What is the goal of checksum?
Answers
The goal of checksum is to detect errors that may have occurred during data transmission.
A checksum is a verification procedure that is employed to detect and protect errors in data. When data is transmitted across a network or written to a storage device, it can become corrupted or compromised. When data is transmitted, it is often partitioned into smaller blocks to make transmission more efficient.
The sender performs a mathematical computation on each block to generate a unique checksum value. When the receiver receives the data, it performs the same checksum calculation on the data block it received, and if the checksum value matches that of the sender, the data is accepted as correct, and if it does not match, the receiver discards the block and requests that the sender resend it.
You can learn more about checksum at
https://brainly.com/question/23091572
#SPJ11
Related Questions
Examine the following declarations:
int area;
Point pt;
Which of the following is true?
a. both are primitive variables
b. area is a primitive variable, and pt is an object reference variable.
c. both are reference variables
d. area is an object reference variable, and pt is a primitive variable.
Answers
Consider the following method:
public static void mix(String word, String letter)
{
int counter = 0;
while(word. IndexOf(letter) > 0)
{
if(word. Substring(counter,counter + 1). Equals(letter))
{
word = word. Substring(0, counter) + "0"
+ word. Substring(counter +2, word. Length());
}
counter++;
}
System. Out. Println(word);
}
What value word would be printed as a result of the call mix("Hippopotamus", "p")?
Hippopotamus
Hi0o0tamus
Hi00o0otamus
Hiootamus
Hi0po0otamus
Answers
Answer:
The value that would be printed as a result of the call mix("Hippopotamus", "p") is Hi0po0otamus.
The method starts by initializing the counter variable to 0. It then enters a while loop that continues as long as the IndexOf method returns a value greater than 0. This means that the loop will continue as long as the letter "p" is found in the word.
Inside the loop, the code checks if the character at the current position in the word (determined by the counter variable) is equal to the letter "p". If it is, it replaces that character with the character "0" and updates the value of the word variable. If it is not, the counter variable is incremented and the loop continues.
Since the word "Hippopotamus" contains two occurrences of the letter "p", the loop will run twice and replace both occurrences with "0", resulting in the output Hi0po0otamus.
Explanation:
A piece of copper metal is initially at 100.0 ∘
C. It is dropped into a coffee cup calorimeter containing 50.0 g of water at a temperature of 20.0 ∘
C. after stirring, the final temperature of both copper and water is 25.0 ∘
C. Assuming no heat losses, and that the specific heat of water is 4.18 J/g 0
C, what is the heat capacity of the copper? none of these choices is correct 2.79 13.9 3.33 209
Answers
To find the heat capacity of the copper, we can use the principle of heat transfer. The heat lost by the copper is equal to the heat gained by the water.
First, we need to calculate the heat gained by the water using the formula:
Q = m * c * ΔT
Where:
Q is the heat gained by the water
m is the mass of the water (50.0 g)
c is the specific heat of water (4.18 J/g°C)
ΔT is the change in temperature of the water (final temperature - initial temperature)
ΔT = 25.0°C - 20.0°C = 5.0°C
Q = 50.0 g * 4.18 J/g°C * 5.0°C = 1045 J
Since the heat lost by the copper is equal to the heat gained by the water, the heat capacity of the copper can be calculated as:
Q = m * c * ΔT
Rearranging the equation, we get:
Copper heat capacity = Q / ΔT = 1045 J / 5.0°C = 209 J/°C
Therefore, the heat capacity of the copper is 209 J/°C.
To know more about heat transfer visit-
https://brainly.com/question/31778162?referrer=searchResults
#SPJ11
When logging into a website that uses a directory service, what command authenticates your username and password?.
Answers
Answer: Bind
Explanation: When you log into a website that uses a directory service, the website will use LDAP to check if that user account is in the user directories and that the password is valid.
your friend joe wants to add another hard drive to his computer. what should he check to make sure that his system will support it?
Answers
Programs and data are stored and retrieved using a data-recording method that uses a solid disk of magnetic material rotating at high speeds.
A hard drive drive is what?
A non-volatile data storage device is a hard disk drive (HDD) in a computer. Storage systems that retain data after shut off are referred to as non-volatile. HDDs are merely one form of storage device, which is something that all computers require.
Which 2 types of hard drives are there?
Hard disk drives (HDD) and solid-state drives are the two most used types of storage components for laptops and desktop computers (SSD).
To know more about Hard drive visit;
https://brainly.com/question/10677358
#SPJ4
In which directory would a system administrator store scripts that should be run monthly by the cron daemon?
Answers
Answer: /etc/cron.monthly
Explanation:
Select the correct answer.
Nancy wants to buy a cooking stove that’s electrically insulated and resistant to heat. What material should she choose for the cooktop?
A.
composite
B.
polymer
C.
metal
D.
ceramic
E.
semiconductor
Answers
Answer:
E I think is the best answer
WILL MARK BRAINLIEST ONLY ANSWER LAST PART
Create a concept for a new social media service based on new technologies. The service must include functions or features that require using rich media and geolocation or some other location-sharing technology that you have researched.
Submit your plan using both text and visual elements (graphics or drawings).
These are some key points you need to cover in your concept document:
What type of social media service is it?
What is the purpose of the service?
List the functions that the service provides.
List the features that the service provides
What makes the service unique?
Who is the target audience?
What type of layout did you use for the service?
Answers
The concept for a new social media service based on new technologies that i would love to introduce the act of celebrating our social media followers on their birthdays by sending them emails or text offline.
How is the changing technology important for media?The use of technology by mass media users is one that has changed a lot in course of the years and it is still changing.
The use of changing technology or tools can help the media to reach a lot of people and one can get more customers.
Conclusively The use of Email automatic services or messages to target audience such as people between the ages of 18- 50 to celebrate our social media followers can help us to have more customer base as customers often value when they are been celebrated.
Learn more about social media service from
https://brainly.com/question/3653791
Next, let's examine what happens when you apply a style to an element that contains other elements. The body element in the HTML file contains all the elements that are displayed. Clear the existing code from the style sheet, and set the color of the body element to green. Write the code for the style change and record what you observe.
Answers
Answer:
When the body element CSS color style was changed, The color of all the text in the HTML file changed to the specified color, the same goes for font-size, font-weight, etc.
Explanation:
HTML or hypertext markup language is a markup language used in web development to implement the position and structure of the web page. It has no style, so, CSS or cascading style sheet is used to style the HTML elements in the web page.
computer programmers often refer to memory addresses using ____ notation.
Answers
Computer programmers often refer to memory addresses using hexadecimal notation.
Computer programmers often refer to memory addresses using hexadecimal notation. This is a base-16 numbering system that uses 16 digits, including 0-9 and A-F, to represent values. Each digit represents a different value, with the least significant digit on the right and the most significant digit on the left. Memory addresses are important in programming because they are used to access specific locations in memory, where data and instructions are stored. By using hexadecimal notation, programmers can represent memory addresses more efficiently, as each digit represents four binary digits, or bits, rather than just one. This makes it easier to work with large memory addresses and to understand the relationships between different memory locations. Overall, understanding memory addresses and how to represent them using hexadecimal notation is an important skill for any computer programmer.
To know more about hexadecimal notation visit: https://brainly.com/question/31478130
#SPJ11
what is the 'key exchange' problem in modern information security? encryption keys are too long. there are too many encryption keys to keep track of. two parties need to privately share the secret encryption key before communicating. the encryption key is too complicated to calculate.
Answers
The 'key exchange' problem in modern information security refers to the challenge faced by two parties who need to privately share a secret encryption key before communicating securely. Encryption is a method of converting data into an unreadable format, so that only authorized parties with the correct decryption key can access the information.
Key exchange is crucial for ensuring secure communication because it allows the involved parties to establish a shared secret key that can be used for encryption and decryption. However, exchanging keys securely can be a challenge, especially when communication is happening over an unsecured channel where eavesdroppers can intercept the messages.
One common solution to the key exchange problem is using asymmetric encryption algorithms, such as RSA or Elliptic Curve Cryptography (ECC), which involve the use of public and private key pairs. In this system, each party has a public key that can be shared openly and a private key that is kept secret. The sender encrypts the message with the recipient's public key, and the recipient decrypts it with their private key.
While asymmetric encryption provides a solution to the key exchange problem, it is generally slower than symmetric encryption methods, which use a single shared key for both encryption and decryption. To achieve the best of both worlds, many secure communication protocols combine both techniques, using asymmetric encryption to securely exchange a symmetric key that is then used for encrypting the actual data.
Learn more about key exchange here:
https://brainly.com/question/28707952
#SPJ11
in power automate how to generate dynamic title id with alphanumeric values in flow when form submitted with list update?
Answers
To generate a dynamic title ID with alphanumeric values in a flow when a form is submitted with list updates, you can use Power Automate. Here's how to do it:
Step 1: Start by logging into the Power Automate portal and creating a new flow.
Step 2: From the trigger drop-down, select the trigger that corresponds to the event that you want to capture. In this case, it will be "When an item is created or modified."
Step 3: Next, we need to set up our flow to use the form data to create a unique ID for each new form submission. This will require the use of variables to capture and store information from the form fields. We'll create two variables: one for the title ID and one for the form data. Here's how to create them:
Click the "New Step" button at the bottom of the flow designer. Choose "Add an Action." Type "initialize variable" in the search box and select it from the list of available actions. Give the variable a name and select the data type as "string." In the value field, enter the formula that you want to use to generate the ID. This could be something as simple as concatenating the current date and time with a unique identifier (e.g., "20211110-1234"). Repeat this process to create a second variable for the form data. This will allow us to capture and store the data that is submitted via the form.Step 4: Now we need to create an action to update the list item with the generated title ID and form data. Here's how to do it:
Click the "New Step" button at the bottom of the flow designer.Choose "Add an Action."Type "update item" in the search box and select it from the list of available actions.Select the site, list, and item that you want to update.In the "Title" field, enter the formula that you created earlier to generate the title ID.In the "Body" field, select the "Enter custom value" option and enter the formula that you created earlier to capture the form data.Step 5: Save and test your flow to ensure that it is working correctly. You should now be able to generate a unique title ID with alphanumeric values whenever a new form submission is made.
To learn more about "power automate", visit: https://brainly.com/question/31107034
#SPJ11
about IPO cycle with a digram
Answers
Answer:
The IPO Cycle is termed as Input-Processing-Output cycle. A computer receives data as input, processes it, stores it and then produces output. ways. This manipulation is called processing.

Does my answer differentiate between RAM and ROM. Sorry I need to be petty for this. <3

Answers
Answer:
Yes
Explanation:
Yes, your answer correctly states the difference between RAM and ROM clearly and does not need to be changed. RAM and Cache memory are volatile memory while ROM and HDD are non-volatile memory. That is the main difference and aside from this you went into more detail on each one. Therefore, in this scenario you are correct and the individual stating "bad wrong" is the one that is incorrect, most likely because they did not fully understand the answer.
Which of the following are results of technological advancements and increased automation?
Increased labor demand
Decreased productivity
Increased cost
Increased productivity
Answers
Answer:
increased productivity
Explanation:
sorry if i am not correct
true or false? the idea that users should be granted only the levels of permissions they need to perform their duties is called the principle of least privilege.
Answers
Answer: True.
Explanation:
What is Principle of least privilege ?
The notion of least privilege (POLP) in computer security restricts user's access rights to only those that are absolutely necessary for them to perform their duties.Only the files or resources required for them to do their duties are given to users authorization to read, write, or execute.Hence, the idea that users should be granted only the levels of permissions they need to perform their duties is called the principle of least privilege.
You can learn more about Principle of least privilege from the given link
https://brainly.in/question/35875103
why should one avoid noise in the computer room
Answers

For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
For all hypertext links in the document, set the font-color to ivory and set the text-decoration to none.
(CSS)
Answers
Using the knowledge in computational language in html it is possible to write a code that For ul elements nested within the nav element, set the list-style-type to none and set the line-height to 2em.
Writting the code:<!doctype html>
<html lang="en">
<head>
<!--
<meta charset="utf-8">
<title>Coding Challenge 2-2</title>
</head>
<body>
<header>
<h1>Sports Talk</h1>
</header>
<nav>
<h1>Top Ten Sports Websites</h1>
<ul>
</ul>
</nav>
<article>
<h1>Jenkins on Ice</h1>
<p>Retired NBA star Dennis Jenkins announced today that he has signed
a contract with Long Sleep to have his body frozen before death, to
be revived only when medical science has discovered a cure to the
aging process.</p>
always-entertaining Jenkins, 'I just want to return once they can give
me back my eternal youth.' [sic] Perhaps Jenkins is also hoping medical
science can cure his free-throw shooting - 47% and falling during his
last year in the league.</p>
<p>A reader tells us that Jenkins may not be aware that part of the
least-valuable asset.</p>
</article>
</body>
</html>
See more about html at brainly.com/question/15093505
#SPJ1


Which software development model encourages the creation of test plans at every phase?
A waterfall model
B V-model
C incremental model
D rapid application development model
Answers
Some one help pls will mark brainless !!!!!
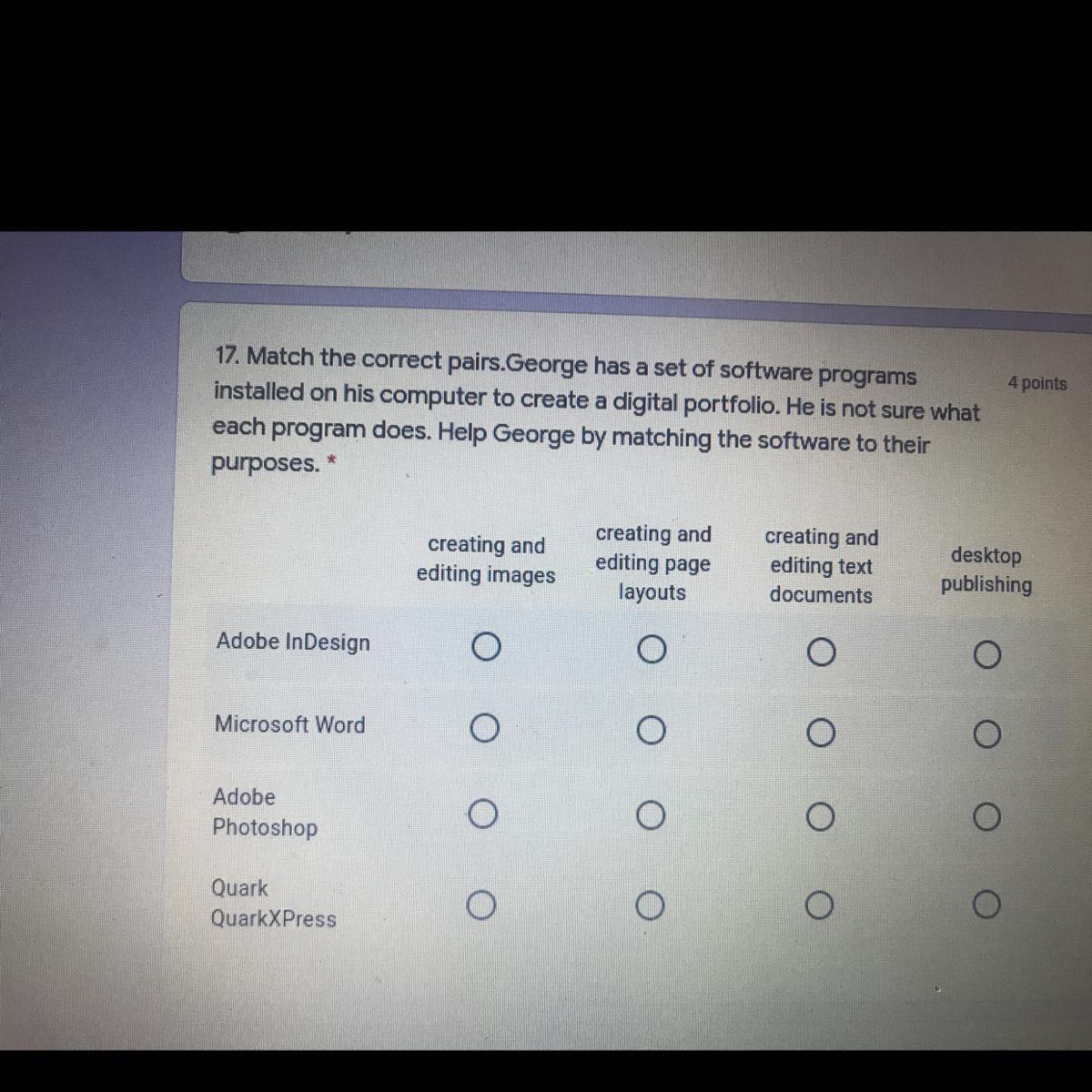
Answers
microsoft word- creating and editing word documents
adobe indesign- layouts
qaurk- publishing
Select the correct answer from each drop-down menu.
Choose the correct word to complete the sentence to explain the type of process described.
In a
process, workers shape a material by removing excess material. This process is an example of a
manufacturing process.
Answers
"In a machining process, workers shape a material by removing excess material. This process is an example of a manufacturing process."
Machining is a manufacturing process that involves the removal of material from a workpiece to achieve the desired shape, size, and surface finish. It typically involves the use of machine tools such as lathes, milling machines, drills, and grinders.
During machining, the workpiece is secured and the cutting tool is brought into contact with it, removing excess material through cutting, grinding, drilling, or other operations. This process is commonly used in industries such as automotive, aerospace, and machinery manufacturing to create precise components with tight tolerances.
Machining can be performed on a variety of materials, including metals, plastics, and composites, and allows for the production of complex shapes and intricate details.
This question should be provided as:
Select the correct answer from each drop-down menu. Choose the correct word to complete the sentence to explain the type of process described:
In a _____ process, workers shape a material by removing excess material. This process is an example of a manufacturing process.Learn more about Machining: https://brainly.com/question/29667694
#SPJ11
what do you understand by hybrid computer
Answers
Explanation:
Hybrid computers are computers that exhibit features of analog computers and digital computers. The digital component normally serves as the controller and provides logical and numerical operations, while the analog component often serves as a solver of differential equations and other mathematically complex equations.
(50 POINTS) A folder has been shared with other users and set to read-only. What does this mean for users?
Users can only read the name of the shared folder.
Users cannot add new folders or files.
Users can read and edit files.
Users can add new files but not new folders.
Answers
Answer:
B
Explanation:
1.21 lab: divide by x write a program using integers user_num and x as input, and output user_num divided by x three times. ex: if the input is:_________
Answers
A program using integers user_num and x as input, and output user_num divided by x three times is given below:
The Program#include <stdio.h>
int main(void) {
int userNum;
int x;
int ans1;
int ans2;
int ans3;
scanf("%d", &userNum);
scanf("%d", &x);
ans1 = userNum/x;
ans2 = ans1/x;
ans3 = ans2/x;
printf("%d %d %d\n", ans1, ans2, ans3);
return 0;
}
Read more about programming here:
https://brainly.com/question/23275071
#SPJ1
Keisha wants to change the default printer before printing an e-mail. Which steps will accomplish this task?
on the Home tab, clicking Print and choosing the desired printer from the Printer drop-down list
O on the File tab, clicking Print and choosing the desired printer from the Printer drop-down list
O on the Home tab, clicking Open and choosing the desired printer from the Printer drop-down list
O on the File tab, clicking Open and choosing the desired printer from the Printer drop-down list
lol
Answers
Answer:
The steps that will accomplish the task are;
On the File tab, clicking Print and choosing the desired printer from the Printer drop-down list
Explanation:
In steps required to change the default printer on Microsoft Outlook before printing as e-mail are as follows;
1) Select the File tab on the Menu bar
2) Click on the Print option on the File's Menu
3) From the Print window displayed under the File Menu in Microsoft Outlook select the desired printer from the Printer options drop-down list
The steps that will accomplish the task are On the File tab, clicking Print and choosing the desired printer from the Printer drop-down list.
he memory protection requirement must be satisfied by the operating system rather than the processor. True False
Answers
Answer:
true
Explanation:
because memory protection and if not protect all is dead
What 5 factors determine the seriousness of a gunshot wound?
Answers
Bullet size, velocity, form, spin, distance from muzzle to target, and tissue type are just a few of the many factors that can cause gunshot wound.
The four main components of extremities are bones, vessels, nerves, and soft tissues. As a result, gunshot wound can result in massive bleeding, fractures, loss of nerve function, and soft tissue damage. The Mangled Extremity Severity Score (MESS) is used to categorize injury severity and assesses age, shock, limb ischemia, and the severity of skeletal and/or soft tissue injuries. [Management options include everything from minor wound care to amputation of a limb, depending on the severity of the injury.
The most significant factors in managing extremities injuries are vital sign stability and vascular evaluation. Those with uncontrollable bleeding require rapid surgical surgery, same like other traumatic situations. Tourniquets or direct clamping of visible vessels may be used to temporarily decrease active bleeding if surgical intervention is not immediately available and direct pressure is ineffective at controlling bleeding. People who have obvious vascular damage require rapid surgical intervention as well. Active bleeding, expanding or pulsatile hematomas, bruits and thrills, absent distal pulses, and symptoms of extremities ischemia are examples of hard signs.
To know more about wound:
https://brainly.com/question/13137853
#SPJ4
Which of the following statements are true? Select one or more: a. A socket is a kind of opening. b. A socket represents one endpoint of a network connection. c. A program uses a socket to communicate with another program over the network. d. Data written by a program to the socket at one end of the connection is transmitted to the socket on the other end of the connection, where it can be read by the program at that end.
Answers
Answer:
a. A socket is a kind of opening.
b. A socket represents one endpoint of a network connection.
c. A program uses a socket to communicate with another program over the network.
d. Data written by a program to the socket at one end of the connection is transmitted to the socket on the other end of the connection, where it can be read by the program at that end.
Explanation:
A socket is an endpoint in the network node of a computer network that serves the role of sending and receiving data written by a program across the network. The application programming interface specifies the attributes of a socket, through the socket descriptor. The socket address serves the purpose of making the socket identifiable by other hosts.
The socket address consists of the transport protocol, IP address, and port number. Just like a port serves as the endpoint in hardware, so does the socket also function as an endpoint in a network connection.
HELP HELP. I NEED 2 CODES SOLVED


Answers
The code is written in an incorrect syntax and has a few errors. It seems to be a mixture of two different procedures that are not well-defined.
How to explain the codeHowever, based on the structure and assumptions, I can infer that the output of this code will display the value of ans, which is the sum of the result of F(11,20) and G(-4,3).
The result of F(11,20) will be either 20.5 or 20, depending on the value of the variable p in the if-else statement. The result of G(-4,3) will be 3 because the loop inside the G procedure iterates three times, incrementing the value of val by 1 each time, and then returns val, which is 3. Therefore, the output of the code will be 23.
Learn more about code on
https://brainly.com/question/26134656
#SPJ1
Add pictures using the_____tab
Answers
insert
in word, click on the insert tab at the navigation pane.