true or false? the marketing hub uses shared contact information with the sales hub and service hub via the crm contacts database. true false
Answers
A method that focuses on utilizing a software program to conveniently store and source a contact's information, including their name, contact history, email address, and more
The source of a visitor is determined by HubSpot in what ways?
HubSpot places tracking cookies in users' browsers when they arrive on your site, where it monitors their activity and recognizes them as a distinct visitor. HubSpot can update the source property values of your contacts by using these tracking cookies.
The purpose of a sales hub
With all of your tools and data in one simple-to-use, robust CRM platform that your entire team adores, Sales Hub accelerates your sales process and reduces friction. You are now free to concentrate on your clients, who are what actually matters.
To know more about HubSpot visit;
https://brainly.com/question/29488459
#SPJ4
Related Questions
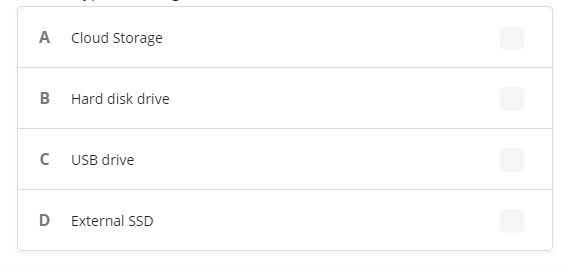
Joshua needs to store all of his music (over 2 GB), his movies (4GB), and his pictures (1GB). He wants to be able to access his media wherever he goes. He needs a cheap storage solution. Which type of storage would be best for Joshua?
Answers
Answer:Cloud storage
Explanation:I think that the cloud storage would be his best choice, because there are free cloud storages for use and all you need is access to the internet to upload or download files from them.
What is the output of the following code:
list1 = [ 'cyber', 786 , 2.23, 'square', 70.2 ]
print (list1[1] )
Answers
786
Explanation:In Python, and of course many other programming languages, lists are one of the built-in data types used to store several items in a variable.
In creating a list, the items, which may be of different types (e.g integer, float, string e.t.c), are placed in a square bracket and each item is separated from the other by a comma. The following are an example of a list.
myList = ["fish", "meat", 5, 8, "egg"]
scores = [10, 34, 78, 90]
To access or retrieve an item in a list, the index of that item is used. Indexes start from 0. For example, in myList the first item (which is fish) has an index of 0. The second item (which is meat) has an index of 1 and so on. In scores, the first item (which is 10) has an index of 0, 34 has an index of 1, 78 has an index of 2 and so on.
Now;
i. to access the first item in myList, we simply write: myList[0]. This will give fish
ii. to access the third element in scores, we simply write: scores[2]. This will give 78
From the list given in the question which is:
list1 = [ 'cyber', 786 , 2.23, 'square', 70.2 ]
print(list1[1]) will print the item at index 1 which is 786.
Therefore, the output of the code is 786
The String otherObjects() method relies on the ____________.
a) name.indexOf() method
b) name.equals() method
c) name.compareTo() method
d) name.length()
Answers
Think of a binary communication channel. It carries two types of signals denoted as 0 and 1. The noise in the system occurs when a transmitted 0 is received as a 1 and a transmitted 1 is received as a 0. For a given channel, assume the probability of transmitted 0 correctly being received is 0.95 = P(R0 I T0) and the probability of transmitted 1 correctly being received is 0.90 = P(R1 I T1). Also, the probability of transmitting a 0 is 0.45= P(T0). If a signal is sent, determine the
a. Probability that a 1 is received, P(R1)
b. Probability that a 0 is received, P(R0)
c. Probability that a 1 was transmitted given that a 1 was received
d. Probability that a 0 was transmitted given that a 0 was received
e. Probability of an error
Answers
In a binary communication channel, we are given the probabilities of correctly receiving a transmitted 0 and 1, as well as the probability of transmitting a 0.
a. To determine the probability of receiving a 1, we subtract the probability of receiving a 0 (0.45) from 1, resulting in P(R1) = 1 - P(R0) = 1 - 0.45 = 0.55.
b. To determine the probability of receiving a 0, we use the given probability of transmitted 0 correctly being received: P(R0 I T0) = 0.95. Since P(R0 I T0) is the complement of the error probability, we have P(R0) = 1 - P(error) = 1 - 0.05 = 0.55.
c. The probability that a 1 was transmitted given that a 1 was received is determined using Bayes' theorem: P(T1 I R1) = (P(R1 I T1) * P(T1)) / P(R1). Substituting the given values, we have P(T1 I R1) = (0.9 * 0.55) / 0.55 = 0.9.
d. Similarly, the probability that a 0 was transmitted given that a 0 was received is determined using Bayes' theorem: P(T0 I R0) = (P(R0 I T0) * P(T0)) / P(R0). Substituting the given values, we have P(T0 I R0) = (0.95 * 0.45) / 0.55 = 0.8936 (approximately).
e. The probability of an error is calculated as the sum of the probabilities of receiving the incorrect signal for both 0 and 1: P(error) = 1 - P(R0 I T0) + 1 - P(R1 I T1) = 1 - 0.95 + 1 - 0.9 = 0.05 + 0.1 = 0.1564 (approximately).
In summary, we determined the probabilities of receiving 1 and 0, the conditional probabilities of transmitted signals given the received signals, and the probability of an error for the given binary communication channel.
Learn more about Probability
brainly.com/question/31828911
#SPJ11
metadata is data about data. what kinds of information can metadata offer about a particular dataset? select all that apply
Answers
Metadata can offer a range of information about a particular dataset, such as its origin, purpose, date created/modified, author, license, format, size, and any other relevant information.
What is metadata?Metadata is data that describes other data. It provides information about a specific item's content such as its title, author, date of creation, and type of media. Metadata can be used to describe any type of digital content, including images, videos, audio, text documents, webpages, and more. Metadata can be stored and organized in databases, making it easy to search and find items. It can also be used to help organize content, provide context and information about the content, and give access rights to specific users. Metadata also helps to improve search engine optimization and can be used to direct users to certain content. In short, metadata makes it easier to find, access, and manage digital content.
To learn more about metadata
https://brainly.com/question/24920518
#SPJ4
Constance wants to run the spelling feature to check all her worksheet at once. Place the steps in order from first to last.
Answers
Answer:
1.highlight to select the cells
2.click the review tab
3.clock spelling
Explanation:
just did it
Consider the following code segment:
ArrayList scales = new ArrayList ();
scales.add("DO");
scales.add("RE");
scales.add("MI");
scales.add("FA");
scales.add("SO");
String swap = scales.get(2);
scales.remove(2);
String set = scales.remove(scales.size()-1);
scales.add(scales.get(0));
scales.set(0,set);
scales.add(scales.size()/2, swap);
Which of the following represents the value of scales after the code has been executed?
[SO, RE, FA, DO]
[SO, RE, MI, FA, DO]
[SO, RE, MI, DO]
[FA, RE, MI, DO]
[FA, SO, RE, MI, DO]
Answers
The scales value after code execution will be [FA, SO, RE, MI, DO].
How to Perform Scale Programming?The scale schedule must be used for a predetermined period (temporary), as it will not generate an event for eSocial.
To include it, access the menu: Schedules/ Schedule Schedules.
Example: If an employee makes the 0002 scale, it can be informed that in a certain period he will make the 0003 scale. And at the end of this period, the system will consider the Contract's initial scale again.Scheduling can be done individually or collectively. It can also be in a single day or in a range of days.
Learn more about code execution in https://brainly.com/question/16698901
Answer:
[SO, RE, MI, FA, DO]
Explanation:

On the Internet, there is incredible access to information of all sorts. This can be classified as what kind of impact
Answers
The impact of the incredible access to information of all sorts that can be classified as positive.
There is no doubt that the Internet has revolutionized the way that people live their lives. It has made it easier to stay in touch with friends and family members, learn new things, find employment opportunities, and much more.One of the most significant impacts of the Internet is that it has made it easier than ever before for people to access information of all sorts.
This includes everything from news stories to academic research to entertainment content, and much more. This is a positive impact because it means that people are able to learn more about the world around them and stay up-to-date with the latest developments in their fields of interest.In conclusion, the incredible access to information of all sorts on the internet has a positive impact.
To know more about incredible access visit :
https://brainly.com/question/31358236
#SPJ11
Which of the following is a necessary step prior to replacing the removable battery pack in a laptop computer?
a. Remove the laptop keyboard bezel, and if needed, remove the keyboard.
b. Verify the computer system is configured in sleep mode.
c. Verify the laptop system is powered off and configured for Ship Mode.
d. Confirm the replacement battery is recommended by the laptop manufacturer.
Answers
Answer:
number c is the correct answer
two uses of hexadecimal
Answers
Answer:
it allows you to store more information using less space. It is fast and simple to convert between hexadecimal numbers and binary.
Explanation: Hexadecimal can be used to write large binary numbers in just a few digits. It makes life easier as it allows grouping of binary numbers which makes it easier to read, write and understand.
_______ is extremely fast data transmission delivered through a wireless local area network.
Answers
Wi-Fi is extremely fast data transmission delivered through a wireless local area network.
WiFi allows for extremely fast data transmission through a wireless local area network. It is a popular technology used in homes, offices, and public spaces to provide internet connectivity without the need for physical cables.
WiFi allows multiple devices to connect to the network simultaneously and enables users to stream high-definition videos, play online games, and browse the internet with ease.
With advancements in WiFi technology, speeds have increased, and coverage has expanded, making it more reliable and accessible than ever before.
Learn more about wireless at https://brainly.com/question/30557441
#SPJ11
Security personnel, whose post is located outside the entrance to an alcohol establishment, has the primary responsibility to control the number of patrons entering and to check their IDs. Does the bouncer need to be certified
Answers
You were fortunate to get the ice off of the wings, but whatever caused the cabin to depressurize also vented all of your fuel overboard. You are now a big gilder and are going to have to land in Lake Michigan. You need to slow down to minimize the impact, but you don’t want to stall.
What device can you use to help and how do they work?
Answers
Answer:
A speed govenor
Explanation:
speed governor is an electronic device linked to the gearbox where sensors capture the movement of the vehicle. If the vehicle exceeds the specified speed limit, the device automatically slows the vehicle.
Is the use of networks or the internet to carry out business of any type.
Answers
Explanation:
Personal Area Network.because for some network like Home Area Network the difference from each
Yes, the use of networks or the internet to carry out business of any type is called e-commerce or electronic commerce.
E-commerce refers to the buying, selling, and exchanging of goods or services using electronic platforms, such as websites and mobile applications. It has revolutionized the way businesses operate, enabling them to reach a wider audience, streamline operations, and enhance communication.
Step 1: Businesses create an online presence through websites, social media, and email marketing to reach potential customers. This allows them to showcase their products or services and engage with their target audience.
Step 2: Secure payment gateways are integrated into e-commerce platforms, enabling customers to make transactions easily and safely. This process also includes the use of digital wallets and various payment options like credit cards, debit cards, and online banking.
Step 3: Online order management systems are used to track and manage customer orders, ensuring timely and accurate deliveries. This includes processing customer information, managing inventory, and coordinating with logistics partners.
Step 4: Customer relationship management (CRM) tools are utilized to improve customer satisfaction and maintain long-term relationships. This involves offering customer support, addressing queries, and providing personalized experiences.
Step 5: E-commerce businesses use digital marketing strategies, such as search engine optimization (SEO), pay-per-click (PPC) advertising, and content marketing to promote their products or services and drive traffic to their online platforms.
Step 6: Analyzing data collected from online interactions helps businesses understand customer behavior, preferences, and trends, allowing them to make informed decisions and improve their offerings.
In conclusion, e-commerce is a convenient and efficient method for conducting business, benefiting both consumers and businesses through its ease of use, accessibility, and versatility.
Know more about the E-commerce click here:
https://brainly.com/question/30268188
#SPJ11
Write a subroutine that computes the following expression: F=a ! + 2*b ! by Pascal
Answers
Here is a Pascal subroutine that computes the expression F = a! + 2*b!: Define a function to compute the factorial of a number. Use the defined function to compute the expression.
This Pascal subroutine takes in two integers a and b and a variable F by reference. It computes the expression F = a! + 2*b! using loops to calculate the factorials of a and b, then adding them together with the appropriate multiplication.
To compute the factorial of a number, we start with 1 and multiply by every number from 1 to the input number. We do this using a for loop, where the loop variable i starts at 1 and goes up to the input number. Once we have calculated the factorials of a and b, we simply add them together with the appropriate multiplication to get the final value of F.
The `factorial` function calculates the factorial of a given integer `n`. The `compute_expression` procedure takes two integer inputs `a` and `b`, calculates the expression F = a! + 2 * b! using the `factorial` function, and stores the result in the variable `F`.
To know more about subroutine visit:
https://brainly.com/question/29854384
#SPJ11
9.6 Code Practice
Instructions
1
Declare a 4x 5 array called N
Please helppp
Answers
Answer:
See Explanation
Explanation:
The question lacks so many details, as the array type and the programming language is not stated.
Assume that, it is Java:
The rule to follow is:
Data-Type[][]Array-Name = new Data-type[rows][columns]
If the given information is for an array of type integer, the code will be;
int[][] N = new int[4][5]
Where
N = Array-Name
int = Data-type
4 and 5 are the dimensions of the array
There are many different types of decision-making. Which of the following is NOT a type of decision-making? a. fiat rule b. single decision-maker c. majority rule d. consensus/collaboration
Answers
Answer:
These are all correct but if you want to get technical I would choose A, because fiat rule is used in the military without any consent from any political standpoint.
Explanation:
Answer:
the answer is A
Explanation:
Edhesive code practice 4.8 Question 3
Answers
Answer:
for i in range(200,301,2):
print(i)
Explanation:
just copy and paste 100 percent
Assignment 4 divisible by 3 in project stem
Please help fast!

Answers
Using the knowledge of the computational language in python it is possible to write a code that print a list of the first 100 numbers wich is divide by 3 and 5 and not 7.
Writting the code:# create an empty list to store the numbers
numbers = []
# set n to start number 1
n = 1
# loop until the list contains 100 numbers
while len(numbers) < 100:
# current value of n is divisible by 3 and 5 but not divisible by 7, append n to numbers list
if n%3 == 0 and n%5 == 0 and n%7 != 0:
numbers.append(n)
n += 1 # increment n by 1
# display the numbers list
print("List of first 100 numbers divisible by 3 and 5, but not by 7:\n",numbers)
# end of program
See more about python at brainly.com/question/18502436
#SPJ1

Write a single shell script which uses grep to get the following information from judgeHSPC05.txt:
How many lines start with a period (.) followed by an asterisk (*)?
Answers
To write a shell script that uses grep to count the number of lines starting with a period (.) followed by an asterisk (*) in the file judgeHSPC05.txt, follow these steps:
1. Create a new shell script file, e.g., count_lines.sh, and open it in a text editor.
2. Add the following line to the script:
```bash
grep -c '^\.\*' judgeHSPC05.txt
```
This command uses grep to search for lines that start with a period (.) followed by an asterisk (*) in judgeHSPC05.txt. The `^` indicates the start of a line, the `\.` matches a period (escaped with a backslash because a period has a special meaning in regular expressions), and the `\*` matches an asterisk (also escaped with a backslash). The `-c` flag tells grep to output the count of matching lines.
3. Save and close the script file.
4. Make the script executable by running:
```bash
chmod +x count_lines.sh
```
5. Run the script:
```bash
./count_lines.sh
```
Learn more about grep here:
https://brainly.com/question/31256733
#SPJ11
the information systems operations group is responsible for the day-to-day running of is hardware to process the organization’s information systems workload.
a. True
b. False
Answers
The given statement "the information systems operations group is responsible for the day-to-day running of is hardware to process the organization’s information systems workload" is true.
This means that option a is the correct answer.Workload:The workloads are used to refer to the amount of work assigned to a computer, server, or a group of computers. It is defined as the amount of processing that a computer has been assigned to do.Information Systems Operations:The IS operations (Information Systems Operations) group is responsible for the day-to-day running of hardware to process an organization's information systems workload.
It is responsible for the administration and operation of an organization's computer systems. It plays a crucial role in the development of information systems. It is also responsible for ensuring that the information system is in good working condition, efficient, and secure.
It is important to note that the information systems operations group is responsible for the maintenance of hardware and ensuring that all systems are running effectively and efficiently. They are responsible for the day-to-day running of the hardware that processes the organization's workload.
To learn more about hardware:
https://brainly.com/question/32810334
#SPJ11
a(n) ____ in a sql command instructs oracle 12c to use a substituted value in place of the variable at the time the command is actually executed.
Answers
A bind variable in a SQL command instructs Oracle 12c to use a substituted value in place of the variable when the command is executed.
It is a placeholder in a SQL statement where a data value is expected to be substituted. Bind variables are used to pass data into a SQL statement in a secure and efficient manner.
A bind variable is a parameterized SQL statement element. Bind variables are utilized in SQL commands to replace data with literal values. They assist to keep your query safe, as data injection attacks can't occur, and they assist to improve query performance.
Learn more about SQL commands at
https://brainly.com/question/32924871
#SPJ11
What causes electrical interference?
A. Radio frequencies
B. Mic placement
C. Multiple signal wave forms interacting
D. Crossed cables

Answers
Answer:Radio Frequencies
Explanation: This is because electrical interference is caused by another electric device.
A bicycle moves forward 4.0 m when the pedals are rotated through a distance of 1.0 m. What is the IMA (Ideal mechanical advantage) of this bicycle?
Answers
Answer:
IMA = 0.25
Explanation:
Given the following data;
Input distance = 1m
Output distance = 4m
To find the ideal mechanical advantage;
Mathematically, IMA is given by the formula;
\( IMA = \frac {distance \; over \; which \; the \; effort \; is \; applied}{distance \; the \; load \; travels} \)
NB: The ideal mechanical advantage has no units.
Substituting into the equation, we have;
\( IMA = \frac {1}{4}\)
IMA = 0.25
Therefore, the ideal mechanical advantage (IMA) of this bicycle is 0.25.
what is the best combos for Nix in Brawlhalla (PS4)?
Answers
Answer:
sycthe is simple. Do down light and then turn them around. Then do chase dodge to neutral air. its an infinite combo
Explanation:
which of the following is a limitation of a dmz? (5 points) a dmz has no power after a trojan enters the network. a dmz can only monitor a web server. a dmz will completely protect a network. a dmz can only monitor one computer at a time.
Answers
A DMZ makes it possible for external clients to access information on secure systems, like web servers, without jeopardizing the integrity of the inside network's security.
What on the Mcq network is a DMZ?A demilitarized zone (DMZ) is a physical or logical subnet in computer networks that isolates a local area network (LAN) from other untrusted networks, typically the public internet.
Why is a DMZ typically used?DMZs are a crucial component of network security for both small businesses and enormous corporations. By prohibiting remote access to internal servers and information, which can be seriously harmful if compromised, they add an extra degree of security to the computer network.
To know more about limitation dmz visit:-
https://brainly.com/question/12539419
#SPJ4
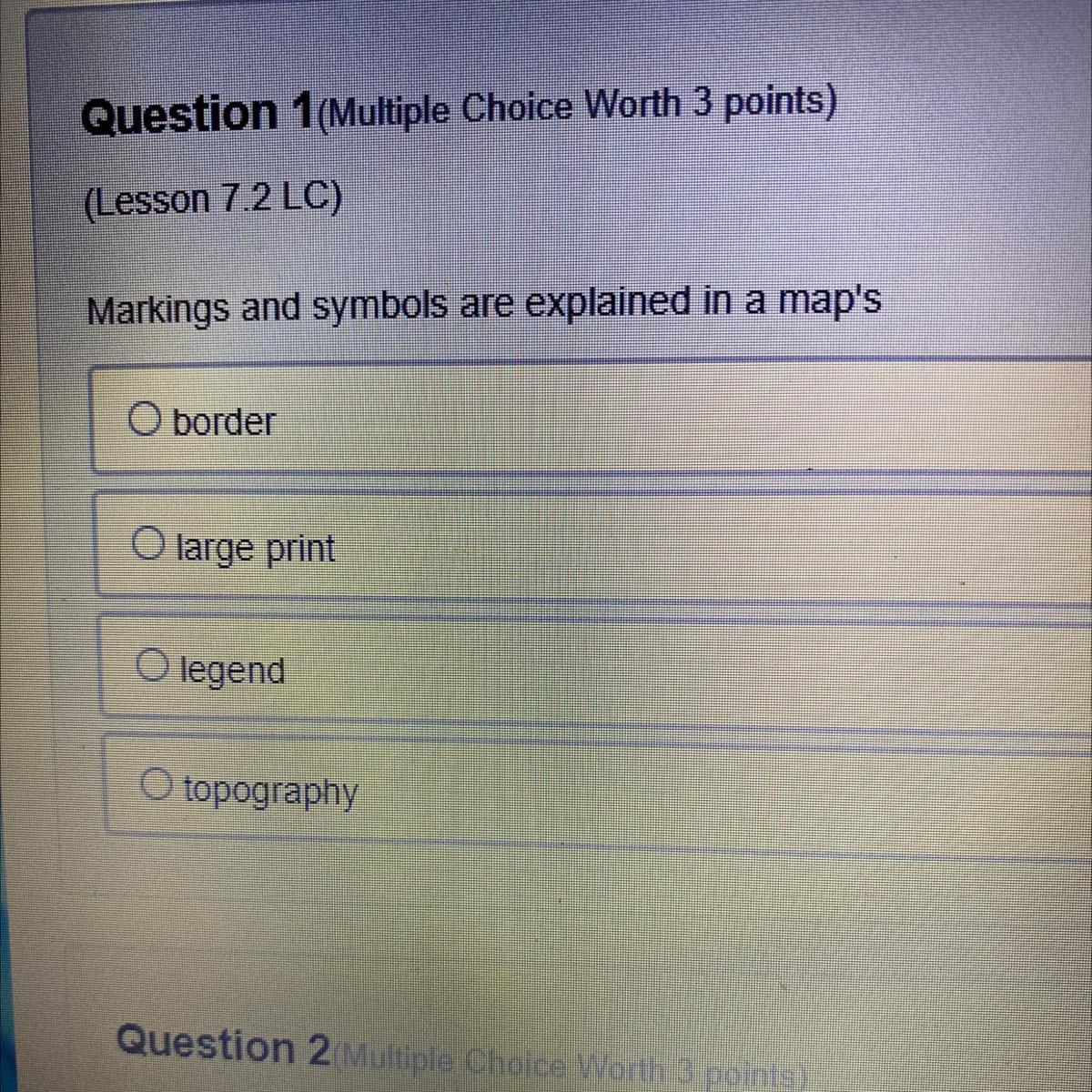
Helppppp meeeeee eee
Answers
Answer:
Option C is correct
Explanation:
A map legend or key is a visual explanation of the symbols used on the map. It typically includes a sample of each symbol (point, line, or area), and a short description of what the symbol means.
The process by which the raw data are transformed into new variables that have a mean of 0 and variance of 1 is called?
Answers
The process by which the raw data are transformed into new variables that have a mean of 0 and variance of 1 is called standardization.
Standardization is a statistical method for transforming a variable in a dataset into a standard scale.
It transforms the values of a variable such that the new transformed values have a mean of zero and a standard deviation of 1. Standardization can be applied to a single variable or an entire dataset and is useful when comparing variables that have different units or scales.
Learn more about database at:
https://brainly.com/question/31798452
#SPJ11
A capability list for a domain is ____________________ A. a list of operations together with the list of processes allowed to run the operations on those objects. B. a list of objects together with the list of processes allowed to access those objects. C. a list of objects together with the operations allowed on those objects. D. a list of triplet .
Answers
Answer:
a list of objects together with the operations allowed on those objects.
Need answer Asap!!!! Which file type is the best choice if the image will be made into a billboard?
Answers
Answer:
A .psd file
Explanation:
Adobe photoshop files are always going to be same and there is no compression. Even better .ai files are saved into equations so you can't alter or dumb it down.