What best describes the effect of the sensory imagery used in this excerpt?.
Answers
The sensory imagery used in this excerpt presents a vivid description of the setting and evokes a strong emotional response from the reader. It helps to create a sense of place and atmosphere, immersing the reader in the experience of the character and making the scene more memorable.
Sensory imagery is the use of vivid descriptions that engage the reader's senses of sight, sound, touch, taste, and smell. In this excerpt, the author uses sensory imagery to create a vivid description of the setting, which helps to establish the mood and atmosphere of the scene. The reader can picture the snow-covered mountains, the sound of the river, and the icy wind blowing through the trees. This sensory imagery also evokes an emotional response in the reader, making the scene more memorable and impactful. The use of sensory imagery is an effective way to draw the reader into the story and bring the setting to life.
In conclusion, the effect of the sensory imagery used in this excerpt is to create a vivid description of the setting and evoke a strong emotional response from the reader. By engaging the reader's senses, the author makes the scene more memorable and immersive, drawing the reader into the story and making them feel like they are a part of the experience. The use of sensory imagery is an effective tool for creating a sense of place and atmosphere in a story.
To know more about sensory imagery visit:
https://brainly.com/question/30105628
#SPJ11
Related Questions
why was the tesla model s help change the was we see EV
Answers
Answer:
It showed people that electric cars are advancing, and soon will be the norm.
Lots of people thought that EV cars would never be able to last as long as gas powered cars. However, with technology importing, Tesla cars are getting closer and closer to being able to provide the same amount of millage as the gas powered cars.
This is used to track a user’s browser and download history with the intent to display popup banner ads that will lure a user into making a purchase.
Select one:
Adware
Worm
Phishing
Malware
Answers
Answer:
Adware
Explanation:
Adware is software designed to display advertisements on your screen, most often within a web browser.
Hope that helps.
A software that used to track a user’s web browser and download history with the intent to display popup banner adverts (ads) that will lure an end user into making a purchase is: A. Adware.
An adware is also referred to as an advertisement-supported software and it can be defined as a software application (program) that is designed and developed to automatically display advertising materials such as banners or pop-up adverts (ads) on the graphical user-interface (GUI) of a user's computer system or mobile device.
The main purpose for the development of an adware is to automatically display popup banner adverts (ads), in order to lure or convince an end user into making purchase of the advertised product or service.
In conclusion, an adware is a software that is typically used to track and gather information about a user’s web browser and download history with the intent to display popup banner adverts (ads) that will lure an end user into making a purchase.
Read more on adware here: https://brainly.com/question/9692296
A computer screen that is contained in its own case and is not part of the computer system is called a

Answers
Answer:
Monitor is the correct answer
Answer:
display
Explanation:
what is system software ? write it's type ?
Answers
The types are Operating system, Utility software and language processor
Today, scientists agree that good research is ethical in nature and is guided by basic respect for human dignity and safety. However, as you read in the Tuskegee Syphilis Study, this was not the case. Discuss any THREE (3) the ethical violations in the study
Answers
Answer:
Ethical violations in the Tuskegee Syphilis Study
1) Discrimination. Syphilis was recognized as a disease with a major impact on the afro-descendant and in poor conditions population. The studied population was not treated fairly, they were selected from a vulnerable group. Against the bioethical principles of justice.
2) The ethical principle of beneficence was violated since the participants did not have a real benefit from their participation and in the case of the sick people, they had no option to be treated (in 1947 penicillin was already used as a treatment).
Due to the ignorance of the study, the general population was affected by the transmission of the infectious disease.
3) There was no informed consent against the autonomy principle of clinical Ethic. People were studied for about 40 years (1932 - 1972) with no information about it.
Explanation:
It was a study conducted by the Public Health Service in the city of Tuskegee (Alabama). The objective was the study of the natural progression of syphilis.
The controversies regarding this study were related to the fact that it was conducted in an African American and literate population that was not informed and did not have access to treatment.
true or false? the benefit of replay attacks is when the attacker has already broken the session key presented in the replayed messages.
Answers
False. The benefit of replay attacks is not necessarily dependent on whether the attacker has already broken the session key presented in the replayed messages.
A replay attack is a type of cyber attack where an attacker intercepts and re-transmits a previously captured message with the intent of causing harm or gaining unauthorized access.
The attacker may be able to use the replayed message to gain access to sensitive information or resources without having to go through the authentication process again. Replay attacks can be prevented by using techniques such as nonce values, timestamps, and sequence numbers to ensure that messages cannot be replayed. Nonce values are random numbers that are used only once in a communication session to prevent replay attacks. Timestamps can be used to ensure that messages are only accepted within a certain time period, while sequence numbers can be used to ensure that messages are processed in the correct order and cannot be replayed out of sequence. In summary, replay attacks can be a serious threat to the security of a system or communication session, but the benefit of the attack is not dependent on whether the attacker has already broken the session key presented in the replayed messages.Know more about the replay attacks
https://brainly.com/question/25807648
#SPJ11
Consider yourself as a leader of a team, in what ways can you create environments in which diverse teams achieve success? What are potential challenges?
Answers
Creating a successful diverse team can be challenging, and potential challenges include communication barriers, bias, and conflicts that may arise due to different beliefs, values, and cultural norms.
To overcome these challenges, it is important to establish open communication channels and encourage team members to share their thoughts and ideas freely. Regular team-building activities, such as cultural potlucks, can help break down barriers and create a sense of belonging.
Another potential challenge is unconscious bias. Leaders can address this by providing bias awareness training for their team and encouraging team members to recognize and challenge their biases.
Additionally, leaders can take steps to ensure that hiring practices are unbiased, and that team members are evaluated based on their performance and not their demographic.
Learn more about leader https://brainly.com/question/32319795
#SPJ11
Shonda is tasked with creating a network structure that would come up with a speedy decision. Which of the following small group network structures should she avoid?
a. wheel
b. both wheel and all - channel
c. chain
d. all-channel
Answers
Shonda should avoid the all-channel network structure. Option D is the correct answer.
The all-channel network structure is characterized by every member of the group being connected to every other member. While this type of structure may seem ideal for speedy decision-making due to its high connectivity, it often leads to information overload, decreased efficiency, and difficulty in reaching a consensus. With too many channels of communication, it can be challenging to manage the flow of information and make decisions quickly.
On the other hand, the wheel network structure has a central person who controls the flow of information and decision-making, which can streamline the process. The chain network structure involves linear communication between members, allowing for efficient transmission of information. Both of these structures offer more focused communication channels compared to the all-channel structure.
Therefore, Shonda should avoid the all-channel network structure. Option D is the correct answer.
You can learn more about communication channels at
https://brainly.com/question/848260
#SPJ11
One of the big components of UI design concerns where items are positioned on the screen. What is the term for this positioning?
A.
menu
B.
scale
C.
strategy
D.
layout
Answers
One of the big components of UI design concerns where items are positioned on the screen. The term for this positioning is "layout" (Option D)
What is UI Design?User interface design, also known as user interface engineering, is the process of creating user interfaces for equipment and software such as laptops, household appliances, mobile devices, and other electronic devices with the goal of increasing usability and user experience.
Responsibilities of a UI/UX Designer include:
In coordination with product managers and engineers, gather and evaluate user needs. Using storyboards, process flows, and sitemaps to illustrate design concepts. Creating visual user interface components like menus, tabs, and widgets.
Learn more about UI Design:
https://brainly.com/question/15420719
#SPJ1
What is an example of a manufactured product ?
A. A shirt purchased at a store
B. Cotton in a field
C. Wood on a sheep’s back
D. Silk made from a worm
Answers
Answer:
A shirt purchased at a store
Explanation:
Name a utility that will help achieve better data organization and processing performance on a
computer by eliminating unnecessary fragments and rearranging files and unused disk space.
(1 point)
O backup
O anti-virus
O disk defragmenter
O character map
Answers
Answer:
Disk defragmenter
Explanation:
A disk defragmenter is a utility that can help achieve better data organization and processing performance on a computer by eliminating unnecessary fragments and rearranging files and unused disk space. This can be particularly useful for optimizing the performance of a computer that has been in use for an extended period of time, as the accumulation of fragments and disorganized data can negatively impact the speed and efficiency of the system. By using a disk defragmenter, users can ensure that their computer is functioning at its best, and can make it easier to locate and access specific files and data.
you are working in the headquarters of an organization and you're asked to deal with the interruption in services due to network issues found in the isp servers. how will you tackle this situation?
Answers
Using NIC teaming is the way to tackle the situation.
What is network?Network is defined as a network of linked computers, servers, mainframes, peripherals, network devices, or other devices that facilitate data sharing. Because it is a global network of computers connected by telephone and cable lines, the Internet is known as a network of networks and allows for communication between them.
Users can combine two or more physical NICs into a single logical network device known as a bond via NIC teaming. The virtual machine is unaware of the underlying physical NICs after a logical NIC is configured.
Thus, using NIC teaming is the way to tackle the situation.
To learn more about network, refer to the link below:
https://brainly.com/question/15088389
#SPJ1
Which of these is NOT a way that technology can solve problems?
Group of answer choices
sorting quickly through data
storing data so that it is easily accessible
making value judgments
automating repetitive tasks
Answers
Answer:
making value judgements
Explanation:
honestly this is just a guess if there is any others pick that but this is just what I'm thinking
As part of the communication element, many websites use sophisticated computer programs called ______ which mimic human conversation using artificial intelligence.
Answers
Answer:
ai based learing i think
Explanation:
The base 10 number 18 is equal to which base 16 number?
10
12
14
16
Answers
Answer:
1 2 base 16
Explanation:
To convert to base 16 you divide the number with 16. 18/16=1 remainder 2;1 divide by 16 is =1
From bottom to top :1 2
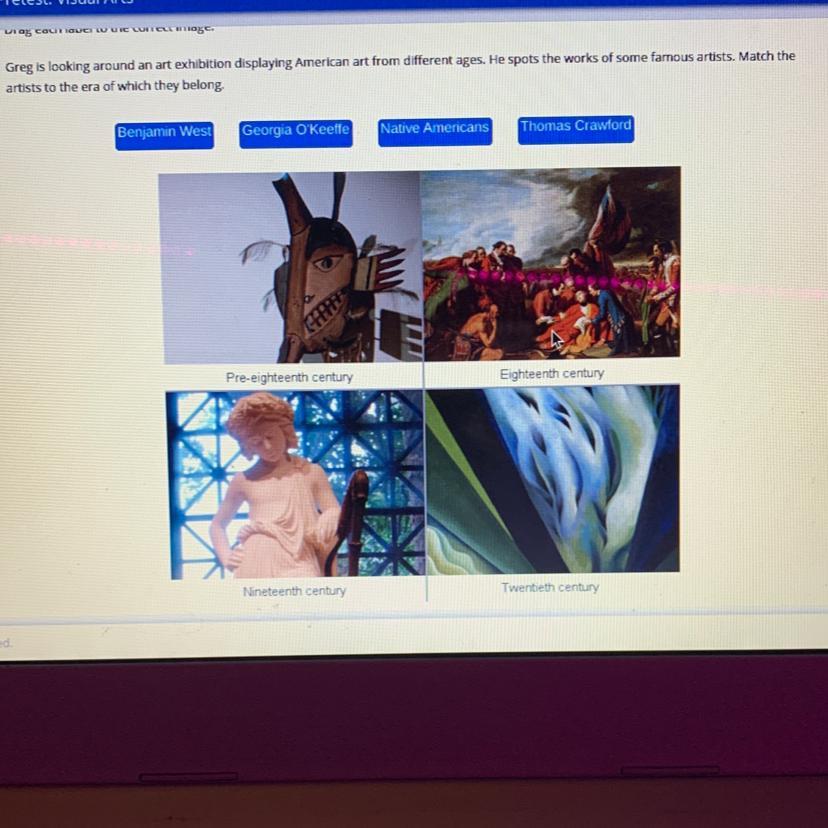
Greg is looking around an art exhibition displaying American art from different ages. He spots the works of some famous artists. Match the
artists to the era of which they belong.
Benjamin West
Georgia O'Keeffe
Native Americans
Thomas Crawford
Answers
Answer:
Benjamin west is 18th century
Thomas Crawford is 19th century
Native Americans is pre-18th century
Georgia O'Keeffe is 20th century
Explanation:
what is autocomplete

Answers
Autocomplete, or word completion, is a feature in which an application predicts the rest of a word a user is typing. In Android and iOS[1] smartphones, this is called predictive text. In graphical user interfaces, users can typically press the tab key to accept a suggestion or the down arrow key to accept one of several.
Autocomplete speeds up human-computer interactions when it correctly predicts the word a user intends to enter after only a few characters have been typed into a text input field. It works best in domains with a limited number of possible words (such as in command line interpreters), when some words are much more common (such as when addressing an e-mail), or writing structured and predictable text (as in source code editors).
PLZ HELPP ME!!!
You are driving on a highway and your gas pedal gets jammed. You cannot reduce engine
power. You should keep your eyes on the road and
A: Stay in the gear you are in. Turn off the ignition, and remove the ignition key from the lock.
B: Shift into neutral. Then turn off the ignition without locking the steering, and use your brakes to
stop.
C: Shift your vehicle into top gear. Then apply the parking brake as hard as you can
Answers
Answer:
b
Explanation:
shift to neutral then use brakes
In pedal gets jammed, Shift into neutral. Then turn off the ignition without locking the steering, and use your brakes to stop.
What to do in the above case?If the vehicle that is its accelerator pedal is said to be stuck in case a person is driving, one can press the brake and also put their hands on the wheel and then shift the gear to neutral.
Conclusively, When your gas pedal gets jammed, by doing the above that is shifting your gear into neutral and turning off the ignition without locking the steering, one can use the brakes to come to a stable halt.
Learn more about highway from
https://brainly.com/question/2919240
#SPJ2
An information system interacts with its environment by: A. processing data. B. XML protocols. C. receiving data. D. systems analysts. E. sending data.
Answers
Answer:
C. receiving data.
Explanation:
An information system interacts with its environment by receiving data in its raw forms and information in a usable format.
Information system can be defined as a set of components or computer systems, which is used to collect, store, and process data, as well as dissemination of information, knowledge, and distribution of digital products.
Generally, it is an integral part of human life because individuals, organizations, and institutions rely on information systems in order to perform their duties, functions or tasks and to manage their operations effectively. For example, all organizations make use of information systems for supply chain management, process financial accounts, manage their workforce, and as a marketing channels to reach their customers or potential customers.
Additionally, an information system comprises of five (5) main components;
1. Hardware.
2. Software.
3. Database.
4. Human resources.
5. Telecommunications.
Hence, the information system relies on the data it receives from its environment, processes this data into formats that are usable by the end users.
Seneca has just applied conditional formatting and realizes that she has made a mistake. Which action should she take to fix the mistake?
Clear the rule she created by going to the Conditional Formatting Rules Manager dialog box and deleting the rule.
Clear all rules that have been applied to the worksheet or selected range by clicking the Clear Rules button.
Use the Undo button or Ctrl+Z.
Right-click the area where the conditional formatting rule has been applied, and select Clear Rule from the menu list.
Answers
If Seneca has not done anything since the conditional formatting she can undo what her last action was. This is done by either pressing control+Z or by clicking on the undo icon.
If other actions have been done, there are a few more steps that need to be taken in order to clear the formatting. They are:
1. Select the cell or cells whose formatting you want to delete.
2. Display the Home tab of the ribbon.
3. In the Editing group, click Clear | Clear Formats.
Answer:
ITS C HOLY MOLLY
Explanation:
The purpose of a function that does not return a value is Group of answer choices to insert a temporary implementation of a function that can be refined later only used when the function needs to produce output to package a repeated task as a function even though the task does not yield a value to provide a function that can only be included in an assignment statement
Answers
Answer:
to package a repeated task as a function even though the task does not yield a value.
Explanation:
In Computer programming, a function can be defined as a group of organized, reusable sets of code that is used to perform a specific task i.e a single but related action. Thus, a function accepts data as an input, process the data and return a single result or a set of results.
Some of the notable characteristics of a function includes;
I. The name and arguments of the function must be specified by a function.
II. The implementation of a function is usually designed to be hidden from the caller.
IIII. A function define specific tasks that reusable at many points in a program.
A function that does not return a value after it executes is generally referred to as a void function. Thus, a void function uses the keyword "void" and has no explicit return statement in its body, with respect to a data type.
The purpose of a void function is to control returns back to the caller or package a repeated task as a function but, it doesn't yield a value.
What can you add to your presentation from the Insert tab?
Animations
Pictures
Variants
Transitions
Answers
Answer:
B. PICTURES
Explanation:
Answer:
I know its late but pictures is the answer.
Explanation:
I took the test and got it right.
A user is redesigning a network for a small company and wants to ensure security at a reasonable price. The user deploys a new application-aware firewall with intrusion detection capabilities on the ISP connection. The user installs a second firewall to separate the company network from the public network. Additionally, the user installs an IPS on the internal network of the company. What approach is the user implementing
Answers
"Layered approach" will be the appropriate response.
The method that divides the OS into multiple layers, is a layered approach. The latter empowers application developers to modify their internal functions as well as enhances adaptability.The network idea throughout this method is generally separated into multiple levels and a certain responsibility or activity is delegated to every other layer.
Thus the above is the right answer.
Learn more layered approaches here:
https://brainly.com/question/10105615
what is the order of gpos that are being applied to the east ou?
Answers
To determine the order of Group Policy Objects (GPOs) being applied to the East OU (Organizational Unit), you can use the Resultant Set of Policy (RSOP) or Group Policy Modeling tools in Active Directory.
These tools provide insights into the applied GPOs and their order of precedence.
Here are the general steps to find the order of applied GPOs:
Open the Group Policy Management Console (GPMC) on a domain controller or a system with the GPMC installed.
Expand the domain in the GPMC, then navigate to the East OU.
Right-click on the East OU and select "Group Policy Results" or "Group Policy Modeling."
Follow the prompts to specify the target user or computer account and other relevant settings.
Once the analysis is complete, you will be presented with a report or summary that shows the GPOs applied to the East OU and their order of precedence.
The order of GPOs is crucial because conflicts or conflicting settings in GPOs can be resolved based on their precedence. The GPO with the highest priority is applied last, overriding any conflicting settings from lower priority GPOs.
Know more about Group Policy Objects here:
https://brainly.com/question/31752416
#SPJ11
How do a router and switch differ when handling a message? Both a router and a switch use the message’s destination address to select the line to route the incoming message to. The switch will purposefully drop messages if message traffic exceeds its capacity. The router will purposefully drop messages if message traffic exceeds its capacity. There is no difference in how a router and a switch handle messages.
Answers
Answer:
The router will purposefully drop messages if message traffic exceeds its capacity.
Explanation:
As we know that the router and the switch are the connecting devices. The router works at the network layer and used for determining the shortest path
On the other hand the switch work is to connected many devices that are available in the network.
Therefore the correct option is second as the router also depicts when there is the purpose of the messaged drop[ed if the traffic of message exceeds than its capacity
Can you recommend me a movie?
Answers
anyone know how to do this

Answers
The completed program that finds the area and perimeter of the rectangle using a C Program is given below:
The Program// C program to demonstrate the
// area and perimeter of rectangle
#include <stdio.h>
int main()
{
int l = 10, b = 10;
printf("Area of rectangle is : %d", l * b);
printf("\nPerimeter of rectangle is : %d", 2 * (l + b));
return 0;
}
OutputThe area of the rectangle is : 100
The perimeter of the rectangle is : 40
If we make use of functions, it would be:
// C program to demonstrate the
// area and perimeter of a rectangle
// using function
#include <stdio.h>
int area(int a, int b)
{
int A;
A = a * b;
return A;
}
int perimeter(int a, int b)
{
int P;
P = 2 * (a + b);
return P;
}
int main()
{
int l = 10, b = 10;
printf("Area of rectangle is : %d", area(l, b));
printf("\nPerimeter of rectangle is : %d",
perimeter(l, b));
return 0;
}
OutputThe area of rectangle is : 100
The perimeter of rectangle is : 40
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Which of the following describes all illustrations created by freehand?
extension lines
sketches
leader lines
dimensions
Answers
Python - Write a program to print the multiplication table as shown in the image by using for loops.

Answers
Answer:
Explanation:
The following python code creates the multiplication table for 10 rows and 10 columns. This code uses nested for loops to traverse the table and print out the product of each multiplication. The image attached shows the output of the code.
for x in range(1, 11):
for y in range(1, 11):
z = x * y
print(z, end="\t")
print()

The program to print the multiplication table as shown in the image by using for loops is in the Source code.
The Python program that uses nested for loops to print the multiplication table:
Source code:
for i in range(1, 11):
for j in range(1, 11):
if i == 1 and j == 1:
print("x", end=" ")
elif i == 1:
print(j, end=" ")
elif j == 1:
print(i, end=" ")
else:
print(i * j, end=" ")
print()
This program will iterate through the values of `i` from 1 to 10 and `j` from 1 to 10. It checks for special cases when `i` or `j` is equal to 1 to print the headers (x and the numbers 1 to 10).
For other cases, it calculates the multiplication of `i` and `j` and prints the result.
Learn more about Nested loop here:
https://brainly.com/question/33832336
#SPJ6
what two methods might be used by an ics to control a physical system?
Answers
Two methods that an ICS (Industrial Control System) might use to control a physical system are PID (Proportional-Integral-Derivative) control and fuzzy logic control.
PID control calculates and adjusts the control output based on the error between the desired setpoint and the measured process variable. The proportional term provides immediate response to changes in the error, the integral term helps to eliminate steady-state error, and the derivative term helps to stabilize the response. Two methods that an ICS (Industrial Control System) might use to control a physical system are PID (Proportional-Integral-Derivative) control and fuzzy logic control. Fuzzy logic control uses linguistic variables to describe the system and its behavior. It takes into account the uncertainty and imprecision of measurements and uses rules based on expert knowledge to determine the control action. Fuzzy logic control can handle nonlinear systems and is more tolerant to changes in the environment and the system.
learn more about ICS (Industrial Control System) here:
https://brainly.com/question/10430559
#SPJ11