what is the main purpose of automatic calculation and posting controls?
Answers
The main purpose of automatic calculation and posting controls is to ensure accuracy and efficiency in financial transactions and record-keeping.
Automatic calculation and posting controls are a set of features in accounting software that automatically calculate and post financial transactions. These controls help ensure that financial data is accurate, up-to-date, and reliable, and they make it easier to track transactions and generate reports.
Automatic calculation and posting controls can include features such as automatic tax calculations, automatic depreciation calculations, and automatic reconciliation of accounts. These features help streamline accounting processes, reduce errors, and save time and effort for accounting professionals. The benefits of automatic calculation and posting controls include:
Accuracy: By automating financial calculations and postings, accounting professionals can reduce the risk of errors and ensure the accuracy of financial data. This helps ensure that financial reports are reliable and trustworthy.Efficiency: Automatic calculation and posting controls can help accounting professionals save time and effort, allowing them to focus on higher-level tasks such as financial analysis and planning.Productivity: By automating routine tasks such as data entry and calculations, accounting professionals can increase their productivity and efficiency in the workplace.Reporting: Automatic calculation and posting controls make it easier to generate financial reports, which can be used for financial analysis, planning, and decision-making in the organization.You can learn more about financial transactions at
https://brainly.com/question/30023427
#SPJ11
Related Questions
5.if a customer intends to transmit more data than they receive, which forms of dsl would be appropriate?
Answers
If a customer intends to transmit more data than they receive, the appropriate form of DSL would be Asymmetric Digital Subscriber Line (ADSL).
ADSL provides higher upload speeds compared to download speeds, making it suitable for users who need to send more data than they receive. To use ADSL, the customer would need an ADSL modem and a subscription from a DSL service provider.
#SPJ11
Learn more about DSL: https://brainly.com/question/12859851
If a customer intends to transmit more data than they receive, Asymmetric Digital Subscriber Line (ADSL) and Symmetric Digital Subscriber Line (SDSL) are the two DSL types that would be appropriate.
The following are some distinctions between the two:ADSL (Asymmetric Digital Subscriber Line): ADSL allows for a faster download speed than upload speed, making it suitable for customers who prefer to download more content than upload. ADSL is an acronym for Asymmetric Digital Subscriber Line. The speed is determined by the type of ADSL service you have subscribed to; for instance, ADSL2+ has a speed limit of 24 Mbit/s downstream and 1 Mbit/s upstream.SDSL (Symmetric Digital Subscriber Line): SDSL is a type of DSL that provides equal upload and download speeds, making it appropriate for customers who require a balanced amount of download and upload speed. SDSL is an acronym for Symmetric Digital Subscriber Line. The speed is the same for uploading and downloading, with a range of 128 Kbps to 3 Mbps.Learn more about data: https://brainly.com/question/179886
#SPJ11
What are the local, state, and national opportunities that may be available to those who participate in CTSOs?
Answers
Answer: Students
Explanation:
The National Coordinating Council for Career and Technical Student Organizations (CTSO) advocate for the values that the Career and Technical Education (CTE) curriculum instills in students.
In association with the Association for Career and Technical Education (ACTE), the CTSO work to instill career skills to students in middle school, high school, and post-secondary institutions such as Business, Health science, Information Technology and Finance amongst others.
CTSOs such as Educators Rising and Business Professionals of America encourage and support CTE programs for their members which also has a Federal Support of $1.1 billion.
can someone give me an window blur code in javascript like i mean full coding
Answers
Answer:
uh wha- what?!?!
Explanation:
no
find it urself
:P
jekqfjewil bored anyways
What plan can businesses use to protect sensitive data from malicious attacks?
Anti-spyware
Cybersecurity
Ethical hacking
Information assurance
Answers
Answer:
cybersecurity
Explanation:
it's either that or anti-spywhare but cybersecurity seems more likely
So no one will be able to access their information from hacking to their screen
Pls true or false answer correctly plsss needs help

Answers
32.
are also known as cyber burglars.
a. Hackers
b. Programmers
c. Software Engineers d. Crackers.
Page 3 of 4
Answers
Answer:
a
Explanation:
hackers access your system unauthorized
What 5 factors determine the seriousness of a gunshot wound?
Answers
Bullet size, velocity, form, spin, distance from muzzle to target, and tissue type are just a few of the many factors that can cause gunshot wound.
The four main components of extremities are bones, vessels, nerves, and soft tissues. As a result, gunshot wound can result in massive bleeding, fractures, loss of nerve function, and soft tissue damage. The Mangled Extremity Severity Score (MESS) is used to categorize injury severity and assesses age, shock, limb ischemia, and the severity of skeletal and/or soft tissue injuries. [Management options include everything from minor wound care to amputation of a limb, depending on the severity of the injury.
The most significant factors in managing extremities injuries are vital sign stability and vascular evaluation. Those with uncontrollable bleeding require rapid surgical surgery, same like other traumatic situations. Tourniquets or direct clamping of visible vessels may be used to temporarily decrease active bleeding if surgical intervention is not immediately available and direct pressure is ineffective at controlling bleeding. People who have obvious vascular damage require rapid surgical intervention as well. Active bleeding, expanding or pulsatile hematomas, bruits and thrills, absent distal pulses, and symptoms of extremities ischemia are examples of hard signs.
To know more about wound:
https://brainly.com/question/13137853
#SPJ4
Who Likes K-pop? Which group or groups do you like



Answers
Answer:
i like k pop a little and im a blink i also like mother mother and arctic monkeys
Explanation:
Answer:
k-pop & Blackpink
Explanation:
<3
Why is John Von Neumann to a remarkable name?
si
Answers
Answer:
John von Neumann is remarkable for his vast knowledge of mathematics, and the sciences as well as his ability to correlate the pure and applied sciences.
Explanation:
John von Neumann who was born on December 28 1903, and died on February 8,1957 was known for his extensive knowledge of mathematics, physics, computer, economics, and statistics. In computing, he was known to conceive the idea of the self-replicating machines that thrive in the automata cellular environment, the von Neumann architecture, stochastic computing and linear programming.
He developed the game theory in Economics, and laid the foundation for several mathematical theories. He contributed greatly to quantum mechanics and quantum physics. Little wonder, he was dubbed "the last representative of the great mathematicians."
Which of these statements about tags is false?
Group of answer choices
Their font is center-aligned by default.
They serve as the label for a row or column.
They automatically display as the first row or column.
Their font is bold by default.
Answers
Answer:
LOL i don't even know
Explanation:
Find solutions for your homework
engineering
computer science
computer science questions and answers
this is python and please follow the code i gave to you. please do not change any code just fill the code up. start at ### start your code ### and end by ### end your code ### introduction: get codes from the tree obtain the huffman codes for each character in the leaf nodes of the merged tree. the returned codes are stored in a dict object codes, whose key
Question: This Is Python And Please Follow The Code I Gave To You. Please Do Not Change Any Code Just Fill The Code Up. Start At ### START YOUR CODE ### And End By ### END YOUR CODE ### Introduction: Get Codes From The Tree Obtain The Huffman Codes For Each Character In The Leaf Nodes Of The Merged Tree. The Returned Codes Are Stored In A Dict Object Codes, Whose Key
This is python and please follow the code I gave to you. Please do not change any code just fill the code up. Start at ### START YOUR CODE ### and end by ### END YOUR CODE ###
Introduction: Get codes from the tree
Obtain the Huffman codes for each character in the leaf nodes of the merged tree. The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively.
make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.
CODE:
import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = None # Get the root node
current_code = None # Initialize the current code
make_codes_helper(None, None, None) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
pass # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
pass # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
pass # Make a recursive call to the left child node, with the updated current code
pass # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
Expected output
Example 1:
"i" -> 001
"t" -> 010
" " -> 111
"h" -> 0000
"n" -> 0001
"s" -> 0111
"e" -> 1011
"o" -> 1100
"l" -> 01100
"m" -> 01101
"w" -> 10000
"c" -> 10001
"d" -> 10010
"." -> 10100
"r" -> 11010
"a" -> 11011
"N" -> 100110
"," -> 100111
"W" -> 101010
"p" -> 101011
Example 2:
"a" -> 0
"c" -> 100
"b" -> 101
"d" -> 111
"f" -> 1100
"e" -> 1101
Answers
Get codes from the treeObtain the Huffman codes for each character in the leaf nodes of the merged tree.
The returned codes are stored in a dict object codes, whose key (str) and value (str) are the character and code, respectively. make_codes_helper() is a recursive function that takes a tree node, codes, and current_code as inputs. current_code is a str object that records the code for the current node (which can be an internal node). The function needs be called on the left child and right child nodes recursively. For the left child call, current_code needs increment by appending a "0", because this is what the left branch means; and append an "1" for the right child call.CODE:import heapq
from collections import Counter
def make_codes(tree):
codes = {}
### START YOUR CODE ###
root = tree[0] # Get the root node
current_code = '' # Initialize the current code
make_codes_helper(root, codes, current_code) # initial call on the root node
### END YOUR CODE ###
return codes
def make_codes_helper(node, codes, current_code):
if(node == None):
### START YOUR CODE ###
return None # What should you return if the node is empty?
### END YOUR CODE ###
if(node.char != None):
### START YOUR CODE ###
codes[node.char] = current_code # For leaf node, copy the current code to the correct position in codes
### END YOUR CODE ###
### START YOUR CODE ###
make_codes_helper(node.left, codes, current_code+'0') # Make a recursive call to the left child node, with the updated current code
make_codes_helper(node.right, codes, current_code+'1') # Make a recursive call to the right child node, with the updated current code
### END YOUR CODE ###
def print_codes(codes):
codes_sorted = sorted([(k, v) for k, v in codes.items()], key = lambda x: len(x[1]))
for k, v in codes_sorted:
print(f'"{k}" -> {v}')
Test code:
# Do not change the test code here
sample_text = 'No, it is a word. What matters is the connection the word implies.'
freq = create_frequency_dict(sample_text)
tree = create_tree(freq)
merge_nodes(tree)
codes = make_codes(tree)
print('Example 1:')
print_codes(codes)
print()
freq2 = {'a': 45, 'b': 13, 'c': 12, 'd': 16, 'e': 9, 'f': 5}
tree2 = create_tree(freq2)
merge_nodes(tree2)
code2 = make_codes(tree2)
print('Example 2:')
print_codes(code2)
To know more about Huffman codes visit:
https://brainly.com/question/31323524
#SPJ11
a web services provider has suggested improving their security through the implementation of two-factor authentication. what would be the most likely authentication method?
Answers
The most likely authentication method for the web services provider to implement two-factor authentication would be to use a combination of something the user knows (such as a password) and something the user has (such as a token or code sent to their mobile device). This would add an extra layer of security to the authentication process and reduce the risk of unauthorized access to the web services.
Two-factor authentication (2FA) is a security measure that requires users to provide two different types of authentication factors to verify their identity.
The most common combination for two-factor authentication is something the user knows (knowledge factor) and something the user has (possession factor).
The knowledge factor is typically a password, which the user knows and provides as the first authentication factor.
The possession factor can be a physical token, a mobile app that generates one-time passcodes, or a hardware-based authentication device that the user possesses.
By combining these two factors, the web services provider adds an extra layer of security to the authentication process.
Even if an attacker manages to obtain the user's password, they would still need to possess the second factor (e.g., physical token or mobile device) to gain access.
This combination of two different authentication factors enhances the security of web services and reduces the risk of unauthorized access.
Learn more about two-factor authentication:
https://brainly.com/question/31255054
#SPJ11
Gottfried semper said that a people, their technology, and their aesthetics were all connected. according to him, the four basic kinds of technology available are: (select all that apply)
Answers
They reflected the values, traditions, and craftsmanship of a particular civilization.
What are the four basic kinds of technology according to Gottfried Semper?Gottfried Semper believed that the four basic kinds of technology available are:
Tectonic: Refers to the construction and assembly of buildings and structures using materials like wood, stone, and metal. It involves the principles of structural engineering and architectural design.Ceramic: Involves the use of fired clay or pottery for various purposes such as pottery vessels, bricks, tiles, and decorative objects. It includes techniques like pottery wheel throwing, molding, and glazing.Textile: Relates to the production of fabrics and textiles using techniques like weaving, knitting, and embroidery. It encompasses the creation of clothing, tapestries, carpets, and other textile-based products.Composite: Involves the combination of different materials to create new materials with enhanced properties. It includes practices such as laminating, layering, and bonding materials together.Semper believed that these four types of technology were interconnected and influenced by a people's culture, aesthetics, and society.
Learn more about craftsmanship
brainly.com/question/30107694
#SPJ11
how to find the volume of cube in computer in QBASIC program
Answers
Answer:
QBasic Programming
REM PROGRAM TO DISPLAY VOLUME OF CUBE. CLS. INPUT “ENTER LENGTH”; L. ...
USING SUB PROCEDURE.
DECLARE SUB VOLUME(L) CLS. INPUT “ENTER LENGTH”; L. ...
SUB VOLUME (L) V = L ^ 3. PRINT “VOLUME OF CUBE ”; V. ...
USING FUNCTION PROCEDURE.
DECLARE FUNCTION VOLUME (L) CLS. ...
FUNCTION VOLUME (L) VOLUME = L ^ 3.
Differences between electricity geyser and gas geyser.
plz help me.answer correctly.
Answers
Answer:
ELECTRIC GEYSER
1. Electric geyser works with the help of electricity
2. Electric geyser is widely used by all over the world
3. Electric geyser is expensive
4. Electric geyser is a consumes high watts
GAS GEYSER
1.Gas geyser works with the help of lpg (liquid petroleum gas)
2.Gas geyser is used less by the people all over the world
3. Gas is not expensive
4. Gas geyser consumes gas like liquid petroleum gas etc
consider the code segment below. the code consists of seven lines. some of the lines of code are indented. begin block line one: if, begin block, on time closed up with initial capital t, end block. line two is indented one tab: begin block, display, begin block open quote, hello period, close quote, end block, end block. line three: else begin block line four is indented one tab: if, begin block absent end block. line five is indented two tabs: begin block, display, begin block open quote, is anyone there, question mark, close quote, end block, end block. line six is indented one tab: else line seven is indented two tabs: begin block, display, begin block open quote, better late than never, period, close quote, end block, end block. end block. end block. if the variables ontime and absent both have the value false, what is displayed as a result of running the code segment?
Answers
Better late than never is displayed as a result of running the code segment if both the onTime and absent variables have the value false.
Which grid's robot is moved to the gray square by the program correctly?While the program will not accurately move the robot to the gray square in Grid II, it will do so in Grid I. The right choice is this one.
Which of the following statements most accurately sums up how comparisons between items between pairs behave?MyList is iterated over in the code segment, with each element being compared to all succeeding elements.
To know more about code segment visit :-
https://brainly.com/question/20063766
#SPJ4
What is not an option when a user is exporting contacts to share with others?
- VCARD files
-Electronic business cards
-XML
-CSV
Answers
Answer:
i think it is CSV
Explanation:
The one among the option that is not used when a user is exporting contacts to share with others is CSV.
What is exporting contacts?This is known to be the movement of contacts or information of people or clients from one server, place to another.
Note that The one among the option that is not used when a user is exporting contacts to share with others is CSV as that does not concern this movement at all.
Learn more about contacts from
https://brainly.com/question/12831236
#SPJ2
Justine was interested in learning how to play the piano. She has successfully passed every level of music book and is planning her own concert. What stage of ability development is Justine at?
a.
Novice
b.
Apprentice
c.
Master
d.
Mentor
Please select the best answer from the choices provided
A
B
C
D
Answers
Answer:
C
Explanation:
Edge 2021
The stage of ability development is Justine at Master. The correct option is C.
Thus, The four basic phases of ability development are as follows: Novice Apprentice, Advanced Mentor stage.
Justine has successfully passed every level of music book, indicating a high level of proficiency and expertise in playing the piano.
Planning her own concert further suggests that she has achieved a mastery of the instrument and is now capable of performing at an advanced level. Therefore, the stage of ability development that Justine is at is the "Master" stage.
Thus, The stage of ability development is Justine at Master. The correct option is C.
Learn more about Master, refer to the link:
https://brainly.com/question/16587416
#SPJ7
what are the key features of the point-to-point protocol (ppp)? (choose three) can authenticate devices on both ends of the link. can be used on both synchronous and asynchronous serial links. establishes, manages, and tears down a call. does not carry ip as a payload
Answers
C, a replacement for the programming language B, was initially created by Ritchie at Bell Labs between 1972 and 1973 to create utilities for Unix.
Thus, It was used to re-implement the Unix operating system's kernel. C increasingly gained popularity in the 1980s.
With C compilers available for almost all current computer architectures and operating systems, it has grown to be one of the most popular programming languages.
The imperative procedural language C has a static type system and supports recursion, lexical variable scoping, and structured programming. It was intended to be compiled, with minimal runtime assistance, to offer low-level memory access and language constructs that easily map to machine instructions.
Thus, C, a replacement for the programming language B, was initially created by Ritchie at Bell Labs between 1972 and 1973 to create utilities for Unix.
Learn more about C, refer to the link:
https://brainly.com/question/30905580
#SPJ4
Which function allows you to use master clips from another project, without creating new media or importing?
Answers
Media referencing or also known as media linking is the function that allows user to make a video creation and use master clips without creating new media or importing.
Media referencing allows editors to link to media files, such as video, audio, or images, that are stored in another project, instead of importing or duplicating them into a new project. This can be useful in many scenarios, such as when working with large video files, or when collaborating with other editors who are working on different parts of the same project.
When you use media referencing, the original media files remain in their original location, and are not copied or duplicated into the new project. This saves storage space and reduces the time it takes to import media files.
When you make changes to the linked media files in the original project, those changes are automatically reflected in the linked files in the new project. This makes it easy to reuse and repurpose media files across multiple projects, without having to manage multiple copies of the same files.
Media referencing is a common feature in professional video editing software, such as Adobe Premiere Pro and Avid Media Composer. It is often used in post-production workflows for film and television, where editors need to work with a large number of media files and collaborate with other team members.
Learn more about video creations here:
https://brainly.com/question/28019000
#SPJ11
when a compiler generates the binary code for a source program written in a high-level programming language, it does not know where and how the binary code will be loaded by the operating system. why not? in order to generate a binary code, the compiler, however, must make certain assumptions on where and how the binary code will be loaded in the main program by the operating system. what are the reasonable assumptions that are made by most of compilers in terms of where and how?
Answers
Because the loading process depends on the particular operating system and hardware platform being utilized, a compiler cannot predict where or how the binary code will be loaded by the operating system.
Where is binary data kept?The hard disk drive is where binary data is primarily kept (HDD). A spinning disk (or disks) with magnetic coatings and heads that can read and write data in the form of magnetic patterns make up the device.
How is binary code employed in computer systems? What is binary code?Every binary code used in computing systems is based on binary, which is a numbering system in which each digit can only have one of two potential values, either 0 or 1.
To know more about operating system visit:-
https://brainly.com/question/6689423
#SPJ4
Dose brainly give you notifications on you're phone when you go into the site
Answers
Answer:
Yep it does ^_^
What limits the lifespan or lifetime of data in a computer or network?
ARP
TTL
ACK
SYN
Answers
The TTL value is a mechanism that limits the lifespan or lifetime of data in a computer or network.
Which of the following is used to describe a computer that is used to access an iSCSI hard disk across the network?
a. iSCSI target
b. iSCSI requestor
c. iSCSI initiator
d. iSCSI terminator
Answers
An iSCSI initiator refers to the computer or device that initiates the connection and sends requests to access an iSCSI (Internet Small Computer System Interface) hard disk across the network.
It is responsible for establishing and managing the communication between the initiator and the iSCSI target, which is the storage device being accessed. The iSCSI initiator encapsulates SCSI commands into IP packets and transmits them over the TCP/IP network to access the storage resources on the iSCSI target. In simpler terms, the iSCSI initiator acts as a client that enables a computer to connect to and utilize storage resources on remote iSCSI devices, such as hard disks, over a network connection.
Learn more about network here:
https://brainly.com/question/29350844
#SPJ11
To set a column style, click this button of the page layout tab?
Answers
Answer:
Click the page layout in the ribbon menu of the application, then click the down button of the columns option and select the desired column style.
Explanation:
Microsoft word is a software used to create and edit text documents. The ribbon menu is at the top of the application. It holds the functions and styles of the word processing tool.
The column of a word document can be styled to have one (default) or more columns. This functionality is found in the page tab in the ribbon.
anyone help me please
# help # be care #

Answers
2. Telecommunications, also known as telecom, is the exchange of information over significant distances by electronic means and refers to all types of voice, data and video transmission. ... A complete, single telecommunications circuit consists of two stations, each equipped with a transmitter and a receiver.
3. Data transmission and data reception or, more broadly, data communication or digital communications is the transfer and reception of data in the form of a digital bitstream or a digitized analog signal over a point-to-point or point-to-multipoint communication channel.
I HOPE IT'S HELP :)
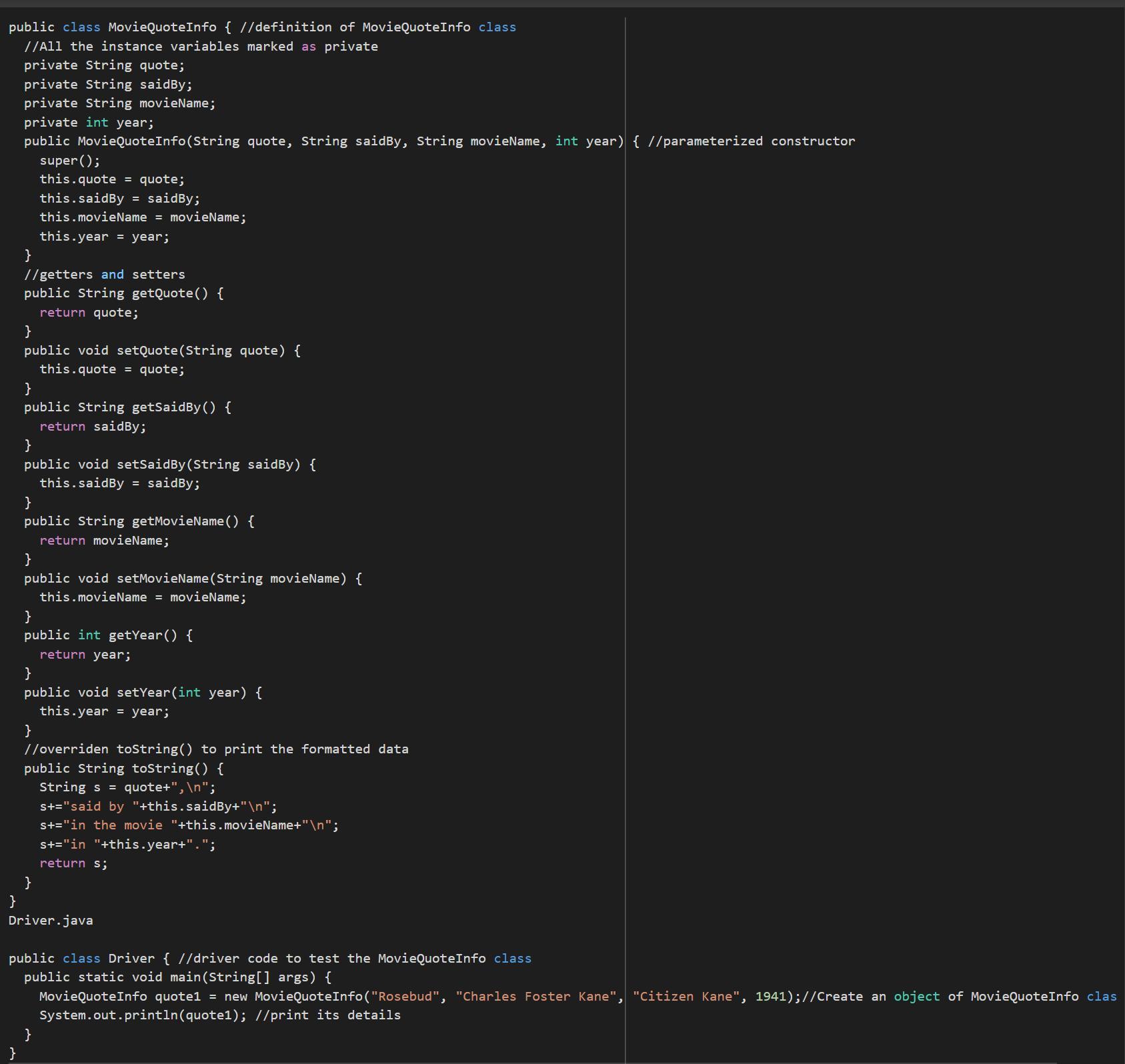
Write, compile, and test the MovieQuoteInfo class so that it displays your favorite movie quote, the movie it comes from, the character who said it, and the year of the movie: I GOT IT DONT WATCH AD.
class MovieQuoteInfo {
public static void main(String[] args) {
System.out.println("Rosebud,");
System.out.println("said by Charles Foster Kane");
System.out.println("in the movie Citizen Kane");
System.out.println("in 1941.");
}
}
Answers
Using the knowledge of computational language in JAVA it is possible to write a code that removes your favorite phrase from the movie. It consists of two classes in which one is driver code to test the MovieQuoteInfo class.
Writing code in JAVA:
public class MovieQuoteInfo { //definition of MovieQuoteInfo class
//All the instance variables marked as private
private String quote;
private String saidBy;
private String movieName;
private int year;
public MovieQuoteInfo(String quote, String saidBy, String movieName, int year) { //parameterized constructor
super();
this.quote = quote;
this.saidBy = saidBy;
this.movieName = movieName;
this.year = year;
}
//getters and setters
public String getQuote() {
return quote;
}
public void setQuote(String quote) {
this.quote = quote;
}
public String getSaidBy() {
return saidBy;
}
public void setSaidBy(String saidBy) {
this.saidBy = saidBy;
}
public String getMovieName() {
return movieName;
}
public void setMovieName(String movieName) {
this.movieName = movieName;
}
public int getYear() {
return year;
}
public void setYear(int year) {
this.year = year;
}
//overriden toString() to print the formatted data
public String toString() {
String s = quote+",\n";
s+="said by "+this.saidBy+"\n";
s+="in the movie "+this.movieName+"\n";
s+="in "+this.year+".";
return s;
}
}
Driver.java
public class Driver { //driver code to test the MovieQuoteInfo class
public static void main(String[] args) {
MovieQuoteInfo quote1 = new MovieQuoteInfo("Rosebud", "Charles Foster Kane", "Citizen Kane", 1941);//Create an object of MovieQuoteInfo class
System.out.println(quote1); //print its details
}
}
See more about JAVA at brainly.com/question/12975450
#SPJ1
9
10
1
2
3
4
5
Which is a valid velocity reading for an object?
45 m/s
45 m/s north
O m/s south
0 m/s
Answers
Answer:
Maybe 45 m/s north I think I'm wrong
Answer:45 ms north
Explanation:
Classroom content transaction
examples use of IT
Answers
Answer:
1. Online classes
2. Presentation
3. Account of books
Nathan notices his computer System is slowing down when he tries to copy documents to it he also gets a prompt I warned him that the system is running low on storage space which hardware device should he consider upgrading in order to increase the system storage space?
Answers
Answer:Hard drive or Solid State drive
Explanation: