we have deployed three virtual machines running iis in an azure virtual network. no network security groups are assigned to the virtual machines or the subnets in the vnet. what is the expected network traffic flow?
Answers
Where three virtual machines running IIS (Internet Information Services) are deployed in an Azure Virtual Network without any Network Security Groups (NSGs) assigned to the virtual machines or the subnets, the expected network traffic flow would be as follows:
Inbound Traffic:
The external clients or users would send requests to access the web servers hosted on the virtual machines. The requests would reach the public IP address associated with the Azure Virtual Network or the load balancer (if one is configured). Azure Load Balancer (if used) distributes the incoming traffic across the three virtual machines. The load-balanced traffic would be forwarded to the respective virtual machines running IIS.
Outbound Traffic:
Outbound traffic initiated from the virtual machines would be allowed by default. The virtual machines can communicate with external resources, such as accessing the internet for updates or making requests to external APIs or databases. It's important to note that without any NSGs, the network traffic is not restricted or controlled at the network layer. This configuration allows for unrestricted communication both inbound and outbound. It is recommended to implement appropriate NSGs to secure and control network traffic based on your specific requirements and security policies.
Learn more about virtual machines here : brainly.com/question/31674417?
#SPJ11
Related Questions
the process of ______________ requires that each user must log in with a valid user name and password before gaining access to a user interface.
Answers
The process of authentication requires that each user must log in with a valid user name and password before gaining access to a user interface.
Authentication is the process of verifying the identity of a user or system entity. It is an important aspect of computer security, as it ensures that only authorized users are granted access to sensitive data or resources.
In the context of user interfaces, authentication typically involves the use of login credentials, such as a username and password, which are verified against a database of authorized users. Once the user's identity has been verified, they are granted access to the user interface and its associated functionalities.
Without proper authentication measures in place, unauthorized users could gain access to sensitive information or perform actions that could compromise the security of the system.
Learn more about user interface https://brainly.com/question/32269594
#SPJ11
You are reviewing a friend’s HTML project. You notice that the only metadata is the title. Furthermore, you ask your friend about this, and they say, “Look—it doesn’t even show up on the webpage. It’s just a waste of time if it works fine without it.” How might you respond to your friend?
Answers
Generally, the meta title is used to specify the main title of a website. The meta title is the text that is displayed in the search engine results pages, and in the tabs of a web browser. It indicates what a page is about and what it is about. You should keep it.
Hope it helps :)
Write the text of the program in Python.

Answers
Answer:
wow its quite long ill send it to you in a couple of days
What is a named bit of programming instructions?
Answers
Answer:
Function: A named bit of programming instructions. Top Down Design: a problem solving approach (also known as stepwise design) in which you break down a system to gain insight into the sub-systems that make it up.
(1) describe how you generally use your cellphone on a daily basis (including with whom do you communicate for what purpose with what frequency); (2) read the Supplementary Reading (click here: Does the Internet Make You More or Less Connected?), and discuss how YOUR cellphone use make YOU more or less connected.
Answers
Brainly wasn't letting me answer, so here's an attachment of the answer
idea citizen activation
Answers
Answer: The Citizen Activation badge is part of the iDEA Silver Award and is in the Citizen category, helping you learn digital awareness, safety and ethics.
Want to know more about iDEA?
iDEA helps people develop digital, enterprise & employability skills for free. Log in or sign up to start a badge and begin to earn points on iDEA.
You are the administrator for the ABC Company. You are looking to install Windows Server 2016, and you need to decide which version to install. You need to install a version of Windows that is just for logon authentication and nothing else. You want the most secure option and cost is not an issue. What should you install
Answers
REMINDER, array indexes START AT 0 in C#. So the first element will be of index 0.
// 1. Create a single-dimensional array of type int. Populate it with 6 numbers.
int[] array1 = new int[] { 1, 3, 5, 7, 9, 11};
// 2. Now pull out the 5th number in the array and store it in a variable of type int
// 3. Create a multi-dimensional int array with two rows, each row being 5 elements long
// Prepopulate it with data
int[,] array2D = new int[,] { { 1, 2, 3, 4, 5 }, { 6, 7, 8, 9, 10},
// 4. Now pull out the 3rd number in the 2nd row of that array and store it in a variable
Console.WriteLine(array2D[1, 2];
// 5. Create a jagged array with 4 rows.
// Make the 1st row 3 columns long
// Make the 2nd row 5 columns long
// Make the 3rd row 2 columns long
// Make the 4th row 4 columns long
// Prepopulate each row with data
int[][] jaggedArray = new int[4][];
{
jaggedArray[0] = new int[3] { 4, 6, 8 };
jaggedArray[1] = new int[5] { 7, 9, 11, 13, 15 };
jaggedArray[2] = new int[4] { 12, 42, 52, 62 };
jaggedArray[3] = new int[4] { 3, 5, 1, 2};
};
// 6. Change the 3rd element in the 4th row.
// 7. Create a list of type string
// 8. Manually add 4 strings to the list. Then remove the LAST 2 elements BY INDEX.
// 9. Create a dictionary where the key is of type int and the value is of type string.
// Populate it with 5 elements.
// 10. Print any two values from the dictionary to the console. You should pull them by key.
Answers
// 2. Pull out the 5th number in the array and store it in a variable of type int
int fifthNumber = array1[4];
// 4. Pull out the 3rd number in the 2nd row of the 2D array and store it in a variable
int numberFrom2DArray = array2D[1, 2];
// 6. Change the 3rd element in the 4th row of the jagged array
jaggedArray[3][2] = newValue;
// 7. Create a list of type string
List<string> stringList = new List<string>();
// 8. Manually add 4 strings to the list. Then remove the LAST 2 elements by index.
stringList.Add("Apple");
stringList.Add("Banana");
stringList.Add("Orange");
stringList.Add("Grape");
stringList.RemoveAt(stringList.Count - 1);
stringList.RemoveAt(stringList.Count - 1);
// 9. Create a dictionary where the key is of type int and the value is of type string. Populate it with 5 elements.
Dictionary<int, string> dictionary = new Dictionary<int, string>();
dictionary.Add(1, "One");
dictionary.Add(2, "Two");
dictionary.Add(3, "Three");
dictionary.Add(4, "Four");
dictionary.Add(5, "Five");
// 10. Print any two values from the dictionary to the console. You should pull them by key.
int key1 = 3;
int key2 = 5;
Console.WriteLine(dictionary[key1]);
Console.WriteLine(dictionary[key2]);
To know more about array visit:
https://brainly.com/question/13261246
#SPJ11
computer hacking would be placed under which category in wall's typology of cybercrime? computer hacking would be placed under which category in wall's typology of cybercrime?
Answers
Computer hacking would be placed under cyber-trespass category in wall's typology of cybercrime.
What is software trespass?Intentionally accessing, altering, deleting, or otherwise interfering with a computer without authorisation is considered computer trespass.
Therefore, a computer trespass is defined as getting access to a secured computer without the necessary authorization and taking financial information, departmental information, or agency information. Although each state has its own rules involving computer trespassing, they all in some way mirror the federal legislation.
Learn more about cyber-trespass from
https://brainly.com/question/25157310
#SPJ1
the vast majority of the population associates blockchain with the cryptocurrency bitcoin; however, there are many other uses of blockchain; such as litecoin, ether, and other currencies. describe at least two cryptocurrencies with applicable/appropriate examples and discuss some of the similarities and differences.'
Answers
Litecoin is a cryptocurrency similar to Bitcoin but with faster transaction confirmation times and a different hashing algorithm.
What are the advantages of using litecoin?It enables quick and low-cost transfers, making it suitable for everyday transactions. For instance, a person can use Litecoin to buy goods or services online, such as purchasing a digital product.
Ether, on the other hand, powers the Ethereum blockchain, which is a decentralized platform for building smart contracts and decentralized applications (DApps). It serves as the native currency for executing transactions and powering operations on the Ethereum network.
Read more about cryptocurrency here:
https://brainly.com/question/26103103
#SPJ4
The role of the
protocol is to make sure communication is maintained.
FTP
IP
ТСР
HTTP
Answers
Answer:
Tcp
Explanation:
How many outcomes are possible in this control structure?
forever
A. One
B. Two
C. Four
D. Three
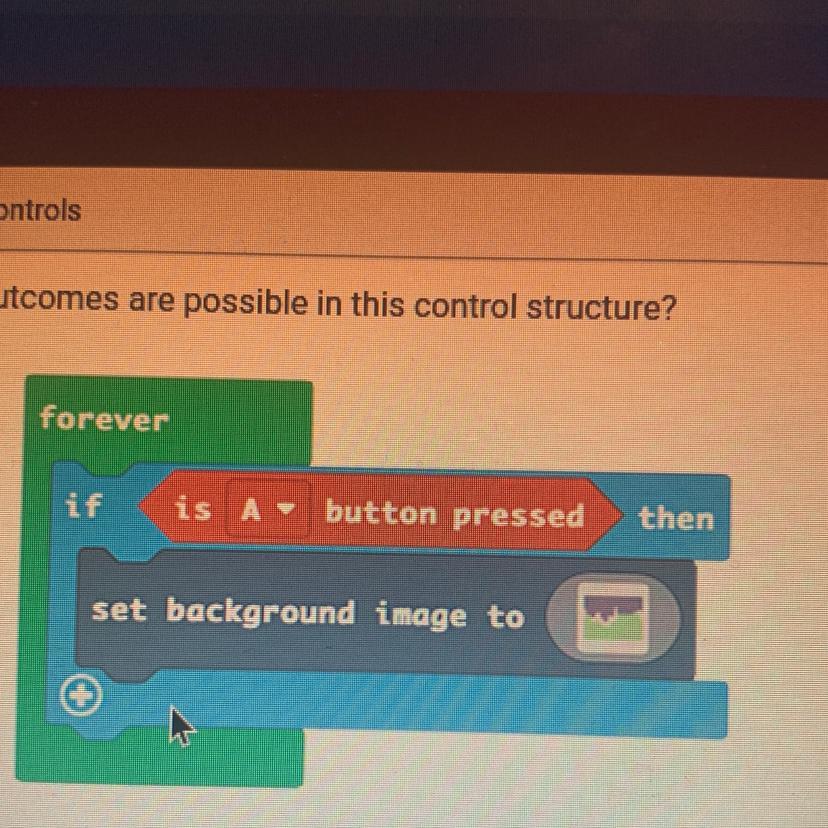
Answers
In this control system, just one conceivable outcome can occur.
What exactly is a control structure?
The sequence in which statements, instructions, or function calls are performed at the conclusion of a programme is known as the control structure. In computer programming, it is a fundamental idea that outlines how a programme will carry out its operations and choose which instructions to carry out. Control structures are used to particular specify the order in which operations in a system should be performed, to reactivities a predetermined number of times or until a predefined condition is satisfied, and to choose what operations to run based on preset criteria.
To know more about control structure
https://brainly.com/question/15008951
#SPJ1
Does anyone know what's wrong with this code in Unity? HELP FAST PLEASE! This is for my game design course, I will give brainiest if you can help

Answers
its expecting a "{} around a certain area.
hope this helps!!!
State 3 limitations of the ancient methods of information transmission
Answers
Answer:
(I put two more just incase )
1 lack of speed. 2 lack of sustainability.3 fragile4 low security measures.5 lack of comparabilityConsider a recent software development project in which you have participated. Did your process need more discipline or more agility to be effective? Why?
Answers
While discipline and agility are both important in software development, it is essential to evaluate project needs and requirements. In my experience, agile methodology was the best approach to meet our project objectives and deliver a quality product to our clients.
In recent years, the agile methodology has become increasingly popular in software development. However, traditional software development processes can still be effective. When deciding between discipline and agility in a software development project, it is important to consider the project's requirements, scope, and timelines.
Discipline is essential in software development processes as it helps keep the project on track and within budget. Project managers use various project management tools and techniques to ensure that project tasks are executed as planned. Discipline helps in tracking, reviewing, and reporting on the project progress, which is critical in keeping the project stakeholders informed of the project's status.
Agility is also crucial in software development projects. In an agile project, requirements and solutions evolve through the collaborative effort of self-organizing and cross-functional teams. Agile software development prioritizes collaboration, responsiveness to changes, and customer satisfaction. The Agile methodology helps developers create a product that meets the customer's needs and is continuously improved upon based on feedback.
In a recent software development project that I participated in, I believe that our process needed more agility than discipline. We were working on a mobile app project with a tight timeline. Due to unforeseen issues, we had to pivot and make significant changes to the project scope, design, and requirements. Our team embraced the agile methodology and worked closely with the client to make changes quickly and efficiently.
Learn more about agile methodology here:-
https://brainly.com/question/31429175
#SPJ11
What is the ICD-10 for moderate constipation?
Answers
Answer: K59.00
Explanation:
----------------------------
Please summarize into 1.5 pages only
----------------------------
Virtualization
Type 2 Hypervisors
"Hosted" Approach
A hypervisor is software that creates and runs VM ins
Answers
Virtualization: It is a strategy of creating several instances of operating systems or applications that execute on a single computer or server. Virtualization employs software to reproduce physical hardware and create virtual versions of computers, servers, storage, and network devices. As a result, these virtual resources can operate independently or concurrently.
Type 2 Hypervisors: Type 2 hypervisors are hosted hypervisors that are installed on top of a pre-existing host operating system. Because of their operation, Type 2 hypervisors are often referred to as "hosted" hypervisors. Type 2 hypervisors offer a simple method of getting started with virtualization. However, Type 2 hypervisors have some limitations, like the fact that they are entirely reliant on the host operating system's performance.
"Hosted" Approach: The hosted approach entails installing a hypervisor on top of a host operating system. This hypervisor uses hardware emulation to create a completely functional computer environment on which several operating systems and applications can run concurrently. In general, the hosted approach is used for client-side virtualization. This method is easy to use and is especially useful for the creation of virtual desktops or the ability to run many operating systems on a single computer.
A hypervisor is software that creates and runs VM instances: A hypervisor, also known as a virtual machine manager, is software that creates and manages virtual machines (VMs). The hypervisor allows several VMs to execute on a single physical computer, which means that the computer's hardware can be utilized more efficiently. The hypervisor's role is to manage VM access to physical resources such as CPU, memory, and I/O devices, as well as to provide VM isolation.
Know more about virtualization, here:
https://brainly.com/question/31257788
#SPJ11
restart the computer and press the f2 or delete key on your keyboard to enter the bios setup program. then explore the current bios settings to find the answers to the following questions: which brand of processor is installed? how much memory is installed in the computer? what is the bios version number? how many hard drives are installed? what is the status of the integrated nic? what is the current status of the usb 3.0 controller?
Answers
To restart your computer and enter the BIOS setup program, press the F2 or Delete key on your keyboard. Once you are in the BIOS setup program, you can explore the current settings to find the answers to the following questions:
Which brand of processor is installed? You can find this information by looking in the System Configuration section of the BIOS.How much memory is installed in the computer? You can find this information by looking in the Memory Configuration section of the BIOS.What is the BIOS version number? You can find this information in the System Information section of the BIOS.How many hard drives are installed? You can find this information by looking in the Storage Configuration section of the BIOS.What is the status of the integrated NIC? You can find this information by looking in the Network Configuration section of the BIOS.What is the current status of the USB 3.0 controller? You can find this information by looking in the USB Configuration section of the BIOS.Learn more about BIOS setup program
https://brainly.com/question/13103092
#SPJ4
How did tribes profit most from cattle drives that passed through their land?
A.
by successfully collecting taxes from every drover who used their lands
B.
by buying cattle from ranchers to keep for themselves
C.
by selling cattle that would be taken to Texas ranches
D.
by leasing grazing land to ranchers and drovers from Texas
Answers
The way that the tribes profit most from cattle drives that passed through their land is option D. By leasing grazing land to ranchers and drovers from Texas.
How did Native Americans gain from the long cattle drives?When Oklahoma became a state in 1907, the reservation system there was essentially abolished. In Indian Territory, cattle were and are the dominant economic driver.
Tolls on moving livestock, exporting their own animals, and leasing their territory for grazing were all sources of income for the tribes.
There were several cattle drives between 1867 and 1893. Cattle drives were conducted to supply the demand for beef in the east and to provide the cattlemen with a means of livelihood after the Civil War when the great cities in the northeast lacked livestock.
Lastly, Abolishing Cattle Drives: Soon after the Civil War, it began, and after the railroads reached Texas, it came to an end.
Learn more about cattle drives from
https://brainly.com/question/16118067
#SPJ1
The blue section of the following Venn diagram could represent which of the following Boolean statements?

Answers
Answer:
Last option: Not statement
Explanation:
Anything outside the borders of the circles are considered the not Boolean statement since the circles represent or and the overlap represents and.
Hope this helps :)
A Venn diagram is a type of visual representation that uses circles to emphasize the relationships among certain objects or constrained groups of things.
What Venn diagram could represent boolean statements?Circles with overlaps have some properties that circle without overlaps do not. Venn's diagrams are useful for showing how two concepts are related and different visually.
John Venn (1834–1923) popularized the Venn diagram, a common diagram type that illustrates the logical relationship between sets, in the 1880s.
Two circles in a box that lock together to form a Venn diagram represent one categorical assertion. The entire conversation universe is represented by the box, including the circles.
Therefore, Given that the overlap symbolizes and the circles represent or, anything outside their boundaries is seen as not being a Boolean statement.
Learn more about Venn diagram here:
https://brainly.com/question/29301560
#SPJ5
what kind of information does a smartphone handle
Answers
Answer:
Mobile devices can be used to save several types of personal information such as contacts, photos, calendars and notes, SMS and MMS messages. Smartphones may additionally contain video, email, web browsing information, location information, and social networking messages and contacts. Explanation:
view shows a list of files and folders, along with common properties, such
as Date Modified and Type.
A. tiles b. Details c. Medium icons d. Large icons
Answers
Answer:
A. list
Explanation:
Click this link to view O*NET’s Work Activities section for Chefs and Head Cooks.
Note that common activities are listed toward the top, and less common activities are listed toward the bottom.
According to O*NET, what are common work activities performed by Chefs and Head Cooks? Check all that apply.
making decisions and solving problems
repairing electronic equipment
coordinating the work and activities of others
maintaining interpersonal relationships
taking payments from customers
inspecting equipment
Answers
Answer:
A, C, D, and F
Explanation:
I just did it
Answer:
1, 2, 3 and 5
Explanation:
Leana was correct
which mobile device feature allows tracking how far someone has walked this week? group of answer choices virtual assistant accelerometer gyroscope pedometer
Answers
The mobile device feature that allows tracking how far someone has walked this week is called a pedometer. A pedometer is a device that uses an accelerometer to measure the number of steps taken by an individual.
It can track and provide information on the distance covered during a specific period of time, such as a week. The pedometer feature can be found on many mobile devices and fitness apps, enabling users to monitor their walking or running activity.
In summary, the main answer is "pedometer," and the explanation is that it uses an accelerometer to track the distance walked. A pedometer is a device that uses an accelerometer to measure the number of steps taken by an individual.
To know more about accelerometer visit:
https://brainly.com/question/33945794
#SPJ11
Hey, can anyone please help me?

Answers
Answer:
i think the answer is b not sure tho
Explanation:
mb for being rly late lol hopefully this helps :)
Fault tolerance refers to
how a network fails.
how well a network recovers after a failure.
mirror operations.
servers.
Answers
Answer:
servers
Explanation:
because it good for servers
Answer: How well a network recovers after a failure.
Explanation:
2. INFERENCE (a) The tabular version of Bayes theorem: You are listening to the statistics podcasts of two groups. Let us call them group Cool og group Clever. i. Prior: Let prior probabilities be proportional to the number of podcasts each group has made. Cool made 7 podcasts, Clever made 4. What are the respective prior probabilities? ii. In both groups they draw lots to decide which group member should do the podcast intro. Cool consists of 4 boys and 2 girls, whereas Clever has 2 boys and 4 girls. The podcast you are listening to is introduced by a girl. Update the probabilities for which of the groups you are currently listening to. iii. Group Cool does a toast to statistics within 5 minutes after the intro, on 70% of their podcasts. Group Clever doesn't toast. What is the probability that they will be toasting to statistics within the first 5 minutes of the podcast you are currently listening to? Digits in your answer Unless otherwise specified, give your answers with 4 digits. This means xyzw, xy.zw, x.yzw, 0.xyzw, 0.0xyzw, 0.00xyzw, etc. You will not get a point deduction for using more digits than indicated. If w=0, zw=00, or yzw = 000, then the zeroes may be dropped, ex: 0.1040 is 0.104, and 9.000 is 9. Use all available digits without rounding for intermediate calculations. Diagrams Diagrams may be drawn both by hand and by suitable software. What matters is that the diagram is clear and unambiguous. R/MatLab/Wolfram: Feel free to utilize these software packages. The end product shall nonetheless be neat and tidy and not a printout of program code. Intermediate values must also be made visible. Code + final answer is not sufficient. Colours Use of colours is permitted if the colours are visible on the finished product, and is recommended if it clarifies the contents.
Answers
(i) Prior probabilities: The respective prior probabilities can be calculated by dividing the number of podcasts made by each group by the total number of podcasts made.
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Group Cool: 7 podcasts
Group Clever: 4 podcasts
Total podcasts: 7 + 4 = 11
Prior probability of Group Cool: 7/11 ≈ 0.6364 (rounded to four decimal places)
Prior probability of Group Clever: 4/11 ≈ 0.3636 (rounded to four decimal places)
(ii) Updating probabilities based on the gender of the podcast intro: Since the podcast intro is done by a girl, we need to calculate the conditional probabilities of the group given that the intro is done by a girl.
Group Cool: 4 girls out of 6 members
Group Clever: 4 girls out of 6 members
Conditional probability of Group Cool given a girl intro: P(Group Cool | Girl intro) = (4/6) * 0.6364 ≈ 0.4242 (rounded to four decimal places)
Conditional probability of Group Clever given a girl intro: P(Group Clever | Girl intro) = (4/6) * 0.3636 ≈ 0.2424 (rounded to four decimal places)
(iii) Probability of toasting to statistics within the first 5 minutes: Since Group Cool toasts on 70% of their podcasts and Group Clever doesn't toast, we can directly use the conditional probabilities.
Probability of toasting within the first 5 minutes given Group Cool: P(Toasting | Group Cool) = 0.70
Probability of toasting within the first 5 minutes given Group Clever: P(Toasting | Group Clever) = 0
The overall probability of toasting within the first 5 minutes of the podcast you are currently listening to can be calculated using the updated probabilities from step (ii):
P(Toasting) = P(Toasting | Group Cool) * P(Group Cool | Girl intro) + P(Toasting | Group Clever) * P(Group Clever | Girl intro)
= 0.70 * 0.4242 + 0 * 0.2424
≈ 0.2969 (rounded to four decimal places)
The prior probabilities of Group Cool and Group Clever were calculated based on the number of podcasts each group made. Then, the probabilities were updated based on the gender of the podcast intro. Finally, the probability of toasting to statistics within the first 5 minutes of the current podcast was estimated using the conditional probabilities.
To know more about Prior Probabilities, visit
https://brainly.com/question/29381779
#SPJ11
The IT manager has tasked you with installing new physical machines. These computer systems are barebone systems that simply establish a remote connection to the data center to run the user's virtualized desktop. Which type of deployment model is being used
Answers
The type of deployment model that is used is referred to as Thin client.
A thin client is also referred to as lean client. It is a model that runs on the resources that are stored on a central server rather than in the resources if the computer.
A thin client is useful for shared services, and desktop virtualization. The work carried out by the server include storage of data, performing if calculation, launching software programs etc.
On conclusion, since the information given in the question explains that there's a remote connection to the data center to run the user's virtualized desktop, then the deployment model is a thin client.
Read related question on:
https://brainly.com/question/13934016
A chosen ciphertext attack (cca) is an attack in which the adversary chooses a number of ciphertexts and is then given the corresponding plaintexts, decrypted with the target's private key. true false
Answers
Answer: True
Explanation: True
PHOTOGRAPHY: In 200 words or more explain the difference between deep and shallow depth field and when would you use either technique when taking a photograph?
Answers
The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.What is the difference between deep and shallow focus?The Images gotten in shallow focus is one that needs little or shallow depths of field, and its lenses also needs long focal lengths, and big apertures. But Deep focus images needs small focal lengths and long depths of field.
In the case above i recommend deep depth field and therefore, The differences are:
A shallow depth of field is said to be a small area in view and its background is always blurred but a A deep depth of field is known to be one that captures a bigger area in view and its image are said to be sharp and clear.Learn more about photograph from
https://brainly.com/question/13600227
#SPJ1