To effectively store and turn-over warehouse materials, which type of inventory should be cleared first?
Answers
Answer:
First in first out (FIFO) warehousing means exactly what it sounds like. It's an inventory control method in which the first items to come into the warehouse are the first items to leave
Explanation:
To effectively store and turn over warehouse materials, the type of inventory that should be cleared first is the First-In, First-Out (FIFO) method. This inventory management technique ensures that older items are sold or used before newer ones.
By clearing stock in the order it arrives, businesses can minimize the risk of spoilage, obsolescence, and depreciation.
FIFO is particularly important for perishable goods, such as food or pharmaceuticals, where expiration dates play a critical role in maintaining product quality and safety.
By selling older items first, companies can reduce waste and maintain customer satisfaction. Additionally, FIFO helps maintain accurate financial records, as it aligns with the natural flow of inventory in most businesses. This alignment simplifies accounting processes, making it easier to determine the cost of goods sold and maintain an accurate valuation of the remaining inventory.
In summary, clearing inventory using the First-In, First-Out method ensures efficient warehouse management by reducing waste, maintaining product quality, and simplifying financial record keeping.
You can learn more about inventory at: brainly.com/question/15118949
#SPJ11
Related Questions
What are the different data types that a variable can be in computer programming?
Answers
Answer:String (or str or text)
Character (or char)
Integer (or int)
Float (or Real)
Boolean (or bool)
Explanation:
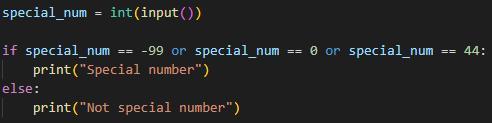
Can you solve this challenging activity?

Answers
Answer:
special_num = int(input())
if special_num == -99 or special_num == 0 or special_num == 44:
print("Special number")
else:
print("Not special number")
Explanation:
___ are stem professionals who collect, analyze, and interpret data
Answers
Answer:
Statisticians
Explanation:
Statistics is a science, technology, engineering, and math (STEM) related degree that involves acquiring knowledge through data. A statistician sources data through administering questionnaire, taking polls and carrying out experiments. From the collected data, the statistician makes use of statistical concepts to sift through large data sets, develop data interpretation and deduce relevant information from the data and present meaningful conclusion to the relevant bodies in fields such as education, manufacturing, marketing, government and healthcare.
Answer:
statiscians
Explanation:
Explain why computer professionals are engaged in technical services
Answers
Answer: It's probably because they love computers and they know what they are doing. Also they can write specs for new computers.
Explanation: Hope this helps.
what are the uses of plotters
Answers
Answer:
Plotters are use to produce the hard copy of schematics and other similar applications They are mainly used for CAE applications.They can print on a wide variety of flat materialsHope it helps :)❤
Answer:
Plotters are used to print graphical output on paper. It interprets computer commands and makes line drawings on paper using multicolored automated pens. It is capable of producing graphs, drawings....
How doe a network-baed intruion prevention ytem protect a network?
It monitor log file. It analyze protocol activity. It record network acce. It focue on the protection of oftware
Answers
The confidentiality, integrity, and availability of a network are all protected by a network-based intrusion prevention system (NIPS).
What kind of protection does a network-based intrusion prevention system provide?
An intrusion prevention system (IPS) is indeed a network security technology that continuously checks a network for malicious activity and responds to it by reporting, blocking, or discarding it as it occurs. It could be hardware or software.
What is the operation of a network intrusion detection system?
NIDS are positioned strategically throughout the network to watch over traffic going to and coming from all connected devices. It analyzes the traffic traveling across the entire subnet and compares it to the traffic passing across the subnets to the collection of well-known assaults.
To know more about monitor network visit:-
brainly.com/question/29992945
#SPJ4
____ can only be specified when a column list is used and identity_insert is on
Answers
The phrase "identity_insert" is typically used in the context of SQL databases, specifically when dealing with tables that have an identity column.
How can this be explained?In such cases, when performing an INSERT operation and explicitly specifying column values, the "identity_insert" property must be enabled for the table.
Additionally, when specifying columns explicitly during an INSERT operation, the column list must also be provided. These conditions ensure that the values being inserted into the identity column are allowed and controlled.
Without enabling "identity_insert" or providing a column list, the operation will not be permitted.
Read more about SQL here:
https://brainly.com/question/25694408
#SPJ1
Which web source citations are formatted according to MLA guidelines? Check all that apply.
“Nelson Mandela, Anti-Apartheid Icon and Father of Modern South Africa, Dies.” Karimi, Faith. CNN. Turner Broadcasting. 5 Dec. 2013. Web. 1 Mar. 2014.
“Nelson Mandela Biography.” Bio.com. A&E Television Networks, n.d. Web. 28 Feb. 2014.
Hallengren, Anders. “Nelson Mandela and the Rainbow of Culture.” Nobel Prize. Nobel Media, n.d. Web. 1 Mar. 2014.
“Nelson Mandela, Champion of Freedom.” History. The History Channel. Web. 1 Mar. 2014.
“The Long Walk is Over.” The Economist. The Economist Newspaper, 5 Dec. 2013. Web. 1 Mar. 2014.
Answers
The citation that is formatted according to MLA guidelines is:
“Nelson Mandela, Anti-Apartheid Icon and Father of Modern South Africa, Dies.” Karimi, Faith. CNN. Turner Broadcasting. 5 Dec. 2013. Web. 1 Mar. 2014.
What is Apartheid?
Apartheid was a system of institutional racial segregation and discrimination that was implemented in South Africa from 1948 to the early 1990s. It was a policy of the government that aimed to maintain white minority rule and power by segregating people of different races, and denying non-whites their basic rights and freedoms.
This citation follows the basic MLA format for citing a web source. It includes the following elements:
None of the other citations are formatted according to MLA guidelines because they either have missing or incorrect elements. For example, the citation for "Nelson Mandela Biography" does not include the date of publication, and the citation for "Nelson Mandela and the Rainbow of Culture" does not include the name of the publisher. The citation for "Nelson Mandela, Champion of Freedom" does not include the date of publication or the name of the publisher. The citation for "The Long Walk is Over" includes the date of publication, but it does not include the name of the publisher, and the title is not italicized.
To know more about citation visit:
https://brainly.com/question/29885383
#SPJ1
code-switching decreases the chances of achieving your communication goals
Answers
The statement "Code-switching decreases the chances of achieving your communication goals" is false.
What is Code-switching?Code-switching is the use of more than one language or linguistic style in a conversation or interaction. Code-switching can be between different languages, dialects, registers, or speech styles.In various multilingual and multicultural societies, code-switching is a frequent and natural phenomenon.
People code-switch for a variety of reasons, such as to express identity, cultural allegiance, social distance, and so on.However, code-switching has been found to improve communication by allowing speakers to express themselves more accurately and fluently, as well as to communicate with a more diverse group of people
Learn more about code-switching at
https://brainly.com/question/31452528
#SPJ11
State whether the given statement is True/False. Arguments are the input values to functions upon which calculations are performed.
Answers
___________ is the number of pixels per inch
Answers
Answer:
Explanation:
What ever the number is inches is divide it by pixels
Display a program that accepts the length and width of rectangle it should calculate and display its area
Answers
A program that accepts the length and width of a rectangle it should calculate and display its area is given below'
The Program# Python Program to find Perimeter of a Rectangle using length and width
length = float(input('Please Enter the Length of a Triangle: '))
width = float(input('Please Enter the Width of a Triangle: '))
# calculate the perimeter
perimeter = 2 * (length + width)
print("Perimeter of a Rectangle using", length, "and", width, " = ", perimeter)
The OutputPlease Enter the Length of a Triangle: 2
Please Enter the Width of a Triangle: 2
preimeter of a rectamgle is 8.0
preimeter of a rectamgle is 4.0
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
You defined a shoe data type and created an instance.
class shoe:
size = 0
color = 'blue'
type = 'sandal'
myShoe = shoe()
Which statement assigns a value to the type?
type = 'sneaker'
myShoe.type( 'sneaker')
myShoe.type = 'sneaker'
NEXT QUESTION
ASK FOR HELP
Answers
Answer:
myShoe.type = 'sneaker'
Explanation:
type is a field of the class shoe. The myShoe object which is an instance of the class shoe has the field type also.
To assign a value to type filed of the object myShoe, reference the object then the field as such;
myShoe.type = "sneaker"
You defined a shoe data type and created an instance. The statement that assigns a value to the type is myShoe.type = 'sneaker'. The correct option is C.
What is data in programming?A variable's data type and the kinds of mathematical, relational, and logical operations that can be performed on it without producing an error are classified as data types in programming.
An attribute of a piece of data called a "data type" instructs a computer system on how to interpret that data's value.
type is one of the class shoe's fields. The field type is also present in the myShoe object, which is an instance of the class shoe.
Reference the object and the field as such in order to assign a value to the type field of the object myShoe;
Therefore, the correct option is C. sneaker" in myShoe.type.
To learn more about data in programming, refer to the link:
https://brainly.com/question/14581918
#SPJ2
What is the prefix for the host address 2001:db8:bc15:a:12ab::1/64? the network portion, or prefix, of an ipv6 address is identified through the prefix length. a /64 prefix length indicates that the first 64 bits of the ipv6 address is the network portion. hence the prefix is 2001:db8:bc15:a.
Answers
An IPv6 address's prefix length serves as a means of identifying the network portion, or prefix. The network portion of an IPv6 address is the first 64 bits, as indicated by a prefix length of /64. The prefix is 2001:DB8:BC15:A as a result.
The IPv6 address 2001 db8 is associated with what prefix?A unique IPv6 prefix that is used only for documentation examples is 2001:db8::/32. Additionally, you can specify a subnet prefix, which tells a router how the network is organized internally. The subnet prefix for the example IPv6 address is as follows. The subnet prefix is always 64 bits long.
Describe the IPv6 prefix.The idea of IPv6 prefixes is comparable to IPv4 subnetting. When an IPv6 address has a prefix, it is written as an IPv6 address followed by a decimal number that indicates how many bits in the address make up the prefix.
To know more about network visit:-
brainly.com/question/29350844
#SPJ4
Using real life example explain the use of data analytics in healthcare?
Answers
Data analytics plays a crucial role in healthcare, enabling professionals to extract valuable insights from large volumes of healthcare data. Here's a real-life example to explain the use of data analytics in healthcare:
Consider a hospital that wants to improve patient outcomes and reduce readmission rates for a specific medical condition, such as heart failure. By leveraging data analytics, the hospital can analyze various healthcare data sources, including electronic health records (EHRs), medical devices, and patient surveys, to gain valuable insights and make informed decisions.Predictive Analytics: Data analytics can be used to develop predictive models that identify patients at high risk of readmission.
To know more about data click the link below:
brainly.com/question/21927058
#SPJ11
can I run crisis remastered on max settings?
Answers
Yes....................................
28.1. why is it that software organizations often struggle when they embark on an effort to improve local software process
Answers
Software organization often struggles when they embark on an effort to improve local software process because they have little more than ad hoc.
What is a software organization?An organizational tool is a program or app designed to improve your daily task performance. You may come across a variety of tools, such as project management software, note-taking systems, notebooks, and day planners.
Therefore, because they have little more than ad hoc resources, software organizations frequently suffer when attempting to improve local software processes.
To learn more about software organization, refer to the link:
https://brainly.com/question/14483430
#SPJ1
suppose an isp owns the block of addresses of the form 128.119.40.64/26. suppose it wants to create four subnets from this block, with each block having the same number of ip addresses. what are the prefixes (of form a.b.c.d/x) for the four subnets?
Answers
To create four Subnets from the block of addresses of the form 128.119.40.64/26, the ISP would need to divide the address range evenly into four blocks, each with the same number of IP addresses.
The original block has 64 addresses, so each of the four subnets would need to have 16 addresses. To achieve this, the ISP would need to create four new prefix ranges of the form a.b.c.d/x.
To calculate the prefix for each new subnet, the ISP would need to borrow bits from the host portion of the original /26 subnet mask.
Starting with the original block of 128.119.40.64/26, the subnet mask is 255.255.255.192, which means there are 6 host bits available (since 2^6 = 64).
To create four subnets with 16 addresses each, we need 4 bits for the host portion of each subnet. So, we borrow 4 bits from the original 6, leaving 2 host bits for each subnet.
The new subnet mask for each of the four subnets is therefore 255.255.255.240, which means the prefix for each subnet is:
- 128.119.40.64/28
- 128.119.40.80/28
- 128.119.40.96/28
- 128.119.40.112/28
Each of these subnets has 16 addresses, and the ISP can now assign them as needed to its customers or internal network devices.
To Learn More About Subnets
https://brainly.com/question/29039092
#SPJ11
Hey can y’all help me with this thanks

Answers
Answer:The answer is 144
Explanation:First you subtract the two numbers which would be 8-2=6
Then you multiply the 6 by how many numbers there are: 6x2=12
then you multiply 12 by itself: 12x12=144
Which is non executable statement used to write some information.
Answers
Answer:
Programming command that is not run or executed when being read by the computer. For example, a commonly used nonexecutable statement is REM (remark) used in batch files and other Microsoft Windows and DOS programs.
Why are financial records important? How does keeping organized financial records contribute to successful money manageme?
Answers
Answer:
Financial records are very important for any organization. There are many reasons to keep records such as knowing financial situation, meeting tax obligations
Explanation:
Firstly is knowing the financial situation of the company which help to further contribute with organization.
Secondly organization meet the ta obligations assign by the government.
A ___ error means the web page you are trying to view isn't available, perhaps because the page has been deleted from the server.
601
404
500
Answers
Answer:
A 404
Explanation:
I've seen it many times.
Answer:
404
Explanation:
an array is not: group of answer choices a consecutive group of memory locations. none of the above. made up of different data types. subscripted by integers.
Answers
By using structures, sometimes referred to as structs, you can group together multiple related variables in one place.
A data arrangement that contains a group and collection of items is known as an array in the digital world. These components share a common data type that is more akin to an integer or string. In program computing, arrays are typically used to categorize and organize data such that sorting or searching for a related or equivalent group of values is simple. Each variable in the structure is referred to as a member of the structure. In contrast to an array, a structure can hold a variety of data types (int, string, bool, etc.). A structure is a solitary object that has logically connected variables of different data types. All of the data members of the structure are accessible to the functions declared outside of it.
Learn more about An array here:
https://brainly.com/question/15047582
#SPJ4
What is an example of a recent development in technology
Answers
Artificial Intelligence (AI) and Machine Learning. ...
Robotic Process Automation (RPA) ...
Edge Computing. ...
Quantum Computing. ...
Virtual Reality and Augmented Reality. ...
Blockchain. ...
Internet of Things (IoT) ...
5G.
Answer:
every day new things are made and different.
You have two identical print devices that are set up in a work room. Currently, the Windows print server has two printers configured-one for each print device. Some of your users have one printer configured on their computer and other users have the other printer configured. You have found that users are often waiting for their print job to start because another print job is running on the same print device while the other print device sits idle. You want to maximize usage of both printers and avoid having users wait. What should you configure
Answers
Since you want to maximize the usage of both identical print devices (printers) and avoid having users wait, you should configure: printer pooling.
A printer can be defined as an electronic output device that is typically designed and developed to be used for printing paper documents containing textual information and images.
In this scenario, you want the two (2) identical print devices (printers) to print concurrently, so as to prevent users from waiting for their print job to start while the other print device sits idle.
Hence, you should configure printer pooling on both print devices (printers) because this feature would allow the two (2) identical print devices (printers) to share the same name and function as a single printer.
In conclusion, load balancing of print jobs can be achieved by configuring printer pooling on two or more printers.
Read more: https://brainly.com/question/17100575
during a web application test, ben discovers that the application shows sql code as part of an error provided to application users. what should he note in his report?
Answers
Ben's discovery during the web application test is crucial. In his report, he should note the following:
1. Identified Issue: Ben should clearly state that the web application is displaying SQL code as part of an error message shown to users, which is a security concern.
2. Severity: He should emphasize the severity of this issue, as it exposes the application's underlying database structure and may potentially lead to SQL injection attacks.
3. Vulnerability: Mention that this issue is related to improper error handling and sensitive information exposure, which are common web application vulnerabilities.
4. Reproduction Steps: Ben should provide detailed steps on how to reproduce the issue, including the specific input or action that triggered the error message with SQL code.
5. Recommendation: He should recommend implementing proper error handling mechanisms to prevent sensitive information from being exposed to users. This could involve displaying generic error messages, logging errors internally, and notifying developers or administrators for further investigation.
6. Potential Risks: Lastly, Ben should highlight the potential risks associated with this issue, such as unauthorized access to sensitive data, manipulation of the database, or compromising the entire application.
By noting these key points in his report, Ben will help ensure that the developers understand the importance of addressing this vulnerability to protect the web application and its users.
For such more question on vulnerabilities
https://brainly.com/question/13138322
#SPJ11
Portable Document Format is a proprietary document file type created by Adobe Systems that is compatible with most computer systems.
a
DOC
b
XLS
c
PDF
d
GIF
e
JPG
f
PS
g
MP3
h
OGG
i
AVI
j
MPEG
Answers
Answer: PDF
Explanation:
Click to review the online content. Then answer the question(s) below. using complete sentences. Scroll down to view additional
questions.
Memory Matters
Explain the difference between occasional forgetfulness and Alzheimer's disease.
Answers
Answer:
The answer is below
Explanation:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.
Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.
Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Answer:
Alzheimer's disease is a progressive neurologic disorder which causes the brain to shrink (atrophy) and brain cells to die leading to memory loss and confusion.Occasional forgetfulness are usually age related that is it occurs in older people while Alzheimer's disease is a memory loss which is progressive (that means that it gets worse over time.Occasional forgetfulness is forgetting the position of some things while Alzheimer's disease involves Forgetting important information.
Explanation:
got 100% on edg
Write pseudocode to combine two integer arrays, array1 and array2. The elements of the second array should come after the elements of the first array.
Answers
Here is the pseudocode to combine two integer arrays, array1 and array2, with the elements of the second array coming after the elements of the first array:```
// Declare the arrays
array1 = [1, 2, 3, 4, 5]
array2 = [6, 7, 8, 9, 10]
// Get the lengths of the arrays
length1 = length of array1
length2 = length of array2
// Create a new array to store the combined elements
combinedArray = new array of length (length1 + length2)
// Copy the elements of array1 to the new array
for i from 1 to length1 do
combinedArray[i] = array1[i]
// Copy the elements of array2 to the new array
for j from 1 to length2 do
combinedArray[length1 + j] = array2[j]
To know more about pseudocode visit
https://brainly.com/question/30942798
#SPJ11
#3: Which combination of statements can be used to express algorithms?
A) Iterative, sequential, and selection
B) Correctness, efficiency, and clarity
C) Readable, iterative, and efficient
D) Selection, conditional, and Boolean
Answers
Answer:
A) Iterative, sequential, and selection
Explanation: