Unic Research and Find out two ways each in which
Programming language and used Form
& Scientific Application
A
Buisness
8
Application
Answers
The Scientific Applications are :
Data AnalysisSimulation and ModelingBusiness Applications:
Web DevelopmentData Management and AnalysisWhat is the Programming language?Data Analysis: Python, R, and MATLAB are used in research for statistical analysis, visualization, and modeling. Scientists use programming languages for data processing, analysis, calculations, insights, simulations, and modeling.
Web Development: HTML, CSS, and JavaScript are used to create websites and web apps. HTML provides structure, CSS styles, and JavaScript adds interaction.
Learn more about Programming language from
https://brainly.com/question/16936315
#SPJ1
Related Questions
When can design templates be applied to the presentation?
when you start
when you add a new slide
before you close the program
all of the above
none of the above
[ DO NOT REPLY FOR POINTS YOU WILL BE REPORTED ]
(one answer) (edgenuitу)
Answers
Another PowerPoint question? I got you!
B. When you add a new slideApplying a design template can be applied when you have a slide. You can't apply one without a new slide.
What is information
Answers
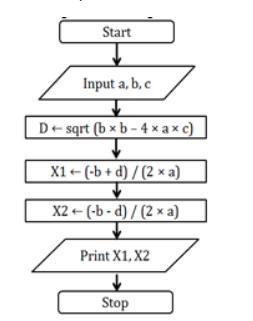
1 Design a flowchart to compute the following selection
(1) Area of a circle
(2) Simple interest
(3) Quadratic roots an
(4) Welcome to INTRODUCTION TO COMPUTER PROGRAMM INSTRUCTION
Answers
A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes.
What is a flowchart?A flowchart exists as a graphic illustration of a function. It's a chart that displays the workflow needed to achieve a task or a set of tasks with the help of characters, lines, and shapes. Flowcharts exist utilized to learn, enhance and communicate strategies in different fields.
Step Form Algorithm:
Start.
Declare the required variables.
Indicate the user to enter the coefficients of the quadratic equation by displaying suitable sentences using the printf() function.
Wait using the scanf() function for the user to enter the input.
Calculate the roots of the quadratic equation using the proper formulae.
Display the result.
Wait for the user to press a key using the getch() function.
Stop.989
Pseudo Code Algorithm:
Start.
Input a, b, c.
D ← sqrt (b × b – 4 × a × c).
X1 ← (-b + d) / (2 × a).
X2 ← (-b - d) / (2 × a).
Print x1, x2.
Stop.
Flowchart:
A flowchart to calculate the roots of a quadratic equation exists shown below:
import math
days_driven = int(input("Days driven: "))
while True:
code = input("Choose B for class B, C for class C,D for class D, or Q to Quit: ")
# for class D
if code[0].lower() == "d":
print("You chose Class D")
if days_driven >=8 and days_driven <=27:
amount_due = 276 + (43* (days_driven - 7))
elif days_driven >=28 and days_driven <=60:
amount_due = 1136 + (38*(days_driven - 28))
else:
print("Class D cannot be rented for less than 7 days")
print('amount due is $', amount_due)
break
elif code[0].lower() == "c":
print("You chose class C")
if days_driven \gt= 1 and days_driven\lt=6:
amount_due = 34 * days_driven
elif days_driven \gt= 7 and days_driven \lt=27:
amount_due = 204 + ((days_driven-7)*31)
elif days_driven \gt=28 and days_driven \lt= 60:
amount_due = 810 + ((days_driven-28)*28)
print('amount due is $', amount_due)
# for class b
elif code[0].lower() == "b":
print("You chose class B")
if days_driven >1 and days_driven<=6:
amount_due = 27 * days_driven
elif days_driven >= 7 and days_driven <=27:
amount_due = 162 + ((days_driven-7)*25)
elif days_driven >=28 and days_driven <= 60:
amount_due = 662 + ((days_driven-28)*23)
print('amount due is $', amount_due)
break
elif code[0].lower() == "q":
print("You chose Quit!")
break
else:
print("You must choose between b,c,d, and q")
continue
To learn more about computer programs refer to:
https://brainly.com/question/21612382
#SPJ9
In Java only please:
4.15 LAB: Mad Lib - loops
Mad Libs are activities that have a person provide various words, which are then used to complete a short story in unexpected (and hopefully funny) ways.
Write a program that takes a string and an integer as input, and outputs a sentence using the input values as shown in the example below. The program repeats until the input string is quit and disregards the integer input that follows.
Ex: If the input is:
apples 5
shoes 2
quit 0
the output is:
Eating 5 apples a day keeps you happy and healthy.
Eating 2 shoes a day keeps you happy and healthy
Answers
Answer:
Explanation:
import java.util.Scanner;
public class MadLibs {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
String word;
int number;
do {
System.out.print("Enter a word: ");
word = input.next();
if (word.equals("quit")) {
break;
}
System.out.print("Enter a number: ");
number = input.nextInt();
System.out.println("Eating " + number + " " + word + " a day keeps you happy and healthy.");
} while (true);
System.out.println("Goodbye!");
}
}
In this program, we use a do-while loop to repeatedly ask the user for a word and a number. The loop continues until the user enters the word "quit". Inside the loop, we read the input values using Scanner and then output the sentence using the input values.
Make sure to save the program with the filename "MadLibs.java" and compile and run it using a Java compiler or IDE.
Use the drop-down menus to complete statements about how to use the database documenter
options for 2: Home crate external data database tools
options for 3: reports analyze relationships documentation
options for 5: end finish ok run

Answers
To use the database documenter, follow these steps -
2: Select "Database Tools" from the dropdown menu.3: Choose "Analyze" from the dropdown menu.5: Click on "OK" to run the documenter and generate the desired reports and documentation.How is this so?This is the suggested sequence of steps to use the database documenter based on the given options.
By selecting "Database Tools" (2), choosing "Analyze" (3), and clicking on "OK" (5), you can initiate the documenter and generate the desired reports and documentation. Following these steps will help you utilize the database documenter effectively and efficiently.
Learn more about database documenter at:
https://brainly.com/question/31450253
#SPJ1
A program takes 35 seconds for input size 20 (i.e., n=20). Ignoring the effect of constants, approximately how much time can the same program be expected to take if the input size is increased to 100 given the following run-time complexities?
a. O(N)
b. O(N + log N)
c. O(N^3)
d. O(2^N)1
Answers
Given :
\(n_i=20\\t_i=35\ s\\n_f=100\)
To Find :
Expected time for :
a. O(N)
b. O(N + log N)
c. O(N^3)
d. O(2^N)
Solution :
a.
In O(N) relation is ,
t = kn
So ,
35 = k(20)
t = k(100)
t = 175 seconds .
b .
In O( N + log N ) , N is dominating term . So the complexity is simplified in O(N) .
So , t = 175 seconds .
c .
The relation is given by :
\(t=kn^3\)
So ,
\(35=k(20)^3\\\\t=k(100)^3\\\\t=35(\dfrac{100}{20})^3\\\\t=4375\ seconds\)
d .
The relation is given by :
\(t=k(2)^n\)
So ,
\(35=k(2)^{20}\\\\t=k(2)^{100}\\\\t=35\times (2)^{80}\)
Hence , this is the required solution .
give the imporntance of having standard funiture in the laboratory
Answers
Answer:
I guess if there is experiment going on in absence one of those furniture then the experiment isn't successful
Many documents use a specific format for a person's name. Write a program that reads a person's name in the following format:
firstName middleName lastName (in one line)
and outputs the person's name in the following format:
lastName, firstInitial.middleInitial.
Ex: If the input is:
Pat Silly Doe
the output is:
Doe, P.S.
If the input has the following format:
firstName lastName (in one line)
the output is:
lastName, firstInitial.
Ex: If the input is:
Julia Clark
the output is:
Clark, J.
Answers
Using the knowledge in computational language in JAVA it is possible to write the code that write a program whose input is: firstName middleName lastName, and whose output is: lastName, firstName middleInitial.
Writting the code:import java.util.Scanner;
import java.lang.*;
public class LabProgram{
public static void main(String[] args) {
String name;
String lastName="";
String firstName="";
char firstInitial=' ',middleInitial=' ';
int counter = 0;
Scanner input = new Scanner(System.in);
name = input.nextLine(); //read full name with spaces
int i;
for(i = name.length()-1;i>=0;i--){
if(name.charAt(i)==' '){
lastName = name.substring(i+1,name.length()); // find last name
break;
}
}
for(i = 0;i<name.length()-1;i++){
if(name.charAt(i)==' '){
firstName = name.substring(0, i); // find firstName
break;
}
}
for(i = 0 ;i<name.length();i++){
if(name.charAt(i)==' '){
counter++; //count entered names(first,middle,last or first last only)
}
}
if(counter == 2){
for(i = 0 ;i<name.length();i++){
if(Character.toUpperCase(name.charAt(i)) == ' '){
middleInitial = Character.toUpperCase(name.charAt(i+1));//find the middle name initial character
break;
}
}
}
firstInitial = Character.toUpperCase(name.charAt(0)); //the first name initial character
if(counter == 2){
System.out.print(lastName+", "+firstName+" "+middleInitial+".");
}else{
System.out.print(lastName+", "+firstName);
}
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1

Write a program that allows two players to play the Tic-Tac-Toe game. One of the players can be the computer or human, the other must be human. Your program must contain the class ticTacToe to implement a ticTacToe object. Include a 3 by 3 two-dimensional array, as a private member variable, to create the board. If needed, include additional member variables
Answers
Answer:
Explanation:
The following is a tictactoe game written in Java with all the necessary variables and methods needed for the game to function correctly. The game plays against the computer which randomly chooses a position to play every round. Due to technical difficulties the code was added as a txt file below and the output was added as a picture.

Students might earn either a Master of Arts (M.A.) or a Master of Science (M.S.) degree with an emphasis in digital communications in order to become a
Answers
Answer: Digital Communications Specialist
Explanation:
Took The Test Myself
Students might earn either a Master of Arts (M.A.) or a Master of Science (M.S.) degree with an emphasis in digital communications, in order to become a: Digital Communications Specialist.
What is a bachelor's degree?A bachelor's degree can be defined as an academic degree that is formally awarded by a tertiary institution (university or college) to a student after the successful completion of his or her high school, and it usually takes about 4 or 5 years to complete a bachelor's degree.
What is a master's degree?A master's degree can be defined as an academic degree that is formally awarded by a tertiary institution (university or college) to a student after the successful completion of his or her bachelor's degree programme.
In conclusion, students are required to earn either a Master of Arts (M.A.) or a Master of Science (M.S.) degree in digital communications, in order to become a Digital Communications Specialist.
Read more on Digital Communications Specialist here: https://brainly.com/question/27746922
#SPJ1
What makes up the cloud in cloud computing ?
Answers
Answer:
storage
Explanation:
hope this helps
Q1. Information systems that monitor the elementary activities and transactions of the organizations are: I a. Management-level system b. Operational-level system C. Knowledge-level system d. Strategic level system
Answers
Answer:
B. Operational-level systems monitor the elementary activities and transactions of the organization.
The information systems that monitor the elementary activities and transactions of the organizations are Operational-level systems. Thus, the correct option for this question is B.
What do you mean by Information system?An information system may be defined as a type of system that significantly consists of an integrated collection of components particularly for gathering, storing, and processing data and for providing information, knowledge, and digital products.
According to the context of this question, the management level system deals with managing the components of activities in a sequential manner. Knowledge level system works on influencing the source of information and data to the connected devices.
Therefore, the operational level system is the information system that monitors the elementary activities and transactions of the organizations. Thus, the correct option for this question is B.
To learn more about Information systems, refer to the link:
https://brainly.com/question/14688347
#SPJ2
In this section of your final project, you will write a basic script to create and back up files. You will create this script with the vi editor. The script will combine multiple commands and simplify a repeatable task. Your script should be named Firstname Lastname.BASH. Your script and your Linux directory structure should demonstrate that you have correctly written the script to do the following: Create files: In this section, you will demonstrate your ability to utilize various Linux commands to create text files. Create these files in the NEW directory. Ensure that the commands in your log file show that the following three text files were created using three different methods. Create the following files
XI A. A text file listing the quantity of operating system free space, titledFree_Space Content.txt B. A text file listing the directory contents of the OLD folder, titled OLD_Content.txt C. A text file showing the current month, day, and time (Title this fileTime File.tx.)
XI Modify and Move files: Utilize Linux commands to copy files to a different directory and renamethem A. Copy the following selected files from the OLD directory to the BACKUP directory. Ensure that you change the filename suffix fro XXX OLD to XXX BACKUP i. Free_Space_Content OLD.txt ii Directory Content OLD.txt i Time File OLD.txt Move all files from the NEW directory to the BACKUP directory (no renaming necessary). Clean up the Linux directory structure by deleting the items in the NEW directory B.
Answers
Answer:
bjdjdindbdubduf kndjnxjxjfujdjbdjbd bzjbd djbdibdu jdjdidnidndi xubdubdufjksk. xud ufbsjjdi djneibdudbdujfjfbjbdj fu. fjfjjdubdjjdbjd jdbdinkdkdnd. djjdibnfjdkndindundi jdudjbdubd djbdu bdudjdjjd djidndud dudbid anís us dj
Answer:
####Bash Script Start###################################
#######Please check the permissions on the folders inorder to make sure the script works
#!/bin/bash
if [ ! -d NEW ]; then
mkdir -p NEW;
fi
df > "NEW/Free_Space_Content.txt"
touch "NEW/OLD_Content.txt" | ls -l OLD > "NEW/OLD_Content.txt"
> "NEW/Time_File.txt" | date +"%B %c" > "NEW/Time_File.txt"
cp "OLD"/*.txt "BACKUP"
rename OLD BACKUP "BACKUP"/*.txt
mv "NEW"/*.txt "BACKUP"
#############Bash Script End##################################
########Script_Assessment.txt#####################
Commands which were used to create files:
touch filename
command > filename
> filename
Directory and its contents:
NEW: Contained the newly created file
OLD: Contained sample files with OLD suffix
BACKUP: Contains all the files moved from NEW and OLD directories
Free_Space_Content.txt contains the disk info such as used and free space
OLD_Content.txt contains the directory contents info of OLD directory
Time_File.txt : Contais the current month, day and time info
Explanation:
Because of inability to manage those risk. How does this explain the team vulnerability with 5 points and each references
Answers
The team is vulnerable due to a lack of risk assessment. Without risk understanding, they could be caught off guard by events. (PMI, 2020) Ineffective risk strategies leave teams vulnerable to potential impacts.
What is the inability?Inadequate contingency planning can hinder response and recovery from materialized risks. Vulnerability due to lack of contingency planning.
Poor Communication and Collaboration: Ineffective communication and collaboration within the team can make it difficult to address risks collectively.
Learn more about inability from
https://brainly.com/question/30845825
#SPJ1
Which of these is not a valid form
layout in Microsoft Access?
Answers
what are the main components involved in data transmission
Answers
Answer:
connection
Explanation:
connection between each device
Largest and Smallest
Write a Flowgorithm program that performs the following tasks:
o Utilizing nested loops
o Outside loop keeps the program running until told to stop
o Inside loop asks for input of number, positive or negative
o Input of a zero (0) terminates inside loop
o Display the largest and smallest number entered when inside loop is terminated
o Ask if the user wants to enter new set of numbers
Remember the following:
declare necessary variables & constants
use clear prompts for your input
use integers for the input numbers
clearly label the largest and smallest number on output
the zero to stop the inner loop is not to be considered the lowest number, it just stops the inner loop
consider a "priming read" to set initial values of large and small
Answers
The program based on the given question prompt is given below:
The ProgramBeginning
// initiate variables
largest = -999999999
smallest = 999999999
interruption = false
while not interruption do
// reset variables for fresh set of numbers
hugest_set = -999999999
pettiest_set = 999999999
// input cycle for gathering of numbers
duplicated
output "Input a number (0 to cease collection):"
input figure
if figure != 0 then
if figure > hugest_set then
hugest_set = figure
end if
if figure < pettiest_set then
pettiest_set = figure
end if
end if
until figure = 0
// examine whether this bunch of figures accommodates new boundaries
if hugest_set > largest then
largest = hugest_set
end if
if pettiest_set < smallest then
smallest = pettiest_set
end if
// produce the hugest and pettiest aspects for this set of numbers
output "Foremost number within this set:", hugest_set
output "Minimum number within this set:", pettiest_set
// solicit whether the user wants to persist
output "Do you wish to insert a new swarm of figures? (Y/N):"
input answer
if answer = "N" or answer = "n" then
interruption = true
end if
end while
// deliver grand total hugest and least parts
output "Complete most extensive amount:", largest
output "Overall minimum magnitude:", smallest
Read more about flowcharts here:
https://brainly.com/question/6532130
#SPJ1
Discuss how to enhance the security of a Linux computer in a systematic manner.
Answers
Answer:
So here are five easy steps to enhance your Linux security.
1. Choose Full Disk Encryption (FDE) No matter which operating system you are using, we recommend that you encrypt your entire hard disk.
2. Keep your software up-to-date.
3. Learn how to use Linux’s firewall.
4. Tighten up security in your browser.
5. Use anti-virus software.
Explanation:
Linux has five steps for enhanced security.
What are the five layers of security in Linux?A Linux is an operating system and has a Linux kernel that is based on the system and consists of five-layer of enhanced security.
These are FDE that is chosen full disk encryption, followed by keeping software up to date and learning how to make use of a firewall. It also tightens the browser's security plus the use of anti-virus.
Fin dout more infimation about the linux.
brainly.com/question/25480553
What is the second step in opening the case of working computer
Answers
Answer: 1. The steps of opening the case of a working computer as follows:
2. power off the device.
3. unplug its power cable.
4. detach all the external attachments and cables from the case.
5. Remove the retaining screws of the side panel.
6. Remove the case's side panel.
Explanation:
Write code that outputs variable numCats. End with a newline.
Answers
Answer:
#include <iostream>
#include <cmath>
using namespace std;
int main() {
int numCats;
cin>>numCats;
cout<<numCats<<endl;
Explanation:
customer seeks to buy a new computer for private use at home. The customer primarily needs the computer to use the Microsoft PowerPoint application for the purpose of practicing presentation skills. As a salesperson what size hard disc would you recommend and why?
Answers
Explanation:
The most reliable hard drives are those whose most common size is 3.5 inches, their advantages are their storage capacity and their speed and a disadvantage is that they usually make more noise.
For greater speed, it is ideal to opt for two smaller hard disks, since large disks are slower, but are partitioned so that there are no problems with file loss.
For a person who needs to use content creation programs, it is ideal to opt for a hard drive that has reliability.
4
Multiple Choice
You wrote a program to find the factorial of a number. In mathematics, the factorial operation is used for positive integers and zero.
What does the function return if the user enters a negative three?
def factorial number):
product = 1
while number > 0
product = product number
number = number - 1
return product
strNum = input("Enter a positive integer")
num = int(str Num)
print(factorial(num))
O-6
O-3
O There is no output due to a runtime error.
0 1
< PREVIOUS
NEXT >
SAVE
SUBMIT
© 2016 Glynlyon, Inc. All rights reserved.
V6.0 3-0038 20200504 mainline
Answers
The function will output positive 1 to the console. This happens because we declare product as 1 inside our function and that value never changes because the while loop only works if the number is greater than 0.
If a company gave you a free version of their software and encouraged you to try and improve it and share it with the only community, what kind of software would this be?
Answers
Answer:
Explanation:
crm
You are developing a system to process lists of days of the week, represented as strings. Create a function is_weekend that consumes a list and returns whether the list has the string "Saturday" or the string "Sunday" in it. Call and print this function once with a list of days of the week.
Answers
Answer:
public static boolean is_weekend(List week){
if(week.contains("Saturday")||week.contains("Sunday"))
{
System.out.println("List has a weekend");
return true;
}
else{
System.out.println("List has no weekend");
return false;
}
}
Explanation:
Using java programming languageImport java.util.ArrayList and import java.util.List; so you can implement a java listCreate a list and add the days of the weekCreate the required method using the contains() method to check for Sunday and Saturday and return true if the list contains themSee the complete program with a call to the methodimport java.util.ArrayList;
import java.util.List;
public class Car {
public static void main(String[] args) {
List<String> daysOfWeek = new ArrayList<>();
daysOfWeek.add("Sunday");
daysOfWeek.add("Moday");
daysOfWeek.add("Tuesday");
daysOfWeek.add("Wednesday");
daysOfWeek.add("Thursday");
daysOfWeek.add("Friday");
daysOfWeek.add("Saturday");
is_weekend(daysOfWeek);
}
public static boolean is_weekend(List week){
if(week.contains("Saturday")||week.contains("Sunday"))
{
System.out.println("List has a weekend");
return true;
}
else{
System.out.println("List has no weekend");
return false;
}
}
}
Which term describes a Cloud provider allowing more than one company to share or rent the same server?
Answers
The term that describes a cloud provider allowing more than one company to share or rent the same server is known as Multitenancy.
What is a cloud?A third-party business offering a cloud-based platform, infrastructure, application, or storage services is known as a cloud service provider.
Companies often only pay for the cloud services they use, as business demands dictate, similar to how a homeowner would pay for a utility like electricity or gas.
Data for each renter is separated and inaccessible to other tenants. Users have their own space in a multi-tenant cloud system to store their projects and data. Multi-tenant cloud system helps in the clouding of private and public sectors.
Thus, Multitenancy is the term used to describe a cloud service that permits many businesses to share or rent the same server.
To learn more about cloud, refer to the link:
https://brainly.com/question/27960113
#SPJ2
true or false. Two of the main differences between storage and memory is that storage is usually very expensive, but very fast to access.
Answers
Answer:
False. in fact, the two main differences would have to be that memory is violate, meaning that data is lost when the power is turned off and also memory is faster to access than storage.
.
5. The extension name of a C++ source code file is
Answers
.CCP
Explanation:
this is the extension of C++
EVALUATING A HUMAN RIGHTS CAMPAIGN • Identify an organization (name) and the human right that they are campaigning for. (1+2=3) • Describe (their) FOUR possible objectives of the campaign (4x2=8) • Discuss THREE actions that you may take to get involved in a campaign (3x2=6) Evaluate the success of the campaign (indicate their successes, challenges, failures) (3x2=6) [44] 4. RECOMMENDATIONS Recommend, at least TWO practical ways by which the campaign could be assisted to ensure its successes. (2x2=4) 5. CONCLUSION In your conclusion, summarize the significance of key findings made out of your evaluation and suggest about what could be done about the findings (1x3=3)
Answers
With regards to the human rights campaign, Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
The explanation1. The Organization is Amnesty International
Human Right is Freedom of Expression
2. Objectives is Raise awareness, advocate for release of imprisoned individuals, lobby for protective laws, mobilize public support.
3. Actions is Join as member/volunteer, sign petitions, attend protests.
4. Evaluation is Successes include increased awareness and releases, challenges faced from governments and limited resources, failures in changing repressive laws.
5. Recommendations is Collaborate with organizations, engage influencers to amplify impact.
Conclusion - Amnesty International's campaign for freedom of expression plays a vital role, with successes, challenges, and room for improvement through collaboration and engagement.
Learn more about Human rights campaign at:
https://brainly.com/question/31728557
#SPJ1
Put the Code in Order: Rearrange the given blocks of code
to make a
functioning program. Place the letter value before the line of code in the vertical order that they
would appear in the code editor. For this exercise, sections of code are combined together, but |
should still be put in correct order. The output should be the DAW screenshot depicted below:
EFFECTS
3
M
Bypass
(М
Bypass
Effect 1
Bypass
M
Bypass
00:02
00:00
1
HOUSE DEEP SINEPAD 001
REVERB-REVERB TIME
RD WORLD PERCUSSION DRUMSMAIN 6
DISTORTION-DISTO GAIN
00:04
DISTORTION-MIX
*****+++ | || | | | | |--
CHORUS CHORUS NUMVOICES
00:06
HOUSE DEEP SINEPAD 001
YO TRAP SYNTH MELODY 1
00:08
Answers
1/67600 is the code to make a functioning program. For this exercise, sections of code are combined together.
What will be the probability that code is 43MZ?Probability that the code is 43MZ:
Probability = (Total Required outcome / total possible outcomes)
Possible outcomes (digit) = (00,.............. ..., 99)
Possible outcomes (alphabet) = (A, B,............... .., Z)
P(43MZ) = P(43) × P(M) × P(Z)
P(43) = 1/100
P(M) = 1/26
P(Z) = 1/26
Therefore, P(43MZ) = (1/100) × (1/26) × (1/26) = 1/67600
Learn more about Probability on:
https://brainly.com/question/11234923
#SPJ1
You can use Word to create ____.
a. reports c. letters and memos
b. tables d. all of the above