What is a class in CSS?
A.a grouping of HTML tags for which style properties can be declared
B.a selector used to define a unique style
C.a tag used to apply styles to a block of content
D.the part of a declaration describing the type of style to be applied
Answers
Answer:
A grouping of HTML tags for which style properties can be declared
Explanation:
CORRECT
Related Questions
Kaleb is looking at the list of WiFi devices currently connected to the network. He sees a lot of devices that all appear to be made by the same manufacturer, even though the manufacturer name is not listed on the screen. How could he have determined that they were made by the same manufacturer?
Answers
Kaleb can determined that they were made by the same manufacturer by the use of option c. There are a large number of devices that have addresses ending in the same 24 bits.
What unidentified devices are linked to my network, and how can I identify them?How to locate unfamiliar devices on a network manually
Open the Terminal or the Command window on your Windows, Linux, or macOS computer.Use the command prompt to look up every network setting, including the default gateway and IP address.To obtain a list of all IP addresses linked to your network, type the command "arp -a".Nowadays, every router has a distinct Wi-Fi password that is practically impossible to crack. It denotes that your mysterious devices are likely appliances you've neglected, such your DVR (perhaps a Freeview or Sky box), a smart thermostat, plug, or other smart home appliance.
Learn more about WiFi from
https://brainly.com/question/13267315
#SPJ1
See full question below
Kaleb is looking at the list of WiFi devices currently connected to the network. He sees a lot of devices that all appear to be made by the same manufacturer, even though the manufacturer name is not listed on the screen. How could he have determined that they were made by the same manufacturer?
a. There are a large number of devices that have the same OUI.
b. The first four characters are the same for a large number of the device MAC addresses.
c. There are a large number of devices that have addresses ending in the same 24 bits.
d. There are a large number of devices using the same WiFi Channel.
Expert Answer
what to write about technology?
Answers
Answer:
Lt is the moreen way or machine that helps life to be simple and easy
100 POINTS
PYTHON PROGRAMMING I:
TURTLE GRAPHICS PROJECT
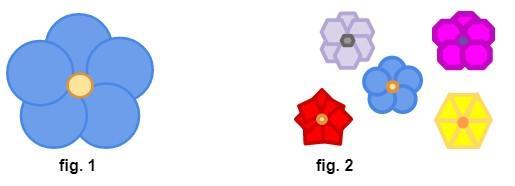
For this project you are going to create a program that draws at least 5 flowers. Each flower must have at least 5 flower petals, and can be of any shape, size or color, but each flower petal must be distinguishable from the other. See fig. 1 below. Only one of the flowers may be centered on the canvas. The rest of the flowers can be placed visibly anywhere on the canvas. See fig. 2 Each flower must use a different shape and color scheme.
Answers
For this project, you will need to use the Turtle Graphics library in Python. This library allows you to draw shapes and objects on the screen using commands.
To start, you will need to import the Turtle library. You can do this by typing the following code into your Python program:
import turtle
Next, you will need to create a turtle object. This will be the object that you will use to draw your flowers. You can do this by typing the following code into your program:
flower_turtle = turtle.Turtle()
Now that you have your turtle object, you can start drawing your flowers. To draw a flower, you will need to use the turtle's methods to draw the petals. For example, you can use the turtle's forward() method to draw a line, and the turtle's left() or right() methods to turn the turtle.
To draw a flower with 5 petals, you can use a for loop to repeat the drawing of the petals. For example, you can use the following code to draw a flower with 5 petals:
for i in range(5):
flower_turtle.forward(50)
flower_turtle.left(72)
You can also use the turtle's color() method to change the color of the petals. For example, you can use the following code to draw a flower with 5 red petals:
for i in range(5):
flower_turtle.color("red")
flower_turtle.forward(50)
flower_turtle.left(72)
Once you have drawn your first flower, you can repeat the process to draw more flowers. You can also use the turtle's penup() and pendown() methods to move the turtle without drawing a line.
Once you have finished drawing your flowers, you can use the turtle's done() method to close the window.
Good luck with your project!
PowerPoint is a visual aid for many speakers. Discuss some points to remember when adding text to a PowerPoint presentation. How do they help make the experience better for the audience and the presenter? What things can you do when creating a PowerPoint presentation to assure that your work adds to the speaker’s presentation without detracting attention from the speaker?
Answers
Answer:
Use a lot of spinning animations to draw attention. Use many colors. A lot of text so you can read from the slide in case you get lost.
Why would you use a computer's secondary memory?
O A. To look at files created on your home computer on a public
computer
B. To run word processing software on your computer
O C. To save a slide show presentation on your computer
D. To start up your computer and perform its basic tasks
Answers
Answer:
I think B
Explanation:
Secondary storage is needed to keep programs and data long term. Secondary storage is non-volatile , long-term storage. Without secondary storage all programs and data would be lost the moment the computer is switched off.
A computer's secondary memory would be used to look at the files created on the home screen of the computer.
Option A is the correct answer.
A computer is an electronic device that is used to do various kinds of operations automatically.
Now, Secondary memory can be utilized to store the data or information which can be instantly recovered.
It is also known as backup memory. USB drives, hard disk drives, optical drives, etc. are some examples of secondary memory.
Therefore, the task of locating the files in the computer is to be done by using the computer's secondary memory. So option A is true.
Learn more about the secondary memory in the related link:
brainly.com/question/24901228
#SPJ6
describe the implications of data exchange on social exchanges
Answers
The exchange of information has noteworthy consequences for interpersonal interactions.
How has social media affected this?Due to the abundance of social media channels and digital communication, personal information is frequently exchanged and scrutinized. The information available has the potential to generate personalized marketing, impact user actions, and affect social connections.
The potential outcome of this is also the possibility of privacy issues due to the vulnerability of personal information and its possible abuse and misuse.
Furthermore, the sharing of information has the potential to establish closed networks and biased environments, which can strengthen pre-existing convictions while constraining opportunities for encountering differing views.
Read more about data exchange here:
https://brainly.com/question/518894
#SPJ1
how many pieces can be connected on to a to an SPS
Answers
Answer:
i dont know
Explanation:
A Quicksort (or Partition Exchange Sort) divides the data into 2 partitions separated by a pivot. The first partition contains all the items which are smaller than the pivot. The remaining items are in the other partition. You will write four versions of Quicksort:
• Select the first item of the partition as the pivot. Treat partitions of size one and two as stopping cases.
• Same pivot selection. For a partition of size 100 or less, use an insertion sort to finish.
• Same pivot selection. For a partition of size 50 or less, use an insertion sort to finish.
• Select the median-of-three as the pivot. Treat partitions of size one and two as stopping cases.
As time permits consider examining additional, alternate methods of selecting the pivot for Quicksort.
Merge Sort is a useful sort to know if you are doing External Sorting. The need for this will increase as data sizes increase. The traditional Merge Sort requires double space. To eliminate this issue, you are to implement Natural Merge using a linked implementation. In your analysis be sure to compare to the effect of using a straight Merge Sort instead.
Create input files of four sizes: 50, 1000, 2000, 5000 and 10000 integers. For each size file make 3 versions. On the first use a randomly ordered data set. On the second use the integers in reverse order. On the third use the
integers in normal ascending order. (You may use a random number generator to create the randomly ordered file, but it is important to limit the duplicates to <1%. Alternatively, you may write a shuffle function to randomize one of your ordered files.) This means you have an input set of 15 files plus whatever you deem necessary and reasonable. Files are available in the Blackboard shell, if you want to copy them. Your data should be formatted so that each number is on a separate line with no leading blanks. There should be no blank lines in the file. Even though you are limiting the occurrence of duplicates, your sorts must be able to handle duplicate data.
Each sort must be run against all the input files. With five sorts and 15 input sets, you will have 75 required runs.
The size 50 files are for the purpose of showing the sorting is correct. Your code needs to print out the comparisons and exchanges (see below) and the sorted values. You must submit the input and output files for all orders of size 50, for all sorts. There should be 15 output files here.
The larger sizes of input are used to demonstrate the asymptotic cost. To demonstrate the asymptotic cost you will need to count comparisons and exchanges for each sort. For these files at the end of each run you need to print the number of comparisons and the number of exchanges but not the sorted data. It is to your advantage to add larger files or additional random files to the input - perhaps with 15-20% duplicates. You may find it interesting to time the runs, but this should be in addition to counting comparisons and exchanges.
Turn in an analysis comparing the two sorts and their performance. Be sure to comment on the relative numbers of exchanges and comparison in the various runs, the effect of the order of the data, the effect of different size files, the effect of different partition sizes and pivot selection methods for Quicksort, and the effect of using a Natural Merge Sort. Which factor has the most effect on the efficiency? Be sure to consider both time and space efficiency. Be sure to justify your data structures. Your analysis must include a table of the comparisons and exchanges observed and a graph of the asymptotic costs that you observed compared to the theoretical cost. Be sure to justify your choice of iteration versus recursion. Consider how your code would have differed if you had made the other choice.
Answers
The necessary conditions and procedures needed to accomplish this assignment is given below. Quicksort is an algorithm used to sort data in a fast and efficient manner.
What is the Quicksort?Some rules to follow in the above work are:
A)Choose the initial element of the partition as the pivot.
b) Utilize the same method to select the pivot, but switch to insertion sort as the concluding step for partitions that contain 100 or fewer elements.
Lastly, Utilize the same method of pivot selection, but choose insertion sort for partitions that are of a size equal to or lesser than 50 in order to accomplish the task.
Learn more about Quicksort from
https://brainly.com/question/29981648
#SPJ1
When you save something to the Desktop on a school computer, what drive letter will it save to
Answers
When you save something to the Desktop on a school computer, the drive letter it will save to the C drive.
What is a C drive?C drive is that part of the computer that contains the operating system and files of the system. The files on which we worked are saved on the C drive of the system.
This is a type of hard drive. The work we have done on the system is automatically saved on the drive. We can easily find the C drive on the computer's file explorer. It automatically saved the data, but you can save manually the data of the D drive.
Thus, the drive letter it will save to the C drive.
To learn more about C drive, refer to the link:
https://brainly.com/question/2619161
#SPJ1
A user is operating client A and sends a message to client B what is used to identify the note the transmission is meant for
Answers
Answer:
Explanation:
The connection for TCP is called a connection-oriented protocol; while in UDP it is called connectionless protocol/best-effort protocol.
A coach wants to divide the basketball team into two groups for a practice game. Which statistical measurement is the coach most likely to use?
A) percentile
B) mean
C) median
D) mode
Answers
Answer:
median
Explanation:
Answer:
C) Median
Explanation:
How many fnaf games did Scott Cawthon make?
Answers
Answer:
8 but he is making FNaF security breach
Explanation:
there is FNaF VR help wanted
Answer:
8 or 10
Explanation:
You are given an array of integers, each with an unknown number of digits. You are also told the total number of digits of all the integers in the array is n. Provide an algorithm that will sort the array in O(n) time no matter how the digits are distributed among the elements in the array. (e.g. there might be one element with n digits, or n/2 elements with 2 digits, or the elements might be of all different lengths, etc. Be sure to justify in detail the run time of your algorithm.
Answers
Answer:
Explanation:
Since all of the items in the array would be integers sorting them would not be a problem regardless of the difference in integers. O(n) time would be impossible unless the array is already sorted, otherwise, the best runtime we can hope for would be such a method like the one below with a runtime of O(n^2)
static void sortingMethod(int arr[], int n)
{
int x, y, temp;
boolean swapped;
for (x = 0; x < n - 1; x++)
{
swapped = false;
for (y = 0; y < n - x - 1; y++)
{
if (arr[y] > arr[y + 1])
{
temp = arr[y];
arr[y] = arr[y + 1];
arr[y + 1] = temp;
swapped = true;
}
}
if (swapped == false)
break;
}
}
explain the digitization process
Answers
Answer:
Digitization is the process of converting information into a digital (i.e. computer-readable) format. The result is the representation of an object, image, sound, document or signal (usually an analog signal) by generating a series of numbers that describe a discrete set of points or samples
Explanation:
The list of all passwords is kept within the operating system. Thus, if a user manages to read this list, password protection is no longer provided. Suggest a scheme that will avoid this problem. (Hint: Use different internal and external representations.)
Answers
The saved password in the operating system can be protected by the encryption method that can only be assessed by the person who knows the decryption method.
What are encryption and decryption?Encryption and decryption is a protection method that allows the safety of the passwords, texts, images, and videos from the third party or hackers.
The passwords can be protected if they are in encrypted formats where the codes are only known by the developer or the owner of the content. The readable letters and messages are converted into codes that are unreadable in the encrypted format.
When the person with the authority converts this unreadable into readable form then it is called decryption. Hence it protects the passwords from external access.
Therefore, the encrypted codes can be used to protect the passwords.
Learn more about encryption and decryption here:
https://brainly.com/question/15199366
#SPJ1
all foreign language results should be rated as fails to meet. True or false?
Answers
All foreign language results should be rated as fails to meet. This statement is true. Thus, option (a) is correct.
What is languages?
The term language refers to the spoken and written. The language is the structure of the communication. The language are the easily readability and understandability. The language are the component are the vocabulary. The language is the important phenomenon of the culture.
According to the languages are to explain the all the foreign languages are to learn in the study in the learning habits. But there is not the easy to learn. There are the must easy to the interest of to learn foreign languages.
As a result, the foreign language results should be rated as fails to meet. This statement is true. Therefore, option (a) is correct.
Learn more about on language, here:
https://brainly.com/question/20921887
#SPJ1
describe each of the following circuits symbolically. use the principles you have derived in this activity to simplify the expressions and thus the design of the circuits

Answers
The Ohm's law states that the current passing through the conductor is proportional to the voltage applied across its ends. Kirchhoff's law applies to the conservation of charge and energy in an electric circuit. Series resistors are combined end-to-end, and their combined value is equal to the sum of the individual resistors. Parallel resistors, on the other hand, are combined side-by-side, and their combined value is equal to the reciprocal of the sum of the individual resistors.
In electronic circuit diagrams, symbols represent circuit components and interconnections. Electronic circuit symbols are used to depict the electrical and electronic devices in a schematic diagram of an electrical or electronic circuit. Each symbol in the circuit is assigned a unique name, and their values are typically shown on the schematic.In the design of circuits, it is crucial to use the principles to simplify expressions.
These principles include Ohm's law, Kirchhoff's laws, and series and parallel resistance principles. The Ohm's law states that the current passing through the conductor is proportional to the voltage applied across its ends. Kirchhoff's law applies to the conservation of charge and energy in an electric circuit. Series resistors are combined end-to-end, and their combined value is equal to the sum of the individual resistors. Parallel resistors, on the other hand, are combined side-by-side, and their combined value is equal to the reciprocal of the sum of the individual resistors. Therefore, in circuit design, simplification of the circuits can be achieved by applying these principles.
For more such questions on Ohm's law, click on:
https://brainly.com/question/231741
#SPJ8
Below functions flatten the nested list of integers (List[List[int]]) into a single list and remove duplicates by leaving only the first occurrences. When the total number of elements is N, choose the one that correctly compares the time complexity with respect to N of each function.
Answers
The time complexities of the functions is (a) f1 = f3 < f2
How to compare the time complexities?The code of the functions f1, f2 and f3 are added as an attachment
To compare the time complexities of the functions, we check the loop and conditional statement in each function.
From the attached code, we can see that:
Function f1: 2 loops and 1 conditional statementFunction f2: 2 loops and 1 conditional statement in the second loopFunction f3: 2 loops and 1 conditional statementIn function f2, we have:
The conditional statement in the second loop implies that the conditional statement would be executed several times as long as the loop is valid.
This implies that:
f2 > f1 and f2 > f3
The number of loops and conditional statement in functions f1 and f3 are equal
This means that
f1 = f3
So, we have:
f2 > f1 = f3
Rewrite f2 > f1 = f3 as:
f1 = f3 < f2
Hence, the time complexities of the functions is (a) f1 = f3 < f2
Read more about time complexities at:
https://brainly.com/question/15549566
#SPJ1
![Below functions flatten the nested list of integers (List[List[int]]) into a single list and remove duplicates](https://i5t5.c14.e2-1.dev/h-images-qa/answers/attachments/kyR2nTWrbLkPxUX5lXkzrSL0PtJ99VwT.jpeg)
Build an NFA that accepts strings over the digits 0-9 which do not contain 777 anywhere in the string.
Answers
To construct NFA that will accept strings over the digits 0-9 which do not contain the sequence "777" anywhere in the string we need the specific implementation of the NFA which will depend on the notation or tool used to represent NFAs, such as state diagrams or transition tables.
To build an NFA (Non-Deterministic Finite Automaton) that accepts strings over the digits 0-9 without containing the sequence "777" anywhere in the string, we can follow these steps:
Start by creating the initial state of the NFA.
Add transitions from the initial state to a set of states labeled with each digit from 0 to 9. These transitions represent the possibility of encountering any digit at the beginning of the string.
From each digit state, add transitions to the corresponding digit state for the next character in the string. This allows the NFA to read and accept any digit in the string.
Add transitions from each digit state to a separate state labeled "7" when encountering the digit 7. These transitions represent the possibility of encountering the first digit of the sequence "777".
From the "7" state, add transitions to another state labeled "77" when encountering another digit 7. This accounts for the second digit of the sequence "777".
From the "77" state, add transitions to a final state when encountering a third digit 7. This represents the completion of the sequence "777". The final state signifies that the string should not be accepted.
Finally, add transitions from all states to themselves for any other digit (0-6, 8, 9). This allows the NFA to continue reading the string without any constraints.
Ensure that the final state is non-accepting to reject strings that contain the sequence "777" anywhere in the string.
In conclusion, the constructed NFA will accept strings over the digits 0-9 that do not contain the sequence "777" anywhere in the string. The specific implementation of the NFA will depend on the notation or tool used to represent NFAs, such as state diagrams or transition tables.
For more such questions on NFA, click on:
https://brainly.com/question/30846815
#SPJ8
In which sections of your organizer should the outline be located?
Answers
The outline of a research proposal should be located in the Introduction section of your organizer.
Why should it be located here ?The outline of a research proposal should be located in the Introduction section of your organizer. The outline should provide a brief overview of the research problem, the research questions, the approach, the timeline, the budget, and the expected outcomes. The outline should be clear and concise, and it should be easy for the reader to follow.
The outline should be updated as the research proposal evolves. As you conduct more research, you may need to add or remove sections from the outline. You may also need to revise the outline to reflect changes in the project's scope, timeline, or budget.
Find out more on outline at https://brainly.com/question/4194581
#SPJ1
The data science team created a machine learning model to group together customers with similar purchases, and divides those customers based on customer loyalty. How would you describe this machine learning approach?
Answers
Answer: This machine learning approach can be described as a clustering algorithm that groups customers based on their purchasing patterns and then further divides them based on their loyalty.
And office now has a total of 35 employees 11 were added last year the year prior there was a 500% increase in staff how many staff members were in the office before the increase
Answers
There were 5 staff members in the office before the increase.
To find the number of staff members in the office before the increase, we can work backward from the given information.
Let's start with the current total of 35 employees. It is stated that 11 employees were added last year.
Therefore, if we subtract 11 from the current total, we can determine the number of employees before the addition: 35 - 11 = 24.
Moving on to the information about the year prior, it states that there was a 500% increase in staff.
To calculate this, we need to find the original number of employees and then determine what 500% of that number is.
Let's assume the original number of employees before the increase was x.
If we had a 500% increase, it means the number of employees multiplied by 5. So, we can write the equation:
5 * x = 24
Dividing both sides of the equation by 5, we find:
x = 24 / 5 = 4.8
However, the number of employees cannot be a fraction or a decimal, so we round it to the nearest whole number.
Thus, before the increase, there were 5 employees in the office.
For more questions on staff members
https://brainly.com/question/30298095
#SPJ8
Creating a company culture for security design document
Answers
Use strict access control methods: Limit access to cardholder data to those who "need to know." Identify and authenticate system access. Limit physical access to cardholder information.
Networks should be monitored and tested on a regular basis. Maintain a policy for information security.
What is a healthy security culture?Security culture refers to a set of practises employed by activists, most notably contemporary anarchists, to avoid or mitigate the effects of police surveillance and harassment, as well as state control.
Your security policies, as well as how your security team communicates, enables, and enforces those policies, are frequently the most important drivers of your security culture. You will have a strong security culture if you have relatively simple, common sense policies communicated by an engaging and supportive security team.
What topics can be discussed, in what context, and with whom is governed by security culture. It forbids speaking with law enforcement, and certain media and locations are identified as security risks; the Internet, telephone and mail, people's homes and vehicles, and community meeting places are all assumed to have covert listening devices.
To learn more about security culture refer :
https://brainly.com/question/14293154
#SPJ1
Are AWS Cloud Consulting Services Worth The Investment?
Answers
AWS consulting services can help you with everything from developing a cloud migration strategy to optimizing your use of AWS once you're up and running.
And because AWS is constantly innovating, these services can help you keep up with the latest changes and ensure that you're getting the most out of your investment.
AWS consulting services let your business journey into the cloud seamlessly with certified AWS consultants. With decades worth of experience in designing and implementing robust solutions, they can help you define your needs while executing on them with expert execution from start to finish! AWS Cloud Implementation Strategy.
The goal of AWS consulting is to assist in planning AWS migration, design and aid in the implementation of AWS-based apps, as well as to avoid redundant cloud development and tenancy costs. Project feasibility assessment backed with the reports on anticipated Total Cost of Ownership and Return on Investment.
Learn more about AWS consulting, here:https://brainly.com/question/29708909
#SPJ1
Analyze the (generic) concept of “windows” used on PCs and MACs as part of a user-friendly GUI interface(i.e. What are they? What are they used for? What do they look like? Do they move, and if so, how? Why do you think they were named “windows”?)
Answers
Microsoft adopted the name "Windows" because it allows different jobs and applications to run at the same time. Because a popular term like "Windows" cannot be trademarked, it is officially known as "Microsoft Windows." Microsoft Windows 1.0, launched in 1985, was the initial version of the operating system.
What is a Graphic User Interface Used for?A graphical user interface (GUI) is computer software that allows a human to communicate with a computer.
The phrase "graphical user interface" (GUI) or simply "graphical interface" refers to a user interface that employs a mouse, icons, and windows. The name was coined to contrast with command line interfaces and full-screen character interfaces.
GUIs are important because they are:
Simple to useUsers can readily recognize, classify, and browse alternatives because data is represented by symbols, forms, and icons.Provide Data visualization which is recognized faster than words.Attractive.Shortcuts are provided.Multitasking is possible.Learn more about Windows:
https://brainly.com/question/25243683
#SPJ1
The most effective technique of malware propagation among the following list
Answers
Question Completion with Options:
A. Embedding & packing malcode in application programs
B. Replacing the Import-Address-Table (IAT)
C. Appending & prepending malcode into application programs
D. Embedding malcode in documents, such as MS O Office & PDF
Ε. Replicating malcode's source code
Answer:
The most effective technique of malware propagation among the following list is:
A. Embedding & packing malcode in application program
Explanation:
Malware propagation becomes effective and replicates effortlessly when malicious codes (otherwise called malcodes, which are self-replicating malicious programs) are embedded and packed in application programs. These usually take many years before they start to manifest, making them very difficult to detect. They are often triggered by some set events. Given the nature of malcodes and the culprits behind them, they are very dangerous to applications and pose substantial business risks.
1. What is virtual memory?
The use of non-volatile storage, such as disk to store processes or data from physical memory
A part of physical memory that's used for virtualisation
Some part of physical memory that a process though it had been allocated in the past
O Future physical memory that a process could be allocated
Answers
Answer:
The use of non-volatile storage, such as disk to store processes or data from physical memory.
Explanation:
Virtual memory is used by operating systems in order to allow the execution of processes that are larger than the available physical memory by using disk space as an extension of the physical memory. Note that virtual memory is far slower than physical memory.
The phrase “I suppose” helps Roosevelt create which kind of tone?
suspicious
negative
proper
humble
Answers
The phrase “I suppose” helps Roosevelt create a humble kind of tone
for better understanding, lets understand what a humble tone means
Humble kind of tone is simply a kind of tone that is said to be not proud or arrogant, modest , usually the individual feels insignificance or inferiorityExample: In the presence of so many game developers, I felt very humble. It also mean for someone to be respectful e.g. In my humble opinion your idea was wrongFrom the above, we can therefore say that the answer The phrase “I suppose” helps Roosevelt create a humble kind of tone is correct
learn more about humble tone from:
https://brainly.com/question/16589885
Answer:
it's humble
Explanation:
Lily has a cell value in a formula listed as $C$4. Which of the following is the correct term to describe this?
O Reference
O Relative Reference
O Absolute Reference
O Static Reference
Answers
Answer:
O Absolute ReferenceExplanation:
The correct term to describe a cell value in a formula that is listed as $C$4 is an absolute reference. In Excel, an absolute reference is a cell reference that includes a dollar sign ($) before the column letter and the row number. This tells Excel to always refer to the same cell, even if the formula is copied or moved to another location. In the example you provided, the cell reference $C$4 always refers to the cell at the intersection of column C and row 4, no matter where the formula is used.
Absolute Reference is the correct term to describe this, Thus, option C is correct.
What is cell value?The Cell provides details on a cell's layout, position, or contents. For instance, before doing a computation on a cell, administrators might wish to ensure that it has a number value rather than text.
An absolute reference is a right phrase to define a cell value inside a formula that is specified as $C$4. A cell reference in Excel that has a dollar sign ($) preceding the column letter as well as the row number is known as an absolute reference.
This instructs Excel to always use the same cell, regardless of whether the formula has been transferred or changed. no matter in which the formula is employed, the cell connection $C$4 in the instance that you gave will always point to the cells at the junction of column C and row 4.
Therefore, option C is correct.
Learn more about cell value, here:
https://brainly.com/question/29615796
#SPJ2
Name three risks of developing a stragtic role for information systems in a business. Explain one risk in more detail..
Answers
One risks of developing strategic role for information systems is the possibility of overspending on IT projects which may not generate the desired returns on investment.
What is the risk of overspending on IT projects?Today, businesses are engrossed with latest and greatest technological advancements which leas to overspending on IT projects that may not ultimately provide the intended value.
This risk can arise from a lack of understanding on how technology fits into business strategy or failure to properly assess the potential benefits and risks of new IT initiatives.
In an overall, the overspending on IT projects can lead to financial strain and can ultimately harm the business's ability to achieve its strategic goals.
Read more about strategic role
brainly.com/question/28332723
#SPJ1