What are steps for properly cleaning a PC or Mac laptop fan? Check all boxes that apply.
For a PC laptop, remove the CPU case, locate the fans, and then use compressed air to blow dirt through the internal slits.
For a Mac laptop, visit an Apple Store or take a look at your Apple Care Protection Plan, if applicable.
For PC and Mac laptops, use compressed air on all ports and drives.
For PC and Mac laptops, consider getting an experienced technician to help you.
Answers
The steps for properly cleaning a PC or Mac laptop fan is :
For a Mac laptop, visit an Apple Store or take a look at your Apple Care Protection Plan, if applicable.For PC and Mac laptops, consider getting an experienced technician to help you.What is meant by mac laptop ?The MacBook range of Mac notebook computers, which utilise the macOS operating system, has been produced and offered for sale by Apple Inc. since 2006. When Apple announced in 2005 that it will move to employing Intel CPUs, the PowerBook and iBook brands were replaced.
The fact that a MacBook and a laptop use separate operating systems is their main distinction. Another laptop running the Macintosh operating system is the MacBook. Unlike a typical laptop, which comes with either a Windows or a Linux operating system.
The high-quality audio, video, and typing experiences of MacBook's are another factor that sets them apart from the competitors and makes them more immersive gadgets overall.
To learn more MacBook refer to :
https://brainly.com/question/1002481
#SPJ1
Related Questions
List at least two reasons why database systems support data manipulation using a declarative query language such as SQL, instead of just providing a library of C or C++ functions to carry out data manipulation
Answers
Easier for both programmers and non-programmers to learn. The choice of an efficient execution technique is left up to the database system, so the programmer does not have to worry about how to create queries to make sure they will execute quickly.
Why do database systems allow for the alteration of data?Data presented in a uniform manner allows it to be more easily organized, read, and comprehended. When combining data from several sources, you might not have an uniform perspective, but you can ensure that the data is formatted and stored consistently with data manipulation and commands.
What is DBMS, and why should you know at least two of its benefits?Data is managed by the DBMS, and it can be read, locked, and modified using the database engine.
To know more about SQL visit :-
https://brainly.com/question/24180759
#SPJ4
Which of these are tools used to diagnose and test code? Check all of the boxes that apply.
debugging software
creating data sets
compiler software
error messages
Answers
Answer:
A C D
Explanation:
Answer:
Correct
Explanation:
1. Discuss data processing concepts and the representation of data in the computer
2. Explain how they work together to process data
Answers
Answer:
gkvjbdsvjnmfbhui jgbfdshjcxvabgsuciusgBFIULWGSfuRyt vqwyrgfgweVGYGTV7BWUIEGDWYUGDCYg
Explanation:
Which of the following would help build effective verbal communication skills?
a.
reading body language accurately
b.
understanding how to dress well
c.
developing a better vocabulary
d.
controlling inappropriate facial expressions
Please select the best answer from the choices provided
A
B
C
D
Answers
Answer:
developing a better vocabulary
Module 7: Final Project Part II : Analyzing A Case
Case Facts:
Virginia Beach Police informed that Over 20 weapons stolen from a Virginia gun store. Federal agents have gotten involved in seeking the culprits who police say stole more than 20 firearms from a Norfolk Virginia gun shop this week. The U.S. Bureau of Alcohol, Tobacco, Firearms and Explosives is working with Virginia Beach police to locate the weapons, which included handguns and rifles. News outlets report they were stolen from a store called DOA Arms during a Tuesday morning burglary.
Based on the 'Probable Cause of affidavit' a search warrant was obtained to search the apartment occupied by Mr. John Doe and Mr. Don Joe at Manassas, Virginia. When the search warrant executed, it yielded miscellaneous items and a computer. The Special Agent conducting the investigation, seized the hard drive from the computer and sent to Forensics Lab for imaging.
You are to conduct a forensic examination of the image to determine if any relevant electronic files exist, that may help with the case. The examination process must preserve all evidence.
Your Job:
Forensic analysis of the image suspect_ImageLinks to an external site. which is handed over to you
The image file suspect_ImageLinks to an external site. ( Someone imaged the suspect drive like you did in the First part of Final Project )
MD5 Checksum : 10c466c021ce35f0ec05b3edd6ff014f
You have to think critically, and evaluate the merits of different possibilities applying your knowledge what you have learned so far. As you can see this assignment is about "investigating” a case. There is no right and wrong answer to this investigation. However, to assist you with the investigation some questions have been created for you to use as a guide while you create a complete expert witness report. Remember, you not only have to identify the evidence concerning the crime, but must tie the image back to the suspects showing that the image came from which computer. Please note: -there isn't any disc Encryption like BitLocker. You can safely assume that the Chain of custody were maintained.
There is a Discussion Board forum, I enjoy seeing students develop their skills in critical thinking and the expression of their own ideas. Feel free to discuss your thoughts without divulging your findings.
While you prepare your Expert Witness Report, trying to find answer to these questions may help you to lead to write a conclusive report : NOTE: Your report must be an expert witness report, and NOT just a list of answered questions)
In your report, you should try to find answer the following questions:
What is the first step you have taken to analyze the image
What did you find in the image:
What file system was installed on the hard drive, how many volume?
Which operating system was installed on the computer?
How many user accounts existed on the computer?
Which computer did this image come from? Any indicator that it's a VM?
What actions did you take to analyze the artifacts you have found in the image/computer? (While many files in computer are irrelevant to case, how did you search for an artifacts/interesting files in the huge pile of files?
Can you describe the backgrounds of the people who used the computer? For example, Internet surfing habits, potential employers, known associates, etc.
If there is any evidence related to the theft of gun? Why do you think so?
a. Possibly Who was involved? Where do they live?
b. Possible dates associated with the thefts?
Are there any files related to this crime or another potential crime? Why did you think they are potential artifacts? What type of files are those? Any hidden file? Any Hidden data?
Please help me by answering this question as soon as possible.
Answers
In the case above it is vital to meet with a professional in the field of digital forensics for a comprehensive analysis in the areas of:
Preliminary StepsImage Analysis:User Accounts and Computer Identification, etc.What is the Case Facts?First steps that need to be done at the beginning. One need to make sure the image file is safe by checking its code and confirming that nobody has changed it. Write down who has had control of the evidence to show that it is trustworthy and genuine.
Also, Investigate the picture file without changing anything using special investigation tools. Find out what type of system is used on the hard drive. Typical ways to store files are NTFS, FAT32 and exFAT.
Learn more about affidavit from
https://brainly.com/question/30833464
#SPJ1
4. Create a Java program that asks for the names of three
runners and the time, in minutes, it took each of them to
finish a race. The program should display the names of
the runners in the order they finished.
Answers
Answer:
Explanation:
Here's a Java program that asks for the names of three runners and the time, in minutes, it took each of them to finish a race, and then displays the names of the runners in the order they finished:
import java.util.Scanner;
public class RunnerRace {
public static void main(String[] args) {
Scanner input = new Scanner(System.in);
// ask for the names of the runners and their race times
System.out.print("Enter the name of runner 1: ");
String runner1 = input.nextLine();
System.out.print("Enter the time it took runner 1 to finish (in minutes): ");
int time1 = input.nextInt();
input.nextLine();
System.out.print("Enter the name of runner 2: ");
String runner2 = input.nextLine();
System.out.print("Enter the time it took runner 2 to finish (in minutes): ");
int time2 = input.nextInt();
input.nextLine();
System.out.print("Enter the name of runner 3: ");
String runner3 = input.nextLine();
System.out.print("Enter the time it took runner 3 to finish (in minutes): ");
int time3 = input.nextInt();
input.nextLine();
// determine the order of the runners based on their race times
String firstPlace, secondPlace, thirdPlace;
int firstTime, secondTime, thirdTime;
if (time1 < time2 && time1 < time3) {
firstPlace = runner1;
firstTime = time1;
if (time2 < time3) {
secondPlace = runner2;
secondTime = time2;
thirdPlace = runner3;
thirdTime = time3;
} else {
secondPlace = runner3;
secondTime = time3;
thirdPlace = runner2;
thirdTime = time2;
}
} else if (time2 < time1 && time2 < time3) {
firstPlace = runner2;
firstTime = time2;
if (time1 < time3) {
secondPlace = runner1;
secondTime = time1;
thirdPlace = runner3;
thirdTime = time3;
} else {
secondPlace = runner3;
secondTime = time3;
thirdPlace = runner1;
thirdTime = time1;
}
} else {
firstPlace = runner3;
firstTime = time3;
if (time1 < time2) {
secondPlace = runner1;
secondTime = time1;
thirdPlace = runner2;
thirdTime = time2;
} else {
secondPlace = runner2;
secondTime = time2;
thirdPlace = runner1;
thirdTime = time1;
}
}
// display the names of the runners in the order they finished
System.out.println("First place: " + firstPlace + " (" + firstTime + " minutes)");
System.out.println("Second place: " + secondPlace + " (" + secondTime + " minutes)");
System.out.println("Third place: " + thirdPlace + " (" + thirdTime + " minutes)");
}
}
The program first asks for the names of the runners and their race times. It then determines the order of the runners based on their race times, using nested if statements to compare the race times. Finally, the program displays the names of the runners in the order they finished, along with their race times.
What are the advantage of an e-library
Answers
Answer:
Makes it easier to read... summarize cite electronic versions of editions
One of the common tests used to evaluate the accessibility of a web page consists of
using an Internet search engine to see if the page can be found easily.
clicking all hyperlinks in the page to test for broken or inaccurate links.
using the TAB and ENTER keys to move through the page’s content.
comparing the page with others in the website to find inconsistent layout.
Answers
The statement provided is True. An Internet search engine examination is a comprehensively employed method to evaluate the accessibility of a webpage, gauging if the page can be expeditiously found by users.
Other methods of accessing dataFurthermore, all hyperlinks in the page are clicked upon to weed out broken or inaccurate links which may negatively affect user experience by leading them astray. This rubric helps identify any links that may pose difficulties in accessing an accurate destination or even incorrect one, thus excluding any possibility of misunderstanding or degradation of user satisfaction.
An additional arbiter frequently employed to determine the accessibility of a webpage is using TAB and ENTER keys on a keyboard only interface. Loopholes for a comfortable exploration via keyboards when digital displays cannot help decipher is demonstrated in this manner; important for those susceptible to low vision or motor impairments obeying disability codes with accessible requirements or anyone else lacking interaction means save the keyboard.
Learn more about Internet search engine at
https://brainly.com/question/26488669
#SPJ1
A generator that is not producing voltage or current may have an open stator winding. True or False?
Answers
Answer:
True. An open stator winding is a common cause of a generator not producing any voltage or current. The stator winding is responsible for producing the electromagnetic field that induces voltage in the generator's rotor, which then produces the current. If the stator winding is open or broken, the magnetic field will not be produced, resulting in no voltage or current being generated.
In Coral Code Language - A half-life is the amount of time it takes for a substance or entity to fall to half its original value. Caffeine has a half-life of about 6 hours in humans. Given the caffeine amount (in mg) as input, output the caffeine level after 6, 12, and 18 hours.
Ex: If the input is 100, the output is:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
Note: A cup of coffee has about 100 mg. A soda has about 40 mg. An "energy" drink (a misnomer) has between 100 mg and 200 mg.
Answers
To calculate the caffeine level after 6, 12, and 18 hours using the half-life of 6 hours, you can use the formula:
Caffeine level = Initial caffeine amount * (0.5 ^ (time elapsed / half-life))
Here's the Coral Code to calculate the caffeine level:
function calculateCaffeineLevel(initialCaffeineAmount) {
const halfLife = 6; // Half-life of caffeine in hours
const levelAfter6Hours = initialCaffeineAmount * Math.pow(0.5, 6 / halfLife);
const levelAfter12Hours = initialCaffeineAmount * Math.pow(0.5, 12 / halfLife);
const levelAfter18Hours = initialCaffeineAmount * Math.pow(0.5, 18/ halfLife);
return {
'After 6 hours': levelAfter6Hours.toFixed(1),
'After 12 hours': levelAfter12Hours.toFixed(1),
'After 18 hours': levelAfter18Hours.toFixed(1)
};
}
// Example usage:
const initialCaffeineAmount = 100;
const caffeineLevels = calculateCaffeineLevel(initialCaffeineAmount);
console.log('After 6 hours:', caffeineLevels['After 6 hours'], 'mg');
console.log('After 12 hours:', caffeineLevels['After 12 hours'], 'mg');
console.log('After 18 hours:', caffeineLevels['After 18 hours'], 'mg');
When you run this code with an initial caffeine amount of 100 mg, it will output the caffeine levels after 6, 12, and 18 hours:
After 6 hours: 50.0 mg
After 12 hours: 25.0 mg
After 18 hours: 12.5 mg
You can replace the initialCaffeineAmount variable with any other value to calculate the caffeine levels for different initial amounts.
for similar questions on Coral Code Language.
https://brainly.com/question/31161819
#SPJ8
10. Where in Fusion 360 do you access, manage,
organize, and share Fusion 360 design data?
O Data Panel
O ViewCube
O Display Settings
O Timeline
Answers
In Fusion 360, you access, manage, organize, and share design data through the Data Panel. Option A.
In Fusion 360, the Data Panel is the central location where you can access, manage, organize, and share design data. It serves as a hub for all your design files, components, assemblies, drawings, and related resources within the Fusion 360 environment.
The Data Panel provides a tree-like structure where you can navigate through your projects, folders, and files. It allows you to create new designs, import existing files, and organize them into logical groups. Within the Data Panel, you can perform various actions on your design data, such as renaming, duplicating, moving, or deleting files and folders.
Additionally, the Data Panel offers collaboration and sharing capabilities. You can invite team members or external collaborators to access and collaborate on your design data. It provides options to control access permissions, track changes, and comment on specific design elements.
Furthermore, the Data Panel allows you to manage design revisions and versions. You can create new versions of your designs, compare different versions, and roll back to previous iterations if needed.
Overall, the Data Panel in Fusion 360 is a powerful tool that centralizes the management and organization of design data. It simplifies the workflow by providing easy access to files, collaboration features, and version control capabilities, making it a key component for working with and sharing Fusion 360 design data. So Option A is correct.
For more question on organize visit:
https://brainly.com/question/31612470
#SPJ8
Cristina works in the sales department of a company that provides security services to businesses. She is writing a proposal to persuade a shopping mall to hire her company. She is using the most recent version of Microsoft word but just learned that the customer has an older version. What word-processing function will let her provide a document her customer's software can read?
Answers
In such a situation, Cristina must save the document in a format that the customer's software can read.To ensure compatibility, Cristina can use the "Save As" function to save the document in an earlier version of Microsoft Word format. When using this function, she must choose the earliest version that is compatible with the customer's software.
When writing a proposal to persuade a shopping mall to hire a company that provides security services to businesses, the writer must ensure that the proposal is compatible with the software the customer uses. Cristina works in the sales department of such a company, and she is using the most recent version of Microsoft Word. However, she just learned that the customer has an older version.
In such a situation, Cristina must save the document in a format that the customer's software can read.To ensure compatibility, Cristina can use the "Save As" function to save the document in an earlier version of Microsoft Word format. When using this function, she must choose the earliest version that is compatible with the customer's software.
In this case, she must save the document in a format that is compatible with the older version of Word used by the customer.The "Save As" function in Microsoft Word is used to create a new version of the same document with a different name and file format. It is used to save the document in a different location and to save it in a different format from the original. The function is useful when a document must be saved in a different file format to be compatible with other software programs.
For more such questions on Microsoft Word, click on:
https://brainly.com/question/25813601
#SPJ8
Our accounting system runs on a server here at the office. If we put this CRM system in the cloud, does that mean we just install it on a VM server running in the cloud?
Answers
The edition of windows server 2019 that you should install on the new virtualization servers is Datacenter.
What does "datacenter" mean?This is known to be the division of an organization responsible for housing and maintaining the organization's mainframes, servers, and databases is known as the data center.
Note that When big, centralized IT operations were said to be prevalent, this division as well as all of the systems were housed in a single physical location, thereby giving rise to the moniker that is called "data center."
Therefore, The edition of windows server 2019 that you should install on the new virtualization servers is Datacenter.
Learn more about virtualization on:
https://brainly.com/question/19906390
#SPJ1
As you know computer system stores all types of data as stream of binary digits (0 and 1). This also includes the numbers having fractional values, where placement of radix point is also incorporated along with the binary representation of the value. There are different approaches available in the literature to store the numbers having fractional part. One such method, called Floating-point notation is discussed in your week 03 lessons. The floating point representation need to incorporate three things:
• Sign
• Mantissa
• Exponent
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-
point notation.
B. Determine the smallest (lowest) negative value which can be
incorporated/represented using the 8-bit floating point notation.
C. Determine the largest (highest) positive value which can be
incorporated/represented using the 8- bit floating point notation.
Answers
Answer:
A. Encode the (negative) decimal fraction -9/2 to binary using the 8-bit floating-point notation.
First, let's convert -9/2 to a decimal number: -9/2 = -4.5
Now, let's encode -4.5 using the 8-bit floating-point notation. We'll use the following format for 8-bit floating-point representation:
1 bit for the sign (S), 3 bits for the exponent (E), and 4 bits for the mantissa (M): SEEE MMMM
Sign bit: Since the number is negative, the sign bit is 1: 1
Mantissa and exponent: Convert -4.5 into binary and normalize it:
-4.5 in binary is -100.1. Normalize it to get the mantissa and exponent: -1.001 * 2^2
Mantissa (M): 001 (ignoring the leading 1 and taking the next 4 bits)
Exponent (E): To store the exponent (2) in 3 bits with a bias of 3, add the bias to the exponent: 2 + 3 = 5. Now, convert 5 to binary: 101
Now, put the sign, exponent, and mantissa together: 1101 0010
So, the 8-bit floating-point representation of -9/2 (-4.5) is 1101 0010.
B. Determine the smallest (lowest) negative value which can be incorporated/represented using the 8-bit floating-point notation.
To get the smallest negative value, we'll set the sign bit to 1 (negative), use the smallest possible exponent (excluding subnormal numbers), and the smallest mantissa:
Sign bit: 1
Exponent: Smallest exponent is 001 (biased by 3, so the actual exponent is -2)
Mantissa: Smallest mantissa is 0000
The 8-bit representation is 1001 0000. Converting this to decimal:
-1 * 2^{-2} * 1.0000 which is -0.25.
The smallest (lowest) negative value that can be represented using the 8-bit floating-point notation is -0.25.
C. Determine the largest (highest) positive value which can be incorporated/represented using the 8-bit floating-point notation.
To get the largest positive value, we'll set the sign bit to 0 (positive), use the largest possible exponent (excluding infinity), and the largest mantissa:
Sign bit: 0
Exponent: Largest exponent is 110 (biased by 3, so the actual exponent is 3)
Mantissa: Largest mantissa is 1111
The 8-bit representation is 0110 1111. Converting this to decimal:
1 * 2^3 * 1.1111 which is approximately 1 * 8 * 1.9375 = 15.5.
The largest (highest) positive value that can be represented using the 8-bit floating-point notation is 15.5.
Explanation:
Look at the following description of a problem domain:
The bank offers the following types of accounts to its customers: savings accounts, checking accounts, and money market accounts. Customers are allowed to deposit money into an account (thereby increasing its balance), withdraw money from an account (thereby decreasing its balance), and earn interest on the account. Each account has an interest rate.
Assume that you are writing a program that will calculate the amount of interest earned for a bank account.
Identify the potential classes in this problem domain.
Refine the list to include only the necessary class or classes for this problem.
Identify the responsibilities of the class or classes.
(I'm not sure what I'm supposed to do. Can anyone provide an example? Thank you!:) )
Answers
Based on the description of the problem domain, potential classes that could be identified are:
BankAccount: This class could represent the general attributes and behaviors of a bank account, such as the type of account (savings, checking, money market), balance, interest rate, and methods for depositing, withdrawing, and calculating interest.What is the bank issue about?Others are:
Savings Account: This class could inherit from the BankAccount class and include specific attributes and behaviors related to a savings account, such as any additional rules or restrictions, and methods for calculating interest specific to savings accounts.CheckingAccount: This class could inherit from the BankAccount class and include specific attributes and behaviors related to a checking account, such as any additional rules or restrictions, and methods for performing checking account-related tasks.MoneyMarketAccount: This class could inherit from the BankAccount class and include specific attributes and behaviors related to a money market account, such as any additional rules or restrictions, and methods for calculating interest specific to money market accounts.Refining the list, the necessary class or classes for this problem could be:
BankAccount: This class could represent the general attributes and behaviors of a bank account, including methods for depositing, withdrawing, and calculating interest. It could also include attributes for account type (savings, checking, money market), balance, and interest rate.
The responsibilities of the BankAccount class could include:
Managing the account balance: Methods for depositing money (increasing balance), withdrawing money (decreasing balance), and calculating interest on the account based on the interest rate.Managing account type: Storing and retrieving the type of account (savings, checking, money market).Managing interest rate: Storing and retrieving the interest rate associated with the account.Handling any other general behaviors or attributes related to a bank account that may be required in the problem domain.It's important to note that the specific responsibilities of the class or classes may vary depending on the requirements and constraints of the problem domain, and further refinement may be needed based on the actual implementation of the program.
Read more about bank here:
https://brainly.com/question/25664180
#SPJ1
What is the disadvantage of using programs to help you build a website if you have little or no understanding of markup languages?.
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least
Answers
The epa requires spray guns used in the automotive refinishing process to have transfer efficiency of at least 65 percent transfer efficiency.
What is the transfer efficiency
EPA lacks transfer efficiency requirement for auto refinishing spray guns. The EPA regulates auto refinishing emissions and impact with rules. NESHAP regulates paint stripping and coating operations for air pollutants.
This rule limits VOCs and HAPs emissions in automotive refinishing. When it comes to reducing overspray and minimizing wasted paint or coating material, transfer efficiency is crucial. "More efficiency, less waste with higher transfer rate."
Learn more about transfer efficiency from
https://brainly.com/question/29355652
#SPJ1
PLEASE HELP ITS CODING AND I INCLUDED A SCREENSHOT OF WHAT TO DO

Answers
def even_checker(lst):
for x in lst:
if x%2==0:
print(x)
l = [1,2,3,4,5,6,7,8,9,10]
even_checker(l)
I wrote my code in python 3.8. I hope this helps.
QUESTION 10
If there is an Apple logo somewhere on your computer, more than likely your computer runs what type of operating system?
O Linux
Windows
macos
Unix
Answers
Davos has been reading about encryption recently. He begins to wonder how anything can be secure if everyone is using the same set of algorithms. After all, anyone using the same algorithm would be able to decrypt anything that had been encrypted using that algorithm. Which of the following helps make the data unusable by anyone else using that same encryption scheme without having this information?
a. Algorithm
b. Cipher
c. Key
d. Block
Answers
Answer:
The correct answer is B. Cipher.
Explanation:
Cipher is a system of reversible transformations that depends on some secret parameter, called key, and is designed to ensure the secrecy of transmitted information.
The cipher can be a combination of conventional characters or an algorithm for converting ordinary numbers and letters. The process of making a message secret with a cipher is called encryption. An important parameter of any cipher is the key - a parameter of the cryptographic algorithm, which ensures the selection of one transformation from the set of transformations possible for this algorithm. In modern cryptography, it is assumed that all the secrecy of a cryptographic algorithm is concentrated in the key.
You've been called in to recommend a server for a company that's opening a new office. You're meeting with the operations manager to get preliminary information about what the company needs and will make a recommendation for this new server's hardware and OS. List the top five questions you should ask the operations manager so that you can make the best recommendation.
3) CNT-Books want an affordable way to establish remote connections for its salespeople, who log on from customer sites all over the country, and its three branch offices. The company's main office is in Phoenix, AZ, and its branch offices are in Los Angeles, CA, Chicago, IL, and Orlando, FL. Explain what kind of connections the salespeople and branch offices should use and what kinds of services should be installed on the main office's network to keep communication costs to a minimum.
Answers
Explanation:
The following question could be asked:
What is the company's budget for the new server hardware?What purpose would the server serve; email, web, print server, etc?How much data would be stored on the server?What kind of data operations would be done on the server? What is the security level placed on the data stored on the server?3. A Virtual Private network should be used by CNT-Books since it provides the needed infrastructure for remote connections by the salespeople. Services that could be installed to keep communication costs to a minimum includes;
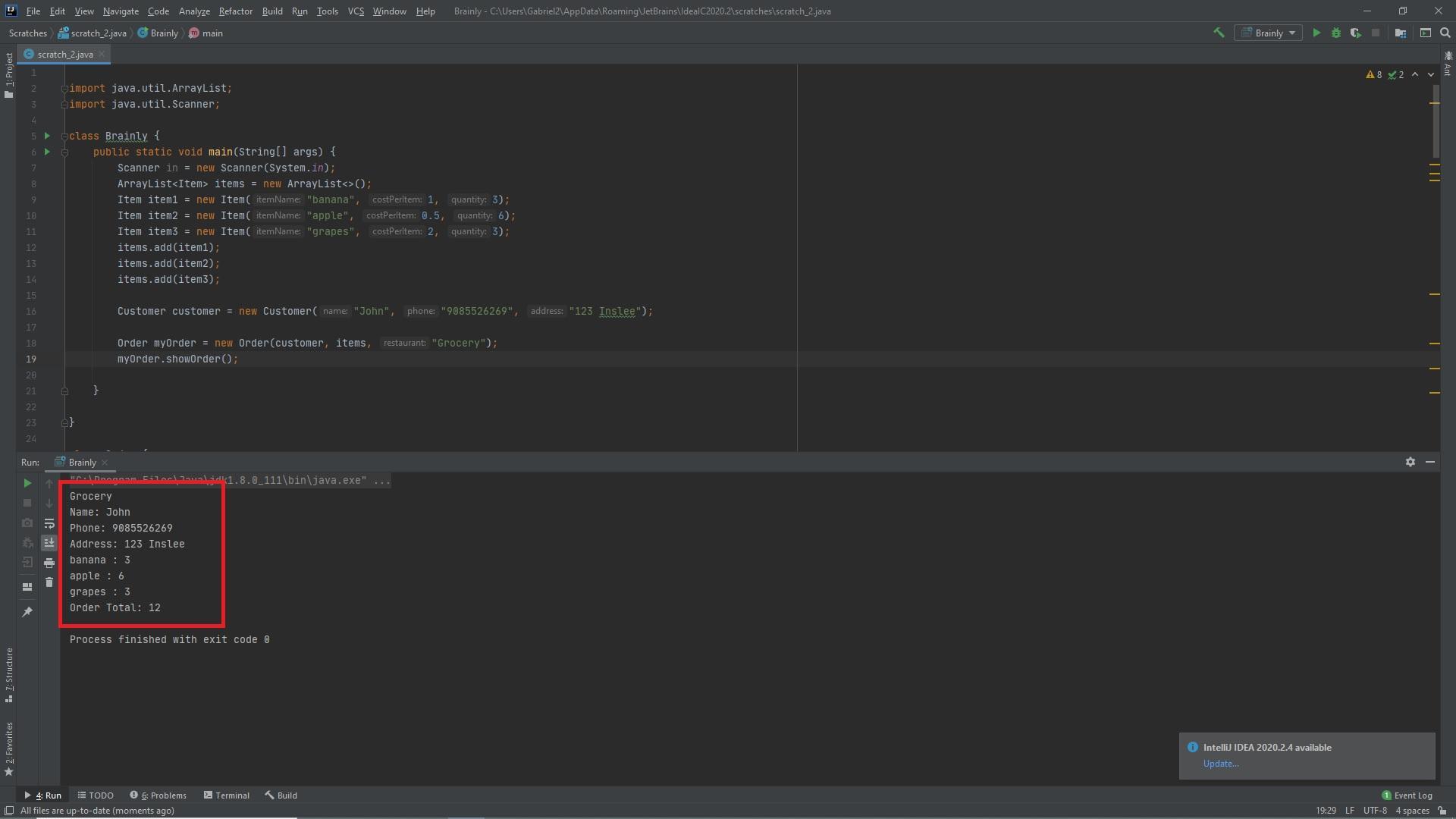
Secure Hash Algorithms-256,Advanced Encryption Standard-256.Consider an online food delivery service, such as Seamless. Customers and Items are represented by the classes given below. Your task is to create an Order class that will contain information about the customer, an ArrayList of items, and the restaurant name. Create the following methods: - a constructor to initialize these attributes - computeTotal method to compute the total of all items - showOrder method to display the information about the customer, items, and order, including the total public class Customer { private String name; private String phone; private String address; public Customer(String name, String phone, String address) { this.name
Answers
Answer:
Explanation:
Since none of the classes were provided in the question I created all of the classes so that the program works as requested in the question. I also created a test order so that you can see the output of the program in the attached picture below.
import java.util.ArrayList;
import java.util.Scanner;
class Brainly {
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
ArrayList<Item> items = new ArrayList<>();
Item item1 = new Item("banana", 1, 3);
Item item2 = new Item("apple", 0.5, 6);
Item item3 = new Item("grapes", 2, 3);
items.add(item1);
items.add(item2);
items.add(item3);
Customer customer = new Customer("John", "9085526269", "123 Inslee");
Order myOrder = new Order(customer, items, "Grocery");
myOrder.showOrder();
}
}
class Order {
Customer customer;
ArrayList<Item> items = new ArrayList<>();
String restaurant;
public Order(Customer customer, ArrayList items, String restaurant) {
this.customer = customer;
this.items = items;
this.restaurant = restaurant;
}
public void computeTotal() {
int total = 0;
for (Item x: items) {
total += x.total();
}
System.out.println("Order Total: " + total);
}
public void showOrder() {
System.out.println(restaurant);
System.out.println("Name: " + customer.getName());
System.out.println("Phone: " + customer.getPhone());
System.out.println("Address: " + customer.getAddress());
for (Item x :items) {
System.out.println(x.itemName + " : " + x.quantity);
}
computeTotal();
}
}
class Item {
String itemName;
double costPerItem;
int quantity;
public Item(String itemName, double costPerItem, int quantity) {
this.itemName = itemName;
this.costPerItem = costPerItem;
this.quantity = quantity;
}
public double total() {
double total = costPerItem * quantity;
return total;
}
}
class Customer {
private String name;
private String phone;
private String address;
public String getName() {
return name;
}
public void setName(String name) {
this.name = name;
}
public String getPhone() {
return phone;
}
public void setPhone(String phone) {
this.phone = phone;
}
public String getAddress() {
return address;
}
public void setAddress(String address) {
this.address = address;
}
public Customer(String name, String phone, String address) {
this.name = name;
this.phone = phone;
this.address = address;
}
}
Explain quantum computing in advance terms, please
(omg pizzaboy where are you?)
Answers
Quantum computers are computers that use phenomenons of quantum mechanics like superposition and quantum entanglement for computing and the process is called quantum computing.
From the time when the first computer was made and was publicly released the computer industry is growing exponentially. It thrives to make the future easier for us by making the computer faster, more efficient, and smaller than before. In spite of all these the computer industry has come to its physical limits.
Nowadays, a computer with a size of an atom is available to humankind, in the race of making the parts smaller so that it would be easy for someone to carry to operate and works efficiently at the same time.
No matter which computer we talk about all of them work on the same basic principle of taking input from the user processing it and providing the user with the output. Computers contain small chips called processors which contain basic modules, which contain logic gates, which contain transistors. Yes, it's a complicated machine but quite interesting.
In a nutshell, we can say that transistors are types of tiny switch that helps in the transfer of data throughout the processor. Now bits are used to relay data throughout the CPU where ever needed. Transistors are used to form logic gates which help in the processing of the basic arithmetical operation.
With new technologies coming out nowadays transistors are made smaller and smaller, the smallest transistors that have been formed are just 14 nanometers in size which are 500 times smaller than the actual size of the red blood cell.
The transistors are now as small as the size of an atom so they can literally transfer themselves to the other side of the blocked passage through a process called Quantum tunneling.
Physics works differently in the Quantum realm so the normal computer stops making sense. Due to this difference in physics normal computers reaches their physical limits.
In order to overcome these barriers scientist uses these unusual Quantum Properties to their advantage by creating quantum computers. The computations that are done by these computers are unusually fast.
Quantum Computing doesn't use the classic computing styles which means the use of 1 and 0 at binary bits to relay the data, in fact, it uses quantum bits or qubits which can exist in both 1 and 0 at once thus it makes the computing way faster and accurate. Quantum computing is not at all similar to normal computing, it is far superior.
Know more about Superposition at:
https://brainly.com/question/29971820
A public Wi-Fi risk that can be minimized by only visiting encrypted sites with an HTTPS indicator is: *
Junk Mail
Rogue Public Wi-Fi
Harmful Software Attacks
Snooping
Answers
Answer: Harmful software attacks is the answer
Explanation:
What characteristics are common among operating systems? List types of operating systems, and examples of each. How does the device affect the functionality of an operating system?
Answers
The operating system (OS) controls all of the computer's software and hardware. It manages files, memory, and processes, handles input and output, and controls peripheral devices like disk drives and printers.
What are the characteristics of OS?The fundamental software applications running on that hardware enable unauthorized users to interact with the equipment because instructions can be sent and results can be obtained.Developers provide technology that may be compatible, mismatched, or completely incompatible with several other OS categories across multiple versions of the same similar OS.The operating systems are frequently 32-Bit and 64-Bit in two different versions.Types of Operating System:Distributed OS .
Batch processing OS.
Time sharing OS.
To learn more about operating system refer to :
https://brainly.com/question/22811693
#SPJ1
what is the meaning of Ram?
Answers
Answer:
Random-Access Memory
Explanation:
used as a short-term memory for computers to place its data for easy access
A tech class question any help will be greatly apprieciated
Why would a programmer use a software artifact, such as a flowchart?
Answers
Answer:
With a code artifact, a software programmer can test the program in detail and perfect things before launching the software. The program can easily pass the testing phase for a project management artifact without any problems if errors are corrected at the level of the coding
Explanation:
:)
Question 2 of 8
The Layer Properties Manager shows you
Select Answer
O All of the layers
O Layer names
O Layer color
O All of these
Answers
The correct answer is All of layers. All of the layers are displayed in the Layer Properties Manager.
What is Layer Properties Manager?The Layer Properties Manager helps you organize, sort, and group layers, and allows you to work with layer standards, layer key styles, layer filters, layer overrides, and saved layer states. In the Layer Properties Manager you can perform all activities related to layers: Create, rename, and delete layers. Displays a list of the layers in the drawing and their properties. You can add, delete, and rename layers, change their properties, set property overrides in layout viewports, and add layer descriptions.
Layers and Layer Properties:
New Layer ;
Creates a layer with a default name that you can immediately change. The new layer inherits the properties of the currently selected layer in the layer list.
Layer List
Modify the layer properties using the layer list. Click the current setting to change the layer property for the selected layer or group of layers.
Note: The layer list can be filtered and sorted to make it easier to find and select the layers that you want to change.
Sort
Click a column label to sort by that column.
Column Order
Drag a column to a new location in the list to change the column order.
To learn more about layer properties manager refers to;
https://brainly.com/question/21623455
#SPJ1
Does the estimate of a tolerance level of 68.26% of all patient waiting times provide evidence that at least two-thirds of all patients will have to wait less than 8 minutes?
Answers
Answer:
Yes, because the upper limit is less Than 8 minutes
Explanation:
According to the empirical formula :
68.26% of data lies within 1 standard deviation from the mean;
Hence,
Mean ± 1(standard deviation)
The sample mean and sample standard deviation of the given data is :
Sample mean, xbar = Σx / n = 546 / 100 = 5.46
Sample standard deviation, s = 2.475 (Calculator)
The interval which lies within 68.26% (1 standard deviation is) ;
Lower = (5.460 - 2.475) = 2.985
Upper = (5.460 + 2.475) = 7.935
(2.985 ; 7.935)
Since the interval falls within ; (2.985 ; 7.935) whose upper level is less than 8 means patients will have to wait less Than 8 minutes.
Design an algorithm which generates even numbers between 1000 and 2000, print them in the standard output and gives the total sum of all the even numbers. Represent your algorithm with a corresponding pseudocode and a flowchart
Answers
Algorithms are simply the methods and procedures to solve a problem
They can be in graphical form (i.e. flowcharts)They can also be in form of texts (i.e. pseudocodes)Algorithms do not conform to programming rules, and they do not have definite syntax.The pseudocode that represents the required algorithm is as follows:
Sum = 0
For even = 1000 to 2000 step = 2
print even
sum = sum + even
print sum
The first line of the pseudocode intializes sum to 0The next line iterates through even numbers between 1000 and 2000Within the iteration, the even numbers are printed and the sum is calculatedAfter the iteration, the sum of even numbers is printedThe last line ends the pseudocodeThe above explanation is also applicable to the flowchart (see attachment)
Read more about algorithms, flowchart and pseudocode at:
https://brainly.com/question/21220060
