what are the action taken by antivirus software
Answers
Answer: Antivirus software protects your computer from incoming threats and scans your computer for current threats. They also identify any malware and block any malicious coding and software.
Related Questions
what is output? my_string = 'what is your name?' print(my_string.split('?'))
Answers
The output of the given code snippet will be: ['what is your name', '']
What is output?Student question: what is output? my_string = 'what is your name?' print(my_string.split('?'))
In the given code snippet, the given string 'what is your name?' is being split at the delimiter '?' using the 'split' method.
The 'split' method is used to split a given string into a list of strings based on the given separator. The syntax of the 'split' method is: string.split(separator, maxsplit)Where, 'separator' is the delimiter on which the string will be split, and 'maxsplit' is the maximum number of splits that can be made.
The given string 'what is your name?' has '?' as its delimiter. So, when the 'split' method is called on the string using the delimiter '?' as the argument, it will split the string into a list of two strings: 'what is your name' and '' (empty string).
Therefore, the output of the given code snippet will be: ['what is your name', '']
Learn more about programming: https://brainly.com/question/26134656
#SPJ11
What is the next line?
>>> tupleA = (5, 20, 30, 40, 30)
>>> tupleA.index(30)
3
1
0
2
Answers
Explanation:
solução de ácido clorídrico (HCI 6 m e HCI 0,6 m)
Answer:
2
Explanation:
edge 2020
Breakout:
I have my code, it’s all worked out, but my paddle doesn’t move. Where is it wrong?
/* Constants for bricks */
var NUM_ROWS = 8;
var BRICK_TOP_OFFSET = 10;
var BRICK_SPACING = 2;
var NUM_BRICKS_PER_ROW = 10;
var BRICK_HEIGHT = 10;
var SPACE_FOR_BRICKS = getWidth() - (NUM_BRICKS_PER_ROW + 1) * BRICK_SPACING;
var BRICK_WIDTH = SPACE_FOR_BRICKS / NUM_BRICKS_PER_ROW;
/* Constants for ball and paddle */
var PADDLE_WIDTH = 80;
var PADDLE_HEIGHT = 15;
var PADDLE_OFFSET = 10;
var paddle;
var setPosition;
var rectangle;
var BALL_RADIUS = 15;
var ball;
var dx = 4;
var dy = 4;
function start(){
drawBricks();
drawBALL(BALL_RADIUS, Color.black, getWidth()/2, getHeight()/2);
mouseMoveMethod(pad);
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw,20);
}
function drawBricks(){
for(var j = 0; j < NUM_ROWS;j++){
for(var i = 0; i < NUM_BRICKS_PER_ROW; i++){
var brick = new Rectangle(BRICK_WIDTH, BRICK_HEIGHT);
if((j + 1) % 8 == 1 || (j + 1) % 8 == 2){
brick.setColor(Color.red);
} else if ((j + 1) % 8 == 3 || (j + 1) % 8 == 4){
brick.setColor(Color.orange);
}else if ((j + 1) % 8 == 5 || (j + 1) % 8 == 6){
brick.setColor(Color.green);
}else if ((j + 1) % 8 == 7 || (j + 1) % 8 == 0){
brick.setColor(Color.blue);
}
brick.setPosition(BRICK_WIDTH * i + BRICK_SPACING * (1 + i), BRICK_TOP_OFFSET + BRICK_HEIGHT * j + BRICK_SPACING * (1 + j));
add(brick);
}
}
}
function drawBALL(BALL_RADIUS, color, x, y){
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw, 20);
}
function draw(){
checkWalls();
ball.move(dx, dy);
}
function mousemoveMethod(pad){
ball = new Circle (BALL_RADIUS);
ball.setPosition(200, 200);
add(ball);
setTimer(draw, 20);
}
function checkWalls(){
if(ball.getX() + ball.getRadius() > getWidth()){
dx = -dx;
}
if(ball.getX() - ball.getRadius() < 0){
dx = -dx;
}
if(ball.getY() + ball.getRadius() > getHeight()){
dy = -dy;
}
if(ball.getY() - ball.getRadius() < 0){
dy = -dy;
}
var elem = getElementAt(ball.getX(), ball.getY() - ball.getRadius());
if (elem != null) {
dy = -dy;
remove(elem);
}
elem = getElementAt(ball.getX(), ball.getY() + ball.getRadius());
if (elem != null) {
dy = -dy;
}
}
function pad(e){
paddle = new Rectangle(PADDLE_WIDTH, PADDLE_HEIGHT);
paddle.setPosition(getWidth()/2 - paddle.getWidth()/ 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
mouseMoveMethod(pad);
add(paddle);
}
Answers
In your code, I can see a few issues that might be causing your paddle not to move correctly:
In the mousemoveMethod(pad) function, you have defined pad as a parameter, but you're not using it within the function. Instead, you should use the e parameter, which represents the mouse event. Modify the function to use e instead of pad.
You are calling the mousemoveMethod(pad) function inside the pad(e) function. This creates an infinite loop and may cause unexpected behavior. You should remove the mousemoveMethod(pad) function call from the pad(e) function.
The mousemoveMethod(pad) function is creating a new circle and adding it to the canvas, which is unnecessary for moving the paddle. Instead, you should update the position of the existing paddle based on the mouse movement. Modify the mousemoveMethod(pad) function as follows:
javascript
Copy code
function mousemoveMethod(e) {
var x = e.getX();
paddle.setPosition(x - paddle.getWidth() / 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
}
Make sure to update all the function calls and event listeners accordingly.
By making these changes, your paddle should move correctly based on the mouse movement.
I apologize for the confusion. It seems that there was a mistake in my previous response. In the provided code, the mouse event parameter is not being passed correctly to the mousemoveMethod function. To fix this issue, you can modify your code as follows:
In the pad(e) function, change the line mouseMoveMethod(pad); to mouseMoveMethod(e);. This will pass the mouse event parameter to the mousemoveMethod function correctly.
Modify the mousemoveMethod function to access the mouse coordinates correctly. Use e.getX() and e.getY() to get the current mouse position. Update the paddle position accordingly:
javascript
Copy code
function mousemoveMethod(e) {
var x = e.getX();
paddle.setPosition(x - paddle.getWidth() / 2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
}
With these changes, the paddle should move correctly based on the mouse position.
The mouseMoveMethod function is not correctly defined. The parameter "pad" is not necessary and should be removed. Instead of calling mouseMoveMethod(pad) inside the pad function, you should call the mouseMoveMethod function directly.
Here's the corrected code for the pad function:
function pad(){
paddle = new Rectangle(PADDLE_WIDTH, PADDLE_HEIGHT);
paddle.setPosition(getWidth()/2 - paddle.getWidth()/2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
add(paddle);
mouseMoveMethod();
}
The mousemoveMethod function is unnecessary and can be removed. It is also misspelled, as the correct name is mouseMoveMethod (with a capital 'M'). You can directly include the code to handle the mouse movement inside the pad function.
Here's the corrected code for the mouseMoveMethod:
function mouseMoveMethod(){
onMouseMove(function(e){
paddle.setPosition(e.getX() - paddle.getWidth()/2, getHeight() - paddle.getHeight() - PADDLE_OFFSET);
});
}
By making these corrections, your paddle should now move according to the mouse movement.
how are web design & web development different from each other?
Answers
Answer:
Developers are people who build a website's core structure using coding languages, while designers are more visually creative and user-focused. Developers use their programming knowledge to breathe life into the designer’s creative vision.
You could think of developers as construction workers, and web designers as architects – both necessary, but different, skill sets.
I hope this helped :D
Explanation:
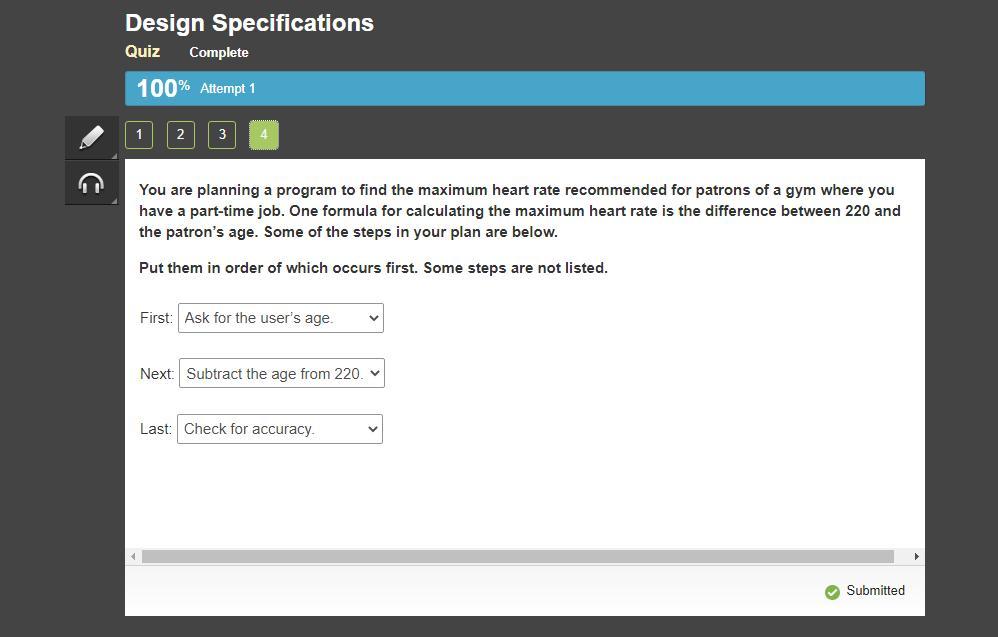
You are planning a program to find the maximum heart rate recommended for patrons of a gym where you have a part-time job. One formula for calculating the maximum heart rate is the difference between 220 and the patron’s age. Some of the steps in your plan are below.
Put them in order of which occurs first. Some steps are not listed.
Answers
Answer:
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Explanation:
The programs will be as follows
Age = int(input(Enter your age? "))
print(f"Your maximum heart rate is {220 - age}.")
Answer:
got 100 on the quiz
Explanation:
What values may be variables or expressions passed on to the function and are normally found in the function call
Answers
The values that may be variables or expressions passed on to the function and are normally found in the function call are called arguments.
When calling a function, arguments are provided within the parentheses. They can be variables or expressions that provide specific values or data to be used by the function during its execution. Arguments can be of various types, such as numbers, strings, booleans, or even more complex data structures like arrays or objects.
Passing arguments to a function allows for flexibility and customization, as it enables the function to work with different values each time it is called. The function can then utilize these arguments to perform specific operations or calculations, return results, or modify external variables.
Learn more about argument here:
https://brainly.com/question/30468303
#SPJ11
Specify the correct order of the steps necessary for adding a Nano Server to a domain.
Connect to the Nano Server with the EnterPSSession cmdlet.
On a domain controller, run the djoin.exe cmdlet.
Configure the Windows Firewall on the Nano Server.
Copy the odjblob file to the NanoServer and use the djoing command.
Reboot the Nano Server.
On a domain controller, use the Set-Item WSMan cmdlet that will add the computer to the trusted host list.
Answers
The correct order for adding a Nano Server to a domain is: Configure the Windows Firewall, Copy the odjblob file, Run the djoin.exe cmdlet, Reboot the Nano Server, Connect with EnterPSSession, Use Set-Item WSMan.
To add a Nano Server to a domain, the following steps should be followed in the correct order:
1. Configure the Windows Firewall on the Nano Server: This ensures that necessary communication can take place between the server and the domain.
2. Copy the odjblob file to the Nano Server: This file contains the necessary domain join information.
3. Run the djoin.exe cmdlet on a domain controller: This command is used to add the Nano Server to the domain.
4. Reboot the Nano Server: This step ensures that any changes made take effect.
5. Connect to the Nano Server with the EnterPSSession cmdlet: This allows remote management of the Nano Server.
6. Use the Set-Item WSMan cmdlet on a domain controller: This adds the Nano Server to the trusted host list, enabling remote management and communication with the server.
Following these steps in the specified order ensures a successful addition of the Nano Server to the domain.
learn more about Nano Server here:
https://brainly.com/question/17190997
#SPJ11
What are the knowledge gaps, future challenges to risk
assessment and experimental evaluation of risk with respect to
nanotechnology?
Answers
The knowledge gaps and future challenges in risk assessment and experimental evaluation of nanotechnology arise from limited understanding of long-term effects, lack of standardized protocols.
Nanotechnology, the manipulation and utilization of materials at the nanoscale, holds great promise for numerous industries. However, as with any emerging technology, there are knowledge gaps and challenges in assessing and evaluating the risks associated with its use.
One of the main knowledge gaps lies in our understanding of the long-term effects of nanomaterials on human health and the environment. While short-term studies have provided valuable insights, the potential for chronic exposure to these materials and their accumulation over time remains largely unknown. Longitudinal studies are needed to assess the potential risks and health impacts over extended periods.
Another challenge is the lack of standardized protocols for risk assessment and evaluation. Nanotechnology is a diverse field, encompassing various materials, manufacturing processes, and applications. The lack of standardized procedures hinders the comparability and reproducibility of experimental results, making it difficult to draw definitive conclusions about the risks associated with specific nanomaterials or applications.
Comprehensive toxicity studies are also essential to address the challenges in risk assessment. Nanomaterials can exhibit unique properties that differ from their bulk counterparts, and their interactions with biological systems are complex. To accurately evaluate the risks, it is crucial to conduct thorough toxicity studies that consider factors such as particle size, surface chemistry, and exposure routes.
In summary, the knowledge gaps and future challenges in risk assessment and experimental evaluation of nanotechnology stem from limited understanding of long-term effects, lack of standardized protocols, and the need for comprehensive toxicity studies. Addressing these gaps and challenges will contribute to the responsible development and safe implementation of nanotechnology in various industries.
Learn more about knowledge gaps
brainly.com/question/31801064
#SPJ11
Instructions
Write a one-line program to output the following haiku. Keep in mind that for a one-line program, only one print command is used.
Moon and stars wonder
where have all the people gone
alone in hiding.
- Albrecht Classen.
Hint: Remember that the escape sequences \n and \t can be used to create new lines or tabs for extra spacing.
Answers
Answer:
python
Explanation:
print("Moon and stars wonder\nwhere have all the people gone\nalone in hiding.\n- Albrecht Classen.")
how do hand tools,Farm implements and farm equipment differ from one another
Answers
Which of the following would have a quadratic Big O run-time complexity? Retrieve the element at a given index in an array none of these Multiply two numbers by long-hand Find the word that fits a given definition in a dictionary Crack a binary passcode of n digits by brute force
Answers
The task "Crack a binary passcode of n digits by brute force" would have a quadratic Big O run-time complexity.
Which task would have a quadratic Big O run-time complexity: Retrieving the element at a given index in an array, multiplying two numbers by long-hand, finding the word that fits a given definition in a dictionary, or cracking a binary passcode of n digits by brute force?why "Crack a binary passcode of n digits by brute force" would have a quadratic Big O run-time complexity:
To crack a binary passcode by brute force, you would systematically generate and check all possible combinations of binary digits until you find the correct passcode. Since the passcode has n digits, there are a total of 2^n possible combinations.
In the worst-case scenario, where the correct passcode is the last combination you check, you would need to go through all 2^n combinations. As the number of digits (n) increases, the number of combinations grows exponentially.
When analyzing the time complexity, we consider the number of operations required as a function of the input size. In this case, the input size is the number of digits (n). Each combination requires constant time to generate and check, so the overall time complexity can be expressed as O(2^n).
Since the time complexity is exponential in terms of the input size, it is considered to have a quadratic Big O run-time complexity.
Note that the other options mentioned in the question do not have a quadratic complexity:
- Retrieving the element at a given index in an array has a constant time complexity of O(1).
- Multiplying two numbers by long-hand typically has a linear time complexity of O(n) where n is the number of digits in the numbers.
- Finding a word that fits a given definition in a dictionary would have a complexity dependent on the size of the dictionary and the specific algorithm used, but it would typically be more efficient than quadratic complexity.
Learn more about quadratic Big
brainly.com/question/28860113
3SPJ11
What part of the computer is responsible for executing instructions to process information?.
Answers
Answer:
The computer does its primary work in a part of the machine we cannot see, a control center that converts data input to information output. This control center, called the central processing unit (CPU), is a highly complex, extensive set of electronic circuitry that executes stored program instructions.
Explanation:
Short: Central Processing Unit or CPU
1
Camile owns Crunch Code, a company that provides quick programming solutions. Clients send Crunch projects via their web page and Crunch bangs out the needed code as quickly as possible. Camile has seven programmers who do all of the coding. On average, a project arrives once every 41 hours, with a standard deviation of 4.3 hours. Each project is assigned to one programmer and that programmer takes on average 19.3 hours to complete each project with a standard deviation of 19.3 hours.
003402)
Round to nearest integer
How many uncompleted projects does Crunch Code have on average at any given time? (Include projects waiting for a programmer as well as those being programmed.)
Answers
On average, Crunch Code has approximately 0.471 uncompleted projects at any given time. This means that, statistically, there are no uncompleted projects waiting for a programmer or being actively programmed, assuming the arrival rate and completion time follow the given averages and the system is in steady-state.
To calculate the average number of uncompleted projects at any given time for Crunch Code, we need to consider the arrival rate of projects and the time taken to complete a project by a programmer. We can use the concept of Little's Law, which relates the average number of customers in a system to the arrival rate and the average time spent in the system.
Let's denote the average number of uncompleted projects as L, the arrival rate of projects as λ (projects per hour), and the average time taken to complete a project by a programmer as W (hours).
Given:
- Arrival rate (λ) = 1 project every 41 hours
- Average time taken to complete a project (W) = 19.3 hours
First, we need to convert the arrival rate to projects per hour:
λ = 1 / 41 projects per hour
Now, we can use Little's Law to calculate the average number of uncompleted projects:
L = λ * W
Substituting the values:
L = (1 / 41) * 19.3
Calculating the value:
L ≈ 0.471
Learn more about code here:
https://brainly.com/question/17204194
#SPJ11
A new printer has been added in your office and connected to a WAP for use by all users in the company.Which of the following best describes the method of connectivity for the new printer?a. Wireless ad hoc modeb. Wireless Bluetoothc. Wireless infrastructure moded. Wired Ethernet
Answers
The best method of connectivity for the new printer would be in wireless infrastructure mode.
Explanation:
This is because wireless infrastructure mode makes use of a wireless access point (WAP) to connect wireless devices to a wired network. In this case, the new printer has been added to the office and connected to a WAP, which can be used by all users in the company. Therefore, wireless infrastructure mode is the best way to connect the new printer in the office.
How do I connect a printer using wireless infrastructure mode?
To connect a printer using wireless infrastructure mode, follow the below steps:
Step 1: Connect the printer to a power source and turn it on.
Step 2: Use the printer's control panel to find the wireless network setup wizard and enter the Wi-Fi network name and password.
Step 3: Once the printer is connected to the wireless network, locate the printer's IP address from the control panel.
Step 4: Use a computer that is also connected to the same wireless network and open a web browser to enter the printer's IP address.
Step 5: Follow the on-screen instructions to install the printer driver and complete the printer setup.
Learn more about infrastructure mode here:
https://brainly.com/question/30029077
#SPJ11
1) what data does the player class contain? 2) why is the playernode class needed? 3) what is a linked list? 4) what is the purpose of the shelllinkedlist class? 5) what is the playerlinkedlist and why is it needed? 6) what is a queue and how does it relate to a linked list? 7) what is the purpose of the playerqueuelinkedlist class?
Answers
The player class contains player data, playernode aids in linked list creation, linked list stores elements linearly, shelllinkedlist implements linked list operations, playerlinkedlist manages players, queue follows FIFO, and playerqueuelinkedlist implements a player queue using a linked list.
1. The player class usually contains data about the player's name, score, and other information relevant to the game.
2. The playernode class is required because it aids in the creation of a linked list by providing a blueprint for a single node in a linked list. A node is an item in a linked list that contains both data and a reference to the next item in the list.
3. A linked list is a data structure that stores a collection of elements in a linear order. It consists of nodes that contain data and references to the next item in the list.
4. The shelllinkedlist class is a class that implements a linked list by keeping track of the first node in the list and providing methods to add, remove, and iterate over the nodes.
5. The playerlinkedlist is a linked list that contains a collection of player objects. It is needed to manage the players in a game, such as adding or removing players and keeping track of their scores.
6. A queue is a data structure that follows the First In First Out (FIFO) principle, where the first element added to the queue is the first one to be removed. A queue can be implemented using a linked list by adding elements to the tail of the list and removing elements from the head of the list.
7. The playerqueuelinkedlist class is a class that implements a queue by using a linked list to manage a collection of player objects. It is used to add players to a waiting list and remove them when it is their turn to play.
Learn more about FIFO: brainly.com/question/24137318
#SPJ11
Add me as a friend on Real pool 3D so we can play a round of pool!!!
Answers
I will but i have to wait till after 3;00 will you still be online by then. If not you can just friend me and message me when you are today
First Person Who Answers Fast As Possible Will Be Marked As Brainiest
Answers
Answer:
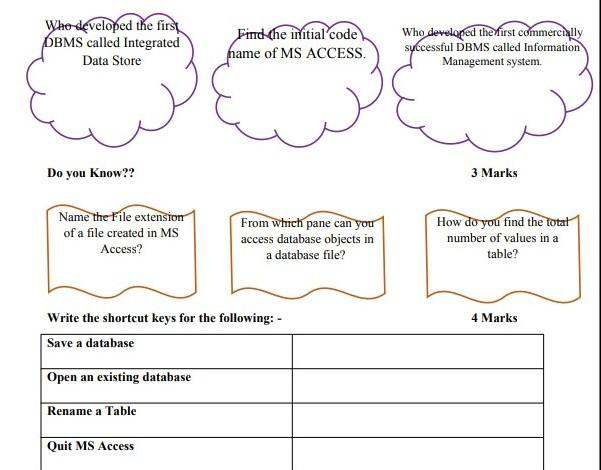
Save a database object Ctrl+S or Shift+F12
Open an existing database Ctrl+O or Ctrl+F12
To quit MS Access ALT+F4
Explanation:
This is a python program.
I managed to get this program to say hello to a user after they input their first and last name, however, I cannot manage to get the program to tell the user how many letters are in the user's name.

Answers
Answer:
word = input("Type your name: ")
print(len(word))
Explanation:
The len function will count all the chars in the string.
2. which core domain includes connection and closeness with others?
Answers
The core domain that includes connection and closeness with others is the social domain. The social domain refers to the relationships between an individual and other people, including the capacity to form and maintain interpersonal connections, attachments, and social networks.
Social domain comprises social interaction, communication, and emotional regulation, as well as the ability to read and interpret social cues and to understand the social rules that govern interpersonal relationships.
In early childhood development, social skills play a significant role as they allow children to establish relationships and connect with other people. They learn to communicate their needs and emotions, engage in imaginative play, and work together to solve problems.
Socialization is also critical in shaping a child's personality, behavior, and self-esteem.
In conclusion, the social domain is essential in a child's holistic development as it enables them to build and maintain relationships, closeness with others, and function effectively in society.
To learn more about closeness: https://brainly.com/question/29457666
#SPJ11
how drone technology can impact recreation and entertainment
Answers
Drones are become more advanced than ever before. Are now, they are starting to impact recreation. They are small, light, and can maneuver incredibly fast. They are being used in movies, skits, short films, and even high-end videos. Here are some ways drones are changing entertainment:
- Providing high-quality filming, even from 200 feet in the air.
- Reaching spaces where bulky helicopters cannot fit into safely
- Laser shows, where drones shine lights and lasers.
Right now, if you tried to hold your phone still to capture a video, you would not be able to do it. Upon checking the footage, you would see the camera shaking, even if it's just tiny bit. While you can lean it on a surface to fix this, it simply cannot be done in the air to capture. Not to worry, though, you've got drones. They can shoot a steady shot 200 feet in the air. The only thing that could rival drones are expensive, bulky choppers. The drones are cheaper and are mass produced.
However, drones are not only being used to filming movies and films. They are also being used for a different kind of entertainment: Shows. Drones move in formation and shine lights in the night sky, like we saw in the Winter Olympics. They are truly stunning(pics attached).

Instructions - recreate the brochure in the example in the included
PDF file.
Go to the Layout menu and change the columns from one to three
columns.
Change the orientation from portrait to landscape
Answers
To recreate the brochure from the provided PDF file, follow these instructions. First, go to the Layout menu and change the columns from one to three columns. Change the orientation from portrait to landscape.
To recreate the brochure in the provided PDF file, you need to make a few adjustments to the layout. Begin by accessing the Layout menu in your preferred design software or word processor. Locate the option to modify the number of columns and change it from one column to three columns. This adjustment will divide the content into three equal-width columns, allowing you to fit more information on each page and creating a visually appealing layout.
Next, you need to change the orientation of the brochure from portrait to landscape. Look for the orientation settings in the same Layout menu or in the Page Setup options, depending on the software you are using. Switching to landscape orientation will widen the page horizontally, providing more space for content and making it easier to arrange text and images in a visually pleasing manner.
By following these instructions and making these modifications, you can recreate the brochure in the provided PDF file. Remember to adjust the content accordingly to fit the new layout and take advantage of the increased space provided by the three-column, landscape format.
Learn more about PDF file here:
https://brainly.com/question/30470794
#SPJ11
A photograph is created by what
A) Silver
B) Shutters
C) Light
4) Mirror
Answers
A photograph is created by Light.
What are photographs made of?Any photograph created is one that is made up of Support and binders.
The steps that are needed in the creation of a photograph are:
First one need to expose or bring the film to light.Then develop or work on the imageLastly print the photograph.Hence, for a person to create a photograph, light is needed and as such, A photograph is created by Light.
Learn more about photograph from
https://brainly.com/question/25821700
#SPJ1
What are the missing whole numbers on this number line? Enter your answers in the boxes. plz show work I'm I need answer 3rd grade

Answers
Which statement supports the benefits of computer-aided design (CAD)?
Privacy is increased.
Designers do not have to be creative.
O Businesses have more control over their designers.
Time and materials are saved.
A. privacy is increased
B. designers do not have to be creative
C. businesses have more control over their designs
D. Time and materials are saved
Answers
Answer:
The correct statement that supports the benefits of computer-aided design (CAD) is "time and materials are saved."
Explanation:
CAD allows designers to create and modify designs quickly and easily using a computer, rather than having to create physical prototypes or drawings. This can significantly reduce the time and materials needed to create and revise designs, as changes can be made digitally rather than having to create new physical models or drawings.
Option A ("privacy is increased") is not a benefit of CAD.
Option B ("designers do not have to be creative") is incorrect because CAD does not replace the need for creativity and design skills.
Option C ("businesses have more control over their designs") is a potential benefit of CAD, but it is not the primary benefit of the technology.
Besides the tool bar panel, where else can you change the stroke and fill colors of selected objects?
O timeline
O properties panel
O on the stage
O library panel
Answers
Advantages & Disadvantages of flow chart
Answers
Answer:
Advantages of flow charts:
1. Communication where flowcharts are a more effective technique of explaining a system's rationale to all parties involved.
2. Efficient interpretation by using a flowchart, a problem can be investigated more effectively, resulting in lower costs and less time wasted.
3. Appropriate documentation such when program flowcharts serve as good documentary evidence, that is required for a variety of objectives, allowing things to run more smoothly.
4. Effective Coding where during the systems analysis and software development phases, the flowcharts serve as a guide or blueprint.
5. Practical Debug where the flowchart assists with the debugging process.
6. Efficient Program Maintenance by using a flowchart, it is simple to maintain an operational program. It allows the programmer to focus his efforts more effectively on that section.
Disadvantages of flow charts:
1. Manual traceability is required to ensure the accuracy of the flowchart drawn on paper.
2. Simple changes to the problem reasoning may necessitate a complete redo of the flowchart.
3. Displaying many branches and looping in flowchart is challenging.
4. When dealing with a complicated project or algorithm, the flowchart becomes very challenging and imprecise.
5. It can take some time to modify a flowchart.
Words like denigrate, the undersigned, and expropriate are examples of high-level diction and should be used liberally in business messages because they will make you sound more professional. Group of answer choices True False
Answers
The given statement is false. Words like denigrate, the undersigned, and expropriate are examples of high-level diction and should not be used liberally in business messages as they tend to make messages sound pretentious and obscure.
Instead, using clear, concise, and easy-to-understand language will make a message sound more professional and effective. The use of high-level diction may also cause confusion and misunderstanding. Therefore, it is important to use appropriate language in business messages.
High-level diction words like denigrate, the undersigned, and expropriate should not be used liberally in business messages as they may make the message sound pretentious and obscure. It is important to use appropriate and easy-to-understand language to make the message sound professional and effective.
To know more about High-level diction visit:
brainly.com/question/1558009
#SPJ11
Using high-level diction in business messages can enhance professionalism, but it should be used thoughtfully and in moderation.
Hence it is false.
False. While using a diverse range of vocabulary is important to convey professionalism in business messages, it's equally important to consider the audience and context. High-level diction should be used judiciously, ensuring clarity and understanding for all readers.
Using excessively complex or unfamiliar words may actually hinder effective communication. It's best to strike a balance and choose words that are appropriate for the specific situation and audience.
To learn more about vocabulary visit:
https://brainly.com/question/24702769
#SPJ4
Larry has created a web page using HTML 4.01. He hasn’t included the declaration in the file. When he opens the page in a browser, Larry sees a page load error. Why does Larry need to use the declaration in an HTML file?
A.
to define the HTML version in which the page is written
B.
to define the web language in which the page is written
C.
to tell the browser what the content is
D.
to check whether the code is error-free
Answers
Answer:
To define the html version in which the page is written.

problem 1. (40 points) consider the following relational database: student ( student number , name ) course ( course number , year , semester , classroom ) registration ( ? ? ? ) (a) (10 points) identify an appropriate primary key for each of the student and course relations. assume that (i) each student is assigned a unique number, (ii) for each combination of year and semester (e.g., 2023 spring), each course is assigned a unique course number, and (iii) a course with a certain course number (e.g., csi 410) may have been offered multiple times (e.g., 2022 fall and 2023 spring). explain why the primary key that you have chosen for the course relation is a candidate key. (b) (10 points) given your choice of primary keys for the student and course relations, identify appropriate attributes for the registration relation. this registration relation must store data regarding the courses that each student has taken. assume that a student may have taken a course (e.g., csi 410) multiple times (e.g., 2022 spring and 2022 fall). also, identify an appropriate primary key for the registration relation. (c) (10 points) given your choice of primary keys, identify all of the foreign keys. for each foreign key, specify the referencing and referenced relations. (d) (10 points) describe a situation where an attempt to update the registration relation violates a foreign key constraint. explain why your answer is correct.
Answers
Removing a row from a foreign key table while leaving the related entry in the primary key table intact.
Using a referential integrity rule will prevent you from adding data to table Y that cannot be linked to data in table X. In order to maintain referential integrity, any records that are linked to a removed record from table X must also be deleted. A database is considered to be in referential integrity when all values for all foreign keys are valid. Foreign keys are a column or set of columns in a table that must contain values that correspond to at least one of the main key or unique key values of a row in its parent table. The necessary entry from the linked primary key table must still be present when removing a row from a database with foreign keys.
Learn more about Referential integrity here:
https://brainly.com/question/29534597
#SPJ4
1. what is software ?
2.what is computer ?
3.who is the father of the computer ?
4.what is operating system ?
Answers
Answer:
A software is just a computer program made up of other several programs that work in conjunction with each other to perform a given task.
A computer is an electronic device that accepts raw data as input and processes it into useful information.
Charles Babbage, the inventor of digital programmable computers, is recognized as the father of computers.
Operating system is a system software that provides an interface by which a user can interact with every service and component in a computer.