to create a new column that stores the combination of the pick-up and drop-off location names, which function do you use?
Answers
Without a WHERE clause, a UPDATE statement will update every row in the table.
Update statement: what is it?
To change or update already-existing records in a table with SQL, use the UPDATE statement. Using the WHERE clause, you can either define a specific subset of entries to edit or use it to update everything at once. A SQL data manipulation command is the UPDATE statement.
Do update statements count as queries?
To modify a current entry or rows in the database, perform a UPDATE query. The rows in all tables can be changed by UPDATE queries, or we can use the WHERE clause to restrict the rows that an update statement affects. To update the data, we typically employ constant values, such as the following structures.
To know more about UPDATE statement visit;
https://brainly.com/question/14271783
#SPJ4
Related Questions
Identify the following as being an advantage or not being an advantage of rfid systems used by zara.
a. Can reduce the time needed to take store inventory b. Can help find a product a customer wants that isn't available in store
c. Can eliminate the need for PoS systems
d. Can lower advertising co
Answers
The advantages of RFID system used by Zara are that it can reduce the time needed to take store inventory, and can help find a product a customer wants that isn't available in store.
It can eliminate the need for POS systems, can lower advertising costs are NOT an advantage of RFID systems used by Zara
Radio Frequency Identification System is referred to as an RFID system. It is an "Identification system employing wireless communication" that enables data to be transferred between "Antenna (or Reader/Writers)" and "RF Tags (or Data Carriers)," which are held by people or affixed to things. A radio communication system, in a sense.
There are several uses for RFID systems including consolidated administration of things and information is possible with an RFID system.
The following applications make up the majority of the uses for RFID in a production plant.
Workplace training (destination instruction)management of history (production history, work history, inspection history, etc.)ID (identification) typically refers to the specific identification of individuals or things.RFID is used to identify objects, just like barcodes and two-dimensional codes.Fingerprints and the iris of the eye are examples of biometrics used to identify persons in a unique way.The identification system is known as ID system. It is a method for reading and recognizing data on people and things, including AIDC (Automatic Identification & Data Capture).
AIDC uses devices that combine hardware and software to identify data acquired from media such as barcodes, 2-dimensional codes, RFID systems, iris, fingerprints, voice, etc. without the need for human participation.
To learn more about RFID system click here:
brainly.com/question/25705532
#SPJ4
PLEASE HELP ASAP (answer is needed in Java) 70 POINTS
In this exercise, you will need to write a program that asks the user to enter different positive numbers.
After each number is entered, print out which number is the maximum and which number is the minimum of the numbers they have entered so far.
Stop asking for numbers when the user enters -1.
Possible output:
Enter a number (-1 to quit):
100
Smallest # so far: 100
Largest # so far: 100
Enter a number (-1 to quit):
4
Smallest # so far: 4
Largest # so far: 100
Enter a number (-1 to quit):
25
Smallest # so far: 4
Largest # so far: 100
Enter a number (-1 to quit):
1
Smallest # so far: 1
Largest # so far: 100
Enter a number (-1 to quit):
200
Smallest # so far: 1
Largest # so far: 200
Enter a number (-1 to quit):
-1
Answers
import java.util.Scanner;
public class MyClass1 {
public static void main(String args[]) {
Scanner scan = new Scanner(System.in);
int smallest = 0, largest = 0, num, count = 0;
while (true){
System.out.println("Enter a number (-1 to quit): ");
num = scan.nextInt();
if (num == -1){
System.exit(0);
}
else if (num < 0){
System.out.println("Please enter a positive number!");
}
else{
if (num > largest){
largest = num;
}
if (num < smallest || count == 0){
smallest = num;
count++;
}
System.out.println("Smallest # so far: "+smallest);
System.out.println("Largest # so far: "+largest);
}
}
}
}
I hope this helps! If you have any other questions, I'll do my best to answer them.
Java exists a widely utilized object-oriented programming language and software platform. Sun Microsystems initially introduced Java, a programming language and computing platform, in 1995.
What is meant by java?Sun Microsystems initially introduced Java, a programming language and computing platform, in 1995. It has grown from its modest origins to power a significant portion of the digital world of today by offering the solid foundation upon which numerous services and applications are developed.
The object-oriented programming language and software platform known as Java are used by millions of devices, including laptops, cellphones, gaming consoles, medical equipment, and many others. The syntax and guiding ideas of Java are derived from C and C++.
The program is as follows:
import java.util.Scanner;
public class MyClass1 {
public static void main(String args[]) {
Scanner scan = new Scanner(System.in);
int smallest = 0, largest = 0, num, count = 0;
while (true){
System.out.println("Enter a number (-1 to quit): ");
num = scan.nextInt();
if (num == -1){
System.exit(0);
}
else if (num < 0){
System.out.println("Please enter a positive number!");
}
else{
if (num > largest){
largest = num;
}
if (num < smallest || count == 0){
smallest = num;
count++;
}
System.out.println("Smallest # so far: "+smallest);
System.out.println("Largest # so far: "+largest);
}
}
}
}
To learn more about Java refer to:
https://brainly.com/question/25458754
#SPJ2
State what the code will do:
int("76423")
Answers
The thing that the code will do: Int("76423"), Asc(" T ") and 12 Mod 5 are:
Take the string "76423" and return the integer 76423.Return the ASCII number for the character "T"Returns the remainder when 12 is said to be divided by 5, i.e. 2.What is Coding?Coding is the process of writing instructions in programming languages for computers, according to the definition. Programming is used to create the websites, apps, and other technologies that we use on a daily basis.
Note that ASCII is the foundation for all character sets used in HTML, on the Internet, and in contemporary computers.
Learn more about ASCII number from
https://brainly.com/question/13143401
#SPJ1
See full question below
State what the code will do: Int("76423"), Asc(" T") and 12 Mod 5.
How many lines are on a standard sheet of typing paper?
Answers
To reduce costs and the environmental impact of commuting, your company decides to close a number of offices and to provide support for staff to work from home. However, the senior management who introduce the policy are unaware that software is developed using Scrum. Explain how you could use technology to support Scrum in a distributed environment to make this possible. What problems are you likely to encounter using this approach
Answers
Answer:
The description including its query is provided throughout the section of the elaboration elsewhere here.
Explanation:
Coordination between teams is the main challenge that this new strategy can make. Agile creation is focused on the teamwork of cross-functional teams, where every other mission is identified and distinct teams are formed. All the departments collaborate and afterward work in stages until the completion of this research project.Unless the organization shuts several departments, contact with various teams and peers will be disrupted and contact differences with workers as well as the team would be established. The best approach will be to provide regular communication calls with multiple project managers such that each project stage is synchronized. In turn, this same project coordinator should always have numerous calls with his group members to even get construction progress.question 9 please help
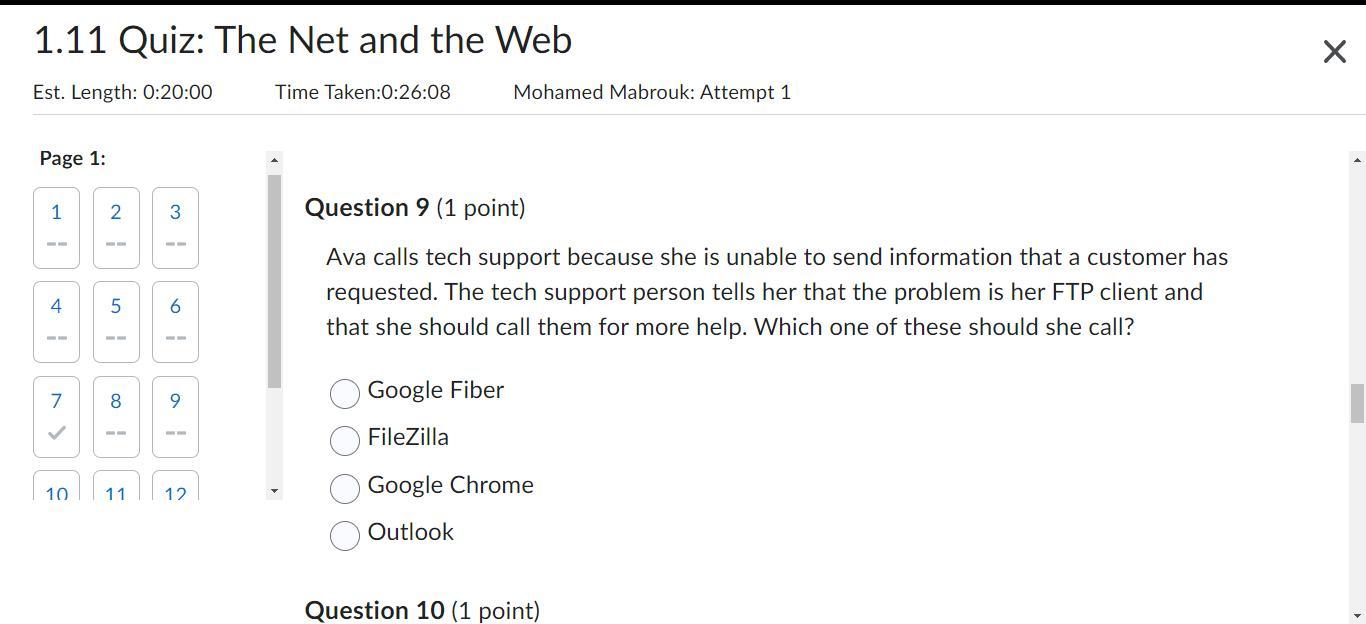
Answers
Answer:
FileZilla
Explanation:
FileZilla is open-source software that supports multiple FTP protocols that allow file exchange over the network.
What are some technical challenges and questions that arise from the need to represent digital information in computers and transfer it between people and computational devices?
Answers
Answer:
security
Explanation:
One technical issue that arises from this is security. Many times the information that is being transferred is private or even valuable, therefore grabbing the attention of hackers/thief's that want this information. This makes security highly important, but making sure that the information is completely secure is impossible. The best that can be done is adding certain safety measures to secure the information as much as possible, which in term is a technical challenge.
Ross is running a small data entry back office, for which he has contracted you for network management. Ross has made it very clear that because he has just started the company he wants to cut down on expenses wherever he can. One such option involves the router-he wants to exchange the router with a similar but less expensive alternative. Which of the following will you refer to Ross in such a situation?
a. A layer 3 switch
b. An SDN controller
c. Storm control
d. A root port
Answers
The right option that I can refer to Ross in such a situation is called a A layer 3 switch.
What is a layer 3 switch?This is known to help make switch packets by looking at IP addresses and also MAC addresses.
Note that Layer 3 switches helps to separate ports into virtual LANs (VLANs) and carry out the routing between them and as such, The right option that I can refer to Ross in such a situation is called a A layer 3 switch.
Learn more about switch from
https://brainly.com/question/17245000
#SPJ4
What is the result when you run the following program?
print(2 + 7)
print("3+1")
9
Ost
3+1
an error statement
O
2 +7
4
9
O A
Answers
Answer:
The answer to this question is given below in the explanation section.
Explanation:
If you run the following program,
print(2 + 7)
print("3+1")
then, you can get the following result respectively against each print statement.
9
3+1
because when you print 2+7 without quotation, it will add the integer digit and print the result of adding 2 and 7.
And, when you run ("3+1") in the double quotation, the program will treat it as a string because of the enclosed double quotation (" ");
Integrated marketing communications require a company's mass-market advertisements, web site, e-mail, and personal selling communications to all ________.
Answers
Integrated marketing communications need a company's mass-market advertisements, website, e-mail, and personal selling communications to all the same clear and compelling message.
What is Integrated Marketing?Integrated marketing exists as a strategy for delivering a unified message across all the marketing channels your brand uses. It furnishes consistency wherever customers select to interact with a company. Without an integrated marketing strategy, you risk delivering mixed messages or communicating in a disconnected voice.
The goal of integrated marketing communications exists to guarantee that customers receive the same message when they interact with a company's brand in different ways. Integrated marketing communication (IMC) can be described as the process utilized to unify marketing communication elements, such as public relations, social media, audience analytics, business development principles, and advertising, into a brand identity that stays consistent across distinct media channels.
A compelling message resonates with the audience's values and beliefs. It stands prepared to help the audience solve their problems, achieve their goals and dreams, and meet their requirements. It uses words and resolutions the audience understands and finds relatable.
Hence, Integrated marketing communications need a company's mass-market advertisements, website, e-mail, and personal selling communications to all the same clear and compelling message
To learn more about Integrated marketing communications refer to:
https://brainly.com/question/9696745
#SPJ4
Which science fiction author was born in the 1800s?
Frank Herbert, Robert Heinlein, Edgar Rice Burroughs, Isaac Asimov
Answers
Answer:
Edgar Rice Burroughs, known for his work in Science Fiction and Fantasy, was born in the 1800s.
Explanation:
Other Choices:
Frank Herbert was also a known Science Fiction writer, but he wasn't born until 1920.
Robert Heinlein was born in 1907 and also a well-published Science Fiction author and military officer.
Isaac Asimov, much like Frank Herbert, wasn't born until 1920 and contributed to the same field of literature.
in the text it was stated that when a mobile host is not at home, packets sent to its home lan are intercepted by its home agent on that lan. for an ip network on an 802.3 lan, how does the home agent accomplish this interception?
Answers
When a mobile host is not at home, packets sent to its home LAN are intercepted by its home agent on that LAN. In an IP network on an 802.3 LAN, the home agent accomplishes this interception through a process called tunneling.
1. When a packet is sent to the mobile host's home LAN, it is first received by the home agent. The home agent is a router located on the home LAN that acts as an intermediary for the mobile host.
2. The home agent encapsulates the packet by adding a new IP header to it. This new header contains the source IP address of the home agent and the destination IP address of the mobile host.
3. The encapsulated packet is then sent to the foreign network where the mobile host is currently located. The encapsulation ensures that the packet is correctly routed to the foreign network.
4. When the encapsulated packet arrives at the foreign network, it is received by a router called the foreign agent. The foreign agent decapsulates the packet by removing the additional IP header added by the home agent.
5. The decapsulated packet is then delivered to the mobile host on the foreign network.
By using this tunneling technique, the home agent is able to intercept packets destined for the mobile host's home LAN and forward them to the mobile host wherever it is currently located. This enables seamless communication for the mobile host even when it is away from its home network.
In summary, the home agent intercepts packets sent to a mobile host's home LAN by encapsulating them and sending them to the foreign network. The foreign agent then decapsulates the packets and delivers them to the mobile host. This process allows the mobile host to receive packets even when it is not at home.
To learn more about mobile host :
https://brainly.com/question/31472821
#SPJ11
1. Is the function void or return
a. void
b. return
2. What is the result of the following expression: int r = 3; r%2 == 0;
a. it evaluates as true
b. it evaluates as false
c. nothing happens
Answers
Answer:
(a) void
(b) Nothing happens
Explanation:
Solving (a): void and return
A function that returns no value is referred to as a void function.
On the other hand, a void can not be return or named return.
So, the function is void
Solving (b):
r = 3
Required
The result of r%2 == 0
Substitute 3 for r in r%2 == 0
3%2 == 0
3%2 is 1.
So, we have:
1 == 0
Hence, the equivalent of r%2 == 0 is 1 == 0.
However, nothing will happen because there is no instruction attached to the statement (i.e. r%2 == 0;)
A _____ is either a single table or a collection of related tables.
Answers
A database is either a single table or a collection of related tables. Databases store and organize data, allowing for efficient retrieval, modification, and management.
Tables within a database consist of rows and columns, where each row represents a unique record and each column contains a specific attribute or field. Related tables can be connected through keys, enabling users to access and analyze data across multiple tables simultaneously. This structure facilitates accurate and comprehensive data representation, simplifying data-driven decision-making processes.
Hence, A database is either a single table or a collection of related tables. Databases store and organize data, allowing for efficient retrieval, modification, and management.
To know more about database visit
https://brainly.com/question/30462775
#SPJ11
What are the assumptions of CPM?
Answers
The components of a project can be broken down into a number of predictable, independent tasks. A non-cyclical network graph with direct connections between each activity and its immediate successors is able to fully depict the precedence relationships of project activities.
What is meant by CPM?Companies pay a fee for every 1,000 impressions an ad obtains when using the paid advertising option known as CPM (cost per mile). An "impression" is when someone views a campaign on social media, search engines, or another marketing site.The critical path method (CPM) is a step-by-step project management strategy for process planning that distinguishes between important and non-critical tasks with the intention of avoiding project schedule issues and process bottlenecks.Corporate performance management (CPM) is a catch-all phrase that denotes the strategies, metrics, processes, and systems used to track and manage an organization's business performance.For the telecoms, general retail, health and beauty, publishing, and entertainment sectors, respectively, a decent CPM is $1.39, $1.38, $1.00, $1.75, and $0.78.To learn more about CPM refer to:
https://brainly.com/question/28498043
#SPJ4
One of the disadvantages of cable technology is that: while it works well for television signals, it is ineffective for data transmissions required by the Internet. while it works well for television signals, it is ineffective for data transmissions required by the Internet. none of the available options are true. none of the available options are true. it is incompatible with most modern communication systems. it is incompatible with most modern communication systems. systems used by many providers require customers to share bandwidth with neighbors. systems used by many providers require customers to share bandwidth with neighbors.
Answers
Answer:
systems used by many providers require customers to share bandwidth with neighbors
Explanation:
One of the disadvantages of cable technology is that systems used by many providers require customers to share bandwidth with neighbors. This ultimately causes many problems since cables would need to be extended to reach every single user that will be sharing the bandwidth. This would mean cables all over the place. Also, it is very difficult to limit the bandwidth per person, meaning that if anyone is using up all of the bandwidth through the cable, the rest of the individuals connected would not have the bandwidth that they need or are paying for.
What does "the challenge page was accidentally cached" mean? How do I fix it?
Answers
"The challenge page was accidentally cached" means that a web page was stored in a browser's cache memory.
What is cache memory?Cache memory is a type of fast memory that is used to store frequently accessed data, instructions and objects. It is located between the CPU and main memory, and is designed to speed up the retrieval of data and instructions by the CPU. Cache memory stores recently accessed information so that when the CPU requests data, it can be retrieved quickly from the cache instead of having to access the main memory.
This can happen when a user visits a web page and their browser mistakenly stores the content of that page locally, instead of downloading a fresh version of it every time they visit.
To fix this, you need to force the browser to clear the page from its cache memory. This can usually be done by pressing the refresh button or by pressing Ctrl+F5. Additionally, you can also clear the browser's cache manually by going to the settings and deleting the cached data.
To learn more about cache memory
https://brainly.com/question/14342135
#SPJ1
Software developers create solutions such as web and desktop applications, mobile apps, games, and operating systems. This week you will complete an activity where you will take on the role of a software developer.
Over the last 6 months, you noticed that your bank account balance is lower than you expected by the 15th of every month. To track your expenditures, you decide to create an expense tracker mobile app that has the following functionalities.
You can add and categorize your expenses.
It has a calculator and a personal spending planner to help you with personal budgeting.
Write a 700-word requirements report that will serve as a starting point for developing the app, by detailing the following:
Include 5 critical features the app must have.
Include descriptions of any 3 expense tracking apps and their features.
Describe 3 software development activities the software developer should consider for this project.
List the software, hardware, and people requirements.
Describe an estimate of the time, cost, and efforts required.
Answers
Expense Tracker Mobile App Requirements ReportRequirements Report is the critical document that sets the stage for software development. This report acts as a starting point for developing an app, and software developers use it to create the app.
This report outlines what the software will do and how it will behave. To design and develop an expense tracker mobile app, software developers will need to complete several tasks. This report contains a description of five critical features the app must have, three software development activities to consider, and software, hardware, and personnel requirements. Finally, this report includes an estimate of the time, cost, and effort required to create this app.
Five critical features the app must-haveThe following are five critical features that the expense tracker mobile app must have.Adding and CategorizingExpenses: An expense tracker mobile app must have the ability to add and categorize expenses. Users can keep track of their expenses by adding and categorizing them.
Personal Budget Planner: The app must have a personal budget planner that allows users to budget their expenses.
Calculator: The app must have a calculator that will allow users to perform calculations such as addition, subtraction, multiplication, and division.
Currency Converter: A currency converter is an essential feature that helps users convert their expenses from one currency to another. Notification System: The app should have a notification system to remind users to enter expenses.
Three expense-tracking apps and their features here are three examples of expense-tracking apps and their features. Mint: Mint is an expense tracker app that connects to your bank account and automatically tracks your spending. It also has a budgeting tool and provides free credit scores. Personal Capital: Personal Capital is another expense tracker app that helps you manage your finances. It offers free financial planning tools, such as retirement planning and investment tracking. Wally: Wally is an expense tracker app that allows you to scan receipts and automatically track your expenses. It has a budget tracker, a savings goal tracker, and a group budgeting feature.
Three software development activities to consider for this projectThe following are three software development activities to consider for this project. Planning: Planning is an essential activity in software development. In this stage, the software developers will define the requirements, features, and objectives of the expense tracker mobile app. Requirements Gathering: During this stage, software developers will gather information from the end users. This activity will help to understand the end user's needs and preferences. User Interface Design: The User Interface Design will be a significant activity in software development. The developers will have to design an intuitive and user-friendly interface that is easy to use.
Software, hardware, and people requirementsThe following are the software, hardware, and people requirements. Software: The app will be developed using the following software development tools: Visual Studio Code, Xcode, Android Studio, Swift, Java, and Node.js.Hardware: The following hardware is required: MacBook Pro, iPhone, iPad, Android phone, and Android tablet.People: The following personnel are required for software development: a project manager, a software developer, a quality assurance tester, and a graphic designer.
Estimate of time, cost, and effortsThe following is an estimate of the time, cost, and effort required to create the app. Time: The project will take approximately three months to complete.Cost: The project will cost approximately $50,000 to develop.Effort: The project will require 20 hours of work per week from each team member. This is equivalent to 320 hours of work per team member.
Know more about Tracker Mobile App Requirements here,
https://brainly.com/question/32145955
#SPJ11
How does the brain influence your emotions, thoughts, and values?
Answers
Amygdala. Each hemisphere of the brain has an amygdala, a small, almond-shaped structure. The amygdalae, which are a part of the limbic system, control emotion and memory and are linked to the brain's reward system, stress, and the "fight or flight" reaction when someone senses a threat.
What are the effects of the brain?Serotonin and dopamine, two neurotransmitters, are used as chemical messengers to carry messages throughout the network. When brain areas get these signals, we recognize things and circumstances, give them emotional values to direct our behavior, and make split-second risk/reward judgments.Amygdala. The amygdala is a small, almond-shaped structure found in each hemisphere of the brain. The limbic systems' amygdalae control emotion and memory and are linked to the brain's reward system, stress, and the "fight or flight" response when someone perceives a threat.Researchers have demonstrated that a variety of brain regions are involved in processing emotions using MRI cameras. Processing an emotion takes happen in a number of different locations.To learn more about Amygdala, refer to:
https://brainly.com/question/24171355
#SPJ1
Urgent!
1. The semantic mode that allows passing data to a subroutine
only is:
No answer is correct
In mode
Inout mode
Out mode
2. The passing method that is also called pass-by-copy is:
Pass-by-Refer
Answers
1. The semantic mode that allows passing data to a subroutine only is Out mode.
2. The passing method that is also called pass-by-copy is Pass-by-Value.
Explanation:
1. The semantic mode that allows passing data to a subroutine only is Out mode.
Out mode is a semantic mode that enables data to be transmitted from the caller to the called function through parameters in the parameter list.
The "out" modifier is used to specify parameters that should be transferred out of the function. If an output argument's value is changed inside a function, the caller is informed of the changes.
2. The passing method that is also called pass-by-copy is Pass-by-Value.
Pass-by-value is a mechanism for passing data to a subroutine or function in which the calling statement passes a copy of the data to the call.
When the called function modifies the data, the modifications do not affect the original copy of the data passed by the calling statement.
A new copy of the information is created, and any changes made in the called function are not reflected in the original copy of the information.
If any modifications are made to the data in the subroutine, they will only affect the copy of the data, and the original data will remain unchanged.
To know more about Pass-by-Value, visit:
https://brainly.com/question/32644556
#SPJ11
1. Predict the output from the following devices a) 1 0 MUX D 0 1 0 1 c) 0 C = ? LUSS F = ? MAY 0 0 b) 0 0 DECODER ENCODER D A A = ? B=7
Answers
Here's the predicted output for the given devices in two lines:
a) 1 0 MUX: 0
b) 0 0 DECODER: 0
Based on the given inputs, here are the predicted outputs for each device:
a) 1 0 MUX: Assuming the inputs A, B, and S represent the select lines of the 1 0 MUX, and D0, D1 represent the input data lines, the output can be determined as follows:
- A = 0, B = 1, S = 0: The output would be D0, which is 0 in this case.
b) 0 0 DECODER: Assuming the inputs A and B represent the input lines of the 2-to-4 decoder, the output can be determined as follows:
- A = 0, B = 0: The decoder will select the 0th output line, resulting in A = 0.
c) ENCODER: Assuming the inputs A and B represent the inputs to the encoder, and C and F represent the output lines, the output can be determined as follows:
- A = 0, B = 1: This represents the binary number 01. The encoder will output C = 0 and F = 1.
So, the predicted outputs are:
a) 0
b) 0
c) C = 0, F = 1
Learn more about Decoder
brainly.com/question/31064511
#SPJ11
The ______ sets rules for both the transport of data packets and the addressing system for a network such as the ARPANET
Answers
The tool that sets rules for both the transport of data packets and the addressing system for a network such as the ARPANET is called; Protocol
Understanding ProtocolsIn computer systems communications, a protocol is defined as a set of rules and regulations that allow a network of nodes to transport and receive data information.
Now, each transport layer in a system of network such as ARAPNET will always have a protocol set such as TCP and IP.
Read more about internet protocols at; https://brainly.com/question/17820678
Pie charts are best used for

Answers
Answer:B
Explanation:Showing parts of a whole.
you are the network administrator for a small consulting firm. you've set up an ntp server to manage the time across all the machines in the network. you have a computer that's experiencing a slight time drift of just a few seconds. which time correction should you use to fix the system's clock?
Answers
NTP is a built-in UDP protocol; NTP server communication takes place over port 123, while NTP clients (such as desktop computers) use port 1023.
What is NTP, or the Network Time Protocol?A network protocol called Network Time Protocol (NTP) is used to synchronize with computer clock time sources. It is a component of the TCP/IP suite and one of its earliest. The computer-based client-server programs and the protocol are both referred to as NTP.
Which NTP server ought to I utilize?If you need to locate multiple NTP servers, use pool.ntp.org (or 0.pool.ntp.org, 1.pool.ntp.org, etc.) in most cases. The system will try to locate the closest servers that are available for you.
Learn more about Network Time Protocol here:
https://brainly.com/question/13068616
#SPJ1
In the Word Online application, color schemes cannot be changed after initial setup. True Or False?
Answers
Answer:
False
Explanation:
refer to the exhibit. what can be determined about the contents of the ite user home directory? the octal representation of the permissions for january is 755. the data files in this user directory contain no data. all users have read, write, and execute permissions to files within the directories. there are two data files and three directories contained in this user directory.
Answers
From the given exhibit, we can determine several things about the contents of the "ite" user home directory.Firstly, there are three directories present within the "ite" user home directory.
These directories are "Desktop", "Downloads", and "Documents". Additionally, there are two data files in this user directory, which are not specified by name or file type.
Secondly, the octal representation of the permissions for the "January" file is 755. This means that the owner of the file has full permissions, including read, write, and execute. The group associated with the file, as well as all other users, have read and execute permissions only.
Lastly, we are told that all users have read, write, and execute permissions to files within the directories. This indicates that the permissions for the directories within the "ite" user home directory are likely set to allow full access to all users.
Overall, we can infer that the "ite" user home directory contains several directories and files with relatively permissive access permissions. However, without additional information, we cannot determine the specific contents or purposes of the directories and files within the directory.
To know more about directory click this link -
https://brainly.com/question/30272812
#SPJ11
You are instructing a user on how to properly use a new laptop. He asks about the special function keys that are used to perform tasks such as toggling the display or adjusting the display brightness. Which key should the user strike in combination with the special function keys
Answers
Answer:
The Fn key.
Explanation:
In this scenario, you are instructing a user on how to properly use a new laptop. He asks about the special function keys that are used to perform tasks such as toggling the display or adjusting the display brightness.
The user should strike the "Fn" key in combination with the special function keys.
In Computer science, the special function keys found on the top row of a keyboard are the F1, F2, F3, F4, F5, F6, F7, F8, F9, F10, F11, and F12 keys. Each of the special function keys just like their name suggests are used to perform different tasks respectively as defined by the operating system of a computer.
Fn is an acronym for function. In order to use the special function keys, a user must first hold down the Fn key before pressing the specific special function key which then triggers functions configured to use this key.
For instance, "Fn+F2" is to reduce brightness on the Windows operating system. Also, "Fn+F12" is to increase audio volume on the Mac operating system.
Prepare a profile on major universities in the country Nepal
Answers
Answer:
Formal higher learning in Nepal began with the establishment of Tri-Chandra College in 1918, the first college in the country. Until 1985, Tribhuvan University (TU) was the only university in the country. The second university to be founded was Mahendra Sanskrit University. The inception of this university was soon followed by Kathmandu University in 1990, and Purbanchal and Pokhara Universities in 1995 and 1996, respectively. Many schools and colleges are run privately but none of the universities in Nepal are private.
This list includes all notable universities and colleges/campuses in Nepal. Entries are organised by courses offered, and listed in alphabetical order. Some entries that provide multiple courses may be duplicated in each of the relevant categories.
There are fourteen universities in Nepal. They are: Khwopa University (Proposed)
Agriculture and Forestry University in Chitwan
Far-western University in Kanchanpur
Gandaki University in Tanahun
Kathmandu University in Dhulikhel
Lumbini Bouddha University
Madan Bhandari University of Science and Technology
Manmohan Technical University in Biratnagar
Mid Western University in Birendranagar
Nepal Open University[1][2] in Lalitpur
Nepal Sanskrit University
Pokhara University in Pokhara
Purbanchal University in Biratnagar
Rajarshi Janak University in Janakpurdham
Tribhuvan University in Kirtipur
The university that will be profiled in their case is the Agriculture and Forestry University, Chitwan, Nepal.
The Agriculture and Forestry University, Chitwan, Nepal offers undergraduate, graduate, and PhD programs in agricultural sciences.
The university has several faculties such as the faculty of agriculture and animal sciences, fisheries, and aquaculture.
Learn more about universities on:
https://brainly.com/question/25853486
Q. How to start a software house,
explain each step in detail. (750 words)
Answers
Starting a software house involves several steps to establish a successful and thriving business in the software development industry.
To start a software house, you need to follow three key steps: research and planning, setting up the infrastructure, and acquiring talent and clients.
Research and Planning:
Before diving into the software house venture, it is essential to conduct thorough research and create a comprehensive business plan. Identify your target market, analyze the competition, and determine the unique value proposition of your software house. Define your niche, such as web development, mobile app development, or specialized software solutions. This research and planning phase will provide a solid foundation for your business and guide your decision-making process.
Learn more about : infrastructure
brainly.com/question/32687235
#SPJ11
Setting up the Infrastructure:
Once you have a clear business plan, it's time to establish the infrastructure necessary to run a software house. This includes securing office space, setting up hardware and software systems, and implementing efficient project management processes. Acquire the necessary equipment, such as computers, servers, and development tools, to support your team's work. Additionally, invest in robust project management and collaboration tools to streamline communication and ensure smooth project execution.
Learn more about :business plan
brainly.com/question/15826679
#SPJ11
Acquiring Talent and Clients:
The success of a software house heavily relies on skilled and talented professionals. Recruit and assemble a team of developers, designers, testers, and project managers who possess the expertise required to develop cutting-edge software solutions. Promote a culture of continuous learning and professional growth within your team. Simultaneously, establish a strong marketing and sales strategy to attract and acquire clients. Leverage digital marketing channels, attend industry conferences, and build a strong online presence to showcase your software house's capabilities and attract potential clients.
Learn more about : sales strategy
brainly.com/question/28139464
#SPJ11
In summary, starting a software house requires careful research and planning, establishing the necessary infrastructure, and acquiring talented professionals and clients. By following these steps, you can lay a solid foundation for your software house and position it for long-term success in the competitive software development industry.
A certain programming language uses 4-bit binary sequences to represent nonnegative integers. For example, the binary sequence 0101 represents the corresponding decimal value 5. Using this programming language, a programmer attempts to add the decimal values 14 and 15 and assign the sum to the variable total. Which of the following best describes the result of this operation?
Answers
Answer:
C
Explanation:
An overflow error will occur because 4 bits is not large enough to represent 29, the sum of 14 and 15
The term "bit" means binary digit, and it is used to represent data in a computer system. 4 bits can hold the sum of 14 and 15 because 4-bit is not large enough to represent 29 (an overflow will occur)
The maximum size of data an n-bit computer can hold is \(2^n\)
So, a 4-bit computer can hold a maximum of:
\(Max = 2^4\)
\(Max = 16\)
i.e a maximum of 16 digits
In binary, the digits are 0000 to 1111 i.e. from 0 to 15
So, when 14 and 15 are added, the result is:
\(14 + 15 = 29\)
The result is 29.
29 in binary is 11101
11101 is out of the range of the 4-bit binary sequence
Hence, an overflow will occur because 4-bit is not large enough to hold the sum
Read more about binary digits at:
https://brainly.com/question/9480337