To what extent do you agree with the assertion that “Collection development begins with community analysis”. (Give reasons to buttress your answer).
Answers
The assertion that collection development starts with community analysis is logically correct.
The collection development policy is vital for setting goals for the collection that mirror the missions of the library. It gives information to the stakeholders of the library about how the collection will be chosen, and who will make the decisions regarding the collection.
Collection development starts with community analysis. The collection plan should follow a logical process in order to be effective. The community should be taken into consideration before the plan is carried out. The more one knows about the community, the better it'll be to make the collection plan effective.
Read related link on:
https://brainly.com/question/21529943
Related Questions
Referring to narrative section 6.4.1.1. "Orders Database" in your course's case narrative you will:
1. Utilizing Microsoft VISIO, you are to leverage the content within the prescribed narrative to develop an Entit
Relationship Diagram (ERD). Make use of the 'Crow's Foot Database Notation' template available within VISIC
1.1. You will be constructing the entities [Tables] found within the schemas associated with the first letter of
your last name.
Student Last Name
A-E
F-J
K-O
P-T
U-Z
1.2. Your ERD must include the following items:
All entities must be shown with their appropriate attributes and attribute values (variable type and
length where applicable)
All Primary keys and Foreign Keys must be properly marked
Differentiate between standard entities and intersection entities, utilize rounded corners on tables for
intersection tables
●
.
Schema
1 and 2 as identified in 6.4.1.1.
1 and 3 as identified in 6.4.1.1.
1 and 4 as identified in 6.4.1.1.
1 and 5 as identified in 6.4.1.1.
1 and 6 as identified in 6.4.1.1.
.
Answers
The following is a description of the entities and relationships in the ERD -
CustomersProductOrdersOrder Details How is this so?Customers is a standard entity that stores information about customers, such as their name, address,and phone number.Products is a standard entity that stores information about products, such as their name, description, and price.Orders is an intersection entity that stores information about orders, such as the customer who placed the order,the products that were ordered, andthe quantity of each product that was ordered.Order Details is an intersection entity that stores information about the details of each order,such as the order date, the shipping address, and the payment method.The relationships between the entities are as follows -
A Customer can place Orders.An Order can contain Products.A Product can be included inOrders.The primary keys and foreign keys are as follows -
The primary key for Customers is the Customer ID.The primary key for Products is the Product ID.The primary key for Orders is the Order ID.The foreign key for Orders is the Customer ID.The foreign key for Orders is theProduct ID.The foreign key for Order Details is the Order ID.The foreign key for Order Details is the Product IDLearn more about ERD at:
https://brainly.com/question/30391958
#SPJ1
which wireless technology connects with most mobile devices?
Answers
Answer:
¡) Internet
¡¡) Alexa
¡¡¡) Electronic Devices
The wireless technology that connects with most mobile devices is
Wi-Fi.
We have,
Wi-Fi is widely available and compatible with a vast range of smartphones, tablets, laptops, and other mobile devices, making it a popular choice for wireless connectivity.
Wi-Fi has become ubiquitous and widespread due to its convenience, flexibility, and high data transfer rates.
Most modern mobile devices come equipped with Wi-Fi capabilities, enabling users to connect to Wi-Fi networks and access the internet without the need for physical cables. It allows for seamless and reliable internet connectivity, enabling users to access online services, browse the web, stream media, send emails, and use various applications on their mobile devices while on the go or within the coverage area of a Wi-Fi network.
Thus,
The wireless technology that connects with most mobile devices is
Wi-Fi.
Learn mroe about wireless technologies here:
https://brainly.com/question/32338552
#SPJ3
jss 1 computer text book
Answers
Note that the generation of computers that used integrated Circuit are called the Second Generation computers. (Option B)
What about Second Generation computers?Throughout the late 1950s and 1960s, a second-generation computer had circuit boards loaded with individual transistors and magnetic-core memory.
These computers remained the standard design until the late 1960s, when integrated circuits appeared, resulting in the third-generation computer.
It was created in 1947 at Bell Labs by three people: William Shockley, Walter Houser Brattain, and John Bardeen.
Unlike the previous generation of computers, the second generation computers employed assembly language rather than binary machine language.
Learn more about second generation computers at:
https://brainly.com/question/31492021
#SPJ1
Full Question:
Which generation was used integrated Circuit?
answer choices
First Generation
Second Generation
Third Generation
Fourth Generation
Match the cell reference to its definition,
absolute reference
The cell has combination of two other types
of cell references.
relative reference
The cell remains constant when copied or
moved.
mixed reference
The cell changes based on the position of
rows and columns

Answers
Answer:
Absolute reference- the cell remains constant when copied or moved
Relative reference- the cell changes based on the position of rows and columns
Mixed references- the cell has combination of two other types of cell references
Explanation:
what is the difference of expository and reflexive documentary
Answers
What year was "scripting" first invented
Answers
Answer:
Late 1950's
Explanation:
I hope this helps, have a great day :)
In order to average together values that match two different conditions in different ranges, an excel user should use the ____ function.
Answers
Answer: Excel Average functions
Explanation: it gets the work done.
Answer:
excel average
Explanation:
What are Divine Laws? Explain the Golden Rule of Divine Laws. How Crime, Sin and Indiscipline are different from each other? Give examples of any State Law which is
(a) Similar to Divine Law (b) Opposite to Divine Law.
Answers
Answer:
Divine law comprises any body of law that is perceived as deriving from a transcendent source, such as the will of God or gods
Golden rule of Divine Laws:
Golden rule law is a modification of the literal rule. It states that if the literal rule produces an absurdity, then the court should look for another meaning of the words to avoid that absurd result.
The difference between sin and crime is that a sin is an opposed to god's will, and crime is opposed to the civil laws
HTML tag that makes a text field used by javascript statement
Answers
Which type of photographer documents plants and weather in their natural habitat?
a
Portrait
b
Nature
c
Product
d
Scientific
Answers
the variables xp and yp have both been declared as pointers to int, and have been assigned values. write the code to exchange the two int values pointed by xp and yp. (so that after the swap xp still points at the same location, but it now contains the int value originally contained in the location pointed to by yp; and vice versa-- in other words, in this exercise you are swapping the ints, not the pointers). Declare any necessary variables?
Answers
The int values pointed by xp and yp are swapped using a temporary variable as a placeholder. int temp;
temp = *xp;*xp = *yp;*yp = temp;In order to swap the int values pointed by xp and yp, a temporary variable is necessary to store the original value of *xp while the value of *yp is being assigned to *xp. The value stored in the temporary variable is then assigned to *yp, thus completing the swap. The code for this is as follows: int temp; temp = *xp; *xp = *yp; *yp = temp;
Learn more about programming: https://brainly.com/question/26134656
#SPJ4
Question #11
If A = 5 and B = 10, what is A* B equal to?
estion #2
estion # 3
restion #4
testion5
O 15
O Five
OTwo
O 50
Read Question
Answers
Answer:
Option 4: 50 is the correct answer.
Explanation:
Arithmetic operations can be performed using the programming languages. Some symbols used in programming languages are different from what we use in mathematics.
The symbol * is used to represent multiplication in programming languages.
Given
A = 5
B = 10
So, A*B will be equal to: 5*10 = 50
Hence,
Option 4: 50 is the correct answer.
PLEASE HELP
A program is designed to determine the minimum value in a list of positive numbers
called numlist. The following program was written
var minimum = MISSING CODE
for(var i = lo; i < numlist.length; i++){
if (numList[1] < minimum)
minimum = numList[1];
console.log("The minimum is" - minimum);
Which of the following can be used to replace ISSING CODE> so that the program works as intended for every possible list of positive numbers?

Answers
The missing code segment is meant to initialize the variable minimum to the first list element.
The missing code is (d) numList[0]
From the question, we understand that the first line of the program should determine the smallest number in the list numList
To do this, we start by initializing the variable minimum to the first element of numList
This is done using the following code segment:
var minimum = numList[0]
Hence, the missing code segment is (d) numList[0]
Read more about similar programs at:
https://brainly.com/question/19484224
30pts! PLEASE ANSWER FAST-BRAINLIEST WILL BE MARKED
the footer is a number and is used in checking to be sure the _____ has not changed
Answers
the footer is a number and is used in checking to be sure the bottom margin of each page has not changed
due to the success of your remote access solution, you now have several remote access servers on your network. to centralize administration of network policies, you need to configure the corpnps server as a radius server.
Answers
The CORPNPS server must first be configured as a RADIUS
Describe how to set up the Corpnps server to act as a Radius server?Install and set up the NPS Server first. On a Windows server, install and set up the NPS Server. Set the appropriate authentication protocols and settings on the NPS Server.Set up the servers for remote access. Set up the remote access servers to need NPS Server authentication. Configure the appropriate authentication settings and protocols.Set up the NPS server settings. Set the NPS Server up to enforce network regulations, including encryption options, authentication procedures, and other security settings.Check and validate the setup. By logging into the remote access servers with the configured authentication methods, you can test and validate the configuration. Check to see if the network policies are being correctly applied.To learn more about The CORPNPS server must first be configured as a RADIUS refer to:
https://brainly.com/question/15289808
#SPJ4
what subject can you find in the house?
Answers
In a house, you can find various subjects or objects related to different areas of knowledge. Some common subjects that you can find in a house include:
Architecture and Design: The structure and layout of the house itself, including the architectural design, interior design elements, and spatial arrangement.
Construction and Engineering: The materials used in building the house, construction techniques, plumbing and electrical systems, and other engineering aspects.
Home Economics: The study of managing and maintaining a household, including topics such as cooking, cleaning, laundry, budgeting, and home organization.
Interior Decoration: The art and science of decorating and arranging the interior spaces of a house, including furniture, color schemes, artwork, and accessories.
Thus, there are so many subjects that can be found at home.
For more details regarding subjects, visit:
https://brainly.com/question/3541306
#SPJ1
how has State-terrorism done for us and how we can prepare for it?
Answers
Answer:
Developing a plan that prepares not just one family but their whole community.
Explanation:
I think a great way to prepare for state-terrorism is by developing a disaster awareness plan. An event that hosts first-responders, medics, policemen, etc. To speak over these circumstances in the event, there are many possibilities with a disaster awareness event, activities for the younger ages that teach kids to be "prepared not scared" this event can go a lot farther than state-terroism a step further would be to prepare people for natural disasters that can occur, and the ways to prepare for this.
Part 3 (The stunner)


Answers
Answer:
nice :)
Explanation:
Answer: Once again, levers where we cant see.
Write a function (getResults) that returns the Fahrenheit equivalents of Celsius temperatures. The function will have the Celsius as the parameter.
The formula for converting a temperature from Celsius to Fahrenheit is
F = 9C + 32
5
F
where F is the Fahrenheit temperature, and C is the Celsius temperature.
Your function returns the Fahrenheit equivalent. (Python)

Answers
Here's a Python function that converts a temperature from Celsius to Fahrenheit using the formula F = 9/5 * C + 32:
The Python Codedef getResults(celsius):
fahrenheit = (9/5 * celsius) + 32
return fahrenheit
You can call this function with a Celsius temperature to get the Fahrenheit equivalent:
>>> getResults(0)
32.0
>>> getResults(100)
212.0
>>> getResults(-40)
-40.0
Note that the function assumes that the input temperature is in Celsius. If you pass in a temperature in Fahrenheit, the result will be incorrect.
Read more about python programming here:
https://brainly.com/question/26497128
#SPJ1
Discuss the important role of remote sensing application in agriculture. Do you think that the use of remote sensing is applicable in the Philippines scenario? Why? Give some of the pros and cons of remote sensing.
Answers
Answer:
Remote sensing gives the soil moisture data and helps in determining the quantity of moisture in the soil and hence the type of crop that can be grown in the soil. ... Through remote sensing, farmers can tell where water resources are available for use over a given land and whether the resources are adequate.
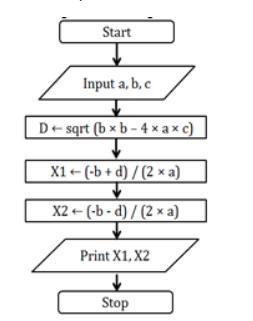
1 Design a flowchart to compute the following selection
(1) Area of a circle
(2) Simple interest
(3) Quadratic roots an
(4) Welcome to INTRODUCTION TO COMPUTER PROGRAMM INSTRUCTION
Answers
A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes.
What is a flowchart?A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes. Flowcharts exist utilized to learn, enhance and communicate strategies in different fields.
Step Form Algorithm:
Start.
Declare the required variables.
Indicate the user to enter the coefficients of the quadratic equation by displaying suitable sentences using the printf() function.
Wait using the scanf() function for the user to enter the input.
Calculate the roots of the quadratic equation using the proper formulae.
Display the result.
Wait for the user to press a key using the getch() function.
Stop.989
Pseudo Code Algorithm:
Start.
Input a, b, c.
D ← sqrt (b × b – 4 × a × c).
X1 ← (-b + d) / (2 × a).
X2 ← (-b - d) / (2 × a).
Print x1, x2.
Stop.
Flowchart:
A flowchart to calculate the roots of a quadratic equation exists shown below:
import math
days_driven = int(input("Days driven: "))
while True:
code = input("Choose B for class B, C for class C,D for class D, or Q to Quit: ")
# for class D
if code[0].lower() == "d":
print("You chose Class D")
if days_driven >=8 and days_driven <=27:
amount_due = 276 + (43* (days_driven - 7))
elif days_driven >=28 and days_driven <=60:
amount_due = 1136 + (38*(days_driven - 28))
else:
print("Class D cannot be rented for less than 7 days")
print('amount due is $', amount_due)
break
elif code[0].lower() == "c":
print("You chose class C")
if days_driven \gt= 1 and days_driven\lt=6:
amount_due = 34 * days_driven
elif days_driven \gt= 7 and days_driven \lt=27:
amount_due = 204 + ((days_driven-7)*31)
elif days_driven \gt=28 and days_driven \lt= 60:
amount_due = 810 + ((days_driven-28)*28)
print('amount due is $', amount_due)
# for class b
elif code[0].lower() == "b":
print("You chose class B")
if days_driven >1 and days_driven<=6:
amount_due = 27 * days_driven
elif days_driven >= 7 and days_driven <=27:
amount_due = 162 + ((days_driven-7)*25)
elif days_driven >=28 and days_driven <= 60:
amount_due = 662 + ((days_driven-28)*23)
print('amount due is $', amount_due)
break
elif code[0].lower() == "q":
print("You chose Quit!")
break
else:
print("You must choose between b,c,d, and q")
continue
To learn more about computer programs refer to:
https://brainly.com/question/21612382
#SPJ9
Help me with this digital Circuit please




Answers
A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Thus, These circuits receive input signals in digital form, which are expressed in binary form as 0s and 1s. Logical gates that carry out logical operations, including as AND, OR, NOT, NANAD, NOR, and XOR gates, are used in the construction of these circuits.
This format enables the circuit to change between states for exact output. The fundamental purpose of digital circuit systems is to address the shortcomings of analog systems, which are slower and may produce inaccurate output data.
On a single integrated circuit (IC), a number of logic gates are used to create a digital circuit. Any digital circuit's input consists of "0's" and "1's" in binary form. After processing raw digital data, a precise value is produced.
Thus, A subset of electronics called digital circuits or digital electronics uses digital signals to carry out a variety of tasks and satisfy a range of needs.
Learn more about Digital circuit, refer to the link:
https://brainly.com/question/24628790
#SPJ1
Which of the following is not a characteristic of a good value log entry
Answers
Organizations that primarily compete on speed of delivery , such as FedEx and UPS , utilize which of the following approaches for location determination : a. Sourcing center b. Hub and spoke c. Air and ground d. LTL consolidation
Answers
Answer: Hub and spoke
To safeguard against losses of computer equipment and important information, businesses should have _____. Select 4 options.
disaster recovery plans
natural disaster plans
emergency response readiness
business continuity plans
intrusion detection systems
Answers
Answer:
A. disaster recovery plans
D. business continuity plans
C. emergency response readiness
E. intrusion detection systems
Explanation:
lmk if im correct
To safeguard against losses of computer equipment, one should have;
Intrusion detection systems.Business continuity plans.Emergency response readiness.What safeguards should computers have?There are a lot of ways to keep your computer equipment and important information, from been stolen, They include:
The use a surge protector. The use of Anti-Virus Programs, etc.Hence, when you use the various methods above, one can be protected in case of loss or against loss.
Learn more about computer equipment from
https://brainly.com/question/23275071
Which of the following would be considered unethical for a programmer to do? (5 points)
Create software used to protect users from identity theft
Ignore errors in programming code that could cause security issues
Protect users from unauthorized access to their personal information
Use someone else's code with the original developer's permission
Answers
One thing that would be onsidered unethical for a programmer to do is B. Ignore errors in programming code that could cause security issues
Why would this be unethical for a programmer ?Creating software designed to protect users from identity theft stands as a commendable and ethical endeavor, demonstrating the programmer's commitment to safeguarding user information and thwarting identity theft.
Engaging in such behavior would be considered unethical since it undermines the security and integrity of the software, potentially exposing users to vulnerabilities and compromising their sensitive data. Respecting intellectual property rights and obtaining proper authorization reflects adherence to ethical and legal standards.
Find out more on programmers at https://brainly.com/question/13341308
#SPJ1
DONT NEED HELL just showing correct results for future students :)
Use the drop-down menus to complete the steps for adding conditional formatting to a form. 1. Locate the switchboard in the navigation pane under Forms. 2. Open the switchboard in [Design ]view. 3. The conditional tab Form Design Tools will open 4. To edit the font, color, or image, click the conditional tab [ Format]. 5. Make all desired changes using [drop-down menus] the Control Formatting command group 6. Save and close. 7. Reopen in [ Form ] view to see the changes.

Answers
The steps on how complete the steps for adding conditional formatting to a form.
How to do conditional formatting to a form. Locate the switchboard in the navigation pane under Forms.Open the switchboard in Design view.The conditional formatting tab, Form Design Tools, will open.To edit the font, color, or image, click the conditional formatting tab, Format.Make all desired changes using the drop-down menus in the Control Formatting command group.Save and close the switchboard.Reopen the switchboard in Form view to see the changes reflected.Read more on conditional formatting https://brainly.com/question/25051360
#SPJ1
Use the drop-down menus to explain how to personalize a letter.
1. Place the cursor where the name and address should appear.
2. Select
v in the mail merge wizard.
3. Select the name and address format and
if needed to link the correct data to the field.
4. Place the cursor below the address block, and select
from the mail merge wizard.
5. Select the greeting line format and click
Answers
Explanation:
Address block
Match Fields
Greeting Line
Ok
Place the cursor where the name and address should appear: This step is important as it identifies the exact location where the personalized information should be placed in the letter.
What is personalization?Personalization refers to the process of customizing a communication, such as a letter or email, to make it more individualized and relevant to the recipient.
To explain how to personalize a letter:
Place the cursor where you want the name and address to appear: This step is critical because it determines where the personalised information should be placed in the letter.
In the mail merge wizard, enter v: This step involves selecting the mail merge feature in the word processor software. The mail merge feature is typically represented by the "v" symbol.
Choose the name and address format, and then [link] to link the correct data to the field: This step entails selecting the appropriate name and address format, such as "First Name," "Last Name," and "Address Line 1." It also entails connecting the data source (for example, a spreadsheet or database) to the relevant fields in the letter.
Place the cursor below the address block and use the mail merge wizard to select [Insert Greeting Line]: This step involves deciding where to place the greeting line in the letter, which is usually below the address block. The mail merge wizard offers formatting options for the greeting line based on the data source.
Choose the greeting line format and press [OK]: This step entails deciding on a greeting line format, such as "Dear [First Name]" or "Hello [Full Name]." Once the format is chosen, the user can finish personalising the letter by clicking "OK."
Thus, this can be concluded regarding the given scenario.
For more details regarding personalization, visit:
https://brainly.com/question/14514150
#SPJ2
What are the reasons why organizations opt for a certificate
issued by third party commercial certification authorities to
secure their web server? [Choose two that applyl.
To secure browsing of social media sites.
To secure data transfer, transactions and logins to the
website.
To securely redirect a customer to a third party
a
website.
lling
To run a trusted web site that conduct business with
the general public.
Answers
The reasons that organizations opt for a certificate issued by third party commercial certification authorities to secure their web server are option B and D:
To secure data transfer, transactions and logins to the website.To run a trusted web site that conduct business with the general public.What Is a Certification Authority?A certificate authority is a third-party organization that operating systems and web browsers trust to generate and distribute digital certificates.
However, they must perform this task for businesses and websites that they have vetted, which is why CAs are crucial to modern digital security (and internet security). These certificates are essentially short data files with verified organization identification information.
What we now usually refer to as a certificate authority or a CA was originally known as a "certification authority." Therefore, you may occasionally encounter them referred to by these many names.
Therefore, When a product is third-party certified, it signifies that an independent body has examined the product's production process and has independently found that the final product complies with certain safety criteria.
Learn more about certification authorities from
https://brainly.com/question/17011621
#SPJ1
what is cyber security ???
Answers
Answer:
Cyber security is the practice if defending computers,servers,mobile devices,electronic systems, networks, and data from malicious attacks