def is_palindrome(string):
reversed_string = string[::-1]
return string == reversed_string
Answer:
Explanation:
Palindrome Program A string is called a palindrome string if the reverse of that string is the same as the original string. For example, radar , level , etc. Similarly, a number that is equal to the reverse of that same number is called a palindrome number. For example, 3553, 12321, etc.
How will bits and bytes of computer networking help in my career goal?
Answers
Answer:
By helping you learn and understand the very basics of computer networking therefor giving you a building block to use
Explanation:
ive been asked this before
Complete the statement below with the correct term.
The primary disk drive that boots the system is known as the
.
Answers
Answer:
boot disk
Explanation:
This disk contains files required by the boot sequence as well as the operating system, which is loaded at the end of the startup process.
Master
Explanation:
Master is the term used for to describe the primary disk, one that boots, or start up, the system
Excel eSkills Assessment
Answers
Excel, a powerful spreadsheet application widely utilized by many businesses, demands proficient Excel competency for anyone wishing to administer, study, or demonstrate data.
What are the fundamental skills?Here are some fundamental eSkills that should be carefully considered:
Fundamental Functions: Knowledge in basic functions, such as SUM, AVERAGE, COUNT, MIN and MAX, is essential for rapidly analyzing information.
Formulas and Calculations: Grasping formulas and calculations will provide the capacity to form intricate spreadsheets that can instantly assess details and generate computations.
Formatting: Becoming well-versed in formatting cells, rows and columns makes data easy to observe and visually attractive. This incorporates utilizing boldface, italics, underlining, coloration, and outlines.
Charts and Graphs: Understanding how to create charts and graphs displays info graphically. This comprehends exact choice of the pertinent chart style and its formatting.
Learn more about Excel on
https://brainly.com/question/24749457
#SPJ1
How do you open a program such as a Microsoft Word when there are no icons on the
desktop?
Select one:
a. Click the start button and select program from the menu
b. Right click to reveal all icons
c. It is not possible to open program if no icons are on the desktop
d. Restart the computer
How do you turn off the computer?
Answers
PLEASE HELP
Find five secure websites. For each site, include the following:
the name of the site
a link to the site
a screenshot of the security icon for each specific site
a description of how you knew the site was secure
Use your own words and complete sentences when explaining how you knew the site was secure.
Answers
The name of the secure websites are given as follows:
Each of the above websites had the security icon on the top left corner of the address bar just before the above domain names.
What is Website Security?The protection of personal and corporate public-facing websites from cyberattacks is referred to as website security.
It also refers to any program or activity done to avoid website exploitation in any way or to ensure that website data is not accessible to cybercriminals.
Businesses that do not have a proactive security policy risk virus spread, as well as attacks on other websites, networks, and IT infrastructures.
Web-based threats, also known as online threats, are a type of cybersecurity risk that can create an unwanted occurrence or action over the internet. End-user weaknesses, web service programmers, or web services themselves enable online threats.
Learn more about website security:
https://brainly.com/question/28269688
#SPJ1

NG STOCK MARKET FRAUD
Assignment Directions
1. For this assignment, you will explore securities or stock market fraud. Title your assignment "Stock Fraud" and ther
list the case you analyzed.
2. Visit the SEC Web site. Select and read through one of the actions against Enron.
Submission Requirements
1. Write a summary of the facts of the case, your understanding of all security law violations, and any settlement or
payment made to the stock-holders or others. Explore her online sources to get additional information.
2. The paper must be between one and two pages in length, double spaced, and with one-inch margins. Be sure to
include a reference page.
e.owschools.com/owsoo/studentAssignment/index?eh-390541091 #section Tab you like to do next?
Answers
Stock market fraud refers to the fraudulent practice of manipulating stock prices and the market. The Nigerian Stock Market Fraud, also known as the N14 billion stock fraud, is one of the most notorious cases of stock market fraud that happened in Nigeria.
It occurred between 2001 and 2002 and involved some of Nigeria’s most influential figures, including stockbrokers, top executives of blue-chip companies, and bankers.The Nigerian Stock Market Fraud is one of the largest stock market scandals in the world. It was the result of a lack of regulation and oversight in the Nigerian stock market, which allowed fraudulent practices to thrive.
The Securities and Exchange Commission (SEC) is the regulatory body responsible for regulating the Nigerian Stock Exchange. However, the SEC was ineffective in preventing the fraud from occurring, and many of its officials were implicated in the scandal.The N14 billion stock fraud involved the manipulation of stock prices, insider trading, and market rigging.
The fraudsters would inflate the price of stocks artificially, then sell the stocks to unsuspecting investors at inflated prices. They would then use the proceeds from the sale of the stocks to buy more stocks, further inflating the prices.
The fraudsters also engaged in insider trading, where they would use insider information to make trades in the stock market. This gave them an unfair advantage over other investors and allowed them to make huge profits from their trades.
In conclusion, the Nigerian Stock Market Fraud was a result of a lack of regulation and oversight in the Nigerian stock market. The SEC was ineffective in preventing the fraud from occurring, and many of its officials were implicated in the scandal. The fraudsters engaged in the manipulation of stock prices, insider trading, and market rigging.
For more such questions on Stock market, click on:
https://brainly.com/question/690070
#SPJ8
What’s the output of this code?

Answers
Answer:
1
Explanation:
console.log: mystery isn't anything necessary because it doesn't have anything to do with the code. The only option for this is 1 because the mystery says a, b and c. As this c < a & c > b gives the number 1.
Have a wonderful day! :-)
When it comes to memory, why is it important to have enough storage space on a hard drive when using many RAM intensive programs?
Answers
Answer:
Memory and storage are important concepts to master in Information Technology. ... This type of memory is volatile which means that the actual data disappears when the computer loses power. Because memory needs to be much faster than storage, it is rather more expensive than storage per GB.
Explanation:
User Interface Design ensures that the interface has elements that are easy to ________________. (Choose all that apply)
Question 1 options:
a) use to facilitate actions
b) change location
c) understand
d) remove
e) access
Answers
Answer:
A, C, D
Explanation:
User Interface (UI) Design focuses on anticipating what users might need to do and ensuring that the interface has elements that are easy to access, understand, and use to facilitate those actions.
And office now has a total of 35 employees 11 were added last year the year prior there was a 500% increase in staff how many staff members were in the office before the increase
Answers
There were 5 staff members in the office before the increase.
To find the number of staff members in the office before the increase, we can work backward from the given information.
Let's start with the current total of 35 employees. It is stated that 11 employees were added last year.
Therefore, if we subtract 11 from the current total, we can determine the number of employees before the addition: 35 - 11 = 24.
Moving on to the information about the year prior, it states that there was a 500% increase in staff.
To calculate this, we need to find the original number of employees and then determine what 500% of that number is.
Let's assume the original number of employees before the increase was x.
If we had a 500% increase, it means the number of employees multiplied by 5. So, we can write the equation:
5 * x = 24
Dividing both sides of the equation by 5, we find:
x = 24 / 5 = 4.8
However, the number of employees cannot be a fraction or a decimal, so we round it to the nearest whole number.
Thus, before the increase, there were 5 employees in the office.
For more questions on staff members
https://brainly.com/question/30298095
#SPJ8
ans as fast as u can important
Answers
1) User-generated content :
User-generated content, also referred to as UGC or consumer-generated content, is unique content created by customers specifically for a brand and shared on social media or through other channels. UGC can take many different forms, such as pictures, movies, reviews, a recommendation, or even a podcast.
2)Open Chrome on your Android device.
Reopen the tab.
Tap Settings next to "Discover." Switch on or off.
3)The speed at which the content on your page loads is referred to as page speed.
Site speed, which is the page speed for a representative sample of page views on a site, is frequently mistaken for page speed. Page speed can be measured in terms of "time to first byte" or "page load time," which measures how long it takes for a page to fully display its content.
Hence I believe i have answered all questions
To know more on page speed follow this link
https://brainly.com/question/26339742
#SPJ9
which technology concept uses computer resources from multiple locations to solve a problem
Answers
Grid computing is a system connecting many computer nodes into a distributed architecture that delivers the computing resources necessary to solve complex problems.
Saved
Excessive typing on a computer and texting on a cell phone can cause _________.
Question 9 options:
a)
mental health problems because a normal social life is deprived
b)
Carpal Tunnel Syndrome
c)
headaches and muscle aches
d)
all of the above
Answers
Answer:
here answer
Explanation:
all of the above
Need help with this python question I’m stuck



Answers
It should be noted that the program based on the information is given below
How to depict the programdef classify_interstate_highway(highway_number):
"""Classifies an interstate highway as primary or auxiliary, and if auxiliary, indicates what primary highway it serves. Also indicates if the (primary) highway runs north/south or east/west.
Args:
highway_number: The number of the interstate highway.
Returns:
A tuple of three elements:
* The type of the highway ('primary' or 'auxiliary').
* If the highway is auxiliary, the number of the primary highway it serves.
* The direction of travel of the primary highway ('north/south' or 'east/west').
Raises:
ValueError: If the highway number is not a valid interstate highway number.
"""
if not isinstance(highway_number, int):
raise ValueError('highway_number must be an integer')
if highway_number < 1 or highway_number > 999:
raise ValueError('highway_number must be between 1 and 999')
if highway_number < 100:
type_ = 'primary'
direction = 'north/south' if highway_number % 2 == 1 else 'east/west'
else:
type_ = 'auxiliary'
primary_number = highway_number % 100
direction = 'north/south' if primary_number % 2 == 1 else 'east/west'
return type_, primary_number, direction
def main():
highway_number = input('Enter an interstate highway number: ')
type_, primary_number, direction = classify_interstate_highway(highway_number)
print('I-{} is {}'.format(highway_number, type_))
if type_ == 'auxiliary':
print('It serves I-{}'.format(primary_number))
print('It runs {}'.format(direction))
if __name__ == '__main__':
main()
Learn more about program on
https://brainly.com/question/26642771
#SPJ1
With which feature or menu option of a word processing program can you make an image like this?
Answers
Answer:
The physical benefits include the following except
You tell Kim about a cloud based Intranet service. This service will allow all the stores to share data, resources, and software.
Answers
Based on the given scenario, a cloud-based intranet service can be a great way for stores to share data, resources, and software
What is a Cloud-Based Intranet Service?This refers to the type of service is typically hosted on a remote server and accessed through the internet, which means that all the stores can access the same information and resources from any location
Some benefits of using a cloud-based intranet service include:
Accessibility: With a cloud-based intranet, all the stores can access the same information and resources from any location, as long as they have an internet connection.
Collaboration: A cloud-based intranet service can make it easier for stores to collaborate and share ideas with each other.
Read more about intranet services here:
https://brainly.com/question/14994759
#SPJ1
1. Which of the following is a general-purpose computing device?
O A. Calculator
O B. Wi-Fi picture frame
OC. Smartphone
O D. Point-of-sale (POS) system
Answers
D. A general-purpose computer is a point-of-sale (POS) system. A wide range of administrative, management, and marketing abilities are required to run a retail store.
What is a POS?A device known as a POS (point of sale) is used to process retail customers' transactions. A type of POS is a cash register. Electronic POS terminals that can process cash as well as credit and debit cards have mostly taken the place of the cash register.
A POS can be a physical device in a physical store or a web-based checkout point.
The features of the software for POS devices are getting more and more complex, making it possible for retailers to track pricing accuracy, collect marketing data, and monitor trends in purchasing and inventory.
A point of sale (POS) is the location where a customer pays for goods or services and may be subject to sales taxes.
To learn more about software visit :
https://brainly.com/question/985406
#SPJ1